One of the challenges in malware research is separating the truly novel innovations in malcoding from new nasties that merely include nominal or superficial tweaks. This dynamic holds true for both malware researchers and purveyors, albeit for different reasons. Researchers wish to avoid being labeled alarmist in calling special attention to what appears to be an emerging threat that turns out to be old news; the bad guys just want to avoid getting scammed into paying for an old malware kit dressed up as the new next big thing.
On Tuesday, RSA Security somewhat breathlessly announced that it had spotted KINS, a ZeuS Trojan variant that looked like “a new professional-grade banking Trojan” that was likely to emerge as the “next Trojan epiphany” in the cybercrime underground. RSA said the emergence of KINS was notable because the reigning ZeuS Trojan derivative – the Citadel Trojan — had long ago been taken off the market, and that crooks were anxiously awaiting the development and sale of a new botnet creation kit based on the leaked ZeuS source code.
“Since December 2012, when the spokesperson of the Citadel team took the Trojan off the semi-open underground market, cyber criminals have been scrambling to find a replacement,” RSA’s Limor Kessem wrote. “In early February 2013, RSA fraud intelligence researchers began tracing hints about a new crimeware tool called ‘KINS’. At the time, the information about the Trojan just a rumor, but in sporadic comments, fraudsters were associating a Trojan named KINS with the Citadel source code, looking for its developer in order to reach out to him and purchase KINS. The rumors were soon hushed and ties to Citadel were denied, mostly in what appeared as a case of fearful fraudsters who did not want to be denied the possibility to buy the next Trojan.”
But according to Fox-IT, a security research and consulting group based in The Netherlands, KINS has been used in private since at least December 2011 to attack financial institutions in Europe, specifically Germany and The Netherlands. Fox-IT says KINS is short for “Kasper Internet Non-Security,” which is likely the malware author’s not-so-subtle dig at the security suite offered by Russian antivirus maker Kaspersky.
In its own analysis of the banking Trojan malware, Fox-IT said KINS is fully based on the leaked ZeuS source code, and includes only minor additions. What’s more, Fox-IT notes, many of the users of KINS have already migrated to yet another ZeuS variant, suggesting that perhaps they were unsatisfied with the product and that it didn’t deliver as advertised.
“While the technical additions are interesting, they are far from ground breaking,” wrote Michael Sandee, principal security expert at Fox-IT. “With an array of fairly standard features, and relatively simple additions to the standard ZeuS, such as reporting of installed security product information, the malware platform does not bring anything really new. There are however some features of this malware, not aimed at the functionality for the person using it, but aimed at complicating malware analysis.”
OLD MALWARE, NEW PAINTJOB?
From the bad-guy perspective, this infighting over malware innovation is on display in a new malware offering that surfaced today on a semi-private forum: The seller is pitching a resurrected and modified version of the DNSChanger Trojan, a global contagion that once infected millions of PCs. The DNSChanger botnet, which hooked into infected systems quite deeply and spread to both Windows and Mac computers, was eradicated only by a worldwide, concerted digital quarantine and vaccination effort — combined with the arrest of its creators.
As its name suggests, DNSChanger works by hijacking the domain name system (DNS) server settings on a computer; these settings point to Internet servers that are responsible for translating human-friendly domain names like example.com into numeric Internet addresses that are easier for computers to understand. DNS Changer swapped out victims’ legitimate DNS server settings with the addresses of DNS Servers controlled the malware’s creators. Armed with that control, the defendants could redirect any part of the Web browsing session on an infected user’s computer.
The original DNSChanger was used to conduct click fraud and to steal advertising revenues. This new version, dubbed Trend DNSChanger Bot, also hijacks the host machine’s DNS settings but with the purpose of extracting a ransomware payment from the victim. Ransomware locks the victim’s PC until he either pays the ransom or finds a way to remove the malware. Victims are instructed to pay the ransom by purchasing prepaid MoneyPak, PaySafe or Ukash cards, sold at everything from Walgreens to Wal-Mart. Victims are then told to send the attackers a 14-digit voucher code that allows the bad guys to redeem those vouchers for cash.
The author of Trend DNSChanger Bot claims his malware includes the best of its predecessor — including a powerful rootkit designed to make the code difficult to detect and remove — as well as the blocking of any Internet traffic between the host machine and antivirus and security vendors. The twist, according to the author, is in how it seeks to monetize hacked PCs.
Ransomware is most often distributed via hacked or malicious sites that exploit browser vulnerabilities. Typically, these scams impersonate the Department of Homeland Security or the FBI (or the equivalent federal investigative authority in the victim’s country) and try to frighten people into paying fines to avoid prosecution for supposedly downloading child pornography and pirated content.
The maker of Trend DNSChanger bot says his malware will invoke messaging from the victim’s own Internet service provider, warning of illicit activity and demanding fines for alleged infractions of the ISP’s terms of service.
“We made it so that it locks the [victim’s browser] to display a page [that mimics] major and medium-sized ISPs in each country in which you work. Imagine a user…seeing a message that their computer is locked, with the logos of its Internet service provider, the name of the provider, and the city in which [the victim] lives. According to our tests, it is very scary and makes them pay.”
It’s not clear whether this purportedly new version of DNSChanger will be embraced by the underground, or indeed will ever come close to inflicting the damage done by its predecessor. For now, the underground community appears interested but skeptical. Several members of the fraud forum where this malware is being sold say it bears strong resemblance to a project announced to great fanfare in 2012, only to be abandoned by its author.
Interestingly, the author of this upstart DNSChanger clone says he was part of the team that coded the original DNSChanger malware, but allows that his innovations are essentially incremental and that parts of his malware first emerged in the above-mentioned KINS Trojan. “In fact, we are not the first who came up with this technology,” the malware author “Trend” wrote. “It was first used in the KINS Trojan. Our team worked on DNSChanger, which is known throughout the world. But this project is only the official version that appeared in 2007. So the technology itself is not new.”



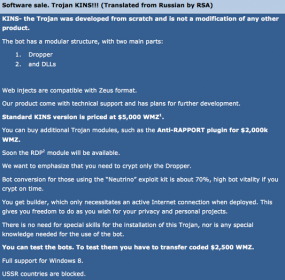


“Fox-IT says KINS is short for “Kasper Internet Non-Security,” which is likely the malware author’s not-so-subtle dig at the security suite offered by Russian antivirus maker Kaspersky.”
F-Secure wrote in “It’s Signed, therefore it’s Clean, right?” regarding forged certificates that the:
Simplest trick is to copy signature fields from clean files
– Usually from Microsoft or well known security companies
– Kaspersky and Symantec seem to be very popular for some reason
http://www.f-secure.com/weblog/archives/Jarno_Niemela_its_signed.pdf
Follow the money … shouldn’t be all that hard for the Feds. I’d be surprised if the crooks didn’t leave some sort of traceable evidence when redeeming a couple dozen Wal* vouchers for cash. Even if they use TOR or whatever, after a long day of botnetting, vodka and zakuski, they are bound to trip up once in a while, get greedy, and click before they think.
As far as I know, Mac is not affected by this. Is that correct?
Jaime — Not affected by what? My story was talking about the old version of DNS Changer, which very much did infect Macs (and routers). I haven’t seen any code from this claimed new version of DNSChanger, but it may have that same capability (although the author didn’t say that).
Thanks for your reply, Brian. I appreciate it. Now I got it. 🙂
http://www.youtube.com/watch?v=QOq6YMdhv6c
lolz krebs and to by Zeus! KINS is Ghosts for Kids
I see that reading comprehension is still a challenge for certain trollish visitors. What’s the point of that very long and boring video, anyway? Yes, it shows an icon with my likeness on it, and some dude refreshing his lame ZeuS panel incessantly to see if he has any new victims (tl;dw – he doesn’t).
Man gets fake FBI child porn alert, arrested for child porn
A man is fooled by an Internet virus into going to a police station to pay a fine for child pornography. He gives the police his computer to examine. They allegedly find child pornography on it.
who saying hackers dont do good things .?
got it from http://news.cnet.com/8301-17852_3-57595811-71/man-gets-fake-fbi-child-porn-alert-arrested-for-child-porn/
Made my day. Thanks