The breach at Target Corp. that exposed credit card and personal data on more than 110 million consumers appears to have begun with a malware-laced email phishing attack sent to employees at an HVAC firm that did business with the nationwide retailer, according to sources close to the investigation.
 Last week, KrebsOnSecurity reported that investigators believe the source of the Target intrusion traces back to network credentials that Target had issued to Fazio Mechanical, a heating, air conditioning and refrigeration firm in Sharpsburg, Pa. Multiple sources close to the investigation now tell this reporter that those credentials were stolen in an email malware attack at Fazio that began at least two months before thieves started stealing card data from thousands of Target cash registers.
Last week, KrebsOnSecurity reported that investigators believe the source of the Target intrusion traces back to network credentials that Target had issued to Fazio Mechanical, a heating, air conditioning and refrigeration firm in Sharpsburg, Pa. Multiple sources close to the investigation now tell this reporter that those credentials were stolen in an email malware attack at Fazio that began at least two months before thieves started stealing card data from thousands of Target cash registers.
Two of those sources said the malware in question was Citadel — a password-stealing bot program that is a derivative of the ZeuS banking trojan — but that information could not be confirmed. Through a PR firm, Fazio declined to answer direct questions for this story, and Target has declined to comment, citing an active investigation.
In a statement (PDF) issued last week, Fazio said it was “the victim of a sophisticated cyber attack operation,” and further that “our IT system and security measures are in full compliance with industry practices.”
There is no question that, like Target, Fazio Mechanical was the victim of cybercrime. But investigators close to the case took issue with Fazio’s claim that it was in full compliance with industry practices, and offered another explanation of why it took the Fazio so long to detect the email malware infection: The company’s primary method of detecting malicious software on its internal systems was the free version of Malwarebytes Anti-Malware.
To be clear, Malwarebytes Anti-Malware (MBAM) free is quite good at what it’s designed to do – scan for and eliminate threats from host machines. However, there are two problems with an organization relying solely on the free version of MBAM for anti-malware protection: Firstly, the free version is an on-demand scanner that does not offer real-time protection against threats (the Pro version of MBAM does include a real-time protection component). Secondly, the free version is made explicitly for individual users and its license prohibits corporate use.
Fazio’s statement also clarified that its data connection to Target was exclusively for electronic billing, contract submission and project management. The company did not specify which component(s) of Target’s online operations that Fazio accessed externally, but a former employee at Target said nearly all Target contractors access an external billing system called Ariba, as well as a Target project management and contract submissions portal called Partners Online. The source said Fazio also would have had access to Target’s Property Development Zone portal.
According to a former member of Target’s security team who asked not to be identified, when a work order for an external vendor is created, the payment is collected through the Ariba system: Vendors log into Ariba, complete the necessary steps to close out the work order and they are later paid. But how would the attackers have moved from Target’s external billing system into an internal portion of the network occupied by point-of-sale devices? The former Target network expert has a theory:
“I know that the Ariba system has a back end that Target administrators use to maintain the system and provide vendors with login credentials, [and] I would have to speculate that once a vendor logs into the portal they have active access to the server that runs the application,” the source said. “Most, if not almost all, internal applications at Target used Active Directory (AD) credentials and I’m sure the Ariba system was no exception. I wouldn’t say the vendor had AD credentials but that the internal administrators would use their AD login to access the system from inside. This would mean the sever had access to the rest of the corporate network in some form or another.”
Last week’s story about Fazio’s role in the attack on Target mentioned that Target could be facing steep fines if it was discovered that the company was not in compliance with payment card industry (PCI) security standards. Among those is a requirement that merchants incorporate two-factor authentication for remote network access originating from outside the network by personnel and all third parties.
Another source who managed Target vendors for a number of years until quite recently said that only “in rare cases” would Target have required a vendor to use a one-time token or other two-factor authentication approach.
“Only the vendors in the highest security group — those required to directly access confidential information — would be given a token, and instructions on how to access that portion of the network,” the source said, speaking on condition of anonymity. “Target would have paid very little attention to vendors like Fazio, and I would be surprised if there was ever even a basic security assessment done of those types of vendors by Target.”
But according to Avivah Litan, a fraud analyst at Gartner, Target wouldn’t have needed to require vendors to use two-factor logins if the company believed it had taken steps to isolate the vendor portals from its payment network.
“In fairness to Target, if they thought their network was properly segmented, they wouldn’t have needed to have two-factor access for everyone,” Litan said. “But if someone got in there and somehow escalated their Active Directory privileges like you described, that might have [bridged] that segmentation.”
OPEN-SOURCE INTEL
Many readers have questioned why the attackers would have picked on an HVAC firm as a conduit for hacking Target. The answer is that they probably didn’t, at least at first. Many of these email malware attacks start with shotgun attacks that blast out email far and wide; only after the attackers have had time to comb through the victim list for interesting targets do they begin to separate the wheat from the chaff.
But Target may have inadvertently made it easier for the attackers in this case, in part by leaving massive amounts of internal documentation for vendors on its various public-facing Web properties that do not require a login. Indeed, many of these documents would be a potential gold mine of information for an attacker.
Here’s an example that just happens to be somewhat specific to HVAC vendors: A simple Google search turns up Target’s Supplier Portal, which includes a wealth of information for new and existing vendors and suppliers about how to interact with the company, submit invoices, etc. That page leads to a separate page of information on Target Facilities Management, which includes a slew of instructions on submitting work orders. That page also includes a link to another set of resources: A Supplier Downloads page that, oddly enough, is little more than a long list of resources for HVAC & refrigeration companies.
What could an attacker learn from this information? For starters, download any of the Microsoft Excel files listed at that page. Then scan the file with a free online service (like this one) that extracts metadata from submitted files. Scanning the file “FM_HVAC_Oct_2011_Summary.xlsx” from the Supplier Downloads Page, for example, tells us that the file was created in June 2011 with a copy of Microsoft Office 2007 licensed to Target Corp. That metadata also indicates the file was created or last edited by a person with the Windows username “Daleso.Yadetta,” and that it was most recently printed to a system on Target’s network in the following Windows domain: “\\TCMPSPRINT04P\”
Getting the layout of the various Windows domains within Target’s internal network would certainly help the attackers focus their attention. For example, consider what we know about a key piece of the malware known to have been used in the Target intrusion, first referenced in a story on Jan. 15, 2014. Investigators who examined the malware quickly noticed that it was designed to move data stolen from Target’s (then malware-infected) cash registers to a central collection point on Target’s network, a Windows domain called “\\TTCOPSCLI3ACS\”.
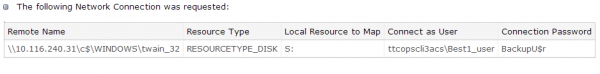
Investigators believe “ttcopscli3acs” wass the name of the Windows domain used by the POS malware planted at Target stores.
A little Googling shows that Target operates two data centers, both in Minnesota: Target Technology Center — or “TTC” for short — is located in Brooklyn Park, Minn. on one of the company’s corporate campuses. The company also operates a redundant data center — Target Technology Center Elk River (TTCE) in Elk River, Minn. as a backup. It’s a good bet that the server referenced inside the malware used in the Target breach resided within the company’s Brooklyn Park facility.




“The company’s primary method of detecting malicious software on its internal systems was the free version of Malwarebytes Anti-Malware.”
PC Magazine has done tests of Malwarebytes Pro and found it to be average at protection. Clean-up is another story, with both Pro and the free version being outstanding. I use it for clean-up, as it finds things regular anti-virus misses.
Malwarebytes has always recommended to use Pro in conjunction with a main-stream anti-virus solution. I have never read any advice that Pro could be used alone. I can guarantee that no reputable source has ever recommended using the free version by itself.
And anti-virus is not expensive. F-Secure, Kaspersky, or Bitdefender, generally the top finishers at AV-TEST and AV-Comparatives, probably would have been able to stop the malware. Malwarebuyes Pro costs $29 or so (for a life-time license) and is sometimes on sale for less.
“Secondly, the free version is made explicitly for individual users and its license prohibits corporate use.”
Fazio might be out-of-business very soon, as it should be. I hope they go after the assets of the owners too.
Great post, as always.
I suspect you won’t have to dig far to find lots of people reliant upon mbam as their primary tool to protect their machines.
I notice when I go to the dentist, that all of their screens have the mbam icon in the tray. But I can’t tell whether they have pro or the free version.
If the icon is in the tray, it’s the Pro Version. Unless you looked the free version is actually running.
Not true. The GUI keeps running with a pop-up, which tells the user the free trial has expired. If the user only knows how to click to clear that pop-up and not how to disable the program from starting up, they will keep seeing that and clear only the pop-up, leaving the icon in the system tray.
There is a new Malwarebytes Anti-Malware 2.0 beta home version with free premium license key, till the end of March for those who like to try new stuff.
https://forums.malwarebytes.org/index.php?showtopic=141268
One thing still makes no sense. Free MBAM does not appear to Windows to be an anti-virus product (Windows still complains about no anti-virus present). I suspect the same is true of Pro, but I forgot to look for that. So someone installing only free MBAM would still have Action Center messages about no anti-virus. These people had to ignore every possible warning.
“Fazio might be out-of-business very soon, as it should be. I hope they go after the assets of the owners too”.
Really? Some $10/hr bookkeeper makes a mistake and opens a phony invoice, so off with their heads? That’s your response?
Get some perspective. Fazio was a victim, like Target. Fazio wasn’t given permission to access Target’s cash registers – they were told to use a web-based billing program to submit their bills. If Target needed them to use a more secure method for accessing their billing system, then it was Target’s responsibility to say “hey, protect yourselves this way to use our systems.”
I’m also sure that if Target had told them “your access gets you into our POS network, and makes you liable for hacking” Fazio would have said “umm…give us an address where we can mail you a paper bill, we’re not going to take that kind of responsibility.”
It was the attacker who committed the crimes, not Fazio. While they may have not had perfect security, they probably had good enough for what they had to do.
@jaded “Get some perspective.”
No, *you* get some. The owner was a cheap a** who would not spring for a $29 lifetime license of Malwarebytes Pro. That plus a *free* anti-virus — Avira, MSE, whatever — would have provided decent protection.
If you worked for a small company, drove their company car, got into a serious wreck, were seriously injured, and then discovered that the owner had been too cheap to fix the brakes, would you care about his problems?
“I’m also sure that if Target had told them ‘your access gets you into our POS network, and makes you liable for hacking'”
Maybe. Or maybe the owner would have had no clue what that meant and signed anyway.
I worked for a small HVAC company a long time ago. The owner thought that software engineers were glorified typists. After he completely screwed-up the account with a large company, he ended up in bankruptcy. There’s more to the story, but the rest all reflects badly on the owner.
Target screwed up, I completely agree. They and Fazio should be sued within an inch of their combined lives.
“It was the attacker who committed the crimes, not Fazio”
True, but both Fazio and Target are guilty of neglect due to their incompetence.
And why don’t we change the scenario slightly? Do you think anyone would cut Fazio any slack if one of their “$10/hr bookkeeper” employees ordered the wrong part, resulting in a fire at a customer site?
Cobbler, think you need some perspective too.
It sounds like Fazio and your old HVAC outfit both were deficient in cybersecurity expertise. Maybe that pattern says some things? Is there any reason to believe *any* HVAC vendor will be any different?
Why must an HVAC vendor be required to know software engineering and network security? Neither has anything to do with running their business. Your expectations to the contrary seem both unreasonable and unrealistic.
Now we see why PCI DSS v3.0 calls for network penetration tests to validate that network segmentation is actually doing what it is supposed to be doing when it is used to reduce the scope of compliance. Target probably thought they had their air gap.
Fazio may have been using a level of security that was appropriate for their business – we don’t know. But they had no idea that their systems were within Target’s PCI scope. And Target didn’t know that either.
“I wouldn’t say the vendor had AD credentials but that the internal administrators would use their AD login to access the system from inside. This would mean the sever had access to the rest of the corporate network in some form or another.”
This is odd. This means that every vendor was a potential threat due to Targets security misconfiguration?
Maybe I’m over parsing, but I didn’t read that that way. I’ll let Brian or others here correct me if I’m wrong, but: I thought the vendor’s credentials allowed the attackers nothing more than entry into the Ariba system. And from there, they somehow managed to compromise some Target AD credentials that had admin access on some other systems.
If that’s off, someone correct me please. But that’s how I was interpreting it.
If I’m right, I’m still missing how they suborned the Target-side AD credentials. But once you’re in a system, you at least have a spot from which to find attack surfaces. Maybe they managed to put a keylogger on and simply waited for a Target admin to log in locally. Maybe they leveraged another vulnerability to expose credentials. Maybe the setup was not up to snuff and the credentials were poorly secured (example: Not requiring NTLMv2 and rejecting anything less). Who knows? That info’s missing (not Brian’s fault of course; if the source doesn’t say it, Brian can’t report it), but it’s not unreasonable to presume there’s another compromise needed to get out of the entry point they gained into the rest of the system.
I’m also still missing how they would’ve leaped the segmentation onto the PCI network, but perhaps that’s where potential misconfigurations come into play. There’s still a lot of details to be released.
In my statement, I’m obviously presuming that either Target had an Ariba server on their corporate network (but not the PCI segment of it), or some Ariba application was running on one of their servers on that same network. If Ariba is completely external to Target then there’s still another level of network penetration that I have not yet seen an explanation for.
I bet we will discover that the Ariba System has a persistent XSS flaw.
1. Attacker phishes Fazio, gets their Ariba cred’s.
2. Attacker posts some seemingly legitimate content to Ariba that leverages XSS flaw.
3. Target employee reviews posted malicious content, gets her own Ariba session stolen, or, worse, get her vulnerable browser/browser plugin exploited.
4. At this point, attacker either has foothold in Target employee’s Ariba session (fruitful for deeper recon) or already owns a Target business office PC.
To which you then compromise the right AD credentials, and then compromise the BMC update server / SCCM server / other update server, which likely was not segmented, but had access to the cardholder environment. Once you compromise the server pushing updates to the registers, you own the environment.
I agree, this seems like the most plausible scenario. Ariba (it looks to me like) has some serious reach into Targets backend. Fazio is smelling more like a red-herring, in that their most serious crime was getting phished (how focused, we have no idea.) As someone mentioned, many small to medium sized businesses, even running full suite AV products, get 0 day’d pretty routinely.
I expect the focus will now move over to Ariba (a very big fish) and it’s ERP processes and how they plugged into Target.
Thanks Brian for keeping on this. This could very well be a case study for net admins everywhere. If you made this into a book, I would buy it.
One way they might have “leaped the segmentation” is the likelihood that the same admins (and AD credentials) used to administer the Ariba box also was used to (remotely) administer the PCI segmented network.
Oh, and claiming that the remote access was outside of the PCI segmented area (or CDE) is a very liberal interpretation of the 8.3 requirement which states, “Incorporate two-factor authentication for remote access (network-level access originating from outside the network) to the network…”. There is no mention of CDE in this requirement – only the network.
The more likely scenario to me (and one I likely would have considered as a QSA) was whether the remote access was actually network level or only application level. If the HVAC company was using a web-based GUI or some client that only gave access to the Ariba application – then that is not network level access and so 8.3 did not apply.
Do we know yet the exact nature of the remote connection? Has there been any discussion around the applicability of 12.3.9?
Well, it’s less that I was claiming ” the remote access was outside of the PCI segmented area”, and more that it’s sort of been an operating assumption in “water cooler” discussions I’ve been in. You’re right, we don’t know if that’s actually the case here.
And yes, I’m interested in the nature of the remote connection myself. I think it’s safe to say that this isn’t an externally top-to-bottom hosted billing service since it was leveraged as an entry point, but we still don’t know how things were constructed. My guess – and I admit, it’s nothing more than an outright guess – is that whatever was running Ariba was hosted by Target and may even have been on it’s own dedicated hardware. Anything less and Target’s security gets even more suspect.
Ariba statement:
Karen Master, a spokeswoman for Sunnyvale-based Ariba, described Ariba as a cloud-based business network companies use to find and conduct business with their vendors. No payment information is exchanged on it, she said.
Target uses software from Ariba to manage transactions with vendors, Master said. The software is housed on Target’s own servers, and Target hosts and manages the software itself and doles out its own Active Directory credentials to vendors.
Ariba does not provide any Active Directory credentials, Master said, and “therefore would not have been involved in the breach.”
http://www.startribune.com/business/245226831.html
I was thinking ACS in server name was probably related to a cloud services but Amazon is usually abbreviated AWS. ACS probably is short for Ariba Cloud Services.
Might it also be “Asynchronous Communication Server”
They do host it. Ok. I was only guessing but that confirms it. Thank you.
Whoa, I hadn’t even considered metadata on documents like that. While not a big hole, it can certainly help malicious entities map your network and look for other weaknesses. I will be checking out our publicly-available documents for metadata like this; luckily, that sort of thing is easy to clean up!
I have no idea how email phishing works, but can imagine the excitement the original person felt when they came across info that gave them hints a trophy specimen was swimming in that see of data.
I would wonder if it isn’t small-time actors that put out these phishing scams, and when they get something of note, perhaps they then put it up for bid or sale on one of those dark markets. It’s hard to imagine someone ballsy enough to take down a Target-sized system would be interested in piddling in kiddy pool email phishing.
But I suppose that is no news to those here who have experience in these things. I’m just a minnow myself,and only got interested when I read Kreb’s initial post on the Target cards being sold online.
Re: “I have no idea how email phishing works” If you don’t know how it works, then you can fall for it and compromise your own system. All it takes is a Google search to find out. And if you don’t know the basics of security, why are you even commenting?
Bruce – I meant that I didn’t know from the perspective of a phisher, how it technically works. I understand how to protect my own self from vulnerability.
Sorry, I misunderstood. I would delete my comment if I could.
@ Bruce Hobbs
They already said they just became interested after reading about the Target breach.
Encourage people to become educated rather than discourage them for not already knowing how to be secure. Education is one of the biggest defenses against these threats.
@ Not Happie
Check out the information in the links below to learn more about phishing and other threats.
http://www.securingthehuman.org/resources/posters (Especially the Don’t Get Hooked poster)
http://www.bbb.org/blog/2013/10/protect-your-identity-dont-get-phished/
And of course, keep reading security news!
Agreed. I would delete my comment if I could.
The organized hacking rings (read organized crime) definitely dabble in email phishing. Using these forms of social engineering (spear phishing) or shotgun style phishing campaigns can net you huge targets. The wider you cast your net the more you catch.
Most of the notable “hacks” of the past year have been nothing more than phishing campaigns that caught a big company. Target may not have been the initial focus, but spamming these smaller service companies is a great way to find a way into a bigger, profitable, company.
The HVAC company mentioned above also serviced other national chains such as Trader Joe’s and Walmart.
The name TTCOPSCLI3ACS is interesting in itself. Naming conventions are useful to network administrators, identifying servers’ purposes… While purely speculation, here’s what it looks like to me: TTC (identifies the DC – pretty common identifier); OPS (used/owned by the operations team); CLI (Command Line Interface – probably a terminal which has permissions to hit all the network gear management interfaces – a ‘hop box’ used for network administration – scary because it means that it has access far and wide); 3 (Just a numerical identifier – as in, the 3rd server of this kind); ACS (just guessing here, but Cisco ACS software? This is what network devices use to process 2-factor authentication, and would make sense that it lives on just this sort of server.). If my (admittedly speculator) theory is anywhere near correct, it would also maybe help explain the mystery of how the attackers were able to exfiltrate the data from the Target ‘secure’ network… Thoughts?
Standard PR bull for a security breach. Small and medium-small businesses don’t even know what the ‘industry practices’ are… other than another business down the road ‘does it this way’. I run into this kind of thing all the time with small businesses. Their ‘security measures’ are generally pretty much nonexistant. Often times I run across businesses with no or expired antivirus solutions, such as those that come with new PCs they ordered. The proprietors do not even realize they NEED any protection because their ‘computers contain nothing of value’. Doing business with places like that feels a lot like a doctor trying to treat colds and viruses for kindergartners during winter.
Fazio said it was “the victim of a sophisticated cyber attack operation,” and further that “our IT system and security measures are in full compliance with industry practices.”
This malware attack is called #Keylogging. A #keylogger, also known as keystroke logging or keylogging, is a method of tracking the strokes on a keyboard without the knowledge of the user. This information is then collected and used to access private accounts or collect personal information. The #hacker use a #polymorphicvirus or #malware by sending it in an Email, Facebook “likes”, Twitter message, Youtube Video, and etc. See Huff Post on Keylogging. There is a solution to this problem in #bestantikeylogging is keyboard encryption. More information on keylogging or how to protect yourself keyloggers visit: https://plus.google.com/u/0/communities/103511850003645158576
Uh, no. There’s a dozen ways to trick someone into giving up the credentials to their email. Most of them do not involve keystroke loggers, and all the other buzzwords you pointlessly hashtagged. (What is this, Twitter?)
Once they had access to an email account, they may have (pure speculation alert) noticed an email from a previous password reset for the Target portal. Bingo. Click reset link again, get new pw and you’re in.
As Brian wrote, “Many of these email malware attacks start with shotgun attacks that blast out email far and wide; only after the attackers have had time to comb through the victim list for interesting targets do they begin to separate the wheat from the chaff.” In this case they found wheat, not chaff.
It’s more then emails blast. Watch this on keylogging: http://youtu.be/iH3OpdyTbdg
“WARNING –PC / Mac and Mobile Device Users All Mobile devices have been compromised!”
Love your LinkedIn profile. Many lolz to be had.
News events such as Target, Facebook, Twitter, and more recently Yahoo, have shown that hackers, known as keyloggers, are the #1 threat to our national security according to the FBI and Interpol.
Uh, wait.. hackers are keyloggers? I’m confused. Or you’re hilarious, I’m not sure which.
Finally someone who understands! Read the Huff Post: Changing Your Password Won’t Change Anything – You Will Still be Hacked
http://www.huffingtonpost.com/james-grundvig/changing-your-password-wo_b_4414149.html
Then a Press Release Keylogging Education and Warning Adopted by Temecula Valley Chamber of Commerce to Inform Its Members of This Cyber Crime: http://www.prweb.com/releases/AntiKeylogging/StopKeyloggers/prweb11491488.htm
Kevin,
Based on the article, the privilege escalation was likely through the web application. Keylogging would not be a factor here, since the HVAC vendor only had access to a web interface.
There are a LOT of ways to exploit a web app–XSS, SQL injection, app coding error. My guess is that since AD seems to be used everywhere, and there seems to be no separate corp employee AD and their corp vendor AD (REALLY TARGET?) The attacker exploited the box and probably got a hash from an update system or waited for an employee or admin to log in. IIS automatically will send the hash when doing NTLM auth.
http://passing-the-hash.blogspot.com/2012/12/wth-is-pth.html
I would have to disagree with you. People at StrikeForce Tech. read this and know that Target and even HVAC company were keylogged. If you want to talk about it with StrikeForce or I let me know.
There ya go, one of the oldest tricks in the book – which apparently still works today. An email, a bored worker and an (in)opportunity for marriage, sex, money,new car, drugs etc and boom, the crooks are IN. Stupid.
Trust is a concept that is not thought about when designing networks. HOPE is not a risk mitigation factor. Most people don’t sit at a round table and go…what happens if this scenarion happens? , in respect to 3rd parties accessing YOUR network?
In the end its a 2 party fault. Target is responsible for their network, and the HVAC company is responsible for allowing unauthorized access to a large corporation. I bet the HVAC company is probably scramblin’ changing the commonly used password on about every network they monitor, or monitored…..
yeah, Curious Observer might be onto something, as I thought about the same thing when I saw ACS on the end. Or its Client #3 as in a specific server name. We willl probably find out soon enough.
IA Eng: One reason that phishing works so well is all the clueless companies that send legitimate messages that look like phish themselves. I get “legitimate” messages all the time with live links in them. What’s the first rule for avoiding phishing? Never click on an email message that takes you to a signon screen.
Once they send out this legitimate crap, it’s easy for a hacker to change it and send out a phish message that the user will fall for. It’s called social engineering and it succeeds more often than not. I’ll bet the typical phish message gets a better response that the typical spam message.
never click on messages that bring you to a longin screen? Eh ?
I never click on them period. How are you going to KNOW when a logon screen appears and not a malicious JPG or other attachmant. I NEVER click on anything suspicious, nor do the counterparts here. You can click and pray, all it takes is a call back to the organization or department that sent the email.
I delete them all if I am not expecting it. If it is extremely important, they will call.
I’ve been doing IA for a very, very long time and I am surprised that people still go DOH once they click on anything.
Clicking on any email message that is not expected has potential for trouble. My advice is DONT click on any unexpected emails and hope they dont have a logon screen. Don’t open them in a preview pane and read them and think your safe. Don’t click on Unsubscribe because, more than likely if you do, its a signal to the other side saying “We’ve got a live “DOh” here.
When it comes to Phish, malvertising or Steganography or other means, its simply NOT a smart idea to click on an email and use HOPE as a mitigation risk that the email only contains a long on.
OPS is probably more likely Operational and Provisioning Services, or something of this nature; architecturally his guess of the name doesn’t make sense to me given the rest of their network naming conventions, though I could be wrong and they do not have to be logical anyway. Location (TC = Target Corporate, TTC =Target Technology Center, etc), then Division probably, then type of services, then number of that server then anything special as a subservice.
“An email, a bored worker and an (in)opportunity for marriage, sex, money,new car, drugs etc and boom, the crooks are IN. Stupid.”
Its not stupid, and it not that complicated.
If I send an email to any Finance Dept, accounts payable, accounts receivable dept…with the subject “Unpaid Invoices”, they will under every scenario, open my invoice, which is really just a malware infected PDF. To make it seem even more legit, I can easily find who you do business with, as posted on the company’s web site, and spoof the email to look like it came from them.
This scenario plays out every day in many small and mid-sized businesses.
I have personally witnessed it, as I was called over to try to fix adobe, which kept crashing as the fake invoice PDF was loaded.
She tried to open it 3 times before calling IT over…
What was I going to tell the Finance Dept…don’t open invoices from clients?
We were current on Adobe (version 7 at the time) and had up-to-date Anti-Virus (McAfee).
The malware tried to load some run-time scripts in the registry, which I quickly found and then unplugged and re-imaged the PC.
To this day, I still don’t have a good plan to prevent these things from getting through…
Why use Acrobat Reader or even allow it to reside on the system when there are numerous free and less targeted [note: I didn’t say more secure, although ipso facto they are, and several are faster] alternative tools out there?
Popular Viewers:
Foxit
Sumatra
Nitro
Chrome
and Lesser Known Viewers:
Cool PDF
STDU
Evince
Xpdf
PDF-XChange
Perfect PDF
Converter (View PDFs in Word)
PDF2Word
Even if the client uses the Adobe Acrobat for creating PDFs, they can use the Acrobat Reader, if necessary, to open, view and confirm accurate document creation of their OWN PDFs, but they can be safer, when viewing PDFs from other sources, by using an alternative.
All of these are (OK many of these programs are) good but it still does not solve the problem and is very easy to get ‘around’ if you want a specific place and know their software. It is the difference between mass exploitation and targeted exploitation.
Obscurity mostly matters if (a) from a technological stand-point, something cannot be experimented with by the attacker easily (for instance developing POS malware requires at least an investment in the hardware and time that comes with probably bricking one or several of the devices; thus it is less convenient for an attacker to learn to do) and (b) the company itself is not being targeted based on its own technology; that is, obscurity is good as long as you are in the minority and you are not the target.
A better solution is probably to have at a minimum a sandboxed situation to open these PDFs/Documents within — or a VM with a secure and static and saved ‘snapshot’ you can keep reverting to (this can be resource consuming of course if you have very many of these documents or customers; a sandbox is probably an easier option) — and most likely opened on a non-networked and non-connected to the internal network machine — and not a machine also used to also perform the accounting that these PDFs often are related to. A ‘clean space’ if you will.
Or as I suggested previously somewhere, chain a couple of applications so that the original documents never get opened; create a graphic image of them or OCR them (sort of like how FAXes used to work).
Fascinating read. If a average internet security minded person can utilize 2FA and tokens then why can’t a company like Fazio Mechanical do the same to protect their network along with third parties. I mean come on the free version of Malwarebytes Anti-Malware. Why not just use Windows XP with Internet explorer 6 without any firewall appliance.
Stupid is what stupid does !
The thing is, this wasn’t really an issue of authentication, although it certainly sounds like Target may not have had its auth scheme (and backend segregation) as buttoned up as it should have been. It was an issue of targeted malware compromising a machine. Once that happens, and the machine connects to the network, the hackers have their way in. It doesn’t matter how many methods of authentication you force on the user–if their machine is compromised, and IP-level connectivity is established, you have serious problems.
Re: MBAM: We should always endeavor to catch malware as close to the source (and as far from the target) as possible. It is a big help to have additional anti-malware on the mail server and/or at the network edge, where threats might be detected long before they reach a platform that they can actually execute on. It is Fazio’s mistake to rely on MBAM as their only protection, not just for the reasons cited, but because a business should have more than layer of protection from these threats.
We can point to the free MBAM software, but as Security practitioners, we all should know that MBAM is just a single technical control. A risk-based approach to security should have revealed that a blend of operation, technical and administrative controls was required – eliminating a single point of security failure. Any company that allows external users to ingress its network must acknowledge that they then become only as secure as their weakest external user. Like pouring water into a porous vessel, it will find a path to the outside if one exists.
Yes, this exactly.
While I know it’s idealistic to sound so sweeping that you come off like “The entry point on Target’s side should’ve been secure enough to where a Win95 computer with a 20 year old virus scanner that hadn’t been updated since the millennium can’t compromise you”, the reality is that any enterprise MUST be secure enough to handle outsiders’ mistakes when they’re connecting to/through your network. That burden’s not entirely fair, but it’s not about fairness, it’s about being safe. It’s all on the admins to figure out the right balance for where they’re at. Not easy, but it’s part of the job.
No antivirus would have mattered. This person probably opened tons of PDFs and documents as a matter of course of their working day. Maybe an AV would catch a clientside. Maybe it wouldn’t. Maybe it was obfuscated properly like a spear. Maybe it would be 0-day, especially if they were definitely identified as high value. Blaming Fazio is ridiculous because any company can be infiltrated with the correct motivation.
The blame is on Target for making Fazio’s infiltration matter to anybody but Fazio for anything other than the specific purposes of their business with Target. Which probably should not have been much more than submitting a false bill to Target’s system (which Target’s system would ideally recognize as false automatically, or if not their accounting department would during processing, but even if not — that is the most that should have been able to have been done to Target. Any exceeding authorization from that point on becomes Target’s responsibility.)
Brian — Have they pin-pointed the actual email/clientside/contents used to exploit Fazio or are they speculating based on simple forensics or likely logic? I am guessing since you included no details that the actual vulnerability/exploit used is not known or perhaps even pinpointed as when or how?
Target never should have allowed a VLAN to their POS to begin with — and they probably did it that way so they could hook up their couponing and databases to their POS systems and registers. Which is to say, you can blame this vulnerability on greed and big data, almost certainly, and cheapness for not running a separate network (because that’d cost more to build and maintain).
Blame the architecture where the problem occurred, not the victim’s vulnerability to possible malware that helped someone get any access at all the to place the real problem occurred. If the architecture were even remotely proper this couldn’t have happened.
If it was Fazio’s POS then I would say blame Fazio. But it wasn’t and there is a likelihood that the person who opened this email attachment or visited a perfectly legitimate website was probably just doing her job and that nothing out of the ordinary even appeared to exist (especially if the payload and exploit were properly FUDed as some might put it online).
Where was it reported that the network was segmented by the use of VLANs?
If so, that was improper by definition. A VLAN is NOT intended to be used as a security barrier. I remember that from when I was active in corporate networks 10 years ago. I’m retired now; don’t ask me how to jump from one VLAN to another, but it can be done, I assure you.
I’ve seen it in several places by now, but it is also a rather logical guess based on some of their public architectural information as well as a number of stories on their ‘big data’ capabilities over some years.
VLAN hopping is easy. Too easy. And if I recall PCI DSS does not require internal firewalls (somebody correct this if I am wrong), not that bypassing a firewall is very difficult either. POS should have its own network. Not a VLAN, not a segment (and I can continue on to other things including synchronousness but I won’t).
When is Fazio’s contract up for renewal?
Depends on the contract. They probably violated a part of the contract that gets them kicked out and landing on their ear. if Target allows them to continue thier ways of practice, especially with their so-called legitimate claim of being secure BEFORE this happened, I would call them a high risk and terminate them and all connections associated, yesterday.
Contracts are a piece of paper. Will the HVAC who caused the compromise be stupid enough to bring legal action? Probably. But then when the Target Corporate legal team slaps them with a suit for 100 million dollars+ , thats when the company folds and something better, hopefully, comes along.
This could have happened to any of thousands of Target supplies who have logins to this system. When you pass out creds on this scale, you better have strong isolation on the other end and that was clearly lacking.
Another reason for organizations to insist that their business partners have effective security awareness training to prevent these kinds attacks.
Security awareness is important, but it still takes only one person for a compromise to occur. I bet RSA has one of the best security awareness programs in the country, but it still fell victim to classic phishing…and thus the rub: the carbon layer is notoriously difficult to patch.
“The carbon layer.”
I am shamelessly incorporating that term into my daily vocabulary. Thanks for the laugh!
Brian,
Great article! Thank you for this great information.
This supports my way earlier comments on your original story, that I bet it was an email. Actually thought I was wrong for once, but I wasn’t.
Any word about the signature for the version of Citadel that hit the vendor? Was it a known signature? Or a new 0 day version?
Vendor assessments are critical, but HVAC companies are typically not the focus of an assessment. It’s usually cloud providers, IT support vendors, and the like. However, this certainly highlights that any third party must be considered.
Calling it an ’email attack’ is a bit much no? It’s more like infection via a stupid employee/weak company policy.
All email coming into our office has every attachment stripped. On our contact form we tell our customers if they must send an attachment to notify us first via telephone after first trying to copy/paste into the body of their email correspondence. And for the ones that routinely do – we whitelist them (but still check before opening!)
All passwords, passphrases, hints etc are also changed biweekly. All customer data is encrypted and stored off of our forward facing web servers and stored under lock and key offline. The only data we keep on our servers are logins for customers and we force them to change passwords every 30 days. Some grumble but too bad – it’s for their own protection!
Canuck,
This approach is exactly what happens in security awareness presentations across corporations. The slides are titled something like “Don’t be the weakest link” and “Do you want to be the ONE?” or “Stupid is, is stupid does” just kidding, never seen that one.
If you and I have never met, but you walk up to me, and say “your the weakest link here at our company” I’m gonna stop listening to you right after weakest link”. Just walk up to any stranger and see what the reaction might be. Just saying, this results in almost immediate shut down.
This is not just my experience after presenting this subject in front of about 12,000 people over the last 4 years, but studies show this as a paradox that most people just have build into their system of response.
It’s time to start changing the way we have these conversations, please just consider our conversation next time you want to help protect your network and engage others in that effort as well.
People simply don’t know what they don’t know.
Who knows, the email could have been almost perfect in its design, format and URL delivered on the hover over of the link.
Sorry for the typo’s but just discovered a problem with a key not hitting on my keyboard. Fixed now.
Do any of your employees have laptops? Can they take those laptops out of the office, and off the corporate network? Then they can connect to their personal webmail and get phished that way.
Many phishing attacks don’t rely on attachments at all, and (even worse) machines can also get compromised (without any sign to the user) by visiting a site that redirects them via a malicious iFrame or ad containing malware. Email protections don’t help against that.
You need robust egress traffic monitoring to detect connections to command and control servers (which, of course, only helps when the impacted endpoint is on your network), but you also look at technologies to prevent installation/execution of code on endpoints.
User security training needs to focus on understanding how people work, and how to enable them to do what they need to do but in a secure manner. It should be viewed as an additional security *veneer*, not the core of your strategy.
Great article, as always!
Reading the Malwarebytes Anti-Malware section of it, I start laughing. It is surreal and incredible!
And I am still laughing even more when I read about a $5 million investment in cybersecurity coalition by Targer corp. on their website.
Guys, it is too late… toooo late. Save those money for good attorneys.
I think the discussion of anti-malware and anti-virus is somewhat irrelevant. Anti virus evasion isn’t difficult to achieve, regardless of which software is being used. I think a more relevant issue is why Target wasn’t able to detect the Malware, either at insertion, or while it was actively sending data out of its network.
Yeah, I debated whether to even mention it, mainly because these attacks routinely breeze by antivirus systems if you happen to be unlucky enough to open the malicious attachment in the first 12-24 hours after it being sent out.
It is relevant.
Using a product with zero protection capability implies one of three things:
1) someone was merely completing a check-list,
2) someone made a decision with absolutely no research, or
3) someone was ordered to make a decision in short order.
Yes, there is overlap in the above.
Using a product with zero protection capability means that you could read the email months after it was first seen in the wild and still become infected. At least with a free anti-virus and MBAM Pro, you’d have a chance of being alerted to a zero-day. Fazio had zero chance.
Yes, but it’s weak relevance, peripheral at best. Regardless of whether Fazio was exceptionally careless or usually hypervigilant, it still doesn’t address what the problems were on **Target’s** end. The larger issue was why Target’s system was vulnerable in the way it was to a compromised external vendor/supplier/contractor’s entry point. The reason for why that external entity was compromised is ultimately not as important as Target’s system design because Target – or any other business – can’t presume perfect security from those they don’t control. And pretty much everything outside their corporation they can’t control.
Fazio’s problem at worst should’ve resulted in nothing more than a compromise of the external contractor’s payment system. The fact that it enabled capture of payment card data is what’s really at heart of the entire discussion, and at that point Fazio becomes nothing more than an accidental, perhaps careless dupe. Their significance dims compared to the problem on Target’s end.
There’s also the problem that such focus can accidentally skew the discussion and thus the average, non-technical person’s takeaways from it. We’re all laughing at Fazio’s use of Malwarebytes, but the significance of that fact is very limited, and the non-technical person may not catch that. Target and businesses like them must design for the possibility of compromise even if their external vendors/contractors don’t use anything protective, or on the opposite side of the spectrum pay through the nose for managed products but get caught out by a zero day or some other compromise. It’s certainly chuckle-worthy that Fazio’s staff used Malwarebytes, but it’s little more than that.
Well said.
@E.M.H. “It’s certainly chuckle-worthy that Fazio’s staff used Malwarebytes, but it’s little more than that.”
The fact that Fazio used a free, not-for business product which provided no real-time protection points to an attitude that computer security is a joke; don’t forget that Windows would still have complained of no anti-virus, as MBAM does not check that box. Their office router is probably a cheap consumer-grade one which never had a password set, allows UPnP, still uses WEP, allows guests, etc. Every Windows user account probably has admin privilege. Some employees look at their Facebook page and personal email during breaks. Employees were never trained to verify that links have a familiar domain name before clicking on them. And so on.
Of course Target should have taken measures to isolate itself from its vendors. But given its degree of outsourcing, that might not be possible. We will never know the full extent of Target’s incompetence because it will never admit that it had many other vulnerabilities, ones which may or may not be fixed after all is said and done.
Phishers are not deities to be idolized, contrary to the opinions of certain people here. The people who fall for phishing generally break a few rules; that is trainable.
I agree that antivirus is a shaky defense. I view it more as a tripwire that the adversary *might* step on, or might not. Still, FM’s use of an antivirus product that doesn’t even have real-time protection earned a mental facepalm.
As an example for co-workers to learn from, I’ve been tracking a couple of malware samples for detection at VirusTotal. Here’s one for anyone interested:
https://www.virustotal.com/en/file/e991f989ec6705cfdbe67de31982621e1e4edcf80eb6d20b553cb4a469305431/analysis/1392261750/
On initial receipt as a .RAR file attached to an email, detection rate was 0/50 at VirusTotal. A week later, it was at 15/49. Three weeks later, it’s at 28/49, and is still not detected by either of the AV vendors to whom I personally submitted it (Microsoft and Kaspersky Lab). And on any given sample, those results could swing in any direction.
What I put more faith in is application whitelisting, with my weapon of choice being Microsoft’s Software Restriction Policy in disallowed-by-default mode. If Fazio Mechanical wanted some effective freebie protection, that would’ve been a great start.
Brian,
Another question I have is about the email. Was it targeted at this company? Spear phishing is very prevalent these days and I have seen some excellent attempts since the LinkedIn breach. Wasn’t sure if you were using the term phishing in general.
I don’t have any information to suggest it was targeted, no.
Brain,
Ok, hopefully some confirmation of this will come from the feds soon and maybe more detail to help better defense against these attacks in the future.
One email, one click, delivery of malicious software. They have to get lucky once, and we all have to nail it every time.
no pun intended, right Brian?
With access to Ariba, it would be fairly trivial to send someone a trojanized invoice (xls or pdf). This would be an easy way to ingress an exploit laden document directly to someone you know is involved in the billing process and avoid email gate anti-virus filtering. Since the Ariba connection would likely be SSL, this ingress vector could also bypass any network malware detction capabilities present in NextGen products like FireEye, Palo Alto, McAfee Web Gateway or any of the other Virtual Machine based “detonation” techologies(unless an explicit effort was made to allow for SSL decryption).
This would basically be spear-phishing, but using Ariba in the delivery phase of the attack.
++
Which is one reason I’ve been thinking processing things of this nature via a straight OCR application before passing it to the actual application would be a logical security precaution.
Does anyone know how the Target ICT team is structured? This would be an interesting piece of information, just to understand what type of competences such a huge retailer has in-house (and if they outsource any of that).
Those strings like ”\\TTCOPSCLI3ACS\” are names of servers, not names of (Active Directory) domains.
I was caught on that too. You can specify a short domain name in that fashion and a domain controller will respond. However, pseudo-standard naming conventions don’t indicate that it was a DC, but merely another server.
Congratulations on another excellent post, Brian! Your timely and intricate reporting on the Target breach, as compared to the “mainstream press” should be an embarrassment to them all. I wonder how much we would actually know if these players weren’t being almost forced to acknowledge what you are reporting well ahead of them. Too many news outlets have now gotten too lazy and too dependent on playing catch-up instead of investigating. There is not a lack of talent, but media orgs do not support reporters anymore in a way that allows them to stick with a story and delve deeper. By the way, I counted 4 times that the HuffPost had to directly attribute to you on the following story: http://www.huffingtonpost.com/2014/02/12/target-hack_n_4775640.html.
I guess that’s why Brian got out of the mainstream press.
Did you also notice that they claimed Brian had characterized it as a spear-fishing attack, rather than a generic email blast. I have not seen that from Brian; in fact, to the contrary:
BrianKrebs
February 12, 2014 at 9:19 pm
I don’t have any information to suggest it was targeted, no.
[i’ve already commented that I’m sure Brian intended no pun]
It appears that HuffPost’s claim that Brian characterized this as “spear-phishing” may have been fabricated so the author could tie in the paragraph about “island hopping”, when in fact it may well be that Fazio was caught by a random generic email blast, and only after gaining access to Fazio’s network, did the hackers discover Fazio’s allegedly limited access to Target’s network.
Many web-based systems with a vulnerability which can be exploited by users have the potential to cause much wider-spread harm than believed. This is why threat modeling of systems and consideration of lateral attacks is so critical. Ben Williams’ presentation at Black Hat EU (Hacking Appliances: Ironic Exploits in Security Products) shares some great examples, with a focus on security products. http://www.youtube.com/watch?v=uZloeFhCMYQ XSS+CSRF => session cookie theft, account privilege change, browser exploit and privilege escalation, etc. Hopefully Target will be fairly transparent and share the details of the breach so we can all be more informed.
So we may have our arms around how the criminal(s) probably accessed an internal vendor web site and gained admin credentials from there. But as far as I know we still don’t yet understand how the POS malware was introduced and distributed to the terminals. We also don’t yet understand how the database of 70 million personal records was breached. But at least it feels like we’re getting closer. Great article Brian!
I thought the database was only theoretically breached, as in it could have been accessed, not that it was accessed, and definitely not that it was definitely copied. In fact if I were betting man I would guess that database did not leave their servers or even seen much at all — this much data going out would be far more obvious than POS data egressing. I think point is they do not know whose things may or may not have been seen.
Recall voksalna there were two attacks. The POS malware (40 million records) and the PII breach (70 million records). The evidence is fairly clear the PII attack was a database breach. There is also evidence the POS Malware could also be a database attack against Target’s configuration management system.
Hello Edward,
My understanding was that this PII breach was simultaneous to and/or leading up to the POS breach, but in either way a part/parcel of the same breach just at different levels. There is no evidence that I have seen to suggest that this data was egressed, and based on the logical sizes of these databases I can almost guarantee there is no way that data could have been egressed, especially if they were using a modern RDBMS (which I assume Target does).
It is more likely that various things were looked at and evaluated and probably certain parts were taken (databases often cluster in networks so where the PII was may have also been a place where credentials may have also been in a different table, for example, and these credentials (if so) most likely were taken). While targeted SPAM may be a ‘gold mine’ in theory, in practice the amount of time and bandwidth it would taken and the almost impossible logistics (almost because I am sure there are store closed hours, probably when the POS malware was inserted, probably when this network was hacked and explored) make it quite unlikely that the PII was pulled out of Target’s network in any sizeable quantity.
Just like how when so many laptops are taken or lost breach reports call it a loss of XXX thousand items of PII but that doesn’t mean the person who obtained the laptop knew or cared, or that was even what they had in mind — or even looked at with any intention.
It becomes a matter of intention, of feasibility, of priorities, of difficulty, of time, of resources, and of what I call “loudness” but Target HAD to say that that portion was breached if the ‘hackers’ were at all on that part of their network given the timing and the situation. Put another way the PII was more of a threat and the POS was more of a promise.
US Banks are at fault here. with out two-factor authenticated transactions chip-and-PIN at the credit card payment device that banks will not pay for will cost billions in credit card fraud. pay now or pay later. credit card customers are at the mercy of the US banks and merchants. the other issue with 2fa is online fraud. every country in the world with 2fa has seen an increase in online fraud. US banks need to start to protect customers banking accounts. visa and master card in the US will try rolling out chip-and-PIN next year 2015 so we will see if visa and master card can pull this off. other option secure card https://www.google.com/patents/US8464936 other option Mastercard PayPass or VISA PayWave (NFC technology) anything connected to the internet is not 100% safe today.
Chip and PIN is not foolproof. However, according to comments from people in Europe who use them, the banks in Europe consider them foolproof and it’s harder to get a invalid charge removed when they are compromised. Be careful what you wish for.
I read that too, but when I brought that up in one discussion elsewhere I was told that American financial laws are different enough here to mitigate that concern. I pressed for details but didn’t get an answer. So since the topic’s been opened: Does anyone else know what it is about US laws that reduce the concern with charge reversal difficulties? I admit, from my perspective, I don’t see it. On the contrary, I fear banks and other institutions will be more willing to challenge reversal requests for the same reasons they do in Europe.
http://www.consumer.ftc.gov/articles/0213-lost-or-stolen-credit-atm-and-debit-cards
Credit Card Loss or Fraudulent Charges
Under the FCBA, your liability for unauthorized use of your credit card tops out at $50. However, if you report the loss before your credit card is used, the FCBA says you are not responsible for any charges you didn’t authorize. If your credit card number is stolen, but not the card, you are not liable for unauthorized use.
The problem isn’t the law today, or even the law of Europe yesterday. It’s the law tomorrow, when Europe introduced chip and pin, the law was changed, introducing a liability shift. That same change could (but IMO certainly Should NOT) be made (roughly enough banks “encouraging” enough legislators to change the laws to “bring them in line with the European laws).
Ok. I was wondering. Thanks for the info. That helps a lot.
And yes, I myself do hope there’s not going to be any liability shift. Even with the law as it is I can see the banks at least requiring some sort of argument from a card owner proving he/she didn’t rack up the charge. And the stinger is, how do you prove that? If there’s large geographic disparity in purchases (such as in my case from years ago, where purchases in France and Germany were right smack in the middle of same-day purchases in the US city I live in), then this is an easy thing to provide. But if the crooks choose to target (no pun intended) you in your area, you can be in for a rough ride. And as Brian’s past articles have shown, some card bundles sell on the illegal market with regional and personal data. Even if the crooks just get lucky by accident in where they choose to run up charges, it will still look legit to a bank. And all of a sudden you’ll have an uphill climb.
But at least the law currently looks to be consumer friendly. That’s a plus, even if it turns out that it’s not perfect protection.
I work with clients similar to Fazio on a regular basis and they are notorious for a cheap approach to IT, often relying on free or outdated products, both for information security and all other aspects of their IT infrastructure.
That being said, it’s hard to see how you can find fault with them over Target’s problem. Target should never have given any kind of network access to an HVAC vendor that could result in network penetration beyond the scope of the vendor’s responsibility. This vendor’s access should have been ACL’d to the systems they needed, no more, and financial systems shouldn’t have been accessible at all.
This would have prevented the more existential threat of a vendor being used as an attack vector but also against the more substantial risk that a vendor themselves might have malicious intent.
While this article is, as usual, excellent and the commentary also insightful, at some point I have to pipe up with an objection to Brian’s use of the word “googling”. I know it’s an accepted word among the public, but I would have thought that those of us with any sort of interest in security would have all stopped using Google a long time ago and started using a non tracking search engine like DuckDuckGo. I realize “duckduckgoing” doesn’t quite roll off the tongue, but using “googling” just encourages us to placidly accept intensive user tracking.
“those of us with any sort of interest in security would have all stopped using Google a long time ago and started using a non tracking search engine like DuckDuckGo”
Or Ixquick. They’re both good.
I always say something like “do an Internet search” instead of “googling.” Not to mention that “googling” sounds like something a toddler would say.
As disgusting and unfortunate as this is, ‘to google’, and thus in transitive sense ‘googling’ as well is perfectly correct English now, as it was introduced into the OED (the standard for dictionaries) as a verb in 2006, and in Merriam-Webster at about the same time (likely because it was added to the OED a month prior).
I realize that English is your second language, but I think you are confusing two concepts.
Using “google” as a verb could mean one of two things:
– using Google’s search engine to search the Internet, or
– searching the Internet in a generic sense, i.e. via Google, Bing, Duckduckgo, Ixquick, etc.
I do not have a current paper dictionary — my older M-W Collegiate has all words necessary for me — so I cannot verify it on paper. But M-W’s webpage for “google” states: “to use the Google search engine to obtain information about (as a person) on the World Wide Web.” This is using definition #1 above.
I’m not GregRPerry, but it seems he was bemoaning the use of “google” when the person actually meant definition #2 above. I agree with him 100%. If you are a google-phile, then use the term “google” when referring to generic searching. But if you aren’t, you are perpetuating a bad habit.
The situation can be compared to the word “kleenex” which originally only referred to a tissue manufactured by Kimberly-Clark. But people started using “kleenex” to refer to a generic tissue. At first K-C complained about this when other companies used “kleenex” to refer to their tissue because K-C had trademarked the word. Eventually K-C lost the trademark status of the word and it is now pretty much synonymous with tissue. The Google situation is the reverse because it wants people to use “google” to refer to generic searching because it further reinforces an existing bias.
I’m not concerned about this because I use 3rd party tools or extensions to manage what Google can track. In the past this included CustomizeGoogle, but now I use Remove Google Tracking, and/or Google Privacy to convert Google’s redirect tracking links to direct links for me to use. Am I missing something here? I do miss the option in CustomizeGoogle to block ads, but ABP does well enough for me.
dave, respectfully yes you are missing something — google is still tracking you across its many networks and extensions can help a little bit but they will not eliminate this. Your IP is also a link to all of their partners as is your browser identification, and so forth. A large part of how results get to the top or bottom of google, are considered relevant, and so forth, is directly related to all of this and more. You will get less “terrific” results with ixquick, startpage or dukdukgo because they do not do so much of this traffic, so it becomes a trade-off.
And if you are logged into any google service at all when you search, or have any google/partner cookies then no number of add-ons will really do much if you are leaving these tracks through all of your searches.
I would also recommend NoScript and one of the many very good AdBlockers as well as one of the higher rated cookie manipulation and wiping addons for your browser, as well as a private browser tab addon.
@voksalna
I already mentioned ABP (AdBlockerPlus) and I also use NoScript already, with google-analytics.com always untrusted. They can have the IP of the proxy in use for any given session; and I don’t care. Blocking of HTTP referer (sic RFC 1945) and spoofing of user agent string is easily accomplished.
Abine DoNotTracMe and Better Privacy extensions as well as Firefox settings manage/wipe cookies and LSOs (Flash cookies) and alert me as to when LSOs are dropped onto my system.
I never log into any Google services.
Also you may want to set your start page in your browser to about:blank or the like. Many browsers now automatically connect out to things they think you might want to see based on your past behaviour and make that part of the tiling in startup giving you cookies you may not even realise you have when you start a session especially if you have ‘stay logged in’ enabled anywhere (ie a login cookie or stored credential that is repeatedly accessed).
My start page is nothing but the google search page, and new pages are always about:blank.
Even if I allowed the Firefox New Page, it would be blank, except for sites in the current session, as I clear the history upon every exit.
I never have ‘stay logged in’ enabled and it would be cleared by Better Privacy, even if I did.
Thank you Brian for the follow-up.
My curiosity point was how did the ‘bad folks’ get access in the first place (which I alluded to in a previous post).
For those who are finding out about the ‘inside’ pieces of security and how valuable a hacked PC/phone really is, please take a bit to read an article posted by Brian back in October of 2012 :: http://krebsonsecurity.com/2012/10/the-scrap-value-of-a-hacked-pc-revisited/ . A most excellent graphic (recently updated) within that article.
Per the IDS/IPS/NIDS (etc.), most SMB’s, IMO, can best benefit through education; that is, having information and processes presented to them in a manner that is relevant to them. Most have the idea that ‘they have very little, if anything, that the bad folks would want’ is a very popular idea among the businesses I’ve been in contact with. That needs to change, and we security folks are the one’s who can assist with that change.
Bottom line to me: keep the O/S up to date (no matter what flavor you’ve chosen to run), keep your A/V products up to date.. AND RUNNING.. and do your best to educate the absolute weakest link in the chain (the user) on best practices.
Again, thanks Brian for relentless digging.