A federal judge has denied bail for Ross Ulbricht, the 29-year-old man arrested last month on suspicion of running the Silk Road, an online black market that offered everything from drugs and guns to computer hackers and hitmen for hire.
The decision came after federal prosecutors in New York dumped a virtual truckload of additional incriminating evidence supporting charges that Ulbricht was the infamous Silk Road administrator known as the “Dread Pirate Roberts” (DPR), and that he was indeed a strong flight risk. To top it off, the government also now alleges that Ulbricht orchestrated and paid for murder-for-hire schemes targeting six individuals (until today, Ulbricht was accused of plotting just two of these executions).
The documents released today indicate that Ulbricht was a likely flight risk; they allege that prior to his arrest, Ulbricht had researched how to buy a citizenship in Dominica. The government said that the laptop seized from Ulbricht contained reference guides for obtaining “economic citizenship” in other countries. “In particular, the computer contained an application completed by Ulbricht for citizenship in Dominica, along with reference materials explaining that Dominica’s ‘economic citizenship’ program offers ‘instant’ citizenship in exchange for a one-time ‘$75,000 donation’ to the country’s government,'”, the government’s bail submission (PDF) notes. A copy of the application for citizenship in Dominica allegedly found on Ulbricht’s laptop is here (PDF).
In addition, prosecutors unveiled a photo showing the assortment of fake IDs that Ulbricht had allegedly ordered off the Silk Road (see image above), which included identity documents bearing his picture and various pseudonyms in Australia, Canada, and the United Kingdom, among other places.
According to the Justice Department, evidence from Ulbricht’s computer also shows that he had contemplated and prepared for a life on the run.
“For example, one file found on the computer, labeled ’emergency,’ contains a list of apparent to-do items in the event that Ulbricht learned that law enforcement was closing in on him. It reads as follows:
encrypt and backup important files on laptop to memory stick:
destroy laptop hard drive and hide/dispose
destroy phone and hide/dispose
Hide memory stick
get new laptop
go to end of train
find place to live on craigslist for cash
create new identity (name, backstory)”
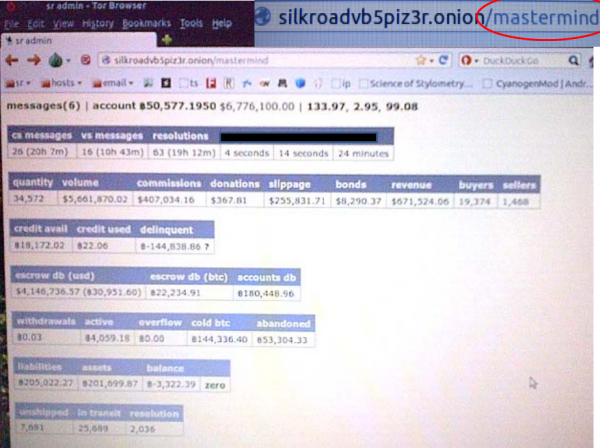
The prosecution also released several screenshots of Ulbricht’s computer as it was found when he was arrested at a San Francisco public library. According to investigators, Ulbricht was logged in to the Silk Road and was administering the site when he was apprehended, as indicated by this screenshot, which shows a Silk Road page titled “mastermind.” The government says this page provided an overview of transactions and money moving through the site:
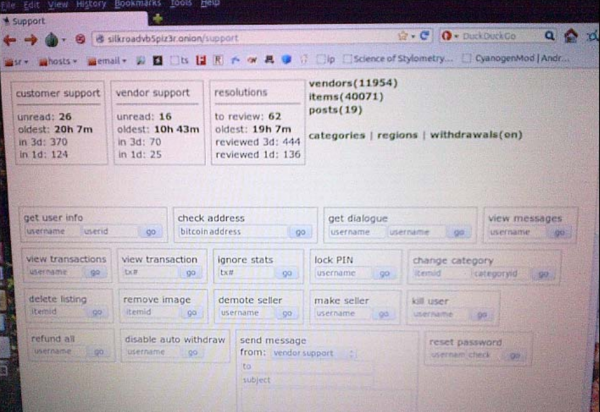
Another screen shot shows the Silk Road “support” page as found logged in on the computer seized from Ulbricht:
Furthermore, the government alleges that Ulbricht kept on his computer a fairly meticulous diary of his criminal activity.
“Additional files from Ulbricht’s computer reflect his continued control of Silk Road up to the time of his arrest. For example, the computer contains a file titled ‘log,’ in which Ulbricht regularly recorded his activity relating to his operation of the site during the period from March 20, 2013, to September 30, 2013, the day before his arrest,” prosecutors told the judge in a filing. “One entry, for example, notes that on May 28, 2013, he ‘finished rewritting [sic] silkroad.php controller.’ Another entry, covering the period from June 5, 2013 to September 11, 2013, describes efforts to ‘develop a monitoring system for the SR infrastructure.’
Another entry, dated June 2, 2013, allegedly references a joint venture with a Silk Road user, to whom he was ‘loaning $500k’ in order to “start vending on SR.”
“Financial files stored on Ulbricht’s computer likewise confirm his continuous control of Silk Road from beginning to end,” prosecutors wrote. “For example, one spreadsheet, titled ‘sr_accounting,’ lists hundreds of expenditures relating to Silk Road, from ‘server rent’ to ‘pay off hacker,’ spread throughout 2010 to 2013. In another spreadsheet, titled ‘NetWorthCalculator,’ Ulbricht listed all of his assets and liabilities, the most notable of which was an entry for ‘sr inc,’ listed as an asset worth $104 million. Moreover, actual proceeds derived from Silk Road were found on the computer, in the form of a Bitcoin wallet containing approximately 144,000 Bitcoins, equivalent to over $20 million based on prevailing exchange rates at the time of Ulbricht’s arrest.”
Other items of interest in the journal document the Silk Road’s early beginnings, as DPR mused on what to call the marketplace and how to get it up and running.
“I began working on a project that had been in my mind for over a year. I was calling it Underground Brokers, but eventually settled on Silk Road. The idea was to create a website where people could buy anything anonymously, with no trail whatsoever that could lead back to them.”
According to prosecutors, the journal entry goes on to describe how Ulbricht allegedly set up ‘a lab in a cabin . . . off the grid,’ where he ‘produced several kilos of high quality shrooms,’ so that he would have something to sell on the website when it first opened.”
Perhaps the most shocking revelation in the Justice Department’s argument against Ulbricht’s petition for bail is that he allegedly ordered not two but six executions. Unfortunately for DPR, he appears to have gotten scammed out of the money he paid for each hit (approximately a half million dollars in Bitcoins in total). On the bright side, despite the fact that Ulbricht said he received “visual confirmation” of the executions, the government says it was unable to confirm that any of the killings were ever carried out.
The government documents leave open several questions about the Silk Road merchant DPR hired to carry out the planned killings — a user who’d adopted the nickname “redandwhite” (apparently a well-worn nickname of the Hells Angels motorcycle gang). Was he a government informant who was working with federal prosecutors to nab Ulbricht, or was he just one of many Internet predators who make a living scamming the scammers?
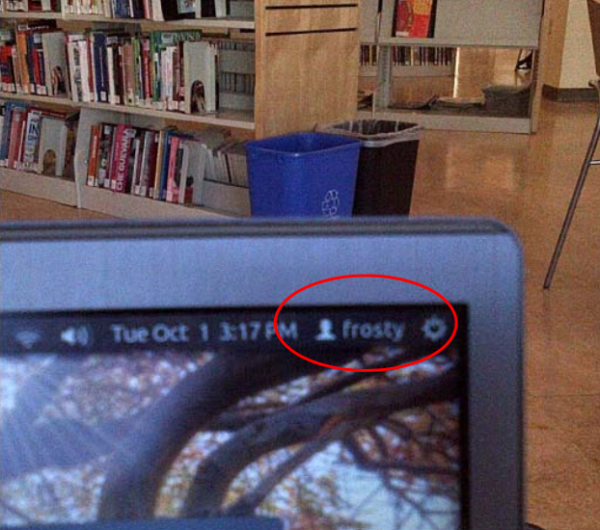
This photo, released by prosecutors, shows Ulbricht’s laptop as seized in the public library, logged in as “Frosty.” According to the government, this was the the name of the only computer authorized to log in to the Silk Road server directly.
Nicholas Weaver, a researcher at the International Computer Science Institute (ICSI) and at University of California San Diego, believes redandwhite was probably the latter, noting that the government’s initial complaint against Ulbricht indicated he’d used redandwhite to purchase fraudulent identity documents.
That’s important because prior to his arrest in San Francisco, investigators with the U.S. Department of Homeland Security paid a visit to the address to which the fake identity cards were to be delivered — confronting Ulbricht at his residence. Weaver said that if redandwhite was acting as an informant, ostensibly DHS agents would have been warned not to spook Ulbricht and potentially tip him off that the government was investigating him as the Dread Pirate Roberts.
“There’s no way they would have had the customs and DHS agents go up to this guy if they knew he was the Dread Pirate Roberts and not just some random guy buying fake IDs,” Weaver said. “If you knew these fake IDs were going to the Dread Pirate Roberts, you would not tip him off. This is a guy with millions of dollars in liquid assets.”
Weaver said Ulbricht’s lawyers will have their work cut out for them if they can’t poke any holes in the government’s case.
“If the defense isn’t able to get the server seizure suppressed, the good ship Revenge is sunk,” Weaver said.
Weaver said Ulbricht’s attorneys have one potentially strong avenue of defense: If federal investigators somehow erred in identifying and seizing the Internet servers used to control the Silk Road.
“The one thing I think could save him is if the FBI somehow screwed up in identifying the server and didn’t dot their I’s and cross their T’s,” Weaver said. “That’s because if you look at the original complaint, everything that says DPR is Ulbricht — everything that led up to them tackling him in the library — is pretty much derived from that server.”
Interestingly, the government’s case against Ulbricht could amount to an unexpectedly massive windfall for the U.S. Treasury. Prosecutors say they found a Bitcoin wallet on Ulbricht’s computer that contained approximately 144,000 Bitcoins, or roughly $20 million at the time. Since then, the value of a single Bitcoin has skyrocketed: Today’s market price puts the value of a single Bitcoin at a whopping USD $780, meaning that seized stash of Bitcoins is now worth more than USD $111 million.





Wonder what kind of laptop he used?
“frosty” screenshot is MacOS X
The screenshot is from a linux distro installation, not mac osx. Not sure which distro but it looks very similar to Ubuntu Desktop.
There was one screen shot the govt released that I didn’t put in the story.
http://krebsonsecurity.com/wp-content/uploads/2013/11/dpr-samsung.png
If you look at it closely, you can see he is using a Samsung laptop. I believe the operating system is probably Ubuntu Linux, and that he is running the Tor Browser Bundle.
Yeah, it’ clearly ubuntu. In one of the screenshots you see the unity launcher
I thought it looked like a slightly personalised version of XUbuntu or Linux Mint (XFCE), especially after seeing Brian’s extra screenshot. Also (not that I knew the man personally) but my guess is Unity would have offended the man’s sensibilities.
You would have thought with the money Ulbricht was pulling in, he would have have had a top of the line laptop computer, running a Linux distro
Is that the exact photo they released? Any chance of deciphering the text onscreen? Sounds interesting. Here’s what I can see:
Ugh. Obviou…
affects sales…
of the purity…
Posting as “d
Come on, wh
behind your
And since wh
percent cont
Ugh, obviously my troll is back, Oh well, he never affects sales when(?) my hundreds of customers know of the purity themselves
posting as
Come on, who are you? *****? keep hiding behind your mask you troll
*
*
*
*
your washing(?) technique you don’t seem to know what your doing.
Funny he had that “Science of Stylometry” article bookmarked. He had much more pressing opsec issues!
“Ulbricht had researched how to buy a citizenship in Dominica. ” He should have also done some research into extradition treaties. See http://en.wikipedia.org/wiki/List_of_United_States_extradition_treaties
I was going to say, going to that country won’t save you from extradition.
OT but that Wikipedia article, as well as most of the other articles floating around on the web, are often years out of date. Your better bet is look at the Department of State’s PDF on the matter — and to bear in mind that not only extradition treaties but diplomatic relations come largely into play. And that just because there is an extradition treaty, or is not one, does not necessarily mean one cannot be extradited. There is an entire section of federal code dealing with extra-extraditional methods, and one of their favourite tactics is offering money, benefits, or “return favours” to countries without formal extradition agreements. There have been many instances of things like this happening, but probably the most recent one that’s gotten much press is the “non-extradition” extradition of Gottfrid Svartholm Warg (aka anakata) from Cambodia — a country without very many extradition agreements. And even still despite all of this, extradition almost always requires what is known as “dual criminality”.
But putting this aside, if he were to have gotten a Dominica (note Dominica is not the Dominican Republic) citizenship, and were to have formally renounced US citizenship, a lot of countries will not extradite their own citizens, especially if there are somewhat shaky relations between the two countries involved.
Taking things a bit further, even if there are extradition arrangements with a country, if one were to pick a country where it is easy to ‘get lost’ and were not sought after til (long?) after they moved to that country, most of the countries without diplomatic relations and extradition treaties tend to be heavily cash-based cultures. Even if extradition were sought, it would be a whole lot easier to drop off the map once you landed there. In fact in most of them it’s probably much harder to get ON the map.
In closing, a lot of people in the US and elsewhere are looking for dual citizenships or to leave the US lately; in fact the numbers of people relinquishing US citizenship if they are expats has trebled or quadrupled in just the past few years — in large part because it is almost impossible to bank as an American citizen outside of the US.
Getting a new passport under a name that would be ‘wanted’ does not strike me as particularly criminal. In context of Ulbrecht’s philosophy it actually makes a lot of sense, absent any possibility of him being DPR. Expats often follow a 3-4-5/etc flag method of living, and this is not illegal at all. For a strongly believing libertarian, http://en.wikipedia.org/wiki/Perpetual_traveler is actually more common than you think, especially in the past ten years. To ignore Ulbrecht’s political leanings is to do him a disservice, even if the possibility cannot be ruled out that he “could” flee. Part of this is because he also has very strong ties and friendships in the US, as well as a very close relationship to his family. People with ties and strong family bonds generally don’t “run”, and if they do they generally do not last long “on the run”.
Wow I was just checking these documents out on Scrib , the shear evidence is amazing.
The thing that makes me wonder is most libraries block ports on their free WIFI networks either by way of a firewall proxy and or filtering. I don’t see how this guy could have connected to a TOR network when libraries are notorious in over protecting all patrons because they fear getting sued from the actions of one bad actor.
My experience witht most local free libraries end up blocking port 465 and 995 so using a email client ( like Thunderbird) is out of the question. If TOR is running on port 9050 /51 shouldn’t it be blocked, therefore Ulbricht would not have not been able to access the Silkroad administration section. Do you real think that library would have had wide open wireless internet without any monitoring or filtering?
Port 9050/1 is irrelevant for just connecting to Tor as a client, not acting as a relay. Unless there is deep packet inspection, it is actually not trivial to block Tor. A Tor client can go out on any port, including the typical port for SSL: 443. And Tor *uses* SSL. Even with deep packet inspection, all it would take is a fresh list of obfsproxy bridges and it would be near impossible to block getting on Tor without active monitoring (think GFW of China). Libraries usually don’t have active network defense monitoring better than the GFW.
I downloaded T..O.R. today on a encrypted USB hard drive and started using for the first time . I see what you mean by saying it can be used behind a firewall with port blocking
I can see a huge benefit of using T.O.R. on a web based email service or even Facebook
Any applications that do not have SOCKS5 built in (as TBird and Quassel do), can be routed through proxychains.
By adjusting torrc you can have it open up as many as 15 client ports, which proxychains can rotate through randomly, if set properly. Each time a different port is used, a new TOR virtual circuit is set up, defeating traffic analysis.
I did a howto a while back on the Manjaro wiki, but took it down after it became clear no one understand what the heck I was talking about.
Whoa, wait wait wait. Your username is TheOreganoRouter (ie TOR), you have .onion at the end of it, and you are saying you have only used TOR for the first time? Are you pulling peoples’ legs? 😛
It’s just a fancy pseudonym for this website probably because I love Italian food
You would correct, in the past I’ve never thought that their would be a need for me to use such a security measure for doing anonymous surfing. My opinion was always things like T.O.R. and Peer to Peer networks where used by criminals who do fraud or used in child exploitation. I tend to stay on the right side of internet security with doing all the correct thing to protect computers and or internet access. When people hear that you’ve used things like T.O.R. they immediately think you are are a criminal hacker or are doing illegal things such as fraud. I wanted to stay away from those negative labels and the bad connotation that go with it.
I mean that is why we are all here, to find out about the bad side of the internet and how things are done so that as readers we are able to better educated on how to protect ourselves from the cyber miscreants . We are all in fact internet contributors no matter the skill level or knowledge of topic.
Thanks to Snowden and this guy, I couldn’t resist the curiosity of checking out the T.O.R. browser
My skill level is a bit above intermittent when it comes to internet security but want to learn a huge amount more.
I hope that explains it :–(
I think the ability for free people to communicate without interference from any entity, government or otherwise is important. Otherwise we eventually end up like the oppressed behind the Great Firewall of China. I realize this capability gives crooks and our enemies the same upper hand, but to me freedom is more important. We can deal with criminal matters using our brains – we don’t need Orwellian tactics to solve crimes, or gather intelligence on terrorist targets.
Arent there are ways of obfuscating or spoofing (mac address, ports…. ) for connection?
I’m pretty naive and I use Bugtraq OS but there are tons of tools on it that could easily skirt the filters put up by most institutions. There are tools out there AFAIK.
What if he had hacked into the network to make certain changes already?
There is so much beyond concurrence.
You can pick any port you want to send traffic of any sort on, depending on how you set your server at the other end. The standard ports are just convention so that stuff works without needing to read a manual every time you want to connect to a new server.
If you set up your tor relay / mail server / vpn server to listen on port 80 (default HTTP) or 443 (default HTTPS) then you will easily get past most public wifi filtering unless they are doing packet inspection…
The Tor browser bundle has two extra options:
– My firewall only lets me connect to certain ports
In which you can enter 80,443
– My ISP blocks connections to the Tor network
The last one lets you enter bridge node IP addresses. Bridge nodes seem to work fairly well unless you are behind the Great Firewall of China, which is fairly aggressive in digging up bridge nodes and blocking them.
you can make tor go through port 80
Next time I fire up up TOR browser, I’m going to try that port number in the settings. Thanks
My brain just cannot reconcile the absolutely awful opsec this guy practices with the fact that he was running *the* “#1 FBI most wanted” illegal website, more or less successfully, for several years.
I mean really, he has a text file listing plans for what to do if he “feels the heat around the corner”, but yet sends his own photograph to people who know he is DPR in order to purchase fake IDs, and then DOESN’T enact his plan when said fake IDs are waved at him by an angry customs agent?
And then of course the whole lack of disk encryption. I’m going to assume the feds deliberately waited to arrest him until they could catch him with his laptop open, running, logged in — so maybe a simple precaution like whole-disk encryption wouldn’t have helped here. But there’s just no excuse for not hiving off all that other extra-damaging stuff like his ledger into a decrypt-only-when-needed subvolume.
Lastly, this guy felt the burning urge to be administering SR from public places wherein he could be sneaked (snuck?) up upon, yet didn’t make some sort of arrangement for safety if he were to be suddenly and forcibly separated from his laptop while logged in (i.e. with disk decryption key in RAM)? Even something as simple as a log-me-out-and-wipe-keys-from-memory proximity sensor? This guy can afford the fancy gadgets. $100 million riding on it and he takes none of these precautions.
Boggles the mind.
That is what arrogance gets you(Ross Ulbricht, that is).
What I find amusing is the FBI took three years to take it down DESPITE the awful opsec this guy used…
They don’t call the FBI the Fumbling Bunch of Idiots for nothing…
It probably took the FBI a year to figure out what Tor was…
There are probably a dozen hackers groups saying right now, “Hey, it took the FBI three years to bring down DSR, with a few tweaks we can make it take them ten years to take us down – we can get rich in that time…” 🙂
The delay probably wasn’t due to incompetence. During those three years, when he should have realized the feds were closing in, he instead concluded he was safe enough to be careless. Three years ago, maybe he was much more vigilant about keeping things encrypted and about not logging on in the public library, but all the details of tight security became tedious after a while.
Evidence in these types of crimes are often hard for judges and juries to understand, so it’s also very helpful if the defendant has gotten so careless that he’s bragging about it on forums.
By the time the feds make an arrest, they like to have so much damning evidence that they can get a defendant to plead guilty to avoid a life sentence for running a continuing criminal enterprise.
http://en.wikipedia.org/wiki/Continuing_Criminal_Enterprise
Why use public place to access internet why not to use 3g dongle or something its much safer. Maybe im wrong .
its so funny to watch how people have 20 million dollars and dont have a clue what to do with it . They cant even buy good bulletproof DDS or VpS with a static IP and use that as a gateway . Stupid , stupid man .
Good point he may have been using a wireless “dongle ” connecting to a 3G or 4G network. But still with all that money you would have thought he would have invested in a real good V.P.N.
Actually if you want GOOD opsec, someone’s commercial VPN isn’t good enough.
What you need is a long-range (a mile or more) wireless connection from your laptop in a place where there are no video cameras ANYWHERE in the neighborhood (and you don’t use the same place each time) to your first hop, which should be a relay to yet another long-range wireless connection (maybe one of several used randomly), which in turn connects to an anonymous wired Internet connection (a room with a phone and cable service rented under fake ID and never visited except to set up the wireless to wired connection – don’t leave any fingerprints or DNA, either; also one of several used randomly), which in turn connects to one of several botnets you’ve set up, so your final connection goes out someone’s compromised PC in Podunk to your target. The latency will be a pain but it’s safer to be slow than caught.
Good luck tracking those IPs back to anything useful, especially if you spoof the MAC addresses at each point and use Tor for each connection to and out of the botnet..
Also, the machine you use for this should have removable encrypted drives which contain the actual data and are hidden where no one will find them, and the main drive in the machine is wiped and reinstalled after EVERY use. That machine is also never used for anything BUT hacking. You have another machine for your normal computer activities – and never the twain shall meet.
This is the kind of opsec hackers should be using: a chain long enough so that even if the Feds are using signals intelligence in real time through the ISPs and phone companies to track the connections they STILL can’t get to you before you have time to wipe everything.
One of the weak points here is that room you never go to with the wired connection. You probably want some form of video surveillance with hidden motion sensors and nanny cams (perhaps in smoke alarms, etc), to send encrypted pings from on an ongoing basis to yet another location you can check to verify there has not been anybody “visiting” this room. It would be trivial for a federal agent to tap this connection, either physically or at the switch, with you being none-the wiser and basically obliterating the point of a lot of your opsec (save perhaps the ‘didn’t see your face’ part). In this case you could very well be worse off by deluding yourself into thinking your opsec is wonderful.
Also, if you wanna be really paranoid, a Faraday cage and sufficient buffering to prevent electronic emanation monitoring. Plus you have to ‘trust’ those people who own those Wifis a mile+ away aren’t being visited and permitting the feds to monitor their connections. You can see where I am going with this. The big problem is people think true opsec can exist, and it almost cannot.
I won’t even pick on the person who suggested a 3G/4G connection (aka free instant geolocation for investigating parties). 😉
You don’t trust other people to run the WiFi. You set up your own clandestine and concealed WiFi access points that no one knows about. The only way they get detected is if someone climbs a tree with a fish.
A Faraday cage isn’t necessary if they can’t find your location in the first place. If you’re far enough away from the hack – which is the point of this chain of connections – they can’t use electronic monitoring even if they run an aerial surveillance craft with SIGINT monitoring gear. Your target is in LA, you’re in Denver, your chain runs through Phoenix and Seattle…Good luck with that. Picking you out of every other electronic signal in the area is going to be difficult and very expensive even if they scramble an AWACS over every city in the connect chain – which they’re not going to do unless you’re Osama returned from the grave…
Again, don’t let the target detect the hack in the first place, make sure there are a lot of connections between you and the target, use those connections once only, never hack from a fixed location, and wipe everything when done. I don’t think any hacker has every been caught under those circumstances, and it’s doubtful any could be without a massive effort.
Every hacker’s arrest I’ve ever heard of was caused by violating one of those requirements and worse.
The key to individual security is the following five requirements:
1) No one knows who you are.*
2) No one knows where you are.*
3) No one knows your motivations or intentions.*
4) You’re mobile.
5) You have overwhelming local firepower – i.e., you can engage any likely adversary who comes across you long enough to be able to disengage and resume states 2) and 4).
*Where “no one” means an adversary.
Hackers are successful in defeating current infosec because they adhere to almost all of those requirements (even if imperfectly) whereas no organization of any kind – even clandestine organizations – can adhere to hardly any of them.
I wonder how hard it would be if one was part of a huge MESH network like the free one they built in France. Every packet goes through every one’s access point, some wired, some wireless; with a hodge-podge of networking assets – some of the government sponsored and some setup with private money. Sure the French government is involved, but with every access point connected directly with almost every other access point in the topography of the network model – I’d think getting all the routing information for a spy operation would be very difficult. In the US, all they need is a few big telcos, and backbone giants, and they got it all under control.
Assuming an agency manages to track the IP chain back to that room – which is unlikely in itself given the random Tor connections in and out of the previous botnet – when they tap that line, yes. they’re going to see everything going in and out.
It would be smart to have a monitor on the room to see if it’s been compromised. That monitor of course would use the same random wireless connections the main connection does. They can certainly tap the signal from outside the room without ever entering it, which kind of moots the point of even bothering to monitor visually. However, one could set up the system to make it very difficult to find, especially if one used wireless communications.
The problem for them is the random multiple wireless IPs that box is communicating back to. They’re going to have to have a fish and track the signals wirelessly back to the wireless access point. From there they have to do the same back to another set of random wireless access points. And from there back to a (preferably mobile) source – the hacker in a van or something.
Yes, it’s doable. Yes, it’s a PITA for them.
The point is there’s no way they can do it in real-time while you’re online, so they’ll never catch you IN THE ACT or with an IP they can point to as directly connected with the target hack.
As someone once said, “I don’t care if they know I did it, just so they can’t prove I did it.”
If you continually alter the hacking infrastructure so it’s not fixed, you can send them running around in circles. Couple that with an inability to be caught in the act, and that’s about as good security as you can get in a system where everything is connected to everything.
And then there’s other means like long-distance laser communication systems they’d have to have special detectors for to even spot. And of course, every intermediate device gets wiped as soon as the connection is broken. The point is to make it arbitrarily difficult to trace back a hack to a physical location.
Of course, it’s better if the hack isn’t detected until it’s entirely over and done with or one that no one even knows actually occurred.
Also a nitpick: Remastersys to a Live ISO is probably far more logical than constantly spending 3 hours every day to reinstall and 2-3 days to fully wipe drives. Silly.
Unless you’re downloading everything from General Dynamics, my guess is the target data isn’t so huge as to require multiple terabytes to be wiped.
Besides, you move the acquired data as it’s being acquired to an external device which is then hidden away somewhere. You don’t store it on your hacking box.
All you’re wiping is the main drive of the hacking machine in order to prevent any artifacts from the hack from being retrieved. Then you reload it from a backup image which was made before it was ever used for anything illegal. Takes half an hour. to reload, plus however long it took to wipe the main drive.
So basically however long it takes to wipe a couple hundred gigs, if that. You don’t need more than that for any hacking if the hacked data goes on an external drive which is subsequently hidden (or destroyed).
The main goal is to eliminate artifacts in the OS and application programs from being forensically recovered. The only sure way to do that is full disk reformatting.
And one should probably hide the hacking machine somewhere as well. A hacking machine should never ever be used for anything else.
Re: “What you need is a long-range (a mile or more) wireless connection”…
A Ubiquiti NanoBridge M2 would be very good for this: http://www.ubnt.com/airmax#nanobridgem
… running OpenWRT with Shorewall. (because UBNT’s firewall is non-functional)
It is fine equipment.
There’s a lot of moderately expensive wireless and laser communication systems that are good for as much as twenty miles (under optimum conditions). That’s not even including the weird hacker setups that go fifty miles or more off the top of some mountain…
A list of some impressive long-range wireless efforts:
http://www.seattlewireless.net/index.cgi/LongShots
And of course:
New World Record for Wi-Fi Distance: 125 Miles
http://www.wifi-toys.com/wi-fi.php?a=articles&id=91
Of course, for hacking purposes, it’s probably not wise to be using ten-foot dish antennas… 🙂
And there’s “Free Space Optics” communications equipment: using lasers point-to-point to get up to GB speeds over distances of up to 2KM. The extra nice part? Security! Quoting one source:
Free Space Optics is a very secure method of wireless communications when compared to RF Signal Networks because the light beams cannot be detected by spectrum analysers, data transmissions can be encrypted, the laser beams are very narrow and invisible making them hard to find or detect and to receive the signal, another matching receiver would have to be aligned within the light path which is quite unlikely to happen.
Just what a hacker needs! Of course, this stuff is VERY expensive – the cheapest seems to be around $1,500 per unit – which of course gets more expensive as you add the other end, and then several more… Still, if you’re going after truly valuable intellectual property or government secrets – and want to stay out of jail – it might be worth it.
I wonder what is the meaning of “go to end of train” in the escape plan?
I am guessing, giving his order of operations, it might involve how he logs in to do the next thing on the list:
“get new laptop
go to end of train
find place to live on craigslist for cash”
So maybe he buys a totally clean laptop, gets on a public train (the end likely having the least surveillance and easiest to get off and on while being on the fewest cameras, perhaps), boot up the 3G so the location is not static, get on craiglist and find a place to stay, close down connection, close down laptop, get off of train, and disappear into relative obscurity.
But that’s just my guess.
I left out, a lot of trains now, especially commuter trains, have on-board WiFi — which would provide even more (and a lot more, perhaps) security than a tossable 3G sim/dongle). That and macchanger and he’d be completely anonymous if attired properly and he avoids cameras getting any clear shots of his face/etc.
In SF, it’s very easy to take the BART to the Caltrain terminal, pay cash for an appropriately zoned ticket, and go pretty far through California, without owning a car or showing ID at an airport. (I did something similar in SF in 2011: was crashing at an apartment & decided to go to Mountain View for a meetup; had no car, but Caltrain worked fine.)
oi krebsky whats your problem . why did u deleted my post ?
Nobody deleted anything. It got held for moderation for some reason. Settle down, Beavis.
> Nobody deleted anything. It got held for moderation for some reason. Settle down, Beavis.
I am the great Cornholio! I need more security for my silkroads!
HA!HA! :v
That’s a pretty robust management system, looks custom yet simple and powerful. Also highly exploitable. :-/
Great article, as always: One editing note:
Might want to change ‘resident’ to ‘residence’
“were to be delivered — confronting Ulbricht at his resident.”
It really baffles me that as an open a view he had, he didn’t even think to hit the power button on the laptop to make it a weeee bit more difficult for the Feds to capture data ?
I don’t know the scenario, but I am sure it was all brought on by a distraction, and a few officers snuck up to him and he hit the floor. Eh, too late to knock some sense into him.
Now all an FBI Tech agent needs to do is create himself an admin account on the site when it was allowed and they can amass data with ease. If the website has financial data on other people, including how much cash the sellers acquired via that website, and a payment processor email address, it gets ugly for sellers.
The feds then have a papertrail of evidence. The IRS has means to demand payment on any taxes that were not paid. I just can invision a massive raid party. I can also see some of the littler sellers shaking in their boots and deep sixing a phone, laptop or CPU and trying to shake off any potential evidence.
I mean, its great that they have a ton of evidence on him that has been released, and I am sure it will stick. The procesution probably has more data than they can handle, and its probably a tough call in what evidence and how much. Too much means holes can show, not enough and well, you know what happens then…
I read somewhere – I think it was on CSO Online that Silk Road II is operational. That can squashed really quick if the Feds already have Silk Road I sellers in chains. It would send a message to them, saying hey – ummm Its against the law in the USA to do this.
I read the stories about the so-called compassionate side of SR, and it freakin doesn’t matter. Period. If it is against the law, it’s against the law. It doesn’t matter if the seller and buyer are “safer” and keeps them off the streets. Now any transaction is tied directly to a name and a bank account, rather than a semi controlled action in a dark alleyway.
Thats a boatload of Bitcoins. Common, if anyone here had that much money, why wouldn’t you just cash in and go to an island and relax for the rest of your life? How far do you have to go, unless you have the need to self destruct, and want to be caught?
In his case, living on the edge not only put him at danger, but alot of the people who visited that illegal website. Who knows for sure how many VIP / Federal/ Contractors/ Health / Postal / Lawyers/ Real Estate and other individuals that hold positions of trust just got thier pants yanked down to the floor.
Go Feds. Bring them all in.
> I don’t know the scenario, but I am sure it was all brought on by a distraction, and a few officers snuck up to him and he hit the floor.
Pretty much. The local SF newspapers covered this based on the witnesses in the library: a female agent walked up to him, went into histrionics, she grabbed his laptop while he tried to figure out who she was and how he had wronged her, and then the guy agents grabbed him and cuffed him.
The Feds won’t be busting any sellers.The only one allowed to access SR directly (not through TOR) was DPR. Remember, everyone else had to go through TOR, and transact in BitCoins.
It’s come out in the Snowden docs that there are a few ways to ‘stain’ a browser, but Javascript must be on or Flash enabled. To ‘mullinize’ it, or put in ‘evercookies’, or Flash cookies. But these by their nature are targeted attacks, and require either control of the web server or inducing the target to open an email attachment. It also requires that the target then visit another controlled website with that browser and without TOR, in order to capture their IP. See “TOR Stinks”.
Most people don’t use TBB for unsecure browsing as TOR is slow. Unlikely any sellers will be traced unfortunately.
Hunh, then this article, and many others like it must be mistaken….
http://mashable.com/2013/10/08/8-silk-road-drug-dealers-arrested/
Given the timing of the MITM attacks on TBB this past summer to prosecute a certain admin/company for KP violations, and the somewhat on-par timing of the data center access on the feds’ parts for the silkroad server(s), it would have been entirely possible to selectively serve CIPAV-like identifying software/cookies to the vendors they were most interested in, using account whitelists to limit exposure so a larger portion of the silkroad users would never be targeted, effectively creating a ‘phone home’ for those vendors who followed more (one could argue rightfully so) paranoid shipping procedures. Especially given the fact that many vendors were not ONLY vendors on silkroad.
By the way, while my sentiments about the questionability of these charges should be left out of this, probably, and the questionability of these ‘malware MITM’ methods as well — I really do believe it does cross the line when ‘law enforcement’ is using unethical means to attack both ethical and unethical users (or maybe any users — how good are we if our ‘heroes’ are dirty and corruptible as our ‘criminals’? There is always such a fine line, and quite a large people *fantasize* about crime; why else would crime movies and books be so popular — but there is a big difference between being interested and following through. I’m pretty sure, for instance, most downloaders of the Anarchists Cookbook have not obtained a copy just so they could blow things to smithereens… and I’ve seen little evidence to suggest most readers of Loompanics books on methods to kill people or readers of PIHKAL are even attempting to make vast quantitys of phenylethylamine-based intoxicants. I’ll be curious to see, as this case unfolds, how many people will wind up being charged with minor crimes getting blown out of proportion/thought crimes, as it were.
In the meanwhile I am greatly enjoying watching the effects of the (alleged) DPR and SilkRoad bitcoin purse seizures on the price of bitcoins. Something to bear in mind for other people who also saw this coming — by having so much access to so many bitcoins the fedss can (and almost certainly will, given their dislike of the currency) also entirely crash the price of bitcoins by dumping a whole lot of them into the market at random times (not too unlike stock manipulation. So to those others of us with (legit) bitcoins laying around, a word of caution.
As I say, first of all sellers would have to have javascript or flash enabled in order to be affected by exploits, and both are disabled in TBB, which is the easiest way to access TOR.
Second, TBB comes with the TorBrowser, which is set to only access The Internets through TBB, without some technical fiddling, so even if a browser is stained it will likely only access sites through TOR, doing the Feds no good.
I recently noticed that my system was hammering away trying to get out port 3333, to an IP in New Jersey. I ARPed that to reporting.theonion.com. I did some analysis of the server listening to 3333 there and found that it was a command/control for the hostile javascript I had running in memory. What had happened was that I visited theonion.com, which had been compromised, it gave me a hostile javascript which then tried to access the C&C, to download a trojan to my machine. But it couldn’t get out because my firewall is so tight. Of course I had javascript turned on because I trust(ed) theonion. I notified them that they had a compromised server which was infecting users, and I gave them the details, but they didn’t believe me. (or wouldn’t admit it) Three weeks later there was a big news story about how their servers had been compromised. Maybe this will help some understand how this works. And why NoScript is valuable.
I agree that the government should never have circumvented the Constitution with this surveillance, much less given a blanket pardon in advance to the telecoms for the program. We no longer have moral authority. When we arrest others’ diplomats, we can expect them to arrest ours.
We are in absolutely no position to be explaining right and wrong to others, when we destroy Iraq (the only thing holding the much worse Iran in check), for $trillions, and get absolutely -nothing- in return. So why. did. it. happen? Why did we for the first time, outsource food service, logistics work, security, and most other traditionally military jobs to private companies, at a cost of 9 to 20 times what it used to cost the military to do? Because in actuality this was the largest transfer of wealth from taxpayers, to private interests, in world history. We have no business calling other governments corrupt.
Lastly, it is not the seizure of SilkRoad wallets that is driving up BitCoins; if anything that is inflationary, and what we are seeing is massive DEflation. It is known that citizens of Cypress bought big when their economy ran into trouble recently. Saudi has been buying up gold (which has driven its price up) and some say they are buying BitCoins now. And China has been agitating for some time to replace the dollar as world reserve currency — with only 22 million BitCoins in existence, it would be nothing for them to drive the value up. Probably it is all three.
All of us regret not having bought more BitCoins, but it’s better than speculating on a new currency only to have it collapse. That said, I think BitCoins are going to be big. A repository has just been made a bank in the EU, and more stores than ever are accepting them. And there are other indications. I say it is not a bubble, and they will have to make a split somehow, soon.
Hunh, (‘Mashable’. Classy.)
You don’t seem to understand how those busts were made.
Article was to prove a point that yes indeed, the sellers are lining up at the court house.
Oh, I understand the way the Feds work, and its really easy to understand. I didn’t have first hand knowledge of this tackle exercise, but another poster cleared it up quite nicely.
In any event, they probably have more information than they need right now. Think of the web history, email addresses and the chats that will be scraped off that box. HA !
Are you concerned that your name is on that box?
Nice
What in the world is a ‘hatsker’? 😉
Hello Brian,
Would you please be so kind as to repair the following mis-linked PDF in your story?
“the government’s bail submission (PDF) notes. A copy of the application for citizenship in Dominica allegedly found on Ulbricht’s laptop is here (PDF).”
links twice to the PDF of the Dominica application, instead of the first being what I believe should be the bail submission document?
Thank you. 🙂
Thanks for fixing. 🙂
I could see why somebody might rave about some of these IDs — the New South Wales and especially the South Carolina are both very very good.
I am curious if, from what you have seen Brian, quality has a huge bearing on volume, or if demand goes down when quality does? I know you have had copies of some of these databases so I thought perhaps you could shed some light on this side of the ‘marketplace’, as it were, especially on an ongoing basis as the government’s documentation of the ID sting unfolds?
More information on the documentation aspect of this line of crime would be quite interesting to read about. You had written before that you were working on a story involving airline loyalty rewards/frequent flier and flight scams, and I’ve often wondered how these sorts of crimes are not prosecuted and penalized more often given the overwhelming reliance on documentation, nowadays, to fly. Or are they being prosecuted and it is largely something that is kept ‘quiet’ (perhaps used to gather informants on forums?).
Wow, how do they get those holograms on the license? Good quality indeed.
One last comment:
This portion of your article contained one of the funniest things I have read in a long time. Is he suffering from dementia?:
“For example, one file found on the computer, labeled ‘emergency,’ contains a list of apparent to-do items in the event that Ulbricht learned that law enforcement was closing in on him. It reads as follows: […]”
I particularly liked how he might forget to obtain a new identity. Also “go to end of train”.
Good article once again! Thanks.
stopped reading on 3rd line
no you could not buy guns or hitmen for hire on SR
You could buy guns. See the Armory.
you can on “SR 2.0” not on Ulbricht SR
see screenshot before take down @ http://www.pcworld.com/article/2061800/silk-road-online-drug-marketplace-resurfaces.html
Dude. The Armory was a thing. Google it. Yes, on the ‘Ulbricht SR’. Don’t make yourself look like an idiot by trying to correct people who were using & documenting SR years before you…
Seriously dude?!? You think a place that catered to the sale of Drugs, hits on ppl you don’t like and HUMAN TRAFFICKING drew the line at GUNS?!? Wow… For reference, you could not only buy guns, but rocket launchers, missiles, submarines and MOTHERF.UCKING TANKS BRO…
You are simply wrong. There was no human trafficking on SR. There were no hitmen (Ross negotiated privately with the 2 scammers who claimed they could do hits for him). The Armory was up only briefly, and there were never any “rocket launchers, missiles, submarines and MOTHERF.UCKING TANKS” – how would these even be delivered?
Unless you personally ordered those off the Armory and received them and are willing to provide signed blockchain transaction IDs and photos – STFU. You don’t know what you are talking about.
Why not? The drug cartels get rocket launchers and PKM machines guns all they can buy, and I guarantee you they don’t get that from US gun dealers. These facts are all out there – I don’t even need to publish a link. It is well known that Chavez, Iran, Israel, and smugglers from the GWOT have been trading in Mexico for years now.
It may be only slightly tangential, but I laughed out loud right after I read this comment, because the very next email I read was one I received today from the US Attorney Preet Bharara in New York:
DEFENDANT WHO SUPPLIED THREE ROCKET-PROPELLED GRENADE LAUNCHERS PLEADS GUILTY IN MANHATTAN FEDERAL COURT TO ATTEMPTING TO PROVIDE MATERIAL SUPPORT TO TERRORISTS
Yep!
Please note the complete absence of the words “Silk Road” in your comment. I don’t know how I can be clearer. You think something has happened. That something has not happened.
Now, I am not one to tell the Mexican cartels where they should buy their heavy weaponry, but I personally would advise them to not buy them on small-time Internet black-markets, but to continue their tried-and-true procurement strategies like smuggling the weapons themselves into Mexico, buying from offline American gun dealers for much less, stealing from the military, and so on and so forth.
The SR business model, as superb as it is for small drug transactions, did not match well such high-value one-off hardware transactions. Such transactions are unusually high in counter-party risk, as Krebs’s link points out – domestic terrorism cases are classic entrapment in providing the ‘weapons’. The usual mailing approaches did not scale to just RPGs, never mind tanks. The Armory never sold such a thing, and heavier weapons than rifles or a few pounds of explosives do not appear in anyone’s spiders of the Armory. There are no legitimate reports of sales, and no linked crimes or weapons. And so on.
tl;dr: You are wrong.
I won’t argue whether it was on Silk Road or not, but it is a teaming market believe me! Just watch COPs once and a while, and you will see. They busted a FULL tanker of AK-47s from China a few years back, and that was only ONE of the ships they caught! The other ones were already unloaded and the booty was gone and disappeared into the US black market. Chinese PRC officials just shrugs their shoulders at this.
A whole armory of the same weapon was taken from a 29Palms military armory a year or two ago, and they’ve never picked up the trail on what happened to those either. I can go on and on –
> I won’t argue whether it was on Silk Road or not
Good, I’m glad we’re done here. This was a page about SR, and so that was the isssue.
The global arms industry is enormous and no doubt it is interesting how its products flow, but not directly relevant to a discussion of Silk Road.
..
It amazes me the lengths to which these people go to try and cover their tracks – only to be outsmarted by the Feds. But the thing that amazed me the most was that the guy wasn’t already in some other country with weak and/or corrupt law enforcement.
I suppose some of the bad guys will learn from this. And the good guys will have to adapt – a continual game of cat-and-mouse.
It said the mistakes included using a Google email address, rossulbricht@gmail.com, for communications linked to Silk Road, such as promotional material about the website dating back to January 2011.
doing this at public library? no panic button binded to shut down in emergency? using persistence… hah, this guy sure had the luck to get rich but no brains to stay rich.
so is that really him on linked in?
http://linkd.in/18h7GmD
and if so – why is the profile still live with only 100 connections.
I just tried to connect to him…