The Wikimedia Foundation last week warned that readers who are seeing ads on Wikipedia articles are likely using a Web browser that has been infected with malware. The warning points to an apparent resurgence in adware and spyware that is being delivered via cleverly disguised browser extensions designed to run across multiple Web browsers and operating systems.
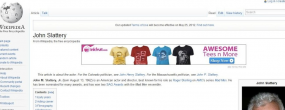
In a posting on its blog, Wikimedia noted that although the nonprofit organization is funded by more than a million donors and does not run ads, some users were complaining of seeing ads on Wikipedia entries. “If you’re seeing advertisements for a for-profit industry (see screenshot below for an example) or anything but our fundraiser, then your web browser has likely been infected with malware,” reads a blog post co-written by Philippe Beaudette, director of community advocacy at the Wikimedia Foundation.
The blog post named one example of a browser extension called “IWantThis!,” which is essentially spyware masquerading as adware. The description at the IWantThis! Web site makes it sound like a harmless plugin that occasionally overlays ads on third-party Web sites and helps users share product or online shopping wish lists with others. As I was researching this extension, I came across this helpful description of it at the DeleteMalware Blog, which points to the broad privacy policy that ships with this extension:
Examples of the information we may collect and analyze when you use our website include the IP address used to connect your computer to the Internet; login; e-mail address; password; computer and connection information such as browser type, version, and time zone setting, browser plug-in types and versions, operating system, and platform; the full Uniform Resource Locator (URL) clickstream to, through, and from the Site, including date and time; cookie; web pages you viewed or searched for; and the phone number you used to call us.
The author of that DeleteMalware post said he found a copy of the IWantThis browser extension bundled with freeware from software download sites (the author doesn’t mention which download site, but it’s worth mentioning again that sites like Download.com have recently begun bundling adware, toolbars and other potentially invasive software with otherwise “free” titles).
The Wikimedia blog post specifically mentions that this extension affects Google Chrome users, but the extension appears to be equally capable of installing across multiple browsers, including Mozilla Firefox and Internet Explorer. Last week, I wrote about LilyJade, a new computer worm that was spreading across Facebook accounts by abusing the free services offered by Crossrider, a platform that makes it simple to develop browser extensions that work seamlessly across browsers and operating systems.
In researching IWantThis, I spoke with Sergey Golovanov, a malware expert at Russian antivirus maker Kaspersky Lab, who pointed out that the IWantThis extension has been delivered via Crossrider since at least February of this year. This may or may not be linked to an affiliate program that rewards people with commissions for convincing people to install the software.This writeup from Symantec’s ThreatExpert malware scanning engine steps through some of the registry changes that the IWantThis extension executes on a host system.
It’s also worth noting that few — if any — antivirus firms are likely to alert users about malicious or invasive browser extensions. For example, none of the 43 antivirus and security applications used to conduct this scan of the IWantThis! extension at Virustotal.com flagged it as malicious, or even a potentially unwanted application.
Broken record alert: If you didn’t go looking for it, don’t install it!




IWantThis = 50 on Red (http://www.50onred.com/) = 215 Apps and Ads2Srv and International Web Services LLC (the ultimate generic scammy shell company name of course). Scumbags.
Brian/Andrea – how timely! I just removed Iwantthis from a client’s computer , also saw 215, and was wondering why Norton hadn’t caught this. Something new to look for!
Unfortunately this stuff is too easy to miss. To many users click next next next until it starts installing without reading a single screen.
Users need to learn to slow down and pay attention.
It would be interesting to see
an updated List of Browser extensions
“gone evil” = sudden adware, malware, etc.
Here’s a concrete example:
—> QuickDrag for Firefox.
It used to be a useful & great FF ext. ,
now suddenly “opts you in” to adware, etc.
See the comments
and the user rage:
https://addons.mozilla.org/en-US/firefox/addon/quickdrag/reviews/
SFdude
Mozilla has a strict “no surprises” policy (http://blog.mozilla.org/addons/2009/05/01/no-surprises/). So extensions reviewed by Mozilla (green install button on addons.mozilla.org) should be free of such issues. As you can see, QuickDrag has a yellow install button, probably for this very reason. This means that there will be no automatic updates and you should expect issues if you install manually. If that isn’t something you can accept – stick to add-ons with the “fully reviewed” note.
While I see the yellow button (really yellow striped button) on the addons site, the real problem is if you go through the add-ons tool in Firefox, you will NOT see the yellow button.
Robert, thx for the heads up on yellow button not being there in the add-ons tool. Oh, goodie!! Another step I have to take before installing an add-on.
Good point. I rarely use Add-ons Manager to install extensions so I didn’t notice. Yes, the lack of warning here is definitely an issue.
Thank you, Wladimir!.
That is truly useful info. to watch for,
before installing any FF ext.
Ext. [ Install button ] is:
Green = ok
– vs –
Yellow = “caveat emptor”.
btw:
I use your excellent AdBlock+ ext.
(of course!).
thks again,
SFdude
Looking at the output from Symantec’s ThreatExpert malware scanning engine – what was the add-on manipulating in the root certificates?
Which affiliate program are these adware authors using surely they must have a black hat affiliate program or are they cloaking white hat ads?
Cloaking is definitely rising rapidly in popularity. LilyJade appears designed for AdSense out of the box but can easily be altered. Other frequents include CPALead, Adscend Media, WhiteFire, Leadbolt, BlamAds/EWA, 007CPA and others in that realm.
Looking into this a bit more deeply, it’s kind of old news. The site to get the extension still seems to be up, but all my attempts to actually download the software (in a VM using IE7) failed. The virus total link is to a different progam based on the md5sum than the Symantec’s ThreatExpert link. (Here’s the real virustotal scan: https://www.virustotal.com/file/7c0fdf3175480557c5e3266faaa2b508b8083201ac0e6140915f993ed092ec7c/analysis/). The last virus total scan was done in Feb 14, 2012, and then 3 engines picked it up, not zero. Since I couldn’t find a place to download it, I couldn’t get virustotal to update the results, but it’s likely almost every AV should pick up on it today.
Use a hosts file and block the ad’s from ever showing up, thats what I do, and I never have any ad’s pop-up, and if they do, they’re usually blank. When I start noticing ad’s, I go back to the site below and get the latest hosts file.
I have used this web site for years to obtain an up-to-date hosts file – http://winhelp2002.mvps.org/hosts.htm
It takes a few minutes to setup, and all the instructions are there… people need to educate themselves on the alternative to Norton, and all the antivirus softwares that don’t really protect you from spybots, adware, etc.
Spybot Search and Destory, and SpywareBlaster are two softwares to use to protect yourselves as well. And they’re free!