For the second time this month, Adobe has issued an emergency software update to fix a critical security flaw in its Flash Player software that attackers are already exploiting. Separately, Microsoft released a stopgap fix to address a critical bug in Internet Explorer versions 9 and 10 that is actively being exploited in the wild.
 The vulnerabilities in both Flash and IE are critical, meaning users could get hacked just by visiting a compromised or booby-trapped Web site. The Flash patch comes just a little over two weeks after Adobe released a rush fix for another zero-day attack against Flash.
The vulnerabilities in both Flash and IE are critical, meaning users could get hacked just by visiting a compromised or booby-trapped Web site. The Flash patch comes just a little over two weeks after Adobe released a rush fix for another zero-day attack against Flash.
Adobe said in an advisory today that it is aware of an exploit that exists for one of three security holes that the company is plugging with this new release, which brings Flash Player to v. 12.0.0.70 for Linux, Mac and Windows systems.
This link will tell you which version of Flash your browser has installed. IE10/IE11 and Chrome should auto-update their versions of Flash, although IE users may need to check with the Windows Update feature built into the operating system.
If your version of Flash on Chrome (on either Windows, Mac or Linux) is not yet updated, you may just need to close and restart the browser. The version of Chrome that includes this fix is v. 33.0.1750.117 for Windows, Mac, and Linux. To learn what version of Chrome you have, click the stacked bars to the right at of the address bar, and select “About Google Chrome” from the drop down menu (the option to apply any pending updates should appear here as well).
The most recent versions of Flash are available from the Adobe download center, but beware potentially unwanted add-ons, like McAfee Security Scan). To avoid this, uncheck the pre-checked box before downloading, or grab your OS-specific Flash download from here. Windows users who browse the Web with anything other than Internet Explorer will need to apply this patch twice, once with IE and again using the alternative browser (Firefox, Opera, e.g.).
As I noted in my Tools for a Safer PC primer, blocking Javascript by default in your Web browser is the best way to block browser-based attacks — including these Flash zero-day flaws. Several Mac users have written in recently to ask about the whereabouts of a Tools for a Safer Mac post, and while that’s a good idea (and a post that may soon be coming), script-blocking via extensions/add-ons like NoScript and NotScripts is an approach that works across multiple OSes.
Another great cross-platform approach to blocking Flash (and Java) content by default is Click-to-Play, a feature built into Google Chrome, Mozilla Firefox and Opera (and available via add-ons in Safari) that blocks plugin activity by default, replacing the plugin content on the page with a blank box. Users who wish to view the blocked content need only click the boxes to enable the Flash or Java content inside of them. Check out this post for more details on deploying Click-to-Play.
MICROSOFT FIX-IT TOOL
 Microsoft has released a security advisory and a FixIt shim tool for a previously unknown zero-day vulnerability in Internet Explorer versions 9 and 10. Microsoft says it is aware of “limited, targeted attacks” that attempt to exploit a vulnerability in Internet Explorer 10. Only Internet Explorer 9 and Internet Explorer 10 are affected by this vulnerability. Other supported versions of Internet Explorer are not affected.
Microsoft has released a security advisory and a FixIt shim tool for a previously unknown zero-day vulnerability in Internet Explorer versions 9 and 10. Microsoft says it is aware of “limited, targeted attacks” that attempt to exploit a vulnerability in Internet Explorer 10. Only Internet Explorer 9 and Internet Explorer 10 are affected by this vulnerability. Other supported versions of Internet Explorer are not affected.
Microsoft says it is working on an official patch, but that in the meantime IE users should consider taking advantage of a new FixIt solution. According to Microsoft, applying the Microsoft Fix it solution here prevents the exploitation of this issue.
Microsoft warns that IE users should make sure they have the latest version of IE before appyling this FixIt solution (that means a visit to Windows Update). Also, the company says that after you install this Fix it solution, you may experience increased memory usage when you use Internet Explorer to browse the web. This behavior apparently occurs until you restart Internet Explorer.




Thanks Brian!
Got your Flash upd. warning 5 minutes after your post!
You are the NORAD of cybersecurity! 🙂
Thank you kindly, good sir
Hey Brian, that second link to the direct downloads without clingons is not installing the correct version, Win 7, anyway.
Which version is it trying to advise/install? Just curious?!
According to the MS Advisory statement, Win7 users appear not to be affected, at least directly. It’s unclear from the advisory language whether the flaw can be exploited under Win7 through one of the Office versions mentioned. Any insight on that, Brian?
https://technet.microsoft.com/en-us/security/advisory/2755801
“Microsoft is announcing the availability of an update for Adobe Flash Player in Internet Explorer on all supported editions of Windows 8, Windows Server 2012, Windows RT, Windows 8.1, Windows Server 2012 R2, and Windows RT 8.1. The update addresses the vulnerabilities in Adobe Flash Player by updating the affected Adobe Flash libraries contained within Internet Explorer 10 and Internet Explorer 11. ”
“This update is not cumulative and requires that cumulative update 2916626, released on January 14, 2014, be installed.”
“If I don’t use Internet Explorer, do I still need to apply the update?
Yes, other applications, such as Microsoft Office 2007 and Microsoft Office 2010, can invoke Adobe Flash Player in Internet Explorer. Microsoft recommends that customers apply the update immediately.”
Flash is built into Windows 8, 8.1, RT, and Server 2012 all with Internet Explorer 11 and is provided directly by Microsoft through Windows Update.
In order to bypass Address Space Layout Randomization (ASLR) protection in Windows, this attack relied on either one of the following configurations:
*Windows XP
*Windows 7 and Java 1.6
*Windows 7 and outdated Microsoft Office 2007/2010
Good posts JimV and Ver1tas. KOS readers will appreciate this! I would also like to add, that Chrome stepped up to the plate this time, (and on time), to update to Version 33.0.1750.117, which should plug any vulnerability there.
This update cycle went smoother than last time. Chrome and Firefox were crashing a lot after that last update – oddly enough, I think it was flash getting into a fight with some other plugin, because the crash report would be different each time. It seems to be stable now!
Couldn’t get to this article this morning – I like Brian’s links, and I’m lazy, however he has given me good habits and just going the the result of a “Get flash” search did the trick. Brian AND Adobe have made this a little easier. I have no idea what happened to the idea of auto-update on Adobe, it hasn’t worked for quite a while. I keep saying I’m going to try Ninite some day but never seem to get around to it.
Oddly, the Adobe Flash automatic updates do seem to work with Windows XP although it can take a while for them to become operational. Windows 7 is another matter: they do not seem to work at all. The grayed radio buttons in the control panel Flash Player advanced tab are probably significant. This might be OK for IE 10/11 users but not for those whose favourite browser uses plugin Flash.
IE’s Flash Player will not update via Windows Update on Win7 systems, unlike Win8.x where it is bundled into Windows by Microsoft. So Win7 users will need to either update Flash Player manually or hope that Adobe’s Flash Player updater will get the Bat-Signal and prompt them.
Oh, and on a tangential note: if you’re a reader here, you probably have an above-average tolerance for security at the expense of minor inconveniences, so if you use IE (or even if you don’t) I’ll suggest enabling ActiveX Filtering by clicking the gear icon at the upper-right, and choosing Safety > ActiveX Filtering.
You can whitelist sites where you want an ActiveX control, such as Flash Player, to be allowed. That’s done by clicking the blue slashy-circle symbol in the address bar. We use ActiveX Filtering full-time at work and the employees have not lynched me yet 😉 so maybe give it a try.
Given that I use/maintain multiple machines, my usual approach is to uninstall rather than try and keep uptodate. Maybe only one or two machines get the update. I would rather do away with the whole thing entirely, but that makes the web rather difficult to use.
Windows and Mac OS X builds of Flash Player 12.0.0.44 and earlier,
AND
Flash Player 11.2.202.336 and earlier for Linux, must be upgraded to fix a trio of bugs.
Brian wrote “Microsoft has released a security advisory”
It is not mentioned at the Microsoft advisory Brian referenced, but installing EMET will block the exploit. EMET 4.1 is the current version.
http://blogs.technet.com/b/srd/archive/2014/02/19/fix-it-tool-available-to-block-internet-explorer-attacks-leveraging-cve-2014-0322.aspx
IE11, another solution to the exploit, is still not fully supported by many websites, as well as having a few GUI problems (e.g. the font size of the pushbuttons on the Organize Favorites dialog is too small).
I had forgotten about upgrading to 4.1 until I saw a reminder here at KOS. It was somewhat untested or in beta back when I got the older version. I like the new tool, it lets you import the previous settings during installation, so you don’t have to go through any rigmarole.
I have to admit, though, the recommended settings are probably just fine for most newbies! I’ve never understood why only Windows media player is checked as running EMET, when the application console shows all protections checked on other apps?! I’m not worried though, even the old one still threw EMET blocking alerts if there was something wrong with a web page.
Even US-Cert is warning about this 0- Day threat
Brian,
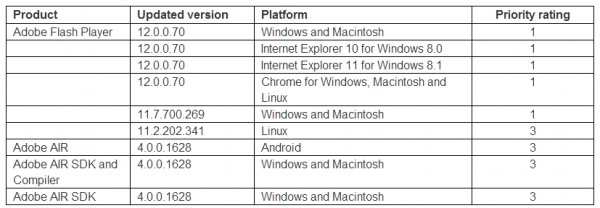
Your table for Flash versions has an extra line. Under Platform, Windows and Macintosh is listed twice, once with a very old version listed.
How does blocking JavaScript have anything to do with blocking Flash? Aren’t they apples and oranges?
Blocking JavaScript is a great way to increase security, but is it really practical?
It is true they are different “animals” – I don’t know – I’ve used No Script, and similar extensions on different browsers and I’d say it’s practical as far as you can be, anyway. If I don’t need the script or flash to run. I just let them block it. If not, I simply either double click the flash video window, or allow java-script to run in the allowed scripts menu for No Script. You can set it to remember that setting for that URL, or do a one time allow, just for utility. It doesn’t seem all that hard to do for me. For folks who are even lazier than I am. They can let Avast’s script blocker watch out for them. It only blocks malicious scripts automatically. Usually, now days, not every page load at an infected website serves up malicious scripts. So if I can’t get an object to perform on a web site, when using Avast, I simply reload the page, and voila! I get functionality. I’d say it is practical, by my definition – YMMV
Of course you probably already know this – I am just providing the information for those who may not be familiar with these solutions.
It’s not my table. That came straight from Adobe.
Most of the attacks that will target some kind of browser plugin will use malicious Javascript. Not apples and oranges at all.
Is blocking scripts ideal? Of course not. Is it great for Grandma? No way. Is it the best approach from a security perspective short of completely uninstalling the vulnerable plugin/add-on? You bet.
The Adobe security bulletin says
“For users of Flash Player 11.7.700.261 and earlier versions for Windows and Macintosh, who cannot update to Flash Player 12.0.0.44, Adobe has made available the update Flash Player 11.7.700.269, which can be downloaded here.”
But there is no “here” link either in this text or at the bottom of the page. Neither is there an explanation of why someone could not update. And 120.0.0.44 is not even the latest version.
Version 11.7.700.261 is also not listed here:
http://www.adobe.com/software/flash/about/
Who knows what Adobe is trying to say.
Check out the table at http://www.adobe.com/software/flash/about/
It has more info on the different versions for each platform, though it doesn’t mention 11.7.x and I can’t find that version on the download center either…
A way to increase usability while maintaining safety for me has been to run 2 browsers. Firefox with noscript and HTTPS labs HTTPS everywhere (for surfing in the wild.) And another browser (fully patched) I use Safari, for just visiting banking and financial sites via direct URL. Safari goes nowhere else (god help me if the bank loads malicious XSS!)
Anyways, it’s a good compromise and increases the spousal acceptance factor.
Doh! What I meant to say was HTTPS Everywhere, published by the EFF -> https://www.eff.org/https-everywhere
They have an opt-in project called SSL observatory.
On the flip side, see how many things use scripting everywhere you go. With it blocked I’d say 2/3 of websites have at least something that doesn’t load right, but often it is unnecessary anyway.
Yep, and funny thing is… you don’t really miss that much. No Auto video loads? Oh Snap!
Come on guys, advising users to turn off JavaScript by default as a means of safely using the web? Seriously? This is the sort of advice you would expect in 2005 not 2014
What kind of experience do you think users will have when they browse the web without JavaScript?
There isn’t a single email service that doesn’t depend on JavaScript being enabled in order for it to be usable
JavaScript isn’t merely optional eye candy for many web services any more – it’s integral to their functionality
The root cause of these security flaws (again and again and again) are Flash and Java – these are the two technologies you should be advising users not to install in their browsers
Using the NoScript browser extension, I can turn on and off script processing based upon the website. Thus I can enable it for sites that I trust and where it is really needed for basic functionality.
And I can leave it off by default for other sites which helps to prevent drive-by infections.
Andy Walpole: “advising users to turn off JavaScript by default as a means of safely using the web? Seriously? This is the sort of advice you would expect in 2005 not 2014”
Turning off active scripting is among Microsoft’s own workarounds in its advisory for the IE vulnerability here:
“Vulnerability in Internet Explorer Could Allow Remote Code Execution”
http://technet.microsoft.com/en-us/security/advisory/2934088
“By default, Internet Explorer on Windows Server 2003, Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, and Windows Server 2012 R2 runs in a restricted mode that is known as Enhanced Security Configuration. This mode mitigates this vulnerability. ”
Sadly, only Windows server OSs which default with Internet Explorer Enhanced Security Configuration (ESC) have active scripting disabled, by default. With Windows client OSs, such as Windows XP and 7, its more difficult to manage a whitelist of one’s legitimate and frequently-visited web sites (see the advisory for details).
Java is definitely something the vast majority of people don’t need, but Flash is still heavily used on the web. I disable most plugins completely except for Flash, and I use NoScript to prevent Flash from loading by default. As for disabling JavaScript, using a tool like NoScript works, but it can be a bit annoying at times. It’s a security/usability tradeoff that I gladly accept, but I agree that most people will not.
Hi Brian
Solid advice in the article above, many thanks.
The way I see it, the major software players you mention are seriously struggling to cope with zero-day threats.
As it seems relevant to your piece I thought I would draw your attention to the info sec provider Glasswall Solutions (http://www.glasswallsolutions.com/) who claim that they can provide impenetrable defence against such threats.
Their CEO, Greg Sim will be attending the RSA event next week in San Fran if you wanted to have a chat with him.
Many thanks for your time.
Sam.
Time to fire up Ninite Pro…
Adobe pushes out critical Flash update – the second zero-day hole of the month
hxxp://nakedsecurity.sophos.com/2014/02/21/adobe-pushes-out-critical-flash-update-second-zero-day-hole-of-month/
Hello, Brian! You are indeed the NORAD of cybersecurity. Your blog rescued me from a very bad Flash intrusion that no one seemed to know how to fix, including Adobe at the time — and saved me from a frightening Cyberlocker attack. Now, windows 9.0 and 10.0? Unbelievable. I resisted going to 10.0, picked 9.0 and unloaded that when it acted hinky. My IE browser may not be the latest, but it’s old enough to be de-bugged, and it doesn’t ATTACK me. Thanks for everything.
Andy Walpole wrote:
‘There isn’t a single email service that doesn’t depend on JavaScript being enabled in order for it to be usable.’
I can mention 2 that have been around for some time:
http://www.fastmail.fm
http://www.safe-mail.net
The contest started out being great fun but devolved into
all sorts of infighting, faked votes, and terrible reviews that were posted for no other reason than meanness.
s computer, it will not allow setting up of other
antivirus programs such as Norton, Mc – Afee or Kaspersky Antivirus, even after its uninstallation.
you will be a little worried, but don’t be – you now need
to go to.
One correction although Chrome for Linux is available with the recommended Flash version, Linux does not have any 12.x versions available. Adobe stopped development on their Linux version. The current latest Linux Flash player is 11.2.202.341.
Adobe Flash will always be a major security weakness no matter how many times they patch it. The best patch Adobe could realease would be to finally put Flash to rest.
Brian: You need an article about the iOS (6/7)/OS X (10.9.0-10.9.1) SSL bug.
In short, users running those platforms without the latest update are vulnerable to MITM attacks against most network enabled software (anything that uses the OS networking / SSL stack in default configurations – which is probably everything except Chrome and Firefox).
If only Adobe’s automatic updates were even adequately rapidly deployed. You can wait for days. I would say that Adobe makes tolerably useless provision for distribution of these critical updates. The consumer level computer user deserves better.
“Microsoft releases fix for Windows Update corruption errors”
http://www.zdnet.com/microsoft-releases-fix-for-windows-update-corruption-errors-7000026582/
“This fix may appear at some point in Windows Update itself, but it is not there as of today.”
Just a heads up.
I wish Microsoft would make these Fix-it hotfixes deployable silently through WSUS or some other means. Asking 80 random people to take the time to install this is pointless in our environment.
I got the impression that 2934088 (the FixIt download) was intended as a temporary workaround, not a permanent patch. If I’m correct, I can see why it’s not pushed via WSUS or normal Windows Update.
Thanks Adobe and Microsoft, security like yours IMO is like throwing a sausage down a hallway.
The WordNazi grants you a waiver on the phrase “hand-waiving” but it will go on your permanent record.
This seems to be another good reason to look into a safer platform, such as Chrome OS, which automatically keeps you ahead of threats like this.
Sure, if you don’t mind all of the background hoovering embedded in its processing.
Yum, Chrome OS is the most secure desktop OS in the world for a reason.
You should mention that Apple also updated IOS 6.x to address this security flaw.
I needed to thank you for this excellent
read!! I certainly enjoyed every bit of it. I have you book marked to look
at new stuff you post…