Until today, Microsoft Windows users who’ve been unfortunate enough to have the personal files on their computer encrypted and held for ransom by a nasty strain of malware called CryptoLocker have been faced with a tough choice: Pay cybercrooks a ransom of a few hundred to several thousand dollars to unlock the files, or kiss those files goodbye forever. That changed this morning, when two security firms teamed up to launch a free new online service that can help victims unlock and recover files scrambled by the malware.
 First spotted in September 2013, CryptoLocker is a prolific and very damaging strain of malware that uses strong encryption to lock files that are likely to be the most valued by victim users, including Microsoft Office documents, photos, and MP3 files.
First spotted in September 2013, CryptoLocker is a prolific and very damaging strain of malware that uses strong encryption to lock files that are likely to be the most valued by victim users, including Microsoft Office documents, photos, and MP3 files.
Infected machines typically display a warning that the victim’s files have been locked and can only be decrypted by sending a certain fraction or number of Bitcoins to a decryption service run by the perpetrators. Victims are given 72 hours to pay the ransom — typically a few hundred dollars worth of Bitcoins — after which time the ransom demand increases fivefold or more.
But early Wednesday morning, two security firms – Milpitas, Calf. based FireEye and Fox-IT in the Netherlands — launched decryptcryptolocker.com, a site that victims can use to recover their files. Victims need to provide an email address and upload just one of the encrypted files from their computer, and the service will email a link that victims can use to download a recovery program to decrypt all of their scrambled files.
The free decryption service was made possible because Fox-IT was somehow able to recover the private keys that the cybercriminals who were running the CryptoLocker scam used on their own (not free) decryption service. Neither company is disclosing much about how exactly those keys were recovered other than to say that the opportunity arose as the crooks were attempting to recover from Operation Tovar, an international effort in June that sought to dismantle the infrastructure that CryptoLocker used to infect PCs.
That effort culminated in the takeover of the GameOver Zeus botnet, a huge crime machine that infected an estimated 500,000 to 1 million PCs and that was being used as a distribution platform for CryptoLocker.
“After Operation Tovar, a significant blow was dealt to criminals infrastructure and we stopped seeing new Cryptolocker infections being spread,” said Uttang Dawda, a malware researcher with FireEye. “They tried to recover that infrastructure, but in the process copied over the private encryption keys to a part of Fox-IT’s infrastructure.”
Dawda said it’s important to note that this service only unlocks files encrypted by CryptoLocker. Although there are several copycat strains of malware — including CryptoWall, CryptoDefense and OnionLocker — CryptoLocker has by far the largest “market share” among them.
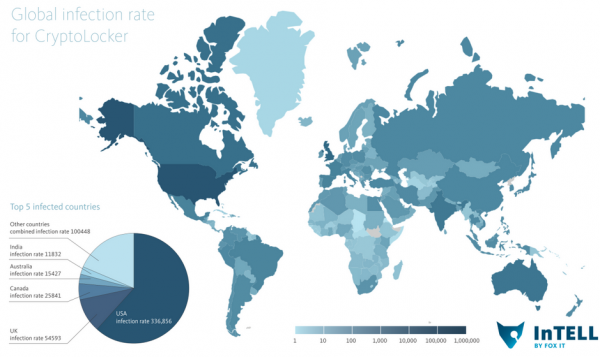
It’s not clear how many systems are infected with CryptoLocker, but it is likely to be in the six figures. According to Fox-It, when CryptoLocker infections first started in September 2013, the largest number of infections in one month occurred during October 2013, with over 155,000 systems affected worldwide. After October 2013 the rates dropped, but still steadily pacing at around 50,000 infections per month.
Sadly, most of those victims probably lost all of their most treasured files. Fox-It says that only 1.3% of victims paid a CryptoLocker ransom.
“Therefore, a large amount of victims likely permanently lost files due to this attack,” the company wrote in a blog post about the new service.




It’s not too late if you still have the encrypted files, as I suspect many people do, hoping that someday a program like this would come along. Some files, such as photos, if not backed up, are truly irreplaceable. I hope this product receives widespread publicity. FireEye & Fox-IT deserve a hearty thanks from all of us.
Absolutely. I sent a message to Krebs about this as soon as I heard this morning in hopes he would help get the word out. Awareness needs to be raised…
Tweet it, FB, G+ —- let’s hit social media folks and spread the word!
There is no program that came along. They did some crazy take down / attack on the crooks botnet and got the crooks to copy their keys to a server they controlled. So they have a list of 2048 keys for those only previously infected. If someone new gets infected and the key is sent to another server only the crooks control it’s the same thing all over again, hence all the variants floating around. That 2048 key is presumably the only way on earth right now to unlock the files. No program dismantles anything. If it did, all encryption used for good, bad, personal privacy would be at risk. Correct me if im wrong, but i think this is the article is saying.
You are correct in that, in theory, a new straight of Cryptolocker could come out that uses a new key, and the service would not be able to decrypt those infections. They could also change the encryption algorithm around and break this recovery service that way too. But a change like that requires a change to be made and then distributed throughout their entire (sketchy connection) infrastructure. Can be done, but it takes time and effort, neither of which are in large supply in organized crime.
The current Cryptolocker is based on a 2048 (bit) key and the security firms got this key. Between this and reverse engineering the encryption technique, they are able to provide this service for both current, past, and future victims of the current form of Cryptolocker.
This would be a model someone should recommend to Hold Security (free to individuals after advising paid clients of their exposure.)
+1 for reading my mind
Need I suggest regular back ups to external drives might be worth while!?
Hopefully people will remember to unplug the drives!
agrees! …and they don’t accidentally include the malware in the backup and over-write a previously good back up…
edit: “the malware” should read “any malware”
just make sure they’re not physically connected drives
Or Synology.
Synology has their own version of cryptolocker.
https://www.synology.com/en-us/company/news/article/470
it only affects older versions of their NAS OS.
That was my point.
Wonder why people still don’t use DVDs to backup. I do.
Most people don’t have the 1000 year M-Disc DVD BluRays (and drives for making them) – and regular DVD-+R’s rely on a dye technology that gradually goes bad after a few years – rendering a backup on them a very shaky proposition unless you’re doing it all the time (which most folks wouldn’t do).
Great new! This ransomware are very hard and well made! Now people can recover his files from this malware.
Any hope for those that copped CryptoWall infection?
Not until they suffer the same fate as the operators of GameOver Zues.
Does this solution help only those that have been encrypted up to now?
I am not that up to date on private and public keys but what happens if someone changes the private key and then infects?
Yes, basically they got lucky and acquired a database dump of all current private keys. So if your files are encrypted with the public key of a private key not found in that dump, you’re SOL.
Nice to see that these companies made the software available for free. Compare this story to the Hold Security story where that company only looked for a way to profit.
But great work reporting both stories Mr. Krebs.
Point of information: The “infection rate” map doesn’t look like it shows rates, just total infections, which makes more sense given the numbers. To show rates the map would have to give the numbers as something like infections per 100,000 computers.
Otherwise, excellent article, as usual.
My guess , it won’t be long before FireEye and Fox-IT will be asking for money for this service.
Exactly my thoughts. The amount of bandwidth to process all these files is going to add up.
Does anyone know if it only locks files on the C drive or ALL conneced drives?
I’m smart enough to only install programs/OS on my C drive and everything else is on other drives, but I know some people store their stuff on the C drive. If did, I’d be processing TB’s of data using this service.
So yea…don’t expect this to be free for long.
I don’t think so. I believe multiple governments were involved in the “takedown” of the network and to allow some company to make money from what were the spoils of a crime would not fly to well with the public… you can pay the crooks or you can pay some company, I don’t think so.
You only need to send them a single encrypted file, which they then use to determine which private key decrypts the file. At that point they send you a program that will decrypt all your files locally using the private key they found to work. I really don’t expect this to become a service with a price. FireEye doesn’t need the chump change and I haven’t seen the money grubbing attitude from Fox-IT.
Yes, it can/will encrypt files on all attached drives, including network shares.
The article pretty clearly states that you only need to submit only 1 encrypted file to them and they will provide you a link to a decryption program…not that you will be sending all your encrypted files to them for decryption.
“Victims need to provide an email address and upload just one of the encrypted files from their computer, and the service will email a link that victims can use to download a recovery program to decrypt all of their scrambled files.”
The thing I am not quite getting is why not just provide the download link to everyone?
Because the private key will not be the same for every user.
From what’s comment a few minutes earlier (http://krebsonsecurity.com/2014/08/new-site-recovers-files-locked-by-cryptolocker-ransomware/comment-page-1/#comment-272806):
> You only need to send them a single encrypted file, which they then use to determine which private key decrypts the file. At that point they send you a program that will decrypt all your files locally using the private key they found to work.
So, if you have thumb drives & external harddrives connected via USB for various backup’s, you should unplug/re-plug in each time you wish to save a file to your external components to keep this issue from affecting all drives? Would be a pain to do so as I backup alot of business files throughout the day, but well worth it if it keeps that data safe in this instance.
It’s a pain but when its important files (especially for a business) you need to back them up to an offline storage location – something that is connected all the time would just get encrypted as well.
Other variants of this program are in circulation and if the owners of Cryptolocker get it going again they’ll use new keys that this site won’t have…its too big a risk not to have a plan and process for your business (since it can literally shut down most small businesses).
It infects/encrpts files on any mapped drive.
Fox IT is providing the Program with the correct Key to do the decryption yourself. In the article it says you only need to upload a single file. It does not say, but can be inferred, this is so they can test the various private keys to find the correct one to provide to the victim in the decryption program.
Your fear mongering about this not being free for long is based on a lack of understanding of what Fox IT and Fire Eye are providing. A closer read of the article should avoid this type of mistake in the future.
No bandwidth is used really unless I’m missing a detail. They were able to get the keys off the server that you’d have to pay the crooks for. So you get your 2048 bit key and de crypt your files locally. It’s not a program that dismantles the encryption they just basically got access to a database of keys the crooks held to enforce the ransom.
Outstanding Brian, thanks!
I always tell people that if you don’t need to be running Microsoft Windows then you should wipe it from your hard drive. It’s the most virus and malware infected OS in the world.
I always tell people that its really easy to get an infection if you cut your hand, so its easiest to just cut them off to prevent this.
SO stealing that!
I always tell people that if you run out of toilet paper you can always use Microsoft Windows discs to wipe your bum.
I didn’t know a synology NAS runs Windows.
Brian, the long list of months on the right? Make it a short list of years, then when clicking on a year, the months are presented. Thanks, as always, for your great work!
Excellent result, it would have been nice to also recover the ransoms and return them to those who were forced to pay, although admittedly that is a much more difficult objective. This is still an acceptable overall outcome and after all the trouble Cryptolocker caused, people might not be so easily caught off guard by future variants.
As usual, FireEye continues to be extremely cool about how they handle these things. Their research has been exceptional over the years. Well done. (And well done FoxIT as well.)
SiL / IKS / concerned citizen
Its not working….
The website is saying that the files are not encrypted…
You were probably attacked by a Cryptolocker clone, not Cryptolocker. The site only works on CL infections.
That or their site could be overwhelmed with submissions. Give it a few hours and try again.
of course like your web site however you have to check the spelling on quite a few of your posts.
A number of them are rife with spelling problems and I find it very troublesome
to inform the reality then again I’ll surely come back again.
Feel free to surf to my page Unreal Tournament 3 PC Trainer Download
Yeah, score one for the good guys.
Have Fun,
Jeff
I wonder if the two security firms used the Hearbleed exploit to get those private keys
Unfortuantely for me, this website couldnt find the decryption keys for the files we had Cryptolockered a few months ago. Not a big deal because most of the data was restored from backup anyway, but would have been fun.
Interesting comment.
Anyone achieve success on getting their Cryptolockered files de-crypted via the website?
Unforutnatelly,
doesnt work for me ether…
I am not sure, If I was infected by Cryptolocker or some other ransomware (my files look like 2jsa2114fndsaon2)… How can I found it out?
thanks
An excellent service being provided for free which shows that white hats are really out there.
Dell have a great hardware firewall called Sonicwall that stops all programs like Cryptolocker as well as viruses, root kits etc…expensive but highly effective
hardly. have you ever heard of iodine tunnels and fastflux? crypters.
bypass firewalls in one, fastflux keeps its IPs ever-dynamic to avoid filters, crypters stop detection.
I know 2 people well enough, who sell their own cryptolocker creations. the truth is, gameover gang’s builder is nothing special.
and cryptolocker isn’t a product name necessarily, it’s just a product type.
either way, great work, Brian, very nice work.
I got saved from the cryptolocker bug by this very blog. Mere hours after reading about CL here on Krebs, I immediately upgraded my malware protection just before these crooks tried to slam my main business PC.
I LOVE seeing these guys getting some their own bitter medicine. Way to go!
Great to see this service is being offered for free by these two companies. Good for them and they deserve the associated publicity.
ironically, those files, documents, pictures, and mp3s are my LEAST important to me.
Interesting how one bunch feeds off the other, one wonders if it isn’t one firm with 2 personalities.
One that criminally creates demand, and one that sells solutions.
I take it you missed the part where this decryption service is being provided for free?
Brian… will you be coming to Minneapolis?
Sorry, wrong thread.
Tried it on a file but got “Unsuccessful loading key: RSA key format is not supported”.
Maybe I didn’t save the key they way they want, but haven’t gotten a response either…
I have for 5 years now kept my external backup device disconnected when backing up files.I want the ability to wipe my drive or get a new to use at a moments notice.Backups of backups never hurts.
I tried to decrypt the files following their instructions and it did spit out a new “decrypted file” but the file still didn’t open 🙁
I have a user that is infected with CryptoWall. I have uploaded an encrypted file, but this application states that it is not encrypted with CryptoLocker.
Any suggesetions?