Microsoft on Monday named a Russian man as allegedly responsible for running the Kelihos botnet, a spam engine that infected an estimated 40,000 PCs. But closely held data seized from a huge spam affiliate program suggests that the driving force behind Kelihos is a different individual who commanded a much larger spam empire, and who is still coordinating spam campaigns for hire.
Kelihos shares a great deal of code with the infamous Waledac botnet, a far more pervasive threat that infected hundreds of thousands of computers and pumped out tens of billions of junk emails promoting shady online pharmacies. Despite the broad base of shared code between the two malware families, Microsoft classifies them as fundamentally different threats. The company used novel legal techniques to seize control over and shutter both botnets, sucker punching Waledac in early 2010 and taking out Kelihos last fall.
On Monday, Microsoft filed papers with a Virginia court stating that Kelihos was operated by Andrey N. Sabelnikov, a St. Petersburg man who once worked at Russian antivirus and security firm Agnitum. But according to the researcher who shared that intelligence with Microsoft — and confidentially with Krebs On Security weeks prior to Microsoft’s announcement — Sabelnikov is likely only a developer of Kelihos.
“It’s the same code with modifications,” said Brett Stone-Gross, a security analyst who came into possession of the Kelihos source code last year and has studied the two malware families extensively.
Rather, Stone-Gross said, the true coordinator of both Kelihos and Waledac is likely another Russian who is well known to anti-spam activists.
WHO IS SEVERA?
A variety of indicators suggest that the person behind Waledac and later Kelihos is a man named “Peter Severa” — known simply as “Severa” on underground forums. For several years running, Severa has featured in the Top 10 worst spammers list published by anti-spam activists at Spamhaus.org (he currently ranks at #5). Spamhaus alleged that Severa was the Russian partner of convicted U.S. pump-and-dump stock spammer Alan Ralsky, and indeed Peter Severa was indicted by the U.S. Justice Department in a related and ongoing spam investigation.
It turns out that the connection between Waledac and Severa is supported by data leaked in 2010 after hackers broke into the servers of pharmacy spam affiliate program SpamIt. The data also include tantalizing clues about Severa’s real identity.
In multiple instances, Severa gives his full name as “Peter North;” Peter Severa translates literally from Russian as “Peter of the North.” (The nickname may be a nod to the porn star Peter North, which would be fitting given that Peter North the spammer promoted shady pharmacies whose main seller was male enhancement drugs).
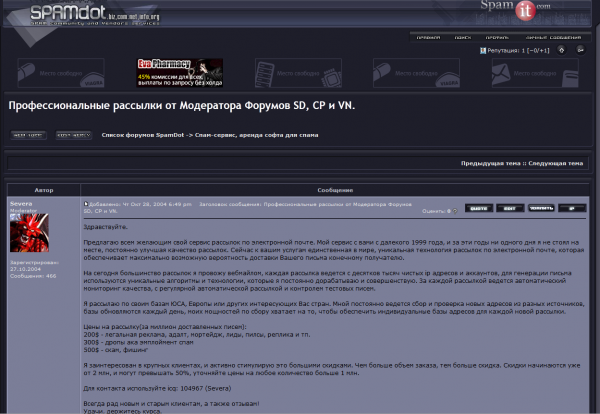
According to SpamIt records, Severa brought in revenues of $438,000 and earned commissions of $145,000 spamming rogue online pharmacy sites over a 3-year period. He also was a moderator of Spamdot.biz (pictured at right), a vetted-members-only forum that included many of SpamIt’s top earners, as well as successful spammers/malware writers from other affiliate programs such as EvaPharmacy and Mailien.
Severa seems to have made more money renting his botnet to other spammers. For $200, vetted users could hire his botnet to send 1 million pieces of spam; junk email campaigns touting employment/money mule scams cost $300 per million, and phishing emails could be blasted out through Severa’s botnet for the bargain price of $500 per million.
Spamhaus says Severa’s real name may be Peter Levashov. The information Severa himself provided to SpamIt suggests that Spamhaus’s intelligence is not far off the mark.
Severa had his SpamIt earnings deposited into an account at WebMoney, a virtual currency popular in Russia and Eastern Europe. According to a source that has the ability to look up identity information tied to WebMoney accounts, the account was established in 2001 by someone who entered a WebMoney office and presented the Russian passport #454345544. The passport bore the name of a then 26-year-old from Moscow — Viktor Sergeevich Ivashov.
SPAMDOT SECRETS
So where are the clues suggesting that Severa ran Waledac? Krebs On Security also managed to secure a copy of the Spamdot.biz forum, including the private messages for all of its users. On August 27, 2009, Severa sent a private message to a Spamdot.biz user named “ip-server.” Those communications show that the latter had sold Severa access to so-called “bulletproof hosting” services that would stand up to repeated abuse claims from other ISPs. The messages indicate that Severa transacted with ip-server to purchase dedicated servers used to control the operations of the Waledac botnet.
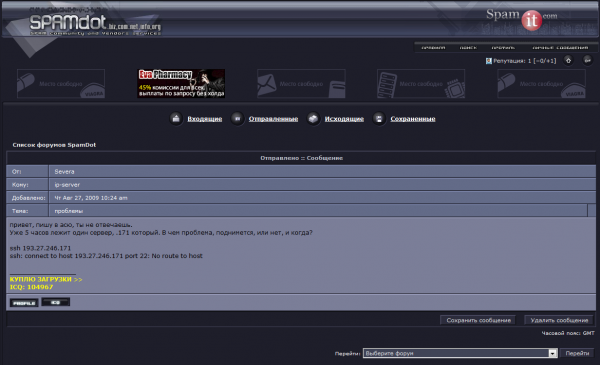 In the private message pictured in the screen shot to the left, Severa writes (translated from Russian):
In the private message pictured in the screen shot to the left, Severa writes (translated from Russian):
“Hello, writing to your ICQ, you are not responding. One of the servers has been down for 5 hours. The one ending on .171. What’s the problem, is it coming up or not, and when?”
ssh 193.27.246.171
ssh: connect to host 193.27.246.171 port 22: No route to host”
Ip-server must have resolved the outage, because the server that Severa was complaining about — 193.27.246.171 — would be flagged a day later by malware analysts, and tagged as a control server for the Waledac botnet.
There are clues that suggest a relationship between Severa and Kelihos that go beyond similarities in the code that powers the two botnets. Last summer, prior to Microsoft’s takedown of Kelihos, I wrote about another venture that Severa widely advertised on hacker forums: “Sevantivir,” an affiliate program that rewarded hackers for tricking people into installing and ultimately paying for fake antivirus software.
In that story, I cited research by French malware investigator and blogger Steven “Xylitol” K, who found that the installer program that Severa was giving to affiliates seeded infected PCs with both fake antivirus and a copy of Kelihos. From that story:
“Steven discovered that the malicious installer that Sevantivir affiliates were asked to distribute was designed to download two files. One was a fake AV program called Security Shield. The other was a spambot that blasts junk email pimping Canadian Pharmacy/Glavmed pill sites. The spambot is detected by Microsoft’s antivirus software as Win32.Kelihos.b. According to Microsoft, Kelihos.b shares large portions of its code with the Waledac worm, an infamous worm that for several years was synonymous with Canadian Pharmacy spam.”
It’s not clear what botnet infrastructure he is using now, but Severa is still the spam service administrator on several underground forums, pimping his spam services, remarkably under most of the same prices he offered them for in 2008.
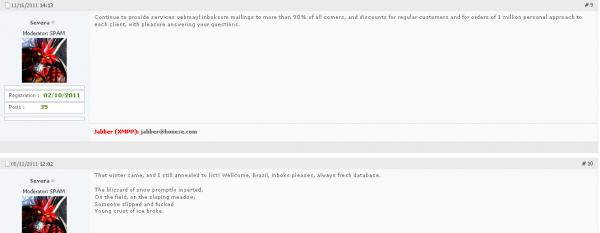
Contacted via instant message and presented with the evidence, Severa denied everything, saying he only did small opt-in mailings, had never used a botnet, and had been out of the business for years. When pressed about his fake antivirus affiliate program, Severa said he didn’t realize his antivirus program was fake, and that he didn’t know anyone named Sabelnikov, or even Ralsky. When presented with the screen shot below — which shows Severa complaining on Spamdot about how his broker ran away and that he was faced to find a new sponsor for spamming penny stocks just days after Ralsky’s arrest in Jan. 2008 — Severa said someone else must have been using his Spamdot account.
“The truth is that some people sharing servers, spamdot account and some other forum accounts [in] those years,” he explained. He gave the same reply when asked about the screen shot showing his renting the server used to control Waledac.
Kelihos may not be completely gone. Stone-Gross said he recently uncovered a malware sample that appears to be another installer for Kelihos.
“The guys running these botnets are making lots of money,” Stone-Gross said. “They’re not just going to sit back and say, ‘Oh no, they took down our botnet, let’s give up on our business.’ They’ll use pay-per-install affiliate programs to reinfect more machines and bring the botnet right back up.”





I am always amazed by the depth of your investigations. Good reading!
Thanks, Adam! Glad you liked it. The story took quite a while to put together.
I was stunned when the Russian authorities said they had no investigation ongoing and none planned after the detailed facebook koobface report was released. I wonder if there would be a similar comment regarding Peter Severa.
I think that article referenced the K Directorate. Which Russian department or authority is tasked with combating online crime, or would you characterize it as more of a case by case basis?
is it just me or do the nicknames read like a Harry Potter novel? 🙂
Awesome in depth investigating Brian. I hope Mr. Levashov is brought to justice.
Not only that, but after reading the text in the second post of the second last picture of the article it makes me wonder if he plucked that gem from one of the auto generated spam emails.
Brian. Might you write an article listing tactics, legal and maybe some not so much so, savvy users might use to attack this problem from below… savage it’s belly, so to speak. My gut tells me the main problem is that the cost to the crooks is insignificant compared with the benefits they reap. Perhaps there are ways we can make their costs more onerous. Burglars avoid houses that are occupied, have dogs, etc, because they can just walk right into the house next door and take what they want… no muss, no hassle.
Also, I know that when you speak of hundreds of thousands of infected PCs, “fixing” one or two is the proverbial drop in the bucket. HOWEVER, if every savvy user could help just two clueless friends and thereby get them off the botnets, cumulatively, we could make a helluva difference. Our mistake, IMO, has been to take the attitude that “the government” should take care of things. Truth is, that’s not happening while billions of dollars are being lost to crooks, often by those who can least afford those losses.
So, can we, literally a guerrilla army shooting from behind trees, do anything to make crime for these people pay less well?
The victim with the infected computer often has no real comprehension of how bad it is. The malware is designed to avoid calling attention to itself. Virus scans come up clean, the computer may be running better than it was before the trojan cleared out all its competitors’ programs, and none of the spam is bouncing back to the correct source. And people who choose to be ignorant of the harm their computers are doing to other people’s computers aren’t held to any consequences. They see no reason to change their sloppy internet habits.
The people who are interested in cleaning up the internet are too ethical to take control of a botnet and publish personal information harvested from the computers of the victims. But we’ve seen the criminals turn on each other and give that type of information to law enforcement. If one of them chose to disseminate lists of owners of infected computers or even lists of which customer purchased which erectile dysfunction drugs, it would do much more permanent harm to the other spammers by making people fearful of spending money on their websites.
> The victim with the infected computer often has no real comprehension of how bad it is. And people who choose to be ignorant of the harm their computers are doing to other people’s computers aren’t held to any consequences. They see no reason to change their sloppy internet habits.? The people who are interested in cleaning up the internet are too ethical to take control of a botnet and publish personal information harvested from the computers of the victims.<
I do not consider that "ethical" any more than publishing the names of hookers but not the johns is "ethical". What is sauce for the goose is sauce for the gander. If Internet slobs don't want to be outed, they should keep themselves above reproach. Otherwise, at least in my mind, they are fair game. They ARE just as complicit in the scams and hiding behind a shield of ignorance is no excuse.
Absolutely! I love it! Let the games begin . Now where the hell is wikileaks when you really need them 🙁
…so…tempting…at…times…
But no, it’s personal health information,. Victims often are sick and uninsured and have no idea that they aren’t dealing with legitimate pharmacies located in Canada. If they were aware of who they were dealing with, they wouldn’t pay with personal credit cards.
My first reply to AC was truncated. I do not know why. Also, I thought the “victims” referred to were those who have infected computers, not people who were defrauded. AC said people with sloppy Internet habits weren’t “held to any consequences”. Since most of them caught their virus on scuzzy websites, if they refuse to clean up their computers, publish THEIR names along with the websites they visited. They are the ones I said were “just as complicit in the scams” and are, therefore, fair game. My full response absolutely did not suggest attacking the people who were scammed.
“Since most of them caught their virus on scuzzy websites…”
Sorry, but that’s an extremely dated perspective on how malware spreads.
See for instance this 2009 InformationWeek article:
http://www.informationweek.com/news/internet/security/212901775
70 Of Top 100 Web Sites Spread Malware
“Advice to visit only legitimate Web sites appears to be meaningless as increasing numbers of mainstream sites contain known malicious code.
“Seventy percent of the top 100 Web sites either hosted malicious content or contained a link designed to redirect site visitors to a malicious Web site during the second half of 2008, claims Websense’s report State of Internet Security, Q3-Q4, 2008.”
Point well taken. I remember a long time ago when the computer world was all aghast at these new-fangled things called viruses. A study came out showing conclusively that the worst source of viruses was NOT the bulletin board you posted on, NOT the freeware you downloaded from aforementioned bulletin board, but UNOPENED, PLASTIC WRAPPED SOFTWARE you purchased at the local book store (they didn’t have computer stores back then). Second worst offender? Your friendly, neighborhood computer repair shop!!! They used diagnostic disks and guess what… said disks could get infected from the computers they were supposed to be diagnosing. Whoops.
Your post highlights the fact that the monitors of legit sites have gotten lazy. They assume it can’t happen to them… Wrong 🙁
I apologize for over-simplifying the situation. Nevertheless, it is still valid to assert that almost all scuzzy sites have hidden malware and that anyone who visits them is at risk for acquiring malware. So if they do, IMO, they deserve what they get.
I’m betting a good percentage of the people here spend part of their family visits removing malware from relatives’ computers. My nieces’ and nephews’ computers were a mess last time I saw them, because slime-ball malware creators use humorous memes to lure visitors to their sites, and because many parents think it isn’t necessary to pay for an up-to-date antivirus on kids’ computers because “there’s nothing important on them.” The victims’ attitude is that they are too obscure and their PCs too worthless to be interesting to the kinds of people who hack computers. They need a wake up call, but they don’t need their kids’ emails posted on Wikileaks.
Yo, AC – I like your heart 🙂 and
I’d agree if the year were 1949. I remember getting up with the Summer sunrise, going out on my fat tired, Columbia bike and riding up and down my street waiting for some other kids to wake up and come out to play. We’d stay out all day… till we heard our Mothers ring the cowbell to come home for dinner. But it’s not 1949.
Kids today know a great deal more than we “knowledgeable” adults give them credit for. My 4th grade GS knows more about the Internet than his Dad, not that he’d cop to that, lol. Plus, ALL kids have a special Spidey Sense about when things are hinky. Are there exceptions? Sure. But mostly not.
So when you clean up your niece’s computer, know that the sweet little darlin’ knew what she was doing when she did what she did AND WILL DO IT AGAIN. You can lecture her all you want but it won’t do any good. She is immortal and untouchable (aren’t we all till death hits too close to home to ignore?) and besides, Uncle can fix anything that’s wrong.
The bottom line is that they’ve already learned how to get into trouble. It is your job as a loving uncle to help them learn how to get out. And the best tool in your box is the universal fear pre-teeners and teenagers have of embarrassment. You let them suffer it, and then you show them how to avoid it. If you just rescue them, then you’re just a codependent. “Tough Love” isn’t always bad… just when the “love” part is missing.
lol, very true. My kids knew they weren’t supposed to be using Internet Explorer, but got pwned after a friend came over and wanted to show my daughter a funny video that just wouldn’t run on Mozilla.
But in most families, it’s not that type of one-time event. They’re always using IE, and they’re always executing Java, Javascript, Flash, the whole package. No one even knows it’s risky, because it’s the default setting for Windows. If there are no naked people, they probably don’t see it as doing anything really wrong, just goofing off. And the kids don’t connect the risky behavior to the malware. The first thing the trojans do is erase IE’s history, so you can’t tell what site infected you. It makes it hard to learn from experience.
So why not install Virtual Box and get them to surf the net from a Linux VM. Tell them to restore a clean snapshot after every session. In fact, why doesn’t everyone do that? Am I being naive here?
I’m not big on OUTING people, I don’t think publishing names will make a huge change. Not in my country, where drugs are cheap. Men here argue they should have every right to visit malware-laiden porn sites.
I think the best solution is to just stop their internet until the problem stops. If an ISP warns a person 3 times in 3 weeks to DO something about malware, and they don’t, then just don’t serve them internet. I don’t know how much clearer you can be to a person…
It would either cause a conscious shift in mentality for people to take responsibility for their computing, OR, would be a boon for IT shops.
We make people have licences to drive a car. While a computer has a hard time killing a person, malware has a huge detriment to the global economy and the current situation just isn’t working.
We’ll know our disinformation program is complete when everything the American public believes is false.– William Casey, CIA Director (from first staff meeting in 1981)
I’m not a Russian speaker but perhaps phishing emails are $500/million according to the screenshot Brian?
Another excellent article, thanks.
Let me guess, the next piece will be about icq 2020230?
that’s a good guess 🙂
My son is a “Geek” and fixes many PCs that are infected with this malware. Most of the time it’s so badly intrenched the only option is to wipe the drive and start from scratch.
It’s so easy to get infected we must constantly be on our guard.
This fucking spammer Severa – senator of Lampeduza.net
Fascinating articles.
BTW, Russian passport number you cite is wrong – Russia uses 4+6 (series+number) digit system for passports.
You can check whether given series and number correspond to a valid passport at http://services.fms.gov.ru/info-service.htm?sid=2000