Earlier this month, beauty products chain Sally Beauty acknowledged that a hacker break-in compromised fewer than 25,000 customer credit and debit cards. My previous reporting indicated that the true size of the breach was at least ten times larger. The analysis published in this post suggests that the Sally Beauty breach may have impacted virtually all 2,600+ Sally Beauty locations nationwide.
Sally Beauty has declined to speculate on how many stores or total cards may have been exposed by the breach, saying in a statement last week that so far its analysis indicates fewer than 25,000 cards were compromised. But that number seems very conservative when viewed through the prism of data from the cybercriminal shop primarily responsible for selling cards stolen from Sally Beauty customers. Indeed, it suggests that the perpetrators managed to hoover up cards used at nearly all Sally Beauty stores.
The research technique used to arrive at this conclusion was the same method that allowed this reporter and others to conclude that the Target hackers had succeeded at installing card-stealing malware on cash registers at nearly all 1,800 Target locations in the United States.
The first indications of a breach at Target came when millions of cards recently used at the big box retailer started showing up for sale on a crime shop called Rescator[dot]so. This site introduced an innovation that to my knowledge hadn’t been seen before across dozens of similar crime shops in the underground: It indexed stolen cards primarily by the city, state and ZIP code of the Target stores from which each card had been stolen.
This feature was partly what allowed Rescator to sell his cards at much higher prices than other fraud shops, because the ZIP code feature allowed crooks to buy cards from the store that were stolen from Target stores near them (this feature also strongly suggested that Rescator had specific and exclusive knowledge about the breach, a conclusion that has been supported by previous investigations on this blog into the malware used at Target and the Internet history of Rescator himself).
To put the ZIP code innovation in context, the Target break-in came to light just a week before Christmas, and many banks were at least initially reluctant to reissue cards thought to be compromised in the breach because they feared a backlash from consumers who were busy doing last minute Christmas shopping and traveling for the holidays. Rather, many banks in the interim chose to put in place “geo blocks” that would automatically flag for fraud any in-store transactions that were outside the customer’s normal geographic purchasing area. The beauty of Rescator’s ZIP code indexing was that customers could buy only cards that were used at Target stores near them, thereby making it far more likely that Rescator’s customers could make purchases with the stolen cards without setting off geo-blocking limits set by the banks.
To test this theory, researchers compiled a list of the known ZIP codes of Target stores, and then scraped Rescator’s site for a list of the ZIP codes represented in the cards for sale. Although there are more than 43,000 ZIP codes in the United States, slightly fewer than 1,800 unique ZIPs were referenced in the Target cards for sale on Rescator’s shop — roughly equal to the number of Target locations across America.
Sally Beauty declined to provide a list of its various store ZIP codes, but with the assistance of several researchers — none of whom wished to be thanked or cited in this story — I was able to conduct the same analysis with the new batch of cards on Rescator’s site that initially tipped me off to the Sally Beauty breach. The result? There are nearly the exact same number of U.S. ZIP codes represented in the batch of cards for sale on Rescator’s shop as there are unique U.S. ZIP codes of Sally Beauty stores (~2,600).
More importantly, there was a 99.99 percent overlap in the ZIP codes. That strongly suggests that virtually all Sally Beauty stores were compromised by this breach.
And here we come full circle to an explanation of why there is almost no chance that the number of breached cards is limited to fewer than 25,000. Let’s assume for the moment that Sally Beauty managed to detect and eradicate the threat that led to this payment card breach within the first 24 hours. That would essentially mean that only 10 transactions total were compromised from each store that day before the company managed to stop the theft. It’s possible, but unlikely.
What is more likely is that this batch of 282,000 cards (dubbed “Desert Strike” by Rescator) will be the first of several pushed out to Rescator’s shops in the coming weeks. Time will tell.
I asked Sally Beauty to comment on my findings. They declined again to offer any more detail on the breach, issuing the following statement:
“As experience has shown in prior data security incidents at other companies, it is difficult to ascertain with certainty the scope of a data security incident prior to the completion of a comprehensive forensic investigation. As a result, we will not speculate as to the scope or nature of the data security incident. Please check sallybeautyholdings.com for updates.”
The zip code analysis is available in this .csv spreadsheet.




That’s interesting about the zip codes overlapping – and if you looked at Sally’s store zip codes and went +-3 to five digits you’d probably have a heckuva lot more breached cards.
+1
That is just spooky … time to go back to a cash only society outside of the net? They get by just fine that way in Asia!
You mean a cash system where savers are penalized by gov’ts that devalue currency with endless printing? Cash is only as good as the public’s faith in its value.
I’ll take any cash you have on hand that you have lost faith in. 🙂
Me three!!!
Problem with cash is that it require one to go to ATM’s. And those get ‘skimmed’ quite frequently as well.
Also paying online is hard with cash. PayPal on occasion works though.
But there really is no issue with credit cards. Just don’t have one with a huge limit, but have 3 or 4 with smaller limits. If one gets stolen/hacked/compromised, either you call or the bank will auto-close depending on who finds it first. And you have no risk, as all gets refunded or in most cases doesn’t even make it to your statement.
In addition, if you have more than 1 card, you can easily use e.g. one for ‘shady’ places like smaller web shops or taxi’s, and use a different one for the weekly family/business expenses. I have one card which I use for that purpose, and so far that is the only one that ever got pulled by the bank though all these years.
The Target and perhaps Sally hack is a bit of an exception but in most cases it is not hard to get a feel for the risk.
Doesn’t mean no improvements can be made to the current system of credit cards, but in general the current flood of breaches only makes me more want to use those, and move even more away from checks and ATM’s.
BTW in some European countries, one needs to type an extra password on a separate (!) website for some credit cards when doing an online payment. Together with the new chip/PIN cards for non-online that already makes life a lot harder for hackers.
Counter point…
“Problem with cash is that it require one to go to ATM’s. And those get ‘skimmed’ quite frequently as well.”
The old fashion way of going to the bank is still available.
“But there really is no issue with credit cards. Just don’t have one with a huge limit, but have 3 or 4 with smaller limits. If one gets stolen/hacked/compromised, either you call or the bank will auto-close depending on who finds it first. And you have no risk, as all gets refunded or in most cases doesn’t even make it to your statement.”
Actually this makes it more difficult to discover the fraud as it is more difficult to keep track of the accounts when there are many as opposed to few.
“In addition, if you have more than 1 card, you can easily use e.g. one for ‘shady’ places like smaller web shops or taxi’s, and use a different one for the weekly family/business expenses. I have one card which I use for that purpose, and so far that is the only one that ever got pulled by the bank though all these years.”
This is assuming that all fraud takes place based on where you use the card. Unfortunately breaches like the one at Heartland Payment Systems would make this strategy a false sense of security. Better to be in the habit of monitoring all your card activity regularly.
Allow me to state the obvious. Credit and debit card transactions in the US are denominated in the same dollars as cash.
How is it then that cash is inferior?
Easy, cash does not pay you to spend it. Credit cards pay you to spend them, anywhere between 1-5% per transaction. If you lose a credit card or have it stolen you have zero liability, if you lose cash you are 100% liable. Cash does not give you a 30 day loan that is interest free, credit cards do. You can collect 30 days interest on the cash you spend and then pay it off at the end of the month. There are so many more advantages to credit cards than cash.
All true solely of credit cards, not debit cards. Do you favor cash over debit?
If given the choice between cash or debit I would choose cash. I have a defined limit I can lose with cash, with debit I could lose my entire bank account if not reported properly and promptly. Credit card ALWAYS wins out unless you are trying to achieve any form of OPSEC then cash would always win out for obvious reasons, or pre-paid credit card if cash is not an option.
Michael, just so you know fraud reporting requirements are very much in the consumer’s favor. You have 60 days from the date of the statement on which the fraudulent transaction(s) appear. Would you not notice and report transactions within that time period?
Additionally, regarding properly reporting, banks may claim you have to fill out their form and try to contact the vendor, etc., but the reality is that Reg E stipulates that you can contact the bank in any way (even phone) and at that point the clock starts ticking on the dispute process. I wouldn’t recommend calling because it’s hard to prove that, but a letter stating you did not authorize this transaction and you would like to dispute it is just fine.
There is nothing in your favor when it comes to debit cards, your account gets drained and you have zero money until you prove/report that it was fraud. I have a tough time believing the banks are tilting anything in the consumer’s favor, they are there to make money not to help you. I can’t see any reason why a person would prefer debit or cash over credit card however unless its an OPSEC scenario.
Depends on the bank. My bank called us last month due to a weird charge from Great Britain. The fraud department verified the last 10 or so charges and that was the only one that stood out. Within 24 hours we had a credit for that amount on the charge while they investigate, and within 7 days, a new debit card for my wife. (It was charged to her card). All for a checking account and debit card.
Not all banks look out for you, but there are still some that do.
I think you will find that nothing has intrinsic value beyond what someone will pay for it. This goes for gold, currency, diamonds, etc.
I use cash more and buy gift cards for Sam’s and Publix. I called Sally’s main number in Dallas and chewed them out for incompetency and said the breach was inexcusable. Also they will be sued like the rest. I was not a victim. I said I will no longer be their long time customer and those in the beauty biz will buy elsewhere or order with pay pal. If these loser businesses like Target , Michaels, Barnes and N., etc. want to anger people they are doing a good job. They can no longer be trusted. People will go less and use cash or quit them. This country is too backward to go with the chip cards, because politicians won’t pass laws.
Were any Canadian Sally Beauty stores hit?
I’ve always wondered: why isn’t it called “Sally’s Beauty Supply”?
Usually everyone overuses the ” ‘s “. Sally forgot it altogether. (Kind of like their approach to IT security)
I guess I’m not surprised at their corporate obsequiousness. It’s like Alfred E Neuman is their CSO: what, me worry?
More cracking journalism. Will be interesting to see what the final card tally is.
Does the ZIP feature on this batch also lead you to believe that Rescator had intimate knowledge of this breach too? Or could this just be a new way in which the data is being stolen, that gives access to this info?
Since the Target breach and it taking my bank 5 weeks to reissue a new card I’ve gone back to cash and “my checkbook” for instore purchases. I hate carrying large quantities of cash, especially when grocery shopping but you just can’t trust your cards out there anymore.
The issue with checkbooks is you give someone your checking account and routing number every time you write a check. Depending on how your bank handles transfers, that can be worse than a credit/debit card being stolen. Cards usually have a max daily limit that can be withdrawn or spent, checks usually do not.
Very valid points about the use of checks & with the prevalence of point of sale systems that scan the checking account# & rountung# then electronically debit your account for your purchase, using checks can still leave you vulnerable to theft by hack.
Brian, don’t you think we are soon going to see HIPAA-style legislation for the payment card industry? I don’t think its far off, complete with penalties and prison time for non-compliance.
+1
How many hospital execs have been sent to prison over HIPAA violation? NONE! Furthermore, HIPAA adds no value, it’s an expensive regulation that accomplishes little. What we’ll end up with is another Dodd/Frank like piece of legislation that’s written and promoted by people who don’t have a clue about the payment card industry. It will be a regulatory and financial burden that will pass massive costs down to the consumer. Get ready for transaction fees paid by the consumer, gone will be the days of no annual fee cards, and credit limits will drop like a rock.
It will take something akin to legislation. I still have large companies using the excuse, “we’re private, we don’t need to be PCIDSS compliant.”
What will make companies take data security more seriously would be forcing more financial liability on the company. Right now, they don’t lose much longer-term money when stuff like this happens. Though, that’s starting to change with the required processing terminals upgrades for the VISA and Master Card merchants.
Legal liabilty would also help, but it rarely has any meaningful impact. Not saying it’s not possible, just there are other things that are more likely to happen that would move the industry forward. I just don’t have much faith in elected officials to get it right.
There are regulations. The problem is that many companies see paying fines as part of doing business. $10k fine for $100k profit? No problem.
Wow it appears my zip code is included in that list. Is there any indication of the time line a card may have been used during to have been breached? I guess what I’m asking is would a card have had to been used during the breach period to have been captured or would it be possible for a card used at another time to have been stolen due to having been stored inside Sally’s system? I’m completely naïveté about how these point-of-sale systems work so I ask from a lay-person view.
Lisa, I feel the same way and what really infuriates me, as a Sally Beauty Supply customer, is that nothing has been said by them to we the customers. I used my card there in late February for a purchase but going forward, all my purchases will either be cash or check. The non-communication, though, that really gets me and I’m looking for another place to buy products. Yes, granted, a breach could happen there but the lack of communication with people who have spent their hard earned money in their stores is a real issue for me.
Mary,I’m so thankful for these updates from Brian. This particular breach hadn’t been covered at all from what I’ve heard in my local media sources. I’m a lay person just trying to keep informed & don’t know the “language”, Terminology, etc. Maybe no one here knows the answer to my question & we’ll just have to wait till all the chips have fallen to see if we’re affected?
I feel your pain. I used my card there TWICE in the last week of February. Went by there again after reading Kreb’s March 5th article to buy something else and asked if their credit card problems were resolved. The worker looked shocked and a bit puzzled and then in a very low (almost whisper) voice said, “Oh yes. Everything is okay, now. What?… Were you in here the other night when we were discussing this?”
It seemed as though they had been told NOT to divulge any info. I was a bit surprised that they were even AWARE of the problem.
Oddly enough, my zip doesn’t appear on the list (although, the zip of the store I shopped at DOES appear).
Strange.
Sally Beauty hasn’t said how big the breach window is. They have told me that they first detected something weird around the 22nd of February, but who knows for how long those systems had been compromised at that point and for how long after that point they remained compromised.
looks like they’re getting desperate over there, that’s why there’s an escalation in these breaches from that sector of the world.
http://www.databreaches.net/potential-7-million-credit-card-details-leaked-by-anonymous-ukraine/
once the Ukraine is absorbed back into the Soviet Union you can almost bet that this is going to get worse. only because the Russian gov. just don’t like competition.
this is the new era of Moon-Shining. Al Capone was an amateur compared to these clowns.
We’ll just call it Card-Shining.
Aaaaa. what’s up doc?
Hhehehehe: Be verwy, verwy qwiet, I’m hunting CweditCauwds.
Here it is:
http://www.hacksurfer.com/posts/us-gives-aid-to-ukraine-ukraine-gives-us-cybercriminals
they’re not giving up their cash cows, but they’ll take more of our money just like the raiders did in the 90’s
it’s a mad world
Thank you for sharing the HackSurfer link!
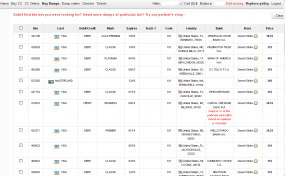
May I ask what “Desert Strike” is? You tagged it to the story, and mention the “Desert Strike” database in the image caption, but I’m not familiar with the phrase in this context.
Is that something readers should recognize? (I.e. am I just being clueless?) Is it malware, or a group? Or just a “code name” the bad guys chose for this attack?
Desert Strike is the name of the cc base at the site hosting the cc. look at the pic with in the story.
that is all!
dis-missed!
Your analysis clearly struck a nerve at Sally Beauty. As of 25 Mar 0925 EDT, store search has been disabled on their website.
How did you come to that conclusion?
Works for me
http://stores.sallybeauty.com/
Some (or most) Sally stores operate in cities that are multi-zip. If you have approximately the same number of zip-codes compromised as store zip-codes, then some stores are missing, or not yet represented.
Also, there are a few Sally stores that operate in cities with no Target location. Fresh meat for the crews it would seem.
Brian, do you know whether the cards stolen during the Nordstrom and Michaels breaches were also sold based on zip code? Thanks for your great work!
Not that I know of. I don’t believe those breaches were the work of the guys that hit Target. I do believe that the Sally Beauty breach was, mainly because their modus operandi was almost exactly the same.
“researchers — none of whom wished to be thanked or cited in this story”
I do enjoy writings which employ subtle wordsmithing.
Off topic – Brian, would you please consider creating a way for readers to receive notifications of comments without having to leave a comment/click “notify” for posts?
The conversations can often be informative and entertaining, but as it stands, one must include at least some comment in order to opt in.
+1 to that & it’d be nice if I could stay logged in so I didn’t have to keep re-entering my email addy. .. Or does that present a security risk? Is entering my name & email addy each time more secure?
In response to comments talking about number of stores per zip:
Sally Beauty says on their website that they have roughly 4500 stores worldwide. In my area, a lot of them are in Wal-Mart SuperCenters. I’ve seen those stores and they are always busy. I agree with Brian and find it very hard to believe that out of all that foot traffic in the stores every day, only 10 people actually spent money??
Great reporting as usual Brian. Thanks!
I don’t quite understand these statements:
“There are nearly the exact same number of U.S. ZIP codes represented in the batch of cards for sale on Rescator’s shop as there are unique U.S. ZIP codes of Sally Beauty stores (~2,600).
More importantly, there was a 99.99 percent overlap in the ZIP codes. That strongly suggests that virtually all Sally Beauty stores were compromised by this breach.”
In metro Pittsburgh, there are 3 Sally Beauty locations, end to end, about 25 miles driving distance:
North Versailles, PA 15137
Pgh, PA 15236 (outside the city limits, but a Pgh post addr)
Bridgeville, PA 15017
End to end, there are 7 different zip codes. If I were a thief buying credit card data, the zip codes of these store locations is not demographically appealing. However, 15241, which is geographically adjacent to the Bridgeville zip code 15017, is a very high-end demographic, but it is not included in the csv file. Zip codes 15237 and 15238 are also prosperous areas, but neither is conveniently located to any of the 3 Pgh area retail locations. I wonder if 15237 and 15238 are offered for sale because they are numerically close (not geogrpahically close) to 15236. I’m beginning to think that the sellers are idiots, and that they don’t understand the USPS zip code system.
In the csv, it looks like there are 166 four-digit zips, which I assume are not valid, and 2486 five-digit zip codes.
It has nothing to do with the relative affluence of cardholders in certain zip codes. The feature is mainly there to help customers (crooks) use the stolen cards for longer periods before the cards are canceled. Hence, buying cards that appear to have been issued to people who live near you (assuming that you are then going to use those cards to shop in nearby big box stores) is the surest way not to set of triggers that the banks put in place to detect out-of-region purchases. Get it?
I understand what you’re saying, Brian. But my comment was poorly worded–I don’t think the criminal sellers get it, based on the way the cards are offered. I think that THEY think that USPS zip codes are numerically ordered for geographically contiguous zones.
Upper St. Clair, PA 15241 is a pot of gold. It is geographically adjacent to the Bridgeville 15017 store. But according to the csv, no cards from 15241 are offered. The frequency of card usage from 15241, at the Bridgeville store location 15017, almost certainly exceeds card number usage from outlying zip codes, at any of the 3 retail locations. Why would these cards not be offered?
I’m only focusing on my geographic area, so I might be missing the big picture in the criminal seller’s mind.
BTW, if you prefix a “0” to any of the the 4-digit zips in the csv file, you will get a valid zip code. I’m guessing the leading 0 may have stripped as researchers were massaging the list.
Usually love your articles and comments.
Not sure about this one.
Why tell the bad guys which zips are affluent?
Your own troubles has proven they read your stuff.
Also, a spell checker would be nice. They work at other sites. My typing is terrible (disabilities).
‘scuse me.
I replied as if Dan Martin s’ post and Krebs’ reply were all Krebs’.
My bad.
Who’s told them which zips are affluent? My story didn’t even touch on that. Not sure I understand your gripe. Algeranon.
Sounds like Potato vs Potatoe to me.
While the cards are offered to match the geobased montoring, it’s also true that cards from a neighborhood with demographics that don’t watch their CC bills closely would make those zip codes more valuable than a zip code where everyone watches every transaction closely.
One general way to do that is apply the US census bureau data to the zip code list. Or use the “110 wealthiest cities by zip code” for cards with likely higher credit limits (and perhaps more transactions in a month).
So sure, it’s by zip so the cards can be used without being flagged… but it’s also true that a card in zip 10022 has an average gross income of a bit north of $250K per year. Now if someone had a card from a zip code that had an average gross of $25K, and another of $250K, which card do you think would have the higher limit, and which so many transactions that it would be hard to flag?
There a whole lot of vectors, and it’s a good example of how data that doesn’t seem useful for a particular purpose is suddenly useful to someone else in a different way.
That’s why ALL data should be considered sacred, and the whole “no personally identifiable data” thing is nonsense. They got the $250K number from aggregation, but it’s used to exploit a specific card. So the aggregate data can and does hurt individuals.
Anyway, I think their complaint about you giving up the wealth data was way off.. but I think they could have made the case for ‘one man’s trash is an another man’s treasure”.
Anyway, good work on the zips, and it could indicate a larger breach than Sally presently has admitted.
Mr. Krebs,
If you read my “‘scuse me” I posted almost immediately after it explains that.
I had quoted 2 paragraphs of the story in a reply. Algeranon mistakenly attributed other parts of my post to Brian’s original article. I apologize for not making my reply clearer.
Just as bad, my line of thinking was off by a mile, and I’m just now climbing out of fhe rabbit hole I was lost in. It would be best for readers to ignore my previous replies to this article. 🙁
Any thoughts/ideas on whether debit PINs were also captured? I have read that the Target breach also included PINs from debit cards used at compromised devices. http://www.mbtmag.com/news/2014/03/mastercard-visa-focus-attention-security
As always, great post.
Cheers
Very interesting article. I like the analysis on how the zip codes match the store location for the selling of the underground card information. More screen shots
of the Rescator’s website would have been nice
Are the dumps being sold with Track 1 Data? Track 2 Data? both?
Both Kreb’s March 17th article and Sally’s site (listed above) say ‘Track 2’ data.
Hello Algeranon,
I don’t want to tip off the crooks. OTOH, I don’t want people in certain areas to have a false sense of security because their zip code does not appear in the csv file.
Chicago IT firm Trustwave sued in Target ‘s holiday hacking incident. http://www.chicagobusiness.com/article/20140325/BLOGS11/140329865/chicago-company-sued-over-target-data-breach
Is the Rescator approach of offering cards sorted by Zip new because no one had thought of it before, or is there something novel about the data grab that makes the zips available? I’m curious why we had not seen this type of selling strategy before.
Quoting Brian, in a reply he posted above:
” The feature [marketing by zip code] is mainly there to help customers (crooks) use the stolen cards for longer periods before the cards are canceled. Hence, buying cards that appear to have been issued to people who live near you (assuming that you are then going to use those cards to shop in nearby big box stores) is the surest way not to set of triggers that the banks put in place to detect out-of-region purchases. ”
The same was true when the Target data was marketed. I don’t know how fine a line (in terms of zip codes) that the illicit buyer could request. My feeling is that some individual zip codes should be far more valuable than others. I noticed that a zip code in my area adjacent to a Sally Beauty retail store was not included in the csv file, and I can’t understand why. Generally speaking, such data seems to lose value over time. Why would the criminal sellers withhold card data from a particularly prosperous zip code?
The criminal buyer can avoid triggering potential red flags by using the stolen card data in the same geographic area of the victimized card holder. But I would think that certain zip codes would have a greater likelihood of higher credit limits. This seems to me to be the most valuable card data to a criminal–a higher limit would increase the potential fraud, and would, at least to my thinking, lessen the significant fraud alert of a credit limit being exceeded.
My point is that people who shopped at Sally Beauty should consider themselves compromised, even if their zip code does not appear on the cvs file.
Many of Sally’s customers will be professional beauticians, cosmetologists, etc. If they used a business credit card … somewhere I recall they don’t get the same protections as consumer credit cards have. Are these cardholders going to experience a different kind of exposure ?
The zip codes are of the stores, not of the cards. I used their store locator on their website and matched all 9 stores within 50 miles of my home zip. There must be a hundred or more zips within 50 miles of my home.
I also checked and since December my wife used the same card there once in December and once in January. Fortunately, it’s a credit card and not debit. I update if I see any clue of fraudulent use.
Ah, okay. Zips are the STORE zips NOT customer zips.
I suspected that might be the case but wasn’t sure.
As Brian wrote, it’s for geo-blocking purposes. If you’re a financial institution doing this (a good thing, at least checking in with customer via phone call or email before allowing, etc.), criteria for blocking would be well outside area.
Might be a distance between zip code of customer and zip code where being used, or a simpler check of not same or surrounding states, something like that. Point is criminal can buy “local” card info and use locally and not be red flagged as out of geographic area. Has nothing to do with income level of anything.
Is that easier to understand?
Brian, as always, your reports are worthy of some serious reporting awards. Hopefully includes some financial rewards. You deserve it.
Without you, we’d have the fairly disgusting responses from places like Sally’s whatever to go on. That’s what these corporations count on. You are just such a level above their nonsense that they can’t get away with it anymore.
So, seriously, what’s a consumer to do. Brian, I learned about your site from the recent NY Times article and have now religiously followed it… for a couple of reasons. We were victims of the Target breach (One of our credit cards sent us a new one, informing us there was a problem with the old one) as well as probably the Michaels and Neiman Marcus (I live in NJ, so no it’s not strange to frequent both of those stores). Additionally, I’ve been put on Experian monitoring because my healthcare provider notified me that two laptops were lost or stolen with my information on them. Also, I’ve recently purchased a NAS device which I see on this site suffered some security holes and exploits.
Where do you begin to protect yourself? I’m following as much information as I can on your site but what’s realistically going to protect you? I’ve told my wife that we need to come up with new passwords for all of our accounts – online banking, e-mail, websites, etc. and change them all at once (which is likely to be a hassle). I am considering getting new cards for all of my accounts so that I have new CC numbers. I’m not happy about the Experian reporting, it’s opened a whole can of worms (bad information that they don’t seem willing to clean up, such as “aliases” for me that are bastardizations of my name). And I’ve taken my NAS off the internet because I’ve just decided that I can’t keep up with the constant port scanning and SSH attacks that I’m trying to harden against… which leads me to believe that I can’t really harden that device against zero-day exploits in any of the “toys” that the NAS builder bundles as nice value added things, like apache and SQL injection attacks etc. It’s just easier to explore my programmer fun on a cheap 1-1 account that doesn’t expose my data to hackers.
It really seems like 2014 is the year hacking went mainstream in a big way.
What’s an average consumer to do to best protect themselves?
Mike,
Credit card fraud is not such a big deal. You are not liable for fraudulent charges. What you should be spun up about is what you can do to protect your identity, credit file and credit score, since crooks (or corporations) tampering with those can have much more far-reaching repercussions. If you haven’t read it already, please see:
http://krebsonsecurity.com/2014/03/are-credit-monitoring-services-worth-it/
Having read Brian’s article, and the Sally Beauty press release, I have to make the choice. Whom do I to believe?
Hard choice, huh!
RE; using zipcode structure as breath of breach indicator
I agree the zipcodes may indicate that more stores were breached (perhaps all of them). At first I thought it wasn’t appropriate to extrapolate them that way, but I’ve changed my mind.
The assumption is that there are valid quantities in each of those zipcode bundles, and that they are not simply place holders.
As an example, many years ago I geocoded telephone numbers and had an SQL structure based on state. There were a few DBs that had the structures and code, but no data (US possessions, such as PR). If one listed the DB’s one would get every state, but in reality there were holes. The same may be true of the zipcode structure, depending on the process used to create the bundles (I could not tell from Brian’s article). So with the assumption that there were no null zipcode bundles (every zipcode represented had members) then it’s a fair guess that the breach was wider than Sally has reported to date.
On the otherhand, if the zipcode list of stores is merely an artifact of the structure of readying them for sale, then it’s usefulness as a breach indicator is in doubt.
I think Sally’s statement was appropriate (as much as I’m pissed that they mishandled other people’s information to begin with) given the circumstances and my limited view of the facts.
As Brian stated, “time will tell” (it has a way of doing that, doesn’t it?).