If your Windows PC has been hijacked by fake anti-virus software or “scareware” anytime in the past few years, chances are good that the attack was made possible by ChronoPay, Russia’s largest processor of online payments.
Tens of thousands of documents stolen and leaked last year from ChronoPay offer a fascinating look into a company that has artfully cultivated and handsomely profited from the market for scareware, programs that infiltrate victim PCs to display fake security alerts in a bid to frighten users into paying for worthless security software.
ChronoPay handles Internet bill payments for a variety of major Russian companies, including domestic airlines and utilities. But ChronoPay also specializes in processing the transactions of so-called “high-risk” industries, including online pharmacies, tobacco sales, porn and software sales. A business is generally classified as high-risk when there is a great potential for credit card chargebacks and a fair chance that it will shut down or vanish without warning.
In June 2009, The Washington Post published the results of a six-month investigation into ChronoPay’s high-risk business. At the time, ChronoPay was one of a handful of processors for Pandora Software, the most prevalent brand of rogue software that was besieging consumers at the time. That story drew links between ChronoPay and an entity called Innovagest2000, which was listed as the technical support contact in the end-user license agreements that shipped with nearly all Pandora rogue anti-virus products.
When I confronted ChronoPay’s CEO Pavel Vrublevsky in 2009 about the apparent ties between Innovagest and his company, he insisted that there was no connection, and that his company’s processing services were merely being abused by scammers. But the recently leaked ChronoPay documents paint a very different picture, showing that Innovagest2000 was but one example of a cookie-cutter operation that ChronoPay has refined and repeated over the last 24 months.
The documents show that Innovagest was a company founded by ChronoPay’s Spanish division, and that ChronoPay paid for everything, from the cost of Innovagest’s incorporation documents to the domain registration, virtual hosting and 1-800 technical and customer support lines for the company.
The same dynamic would play out with other ChronoPay “customers” that specialized in selling rogue anti-virus software. For example, leaked internal documents indicate that ChronoPay employees created two companies in Cyprus that would later be used in processing rogue anti-virus payments: Yioliant Holdings; and the strangely named Flytech Classic Distribution Ltd. ChronoPay emails show that employees also paid for domains software-retail.com and creativity-soft.com, rogue anti-virus peddling domains that were registered in the names and addresses of Yioliant Holdings and Flytech, respectively. Finally, emails also show that ChronoPay paid for the virtual hosting and telephone support for these operations. This accounting document, taken from one of the documents apparently stolen from ChronoPay, lists more than 75 pages of credit card transactions that the company processed from Americans who paid anywhere from $50 to $150 to rid their computers of imaginary threats found by scareware from creativity-soft.com (the amounts in the document are in Russian Rubles, not dollars, and the document has been edited to remove full credit card numbers and victim names).
Further, the purloined documents show these domains were aggressively promoted by external rogue anti-virus affiliate programs, such as Gelezyaka.biz, as well as a rogue anti-virus affiliate program apparently managed in-house by ChronoPay, called “Crusader.”
MEETING IN MOSCOW
Last month, I traveled to Moscow and had a chance to sit down with Vrublevsky at his offices. When I asked him about Innovagest, his tone was much different from the last time we discussed the subject in 2009. This may have had something to do with my already having told him that someone had leaked me his company’s internal documents and emails, which showed how integral ChronoPay was to the rogue anti-virus industry.
“By the time which correlates with your story, we didn’t know too much about spyware, and that Innovagest company that you tracked wasn’t used just for spyware only,” Vrublevsky said. “It was used for a bunch of shit.”
Vrublevsky further said that some of ChronoPay’s customers have in the past secretly sub-let the company’s processing services to other entities, who in turn used it to push through their own shady transactions. He offered, as an example, an entity that I wasn’t previously aware had been a customer of ChronoPay’s: A rogue anti-virus promotion program called TrafficConverter.biz.
As I documented in a March. 2009 story for The Washington Post, Trafficconverter.biz paid its promoters or “affiliates” hundreds of thousands of dollars a month to pimp rogue anti-virus software. The domain Trafficconverter.biz was shut down briefly at the end of November when it was discovered that it was being sought out by millions of Microsoft Windows systems infected with the first variant of the Conficker worm, which instructed infected systems to visit that domain and download a specific file that suggested it would attempt to install rogue anti-virus software.
“That was a case where ChronoPay had a merchant account registered as an Internet payment service provider with Visa Iceland, where the same merchant account was being used by hundreds of small merchants, and one of them turned out to be the infamous TrafficConverter,” Vrublevsky explained.
But what of the leaked documents that show what appear to be ChronoPay employees setting up entire businesses that would later sell rogue anti-virus — including incorporation records, associated bank accounts, Web hosting, domain registration, telephone support and merchant accounts tied to these entities? Wasn’t ChronoPay concerned that this activity could make it appear that the company was simply building rogue anti-virus merchants from the ground up?
No, this is what high-risk payment service providers do, Vrublevsky explained.
“This is part of the service you provide,” he said. “Basically you own the companies that have those merchant IDs, plus you do customer support and everything which is related to that. And that’s how any other payment service provider does it, and you can find the same thing if you dig into companies like Wirecard, and Visa Iceland. So most payment service providers basically register the companies themselves and monitor the whole [operation] from the inside.”
SCAREWARE RESEARCH & DEVELOPMENT
The leaked records also show ChronoPay’s high-risk division worked diligently to stay on the cutting edge of the scareware industry. In March 2010, the company began processing payments for icpp-online.com, a scam site that stole victims’ money by bullying them into paying a “pre-trial settlement” to cover a “Copyright holder fine.” As security firm F-Secure noted at the time, victims of this scam were informed that an “antipiracy foundation scanner” had found illegal torrents from the victim’s system, and those who refused to pay $400 via a credit card transaction could face jail time and huge fines.
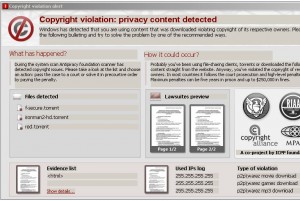 Internal ChronoPay documents show that hundreds of people fell for the scam, paying more than $400 each (the message at the top of the image indicates that the internal ChronoPay formula for counting the number of downloads and sales was generating errors, so take these numbers with a grain of salt).
Internal ChronoPay documents show that hundreds of people fell for the scam, paying more than $400 each (the message at the top of the image indicates that the internal ChronoPay formula for counting the number of downloads and sales was generating errors, so take these numbers with a grain of salt).
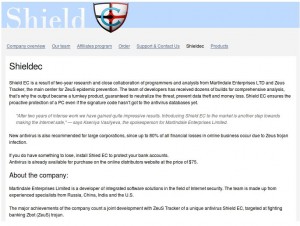
ChronoPay also was the processor for a fake anti-virus product known as Shield-EC, which was processed through a merchant account tied to a company called Martindale Enterprises Ltd. Again, internal documents show that ChronoPay not only created Martindale Enterprises Ltd., and attached bank accounts to the company, but that it also paid for the domain registration, hosting and telephone support lines for shield-ec.com.
The shield-ec scareware scam was unique because the purveyors pitched it as “the result of a two-year research collaboration of programmers and analysts from Martindale Enterprises and ZeusTracker, the main center for ZeuS epidemic prevention.”
ZeusTracker is a free service run by an established security researcher, Roman Hüssy, who monitors Web addresses that are known to be associated with the distribution and management of the infamous ZeuS trojan. As Hüssy noted in a blog post at the time, the Shield-EC scareware campaign came with an interesting twist: The Web site shieldec.com was in fact hosted on a fast-flux botnet that was also being used to host at least two different servers used to control large numbers of PCs infected with ZeuS.
 These days, Vrublevsky said, he’s hoping his company can have a go at the market for legitimate anti-virus products. When I met with him in Moscow, Vrublevsky told me about company plans to create and sell its own anti-virus product: ChronoPay Antivirus. At first I didn’t know whether to take him seriously. But then I found a document in the cache that confirmed that claim. A Russian-language document called ChronoPay AntiVirus Vision (PDF), dated June 15, 2010, details the company’s ambitions in this market.
These days, Vrublevsky said, he’s hoping his company can have a go at the market for legitimate anti-virus products. When I met with him in Moscow, Vrublevsky told me about company plans to create and sell its own anti-virus product: ChronoPay Antivirus. At first I didn’t know whether to take him seriously. But then I found a document in the cache that confirmed that claim. A Russian-language document called ChronoPay AntiVirus Vision (PDF), dated June 15, 2010, details the company’s ambitions in this market.
Curious about what other domains ChronoPay currently owns? Check out this list (PDF), taken from a recent internal email that leaked from the company.





Thanks for another great article Brian. When speaking with people who may not be proficient with computers a common question is why do these malware exist. I always point them at your articles so they can see how profitable these programs are. It is quite alarming to say the least.
Thanks again.
ha! that might make a great antivirus program – who better to make it than an insider… lol
really awesome set of articles Brian, look forward to more installments!
Hmmm, Chronopay AV… This is all good, but what does “Модуль выявления выгодоприобретателя” (“Module of beneficiary’s exposure”?) mean?
Hello! As a native Russian speaker, I’ve looked through this document. It is not a specification nor document- it is a bullshit!!! Common words and technical specification to create anti-vires that primary claim “it should have simple UI” and “it should find viruses” the rest is a crap! I would write better one in a half of hours. I do not have any knowledge about anti-viruses, and concerns too) I’m using linux 🙂
Funny story. So a friend of mine who’s helped with Russian translations in the past pinged me today because he was considering buying a translation product for his computer. He’s been wanting to buy a version of this product for the Mac, and the company that makes it — Softkey — finally produced a Mac version.
My friend paused when he went to buy it and got an SSL cert error on the site. He further paused when he saw that the transaction was being processed through Cyprus. Having read my stories on ChronoPay, he decided to ping me to ask whether I knew if ChronoPay was somehow involved in processing payments for Softkey.
I consulted the cache of documents that were leaked from ChronoPay last year, and learned that SoftKey is indeed a customer of ChronoPay; in fact, according to a ChronoPay employee, it is among the very few “white” or legitimate software projects ChronoPay is currently involved in.
Check this out:
From: Konstantin Abramov [mailto:k.abramov@chronopay.com]
Sent: ceturtdiena, 2010. gada 17. jūnijā 12:30
To: Martins Berkis-Bergs
Cc: Ian Zaryn
Subject: Re: Affiliates
Martins,
Therer’s edefinately some misunderstanding.
We have 1 totally “white soft” project, which is Softkey.net. Runs on Payvision.
We have the plan to have 2 “white soft” webshops as a cover for the real activities, these 2 sites are still in poduction. Ian has more info on this.
We have a dozen merchants selling black software – those sites and software they use to redistribute the product are virtualy unidentifiable.
So to sum it up, whatever neds to be shown, at the moment we have only 4 software URLs for the banks. You’ve seen it.
As for the pharmacies, here is the list of the white ones with no controlleds:
http://www.enhancexl.com/
http://www.xtendrx.com
http://www.securetabs.com
http://www.onlineapoteket.nu
http://www.trustedpharmacy.eu
2010/6/17 Martins Berkis-Bergs
Kostja,
I am talking about 3 cases – pharmacies, software ‘’black’’ and software ‘’white’’. That was business I spoke with bank. You told me that there are no problems to supply information about 1 and 3rd option.
Am I wrong and did not understand some thing? You stated quite clearly that there is no problem with that.
MArtins
From: Konstantin Abramov [mailto:k.abramov@chronopay.com]
Sent: trešdiena, 2010. gada 16. jūnijā 19:41
To: Martins Berkis-Bergs
Cc: Ian Zaryn; Ivanov Sergey
Subject: Re: Affiliates
Martins,
I told you several times, in person, over skype and by mail that it is absolutely impossible to get the affiliates list for the software merchants. We do not know exactly where they sell.
We were discussing the potential fake sites to apply to banks and wee do have 4 sites now, you have that list:
astralsoftware.com
webbrowsingsolutions.com
http://www.vorines.net
euro-softwares.com
as for the pharmacies, beside the URLs told, only Sergey can provide you with more.
2010/6/16 Martins Berkis-Bergs
Kostja,
Last time when I was in Moscow you told me that it is no problem of having list of affiliates selling pharmacies and ‘’white’’ soft. We had a talk together with Ian. Does something have been changed?
Martins
From: Konstantin Abramov [mailto:k.abramov@chronopay.com]
Sent: trešdiena, 2010. gada 16. jūnijā 11:05
To: Martins Berkis-Bergs
Cc: Ivanov Sergey; Ian Zaryn
Subject: Re: Affiliates
Thing is that I am not very busy, but I am sick and staying at home. Have you recieved my message yesterday?
I explained everithing concerning the affiliate saites, there are none for software ones. And noway I can make them up, maybe Ian can help. Below is the text i sent you yesterday.
Sergey,
Would you please give Martins the list of affiliate sites selling pharmacies?
Konstantin Abramov ?
кому: Ian, Martins
Показать подробные сведения
12:50 (23 ч. назад)
Martins,
Are you talking about software ones?
I told you they are unidentifiable. Those used live less then couple of weeks and we never know the URLs.
Whichever we accidentally used to come accross are certainly dead by now. Beside that, the majority of sales are done throught the software itself, not throught the website.
We might ba able to trick the bank with more fake ones but we need time to create those.
So I can only tell you the same ones:
astralsoftware.com
webbrowsingsolutions.com
http://www.vorines.net
euro-softwares.com/
2010/6/16 Martins Berkis-Bergs
Kostja,
Last time when I was in Moscow you told me that it is no problem of having list of affiliates selling pharmacies and ‘’white’’ soft. We had a talk together with Ian. Does something have been changed?
Martins
From: Konstantin Abramov [mailto:k.abramov@chronopay.com]
Sent: trešdiena, 2010. gada 16. jūnijā 11:05
To: Martins Berkis-Bergs
Cc: Ivanov Sergey; Ian Zaryn
Subject: Re: Affiliates
Thing is that I am not very busy, but I am sick and staying at home. Have you recieved my message yesterday?
I explained everithing concerning the affiliate saites, there are none for software ones. And noway I can make them up, maybe Ian can help. Below is the text i sent you yesterday.
Sergey,
Would you please give Martins the list of affiliate sites selling pharmacies?
Konstantin Abramov ?
кому: Ian, Martins
Показать подробные сведения
12:50 (23 ч. назад)
Martins,
Are you talking about software ones?
I told you they are unidentifiable. Those used live less then couple of weeks and we never know the URLs.
Whichever we accidentally used to come accross are certainly dead by now. Beside that, the majority of sales are done throught the software itself, not throught the website.
We might ba able to trick the bank with more fake ones but we need time to create those.
So I can only tell you the same ones:
astralsoftware.com
webbrowsingsolutions.com
http://www.vorines.net
euro-softwares.com/
2010/6/16 Martins Berkis-Bergs
Hi Kostja,
I really need list of our affiliates selling pharmacy and ‘’white’’ soft. The bank had contacted me already 2 times by asking that list. I know you are very busy. Maybe Ian could help? I promised to bank that I will have list in place today?
Regards
Martins
Martins Berkis-Bergs
Regional Manager
—
Sincerely yours,
Konstantin Abramov
Director of Service Development
B.Palashevskiy, 5/1
Moscow. Russia
Website: http://www.chronopay.com
________________________
Tel.: +7 (0)495 780 3060
Fax: +7 (0)495 780 3301
No virus found in this incoming message.
Checked by AVG – http://www.avg.com
Version: 9.0.829 / Virus Database: 271.1.1/2940 – Release Date: 06/15/10 21:35:00
—
Sincerely yours,
Konstantin Abramov
Director of Service Development
B.Palashevskiy, 5/1
Moscow. Russia
Website: http://www.chronopay.com
________________________
Tel.: +7 (0)495 780 3060
Fax: +7 (0)495 780 3301
—
Sincerely yours,
Konstantin Abramov
Director of Service Development
B.Palashevskiy, 5/1
Moscow. Russia
Website: http://www.chronopay.com
________________________
Tel.: +7 (0)495 780 3060
Fax: +7 (0)495 780 3301
No virus found in this incoming message.
Checked by AVG – http://www.avg.com
Version: 9.0.829 / Virus Database: 271.1.1/2941 – Release Date: 06/17/10 14:33:00
—
Sincerely yours,
Konstantin Abramov
Director of Service Development
B.Palashevskiy, 5/1
Moscow. Russia
Website: http://www.chronopay.com
________________________
Tel.: +7 (0)495 780 3060
Fax: +7 (0)495 780 3301
Now that’s what I call customer support, setting up website for your clients so when their bank tries to vet them foir verification they seem legit, looks like the Crimepays–er– Choropay guys seem to really go the extra mile! Fraudulent activities with these guys, no not at all. I have to say though I do feel for the few legitimate clients that use them not realizing the badness these guys are up to, mind you that may change after Brian’s article. BTW Brian Slashdot also picked up on this story of yours, your lil expose is starting to rattle the web… or the criminal undergorund..lol
Hello everybody!
I’m a 100% “white” chronopay customer (not a softkey though :). Yes, we do know all the rumors about Chronopay activities. No, we won’t switch to another payment processor because there aren’t any.
Western companies doesn’t work with merchants from Russia (e.g. PayPal). – They simply turn their backs on us. Local payment processors either doesn’t allow you to process plastic cards or have some funny restrictions (e.g. to open account in specific small bank across the country).
There is some movement in positive direction from “Yandex Money”. Probably we’ll see something interesting before IPO of Yandex. But for now there is no alternatives to Chronopay 🙁
In the meantime – everything Google has been, “updated,” in the last half day, and Secunia has been useless, or seems so, for three.
Come back to America.
Wait a minute. This means Russia’s largest payment processor is actually totally criminal and facilitating rogue antivirus and something with Koobface?
This should be front page news. How much money are these banksters pulling in? This is MAFIA! Maybe RBN?
Get the word out people, Russian bankers are stealing millions from everyone else using malware — it all makes sense now…
>> Russian bankers are stealing millions from everyone else using malware
US bankers are stealing trillions from everyone using law (and disdain for it) – where’s the buzz?
hey f00fighter – who did you think controlled all this? Even if me and you had the fake software and could install it on unwitting peoples pc’s then who would process the payments? I doubt if we called up chronopay they would allow it! Though maybe they would. Chronopay will go the same way as epassporte soon enough.
As much as these guys are trying to paint themselves as innocent payment processors, their Tenacle into many scareware products and the logistics behind them tell the real tale, they are using the scareware model to make money period. The were doing it with their Pharma spam and all the associated domains and paying for those to pimp it out, and they are doing the same with rogue anti-virus apps. LOL… I swear that old Pavel has been driking a little too much of the Jones town Kool-Aid in that he is starting to believe his own B.S…. They can try and spin it anyway they wan’t, they own the domains, they provide the support, they process the payments, it’s their product… they just cjhange the name of it when their is too much heat…. it’s like the counterfit drugs and Pharma spam, the money is too easy to make and they won’t give it up.. their strategy is deny, deny, deny… no matter how much evidence you have they would never admit they are doing wrong. The unfortunate thing is that these guys have russian Law enforcement and politicians in their pocket and their won’t be any end to it anytime soon. It would be nice to see ICANN and the hosts/ASNs/registrars enforce their AUP/ToS and put some of these clowns out of buisness.
“The unfortunate thing is that these guys have russian Law enforcement and politicians in their pocket and their won’t be any end to it anytime soon.”
And that is the real issue here.Yet Russia has the balls to call Western nations corrupt?Ha!At least we can try and take them to court and throw them in jail.Over there?Youll be lucky if you dont “disappear”.
Карусель-карусель, кто успел тот не сел )
http://herbucks.com/ = Herbal Pills Affiliate Program
(looks like the former GenBucks)
Contains a list of “Our sites:”
http://www.xtendrx.com
http://www.acaieasyslim.com
http://www.enhancexl.com
trial.enhancexl.com
Compare that with the list provided above by Konstantin Abramov
At bottom of the herbucks.com web page:
Almarex Alliance ltd 2010
Compare that with registrant details for those sites –
Almarex Alliance ltd
Dayana Carolina Sologuren Toro (calite.kristine@gmail.com)
Geneva Place, Water Front Drive, Road Town,
Tortola
Tortola,Tortola
VG
Tel. +44.2032897777
Same registrant for
xlforce.com
nutritionsupport.net (https only)
resveratrol365.com
prostateforte.com
and the secure website processor at
WEB-PAYMENT-METHOD.COM
And that’s just scratching the surface.
very detailed article like andy said, who better make an anti-virus than an insider.
i was shell shocked to learn some of its employees were selling out its services..
Anyways another lesson learned!!
I hope my MAC laptop provides enough protection…
cheers
Brian,
An offtop question:
What software did you make the timeline with?
Thanks
It’s a Mac program called Timeline 3D.
Thanx Brian.
OK wow, that really does make a lot of sense dude.
http://www.total-privacy.ie.tc
I have question here. Quite a number of times the author has talked about internal leaks at Chronopay. Accepted and believed the author’s story on Chronopay but my question is how the author got access to the internal documents of Chronopay and if it is from an employee at Chronopay isn’t the employee and the author also in breach of security. The employee for obvious reasons and the author because he either bought internal information of an organization from its employee or the author coerced the employee to divulge information.
I still don’t know who took the documents. But it would take quite a bit of effort to fake 30k+ emails, including long conversation threads spread over many months.
The data was offered by an anonymous source, without much explanation of how it was come by. I didn’t ask for the information. ChronoPay execs are convinced it was leaked by a former IT guy at the company.
Who is that Martins Berkis-Bergs http://www.linkedin.com/pub/martins-berkis-bergs/26/a30/ab5