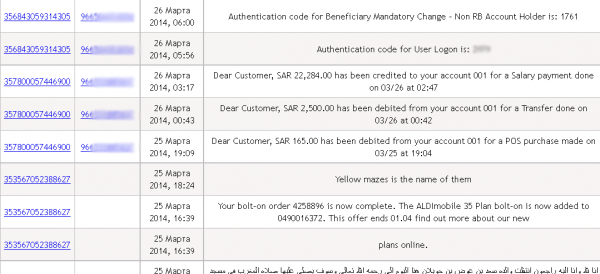
I recently encountered a botnet targeting Android smartphone users who bank at financial institutions in the Middle East. The crude yet remarkably effective mobile bot that powers this whole operation comes disguised as one of several online banking apps, has infected more than 2,700 phones, and has intercepted at least 28,000 text messages.
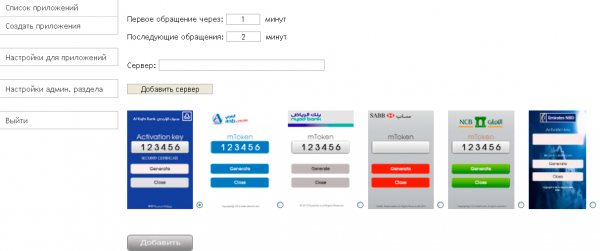
The botnet — which I’ve affectionately dubbed “Sandroid” — comes bundled with Android apps made to look like mobile two-factor authentication modules for various banks, including Riyad Bank, SAAB (formerly the Saudi British Bank), AlAhliOnline (National Commercial Bank), Al Rajhi Bank, and Arab National Bank.
It’s not clear how the apps are initially presented to victims, but if previous such scams are any indication they are likely offered after infecting the victim’s computer with a password-stealing banking Trojan. Many banks send customers text messages containing one-time codes that are used to supplement a username and password when the customer logs on to the bank’s Web site. And that precaution of course requires attackers interested in compromising those accounts to also hack the would-be victim’s phone.
Banking Trojans — particularly those targeting customers of financial institutions outside of the United States — will often throw up a browser pop-up box that mimics the bank and asks the user to download a “security application” on their mobile phones. Those apps are instead phony programs that merely intercept and then relay the victim’s incoming SMS messages to the botnet master, who can then use the code along with the victim’s banking username and password to log in as the victim.
This particular botnet appears to have been active for at least the past year, and the mobile malware associated with it has been documented by both Symantec and Trend Micro. The malware itself seems to be heavily detected by most of the antivirus products on the market, but then again it’s likely that few — if any — of these users are running antivirus applications on their mobile devices.
In addition, this fake bank campaign appears to have previously targeted Facebook, as well as banks in Australia and Spain, including Caixa Bank, Commonwealth Bank, National Australia Bank, and St. George Bank.
The miscreant behind this campaign seems to have done little to hide his activities. The same registry information that was used to register the domain associated with this botnet — funnygammi.com — was also used to register the phony bank domains that delivered this malware, including alrajhiankapps.com, commbankaddons.com, facebooksoft.net, caixadirecta.net, commbankapps.com, nationalaustralia.org, and stgeorgeaddons.com. The registrar used in each of those cases was Center of Ukrainian Internet Names.
I am often asked if people should be using mobile antivirus products. From my perspective, most of these malicious apps don’t just install themselves; they require the user to participate in the fraud. Keeping your mobile device free of malware involves following some of the same steps outlined in my Tools for a Safer PC and 3 Rules primers: Chiefly, if you didn’t go looking for it, don’t install it! If you own an Android device and wish to install an application, do your homework before installing the program. That means spending a few moments to research the app in question, and not installing apps that are of dubious provenance.
That said, this malware appears to be well-detected by mobile antivirus solutions. Many antivirus firms offer free mobile versions of their products. Some are free, and others are free for the initial use — they will scan and remove malware for free but charge for yearly subscriptions. Some of the free offerings include AVG, Avast, Avira, Bitdefender, Dr. Web, ESET, Fortinet, Lookout, Norton, Panda Cloud Antivirus, Sophos, and ZoneAlarm.
Incidentally, the mobile phone number used to intercept all of the text messages is +79154369077, which traces back to a subscriber in Moscow on the Mobile Telesystems network.




This is not new and Intelcrawler already blogged about it two months ago. This is even older… and this specific malware has been used since 2013.
Has anyone ever called you Mr Krabs or Mr Kebab? krebs reminds me of it.
Please reply
mmmmmmm kebabs…now I’m hungry for one.
Mobil is where it is at now. KOS not only keeps improving, but Brian is going farther ahead of the game every day! Thanks!
I vote for Avast – On PCs it has NEVER let me down. On mobile – I have no idea, because I’m not particularly mobile yet. I would certainly trust them 1st at any rate.
Ditto on all of the above. KOS and Avast are awesome.
AppCloud Android botnet
Payment via BTC / PM
AppCloud apk + panel and installation = 299$
AppCloud source code (panel +builder + src) = 1999$
It’s not about the user and the device they use. Internet Banking users trust their institutions to provide security. It may not be the agreement between them, nuts that’s the reality.
Your average technology user cannot be a security expert.
Institutions need to take control and provide secure browsing wrappers. see http//www.quarri..com. This is smart technology.
real? see here
https://rghost.net/53686114/image.png
(Apps On-the-Cloud)
2700 bots or 28 000 messages that is like 10 messages per user .Get the F@ck out of here Mr Plebs . Kids in the first grade have more bots then this .
Can you imagine if the same thing happened with big name corporations here in the U.S.? The outrage would be astounding… Bank of America, Wells Fargo, PNC, etc.? The Android market/Google Play would explode.
I feel bad for those affected though.
https://rghost.net/53686115/image.png
on sale threat coder tell with tech (Apps On-the-Cloud) all fake app can change easy for any bank app
why Bank of America, Wells Fargo, PNC, etc.? and all USA banking app can’t make by it’s?
Such a sales job, you should try craigslist instead.
i’m research it’s on blackhat forum and shared info here for all know about it’s not for sale! you real know about it’s?
Wow. Try Googling Xylibox. See what happens.
Such an idiot, you should try playing in traffic.
Check out Brian’s blog on this guy. What nerve. http://krebsonsecurity.com/tag/xylibox/
Xylitol pinged me privately and said that it wasn’t he who posted those comments, that it was someone else impersonating him.
I knew this WAS NOT Xylitol. His rep in the anti-malware community is what it is: solid. His research and analyses are unquestionably among the best. His reverses are brilliant. His cracking is near legendary. Whoever, attempted to post as Xylitol garbled the English by design. It only fooled a few who are not familiar at all with Xylitol’s work. Xylitol is a Global Moderator on Kernelmode.info.
I use CMS security and AVG antivirus on my cell phone, that seems to take care of any problems
I don’t know who’s using the nick ‘Xylibox’ here but it’s definitely not me.
Also just for information, RSA also talked about this here: https://blogs.rsa.com/behind-scenes-fake-token-mobile-app-operation/
Regards
__
/Xyl
I use the Bitdefender for my Android phone. They come in two different ways:
1. You can buy the total package that will include the mobile app for free with your subscription.
2. You can buy the PC version total package and pay for the mobile app separately.
Users should be using antivirus on their mobile devices. They should also be using best practices when using their mobile devices as well. Users need to learn what looks suspicious and not to fall victim to fake applications that store malware. The general populace downloads apps that “have been removed from the app store/can only get it here now” apps that seem too good to be true, or click on links or follow random text links that get them with a drive-by download of malware. Once users learn best practice and mobile security essentials, they will stop getting malware not only on their mobile devices, but also on their home computers and anything else connected to the internet.
Pretty nice post. I just stumbled upon your weblog
and wanted to say that I have truly enjoyed surfing around your blog posts.
In any case I’ll be subscribing to your rss feed and I hope
you write again very soon!