The recent hacker break-in at Sony Pictures Entertainment appears to have involved the theft of far more than unreleased motion pictures: According to multiple sources, the intruders also stole more than 25 gigabytes of sensitive data on tens of thousands of Sony employees, including Social Security numbers, medical and salary information. What’s more, it’s beginning to look like the attackers may have destroyed data on an unknown number of internal Sony systems.
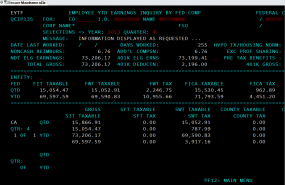
Screen shot from an internal audit report allegedly stolen from Sony and circulating on file-trading networks.
Several files being traded on torrent networks seen by this author include a global Sony employee list, a Microsoft Excel file that includes the name, location, employee ID, network username, base salary and date of birth for more than 6,800 individuals.
Sony officials could not be immediately reached for comment; a press hotline for the company rang for several minutes without answer, and email requests to the company went unanswered. But a comprehensive search on LinkedIn for dozens of the names in the list indicate virtually all correspond to current or former Sony employees.
Another file being traded online appears to be a status report from April 2014 listing the names, dates of birth, SSNs and health savings account data on more than 700 Sony employees. Yet another apparently purloined file’s name suggests it was the product of an internal audit from accounting firm Pricewaterhouse Coopers, and includes screen shots of dozens of employee federal tax records and other compensation data.
The latest revelations come more than a week after a cyberattack on Sony Pictures Entertainment brought down the company’s corporate email systems. A Sony spokesperson told Reuters that the company has since “restored a number of important services” and was “working closely with law enforcement officials to investigate the matter.”
Several media outlets reported at the time that Sony employees had been warned not to connect to the company’s corporate network or to check email, and noted that Sony’s IT departments had instructed employees to turn off their computers as well as disable Wi-Fi on all mobile devices.” Other reports cited unnamed investigators pointing to North Korean hackers as the source of the attack, although those reports could not be independently confirmed.
Such extreme precautions would make sense if the company’s network was faced with a cyber threat designed to methodically destroy files on corporate computers. Indeed, the FBI this week released a restricted “Flash Alert” warning of just such a threat, about an unnamed attack group that has been using malware designed to wipe computer hard drives — and the underlying “master boot record” (MBR) on the affected systems — of all data.
KrebsOnSecurity obtained a copy of the alert, which includes several file names and hashes (long strings of letters and numbers that uniquely identify files) corresponding to the file-wiping malware. The FBI does not specify where the malware was found or against whom it might have been used, noting only that “the FBI has high confidence that these indicators are being used by CNE [computer network exploitation] operators for further network exploitation.” The report also says the language pack referenced by the malicious files is Korean.
The FBI alert references several network traffic “signatures” that organizations can use to detect the traffic seen in previous attacks from this malware — traffic that appears to beacon back to (most likely compromised) systems in Thailand, Poland and Italy. But the alert also says this type of vigilance may only serve to let organizations know that their files are currently in the process of being deleted.
“The following Snort signature can be used to detect the beacon traffic, though by the time the beacons occur, the destructive process of wiping the files has begun,” the alert warned.
Here’s the Snort signature, in case this is useful for any readers who didn’t get this memo:
Alert tcp any any – > [88.53.215.64, 217.96.33.164, 203.131.222.102] [8080, 8000] (msg: “wiper_callout”;
dsize:42; content: “|ff ff ff ff|”; offset: 26; depth: 4; sid: 314;
Update: 1:58 p.m. ET: Multiple sources are reporting that the links to the torrents for the stolen Sony internal data were posted on Pastebin late Monday morning. Less than an hour after that post went live, the individual hosts that were sharing copies of the Sony data came under sustained denial-of-service attacks apparently aimed at keeping the files from being shared with other torrent users.
Also, the security guys over at Packetninjas have posted a useful write-up on a malware sample they spotted from early July 2014 that matches the file name of the malware described in the FBI’s Flash alert about the file-wiping malware. Packetninjas notes that the file also was calling home to the same control server in Thailand that was documented in this week’s FBI alert.
This file directory tree, included in the leaked data, offers a glimpse into the sheer volume of files apparently compromised in this breach.
This is a developing story. More to come. Stay tuned.




“Recipients may share this information…, but not via publicly accessible channels.”
Yup. May not be shared….
For something like 11 years, I’ve vaguely questioned: Why aren’t network traffic “signatures” and blocklists implemented at the national internet border? We have physical border protection, why is there no national internet border protection?
I can fathom rights protections as one explanation for allowing continuing KNOWN maliciousness. And, perhaps law enforcement doesn’t have the permission.
Well for starters, it would be a HUGE rights issue. I can’t think of any way to do that without giving the “border admin” access to read pretty much everything and violating everyone’s right to free speech. Secondly, it’s a technical impossibility. Even countries that attempt to secure their border can’t do it very effectively.
One related working technology is ‘Cleanpipe’ ISPs. There are multiple ISPs running cleanpipes. You could still chose to be on your ‘dirty pipe’–your choice.
Yes, but clean pipe ISP services is entirely different than a ‘national internet border’.
Stolen data, stolen payment card info, ‘zombie-ing’ personal computers, etc isn’t a HUGE enough rights issue yet, rhetorical?
(Home Depot breached, Target breached, etc…Sony Entertainment…)
Define “national internet border”.
@Savoia di Lucania At the ‘Autonomous Systems’ (AS) of the backbone providers–the major backbones running across oceans/borders.
Build cleanpipes etc all the way to the border Autonomous Systems.
national internet border Like China has!?
I’m meaning more like what many corporations are already doing 100’s of thousands of times, or more, but instead move it to the bigger lines where outside malicious acts are coming from outside the country.
Blocklists are sometimes used at corportations. Signature scanning is sometimes done at corporations. Spam-catching is done at some corporations. Etc. Instead, implement it at the bigger lines closer to the outside countries.
They already regularly jump borders via proxies anyway.
Implementing a Geo Block on countries that US has trade embargo wouldn’t hurt .
This does just reinforce that the use, and therefore availability, of usernames and passwords is no longer a via means of user authentication. As long as there is information for hackers to “get” it will be gotten.
Thanks for posting. This story has some lag to it. I think they were saved by the holiday weekend…..but now I’m beginning to see it popping up on all the security lists. Funny, Reddit had it on day one. LOL
The Hollywood Reporter seems to have had the story on the 24th, but no one would have thought to look there.
That previous leak was just a leak of filenames. It was a 200 MB zip file of just filenames, reportedly corresponding to 100 TB of files.
This current leak is a leak of some actual files.
Well it is hard for me to feel sorry for SONY, but then again, maybe they can use their considerably clout along with the MPAA to bring about more action against nation state bad actors in the future.
Quite frankly I view that corporation in pretty much the same light as an American mob organization, and also not much different than NORK.
What a lot of internet commenters seem to be forgetting/ignoring in their gleeful hatred of Sony is that it’s a company like any other that hires regular people who have no vested interest in their product and who lack the power to make any decisions that might have angered the hackers in question. I work in the mailroom at the studio. The mailroom. Not in development. Not in post-production. Not in marketing. I’m as below the line as you can get. NOTHING I say or do affects the product. Yet here I am, a victim of the hack. I can only cross my fingers and hope that I’m too unimportant and low on the corporate ladder for anyone to care enough to steal my info.
Sony will soon mail out letters starting with “Because the security of the personal data of our employees is of utmost importance, we are offering you 12 months of credit monitoring at no cost to you…”
IIRC, the whole idea of free credit monitoring after breaches came from Sony’s response to the PlayStation hack. Ironically, that approach may be better suited to that breach (and this one) than the Target & Home Depot breaches, neither of which involved SSNs or passwords.
they did it last night.
So now the questions I have is are those file names known to A/V packages for scans and removal? Why doesn’t the FBI tell us all what they know? How did Sony get hit? While individual people are not a concern to DPRNK unless they are GOV connected it is always a good idea for all of us to understand what needs to be done to protect our systems. After all our financial lives are as critical to us as to any corporation.
HA! You’re not going to get much from the Secret Service in the way of technical information about this latest hack, mainly due to its overall complexity.
It stinks of an insider job, and this time, the hack is pretty profound, and current. The time it takes to sift through all of this data can take months. It is FAR from a simple process. there are no “easy” buttons or simple forms to fill out. No “twenty free questions” answered by the culprits.
Seeing that the corporation has been compromised in the past, and probably cleaned up to remove the path of the intrusion, the chips have to be all thrown in, in order to find out who is the cause of this. It could have been alot more disasterous if they did not act in the way they did.
The reason the Government doesn’t release corporate information to the public is that they don’t want copy cat attacks using the same methods on other companies.
As a caveat, at least the FBI releases some of the information via private channels to allow others to shore up against these type of attacks. Additionally there are a TON of highly technical websites that are following this incident and offering their technical side of the situation. if your asking for a short sweet answer, that may be released several years from now, when the courts decide to allow the release of the information.
For cases like this, when the majority of the DoJ and other enities are involved, they will go to the Nth degree and figure out who the mole(s) are and they will be the first of a long line standing for judgement.
It may take longer than a snap of a finger – but thats life. In order to prosecute some one, they will need proof without a shadow of a doubt. in this case, I am pretty sure they have captured enough data off the network to reconstruct the scene. Now comes part 1 of the 2 part series, finding out who did it. The second part will be the government showing their findings to a jury.
Can’t wait for the updated information
That screenshot appears to be from an IBM mainframe app (TSO-SPF based, originally intended for a dumb 3270 series screen). Probably accessed by a PC remote client.
If they reached a mainframe CISC (which they seem to have by the look of this 3270 screenshot), that clearly means they got access to a core infrastructure server. They probably got access to a lot of things surrounding it as these mainframes usually acts a middleware between other critical infrastructure components.
Hell is just starting for the employees and other victims…
It is probably a downloaded screenshot graphic file sitting in a Win/Unx user directory rather than one the intruder captured him/herself by accessing CICS, hence the KOS caption “Screen shot from an internal audit report …” .
Not saying CICS or MVS is impervious to penetration but definitely much harder (assuming rational security manager configuration) target than Win/Unx.
That is only a screenshot from an internal audit report. Auditors routinely dump all kinds of errata into their reports. ALT-PRT SC, then paste into Word…
This is a serious enough breach without adding unnecessarily to hysteria.
CICS (‘customer information & control system’) is IBM’s adaptation of the ‘online, all the time’ airline control program originally developed for American Airlines back in the 60s and 70s. ACP and CICS were designed for high efficiency, high volume access and high security.
I was a mainframe computer operator on a IBM CICS system that managed a large insurance company utilizing over 600 terminals, all in an operating system that fit itself and all of the user’s applications into 16MB of RAM on a mainframe system that filled a room the size of a department store.
I also was a CICS systems programmer for six years back in the 80s. There are virtually no recorded instances of CICS systems being systematically, externally hacked by interlopers and outsiders.
The odds of compromising a CICS mainframe system are quite long – those kinds of things are locked down beyond belief.
Even if you had every user IDs and password for a CICS system (and there’s no evidence posted yet of user / PW lists for mainframe system access), it would not help you.
IBM’s RACF (resource access and control facility) is the gold standard for mainframe security.
This is a serious enough breach without adding to hysteria by stating “they reached a mainframe CISC” – there’s no evidence that this happened.
Dear B_Brodie – Youe assertions about the inherent security of CICS are totally misplaced. Until very recently almost every CICS installation out there was still running telnet and ftp as the access protocol and many still are. Once a hacker is on the LAN of a company they can sniff passwords in a second and then log in as an existing user. In my experience most system administrators and programmers for mainframes live in an absurd bubble of self mis-belief that their systems are secure by design, or more usually “by obscurity” and just because they are old. As a result they run the risk of being complacent and ignorant of security practices. That said, when it comes to the other enemy of security, change, they often score quite highly!
But Mainframees are just softwware systems attached to a network and as Joshua Corman says software=vulnerable, networked=exposed.
MadmusoIS, calling mainframe software system insecure due to the possibility of an organization’s use of insecure network protocols to access that system is the same as calling a bank’s server software insecure due to the possibility that a customer could lose a debit card on which the PIN is written.
In any case, though you may be correct that an insecure network may allow an uncredentialed individual to log in to a mainframe software system using a captured userid and password, unless that userid has elevated privilege, the platform will remain uncompromised.
Most mainframe installations I know of require end-to-end SSL encryption of all sessions.
I don’t know if Sony had this policy.
Yep, good eye Vee… Probably CICS tranid EYTF .
You do realise that Sony are a Japanese company, right?
Perhaps they realised that doing a Megaupload style take down wouldn’t work on a company as big as Sony, so ‘stopped the foreign threat’ another way?
North Korea wouldn’t put two hours of effort into stealing some Sony films.
And you know this how?
North Korean officials are upset about the Sony movie depicting an assassination plot against their fearless leader. Don’t you think that is a form of provocation. I am not condoning the hack, but it seems reasonable to me that would be sufficient motivation for state-sponsored hackers to ‘have at it’.
“I don’t generally spend a lot of time writing about breach stories that I didn’t break. Particularly breaches that appear to impact mainly employees of the breached organization, which seems to be the case with the USPS breach.”
This is different from the USPS thing? There are a heck of a lot of postal employees and retirees.
Yes it’s different. I don’t just write about stories that everyone else is writing about unless I can advance the story in some significant way. If you’ve got some information that would help me advance the story about the USPS breach, by all means please share it with me privately.
Should we assume that their customer and client databases have also been pilfered?
Assumptions are always dangerous, but you could do a lot worse than to draw your own conclusions from viewing this listing of the files taken.
http://krebsonsecurity.com/wp-content/uploads/2014/12/tree.txt
At this point, is this simply a list of files or are they documents that have actually been leaked?
The SPEData file that was kicking around (the file that was linked to in the defacement image that the hackers left on screens) was a list of some 16 million filenames that GOP claim to have taken.
This tree appears to be the directory structure of the first batch of released files, which is only about 38500 files, a tiny subset of the data GOP claim to have stolen.
The screener release that everyone has automatically linked to this attack seems fishy, however. Those files were unlikely to have been on these servers, they were likely rips of the awards screeners that Sony mailed to industry members & movie reviewers.
Brian,
Is there any way to find out if this may be several groups taking advantage of the original attack? A group could have hacked employee info (insider even) and waited for the right moment to release SSNs and salaries. Another could have been pirating movies all along but because we are looking more closely at anything Sony related, we saw that.
There is a disconnect between a North Korea attack and “We want Equality” per the original screen shot.
I agree with you, Linda. Despite what some early reports say (citing unnamed US officials), it does’t feel like the work of NK. Seems more opportunistic than that.
Sony to Officially Name North Korea as Source of Hack Attack
http://recode.net/2014/12/03/sony-to-officially-name-north-korea-as-source-of-hack-attack/
Is there any known precedence for state sponsored cyber attackers selling employee or user information like credit card thieves do?
Files do look limited to Sony Entertainment there are several divisions here in the states. When I worked there systems were not connected that is still the case last I knew. btw this link does display employee names in filenames.
Vee, your statements that “WE” Americans are somehow more committed or “better” at securing data is sheer folly. I’ve been in the BIZ since the 1970’s – believe me – we have just as many dodo-heads here as they do in other countries. I KNOW – I have BEEN to nearly every country on earth, and I have assessed data centers in India, China, Thailand, the Philippines, Australia, Israel, Kenya, Nigeria, and many South and Central American countries. You are blatantly wrong in your assumptions that outsourcing is somehow responsible. In fact, Target received info from an “OUTSOURCED” data center in India that had they heeded the info, they may have stopped their breach. The so-called “committed” Americans chose to ignore the info they received from the “Outsourced” folks…
Thank you for redacting the employee’s personal date (name, id, etc) in your sample screen in the article.
I have seen too many security articles showing sample screen shots leaving the personal data in.
What you did is wise.
Thank you.
Mark Allyn
While I’m sure Brian has read the FBI flash, if you are in a security role for your company, you can generally get access to these reports simply by contacting your local FBI office. Ask for Flash Report #A-000044-MW.
Our contact at the FBI is always very helpful. I would assume however, patience may be in order as they likely have their hands full.
The other question is: is this one breach and malware from another source or one hacking with No. Korea laughing at us because we think they sent the malware.
Why would the Koreans post SSN and salaries? That sounds more like the equality asked by the original post by #GOP. Are the Koreans playing a political game on the US after we “assume” it was them because of “The Interview”? Releasing movies for pirating sounds more like an internal group with a cause.
http://www.examiner.com/article/is-sony-hacking-linked-to-no-korea-disgruntled-employees-or-a-publicity-stunt?cid=db_articles
One thing to note is that, despite widespread assumptions to the contrary, the release of the movies almost certainly has nothing to do with the hack.
At least 4 out of the 5 movies had already been mailed out as screener DVDs to movie reviewers and industry professionals, so there were already thousands of copies of those films in circulation prior to the hack. The fifth movie has been around in one form or another for 2-3 years, so it’s not much of a reach to assume that a screener copy of that escaped as well.
There’s no reason to assume that the movie footage was taken as part of the hack, particularly when you consider that the servers that were compromised were unlikely to even contain the footage in the first place.
Almost everyone has just made the assumption that the movies were part of the stolen data simply because of the timing.
Great work Brian
Thank you for all the info, Brian. would love to know if theres any new insight or info as this progresses. To be honest, there’s a lot of Sony employees reading this right now.
There’s also a lot of former Sony employees keeping a very close eye on this thing as well.
The stolen data doesn’t just pertain to current employees, it goes back over a decade.
I know that a lot of reporting organizations have pulled the files themselves, but is there any list still out there someplace where us former Sony employees can look to see if we’ve been confirmed as having been sent into the world?
Sony has been dumping (RIFing) large numbers of people, including those with six-figure salaries. My guess ™ is one or more of them retaliated, along with God only knows who else.
Why? Well, now we see a table of what the execs at Sony are paid (bear in mind these are base salaries, not total compenstaion) released to the public –
https://deadline.com/2014/12/sony-hacker-executive-salaries-michael-lynton-amy-pascal-1201305434/
Heh.
As for all the HR data that seem to have been taken, well, those are not so useful to anyone wanting to make some money from their efforts.
As for the movies, screeners are watermarked. I don’t know how easy stripping those data would be, though.
For what it’s worth, I don’t think much of Sony, at all, and routinely decline work there. The Japanese are nice enough, but the Americans… no. Thus, all this is hardly a surprise to me…
salted hash has photos of the workstation screens on this post;
http://www.csoonline.com/article/2851649/physical-security/hackers-suggest-they-had-physical-access-during-attack-on-sony-pictures.html
I don’t know who you are, and I don’t care. Could be coincidence, but I had used “Vee” for years on here, years ago. And you ain’t me.
I can’t say I really care about a 3 lettered username on a comments section- I really don’t. Carry on, coincidence or not. Seriously, man, I couldn’t care, honestly.
But to point out to the older members around here, like JCitizen: that guy isn’t me, who was the Vee back from years ago. I haven’t posted on Krebs in a year or more.
Is that file tree from the 100TB or only the 40GB that has officially been released?
so far, all I’ve seen is the 40GB collection.
Guys, this story just SCREAMS retaliation for the upcoming movie “The Interview”.
When I saw trailers for the film, I was honestly wondering how the psycho dictator would take it, and what he might do.
It’s the first thing I thought of when I read that it was potentially of Korean origin.
Very interesting, indeed.
I thought so at first, and that may still be the case. But I question if North Korea has the capacity alone to do this so well? I think its clear the US intelligence is pathetic these days and the Countries we should be watching seem to be able to do whatever without our knowledge. We appear to be sitting ducks without anyone firing back
at the enemy and many times we don’t appear to even know who that is?
looks like spe02 torrent is out now and contains 1.1 Gb of Data.
http://rghost.net/59406876
part 1 is here.
http://pastebin.com/5j3usvDD
part 1 link
http://rghost.net/59369171
part 1 of the spe torrent
http://rghost.net/59369171
funy thing was sony’s own cloud servers were seeded the torrent.
http://www.theregister.co.uk/2014/12/03/strange_things_afoot_with_great_sony_pictures_torrent_data_leak/
What I find interesting is this was a combination of taking content,personal data and destroying data. It was not a typical data mining operation which would be more about selling personal data for gain. This is more vengeful in its nature and whoever did it. Was trying to affect Sony from all avenues. I am a bit confused on why our government seems bent on using so much technology to spy on us through agencies like the NSA. But seem to act like a two bit private eye when it comes to corporate hacking? I know we heard from the head of the FBI just weeks ago on how they bad guys are still advancing faster then us. But exactly how fast is that? Tell me when do we start hitting back?
http://fusion.net/story/31227/sony-pictures-hack-spreads-to-deloitte-thousands-of-audit-firms-salaries-are-leaked/
this is from a company wide memo sent to employees:
“Yesterday, we told you that we are offering all employees identity protection services with a third-party service provider, AllClear ID, and that you would receive an email tomorrow outlining steps to sign up. ”
so, that email that was hacked, we’re sending all the protection info to it tomorrow…
“No, it’s cool, we’re pretty sure the email system hasn’t been hacked this week.”