Last weekend, Target finally disclosed at least one cause of the massive data breach that exposed personal and financial information on more than 110 million customers: Malicious software that infected point-of-sale systems at Target checkout counters. Today’s post includes new information about the malware apparently used in the attack, according to two sources with knowledge of the matter.
In an interview with CNBC on Jan. 12, Target CEO Gregg Steinhafel confirmed that the attackers stole card data by installing malicious software on point-of-sale (POS) devices in the checkout lines at Target stores. A report published by Reuters that same day stated that the Target breach involved memory-scraping malware.
This type of malicious software uses a technique that parses data stored briefly in the memory banks of specific POS devices; in doing so, the malware captures the data stored on the card’s magnetic stripe in the instant after it has been swiped at the terminal and is still in the system’s memory. Armed with this information, thieves can create cloned copies of the cards and use them to shop in stores for high-priced merchandise. Earlier this month, U.S. Cert issued a detailed analysis of several common memory scraping malware variants.
Target hasn’t officially released details about the POS malware involved, nor has it said exactly how the bad guys broke into their network. Since the breach, however, at least two sources with knowledge of the ongoing investigation have independently shared information about the point-of-sale malware and some of the methods allegedly used in the attack.
‘BLACK POS’
On Dec. 18, three days after Target became aware of the breach and the same day this blog broke the story, someone uploaded a copy of the point-of-sale malware used in the Target breach to ThreatExpert.com, a malware scanning service owned by security firm Symantec. The report generated by that scan was very recently removed, but it remains available via Google cache (Update, Jan. 16, 9:29 a.m.: Sometime after this story ran, Google removed the cached ThreatExpert report; I’ve uploaded a PDF version of it here).
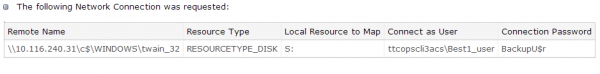
According to sources, “ttcopscli3acs” is the name of the Windows computer name/domain used by the POS malware planted at Target stores; the username that the malware used to upload stolen data data was “Best1_user”; the password was “BackupU$r”
According to a source close to the investigation, that threatexpert.com report is related to the malware analyzed at this Symantec writeup (also published Dec. 18) for a point-of-sale malware strain that Symantec calls “Reedum” (note the Windows service name of the malicious process is the same as the ThreatExpert analysis –“POSWDS”). Interestingly, a search in Virustotal.com — a Google-owned malware scanning service — for the term “reedum” suggests that this malware has been used in previous intrusions dating back to at least June 2013; in the screen shot below left, we can see a notation added to that virustotal submission, “30503 POS malware from FBI”.
The source close to the Target investigation said that at the time this POS malware was installed in Target’s environment (sometime prior to Nov. 27, 2013), none of the 40-plus commercial antivirus tools used to scan malware at virustotal.com flagged the POS malware (or any related hacking tools that were used in the intrusion) as malicious. “They were customized to avoid detection and for use in specific environments,” the source said.
 That source and one other involved in the investigation who also asked not to be named said the POS malware appears to be nearly identical to a piece of code sold on cybercrime forums called BlackPOS, a relatively crude but effective crimeware product. BlackPOS is a specialized piece of malware designed to be installed on POS devices and record all data from credit and debit cards swiped through the infected system.
That source and one other involved in the investigation who also asked not to be named said the POS malware appears to be nearly identical to a piece of code sold on cybercrime forums called BlackPOS, a relatively crude but effective crimeware product. BlackPOS is a specialized piece of malware designed to be installed on POS devices and record all data from credit and debit cards swiped through the infected system.
According the author of BlackPOS — an individual who uses a variety of nicknames, including “Antikiller” — the POS malware is roughly 207 kilobytes in size and is designed to bypass firewall software. The barebones “budget version” of the crimeware costs $1,800, while a more feature-rich “full version” — including options for encrypting stolen data, for example — runs $2,300.
THE ATTACK
Target has yet to honor a single request for comment from this publication, and the company has said nothing publicly about how this breach occurred. But according to sources, the attackers broke in to Target after compromising a company Web server. Somehow, the attackers were able to upload the malicious POS software to store point-of-sale machines, and then set up a control server within Target’s internal network that served as a central repository for data hoovered by all of the infected point-of-sale devices.
“The bad guys were logging in remotely to that [control server], and apparently had persistent access to it,” a source close to the investigation told KrebsOnSecurity. “They basically had to keep going in and manually collecting the dumps.”
It’s not clear what type of software powers the point-of-sale devices running at registers in Target’s U.S. stores, but multiple sources say U.S. stores have traditionally used a home-grown software called Domain Center of Excellence, which is housed on Windows XP Embedded and Windows Embedded for Point of Service (WEPOS). Target’s Canadian stores run POS devices from Retalix, a company recently purchased by payment hardware giant NCR. According to sources, the Retalix POS systems will be rolled out to U.S. Target locations gradually at some point in the future.
WHO IS ANTIKILLER?
A more full-featured Breadcrumbs-level analysis of this malware author will have to wait for another day, but for now there are some clues already dug up and assembled by Russian security firm Group-IB.
Not long after Antikiller began offering his BlackPOS crimeware for sale, Group-IB published an analysis of it, stating that “customers of major US banks, such as such as Chase (Newark, Delaware), Capital One (Virginia, Richmond), Citibank (South Dakota), Union Bank of California (California, San Diego), Nordstrom FSB Debit (Scottsdale, Arizona), were compromised by this malware.”
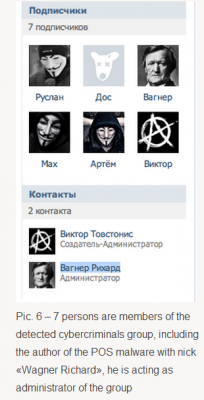
In his sales thread on at least one crime forum, Antikiller has posted a video of his product in action. As noted by Group-IB, there is a split second in the video where one can see a URL underneath the window being recorded by the author’s screen capture software which reveals a profile at the Russian social networking site Vkontakte.ru. Group-IB goes on to link that account to a set of young Russian and Ukranian men who appear to be actively engaged in a variety of cybercrime activities, including distributed denial-of-service (DDoS) attacks and protests associated with the hackivist collective known as Anonymous.
One final note: Dozens of readers have asked whether I have more information on other retailers that were allegedly victimized along with Target in this scheme. According to Reuters, “smaller breaches on at least three other well-known U.S. retailers took place and were conducted using similar techniques as the one on Target.” Rest assured that when and if I have information about related breaches I feel confident enough about to publish, you will read about it here first.




That’s peculiar isn’t it. Snowden has the NSA secrets, he’s in Russia, and he works with these criminals. Hmmmm?
A few blog sites had his girlfriend, Lindsay Mills, working with Anonymous too.
Not really. Replace “Vkontakte.ru” with “Facebook” for a better idea of how close the connection isn’t.
What leads you to think that Snowden works with these folks? He may, or may not, work with some others but that is beside the point.
Why do you intimate that he works with these criminals?
Shallow thinking?
Or disinformation. I imagine a few people (haha, at least a few) want to discredit Mr. Snowden.
Excellent bit of reporting Brian, bravo….. but can you verify whether or not Target was considered to be PCI-DSS compliant? I haven’t seen any reference to whether or not this giant of the retailing business was, in fact, following the rules that all the rest of us merchants are being forced to follow by the card brands… if they were, it really makes the whole PCI-DSS regime a joke…
Earl – As a Level 1 merchant Target in all likelihood was in compliance or would have been paying fines for the privilege of being non-compliant. The non-compliant fine used to be $25k/month which would be a very minor expense for Target to endure, if that’s the case. However, even if they were compliant, and for sake of argument let’s say they truly were 100% compliant – since the malware did not trigger an alert then it would have taken one or more of the other controls to stop this. There in lies the rub. Focusing on the malware is a fool’s errand. The real focus needs to be on the path in for the malware and the path out for the data.
I’d agree John, as we calculated given the fine regime at the time, it would be preferable for us to pay the monthly fine in perpetuity than to ante up the tens of millons of dollars to ensure the house was locked down and fully PCI-compliant. The card brands figured that out early and corrected the fine regime so that it escalated geometrically monthly. so that even the largest merchants with the deepest pockets would eventually feel the pain. As for PCI-DSS itself, I hear ya, it’s not the panacea for addressing every security concern in a merchant’s house, but, it certainly provides enough of a framework to make any intrusion that much more unlikely given the hoops the attacker would have to jump through to be successful. The essence of this breach seems to indicate, at least to me, that some very basic PCI network segmentation was missing…. would love to know who Target used as their QSA…
Earl – The current PCI DSS segmentation technique is used simply to limit the scope of the assessment and is not a requirement. The key is the access control into and out of the cardholder data environment. That’s where the vulnerability almost certainly lies. Almost certainly what happened here, based on the widespread reports of other merchants, is that there is a common POS vendor and the bad guys broke into them first and got support credentials and then waltzed into the POS at the merchants. I’d bet money on it.
Except that even Krebs said in the article that the POS is home grown.
More or less true. You can do a social eng to get your software installed in the POS (get a VISA hat, a VISA polo shirt and a nice badge with your photo, go to one merchant manager and tell him: ” Hey, I’m an independent contractor working for VISA and I’d like to test your POS to see if any is having problems… Are you noticing any delay lately in any of your terminals?”). This will probably give you physical access to the terminals, and maybe even to the local concentrator. I just think the initial vector can be more “normal” and be as efficient as. PS.: Windows CE boot is really easy to bypass if you know what you are doing, and have past experience with activesync.
More than just network segmentation was missing.
File Integrity Monitoring
Application-layer gateway in the DMZ
Firewall egress controls
All missing.
And most Level one merchants self-assess with internal audit staff, not an external QSA.
/source: I’m a QSA
Agreed!
The only concern is how the File Integrity Monitor control usually is audited: I don’t remember having a files integrity monitor on WindowsCE machines in production in place on most companies, as this is a difficult task to perform and automate… Usually they control and monitor the files before sending to the POS, and check right after the update. In case of this virus the original software may be intact (as the virus is reading POS memory in parallel it may not change the original software). But the other controls should catch the unknown packets moving from the POS. (a windows mapped drive is really easy to catch within the network!)
I work for a level 1 retailer and was under the impression we had to use a QSA auditor because we have had one since our first PCI audit.
PCI means squat. Look at the outcome. If a PCI compliant company was “secure” or “vigilant” it wouldn’t have resulted in the stinkin’ mess they are in right now.
Companies aren’t going to scream ” I am NOT compiant – Fine me!”
It takes an audit by the people who manage the PCI to find some one not acting in due diligence, due care or the prudent man rule.
Though these PCI complaint rules look good on paper, unless they are enacted and people are proactive and care, its not going to work no matter how user friendly or strict any law or regulation is.
They were riding the gravy train until they got robbed right in front of their eyes. I’d like to see the logs and times of these persistent connections. I bet they were in the done during staff hours. Its not difficult to catch these guys, but people don’t want to unencrypt traffic that would show continuous traffic to places that they DONT do business with. No “whitelisting” of good traffic lanes, or blacklist the ones they will probably never sell to.
There is plenty wrong with this sort of breach. It is huge, and so are the problems. Call it ignorance, incompetence or whatever, its simply wrong and Target has violated the trust of many people.
Compliance != Security
Not necessarily true. When I went through QSA training the official PCI Council trainer at the time STRONGLY suggested that some of the largest merchants could afford to ignore the PCI standard. The processing bank can choose not to fine the merchant, and can choose to forget those fines if the merchant makes them enough money.
Yes, that is right. If they had anti-malware installed and up to date and anti-malware didn’t detect it, then their compliance won’t be an issue and they won’t be accountable to brands for the brands’ losses. The same goes for other controls . . . . in addition, anybody in PCI compliance knows that with compensating controls and their interpretations and debates the possibilities are endless. We really can’t speculate on their PCI compliance status from this, but can certainly reflect on the PCI standard’s inability to protect organizations and their customers from breach.
I have heard it said by well known white-hat hackers, that PCI-DSS compliance only reduces the risk of compromise by 50%. That being said, PCI-DSS compliance makes one a less attractive target then a business that is not compliant.
You already know they weren’t. The support accounts (if that is how it happened) should be disabled whenever not in use. Passwords should be expiring every 90 days. There should have been logging and a different user/password for each device. Robust firewall, disabling unnecessary services, user privilege separation, etc. I have a hard time seeing how this would happen with all those things being done and them not noticing it for months-years. They were not complaint by any stretch of the imagination and very very few companies truly are.
PCI item 8.3 “Is two factor authentication incorporated for remote access….” I am guessing the answer for Target is no…..unless maybe they were using RSA tokens that were compromised….
Earl,
I’m certain that Target had follow the same PCI-DSS regime as everyone else.
And honestly, if you’ve been involved at all in PCI compliance work, it is often largely a joke. So much of it is simply allowed to be self-reported that it’s easy to have violations and remain “compliant” on paper.
On top of that I’ve had security consultants tell me that even disclosed violations can be “okay” as long as you have some kind of plan on the books to eliminate/mitigate them. Which seems like a bad joke to me.
PCI-DSS like all security is only as serious as any other element of security. You either make it a priority and do it as right as you can, or you don’t.
Thank you, excellent report.
I’m waiting for a techno-thiller novel to come out where a large corporation hires a spec ops team to go in and eliminate the cyber-crime scumbags. There is no reason that they should be untouchable like the Somila terrorists opps sorry – poor oppressed fishmen.
Ray, this is one-time I’d love to see the NSA bring their full power to bear and thump these scumbags, after all, they supposedly see and know all as it transpires live over the internet….
The agency takes care of us in more ways than most people care to imagine. If they did take care of these scumbags – or any other for that matter, I highly doubt they would acknowledge the feat.
They would probably put in an anonymous call to the police or other federal agency in charge ( and who is motivated and not necessarily corrupt) of the area, and let them know who the person is, what they have been doing. Plus as a bonus, if they hurry up – there is significant evidence neatly stacked in folders for them to look over.
If the agency would take care of “acceptible select issues” then its hard to understand what the mentality of acceptance is, since there seems to be some resistance towards the agency.
Like anything else that is controlled by the covertment (yes a political sort of twist on the dark side of their abilities) it will probably be dropped and forgotten before anything is seriously done to any federal agency. Now, they will just carry on, but with a tighter grip on the ways they do “business”.
I’m given to understand that the NSA is a major buyer of exploits. Why would they thump their suppliers (or their suppliers other customers). Bad for business.
I have been a regular follower of your blog. Excellent piece of investigative work forcing companies to disclose data compromise.
In your experience, what do you feel the role of Bank Regulator, say like Fed or OCC in USA or single regulator in case of other jurisdictions. Do you feel they can enforce certain risk management measures through banks ?
For what it is worth, some credit card issuers are now issuing cards with the EMV chip (upon request). I had asked for one from BofA a few weeks ago, and it came in the mail a few days ago. But not every card issuer is doing this yet.
Having the card is one thing – most of the POS terminals in the U.S. don’t yet support a chip on the credit card. That might start to change – in October 2015, the liability starts to shift, so that a merchant that has not yet upgraded the POS terminals to support the chip
That being said, U.S. card issuers are (for now anyways) using “Chip-and-signature” and not “Chip-and-PIN”. This means a couple of things – if you were in Europe, you would still probably have difficulties purchasing a train ticket from an automated kiosk. And to me it isn’t clear what happens at something like a gas pump where there isn’t a place to sign (but the liability shifts for fuel dispensers is Oct 2017).
Eric I can tell you US cards with the chips do work in Europe at kiosks (without a PIN). I travel frequently to UK and upgraded to a card with a chip just for buying tickets and adding credit to my Oyster card from the Kiosk). You are correct, US EMV cards don’t have a PIN (I called to get one and they said no). But I will say when you use it in person in UK they really do scrutinize your signature on the back, which I NEVER see here in the States.
Rick – Ahh thanks – that’s good to know. In a few weeks we will be in the UK, and it was mainly in preparation for the trip that I had requested the chip card in the first place.
Some of the online things that I have read suggested that there would in fact be problems at some kiosks, but if I can get an Oyster card from a kiosk, that basically solves my immediate needs.
Perhaps I misunderstand, but …
Some US EMV cards do have PINs and use of those PINs is mandatory in the parts of the world where I’ve traveled. Never been to the UK, however, so cannot speak to that.
OTOH, in Amsterdam at the airport, using the card to buy train tickets is required. Otherwise, get in line and wait for a human to buy a ticket.
Used the same EMV card in South Africa and Singapore – PIN required.
In Turkey near toursist locations, the EMV card was not needed, but anywhere outside tourist areas our non-EMV cards were refused, flatly. This lead to embarrassment on a few occassions.
I got an e-mail breach notification via my work e-mail address from Target the other day (or to be more exact from target.bfio.com). Odd thing is I have never shopped online at Target, have never provided an e-mail address to them, and if I had it wouldn’t have been my work e-mail address. I do not have a Target credit card and did not use any other card at Target during the breach period.
Search online and you’ll find others complaining that they are getting notifications using e-mail addresses that were never shared with Target. Some people don’t even shop there.
Bfio.com it turns out belongs to Epsilon. What better way to manage a data breach than to use a marketing company that itself had a massive data breach and likes to send phishy looking e-mails.
Forbes.Com seems to agree with you:
http://www.forbes.com/sites/jameslyne/2014/01/07/targets-latest-failure-and-how-to-spot-a-scam/
Kudos to OldSchool for posting that James Lyne / Forbes link about the suspicious Target e-mail using TargetNews@target.bfi0.com.
On Nov.30,2013 I saw a email from walmart.com and went to read it because I have no walmart account,credit card and never ordered anything from walmart online. Then I had 4 correspondance about this from and to walmart help.com. 1 email tated i changed my ersonal informaton and password. I called them in a panic and they could give me no information on why and what this was about. Iasked them to report this to their secrity and I was told they had no security to tell just the billing dept. I TOLD THE THEY ARE PROBABLY THE NEXT ‘TARGET’ SITUATION AND PERHAPS I MIGHT BE ALERTING THEM. The person on the phone just kept saying aha ,O.k. After about 30 min. and talking to the “manager” I GOT NO WHERE AND STILL NO RESPONSE. I AM WORRID. I FEEL VIOLATED AND ON TOP OF THAT THIS STORE CALLED WALMART IS THE LEAST BIT CONCERNED. WHAT TO DO? It has been 4 days and no response of any kind. I told them they would see this on tne news and that the big cheese would then say something. The lady just asked if there was anything else and ready to blow I asked her name towrit down in which she did not think she could and sai thank you and hung up. I am beyond angry about this. Any help or suggestions? Thank you for your attention.
Debra,
I would call/email Corporate HQ and provide all the details with as much info as possible
I get emails like this all the time. If you dig into the email enough you will discover that nobody at WalMart had anything to do with this. It came from a criminal that is trying to get you to click a link which will then steal from you. Either your computer will be stolen – used without your permission for sending spam, or your information on the computer will be stolen.
Simple solution: do not click that link. Don’t open that attachment. Email is not secure, it is not reliable and most of what you get is not to be trusted.
Thanks for your advice and comments on “Tools for a Safer PC” – it’s was a useful resource and I’ve bookmarked a few of them for future reference.
Are there any other antivirus blogs (or web resources in general) that you can recommend to me?
Cheers!
Would the perpetrators have been able to capture any payment card data if P2PE were in place with payment card encrypted at the PIN pad and not decrypted until it reached the acquirer?
>payment card encrypted at the PIN pad and not decrypted until it reached the acquirer
This would have made things much more difficult. It would also require that the card swipe terminal with encryption not have any field-firmware upgrade capabilities without physical access to authorize.
The problem in the US is the payment terminals are generally owned by the merchant or leased to the merchant. So one day they get a call saying they have the opportunity to update their payment terminal to accept NFC (contactless) payments – it is only $2500. Nope, not happening. Same thing with every new “feature” coming down for payment terminals.
Now my understanding is that in UK and EU generally the terminals are owned by the banks – not credit card processing companies but the bank where the merchant has an account. The bank can change these things out whenever they want and probably gets a good price when they buy them by the thousands. This is partly why NFC payments gained ground in EU but not the US.
For the most part, the merchants do not have huge cash reserves lying around to spend $2000 and up on a fancy new terminal – that only the cashier uses – when they have something that works. Large retailers these days are pushing the customer to “use” the terminal, but that doesn’t account for the smaller shops.
Now we are going to get a government requirement that all the terminals be replaced. Huge windfall for a few terminal manufacturers, little benefit for small shops with dial-up terminals that have been working fine since 2000. Yes, for the big merchants with networked POS systems this may be a benefit, but that isn’t where the huge windfall comes from for the terminal makers.
Quote: little benefit for small shops with dial-up terminals that have been working fine since 2000
Actualy, those little shops with dail-out pinpads would not be effected by this walware issue becuase the credit card data would not be on the cashier workstation. That authorization request is via dailup and not the retailers computer network.
Dear Debra,
HUH??
That reads too much like a parody of a very non-technical person being amazed at and overreacting to simple spam.
If this was an IT industry only forum, I’d be tempted to extend the joke by suggesting a call to the FBI; I’d know that other participants would get it. Problem is, there’s been enough news coverage bringing non-IT folks to Brian’s pages here that I fear a prank would misfire and cause someone to actually call law enforcement over a mere spam message. I just want to be careful.
I wonder if law enforcement really care because I have reported a site call GDG-inc.com that offer me a job and I accepted it. only after looking more into the work I was receiving I discover that innocent people was being rob. Luckily one of the packages had a billing address on it, so I decided to contact this individual and later found out his American Express card was use to purchase items that was being ship overseas. I alerted authority and have yet to be talk to about vital information that can be use before it’s too late.
any chance you happened to get a copy of the report for md5: f45f8df2f476910ee8502851f84d1a6e it comes up as also having the BackupU$r password in threat expert
Actually, I do.
http://krebsonsecurity.com/wp-content/uploads/2014/01/FireShot-Screen-Capture-2148-ThreatExpert-Report-_C__Documents-and-Settings_XP_My-Documents_Downloads_ThreatExpert-Report_htm.png
Thanks for sharing.
Pretty pathetic that the hackers gained prolonged and continuous access to Target’s internal network, and no one had a clue.
What type of “security” did they have in place that no one realized something was off? This is the problem when relying heavily on virtualization and digital updates in POS systems. Manual spot-checking goes out of the window. Though computers can do everything human can (and 99% of time, much better), it’s situations like this that prove that there’s always the need for a REAL PERSON to go into the system and make sure everything is running a-ok.
Particularly through the holiday season, when hackers really love to strike, you’d think that corporations would be extremely sensitive with the security of millions of their consumers.
I’m almost certain that when it comes time for the news to break about “how/why this happened”, the terms discussed will lack the detail seen in this article.
Something tells me that there’s even more to the story that’s been discovered right now. I’m betting on an even larger number than 110 million. I’m also betting on the same thing happening again at another retailer soon, under the same terms. Wouldn’t be surprised.
Great work Brian.
Interested to hear about the other retailers. We recently had a company card breached, and it had only been used at a handful of big name retailers none of which are named Target.
When I purchase beer or wine (in CA) at Target, they ask for my driver’s license then swipe it through the card swipe on the register. I assume the bad guys have that data, too. Does anyone know if that data is being sold on the black market?
McAfee’s analysis of the malware:
http://blogs.mcafee.com/mcafee-labs/analyzing-the-target-point-of-sale-malware
Oh, whoops, Brian already posted that on Twitter. Oh well…
From the start of McAfee’s report: “In the last 24 hours, we have started to piece together more and more detail on the malware that is allegedly tied to the campaign against Target. ”
Is it really that hard to link to this blog, McAfee, or be honest about what prompted you to draw those links?
Heh… I was wondering why they didn’t cite you myself. I think I’ll post this thread’s URL there, just to prompt them.
Ok, nevermind. I thought I had an account to that site’s blog, but I don’t. And there’s no register link.
Oh well…
Great insight, Brian.
Was the malware in the ECR or actually in the card swipe device itself?
My heart is not really into posting today but because it is tradition, I must mention that it is not fair to call the people on the Wagner VK friend list ‘a hacker gang’. Yes it was Group-IB but is there proof that this is really a ‘hacker gang’ not to mention that their ‘research’ is from about a year ago? Where is the connection chain from Ree to antikiller to Wagner by the way, I did not see it?
Aside from this whole breadcrumbs portion ;-), good article.
The malware isn’t BlackPOS, it’s a rudimentary track2 RAM scraper that’s been around for years. Xylitol looked at it earlier this year: http://www.xylibox.com/2012/03/pos-carding.html
BlackPOS is http://www.threatexpert.com/report.aspx?md5=89bffc273bd0b44f352c75db9152c35e
(a) If the current security intelligence consensus is that “most firms are either compromised or do not know about it” (b) Most of all the name brands/Fortune 500 have been already hacked and (c) Target malware/process was sophisticated enough to evade the AV/Firewall tools then:
(1) shouldn’t the merchant (Target) be given clemency ?
(2) Show mercy to these merchants by not bombarding with massive civil law suits (already 70)
(3) Our govt should have a clause to protect these merchants from frivolous law suits, penalties etc, especially Small/Medium business community.
(4) Is it another door opener for our already BIG nosy government to step into the affairs of business community by challenging the PCI Compliance efforts, that is not the only framework that gets compromised ?
Time has come that our government to step in to protect our businesses and not pillage through an already exhausted victim.
Receiving your PCI ROC is a point in time nod of approval based on the assessment of (typically) one individual – the QSA. I question the assertion that ‘most’ Tier 1 merchants are doing self assessments. What I do know is that each QSA interprets the PCI-DSS in different ways. Shortcomings in a system can be managed with compensating controls – sideline quarterbacks are always good at saying ‘if I were doing the job’ but how many people really understand all the mechanisms in a Tier 1 merchant’s infrastructure? It’s a trade off of work to be done, time to get it done and money available for the effort. ‘pegr’ gave a short list of things assumed were missing of failing at Target, to which I would add application white-listing, meaningful event log parsing, and administrative access controls and logging.
Non-technical person here. Out of curiosity, what would you recommend someone with a Target card do? I’ve been tracking the card online, of course, and haven’t seen any unauthorized purchases, but am I going to have to do that forever? Am I better off just canceling the card? Will that be a hit on my credit rating? Target keeps sending me soothing emails, but at this point I trust them about as far as I can toss a caber.
Wyn – if you cancel the card (close the account) it might affect your credit rating. Not for sure but it might.
It would be better for you to get the card company to re-issue the card. You get a new number and piece of mind. But no ding on your CR.
“BlackPOS” was discovered by McAfee a year ago …
http://blogs.mcafee.com/mcafee-labs/vskimmer-botnet-targets-credit-card-payment-termina
From a PCI compliance perspective, I can’t see how Target could have been fully compliant.
1. A code/security audit is required on any software updates to the POS (or any PCI system). Either that didn’t happen or the malware was inserted after the audit. If that’s the case, File Integrity Monitoring should have caught it.
2. The system the attackers accessed remotely had to have some connection to the Cardholder Data Environment. That means that two-factor authentication should have been in place.
3. Network Intrusion Detection should have caught that much data with sensitive values (ie 16 digit number that passes the luhn check) leaving the network.
PCI compliance however, relies on a QSA hired by the retailer. If you want your customer to be happy and keep their business, there is an incentive to interpret the PCI-DSS standard in a more ‘generous’ fashion. This is true for some (but not all) QSA’s I’ve worked with in the past. One may accept “Log into the firewall with your AD credentials and then log into the system with your AD credentials” as two-factor for example. Another QSA may not accept that (rightly so).
If PCI is going to provide real security value, rather than simple compliance to avoid fines, QSA’s should be independent, paid by the PCI council and have no conflict of interest with the retailer. Beyond that, rather than ‘interpretation’ the PCI standard, the QSA’s should have a very strict and clear standard to judge against.
Just a few thoughts on the PCI comments here. Firstly, if you are a tier 1 merchant you cannot self certify against PCI. It requires an external assessment (note assessment, not audit, the two terms are used and they are very different things) by a QSA company. It cannot be done by an ISA working for the merchant. PCI has and always will be the absolute minimum for ensuring a basic level of security for the card holder data environment and nothing more. It makes no attempt to look at the wider security issues that any merchant faces. The responsibility for network security lies with the merchant, not the QSA.
Speaking as a QSA I can tell you that if any of my clients believes that PCI is all that is required for network security then I advise them to seek a new CTO / CISO / Security Manager immeadiately.
PCI does allow compensating controls (as does ISO 27001 and many other standards) simply because not every eventualtiy can be accounted for and no company should be forced to bend their working practices to fit a prescribed standard.
As an IT security professional for more than 20 years the fact that I am still having basically the same conversations with clients if slightly depressing. The fact is that in many cases the risks are simply not understood and few companies carry out the effective risk assessment work required to quantify those risks in the first place. Even fewer are then prepared to commit the kind of budget required to do a proper job securing their network (and maintain it). We constantly work on the ‘negative positive’ outcome – in other words, if nothing happens, we’ve done our job! Problem is that is a hard sell into many companies.
Am I surprised at what happened at Target? No, not in the slightest. Given that in my experience it can take many months or even years for these attacks to be detected, I just wonder how many more are out there…
How far along is the adoption of Chip-style payment solutions in the US? I cant recall the last time I used the magnetic strip here in Europe.
So am I expected to believe that 33% of Americans shop at Target using a credit card?? Really?? Or were there 110 million transactions effected? I don’t see my grand children with credit cards yet, and not all Americans (315 million) could possibly shop at 2000 Target stores!?!?
I am in technology and appreciate facts, however I am finding regardless of where you turn “Propaganda” is showing up every where.
It sounds like Target could use a product like AppGuard, which prevents zero-day exploits….
EMV / chip cards would have limited the damage but not completely stopped this kind of attack.
Yes mag stripe is archaic and the US should have dumped it years ago but they didn’t. You could argue the whole set up with credit card payments is way behind the times. It needs a far more radical approach now.
Forgot to say on my previous post – great reporting and investigative journalism Mr Krebs!