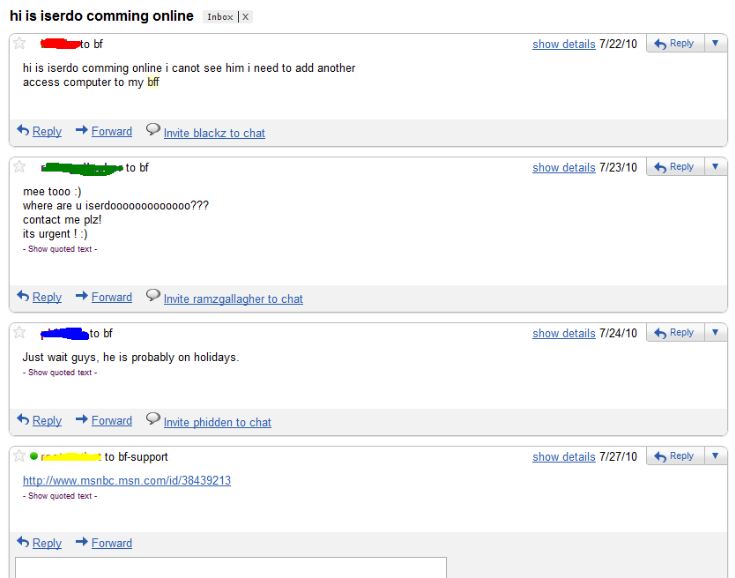
Members of an exclusive underground hacker forum recently sought to plant malware on KrebsOnSecurity.com, by paying to run tainted advertisements through the site’s advertising network — Federated Media. The attack was unsuccessful thanks to a variety of safeguards, but it highlights the challenges that many organizations face in combating the growing scourge of “malvertising.”
Last week, I listed the various ways this blog and its author has been “honored” over the past few years by the cybercrime community, but I neglected to mention one recent incident: On May 27, 2011, several hackers who belong to a closely guarded English-language criminal forum called Darkode.com sought to fraudulently place a rogue ad on KrebsOnSecurity.com. The ad was made to appear as though it was advertising BitDefender antivirus software. Instead, it was designed to load a malicious domain: sophakevans. co. cc, a site that has been associated with pushing fake antivirus or “scareware.”
The miscreants agreed to pay at least $272 for up to 10,000 impressions of the ad to be run on my site. Fortunately, I have the opportunity to review ads that come through Federated’s system. What’s more, Federated blocked the ad before it was even tagged for approval.
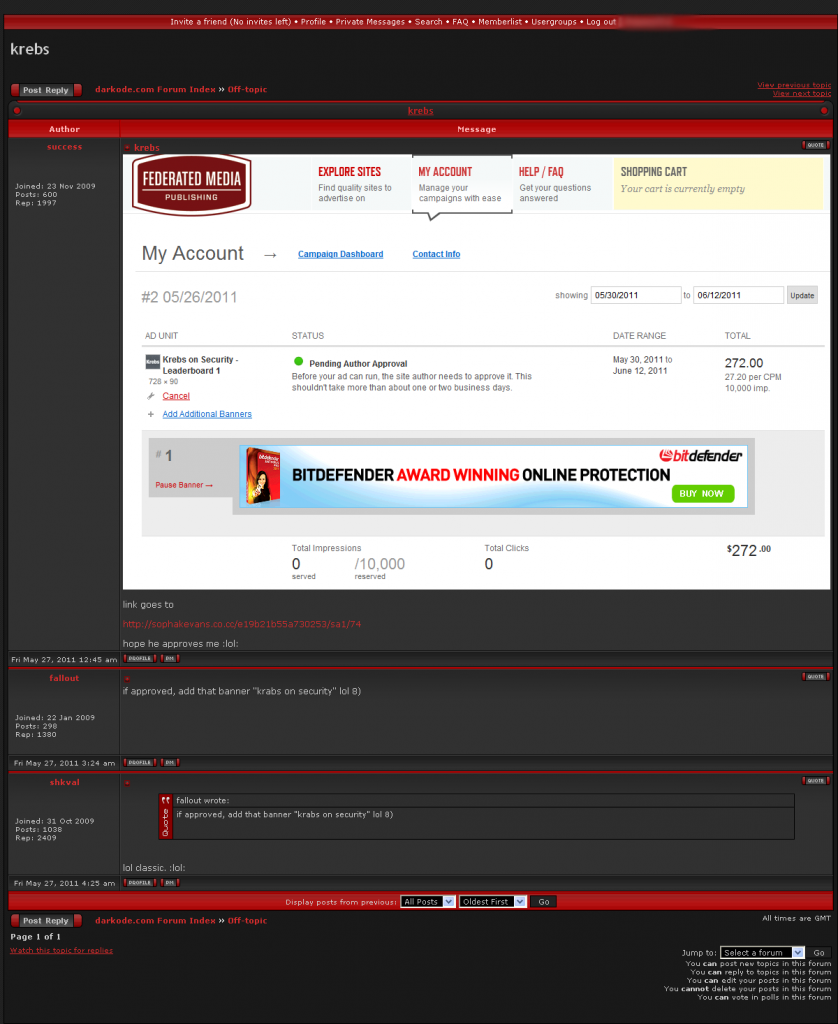
I learned about this little stunt roughly at the same time it was being planned; Much to the constant annoyance of the site administrators, I secretly had gained access to Darkode and was able to take this screen shot of the discussion. The incident came just a few weeks after I Tweeted evidence of my presence on Darkode by posting screenshots of the forum. The main administrator of Darkode, a hacker who uses the nickname “Mafi,” didn’t appreciate that, and promised he and his friends had something fun planned for me. I guess this was it. Interestingly, Mafi also is admin at malwareview.com and is the developer of the Crimepack exploit kit.
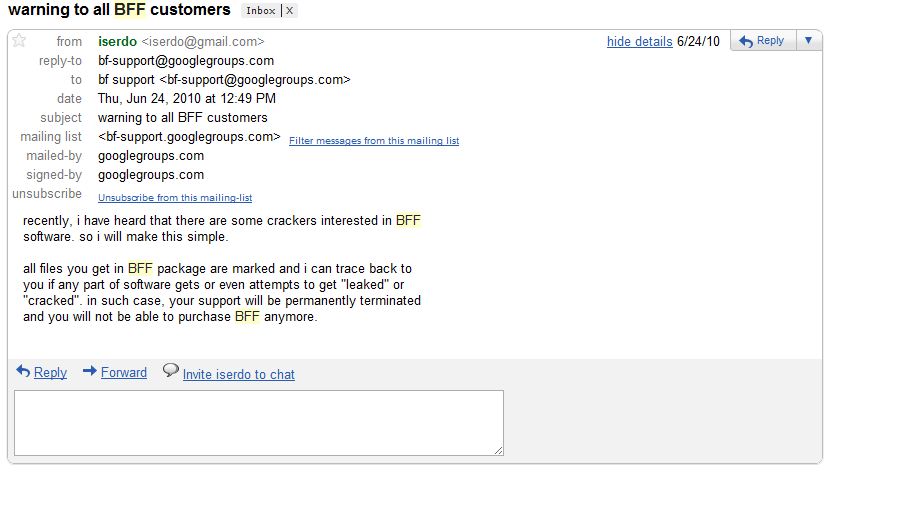
The Darkode forum launched sometime in 2008, and according to past and current members was used primarily as a support forum for the “Butterfly Bot,” a prolific bot program that was sold in the underground for several years by its creator, a hacker who used the name “Iserdo.” At some point, Iserdo sold the forum to other miscreants, and began running support for customers of his Butterfly Bot program via a Google Group called simply “Bf-Support”.
In July 2010, the 23-year-old Iserdo was arrested by authorities in Slovenia on suspicion of running the infamous “Mariposa” botnet. According to the Mariposa Working Group — a partnership between the FBI and private security firms — Iserdo sold thousands of Butterfly kits for prices ranging from $500 to $2,000. The buyers of these kits didn’t need to know much about coding or hacking; the kits allowed even unskilled hackers to create relatively sophisticated botnets.
Butterfly Bot customers wonder why Iserdo isn't responding to support requests. He has just been arrested in Slovenia.
As evidenced by a recent front page story by USA Today’s Byron Acohido, malicious content embedded in online ads, or “malvertising,” is a long-standing problem that has recently taken a sharp turn for the worse: The story points to a recent analysis which documented a peak of 14,694 occurrences of malvertisements in May of this year, up from 1,533 in May 2010.
Many security-conscious readers have chosen to block ads altogether with browser add-ons like Adblock. Wholesale blocking ads can be effective in stopping malvertisements, but this approach also has the perverse effect of blocking a primary source of revenue for many sites (including this one). I have limited Federated Media to serving a very small slice of the ads on KrebsOnSecurity.com, and I am choosy about those that I let in. Add-ons like Noscript for Firefox allow users to be far more selective in which ads/scripts to allow and block.
In addition, many malvertisements rely on scripts that redirect browsers to sites that host exploit kits, software packages that probe the visitor’s browser for unpatched security flaws in popular plugins like Adobe Reader, Adobe Flash Player, Java, QuickTime and WinZip. Keeping these third-party apps up-to-date with the latest security fixes is a great way to fortify your browser against drive-bys. If you need help remembering to patch these programs, consider using a free program like Secunia’s Personal Software Inspector or FileHippo’s Update Checker.




Thanks for the reminder, Brian. As someone who blocks most of the ads on your site, it’s time for me to fire-up PayPal once again.
typo in the headline
Indeed, it propably should be “attempted” rather than “attemped”. A prove that we’re reading text written by a human, rather than highly intelligent bot. ;P
Well, in the words of the criminals themselves: lol, classic 😆
…
You know it’s a funny thing. I make a portion of my income through Pay-Per-Click advertising using a variety of ad networks. Basically I purchase clicks and deliver the user to goods or services or more often potential providers of products and services – in other words I provide leads to customers of my business.
Part of the “mix” of ads I buy is through what I myself consider to be kind of an insidious development – ads delivered through adware platforms. Make no mistake about it: I only use whitehat, legitimate networks that have people agree to have ads placed onto their systems before installing – notice how so many applications are delivered with “toolbars” these days as an example of what I’m talking about – but it’s something that I just couldn’t put up with as a user personally. That’s why I said “funny” heh.
The reason why I support this model with my business? It works for some traffic and it can be very lucrative indeed with 1c per click not being uncommon – do the math. Offers usually convert at say 0.5-0.9% of clicks which means I’m paying $1-2 per lead generated and getting paid multiples of this for each and every one. With all the “ducks in a row” so to speak this happens.
But I can’t help thinking it’s come about as a result of increased blocking of traditional ads which, perhaps ironically, is something I do myself.
TJ is right, I think I’m gonna hit the tip jar Brian … I feel a tad guilty perhaps 😉
A blended defense will take care of this ‘malvertising’ anyway. I never have any trouble with my SpywareBlaster host file blocking any of your ads, but it will on known malicious servers.
MBAM – the pro version has a known bad IP blocker that will block incoming, and if not that – outgoing attempts. If not those two, there are plenty of tools in the blended armor, like Comodo, and other behavior based HIPS.
CCleaner makes quick work of any malware stuck in the temp folders, because NOD32 or Avast is present and won’t allow execution of said malware. The list goes on.
I would love pointing my honey pot lab at your site Brian. I’ve been bored lately – no action on my LAN – anyway. I do have some clients with extremely bad actors targeting them personally. Those do occasionally keep me entertained.
Thanks for sharing this article, Brian.
btw:
I like & trust FileHippo.
but just a quick note:
the “FileHippo’s Update Checker”
requires .NET 2.0,
(.NET = another source of endless security & conflicting update problems…).
I removed .NET & Java from my Win pc
last year –
learned how to live
without these 2 “headache-wares”.
Thank you, Brian
It clearly shows how diligent you are in choosing your advertising network and handpick the adds to run on your page and it shouldn’t be otherwise. You are putting to shame some very large legitimate sites which occasionally ended up serving malware.
I gather that by paying for just 1000 displays they were most likely seeking to take revenge/destroy your credibility and maybe probe your defenses rather than create a revenue stream selling the scareware at sophakevans. co.
I was wondering about the payment details. Did they get “their” money back once Federated Media rejected their add ? Did they attempt to pay by stolen CC or was a legitimate payment ?
Surely the point is that nowadays NO website should be regarded as ‘trusted’. You spotted this attack, but you might miss the next one.
It will ruin the ads market when people feel they have to block everything except text files.
Good job on chasing down Crim/Mafi and finding out about malwareview.com. Mafi is also on a few “Whitehat” malware sites and rubs elbows with malware researchers, which makes me wonder if they know that they are talking to a criminal. Iserdo sold darkode.com to Mafi a while back before he was arrested and just recently Nu11 sold opensc.ws to Mafi as well.
I’m glad that you know what you are talking about, Mafi owns neither of those forums….and chasing down? He’s using the same handle on both malwareview and darkode, and knowing he is adequate on opensc you don’t have to be a brainiac to figure out.
opensc.ws was sold awhile ago but just recently came back online under new owners who have nothing to do with mafi or darkode (and are unknown to the scene as well)…
I mean if you took the time to read the nonsense they claim to be on the verge of selling such as “Pythia bot” you’d have to be some kind of retarted monkey to think that it is real. Pure publicity stunt in the making… Smells of S.Pusher if you ask me.
On other news since you were actually on darkode Brian, you should know all to well mafi might be an super-admin but the forum isn’t his either. It would be interesting to see if you really do know the handle of the owner?
and what “Whitehat” malware sites are you referring to?
Great article Brian, always an interesting read here.
On the note of ‘fortifying’ your browser against attacks, what about a shout out to Microsoft Exploit Mitigation Experience Toolkit (EMET)?
You’ve mentioned it in your articles before, and for me it has become a standard security tool I install on all Windows PCs, regardless of version (ie XP or 7). It’s east to install and setup, and once that’s done, you can pretty much forget about it.
It’s not bulletproof, but I’m willing to bet it will stop 90% of the native attacks against any unpatched Browser (not sure how well it would do against Java attacks). Just my 2 cents.
Thanks, Gaten. Yes, I have mentioned EMET before, but never devoted an entire post to it. Thanks for the reminder. And yes, I use EMET on most internet facing apps. No reason not to, really.
TNO (Trust No One). BLOCK ‘EM ALL! It hurts reliable journalists that depend on ad-based revenue but it’s the only way to be sure.
Critical thinking skills + 1.
Brian: Thank you for the reminder to block *.co.cc
Both darkode.com and malwareview.com are apparently registered via “DIRECTI INTERNET SOLUTIONS PVT. LTD. D/B/A PUBLICDOMAINREGISTRY.COM” and the place to voice concern is here:
http://resources.publicdomainregistry.com/report-abuse/
Krebs – 1
Script kiddies – 0
.oO( If ads on your site aren’t exclusively marketed you’re doing it wrong. ;-))
Well I guess it depends on your situation really but yes I’m surprised that a network is used on this site considering how specialised it is.
But maybe it’s a mix of CPM and exclusive PPC or whatever, who knows.
I’m of the opinion that people who block ads, by whatever means, are people who don’t click on ads anyway. If that is in fact true in most cases, there shouldn’t be any/much loss in revenue.
If ads inform me about products that interest me, both the vendor and I benefit. On a site like this, vendors have a pretty good idea what might interest us without intrusive audience profiling techniques. But advertisers still want to know which ads are bringing in revenue. Readers here have enough understanding to just type in the domain name of the vendor in their browser to avoid dangerous cloaked links, but then there is no way to track which site referred them.
There’s always the old fashioned coupon technique to determine the success of an ad, just as is done in dead tree media. Instead of a click-through link that could be malicious, the ad could display the domain name and ask customers to enter a coupon code at checkout to obtain a discount.
Your’s is one of the few sites I whitelist for ads, even though back when you started your own site I figured you’d be a target for just that tactic, but regardless, Thank you for personally reviewing the ads displayed on your site and helping to protect your users.
By the way, you need to get yourself a profile going over on G+.
I’d unblock ads on your site, BK, if so many of them weren’t the in-your-face flashing/blinking/constantly moving variety.
There’s two reasons why I block ads: One is the reason you mentioned, Heron, and another is that they affect the loading speed of a page. Sometimes even still images are so disturbing that I have to block them.
The “flashing” ads was the reason why I blocked plenty of ad-elements on this site. Before that, I didn’t really care about them, other than maybe occasionally viewed them over curiosity about what kind of ads are shown at here, as they tend to be different sort than what I’ve usually seen.
You know I just re-read the article – if I understand it correctly Brian was on the forum and the owner knew this *before* this attack was attempted – if so it’s not exactly the brightest move to discuss this on the forum hahaha …
Most likely their “only” option. Their mistake was that they did talk about it in too open. They propably wont be doing that mistake again… On the other hand, considering the path they’ve taken in their life, I wouldn’t be suprised if they’d be stupid enough to repeat their errors.
Brian,
Looks like you have a good handle on this stuff, but additional resources never hurt.
Check out https://otalliance.org/resources/malvertising.html, they have a working group on malvertising, if you are interested.
I thought Darkode was pay to register only, with vouches…there must be inside man, I suppose…or Brian Krebs is a good hacker 😀
he just finds members and buy accounts, his attempts at being approved with new accounts never succeded
Buys accounts? Really? I’ve never paid to be on a forum of any kind.
Hi Krebs,
It seems you are very good in catching this. I have the same problem but it hard to monitor this malicious groups. Can you recommend any link which people like me can monitor the underground discussion and eventually protect our system in their planning stage.
Thank you
Impressive that you review can the ads scheduled for display on your site. I guess it’s a safe assumption that Federated Media doesn’t expose you to third party ads.
Very cool if this is the case.