The U.S. Justice Department today announced a series of actions against more than 100 people accused of purchasing and using “Blackshades,” a password-stealing Trojan horse program designed to infect computers throughout the world to spy on victims through their web cameras, steal files and account information, and log victims’ key strokes. While any effort that discourages the use of point-and-click tools for ill-gotten gains is a welcome development, the most remarkable aspect of this crackdown is that those who were targeted in this operation lacked any clue that it was forthcoming.
To be sure, Blackshades is an effective and easy-to-use tool for remotely compromising and spying on your targets. Early on in its development, researchers at CitzenLab discovered that Blackshades was being used to spy on activists seeking to overthrow the regime in Syria.
The product was sold via well-traveled and fairly open hacker forums, and even included an active user forum where customers could get help configuring and wielding the powerful surveillance tool. Although in recent years a license to Blackshades sold for several hundred Euros, early versions of the product were sold via PayPal for just USD $40.
In short, Blackshades was a tool created and marketed principally for buyers who wouldn’t know how to hack their way out of a paper bag. From the Justice Department’s press release today:
“After purchasing a copy of the RAT, a user had to install the RAT on a victim’s computer – i.e., “infect” a victim’s computer. The infection of a victim’s computer could be accomplished in several ways, including by tricking victims into clicking on malicious links or by hiring others to install the RAT on victims’ computers.
The RAT contained tools known as ‘spreaders’ that helped users of the RAT maximize the number of infections. The spreader tools generally worked by using computers that had already been infected to help spread the RAT further to other computers. For instance, in order to lure additional victims to click on malicious links that would install the RAT on their computers, the RAT allowed cybercriminals to send those malicious links to others via the initial victim’s social media service, making it appear as if the message had come from the initial victim.”
News that the FBI and other national law enforcement organizations had begun rounding up Blackshades customers started surfacing online last week, when multiple denizens of the noob-friendly hacker forum Hackforums[dot]net began posting firsthand experiences of receiving a visit from local authorities related to their prior alleged Blackshades use. See the image gallery at the end of this post for a glimpse into the angst that accompanied that development.
While there is a certain amount of schadenfreude in today’s action, the truth is that any longtime Blackshades customer who didn’t know this day would be coming should turn in his hacker card immediately. In June 2012, the Justice Department announced a series of indictments against at least two dozen individuals who had taken the bait and signed up to be active members of “Carderprofit,” a fraud forum that was created and maintained by the Federal Bureau of Investigation.
Among those arrested in the CarderProfit sting was Michael Hogue, the alleged co-creator of Blackshades. That so many of the customers of this product are teenagers who wouldn’t know a command line prompt from a hole in the ground is evident by the large number of users who vented their outrage over their arrests and/or visits by the local authorities on Hackforums, which by the way was the genesis of the CarderProfit sting from Day One.
In June 2010, Hackforums administrator Jesse Labrocca — a.k.a. “Omniscient” — posted a message to all users of the forum, notifying them that the forum would no longer tolerate the posting of messages about ways to buy and use the ZeuS Trojan, a far more sophisticated remote-access Trojan that is heavily used by cybercriminals worldwide and has been implicated in the theft of hundreds of millions of dollars from small- to mid-sized businesses worldwide.
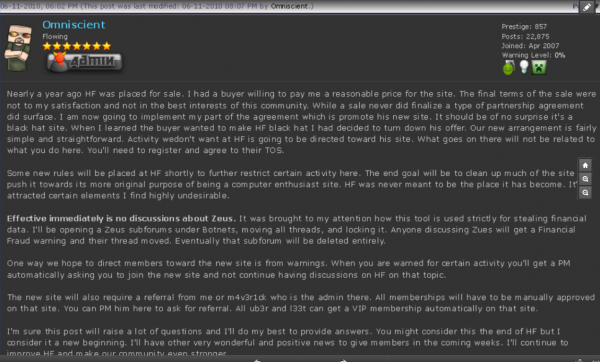
Hackforums admin Jesse “Omniscient” LaBrocca urging users to register at a new forum — Carderprofit.cc — a sting Web site set up by the FBI.
That warning, shown in the screen shot above, alerted Hackforums users that henceforth any discussion about using or buying ZeuS was verboten on the site, and that those who wished to carry on conversations about this topic should avail themselves of a brand new forum that was being set up to accommodate them. And, of course, that forum was carderprofit[dot]eu.
Interestingly, a large number of the individuals rounded up as part of the FBI’s CardProfit sting included several key leaders of LulzSec (including the 16-year-old individual responsible for sending a heavily armed police response to my home in March 2013).
In a press conference today, the FBI said its investigation has shown that Blackshades was purchased by at least several thousand users in more than 100 countries and used to infect more than half a million computers worldwide. The government alleges that one co-creator of Blackshades generated sales of more than $350,000 between September 2010 and April 2014. Information about that individual and others charged in this case can be found at this link.
For a glimpse at what the recipients of all this attention went through these past few days, check out the images below.





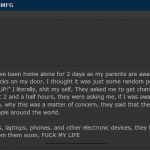
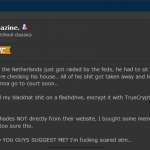

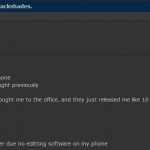
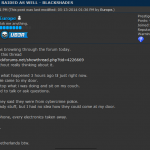


Got this text box when reading your site
http://oi61.tinypic.com/ngri47.jpg
Hope info is useful to you.
Yep, thanks. Was trying out a new plugin that did some bozo ajax calls to a protected directory, which threw up the prompt. Should not be an issue. I republished the post with the archive of images at the bottom. Not a useful or fun, but oh well.
I was getting that log in box too for a while, but it’s not showing up now.
Computers are TOYS. They are used for Playing GAMES. Until the world returns to the entertainment values of computers, a lot of people will get hurt.
From your mouth to the industries ear, its been ages since most companies made a great PC game, now they like to focus on the consoles and port something over that was designed for 1/3 the horsepower and has bad controls and UI.
Its because of piraters and hackers, which have never affected profits on consoles….. Most Devs and gamers started abandoning the PC after 2004.
IMO 2013 was the worst year for pc gaming. BF3 was a big budget release. and the first time I ever saw a developer admit they have been hacked and publicly apologize to the community on their main page. EA and punkbuster(even balance) were constantly getting ddos’d offline. (as were most other games I played) One time EA battlelog went down for I think 10 days lol. I even caught a virus, from battlelog, which came out at that same time, which EA wouldn’t even acknowledge. It seems like all the servers with honest fair play admins, were constantly under attack until they were eventually raged offline and out of the game.
SO many Accounts and credit cards got stolen it was ridiculous. You would think EA wouldn’t even allow links in their forums anymore. One of the top EA moderators, EA Sulti, even tried to hack me through the browser after sending me a personal message. Of course he denied it. The game is still full of fakes, and the only servers left are probably the guys that were booting competing servers offline. But I still play everyday though. They can’t discredit me by saying I’m a whiner whos bad at the game…lol So they just censor me. I’m one of the last mohicans.
I know one kid who outed the NX hack site for selling the ability to boot players from a bf3 server, which was a bonus along with their other hack subscription. Which many people didn’t believe even possible. There was a mass banwave and the kid who whistleblowed on them had his mobo bricked….lol And the NX site is still going strong….
Basically pc gaming communities are synonymous with hacker communities now. They are one in the same imo. In fact most hacker communities have way more members then most games have online players for me. And I always say they have someone on the inside at these game companies. Why do their hack sites stay online? It makes no sense. I don’t think anything will change until consoles meet the same fate eventually, and companies are forced to use resources to go after the cheats.
DOTA and LOL are the only “popular” pc games. Maybe because they are strategy games and not FPS games. But they are not developed for new hardware, and doesn’t deter the fact the pc industry is dying in general. But, imo the main difference, In those communities, is that they discourage alt accounts which they call “smurfing”. They ban quitters…… They don’t have dedicated servers which is a good thing nowadays, they have automatic skill matching, and a huge core playerbase of honest competitive players, that respect video games the same as athletic sports!!!!
Thanks for your report. I read the same story earlier today on the German news portal “Der Spiegel” butthere is one small but minor difference: Spiegel reported that only possesing a copy of Blackshades was reason enough to get a visit from the police. No matter if the person actually used the trojan for something ilicite or not.
Can you please comment on this? In my opinion it would be pretty bad if the possession of a piece of software is enough to get your house searched.
I forget to cite the article from Spiegel Online: http://www.spiegel.de/netzwelt/netzpolitik/schadsoftware-blackshades-weltweite-hausdurchsuchungen-a-970286.html (In german)
§ 202c StGB makes it indeed illegal to possess software that allows you to hack into computers:
http://www.gesetze-im-internet.de/stgb/__202c.html
Depending on the court’s interpretation, sysadmins and security experts might be exempt. But even then, the police can certainly get a search warrant.
http://de.wikipedia.org/wiki/Vorbereiten_des_Aussp%C3%A4hens_und_Abfangens_von_Daten#Reaktionen
In short, that law is a bit of a mess.
Yes, Germany is a bit of an aberration in this respect: Several years ago they outlawed the mere possession of things that might be considered “hacking tools.”
Here in the good ole’ US of A, writing malware is a protected form of free speech; spreading it, or causing/incentivizing others to spread it, is not.
How is it free speech when you can’t distribute it?
because there’s more to malware than spreading it.
there’s also pentesting, there’s research/reverse-engineering, protection, tracking things back, benevolent espionage against blackhats for further prosecution, etc…
and sometimes just to prove what your worth is in knowledge of code and quality therein.
A pretty well known German tech lawyer wrote something about this case a few days ago: https://www.lawblog.de/index.php/archives/2014/05/17/software-kauf-fuehrt-zu-hausdurchsuchung/
Looks like the police might have overstepped their bounds a bit as the constitutional court (BVerfG) has ruled that if there is reasonable doubt that a tool can only be used for hacking, searching someone’s property might not be warranted. Since you can use most of this software for training purposes or legitimate pen tasting, the suspects might have a good case that the searches were unlawful if all the police had was prrof that they bought the tool.
After some more research, it seems that the BVerfG decision depends on what intention the original author of the software had. If it was obviously written as an attack tool (which in this case is pretty clear), then the police was well within their mandate, it seems.
I ask because I am genuinely curious, what is the status of “posessing” hacktools in France, minus spreading?
Xyli makes hacktools from keygens for ice9 to carderPOS malware, one of which he had shared with me before it was leaked on InFraud and then TF.
I know very well that Xyli is one of the whitest of whitehats, and has a few contacts…so….
I presume in France it’s legal to posess, again, just like the U.S, illegal however, to spread?
What about the U.K.? I did not know in the U.S. though that fancies me, given that I collect pieces here and there….
To quote DarkCoderSC in his pastebin EOF post, though indirectly:
malware is like a gun. You don’t punish the malware author, you punish the person who uses it.
On the other hand, guys like Gribo, I have no issue seeing being prosecuted under Federal U.S. law.
DarkCoderSC even ran OpenSC…which was then under investigation, and still is, from what he’s told me. But that was his pet project at least in part, and he’s also from France…
I guess that’s what separates gray from white, right? That being said, I’d probably better leave the no-man’s land.
What Xylitol is doing may be illegal under French law (I don’t know if it is or isn’t, but I wouldn’t be surprised if it is). However, it’s highly unlikely French police would ever charge him with anything.
Most people commit several crimes per day, sometimes knowingly and often unknowingly. Police and governments go after you when they think it’s actually causing harm.
Aren’t we a little concerned that police raids have taken place over the OWNERSHIP of a ‘hacking tool’. I haven’t seen any press confirming there is evidence that each of those raided actively used the tool – but I’m under no illusions a large percentage did.
The concern stems from what’s next; having metasploit on your computer is grounds for a police raid? If authorities had evidence for every raided address that they actively used the RAT then fair enough, but I suspect they are just making their way through a buyers database which is IMO way to heavy handed.
Disclaimer: I don’t own the RAT or feel sympathy for those guys busted in any way. I just think ownership of something shouldn’t be grounds for charges when only the use of the product on people without permission is illegal.
I don’t know either whether those who got visits from the police were merely possessing this or had used it. It seems evident from the declarations by the users themselves (shown in the screenshots at the bottom of this post) that many of them were using it maliciously.
I think the fact that the Justice Department said there were more than a thousand customers and that this action targets a small fraction of that base indicates that they went after people for whom they had evidence they were using Blackshades to compromise other people. In other cases (not necessarily this one) that comes from information included in correspondence between the sellers and the buyers.
Most of ’em used it in their internal LANs.
Xylitol I’m sure is happy, though he hasn’t been on ICQ, so I haven’t been able to ask him, plus he’s doing HY SOP Conference.
These guys were skids even in the most *literal* of definition. Most were coming home from school.
I love this article because it’s humorous with the “couldn’t hack their way out of a paper bag.”
Still getting over the fact most other tech media reports skid news as realistic danger like Anonymous posting their so-called EP, which is NOT an EP, back a few months.
The problem is, like you’ve said, they don’t know how to hack, but they try and think they’re all that.
I have no issue against computer illiterates, but then don’t go messing around with technology they don’t fully understand, and don’t pretend to be a big-time hacker. I’ve seen too many self-proclaimed “master hackers” in my day.
One of the links Brian provided included this quote: “We will continue to work with our law enforcement partners to bring to justice anyone who used Blackshades maliciously.”
Think of it as the same as possession of burglary tools. Police catch you wearing a black ninja suit carrying burglary tools in a weathy neighborhood late at night and you’ll have some explaining to do. Go buying hacker tools on an underground forum and the same will be true. Better be squeaky clean otherwise, not a sketchy script kiddy. No big deal, be a law abiding citizen and you’re very unlikely to find yourself in such a mess.
The whole point is that the authorities should prove a person’s guilt, not that one should have to prove their innocence, whether burglary or malware. Possession alone (at least here) is not a crime, nor even grounds for needing to explain oneself or be “squeaky clean”.
The logic that one has nothing to fear from highly intrusive policing techniques as long as one has done nothing wrong gives great faith — more than America’s founding fathers did — to the infallibility of the executive and judicial machinery. (A faith I certainly do not share.)
I’d really like to hear that the police are only targeting those who used the tools illegally, but (what Brian said notwithstanding) the noises being heard so far make it sound like they’re being less careful than that.
One user says he used the tool to administer his own machines. This tool is similar to something like VNC. So yes, we should be concerned.
I’m quite surprised Omni lead all the wee lambs to the slaughter like that. How did he explain that to everyone else? I’m glad I never bought anything like that but I believed it was fine on my own PC’s. It’s a bit worrying that people are being questioned about it.
life is great isn’t it, yeah?
I still hold Omni to be a skid themself.
It has been told to them that Zeus is a banking bot..
what? that person doesn’t know a single thing to do with infosec. It doesn’t have to come to their attention. If they truly were in the scene, it would never have to “come to their attention”. It’d be heard through the grapevine.
Same thing happened with betabot. ANY formgrabber/keylogger can be a banking bot. But it took a post by RSA for them to know it? And what makes betabot or Zeus different than RATs? I mean, aside from the fact Zeus is more hardcore and even betabot at least has rootkit functionality, albeit ring3.
Again, I will clarify, ANY formgrabber/keylogger can be used as a banking bot. Little do they realize that they’re harboring blackhats in every corner, yet they still allow malware sales? I find that ironic…
they still buy too, even after their prescious programs get cracked and posted on places like tf. I find it kinda funny.
Just too funny — all this teenage mutants cr@pping their pants…
Add to that the concerns voiced by Razor: ” THE POLICE DOES NOT CARE, THEY WILL TAKE YOU STUFF AWAY AND WILL DIGG TROUGH YOUR ENTIRE PORN DIRECTORY.” Source: image 9.
If he has child porn on his PC then Razor’s troubles have only just begun.
True story:
I know how those stupid kids feel, I got raided by the United States Secret Service about four years ago. They came right in with a search warrant and took my computer equipment. This is no joke, you do something wrong on the internet and the federal government will be coming in your door with a ( rubber stamped) search warrant.
So keeping this post brief as possible without a lot of information , I ended getting my computer and hard drives back after about 8 months. I wouldn’t wish the experience on anyone. Trust me it’s not a fun experience to go through.
And yet if you did something wrong, then the search warrant wasn’t rubber stamped.
Doesn’t necessarily mean it was carefully screened… They sign stacks of those at a time and rarely do they bother to verify that there is actually strong evidence making it worth the intrusion… We’ve hit a point where paranoia and population size makes individual rights a thing of the past – the freedoms are largely eroding but it isn’t the usual crap people spout all over the place but really economics. 8 out of 10 people are not really necessary anymore, technology has eliminated their previously good paying job and increasingly they have become inconvenient to those in power to have around. Combine this with for-profit prisons and you have all you need to start rubber stamping stuff like this and fill those prisons with whatever pretext they can come up with.
Not saying that these guys aren’t all guilty as sin, but there is still supposed to be a fair trial to determine that, and increasingly with short budgets and Judges that don’t give a crap about anything but what corporations tell them it isn’t always a clear cut thing.
So we’re supposed to have a fair trial before search warrants are issued now?
No, but the fourth amendment should be followed.
These searches seems to step way over the line.
It is like the robo-signing mess that banks were pulling a few years ago (and probably still do). Banks have a ton of money, they can hire the best lawyers and presumably enough staff to review their documents but instead they hired $10/hr vice presidents to robo sign documents as fast a possible. Do you really think if banks flush with cash got away with this that short funded districts would shy away from doing the same thing to warrants?
That’s exactly the point we are know living in a over zealous police state.
I ended up getting my computer hardware back, but the drawback is that my name is in some government database (Fusion Center) for the rest of my life because the Secret Service made contact with me.
I can not say much because of the S.O.L. is up next year, What I will say is that if you do anything with cyber security be very careful.
Once law enforcement knows that you are above average in knowledge with regards to internet networking , then you will be immediately targeted no matter if you are guilty of not.
Watch what you say and do on the internet !
You sound seriously over the top when you start referring to things such as “police state” regarding the situation in the USA although I’m certainly not without sympathy.
And I’d seriously like to see some evidence of even one person being charged simply for having a higher than usual degree of networking. That isn’t the case regarding the article under discussion.
Over 90 Arrested in Global FBI Crackdown on Blackshades RAT
A collaborative operation by international law enforcement agencies nabbed authors, staff members, and users of the popular software used for everything from blackmail to financial fraud.
httx://www.darkreading.com/over-90-arrested-in-global-fbi-crackdown-on-blackshades-rat/
I am astounded that script kiddies should think that the police should not pay any attention to them as they pile up malicious software.
They are essentially saying that the police have to stand by until they actually pull the trigger before the cops should pay attention to them.
A lot of ordinary people are getting hurt while they are getting their jollies. Why should the cops look the other way????
You realize what you’re saying is that people should be prosecuted for crimes they haven’t committed just because they have the tools to commit a crime.
Are all gun owners also murders and robbers that should be prosecuted? How about anyone who owns a shovel? That is a tool that could be used to hide evidence of a murder.
In the UK, possession of the means to commit crime could result in those in that possession being tried for conspiracy to commit whatever crime those means would facilitate. Of course, other evidence would also be gathered, such as behaviour showing intentions or associations of those alleged to have conspired to commit a crime.
Depending on the jurisdiction, there are many situations where the POSSESSION of a weapon could get you arrested – an unlicensed weapon, a licensed but concealed weapon, an illegal weapon or accessory – think machine gun, silencer……..
Unrelated but just a comment that even small forums can have multiple people with the same name. Please remember that in the future, FBI.
(There was still a moment of WTF, did I post in my sleep?!)
The difference, of course, is that there’s legitimate uses for gun owners. You can go competition shooting, you can go recreational shooting, you can go hunting in the woods…
For many tools, like zeus, there is absolutely no legitimate reason to own them unless you’re a security researcher. And if I was a security researcher, I’d be willing to cooperate with periodic police activity, since I would understand that I’m one of the infinitely small number of people with a legitimate reason to purchase (but not use) the software.
Isn’t Bharara the one who got beaten by cryptocurrency when he decided to shut down payment processors and gambling sites and who will now have to arrest all owners of metasploit?
You’re missing the point that having the tool is the crime if that’s what the law says, not some wishy washy link that they present as evidence.
In the US there are a number of tools you are not allowed to own without legitimate purpose. You are not allowed to own lock-picking tools unless you are a locksmith. You cannot own certain scanners or even the crystals for certain frequencies to pick up cell phone transmissions unless you work for those companies. You cannot possess bugging equipment unless you are a licensed private investigator. The list goes on. Mere possession of the tools is a crime, even to hang them on your wall.
I think it’s interesting that so many people are shocked that they could get caught after visiting a dedicated black hat site and purchasing black hat software; they threw up so many red flags! That being said, it’s nice to see some action once in a white against black hat groups. Thanks for the good news.
This story is just another reminder of how ineffective AntiVirus products are, including Microsoft’s Malicious Software Removal Tool.
The MSRT isn’t an anti-virus product. Were you thinking of MSE?
this is good and really funny in my opinion, crackdown on all the noobs make them think twice about trying to be a hacker again.
This morning it was even being sold at CNET for $15.
It was taken down
No surprise there, CNET still carries Anvisoft. See: http://krebsonsecurity.com/tag/anvisoft/
CNet, via download.com, bundles malware with other people’s software.
They grab someone else’s software on the internet, put a custom wrapper installer around it that includes a payload of their choosing (and they’re not all that choosy), and voila, it’s available for download on their website.
*wipes tear from eye*
This is beautiful.
RIP in pieces in pizza, Script kiddies.
I think one of the most interesting things about the comments is how many people will talk to police without a lawyer. Even more interesting is how many of them will post a confession in a public forum! On a site where they suspect they got caught! Wow.
The comments in the screen prints don’t seem genuine. They all seem like the writing of someone who is mocking teenagers.
They HF teenagers mock themselves and don’t need help from others mocking them.
>I do a lot of shady stuff, but I had no idea how they could come at my door.
Plonker.
I am so glad to hear of this happening. If it were left up to me, these miscreants would be put in stockades in the town square for public display and humiliation.
I would however, prefer nuclear bombs, but that would be looked upon as uncivilized.
The stocks are far more fun. Someone could do a roaring trade in supplying rotten fruit and vegetables with which to pelt the miscreants.
isnt it the same software that was used by the US against IRAN nuclear program.
I think that was Stuxnet.
The law doesn’t mean a damn to the USA government and agencies. It only applies when it’s in their favour.
Well, its not like the law means anything to Iran either.
Nobody held a gun to their head when they signed the NPT.
Isn’t it the same software used to spy Germans, Bahamanians and bittorrent users or is Bharara just a hypocrite?
“THE POLICE DOES NOT CARE, THEY WILL TAKE YOU STUFF AWAY AND WILL DIGG TROUGH YOUR ENTIRE PORN DIRECTORY!”
perks of the job skid.
Couldn’t happen to a nicer bunch of dweebs!
It is likely that the majority of people who are visiting these sites and downloading these programs are going to be using them for negative things because there are not many positive things that can be done with them. That being said, it is a good thing that police are taking initiative and trying to stop these things from happening instead of sitting around and waiting for something to happen because at that point it is too late.
not necessarily.
even malware has legitimate purposes. Even HF crap malware, for that matter.
RATs can be used legitimately.
The problem was Bshades became overbloated for its customer-base and they used stupid paypal. Why not use WMZ or BTC?
Exploit-in bases around wmz and btc. Heck, then there are skids there. Betabot is basically HF crap. People don’t even know that it was leaked. If I were blackhat, I could very well make a profit.
Good! This makes me very happy. I am also happy they got the guy that sent the police to your house Brian. That must have made your feel vindicated somewhat.
Cool, talk about sheer panic to script kiddies. I’d have to guess that most of the raids that are in this thread were people who are young and quite active in forums and text messaging. No matter what they want to say publicly, its what they did behind closed doors that the FBI is interested in.
The FBI will research all the links and use those links, especially the chain of evidence thats available from paypal account payments and pretty much solidify the case against the miscreants mastering any sort of illegal software.
Wanna be criminals and bot herders that get their pants yanked around their ankles is funny. I sat and explained the cyber forensics stuff to my son and one of the quetions I said to him was, do you think the Feds have massive amounts of “infected” workstations in warehouses and is monitoring every keystroke, and potentially injecting software onto the C&C point of contact since traffic goes both ways…. He gave me that deer in the head lights look.
You have to think outside of the computer box at what may be out there and how it can be used against you in the court of law. Don’t like the odds or cost of all your electronics being taken away, and returned when they are legacy devices? Then steer clear of the dark side and you might be saved. What’s this do for a person;s ability to get or hold a job? It may brand them as unstrustworthy, a potential insider or a part time hacker.
People who say they “don’t think” they will get caught, are the ones that will get caught. using your personal credentials on your personal computer on your personal ISP at home buying illegal software doesn’t instill any warnings of what could happen to me if the Feds get involved? The key phrase is they “don’t think”.
Paypal is an electronic paper trail, it has its legitimate use, but in the end, the result is what you see in front of you, arrested individuals who are nothing more than pawns hanging from trees, as the government says ” Be afraid, very afraid, you might be next”. An Electronic Lynch mauling if you will.
Even if they were purchasing the “illegal software” for “private use” , it was purchased with the intent to be used, with the probability of knowing what the software is capable of doing.
Who knows the true intent behind all of this. I have other theories and I wish to keep them under hat just in case they do exist, because I personally don’t want them knocking on my door because I took a SWAG and was right on about a technology that they currently may have as a hush-hush operation.
A Simple slip off the beaten path can ruin a potential career of a person in a heart beat, once your caught with thy pants around they ankles, be polite, cooperative as much as necessary and hopefully, they will release you. As for your electronics, expect them to be back after the court battles have been finished, which may be many, many years.
Way to go Preet Bharara !!! Amazing how may high profile indictments he has brought forward in the recent past. Hopefully he will be a good crusader for the common man.
Great report
Very interesting conversation. We have those who applaud the effort and those who condemn it. Those who are excited for an organized law enforcement effort across physical borders and those who worry about this being a precedence for being arrested just for “owning” a tool.
I am curious how this will play out in the couple of weeks. I imagine all these organizations will have a tough time sorting through the variety of cases/offenders they have on their hands now.
When I first read this it reminded me of the scene in Batman…when Harvey Dent grabs everyone from informers, dealers all the way to distributors and crime bosses… all yelling in the same courtroom, being heard on the same day.
I for one applaud this effort. Crime is increasingly better organized, about time for the authorities to do the same. (I realize that they have orchestrated efforts like this in the past but I cannot recall a more successful organized raid before this one…. perhaps the FBI raid on those using the TOR network to trade in kiddie porn last summer?)
I hear a difference in how arrests, questionings, and confiscations were conducted in different countries. This doesn’t speak of a single law enforcement body that spans the globe with disregard for boundaries, but individual countries’ agencies working together. That should be noted before anyone misunderstands your post. 🙂
lmao at most of the comments being kids in school. Not surprised how they think they are doing nothing wrong, until reality hits and they realize the internet is just another extension of real life.
Life is good when the hackers and peepers are cryin’ instead of spyin’ !
This just seems a little too much like when the Feds used to allow the dope in, to reward the Central American dictators, then track the users that purchased it , and bust them.
Seriously, this looks like an NSA tool that was released into the wild, after being sunsetted by the Advanced cats.
They prob just changed the call back server from Maryland to Quantico……
great to see skids squirming.