Microsoft is warning Internet Explorer users about active attacks that attempt to exploit a previously unknown security flaw in every supported version of IE. The vulnerability could be used to silently install malicious software without any help from users, save for perhaps merely browsing to a hacked or malicious site.
In an alert posted on Saturday, Microsoft said it is aware of “limited, targeted attacks” against the vulnerability (CVE-2014-1776) so far.
Microsoft’s security advisory credits security firm FireEye with discovering the attack. In its own advisory, FireEye says the exploit currently is targeting IE9 through IE11 (although the weakness also is present in all earlier versions of IE going back to IE6), and that it leverages a well-known Flash exploitation technique to bypass security protections on Windows.
 Microsoft has not yet issued a stopgap “Fix-It” solution for this vulnerability. For now, it is urging IE users to download and install its Enhanced Mitigation Experience Toolkit (EMET), a free tool that can help beef up security on Windows. Microsoft notes that EMET 3.0 doesn’t mitigate this attack, and that affected users should instead rely on EMET 4.1. I’ve reviewed the basics of EMET here. The latest versions of EMET are available here.
Microsoft has not yet issued a stopgap “Fix-It” solution for this vulnerability. For now, it is urging IE users to download and install its Enhanced Mitigation Experience Toolkit (EMET), a free tool that can help beef up security on Windows. Microsoft notes that EMET 3.0 doesn’t mitigate this attack, and that affected users should instead rely on EMET 4.1. I’ve reviewed the basics of EMET here. The latest versions of EMET are available here.
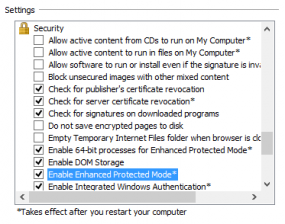
According to information shared by FireEye, the exploit also can be blocked by running Internet Explorer in “Enhanced Protected Mode” configuration and 64-bit process mode, which is available for IE10 and IE11 in the Internet Options settings as shown in the graphic above.
This is the first of many zero-day attacks and vulnerabilities that will never be fixed for Windows XP users. Microsoft last month shipped its final set of updates for XP. Unfortunately, many of the exploit mitigation techniques that EMET brings do not work in XP.




As @dinodaizovi tweeted, the first zero-day for IE that WON’T be fixed in Windows XP. Ready, set, go…
Is this an XP issue or a IE issue? If it’s an IE issue, it’ll be patched on XP as easily as on 8.
Microsoft isn’t issuing patches for IE on Windows XP either – even it still supports that version of IE on later OSes
Where did you see that? My understanding is that XP is no longer receiving updates as an operating system. Other things, such as IE and Office, will still receive updates until they are end of life. IE 8, for example, is officially end of support in 2020, regardless of operating system. IE 8 runs on XP….
I hate to burst your bubble but when Microsoft releases patches they do so by OS. So an IE patch could be for Vista, Windows 7, Windows 8/8.1. So while the specific software may not have reached EOL the patch will not apply to XP.
Correct. Also, it’s important to note that this particular exploit that Microsoft is talking about targets IE 9-11, and according to FireEye it will not work against IE8 or lower. IE9, 10 and 11 will not run on XP.
That doesn’t mean the attackers couldn’t re-write the exploit so that it targets lesser versions of IE; indeed, Microsoft said every version of IE from 6-11 was vulnerable to this flaw.
I didn’t get that. Here’s what I saw at FireEye:
“The vulnerability affects IE6 through IE11, but the attack is targeting IE9 through IE11.”
IE8 updates can still be obtained directly from Microsoft’s website until EOL.
Since this is an IE exploit issue on XP devices, can the XP user just use Google Chrome, FireFox, Safari, etc to avoid the exploit?
Thanks,
Doux
Won’t be fixed in XP? XP users can fix it straightaway, by following this simple instruction:
CHANGE TO A DECENT BROWSER!
You’re welcome.
Obviously, use something other than IE as long as it is NOT Firefox. After they “fired” their head honcho a couple of weeks ago in an attempt to politicize a man’s way of thinking, we switched to Chrome and like it very well, thank you Firefox.
The guy quit.
forced out by fagrits.
Firing him was the right thing to do.
Oh, I’d love to hear why. This ought be to good.
How about he was a poor fit for the culture of the company?
Personality / Cultural fit is a harder thing to come by than tech or business skills in this hiring environment.
Oh, so interesting. It great how the people demanding tolerance and equality will mob up to silence differing opinions. Tolerance Ave. and Equality Ln. are two way streets. It seems your movement is more than hypocritical.
Companies don’t have a culture, it’s a myth. The only things that matters are success, either in share price, return to investors, or in the case of Mozilla the donations/funding received.
A security blog is not the appropriate venue for complaining about how your intolerance is not being tolerated.
BS! You are exactly the person the press release was meant for. With no critical thinking. He was forced to quit because had different PERSONAL views. Where is freedom of speech? Does it apply only to queers? As soon as a straight person objects, it’s discriminatory?!
Of course he has freedom of speech. That is why he wasn’t locked up for what he said. But you see, freedom of speech works both ways. The people did not like what he had to say, and they spoke against his discriminatory views. Mozilla did not feel like enduring the continued wrath of a vocal majority, and so they let him go.
Does that make sense to you?
Of course he has freedom of speech. No-one stopped him saying anything. What they did was say that they would no longer use Firefox while he worked for the company. This has nothing to do with freedom of speech. Next you’ll be saying I should still be a Go Daddy customer because Bob Parsons has the right to bear arms, or even elephant tusks. A simple business decision was made. The guy has always had, and still does have his freedom of speech.
“Where is freedom of speech? Does it apply only to queers?”
Dear sir,
Freedom of speech seems to be thriving as witnessed by your own homophobic rant. Perhaps you’d care to enlighten us on how you feel about Donald Sterling or Clive Bundy. Two more gentlemen just exercising their freedom of speech. Are you upset because so many are demanding that Sterling step aside?
Since you make liberal use of the word queers, I’m interested to know how you refer to different minorities.
No, he shouldn’t have been fired if that is indeed what happened. I’m sure the lawsuit or lack of will give us a better indication of that.
He was forced out not because of something he was doing today, but because he made a private donation years ago to a ballot initiative supporting “traditional” marriage. This was an unforgivable crime in the eyes of the Thought Police.
Was what Mozilla did legal? Sadly yes. “Freedom of Speech” only stops the government from restricting our speech (pause here while the laughter dies down). A private company can restrict all it likes. Should Mozilla have caved under pressure from the Perpetually Indignant? Absolutely not.
But they did
Believe it or not, people like you who discriminate against large segments of the population are becoming more and more of a minority with every day that passes. You have many more years to look forward to being pissed off because someone got equal protection under the law. It’s going to happen more and more frequently as the bigoted population dies off and is replaced with more tolerant and civilized folks.
Interesting perspective……..so what you are saying is that you can be completely intolerant of Christians and people of faith, and ignore their rights, which should be equal to those who make your prized lifestyle choice, but in the end, you don’t think that portion of the population deserves any rights. So, years ago, this man donated some money to a faith-based movement to preserve traditional marriage. Because he did this, he should be forced out of his livelihood and made into a social pariah? This kind of shortsighted thinking, along with the threats that people of faith are “dying off” and the more fecal-oriented, open minded, brilliant, world-brain-trust types will prevail is a hypocritical and somewhat bigoted position. Maybe you should lose your job because you donated to some left-wing cause several years ago. Guess that doesn’t quite work for you.
He left because he had placed himself in an untenable position for a CEO.
It is important to recall that one Mozilla board member, John Lilly, left the board rather than be involved with the hire. Lill’s sense of propriety extended to making very little comment.
In all, a sad moment for Mozilla, and one which will soon enough fade into the dustbin of history. Except for the bigoted dead-enders.
So in your worldview, if a person has morals and ethics and believes in the kind of marriage we have had for 5,000 years, and they donate some money to others who believe that, his position is somehow now “untenable?” Do you now how intolerant and bigoted that sounds? That is the problem with people who are forcing same-sex “marriage” on the majority of the population that don’t buy into it. They hypocrisy of those of you who demand that we all walk in lock-step, and at the same time accuse us of being out of step, is the truly untenable position. Let’s take your job away because you donated to the wildlife fund several years ago.
Homophobia, the last safe zone for cowardly bigots.
Mozilla, the front line for the gay-labeld “Gay Gestapo” http://twitchy.com/2014/04/04/bastion-of-intolerance-and-punishment-tammy-bruce-shreds-mozilla-for-caving-to-gay-gestapo/
gays = America’s worst bullies You fall at our feet, or we destroy you, your reputation, your livelihood and we will accuse you of things you aren’t
I agree! We removed Firefox from all of our Ubuntu PCs. We even removed Thunderbird. Any Mozilla software is no longer used by my wife or myself.
Agreed, I yanked all Mozilla products too… I can’t handle hypocritical bully tactics by anyone.
You’ve switched to the MOST unstable browser out there simply because Mozilla’s head honcho is no longer with the company? Chrome is weak and fraught with more security holes than the swiss chesse that is IE.
Mozilla’s removal of a CTO does not increase your vulnerability to this exploit.
I assume you’ll stop using Javascript as well since the person in question created it as well…
I agree……..go with Chrome. I’m sick of these companies forcing their political agenda on the rest of us. (like Starbucks)
In the case of WinXP, the best line of defense is to switch to a non-Admin user account, then set up a Software Restriction Policy in disallowed-by-default mode, and close all the loopholes with additional Path Rules as needed. The typical exploit, even if it succeeded, would find its payload impossible to execute from any disk location that the user’s now-exploited software could save it to.
As a gotcha, this requires XP Pro or XP Media Center Edition, and it will still be at risk from memory-based attacks that don’t execute from disk. And running XP as a non-Admin is an exercise in frustration compared to its successors. If you can move on, do it.
Yep, everyone knows how to do that .
I did put up a guide showing everyone how to do it, if they want to. If you do an Internet search for Software Restriction Policy, it comes up just below the results from some upstart named “Microsoft” 😉
Another useful mitigation for XP users is the [free] utility DropMyRights. No longer available from M$, it can be downloaded at http://www.it.cornell.edu/security/howto/less_priv.cfm (for an overview and more detailed discussion, see http://www.cnet.com/news/every-windows-xp-user-should-drop-their-rights/).
mechBgon, let’s say you set up a SRP that allows the user to run java.exe from the Java install dir. Then let’s say an exploit causes a malware Java payload (say a jar file) to get saved to a directory that is disallowed by the SRP. Then the exploit tries to run the jar file using java.exe. Would the payload execute since running java.exe is allowed, or would it not execute since the payload is in a disallowed directory?
It’s been a while since I actively rammed my crash-test-dummy computer into Java exploits for a hobby, but I think you would see this:
1. Java gets used to run the .jar file from the user’s temp directory within their user profile. Since .jar isn’t a filetype affected by SRP (unless you add it yourself), that is likely to work.
2. what the .jar file is probably going to be used *for*, is to download and execute a payload. .EXE, for example. If this is happening in the context of the user and he/she is a non-Admin, now SRP intervenes against an .EXE written to a disk location that the user can write to.
Many applications depends on IE to work, Skype is one of them AFAIK!
I don’t think this is true of Skype. Skype runs perfectly well on my PC, and I’ve uninstalled IE long ago.
Skype ran just fine for me on Linux, and I hear it works great on Mac too.
I used to think the same way but now I’m truly confused about this topic. NSS Labs report that IE is safest than Chrome or Firefox (against Socially Engineered Malware and Phishing). I’d like to hear your comments.
https://www.nsslabs.com/reports/categories/test-reports/browser-security
Social engineering is about tricking the user into compromising their system. In this context, it is usually by getting them to click a link, open an attachment, etc.
The vulnerability in this blog post does not require social engineering to exploit. A person browsing with IE merely needs to visit a hacked or malicious site that exploits this flaw to have their system compromised.
I have some add-ons that are not compatible with 64-bit mode, so I do not have the option to enable 64-bit processing. Will Enabling Enhanced Protection Mode alone alleviate the vulnerability?
How long will it be before hackers exploit a currently “unknow” vulnerability in Win XP? Right now, it’s that you avoid using I.E. – although, browser internet settings seem centrally-located as in what you change in I.E. affects all the other browsers in the Window O/S environment. Who’s to say this vulnerability isn’t going to be part of an issue with the O/S and thus, everyone running XP will be wide open for any attack by hackers
“browser internet settings seem centrally-located as in what you change in I.E. affects all the other browsers in the Window O/S environment.”
Totally untrue. You either know nothing about computers or you’re a very poor troll. Possibly you’re a Daily Mail reader as well.
Use a different browser.
Perhaps I’m an overly suspicious XP user, but I’d feel more certain of that warning if it had come from someone other than Microsoft. Fortunately I use Firefox, Thunderbird, and plenty of security and using a number of site scans that report whether a URL is safe or not. WOT and Ghostery are two of my favorites. One rates the site, the other stops scripts.
If they were saying that it only applied to IE 8 and older, you might have a point. But they have said the bug is present in IE 9, 10 and 11, so it doesn’t just effect XP users.
this is a flash exploit
“Do Not Track Me” is awesome in addition to the Ghostery. They have stopped tens of thousands of trackers and cookies on our machine.
In case people are wondering, the Microsoft advisory indicates the flaw is in Microsoft’s VML component. If you don’t recognize VML, you aren’t alone, it was a 3D markup language well over a decade ago. Other than being apparently buggy, it’s been forgotten by pretty much everyone (someone probably used a fuzzer to find this bug…).
I’m tempted to disable it after MS fixes this. I haven’t seen anyone using VML in ages.
VML is a legacy API according to Microsoft.
“VML, a feature that is deprecated as of Windows Internet Explorer 9”
Disabling VML is easy enough – from
https://technet.microsoft.com/library/security/2963983 :
“Unregister VGX.DLL
1.Click Start, click Run, type “%SystemRoot%\System32\regsvr32.exe” -u “%CommonProgramFiles%\Microsoft Shared\VGX\vgx.dll”, and then click OK.
2.A dialog box appears to confirm that the un-registration process has succeeded. Click OK to close the dialog box.
Impact of Workaround:
Applications that render VML will no longer do so once vgx.dll has been unregistered.”
Thanks, Hayton.
Thanks Hayton!
Question:
If VML has already been deprecated in IE 9.0, then why is IE 9.0 still listed as vulnerable?
Does vgx.dll remain registered (as a remnant of IE 8) in IE 9.0 despite not being used? If so, its a good idea to unregister this not needed .dll anyways — for those users that are on IE 9.0 and up!?
Thanks again!
Ed
Yes, exactly that. Once a DLL (or similar) is registered on your PC then it will remain so, and therefore accessible and usable, until it is unregistered or removed (which requires unregistering anway).
Thank you. Eloquently put, and better than I could have phrased it.
I would also suggest trying out ActiveX Filtering. If a potential victim were lured to a rigged website*, Flash Player and other ActiveX doodads would be in a default-deny posture. Where I work, we use ActiveX Filtering (along with EMET, Enhanced Protected Mode and 64-bit tab processes) as best practices.
Users of other browsers can similarly limit Flash Player and other likely targets with a click-to-play approach. In any case, the tradeoff is a little ease-of-use for a layer of proactive security.
*assuming the rigged site is not on the user’s whitelist for Flash Player, that is. A watering-hole attack would negate that layer of protection.
Thanx for the warning. I checked my Internet Options and found the Enhanced Protection Mode unchecked due to a browser reload.
However
now I get a notice at the Amazon log-in page that says ‘wants to load Adobe Shockwave Player” !!!!!!
I deny it to do that. The sign in proceeds OK anyway.
Why in the world does it want to load that on the log-in page?
Adobe Shockwave Player? Could it mean Flash Player? Flash is still called Shockwave Flash by many websites, isn’t it? (I have the Flash Player plugin disabled in Firefox and I get no such message on Amazon’s sign-in page.)
““Enhanced Protected Mode” configuration and 64-bit process mode, which is available for IE10 and IE11 in the Internet Options settings as shown in the graphic above.”
To reach it you have to go Internet Options – Advanced – Settings, and in Settings page down to Security (IE 11).
Going to be fun and games for all of us who have no control over what edition of IE the Borg Collective installs on our office PCs. May have to bring in my personal notebook to get some work done.
Does they permit you to install another browser ?
I normally use chrome, but thanks to this I’ll be using IE the next few weeks at work, maybe I’ll hit the jackpot and get upgraded from windows xp!
unfortunately some institutions require IE.
If this exploits a “well-known” bug, why is this a zero-day exploit?
The technique is well known, but it’s been used in a new way. Fireye has the technical details if you’re interested.
http://www.fireeye.com/blog/uncategorized/2014/04/new-zero-day-exploit-targeting-internet-explorer-versions-9-through-11-identified-in-targeted-attacks.html
I think the best protection for people still running XP is to run Sandboxie or Shadow Defender, etc. Basically anything that will intercept all writes to your hard drive so that your computer doesn’t get infected. Of course malware could still run in memory and capture keystrokes, so even those defenses aren’t perfect.
Just want to clarify one thing here.
I totally understand that Microsoft will not issue patches for the XP OS anymore. But what about products which are still current but are installed on XP systems. Such as Office 2010 or IE 11. Will the XP windows update service not draw down patches for that software anymore also?.
I no longer use XP so I can’t test this. Can anyone just clarify this for me. Thanks.
There was an Office 2010 update right after XP EOL.
Each piece of software generally has its own release cycle and environmental of life schedule.
IE was considered an integrated component of the OS which is why it’s end of lifing at the same time. But normal software has a much shorter life span than OS software.
Ahhhh Good Ole INTERNET EXPLODER.
Didn’t they just get their buns handed to them at the pwn to own? And Black hat? You’d figure, if they continue to have these issues, someone would figure a way to at least make this heap more secure.
Too bad I cannot rip it from the guts of the operating system and flush the load down the commode and use something just a little bit more secure.
Commmon. I have heard of job security – creating work to keep your job, but this is more like job impurity when it comes to good ole Internet Exploder.
*ALL* browsers got their buns handed to them at Pwn2Own…Only IE 11 with EMET 4.0 on Windowns 8.1 survived. Switching browsers to avoid 0-Days is futile. Install EMET and continue to use IE as it’s the most secure configuration available.
Hehehehehe. Yep, that’s right, the ole’ party line. Software can be broken by other software. There is stuff out there that can simply make any security package look stupid.
The most configuration is good for another round of issues with the software. Wait another month or two and you will see the same ole party line once again.
Internet Exploder needs to be a separate beast and easily removed. This people can choose a browser they feel most secure with and not have to worry about something they consider useless and unused.
There will always be holes – for one purpose or another. No matter how much fuzzing or QA they want to perform on Internet Exploder, its one of the more popular surfing engines out there and its use will be, how should I say, viewed by multiple parties on a whim.
Security solutions require more than one layer of defense. putting all your eggs in one basket, from the same developers is not a good idea.
FireEye recommend disabling the Flash plugin in IE; Microsoft recommend (inter alia) disabling VML. IF you do both I don’t see how this vulnerability at least could be effective. This IE zero-day can probably be countered without too much inconvenience or loss of productivity.
That’s my reading of it. Anyone disagree?
Does anyone know if EMET 4.0 can protect against this? The advisory states to use 4.1 and it explicitly says 3.0 will not mitigate, but it does not mention if 4.0 will or not.
I’m not a computer expert so I apologize if my questions are basic:
I decided to “enable enhanced protection mode” on my IE11. Now I am getting a message from Spybot that says its IE protection is not compatible with enhanced security features enabled so they have disabled their IE protection on my computer. Is that OK? Any suggestions?
I have a 64-bit machine but do not have 64-bit process mode in that list of security features on internet options. I re-started my computer after enabling enhanced protection mode, but 64-bit process mode is still not there. Why do you think I don’t have that?
What are the disadvantages to enabling enhanced protection mode in IE? There must be some or wouldn’t it be enabled as a default?
I appreciate your comments.
muffin, are you on Windows 7? If so, I believe the answer is that enabling EPM on 64-bit Win7 does also switch you to 64-bit tab processes.
To confirm that, you could download and run Microsoft Sysinternals Process Explorer. Once it’s running, click View > Select Columns, and choose “Image type” to see what’s 32-bit and what’s 64-bit. Your IE frame will have another IE listed below it for each tab you’ve got running. If they’re 64-bit, that’s what you’re after.
“What are the disadvantages to enabling enhanced protection mode in IE? There must be some or wouldn’t it be enabled as a default? ”
The trade-off is that many browser add-ons aren’t compatible with EPM. I have a real-life example: my surveillance cameras use an ActiveX control to display the video when they’re viewed in a web browser, and that ActiveX control isn’t EPM-compatible. So I opt down to “regular” Protected Mode for their Web pages when the gold bar appears to give me that option. It looks like this, and you would use the “Disable” button:
https://i.stack.imgur.com/UtWG4.png
mechBgon: Yes, I’m on Windows 7. I do have a 64-bit operating system. I’m not going to run the Microsoft Sysinternals Process Explorer you suggested. It sounds like something that’s beyond my slim computer knowledge. Thank you for your info on the disadvantages of EPM. I think I’ll be fine with it. Thanks so much.
I’m confused by the “Flash exploitation technique” – the link behind that text points to Brian’s excellent EMET article but it doesn’t say anything about flash exploitation. Does the Adobe patch released today have anything to do with mitigating this IE vulnerability, or is the only viable solution for IE users (until MS releases a patch) to run EMET and hope for the best?
Sorry, Hamilton, that link got borked. It should point to:
http://www.fireeye.com/blog/technical/cyber-exploits/2013/10/aslr-bypass-apocalypse-in-lately-zero-day-exploits.html
It’s fixed now. Thanks!
Ok I switched to chrome but now Rapport says when I try to login to my.yahoo.com that I am entering my info into a different website than the one I intended. How am I suppose to know if the website is any good and whether I should proceed. For me the internet is broken right now and I am afraid to use it. I will have to go to the bank to get my financial work done today.
I’m biased because it’s my company, but a great (and secure) solution for corporations that still need IE (even on XP) is to use Chrome + IE Tab: http://www.ietab.net/internet-explorer-security-fix-chrome-ie-tab
Chrome supports the Gay agenda. Use a man’s browser, IE.
Don’t go to gay porn sites, they are the ones that have the virus!
Q? How many queers does it take to change a light bulb?
A? NONE. It’s not the light bulb that needs to change.
For some reason all of your latest posts have a date of April 14 even though they quite clearly are more recent.
The big number is the day.
Pity all that lobbying money Microsoft has spent to influence the government, $8,086,000 in 2012 and $10,490,000 in 2013 might have been better used to ensure a little more security.
However, that money doesn’t come close to Google’s lobbying efforts which were $18,220,000 in 2012.
So much sensationalism by the media on this. Example headline: “Homeland Security: Don’t Use Internet Explorer”. What they actually said was: “US-CERT recommends that users and administrators review Microsoft Security Advisory 2963983 for mitigation actions and workarounds. Those who cannot follow Microsoft’s recommendations, such as Windows XP users, may consider employing an alternate browser.”
Not quite the same thing.
I did consider employing an alternate browser, but decided not to. Why? Because the only indication of this vulnerability being exploited is a “limited, targeted, attack”. The FireEye bulletin says “Threat actors are actively using this exploit in an ongoing campaign which we have named “Operation Clandestine Fox.” However, for many reasons, we will not provide campaign details. ”
My interpretation of those statements is that the Chinese government hacking organization used this vulnerability to attack someone, somewhere, and FireEye was directed to not spill any details by a high level government agency.
The news media should cut back on the sensationalism and instead report the facts. With what is currently known, I believe the chance of anyone being a victim of this attack (other than the original victim) is next to zero. If there is any indication of a more widespread attack or use of this exploit, that should be reported and we should all be concerned. Until then, this is all just a bunch of hype. I plan to continue using IE and apply the fix from Microsoft once it is available..
Let’s just use what the government uses. All our information is safe with them. 🙂
Since Microsoft is also advising the same workaround as Fireeye, I feel it might be helpful to warn the newbs like me to be careful about a couple of things in IE11.
First, when you go to settings/internet options your are faced with several tabs. Your initial response might be to go to settings/internet options/security and if you do at the bottom of the page there will a check box which will allow you to ‘Enable Protected Mode’ which might sound a little like what Brian is talking about, but which is NOT the box[es] you need to be concerned with.
Instead you need to go to settings/internet options/advanced. It is under that tab you will find the ability to ‘enable enhanced protection mode’ and ‘enable 64 bit processes for enhanced protection mode’.
I prefer Maxthon as a perfect browser and very fast. Maxthon is used by a greater number of people then all the editions of IE together. Maxthon is available in almost all lanquages and has a perfect system for adding bookmarks. It handles HTML5 very nice.
Give it a try on http://www.maxthon.com/ and choose Maxthon for Windows.
Succes guys.
Out of curiosity:
1. Is whatever version of IE that’s in Windows RT vulnerable?
2. Are there any other browsers available for Windows RT?