Microsoft Corp. today warned that it is seeing a huge uptick in attacks against security holes in Java, a software package that is installed on the majority of the world’s desktop computers.
In a posting to the Microsoft Malware Protection Center blog, senior program manager Holly Stewart warned of an “unprecedented wave of Java exploitation,” and confirmed findings that KrebsOnSecurity.com published one week ago: Java exploits have usurped Adobe-related exploits as attackers’ preferred method for breaking into Windows PCs.
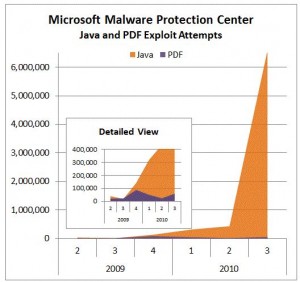
Stewart said the spike in the third quarter of 2010 is primarily driven by attacks on three Java vulnerabilities that have already been patched for some time now. Even so, attacks against these flaws have “gone from hundreds of thousands per quarter to millions,” she added. Indeed, according to Microsoft’s one-year anniversary post for its Security Essentials anti-malware tool, exploits for a Java vulnerability pushed the Renos Trojan to the top of the list for all malware families (malware and exploits) detected in the United States.
My research shows the reason for the spike, and it precedes the 3rd quarter of 2010: Java exploits have been folded into a number of the top “exploit packs,” commercial crimeware kits sold in the hacker underground that make it simple to seed hacked or malicious sites with code that exploits a variety of browser flaws in a bid to install malware.
Stewart asks, “Why has no one been talking about Java-based exploits?” Then she answers her own question:
Looking back at the chart above, you can see that this exploitation has been happening for some time. So, why has no one been talking about Java-based exploits? (Well, almost no one. Brian Krebs broke the ice this week).
I have a theory about why almost no one has noticed. IDS/IPS vendors, who are typically the folks that speak out first about new types of exploitation, have challenges with parsing Java code. Documents, multimedia, JavaScript – getting protection for these issues is challenging to get right. Now, think about incorporating a Java interpreter into an IPS engine? The performance impact on a network IPS could be crippling. So, the people that we expect to notice increases in exploitation might have a hard time seeing this particular spectrum of light. Call it Java-blindness.
So, if the antimalware people can see it, why aren’t *they* talking about it? Because, looking at the numbers, Java exploits (and most exploits for that matter) are very low-volume in comparison to the volume of common malware families like Zbot (a family for which we added detection in MSRT just this week). What we have to remember is that, with exploits, it’s not about volume – they happen in a flash and you have to catch them in the act (with a real-time protection product such as Microsoft Security Essentials) before they open the door to lots of malware. So, even small numbers, especially when they’re against unpatched vulnerabilities, matter a lot.
If you haven’t done so lately, take a moment to see if you have this program installed, and if you do, please make sure it is up to date. Just last week, Oracle issued another update — Java 6 Update 22 — that fixes at least 29 security flaws in the program.
KrebsonSecurity.com will continue to post the newest security updates, when they become available. But, your computer installation of Java also includes a built-in updater that you should configure to check for updates as frequently as possible.
Allow me to reiterate my urgent advice from last week:
Java ships with a built-in updater that by default checks for updates on the 14th day of every month. However, this may not be frequent enough to keep users caught up with the latest version. The program can also be set to check for updates every day or every week, although I have found Java’s updater often fails to detect when a new version is available. Alternatively, programs like FileHippo’s Update Checker and Secunia’s Personal Software Inspector can help users stay up to date on the latest security patches.




Brian, the “t” at the end of “one-year anniversary post” isn’t linked 🙁
fixed. thanks
Hi great article thanks for sharing. Will microsoft security esentials stop Java from working as I need to be able to download information from a?
I don’t understand why something that is supposed to be a sandbox environment is so ill-secured itself. Security companies shouldn’t have to be analysing Java code for exploits, they should be checking the JVM for security-impacting bugs.
Bob — It’s worth noting that the exploitation has been against Java flaws that were already patched. The trouble is that Java has a huge install base — something like 85 percent + of the PCs out there — but very few users probably even know they have this software, or are aware of how important it is to keep it updated.
It’s rumored there’s some 31337 trix played with packet radio, java, and modern cpus:
https://tagmeme.com/subhack/
did you know your soundcard and cables make great packet radio sources and amplifiers?
One of the issues with updating Java in a corporate environment is the lack of support from Oracle for centralized deployment and management of Java.
To my knowledge, Oracle doesn’t have a utility that can be distributed by a system administrator to remove all previous versions of Java. Instead previous versions must be uninstalled silently one command line at a time. However, there is a third-party utility that does this.
There’s also no centralized mechanism from Oracle to enforce that the update feature is enabled and configured.
Until Oracle offers these centralized management tools keeping Java updated in the corporate environment will always be a matter of playing catch-up.
Most of what you are saying is true, but for two years now Java has uninstalled older iterations of itself.
“Update 10 now claims to include “patch in place” capability, meaning future updates will remove older versions upon install. ” (Krebs, Oct. 2008)
http://voices.washingtonpost.com/securityfix/2008/10/java_update_promises_to_remove.html
I will agree this is not a corporate management system, but it does facilitate the removal of old, exploitable versions.
Probably a greater threat would be the required use of old Java versions, because of deprecated objects, and software that has not been updated.
I believe in a corporate windows environment there are other methods to update Java, using MSI, and Group Policy.
The (not so) funny thing is that one major product that seems to rely on ancient versions of Java is ORACLE. If your company hasn’t moved to Oracle 12, you’ll probably require some odd version of Jinitiator and an old JRE on your system. Dependencies are such fun…
Yes, in theory nobody should be installing these old Java versions that aren’t removed automatically. However, it seems that there is still lots of software that will automatically install an outdated Java version on your system – including versions that cannot be removed.
What frustrates our organization so thoroughly isn’t necessarily the new Java versions themselves (though I agree with RJ), but the lack of support from Java developers for these newer JREs.
We have to use older versions of Java to simply keep things working. I don’t think Java developers are under enough pressure to quickly get their apps working with a newer JRE. Like everything else, I’m sure a large amount of exploits may change that fact (as resulting policies tighten Java security, resulting with applied pressure to the developer).
I set my “Java Control Panel” to check daily. Before, it said it was checking on the 25th of each month at 10:00 a.m. Maybe the update day depends on when it is installed.
Does it have to be regurgitated for every wave of JavaScript exploit?
Use Firefox, with “NoScript”, and disable all Microsoft hacks (Silverlight, NET framework, Windows Presentation Foundation, Shockwave, JavaScript, or other active scripting rubbish).
Prevention, not removal.
The best thing for consumers to do (Windows OS) is to uninstall the thing from the Add/Remove programs, reboot, run a program like CCleaner to look for and remove any detritus, then reboot and return to the Sun/Oracle webpage to get the most current version.
Assuming they really want it. I removed it and occasionally get web pages that honk a warning, but with most web pages running JavaScript, it seems Java is going to eventually fade into obscurity in the consumer space.
I’d agree with Tony that Java as a browser plug-in technology will fade. Java in other spaces is a different matter.
It will continue to have a presence in the mobile market for some time, and it is needed for consumer applications like OpenOffice. In that area, it is similar to a framework like .Net.
I don’t want Java in my browser, but I do need it on my PC for other applications.
Unfortunately, every Java install will automatically register all the web hooks as well. This was a strategical decision from Sun, it was their way of pushing Java applets and Java web start. Given that Java is becoming meaningless on the web anyway I would really like to see Oracle reconsider and have JRE install a runtime only – with browser plugin and web start as *optional* components. Which would certainly help consumers but is most likely contrary to Oracle’s business interests 🙁
On a typical Windows XP laptop, what depends on Java? I’m thinking of removing Java from my gf’s laptop but don’t want to break anything.
Her usage: email, simple web browsing, some HTML writing, MS Office, and that’s it.
Then your gf does NOT need Java. It’s easy enough to reinstall if you decide you need it after all.
‘Simple web browsing’ probably includes java enabled pages. I bet she will notice it when it is gone.
I’d still do it though.
Really? I cant remember the last time I encountered a java applet outside of the enterprise space.
For online banking, my bank uses a Virtual Keyboard Java applet to enter account passwords.
Yes because Microsoft does not have any other motive for issuing security warnings on a competitors technology.
How is that win2k3.sys 0 day anyway?
This story would have more teeth if it had multiple sources
From what I have read Sun (and I can only assume now Oracle) pledged to keep JRE 100% backward compatible. Most of the issues have seen with JRE are related to install location specific calls rather than using system variables etc. Certainly a contributing factor to the cause of that is the ability to run multiple versions of JRE, which from the Windows side can cause path nightmares. To make this worse, it seems for a while the default install was to leave previous versions of Java. With the 1.6.x release of Java you have the option of installing “static” or “patch-in-place”, per Sun/Oracle the patch in place method leaves you with one version of JRE per Java “family” (assuming you have multiple families installed).
I think the big challenge is transitioning from the static install to the patch-in-place install. It seems that once patch-in-lace is the standard for corporate environment patching becomes less of a hassle.
Patch-in-place vs. static information found here:
http://lamp.epfl.ch/java/jdk1.6/docs/technotes/guides/jweb/otherFeatures/jre_install.html
The free utility “JavaRa” removes old versions, browser plugins and registry entries. http://raproducts.org
It’s quite an eye-opener to see how much cruft is left behind by the older supposedly stackable updates!
Nick Braak got it right, this app is great. Been recommending it for years.
i removed java more than a year ago on the advice of brian’s column, and have had no need for it. i very much appreciate brian’s columns and the comments.
The Java Updater is a real piece of work.
When you install a JRE, the JU picks a random day of the month ( sorry Brian, not just the 14th ) for the update. I found one of my machines was set to update on the ‘zeroth’ day of the month. I’m not sure what day that is.
If you do show a bit of initiative and set it to daily, if it automatically updates again it will change your settings back to monthly. So you have to constantly watch that setting. Sigh.
If you’re running Vista or 7, you need to track down the control panel applet and ‘run as administrator’ to get the new schedule change to be accepted.
I really wish the boys and girls at Oracle would make the updater a bit more respectable.
It should be noted that changing the update settings for Java in 64 bit versions of Vista and Win 7 is a bit complicated. While Java is listed in Control Panel > Programs, running the Java applet from there opens the Java Control Panel utility without the Update tab visible.
To change the update settings for Java in 64 bit Vista and Win 7, it is necessary to right click and select ‘Run as administrator’. In the command prompt window, type in the following line after the C:\Windows\system32> prompt (including quote marks):
“c:\Program Files (x86)\Java\jre6\bin\javacpl.exe”
Hit Enter and the Java Control Panel applet will open with the Update tab accessible.
Select the Update tab, tick the checkbox to “Check for Updates Automatically”, then click the Advanced button. In the Automatic Update Advanced Settings dialog box, you can select a frequency of Daily, Weekly, or Monthly as well as time of day, day of week, or day of month. You can also run the update manually using the Update Now button.
For 32 bit versions of Win 7 or Vista, refer to:
http://java.com/en/download/help/javacpl.xml
For some reason part of my previous post is missing.
To change the update settings for Java in 64 bit Vista and Win 7, it is necessary to right click Command Prompt and select ‘Run as administrator’. In the command prompt window, type in the following line after the C:\Windows\system32> prompt (including quote marks):
“c:\Program Files (x86)\Java\jre6\bin\javacpl.exe”
Where do I look to see if I have Java on my WinXP PC? Is it a plugin or a program? Thanks.
From the “START” button, choose “Run” and enter ‘cmd.exe’ to get a command line. (There’s a button to click, but I don’t remember if it say ‘Run’ or something else.)
enter ‘java -version’ and hit return.
If java is installed and on the path, you’ll get a version number. If not, you’ll get some sort of command not recognized error message.
Java is a program with a plugin component for some browsers.
The java-version command may not work for newer versions of Java because I always have the latest and greatest and don’t have it. A better more sure-fire way to find if Java is installed on your system is to do a Start, then Control Panel and then double click on the Add / Remove Programs. If it is installed all of the installed versions of Java will show up there. If it isn’t installed you probably don’t need it. Be careful here in a corporate environment. Frequently you are stuck with an older version of Java for soemthing they have internally.
You can also check to see if files are in the %ProgramFiles% folder by starting Windows Explorer or if you can type in file system entries in My Computer there as well. Type in %ProgramFiles%. If you have a Java folder in Windows Explorer but nothing shows up in the Add / Remove Programs I would delete the folder. If you really need Java in a home environment it is probably best to just uninstall all of versions with Add / Remove Programs, delete the folder and start over with the newest version. For the newest versions of Java it no longer leaves older minor versions hanging around but deletes them when you do a minor version update now. Java didn’t use to do that.
I have been stuck at jre6 when Java got installed with OpenOffice which uses Java. It has always uninstalled the previous minor version when it does the update for me and I have it set to check every day and inform me but not to automatically do the install. I am not in Windows all that often and can end up with it attempting to do the monthly Microsoft security updates, the Java updates, one or more browser updates and the AV program updates all at the same time. One at a time please! I never depend on the AV program to do any of it automatically. I force it to update because I am ALWAYS using the AV to test the malware I have identified. My avocation is to do that as part of my effort to provide filters people can use as an extra edge against the threats of the Internet. Currently for me jre6 is plugged into Firefox, Opera, and Safari, but not into Chrome or Internet Explorer. It doesn’t make any sense being put into Internet Explorer since you will use Active-X instead.
I strongly urge you to disable Java in all browsers until you need it. Do NOT uninstall Java if you use OpenOffice since it needs it. Other than that Java is so unused on the Internet that I would worry more about abuse than somebody actually using it for something legititmate. The same does not hold true for Intranets / Corporations. Many corporate environments use Java and usually stick you to using some old outdated crusty, rusty version of it. I suspect that the hackers are targeting the corporate environment in which case the corporations need to put signficantly more effort into keeping their apps up to date and always using the latest version of Java to prevent problems.
I hope the fire hose didn’t kill you.
To address the rise of Sun Java exploits mentioned in this report, if for some reason you cannot simply patch Sun Java runtimes to the latest level, a list of all commonly exploited Sun Java runtime vulns with CVE numbers is at http://sharpesecurity.com/blog/2010/10/25/list-of-currently-exploited-sun-java-vulnerabilities/. This list can be used to ensure your IPSes have all required blocks in place.
Hello? Update. Please?
– http://www.zdnet.co.uk/blogs/walsingham-10020628/guess-who-hasnt-patched-the-java-security-hole-10020866/
25 October, 2010 – “… Only 7% have applied the critical patch. According to Trusteer*, 68% of Internet users are still at risk from the attacks that these Java vulnerabilities expose and goes as far as to claim that it has become the single most exploitable vulnerability on the web today… these things are not called ‘critical’ for the heck of it. ”
* http://www.trusteer.com/company/press/trusteer-finds-massive-internet-security-hole-remains-unpatched-users
Oct. 25, 2010 – “… over a week after Oracle released a critical patch for Java, more than 68 percent of Internet users are still at risk from attacks that exploit these vulnerabilities. This may be the biggest security hole on the Internet today, since 73 percent of Internet computers are using Java…”
___