As documented time and again on this blog, cybercrooks are often sloppy or lazy enough to leave behind important clues about who and where they are. But from time to time, cheeky crooks will dream up a trap designed to look like they’re being sloppy when in fact they’re trying to trick security researchers into being sloppy and infecting their computers with malware.
According to Peter Kruse, a partner and cybercrime specialist with CSIS Security Group, that’s what happened late last month when a Twitter user “Paunchbighecker” started messaging security researchers on Twitter. Paunch the nickname of a Russian hacker who for the past few years has sold the wildly popular Blackhole exploit kit, a crimeware package designed to be stitched into hacked or malicious sites and foist browser exploits on visitors. The person behind Paunchbighecker Twitter account probably figured that invoking Paunch’s name and reputation would add to the allure of his scam.
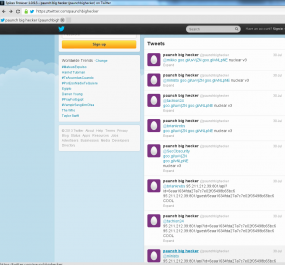
The Paunchbighecker Twitter account appears to have been created on July 30 for the sole purpose of sending tweets to several security researchers, including this author, Mikko Hypponen of Finnish security firm F-Secure, French malware researcher Kafeine, Polish security researcher tachion24, and SecObsecurity. Strangely enough, the other Twitter account that received messages from this user belongs to Sauli Niinistö, the current president of Finland.
The link that Paunchbighecker sent to researchers displays what appears to be the back-end administrative panel for a Nuclear Pack exploit kit. In fact, the landing page was a fake merely made to look like a Nuclear pack statistics panel. Rather, embedded inside the page itself is a series of active Java exploits.
Update, 1:56 p.m.: Security researcher Kafeine said he does not believe this was an attack against security researchers, but rather an intentional leak of badguy credentials. Furthermore, Kafeine notes that visitors to the site link in the Twitter messages would have to take an additional step in order to infect their own computers.
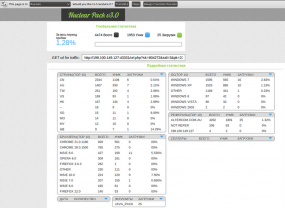
 Original story: Looking at a Virustotal automated analysis of the malware pushed by this exploit kit, it seems the hackers behind this ruse were trying to foist the ZeuS Trojan on unsuspecting (and unpatched) visitors. A separate Virustotal analysis shows that some components of this attack may have been very poorly detected by antivirus tools, if any of the recipients were incautious enough to have clicked through to the fake panel. Also, many of the domains used in this malware attack have long been associated with ZeuS Trojan activity. According to a reverse WHOIS lookup ordered from domaintools.com, the email address has been used to register more than 1,100 domains (CSV), including a large number with a very colorful history.
Original story: Looking at a Virustotal automated analysis of the malware pushed by this exploit kit, it seems the hackers behind this ruse were trying to foist the ZeuS Trojan on unsuspecting (and unpatched) visitors. A separate Virustotal analysis shows that some components of this attack may have been very poorly detected by antivirus tools, if any of the recipients were incautious enough to have clicked through to the fake panel. Also, many of the domains used in this malware attack have long been associated with ZeuS Trojan activity. According to a reverse WHOIS lookup ordered from domaintools.com, the email address has been used to register more than 1,100 domains (CSV), including a large number with a very colorful history.
Assuming this is a trap, it would not be the first time malware purveyors have sought to trick security researchers with fake exploit pack administration panels. In 2010, noted botnet researcher Brett Stone-Gross wrote about another Zeus Trojan attack that hid behind a phony administrative exploit kit panel with fake victim statistics.




“In fact, the landing page was a fake merely made to look like a Nuclear pack statistics panel. Rather, embedded inside the page itself is a series of active Java exploits from what appears to be the Sweet Orange exploit kit.”
I disagree. This was a leak of Customer credentials.
4 links :
1 thread link to NP and associated Stats
same for Cool EK…
The stats were not infected…obviously and per nature, the “thread links” were.
What Kafeine said.
I’ve a dump of these statistic pages and they weren’t infected with Sweet Orange.
the landing pages was working well and really delivered Reveton and Zeus.
http://www.youtube.com/watch?v=BitCYj2GExE
http://www.youtube.com/watch?v=6RFHMEZTA1k
In my blog rotation, this site comes after browsing yours, Xylitol.
Your content is delicious and informative. Please continue.
Right.. just following the breadcrumbs myself. So, the VT report shows a phone home to a server on 195.22.26.231, according to Shadowserver this is some sort of C&C server.
Brian’s CSV list is a list of those domains on that server. Very, very few of those domains are flagged as malicious which is odd. Some are nonsense domains (DGA perhaps), so are rather more pointed (e.g. kasperskygayformula.biz). Some are expired domains that heve been re-registered. Some of the domains in the list have expired and have been registered by other parties.
There’s a cluster of IPs that have these apparent C&C domains:
195.22.26.231
195.22.26.232
195.22.26.235
195.22.26.236
195.22.26.248
OK. So I was willing to say that this was a little evil cluster of C&C domains, but then I drilled into the WHOIS details of one (I won’t mention which in a public forum because it identifies an individual) and the WHOIS details were.. interesting. A little alarm bell went, and I went right back to looking at the DomainTools entry for 195.22.26.231 – http://whois.domaintools.com/195.22.26.231
Check the hostname.. it is anubisnetworks.com. These IPs actually appear to be sinkholes operated by Anubis Networks (a Portuguese IT security firm). Somebody at Anubis has pre-registered these domains and is pointing them to a harmless server.. and all you list actually does is list domains that are currently (or have previously) been sinkholed by Anubis.
It’s a bit odd that the VT report mentioned should be pointing to a sinkhole domain, but perhaps it was live at the time the malware link was pushed and it was sinkholed shortly afterwards?
Google find:
virustracker[dot]info/text/Ramnit_Domains[dot]txt (domains sinkholed by anubisnetworks[dot]com]
Brian why have you not given any comments on the shutdown of Lavabit? It seems like there Is no privacy left. Should we all stop using services connected with USA?
He’s right Brian, what is your take on this? Also, when is that kickstarter film going to appear?
thanks
the link is not infected right? so yo have to make a click in the panel to infect your pc ?
No. You couldn’t be infected via the Panel which were REAL clean panel.
There was another link which was a “Thread link” associated to the stats (in those case it was Rotators).
This kind of link is given to “traffer” (people who bring victims to the exploit kit) to be incorporated in “iframe” (this allow full rotation (domain + landing) with a static link
That link was not infected. But the URL you could see written in the page of the rotator was intrinsically infected.
Btw once infected (on purpose) you could see the result in the associated panel (many people play with it in Virtual Machine and the % of infection even reach 36% …which is something you never see live)
Were you infected? or your friends?
I’ve long suspected this, as have many readers here. It always makes interesting honeypot work.