It’s getting harder to detect some of the newer ATM skimmers, fraud devices attached to or inserted into cash machines and designed to steal card and PIN data. Among the latest and most difficult-to-spot skimmer innovations is a wafer-thin card reading device that can be inserted directly into the ATM’s card acceptance slot.
That’s according to two recent reports from the European ATM Security Team (EAST), an organization that collects ATM fraud reports from countries in the region. In both reports, EAST said one country (it isn’t naming which) alerted them about a new form of skimming device that is thin enough to be inserted directly into the card reader slot. These devices record the data stored on the magnetic stripe on the back of the card as it is slid into a compromised ATM.
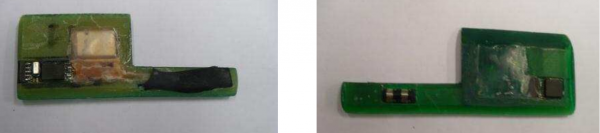
Another EAST report released this week indicates that these insert skimmers are continuing to evolve. Below are two more such devices. Insert skimmers require some secondary component to record customers entering their PINs, such as a PIN pad overlay or hidden camera.

Both of these insert skimmers were designed to be shoved directly into the throat of the card acceptance slot. Credit: EAST.
If you notice something strange about an ATM, don’t use it, and alert the institution responsible for the machine. And if you’re calm and cool enough to remember to snap a picture of the potentially compromised ATM, please send it my way!
This piece is part of an ongoing series about innovations in ATM skimming devices. If you liked this entry, check out the archive — All About Skimmers.




The skimmers in Asia went 1-up by inserting pin-hole cameras to record the PIN number of the cards being skimmed. Picture and report here: http://www.asiaone.com/News/Latest+News/Singapore/Story/A1Story20120113-321738.html
Andrew those cases are also known in Malaysia especially Kuala Lumpur, Johor, and Penang.
In Malaysia similar cases and social engineering has also been on the rise. below link for pictures and info
https://www.facebook.com/photo.php?fbid=10151018602334040&set=a.10151018590969040.452269.283232114039&type=1&theater
Your asking for a picture if we see something amiss gave me an idea. How about if the banks publish a picture of what the ATM *should* look like RIGHT NEXT TO IT. And if it doesn’t look like the picture contact them asap and don’t use it. The picture would have to be protected behind plexiglass but at least it might slow the thieves down …a bit? I guess if it was after hours you’d contact the police …?
Thanks for another great article. Hope you get to take vacation soon, Lindy
Good idea although I can see the crooks placing a “legit” picture with skimmer included … maybe a LCD screen would be a better idea.
(Yeah I know they’ll just put an out of order sign on it but hey … it’s an interesting idea nonetheless).
I used an an ATM last week that was on the wall of a bank, it was a group of four.
They all had stickers on them saying “anti-fraud devices are installed”
Only one of the machines actually had an anti-skimmer device (that actually looks like a skimmer) the rest where just bare.
How do they expect customers to know which machines are safe and which are not when they’re not consistent.
Of course the truly clever crook would have posted those stickers: “Anti-fraud device installed” and then placed skimmers in a slot or two.
Some banks already do this. I have seen this on some newer ATMs. I think they were Wells Fargo machines, but I can’t say for sure.
After a giant skimming wave in the Netherlands, most of the Dutch ATM’s show pictures to describe what the slot should look like.
Although when it comes to this stuff, I am technologically challenged, does not the ATM card reader “know” when something has been inserted in it? When I place a card in it, I do not have to push any buttons to start the transaction. The little screen lights up and asks what I want to do. So if the reader “knows” something is in it, why can it not be programed to eject the something after five minutes? That is long enough to conduct a transaction and even if one were to take too long, a customer can just start a new transaction by reinserting the card. However, a scammer cannot stand there, reinserting his/her skimmer.
At the very least, the machine could be programmed to shut down completely if in any time frame, up to say 1 hour ago, the number of “inserts” in a reader did not equal the number of “ejects”. Could that not be done?
It would seem to me that these new, thinner skimmers occupy just the part of the card slot near the opening. That is so they can scan the entire mag stripe as it passes by as it is inserted. The auto-react feature of the ATM is activated when the card is entirely inserted.
Could ATM manufacturers foil these skimmers by making the card slot so thin/narrow that only a card could be inserted, with no extra room for anything else?
The ATMs at BofA eject the card before asking for the pin, so I don’t see how one of these would work. Wouldn’t the skimmer get ejected?
That can’t work, the PIN is needed to unlock the smartcard on the card to authenticate the user.
Not a smart card, just a debit card. I don’t think BofA uses smart cards.
wiredog, it was a EURO report they use smart cards there 😉
These devices record the data stored on the magnetic stripe on the back of the card as it is slid into a compromised ATM.
Which indicates that these are US style ATMs, not the (almost as vulnerable) chip and pin systems.
Not necessarily. Even in countries that have chip and pin ATMs mostly deployed, the cards will still have a mag stripe. The issue is backwards compatibility for use in countries that don’t have chip and PIN. Interestingly, this fallback feature is the biggest source of fraud for European bank card holders, because the fraudsters can still steal the card info, PIN and counterfeit cards for use in the US.
Does it mean that if I have chip&pin card, and want to use chip&pin ATMs and readers only, I can “erase” the magnetic stripe on my card and it will still work in chip&pin devices? And at the same time it could not be copied?
Yes, if you “erase” the mag stripe on a smart card, it cannot be skimmed. But erasing it may be difficult, depending on the technology. Simply rubbing a magnet on the stripe is not a guarantee that you will successfully erase it. And just making the signal “too weak” with a magnet might mean a real ATM would reject it for not being 100% perfect, but there might still be enough signal left for a skimmer to pick up.
A sure-fire way I use for lab testing of mag stripe card readers is to scratch off the mag stripe in an area big enough to cause a read fault. I normally scratch off only one track at a time in order to test that readers and software properly handle just the unscratched track, but for your purposes you want to render all the tracks unreadable.
Here’s how to do it: hold the card so you are facing the mag stripe, with the mag stripe nearest the top edge. Scratch off about 1/4″ (7mm) of the stripe, starting from about 1/8″ (3mm) from the right hand edge of the card to about 3/8″ (10mm) from the right hand edge. Scratch all the way through the magnetic media down to the base plastic of the card (you will see a color change), and clear the entire area from the top of the stripe to the bottom of the stripe.
No skimmer in the world will recover your account number from that. If you also want to ensure they can’t even recover partial data, scratch off a wider area. Removing a full inch (25mm) will prevent even a partial success.
Reading your instructions John D, reminded me of how I used to obliterate old credit cards before cutting them up – in the old days before shredders were available. That is probably a good practice even if you use a shredder!!
Thanks for that post!
As European, I can confirm this.
In some European countries we have chip-pin and magnetic stripe on the same card (because not all European countries have already implemented the chip system. So we need both systems if we travel between countries)
Some months ago, I saw a person who failed twice putting his pin in the POS of the supermarket. In order to avoid the inactivation of the card (and obviously to pay the shopping) the “check out operator” finally used the magnetic stripe of the card and the customer signed the ticket.
The last system I´ve read about is the contactless cards. But, with this cards, IF you pay anything less than €20 (about $24) you only have to put the card close to the POS terminal ¡¡¡But you don´t need to put your pin!!!. Personally, I think this system is a backwards step.
Regards
Not to smart of a card is it
If my BofA debit card was truely a smartcard, _it_ would be able to detect a SITM (skimmer-in-the-middle)! 😀
If my card was truly smart, it would know that I shouldn’t be using the ATM in the first place. “No good can come of this. Transaction rejected!”
Who has time to stand in line inside a bank? Granted, I use a cash-back credit card for 95% of my transactions. There are some cases where cash still rules, however. Can’t charge a lotto ticket on a credit card.
Are you still using your mattress cash dispenser -B? 😉
>> Who has time to stand in line inside a bank?
This is more or less off-topic but I thought I’d tell how it is in the Land Downunder (Australia):
Australia has 4 “majors”: banks that have been in existence for many decades or longer and have long been considered amongst the best managed in the world as far as banks go, especially in todays climate.
Of course at one time this couldn’t be said of their treatment of Joe Blow customers – they *used* to be godawful as far as hopeless customer service, truly excessive fees for transaction accounts and we’re generally looked upon with disdain by much of the population (not including shareholders LOL).
However in the 80’s (?) from memory banking laws wen’t through reforms that allowed many more players to enter the market and for a long time the many credit unions and building societies etc offered far better service and fee structures.
However about 5 years ago all the major’s apparently suddenly realised this could be a real problem, people we’re leaving in droves – and you know what: they really pulled their finger out of their proverbials and did something about it.
The result is that (at least for me) I love my major bank I use now: queues to get to a teller are almost non-existent (the manager comes out of her office at my local branch to serve people!) and I pay nothing (nada, zip, zilch) for my personal transaction + high interest savings combination (This is NAB I’m talking about for any curious Aussies). The old Credit Union is not even close.
So yeah, tl;dr: sometimes competition works and large banks can actually do a decent job (provided they’re frightened of losing money) … I’m not a “free market” zealot or anything but that’s how I see it.
I like my association; they have a deal you no canna refuse! Plus WE own it!
It’s difficult to determine from the photos just how a card (complete with onboard chips and probably power supply) could fit, along with a swipe card, within such a thin slot. The ATM’s which I’m aware of seem to have sufficient room for a card, and some additional clearance.
Instead of a fixed PIN, what about rotating PIN, kinda like an RSA token, but provided by a mobile app such as Google Authenticator (which has an open API, so it can be used by non-Google related services). The app could actually be Google Authenticator for user convenience, or it could be a VISA or MasterCard issued mobile app. Long term, seems like NFC, which provides a dynamic data stream is the way to avoid the problem. Even if that stream is captured by an NFC skimmer, in short order, seconds or minutes, it would become invalid for future transactions.
Actually, the real solution is for American banks to stop using the antiquated mag stripe authentication. Every other developed country (except for maybe Canada as they rely on American tourism dollars) have chip & pin. The only reason skimming still exists is because we have to have mag stripes for compatibility with American banks and American payment systems.
I can’t see it changing any time soon though, America are still using the imperial system!
Chip & Pin actually provides little additional security (it was developed by the low bidder every step of the way) and only serves to transfer the risk from the bank to the cardholder.
I disagree. I don’t know the specific implementation details for the chip-and-pin that they are using in Europe, but with some of the smartcards that I have used in past, the card itself has a small crypto processor, and the card itself can generate an RSA keypair. You can ask the card for the public key, but you can *never* download the private key.
It really depends on the technology behind the chip card. There are a few different types out there. The most promising one I’ve seen is from First Data/Star. There EVM cards in the original designee was that every time you slide your card the chip create a one time card number that can only be used for this one transaction. The card network would know how to decrypt this number and assign the transaction to you. No decryption would be done at the terminal. The plan was also to do away with the mag strip. This was announced late 2010. Since the plan has change a great deal do to merchant complaints about cost of buying EVM card readers.
Now you will have the same deal as Europe with mag strips and EVM chips for many years while there is a slow integration of card readers that can read both. The current plan is by 2015 if a merchant has not upgraded to an EVM capable reader that if there is a fraudulent transaction that originated from their terminal the will have to refund the transaction. So your are probably looking at some time in the next decade before there are no more mag strip cards. By that time EVM will most likely have the same problems as current debit cards.
Sorry, but Canada has had Chip & Pin for many years. That being said, the my last non-chip card got replaced with a chip card yesterday – it was an American Express.
The right fix for this is what the banks have been trying to avoid for years: use public key encryption with a CPU on the card, so that the MiTM attack doesn’t get any useful information. Even the “chip and pin” systems in Europe are completely vulnerable to MiTM attacks, unfortunately—their highly-touted security really just raises the bar slightly, and doesn’t actually prevent such attacks.
RFID for ATMs instead of swipe? The CVV is different for each transaction, can only be used once, and each CVV must be used in order. I have yet to see an RFID equipped ATM or gas station.
Mobil used to use RFID tags … Speed Pass I think it was called. I believe they still do use them.
… and Citizens Bank uses RFID on their ATMs/cards … I’ve never used them, only seen them.
If ever you do, I advise getting a shielded card case for it, so every Tom, Dick, and Harry RF source you pass doesn’t try to crack the card.
Chris, contactless cards, either RFID or NFC, solve a different problem: that of dirty readers or dirty cards. Radio has no electrical contacts to corrode, so the readers are much more durable, and cost less to maintain, and radio doesn’t require mechanical alignment like electrical contacts do. But NFC by itself does nothing to improve security, and some of the current implementations actually weaken it tremendously by transmitting raw card data in the clear.
Part of the most effective solution is strong asymmetric encryption performed on the card that only the issuing bank can decrypt (public key crypto.) EMV is kind of close, but because it tried to be all things to all people, the protocol ended up with some flaws. But until the consumer’s cards start coming with their own built in PIN pads and displays, there will always be the risk of fraudulent card readers and skimmers.
I still say Passwindow combined with Magneprint is the cheap reliable way to go; but I like what you write about RF tech done right.
The beautiful thing about Magneprint is it actually takes those weaknesses you list about the old technology and turn it into a strength using mathematical/geometric stoichiometry. It would be impossible to replay a swipe or copy a card with this technology.
So there’s “EAST” – is there a United States version of this type of information? Or any other good high/mid level info about ATM/financial fraud events – not counting your own website, of course 🙂
I did a school presentation that touched upon these devices. One of my classmates was a bank teller who said the bank would make them physically check the ATM daily for these devices. To me, this seems like the best proactive measure a bank can take instead of hoping the customer knows what to look for.
Yes please ! Banks should be proactive regarding this issue …
… instead of waiting for customers to become fraud victims.
Not too difficult to scan the ATM machine or physically check it
at regular intervals.
This was what I got when I tried to vote:
Error: Possible CSRF attack, Comment Rating not changed.
I guess there was no voting then! Is this what happens when your site is under attack? I couldn’t come back until now.
JCitizen – I used to get this error all the time when attempting to vote. I informed Brian, but it just kept happening. Enabling the “Send Referrer Information” option in my (Opera) browser settings eventually resolved the problem. Depending on your browser, your mileage may vary.
Referrers on ad-block off and it works for me. Try clearing your cache too
Thanks TJ and Dave;
I keep adblock off when using Mozilla, while on Brian’s site, otherwise I don’t block using Dragon. I’ll try running CCleaner next time. Thanks.
I did think it curious I couldn’t reach this site for over 8 hours after that though – I assumed his site was under another DDOS.
I couldnt’ get here yesterday morning either.
I’m wondering why these ATM manufacturers would not think of a very simple way of detecting ATM skimming fraud by just simply logging the use of the “CANCEL” button if it was used maliciously prior to ATM pin entry.
If you are a ATM Skimmer, what is the first thing that you would do after you installed a ATM Skimming Device? Of course you should test the alignment of the ATM Skimming device if it is aligned with the card slot such that the card would not be jammed, otherwise your ATM skimming activity would be a flap if everytime you insert an ATM card it always gets jammed due to misaligned slots.
This is where the logging of the “CANCEL” button comes in to play (if used maliciously) since fraudsters always insert a ATM card just to test the alignment of the card slot then they immediately press the “CANCEL” button to eject the card ones everything is in order before leaving the site.
If only the logging of the CANCEL botton prior to entering a PIN is available on most ATM brands and the bank is alerted everytime there is a malicious use of the “CANCEL” button activity , then the bank can verify and respond immediately.
“High Tech preventive controls are costly to implement but simple detective controls is a must”.
These ATM skimmer posts are of little value to us, as it is a cat and mouse game and the average ATM user wouldn’t notice a compromised system even if they knew what to look for.
More helpful would be information (statistics) on what ATM’s are mostly likely to be compromised, and general security best practices consumers can take to avoid the machines.
Again, showing photos of skimmers is interesting to a very small subset of readers, and useless info to the rest.
Because some of us operational security folk like to be aware of them because we have a pocket full of plastic?
All these simply work on the basic premise that it is after all man made technology. So, when the technology advances to make things more efficient and convenient, it also paves way for problems. Whatever checks and controls put in place, the hackers come back with newer ways to overcome those.
That means that continuous monitoring and acting on triggers and alarms is the key to keep these frauds away. It is not some thing banks can fix it once, they need to have a highly active and capable security monitoring team and should not ignore vulnerability or exploit reports that comes out from ethical hackers.