Expect phishers and other password thieves to up their game in 2016: Both Google and Yahoo! are taking steps to kill off the password as we know it.
 New authentication methods now offered by Yahoo! and to a beta group of Google users let customers log in just by supplying their email address, and then responding to a notification sent to their mobile device.
New authentication methods now offered by Yahoo! and to a beta group of Google users let customers log in just by supplying their email address, and then responding to a notification sent to their mobile device.
According to TechCrunch, Google is giving select Gmail users a password-free means of signing in. It uses a “push” notification sent to your phone that then opens an app where you approve the log-in.
The article says the service Google is experimenting with will let users sign in without entering a password, but that people can continue to use their typed password if they choose. It also says Google may still ask for your password as an additional security measure if it notices anything unusual about a login attempt.
The new authentication feature being tested by some Gmail users comes on the heels of a similar service Yahoo! debuted in October 2015. That offering, called “on-demand passwords,” will text users a random four-character code (the ones I saw were all uppercase letters) that needs to be entered into a browser or mobile device.
This is not Yahoo!’s first stab at two-factor authentication. Another security feature it has offered for years — called “two-step verification” — sends a security code to your phone when you log in from new devices, but only after you supply your password. Yahoo! users who wish to take advantage of the passwords-free, on-demand password feature will need to disable two-step verification for on-demand passwords to work.
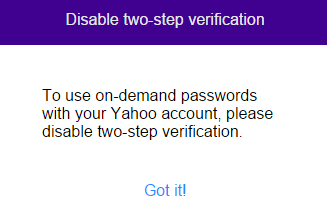
Yahoo! also warns that some non-Yahoo apps like Apple mail and Outlook won’t work. For those programs to access your Yahoo! mail with on-demand passwords enabled, you’ll need to set up app-specific passwords. Yahoo! provides instructions on how to do that here.
The system that Google is reportedly beta testing sounds easier to use, and more like true two-factor authentication. It doesn’t require the user to enter any code, and he just has to click a button on an app that tells the login to proceed.
All of this had me wondering: Should we expect Microsoft to roll out a similar password-free login process for Hotmail or Outlook users? It doesn’t seem likely: A spokesperson for the company referred me to Microsoft’s Passport system, which also uses a password-free authentication system. However, Passport’s key two-factor features are only available to Windows 10 users.
To come full circle on the lead of this story, I think it’s likely we’ll see an increase in more targeted, personalized phishing attacks if Google and Yahoo!’s two-factor solutions gain wide adoption. Perhaps Google anticipated this in April 2015, when it starting offering its Password Alert feature — a Google Chrome browser add-on that will display a warning if you type your Google password into a site that isn’t a Google sign-in page. Google says this protects users from phishing attacks and also encourages people to use different passwords for different sites, a security best practice.
Plenty of other online services now offer two-step authentication. Twofactorauth.org has a fairly comprehensive breakdown of those that do and don’t. Consider dropping by there to see if you’re taking full advantage of all of the security offered for your various online accounts.




Could 2FA (two factor authentication) be compromised by rogue mobile apps (read: apps impersonating 2FA apps?)
Yes Adam, 2FA can be compromised by phone malware. There have actually been a few major attacks in Russia and Europe that leveraged phone malware to intercept bank credentials and then re-direct the SMS (txt message) code to the hackers system so he could authenticate when logging into the victim’s bank accounts.
It’s worth noting that Google’s system of “enter email, acknowledge on phone” is NOT 2-factor. It’s 1-factor — the single factor being that you have the phone.
It’s a much stronger factor than passwords, as phones are rather harder to copy than passwords are 🙂 .. assuming that the technical implementation of the system is secure against redirection.
For less-important things (which a Google identity is not – if you use Gmail, so many other things can be taken over if the bad guys get your Google identity, so this can’t be left to lower security methods) it could be okay to use this (new, different, stronger) 1-factor authentication instead of passwords.
But for important things (like Google identities/ Gmail accounts, any common identity which would grant access to your email), real 2-factor — your password or some other classic factor, plus the physical possession of your mobile device (whether by code generator, push message, or SMS) is still most appropriate.
THIS!!
What Google and Yahoo are really offering are 2 step verification, and a weak form of it to boot. As other posters have mentioned, 2SV with simple yes/no dialogs just promote a ‘swipe yes’ reaction to everything. Imagine if EVERY service did this, you would be inundated with yes/no login notifications on your phone ALL DAY, you are going to muscle memory YES to most things. With the traditional SMS code 2SV, you were still forced to think about the login process by entering the code. This new form of yes/no 2SV gets rid of this.
This type of 2SV is all about frictionless login, and tilts the balance strongly towards usability at the expense of security.
What is beyond ridiculous to me is that Google has a proper 2FA (codes generated out of band w/o connectivity) app already (Google Authenticator – https://support.google.com/accounts/answer/1066447?hl=en) and instead in this case they are promoting something weaker. Granted this 2SV is a trial, but really they should be spending more time coming up with innovative ways to easily enter the Google Authenticator App generated codes for verification.
And lets not all forget, YOU CAN STILL CHOOSE to login with your password/security question at any time. If you need any sign that this is about usability and not security, this is it. Presumably this is only going to protect your password from keyloggers, shoulder surfing, and in transit copying because you no longer need to enter it. But if your password is compromised at rest, or guessed, this will do nothing.
I wrote a little guide on this here: http://www.lessismoreorless.com/2015/12/02/lets-get-2nd-level/
I agree that some people will just click yes, which you could prove by going to a large apartment building and pushing random buzzers until someone buzzes you in the building.
There is, however, another side of this you are ignoring. One of the biggest obstacles in cyber security is getting people to adopt new, more secure, authentication methods. I will personally be sticking with 2FA, rather than this new method as I like the extra piece of mind. However, I applaud Google and Yahoo for trying to make doing the right thing easier. Password re-use, weak passwords, and as an extension, human memory, is likely a much bigger problem than a reflexive yes swipe is likely to be.
I would say that if a person swipes yes to a dialogue asking if you are really trying to log into your account when they are not, then the problem is them, not the system. I also don’t think this will be as common as you have suggested. I know that if I am trying to log into one of my 2FA accounts, then I am on my computer logging into my account, and then I go to my phone to finish the login. I don’t see how not having to enter the code from my phone would become a swipe yes reflex, as I would still be on 2 different devices. Now if a person is logging into a secure site from their phone’s browser and then they only have to approve it from their phone that they are already on, that could be a little different.
Personally, I do not trust the security of a smart phone or app store. I do not think this new method of authentication is the best solution, but I like that it is easy and progress towards eliminating passwords.
“Password re-use, weak passwords, and as an extension, human memory, is likely a much bigger problem than a reflexive yes swipe is likely to be.”
I don’t see how this weak form of 2SV has any correlation to fixing password re-use, weak passwords, or human memory unless Google is doing some sort of education training relating to text passwords with this trial. I’d imagine most users that had weak, re-used passwords before Google’s new 2SV process, will still have them even with the 2SV. Is Google creating new password requirements for these trial users? And this doesn’t help memorability at all – presumably you will only have to use your text password on any new browser/device or when Google is not sure of your current security posture. This could mean weeks to months between using their text password, which would be very hard to remember.
With that said I’m not against 2SV/2FA; I’m actually a fan of it, but only if the user has set up a strong password and security question answer to go with it. If Google paired this with a password manager service that enforced strong passwords that would be one thing, but I’m doubting that.
I do agree that maybe perhaps I was too quick on the analysis of muscle memory responses to 2SV prompts on the phone – perhaps its not as bleak as I suggested.
Re-reading your post one more time, I guess what you are getting at is this is an interesting step in removing the password altogether (thereby eliminating password re-use, weak passwords, memorability issues). I suppose I see your point, but again it needs context.
If google only allowed this feature if your phone was locked down with a 6+ segment pattern password or biometric that would be great, but not sure if I’ve seen the details on that yet. And the reality is that there will likely always need to be some sort of fallback token that only the USER knows and can prove. Right now, it still falls back to text passwords. Maybe in the future we can fall back on some sort of advanced builtin biometric (https://www.nymi.com/), but again any biometric that is observable over time is copyable. The one benefit of the text password is if you set it up right, its known only to you, its not inherently observable outside of the duration of the login session, and if it is observed, you can revoke it and create a new one (unlike biometrics).
I do think we will eliminate the text password eventually, but its going to be replaced with a whole range of frictionless biometrics and perhaps even more advanced biometrics not seen yet.
Surely this isn’t 2FA? There is only one factor (something you ‘have’ i.e. your phone)?
Does this not just make phones even more valuable targets for thieves?
Why does an attacker even need your phone with this?
Just put a massive amount of random gmail addresses in on your own computer. Guaranteed you’ll get at least a 10% rate of people just hitting “accept login” when it pops up on their phone.
We’ve fostered a “just click yes to everything” culture of security warnings, nothing here is gonna change that.
Exactly! All this does is reinforce the Pavlov effect. After a couple weeks of using Email with this “feature” enabled, the users will happily tap “YES OF COURSE IT’S ME” whenever the pop-up appears on the phone.
Maybe the pop-up should ask “Are you a child molester, or are you currently trying to log into your email?” to increase the chance that users actually THINK for half a second before clicking :).
Not all the attackers can get to you and steal your phone.
There should be a lot of insights into this. What if your phone is dead? Probably using a second email account or memorizing one more password!
It’d be def a better solution than pass only.
It is something you have and something you know. your phone and your username.
Clef is another interesting take on using a mobile device for authentication (https://getclef.com/).
All of this presupposes that users have a mobile phone capable of receiving text messages. I guess companies assume that if you do not have such a phone, you do not have money to buy the products being advertised on their sites.
They obviously do not care about people who use different means to access different sites depending on where they and have access to. I for one do not carry my smartphone 24 hours a day and do not intend to.
Google and Yahoo is making cracking the password is difficult. It would be interesting to see how phishers give fight to them.
2step authentication seems to be difficult to be cracked that easily.
So, with mandated backdoors into personal devices/encryption, every 10th app being malware, powning a phone has never been easier for crooks (civilian and government).
Yeah, lol, using a phone for double authentication is as safe as, pulling out.
And how do you propose breaking into my phone? Do you have my fingerprint handy? Or are you going to try to crack a six-digit number?
If an attacker gets a malware on you phone, he does not need to open you pin code or biometric. he can tap into these app and remotely operate them, get their content or even modify thier behaviour.
So if you have malware on your phone, it can be used to sign on to your websites and other nefarious activities. Got it.
I’ll just have to keep that pesky malware off my phone, then.
Not only can malware take over your phone, but even fingerprint scanners are not impossible to defeat. A determined thief will cut off your hand, or if he/she is nice, maybe just the 1 finger/thumb. There is, however, a way that a person can use your fingerprint off of another object (or possibly from your phone itself) to unlock your phone with your hand still attached to your arm.
http://www.theregister.co.uk/2002/05/16/gummi_bears_defeat_fingerprint_sensors/
I’ll stick with my very long and complex password combined with Google authenticator. Thank you.
Is there two factor authentication without a mobile device? In a world of mobile devices, what if you don’t want to give up your phone number? What other method is available?
+1
I’m not really interested in having my cell# disseminated to a billion telemarketers.
In the AppleVerse, my text messages appear on my iPhone, my Watch, and several iCloud-integrated Macs and MacBooks. This would seem to diminish the security of any “phone-based” token, since my attack surface is as wide as my connected devices.
Hoping that eventually the web will adopt Steve Gibson’s SQRL no password needed login system
Gibson is the master of vaporware. Half of what he proposes writing never comes to be and the stuff he actually does start working on takes decades to finish? How long has he been talking about SQRL? Two years? Three? About a year ago, he claimed it was finished. So where is it? We can probably expect Quantum computing to be the norm long before Gibson actually releases this SQRL!
Steve posted Jan. 4th that the Secure Quick Reliable Login (grc.com/SQRL) spec is finished meaning that the client development can be completed now along with documentation.
I have monitored his newsgroup discussions during development of the specification and software testing. It represents an open, dedicated effort to formulate an approach to online identity that is maintainable and secure for the client.
The development world has a history dealing with people wanting things done quickly. Unfortunately some of them have been in control and we are still paying the price for their mistakes when it comes to identity theft.
Steve’s effort represents a solid shot at easily maintaining secure identities online.
What is different about that compared to what LINE messenger does for their computer based login? You have to make the account on a mobile device and the only way to activate LINE messenger on a desktop is to scan a QR code. A few other Japanese applications do this too. There was even a H-Game which did this for DRM purposes.
With all the 2FA, etc., What about those of us who still use a landline but would like security as good as those who do? I assume I’m not the only one.
Regards,
I believe one service understands that you have a landline and an automated voice reads the letters and digits to you. We computer folks can provide solutions to all problems!
I use Gmail 2FA and have alerts and codes going to our land line and to my wife’s iPhone. It may have been back when their 2FA was first announced it did not support (or advertise) that a land line could be specified.
Also, I took Brian’s advice and established a second, recovery Gmail account linked to the main account that also has 2FA. While doing this I had my 2FA verifying phone alert call go to my old Motorola flip phone and it worked by sending a code via a message, not a voice call.
Thinking back, it was Paychex that used a verbal method of getting you the authentication code. Since they deal with businesses, and most business phones can’t accept text messages, I expect that they just use the verbal method by default.
While not accepted on gmail, Duo security has the option, in addition to SMS and apps, to call you on authentication attempts. It uses credits you have to replenish, but its the only service I know that offers Two-Factor with this option.
https://www.duosecurity.com/
Me too, only carry a trac- fone for emergency use, do not want my pc in my pocket with all attendant problems. My land line is easy to manage with caller id & pro call blocker. 2FA won’t work, no text only voice. I’m satisfied not to conform with social expectations like facebook et al. Much safer I think.
So what about the elephant in the room?
What do we do when some malicious outfit is constantly putting our email addresses into yahoo/google trying to log in to them?
This also opens up an interesting MITM attack where someone watching you log in can simply attempt a login with your email address simultaneously, tricking the user into accepting the attackers login request instead of their own. Odds are when they get a second request a few seconds later they’re just gonna shrug it off as a bug.
Can’t wait for my phone to be buzzing asking me to authorize bogus logins 24/7.
This is a good point, though I would imagine that any of these services use 2SV as ‘device recognizer’. In other words, 1st time login from any new device/browser requires the full password. So presumably if any attacker was timing attacks, they’d still have to login with your password the first time from their device.
I’m waiting for hopefully wide adoption of Steve Gibson’s SQRL.
https://www.grc.com/sqrl/sqrl.htm
All this means nothing ! Pointless who want to make money will makit world is dominated by powerful people not single moves are not allowed if this powerful people don’t allow they control Google banks and etc. there why we don’t look as example countries like Finland Estonia Sweden there is no fraud at all basecly !! How come that security is so vurneble in countries like Australia Canada USA UK ? Why they don’t do basecly anything about hacking fraud and etc ? Is it true that only thing that they do is microchipped people then it’s only way to make sure no fraud ? Now Google wallet let you transfer money allmost instantly from debit credit card without really difficult verification so the system himself is so vurneble that offcourse it’s been used so who we blame??
huh, what on earth are you saying?
Brian, you might want to consider doing a story on Venmo if you don’t already have one in the works: https://www.reddit.com/r/personalfinance/comments/3xyvyk/3000_stolen_from_my_checking_account_from/
I thought it was just yahoos way of getting my phone number. No way.
So I will do without a yahoo email, it was just a way to get google play id, never actually read any of the mail. I recently wiped my tablet and wanted to reget some google play apps so I thought I might need the yahoo email to work. Turns out I didn’t.
It’s about getting your phone number. These companies could careless what happens with your free account.
LoginTC were the first do push based authentication and looks like the have an appliance for protecting VPN access:
https://www.logintc.com/
well the thing is with yahoo even if they do change there outlook on the login process, things like there hidden api logins and 3rd party mail “SISTER SERVERS” will still be hosting this type of login. theres loopholes all over yahoo and they are coming out more and more everyday.
You really make it appear really easy together with your presentation but I to find this topic to be actually something which I feel I would by no means
understand. It sort of feels too complex and very extensive for
me. I’m looking ahead on your subsequent publish, I will attempt
to get the cling of it!