The latest version of the SpyEye trojan includes new capability specifically designed to steal sensitive data from Windows users surfing the Internet with the Google Chrome and Opera Web browsers.
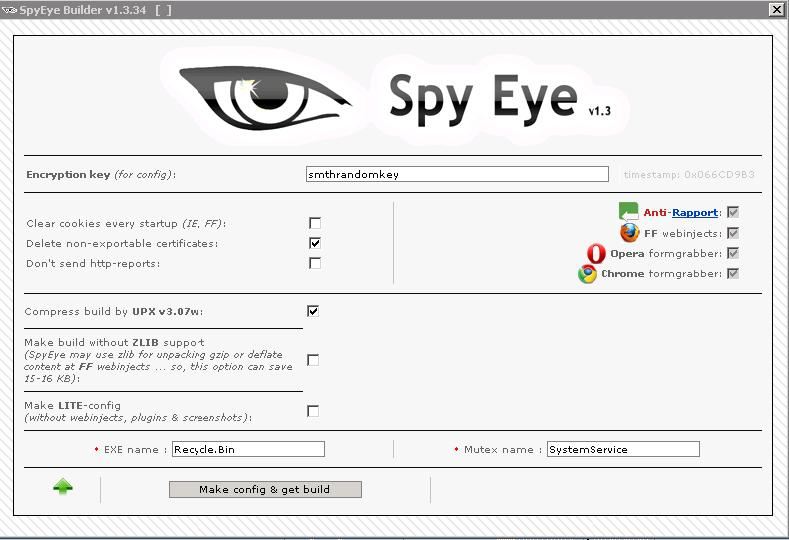
The author of the SpyEye trojan formerly sold the crimeware-building kit on a number of online cybercrime forums, but has recently limited his showroom displays to a handful of highly vetted underground communities. KrebsOnSecurity.com recently chatted with a member of one of these communities who has purchased a new version of SpyEye. Screenshots from the package show that the latest rendition comes with the option for new “form grabbing” capabilities targeting Chrome and Opera users.
Trojans like ZeuS and SpyEye have the built-in ability to keep logs of every keystroke a victim types on his or her keyboard, but this kind of tracking usually creates too much extraneous data for the attackers, who mainly are interested in financial information such as credit card numbers and online banking credentials. Form grabbers accomplish this by stripping out any data that victims enter in specific Web site form fields, snarfing and recording that data before it can be encrypted and sent to the Web site requesting the information.
Both SpyEye and ZeuS have had the capability to do form grabbing against Internet Explorer and Firefox for some time, but this is the first time I’ve seen any major banking trojans claim the ability to target Chrome and Opera users with this feature.
Aviv Raff, CTO and co-founder of security alert service Seculert, said that both SpyEye and ZeuS work by “hooking” the “dynamic link library” or DLL files used by IE and Firefox. However, Chrome and Opera appear to use different DLLs, Raff said.
This strikes me as an incremental yet noteworthy development. Many people feel more secure using browsers like Chrome and Opera because they believe the browsers’ smaller market share makes them less of a target for cyber crooks. This latest SpyEye innovation is a good reminder that computer crooks are constantly looking for new ways to better monetize the resources they’ve already stolen. Security-by-obscurity is no substitute for good security practices and common sense: If you’ve installed a program, update it regularly; if you didn’t go looking for a program, add-on or download, don’t install it; if you no longer need a program, remove it.




Okay, so what are the DLLs that are hooked? What are the forensic artifacts of this stuff?
As far as Firefox goes, I noticed a bogus extension called “z” mentioned in many Adblock Plus issue reports. It uses a random extension identifier which is a pretty good indication that it is malicious (makes sure that blacklisting by extension identifier won’t work). From the name I guess that it might be related to ZBot (Zeus) but that’s only a guess. I wouldn’t be surprised if that extension also does something to prevent showing up in the usual add-ons user interface.
PS: The data for these issue reports is collected automatically (list of installed extensions is optional), the users are most likely not aware of having this extension.
Wladimir, thanks for your comment. That’s very interesting. So this “z” extension shows up as an add-on or a plugin, or what? Also, have you noticed that this add-on/plugin/whatever is consistently accompanied by another add-on/plugin that might not be so normal?
It’s a regular extension, not a plugin. Meaning that it is simply some JavaScript code (which is more than enough to grab form input). And there is no consistent “companion” extension.
That said, it isn’t the only malicious extension I noticed in the reports. Most of them can be identified as adware however, they either change user’s homepage or search page or they inject ads into web pages – they are the reason why users send these reports in the first place. In case of “z” however the reason for the issue report cannot be linked to the extension, the extension apparently doesn’t have any obvious malicious functionality. If it is doing something then it is doing that in the background and the user doesn’t notice.
Would this threat apply equally well to Linux or Mac versions of Chrome and Opera?
“Would this threat apply equally well to Linux or Mac versions of Chrome and Opera?”
I’m no expert, but my guess would be “no”, since DLL files are generally specific to Windows. The spyware runs on the Windows OS and there probably isn’t a variant (yet) for Linux and Mac systems.
Given that the config page in the screenshot lists several Windows-specific options – I don’t think that Spy Eye is targeting either Linux or OS X. And it needs to infect the machine before it can hijack the browsers. So Linux and OS X users should still be mostly on the safe side.
Yeah – more security-through-obscurity. 🙁
Mac and Linux users keep on thinking like this for some strange reason when they should know better. It’s a false sense of security at best, and will mean the first really good crimeware apps will run through the typical technophobe Mac sheep fold like a wolf through spring lambs. At least the linux users (and the techies who use Macs because they are really linux under the hood) will have some awareness of it when they are being predated.
> [Linux and Mac is] more security-through-obscurity
But you’re simply wrong. Linux and Mac don’t allow programs to be installed without the user’s permission. They simply don’t. There has never ever been a single exception to this rule. Unless that security model changes, and that’s extremely unlikely, they will stay virus free.
And Mac is anything but obscure at this point. If it were possible to attack it, people would. Its that simple.
Well, this kind of thing always elicits a “yeah, but Java isn’t part of the OS” argument, but I should note that last year there was a version of koobface that used Java to target/infect Mac systems. It didn’t use a vulnerability in Java per se, but used the same very convincing download prompt that criminal hackers have been using against Windows users.
http://krebsonsecurity.com/2010/10/koobface-worm-targets-java-on-mac-os-x/
> koobface
Fair enough, but I think tricking a user into installing a program is a world different than something being installed without any user action whatsoever, as happens in Windows.
I don’t have stats at the ready to support this, but I would say that probably more malware gets installed on Windows machines these days via social engineering than through vulnerabilities. There’s no reason to assume it would be any different for the Mac.
I hate to burst anybody’s bubble, but most of the malware I see these days isn’t installed “with no user interaction”. And, if the user “authorizes” the install, it doesn’t matter if it is Windows, OS X, or Linux (much of the Windows malware I see runs in the context of the logged-in user, if the user doesn’t have admin rights. This means it is still able to install, though the scope of the damage it can do on a shared computer may well be less.) And, lest you think that Mac users are somehow less prone to enticement attacks than their Windows brethren, remember this: all those new Mac users? Most of them came from a Windows background. And, they brought many of their bad habits (including a propensity to blindly click on clickables, open attachments, and ignore security warnings) with them.
Besides, if you have a vulnerable service running in a security context with high privilege, and that service is exploited, again it doesn’t matter if it is Windows, OS X, or Linux.
~EdT.
SpyEye targets Microsoft Windows machines, period. I’m not aware of anything SpyEye related that targets any other operating system.
That said, there is no reason that the basic approaches to form grabbing methods should work much differently on other OSes. I noticed as I was researching this post that on a couple of carding forums there were members who had quite recently developed and were selling form grabbing code for Chrome. I mention that only because it suggests that the underground community is trying to better understand how these browsers work under the hood.
Interesting to see the anti-Rapport icon in the graphic. Trusteer claims this is marketing and that the anti-Rapport functionality actually Rapport detect and remove Spyeye.
http://www.trusteer.com/blog/turning-tables-spyeye
I found the anti-Rapport icon interesting too because just yesterday I was offered the opportunity to download Rapport after logging into my Bank of America account. But since I do all my banking exclusively via Ubuntu, and Trusteer doesn’t currently support the Linux platform, I decided to decline the offer.
i saw that too and wondered about it. it’d be interesting to see an analysis on the feature.
Interesting AlanS!
I’ve never noticed a removal claim by Trusteer before!? But then, they try to limit too much information for a reason, so the black hats don’t easily develop a counter move.
None-the-less, they have been forthcoming in some detail on forums where IT security types have legitimate questions verifying capability.
> there probably isn’t a variant (yet) for Linux and Mac systems.
And there never will be, for the same reason there never has been: Linux and Mac are secure, Windows isn’t. You could write a program that could do this on Mac/Linux, but it wouldn’t be able to install itself without the user’s permission, which is a super critical difference. In Windows, its retardedly easy to make programs install without permission, and hence be “viral”.
> That said, there is no reason that the basic approaches to form
> grabbing methods should work much differently on other OSes.
Right, its easy to do this on any OS, in Python you can literally make a keylogger with 5 lines of code. But the critical difference is it would never be installed on Mac or Linux without the user intentionally doing so, and of course no user ever would.
“and of course no user ever would.”
I’m assuming this is sarcasm. Please let me know if it isn’t so I can “thumbs down” you.
No user would ever voluntarily install a trojan? Did someone make a rule that all malware will now be labeled with an accurate description of what it does?
People know they’re installing software; they just think it’s a free game, a spyware remover, a video codec (they don’t know what a codec is and they’re not going to embarrass themselves by asking), an online banking update, whatever.
> “and of course no user ever would.”
Oh no, not the thumbs down!
Sorry Bob but your reading comprehension isn’t very good. What I mean is that no user would ever install such a malicious program intentionally. On Windows that doesn’t matter since its possible for programs to install themselves without the user’s persmission. On Mac and Linux this simply isn’t possible, which is why there are no viruses on Linux and Mac.
>On Mac and Linux this simply isn’t possible, which is why there are no viruses on Linux and Mac.
What rock have you been sleeping under for the last 5 years? Not only are there Linux and Mac viruses, but they have drive by downloads –
http://threatpost.com/en_us/blogs/apple-plugs-safari-drive-download-security-holes-090810
“A use after free issue exists in WebKit’s handling of elements with run-in styling. Visiting a maliciously crafted website may lead to an unexpected application termination or arbitrary code execution.”
Arbitrary code execution fits the definition of drive by and malware. Things don’t need to be “installed” in order to steal web browser credentials and all sorts of other havoc.
I’m not surprised that they are going after chrome, which has a reasonable install base, but I am surprised they are bothering with Opera which usually shows up as having a pretty small install base (at least on non-mobile devices). Thanks for the warning though Brian, since Opera is my primary browser.
It would be interesting to know if this trojan would work on Linux running WINE, and then running Chrome and Opera browsers.
Excellent post Brien
Per the Official Wine Wiki – FAQ:
10.1. Wine is malware-compatible
Just because Wine runs on a non-Windows OS doesn’t mean you’re protected from viruses, trojans, and other forms of malware.
http://wiki.winehq.org/FAQ#head-3cb8f054b33a63be30f98a1b6225d74e305a0459
Only if you’re running the windows versions of those browsers under wine. It wouldn’t be able to get at the native linux builds, and it’d be highly unusual for someone to be running a windows build of chrome under wine for general browsing.
“Security-by-obscurity is no substitute for good security practices and common sense…”
Can I get your permission to have that made into a stamp? I have a couple of foreheads in mind.
Or a couple of billion? Wait, how many users are there on the internet now?
What’s interesting is that the subject vulnerability appears tophave been reported by Microsoft. See http://www.theregister.co.uk/2011/04/26/ms_third_party_bug_advisories/
The blog entry by Trusteer linked elsewhere in the comments claims the SpyEye creators have been running an effective media campaign including leaks and screenshots as marketing for their product. Something to consider.
Not sure I want to jump into the “which OS is more secure” debate again but think it is worth noting that Joanna Rutkowska’s group has just released a beta of a new Linux distro called Qubes that looks interesting. Qubes attempts to implement a “security by isolation” approach using a bare-metal hypervisor and VMs.
http://qubes-os.org/Architecture.html
http://theinvisiblethings.blogspot.com/2011/04/qubes-beta-1-has-been-released.html
Pertinent comment on existing OS security: http://theinvisiblethings.blogspot.com/2011/04/linux-security-circus-on-gui-isolation.html
Well AlanS!!!!
You are a fountain of interesting posts today!
I’m not trying to be sarcastic; just genuine! 😀
@JCitizen
You’re welcome!
I haven’t tried Qubes yet. It looks like an interesting project although they note a few limitations. I think what they are trying to accomplish is probably quite difficult. Segmentation and isolation of some sort seems to be critical to any form of defense that is likely to be effective.
I notice it requires 64 bit, so I imagine it’s pretty resource-heavy. You have to think it would be pretty difficult to do.
Off Topic.
Brian, do you have any info as to why filehippo and all the other download sites have the most recent Java version for download, but Oracle does not, nor are they pushing it out via the updater?
Faust – What do you mean they’re not offering the latest version. How do you figure?
http://www.oracle.com/technetwork/java/javase/downloads/jdk-6u25-download-346242.html
If you go to http://java.com/en/download/installed.jsp
and Verify your java version it says:
You have the recommended Java installed (Version 6 Update 24).
Also going to the Control Panel -> Java and checking for Updates says that you have the latest version.
Maybe there is some kind of lag-time before the update is offered on the front page and via auto-update?
Thanks for the deep link. As a few hours ago there is still nothing about the new version at java.com, which is where I naively assumed the latest info would be posted.
https://www.java.com/en/download/manual.jsp
Note that your link is to the JDK, not the JRE.
Most users want the JRE: http://www.oracle.com/technetwork/java/javase/downloads/jre-6u25-download-346243.html
The bookmarkable link for this is probably:
http://www.oracle.com/technetwork/java/javase/downloads/index.html
and you need to click the “Download JRE” button
As a reminder for people who don’t remember which version to get, if you’re using Firefox 4 for Windows then you’re using a 32 bit Firefox and will need a “Windows x86” version of Java — it doesn’t matter if you’re using Windows 7 x64 or Windows Vista x64, Firefox is x86 and the plugin needs to be the x86 version, otherwise you’ll be surprised when nothing happens.
This latest Java release does not include security updates. Otherwise, I’d be all over it like white on rice.
http://www.oracle.com/technetwork/java/javase/6u25releasenotes-356444.html
“Java SE 6u25 does not add any fixes for security vulnerabilities beyond those in Java SE 6u24. Users who have Java SE 6u24 have the latest security fixes and do not need to upgrade to this release to be current on security fixes.”
I use a password manager (LastPass) for userid’s and passwords in forms. Does this thwart the efforts of Zeus and SpyEye to hook DLL’s and capture this information? In similar fashion, I use the LastPass onscreen keyboard to log in to my account. Does this also prevent theft of this password? Anybody know the answers, which probably a number of readers would be interested in. Thanks.
Short answer Bill;
No.
However, if you are using KeyScrambler, you can be reasonable sure that it would be difficult for manual entries. Since Rapport is built to integrate with LastPass and/or KeyScrambler. I should think you could be reasonably sure it would be difficult for keyloggers and video spies to capture your LastPass session.
I will admit I’m not sure how; but we heard from several of the developers on this at Tech Republic, and there are more details in those discussions.
And of course Lloyd Liske is correct also.
One of the best features of LastPass is the fact that none of that information can be found unencrypted on your hard drive. This can be a good place for malware to find the same information.
Bill: LastPass onscreen keyboard is useless against this type of form grabbing because it steals the input after the form information is submitted. LastPass onscreen keyboard would protect against hook based keystroke logging only. Unfortunately there are other methods of Keylogging and in today’s threat world the choice method Crimeware authors use is form grabbing or memory injection form grabbing.
Zeus/Spyeye injects into urlmon.dll, wininet.dll and other system dll’s. The latest Spyeye uses simular browser injection techniques for Opera and Chrome.
This post is accurate in that the author is simply injecting into different memory locations in these newly supported browser dll’s.
+1. Don’t have much to add to Lloyd’s response, other than it is 100 percent spot-on. On-screen keyboards won’t defeat form grabbing. And I don’t think password managers will either. The data has to be submitted to a Web site in a fashion that the Web site understands, and while it may be encrypted by some custom encryption while it’s being stored by lastpass, to my knowledge that’s not going to protect you if a form-grabbing trojan is also on your machine.
The comments by Lloyd and Brian that password managers are not effective against this sort of form grabbing are rather depressing. The better firewalls can prevent personal data from being sent from your machine, but I suppose the theftware is able to defeat this without much problem. How do they do it? Encryption?
Primarily by session riding. Like they say, the information is already in the browser, if you own the browser, then you already have the information. This is why I mention Rapport, because it supposedly blocks this session information. I’ve tested it against form injection, and it works for that.
However, you just have to take them at their word that they can actually do all of this. You got to ask yourself though; if the criminals are bragging about supposedly defeating Rapport, then you have to ask yourself,” who the primary protection is for the browser?” I doubt that they have defeated Rapport yet; but if they do, I’m sure Trusteer will be busting @ss to correct the issue.
Until I read of a take-down of Rapport by the criminals; I bet on Rapport for my clients. They refuse to use LiveCDs, dedicated PCs, and VMs, so this is the best I can do for them. It is compatible with a plethora of browsers, so I’m pretty sure all of them mentioned here, are covered.
Bill asked: “The better firewalls can prevent personal data from being sent from your machine, but I suppose the theftware is able to defeat this without much problem. How do they do it? Encryption?”
JCitizen replied: “Primarily by session riding. Like they say, the information is already in the browser, if you own the browser, then you already have the information. ”
Now, I will be the first to admit that I’m not up on the latest developments in malware. That’s primarily why I’m here.
I think an elaboration on JCitizen’s reply would be that your firewall allows your browser to accept and transmit data to and from the internet – that’s what you want it to do. So if malware has injected itself into your browser’s code and it’s access to your hard drive and internet requests are then indistinguishable from the browser’s, that’s where it wins and you lose. Your firewall will see the request as coming from the browser and allow it. If it’s a zero-day exploit, all of the up-to-date patching and AV/anti-malware software in the world is not going to save you from it. (With the addendum, that your firewall can protect access to your personal data that you’ve configured it to protect, but I haven’t been overly concerned about that. It’s letting that data go out to IP addresses owned by bad guys that’s the problem, as I see it.)
Now, I’m not preaching, advocating or even suggesting that what I do will work for anyone else besides me, but I have a couple of tools I use to mitigate this threat. One is to restrict my browser’s access to ports 80 and 53 (http and https). Granted, some malware can still transmit data on these ports, but I’ve seen a lot of attempts on other ports, so cutting them out of the picture at least helps. Then I use PeerBlock, which blocks access to and from known malware and adware IP addresses. Again, not complete protection, and it is another plug for publicly outing these IP addresses, but it cuts another large slice out of the block of bad guys trying to use your computer. Firefox is doing something similar to PeerBlock, but I have a little more confidence in the comprehensiveness of PeerBlock’s database. I also periodically use Essential Network Tools to monitor the IP addresses that have active connections to my computer. ENT allows you to look up the WHOIS records for any IPs, and also to immediately terminate any of them. Again, not a failproof protection, because it’s just not practical to monitor every connection all the time. But if you make a habit of doing that regularly, you’d spot pretty quick if your machine had been made into a ‘bot.
Perhaps this strategy belongs more in the category of “Beyond Patching and AV/anti-malware Scanning”, as ways to avoid being the victim of a zero-day, but any and all critiques are welcome.
If you get a bot like SpyEye or ZeuS on your system, your firewall is almost certainly *not* going to save you.
In this case, you might actually have more protection against SpyEye by renaming Firefox and Opera to something different, like FF.exe or OP.exe.
Note that while this might accidentally work today, it’s a terrible strategy. It’s true that libraries can hook processes by name, but it’s also common for them to check everything and only select things they like.
For firefox it’d make sense for a library to look to see if ‘xul.dll’ is present, because firefox (or similar things) will link to it….
I’m not sure about Opera, but if someone has spent the time to figure out how to hook it, they should be able to easily detect opera as a process which is hookable for the things they need to hook instead of by app name.
@timeless – I hope (and trust) you understand that my response about renaming the exe was meant to show the relatively uselessness of firewalls these days in the face of malware, not to offer some kind of security defense that would stand up over time.
That said, I’m told that renaming the exe does in fact provide some protection this time around. Maybe not next time, but I also wanted you to know this was not an empty tip, and point out that most of these attacks/malware families are designed to attack standard installations, not a million different permutations of them.
Deborah said:
“Now, I will be the first to admit that I’m not up on the latest developments in malware.”
That’s pretty obvious from this and previous posts!
JCitizen recommends Rapport for his clients, not the convoluted, abstruse partial-protections that you rely on while using an unpatched version of XP. Most of us who struggle against malware prefer simple solutions that run in the background. That’s what readers and clients want and expect.
@JBV
“Most of us who struggle against malware prefer simple solutions that run in the background. That’s what readers and clients want and expect.”
I am completely, 100% convinced that many people want simple security solutions that run in the background. I am not convinced that any we have today are good security protection, because they don’t protect against zero-days.
My approach is to be looking out for the zero-days, and I think that if you effectively do that (within some reasonable margin of error), you can safely run on unpatched XP. And I have, for a long, long time. It’s funny though, the same precautions I put in place back when XP was new still seem to be holding up pretty well today. We didn’t have sandboxing and virtual machines then, which are really hot new additions to one’s toolbox, but almost all of the basics still apply.
I’m not saying that this approach is easy and should be adopted by everyone. It’s a teensy bit of work, and you hardly notice it once you make habits of it, but I feel more secure doing it, and understanding as much as I can so as to upgrade my security measures, if needed.
And I’m not saying that those of you who are in the business of giving security advice are wrong. But there’s more than one way to skin a cat, as I’m sure you know.
@DeborahS, thought that was an interesting approach. A few questions though if you don’t mind:
“One is to restrict my browser’s access to ports 80 and 53 (http and https)” did you mean port 443?
Also out of curiosity how do you keep on top of malware that is fast fluxing? A blacklist isn’t going to be able to keep up with it unfortunately. And unless you are continually monitoring traffic, which no on in their right mind could do, it seems like the horse is out when you slam the barn door?
Interesting approach though thanks for sharing. Its roughly similar to the one I take for researching the actual behavior of malware I’ve intentionally infected a system with. As a reference you might be interested in the book: Malware Analyst’s Cookbook. Its a great read for those interested in malware.
@helly
Arg – yes I meant to say port 443, not 53, for https. I’ve been looking hard at what my new wireless router wants to do, so I guess I had 53 on the brain.
“Also out of curiosity how do you keep on top of malware that is fast fluxing? A blacklist isn’t going to be able to keep up with it unfortunately. And unless you are continually monitoring traffic, which no on in their right mind could do, it seems like the horse is out when you slam the barn door?”
First of all, I’ve never maintained the fantasy that I’m 100% safe. But from what I’ve seen so far, nobody has devised a way for anybody to be 100% safe, other than to just stay off the internet. This is an unacceptable option for most modern people.
I think that the best (or at least a good) way to keep on top of fast fluxing malware is to understand what the attack vectors are and devise protection strategies along those vectors. The content of the malware is constantly changing, but the avenues available for them to attack you remain relatively the same. They keep finding new ways to exploit what’s there, but they can’t change it from what it is. This is why I’m somewhat leary of moving to a new operating system, one that I don’t understand as well as I understand the old one.
No, even the best kept blacklist is not going to block all the bad guys. They can set up new domains faster than even an army of watchers can spot and report. However, a blacklist does keep them from continuing to use their old bases of operation, and it’s eye-opening to see how many of them do keep trying to. It’s conceivable to me that we could eventually wear them down, if enough people were blacklisting them, to the point that they’d get tired of having to pull up stake and move on weekly or even daily. But that’s a pipe dream at this stage – we’re not going to get enough good people (potential victims) to participate in it to make it a reality. Still, there is value in protecting yourself from intrusions by the known bad guys, and there are a lot of those every day.
You are also correct, that monitoring your internet traffic is not practical to do all the time, so it is not an effective means of protection all by itself. But it is a useful tool to have available, and regular checking will tell you whether your computer has been made a ‘bot or not. It’s also helpful to have on hand if something hinky is going on, or you know you’re visiting a potentially dangerous website, etc. Then you can switch it on into full view and watch every connection made, at the ready to disconnect any that look like they’re up to no good.
At this point, internet security is not a science, it’s an art. At least that’s the way I look at it.
It appears I need more protection than just LastPass. I will definitely look into KeyScrambler, cited by JCitizen, as well as Rapport, which he also mentions, as well as AlanS, TJ, and gomez. Thanks for your input. I’m paranoid, as I travel to so-called friendly countries whose govts are known to go after the laptops of visitors, and it’s not always possible to carry your laptop with you. Removing the HD is not simple (nor recommended) and portable apps don’t seem to counter all the threats.
I should mention, all of these utilities are free, and Rapport does have built in keylogging and password protection. I’ve never tried it to see, whether or not, it applies the password to a form; but it does ask you if you want to protect them when they are first entered for a particular URL.
It is better avoid infection in first place. Maybe EMET would help?
That is the whole point; you can’t avoid infection these days. Some malware will always get through. Even with the best blended defenses.
Did you mean ESET? I’ve never heard of “EMET”.
I mentioned EMET in a post here
http://krebsonsecurity.com/2010/12/exploit-published-for-new-internet-explorer-flaw/
Sorry Brian!
My memory is seriously degrading! I did read that article; can’t wait for the follow up!
The silverlight videos at Security Tech Center won’t run, so I’ll have to be happy with the manual.
Well, I think that using Windows standard user account with EMET, and if possible powered by AppLocker is quite solid foundation for safer system.
Now, if you block by default Iframes and JavaScript, download softwares only directly from trustworthy manufacturers and keep system and softwares up-to-date (and remove useless software, like Java, if you really do not need them) and so on. I think you have quite safe now. Of course there is no software that could prevent ‘layer 8’ threats but at least system wide infections is then much harder to get.
Sounds like the hot smokin’ tip for dedicated PCs.
Brian, this was posted on twitter recently (#psnhack) as well as some scene forums
“Rumors are following thru various underground “credit card” trading forums, and on the new #psnhack twitter list that a large section of the PSN database containing complete personal details along with over 2.2million working credit card numbers with the much-needed CVV2 code are being offer up for sale to the highest-bidder, after the “hackers” tried to sell the DB back to Sony for a price, but they of course didn’t answer! ”
Have you seen/heard anything from your sources?
Sorry, I had multiple tabs open and posted on the wrong one. :/
ROFL
funny how the interwebs work. that was taken from several screenshots I posted in the images section of this blog and tweeted earlier today.
Here you go:
Lots of interesting scuttlebutt in the hacker underground on what really happened with Sony #PSNhack, eg: http://bit.ly/j6Ox0s
Lots of interesting scuttlebutt in the hacker underground on what really happened with Sony #PSNhack, eg2: http://bit.ly/jK8ivb
Scuttlebutt from hackerforums on #psnhack. Discussion of the potential price impact of millions of new CCs: 4 sale http://bit.ly/juehk6
Thanks Brian, I should have really checked your tweets before posting.
Knowing the crooks at Sony; I wouldn’t be surprised if this was a sham “breach”. They could always blame abuse on some nefarious cracker gang.
Using an independent limited user account for banking and delicated data is enough against 100% of malware.
Any updates on these legal proceedings? I could not find online court docs other than the initial briefs and the denial of summary judgment last year. I am waiting on a pacer.gov account to see if I can learn more, but would appreciate any updates people can share.
Sorry for the comment goof – meant to leave it for a different article.