Nationwide chain P.F. Chang’s China Bistro said today that it is investigating claims of a data breach involving credit and debit card data reportedly stolen from restaurant locations nationwide.
 On June 9, thousands of newly-stolen credit and debit cards went up for sale on rescator[dot]so, an underground store best known for selling tens of millions of cards stolen in the Target breach. Several banks contacted by KrebsOnSecurity said they acquired from this new batch multiple cards that were previously issued to customers, and found that all had been used at P.F. Chang’s locations between the beginning of March 2014 and May 19, 2014.
On June 9, thousands of newly-stolen credit and debit cards went up for sale on rescator[dot]so, an underground store best known for selling tens of millions of cards stolen in the Target breach. Several banks contacted by KrebsOnSecurity said they acquired from this new batch multiple cards that were previously issued to customers, and found that all had been used at P.F. Chang’s locations between the beginning of March 2014 and May 19, 2014.
Contacted about the banks’ claims, the Scottsdale, Arizona-based restaurant chain said it has not yet been able to confirm a card breach, but that the company “has been in communications with law enforcement authorities and banks to investigate the source.”
“P.F. Chang’s takes these matters very seriously and is currently investigating the situation, working with the authorities to learn more,” the company said in an emailed statement. “We will provide an update as soon as we have additional information.”
A spokesperson for the U.S. Secret Service, which typically investigates breaches involving counterfeit credit and debit cards, declined to comment.
It is unclear how many P.F. Chang’s locations may have been impacted. According to the company’s Wikipedia entry, as of January 2012 there were approximately 204 P.F. Chang’s restaurants in the United States, Puerto Rico, Mexico, Canada, Argentina, Chile and the Middle East. Banks contacted for this story reported cards apparently stolen from PFC locations in Florida, Maryland, New Jersey, Pennsylvania, Nevada and North Carolina.
The new batch of stolen cards, dubbed “Ronald Reagan” by the card shop’s owner, is the first major glut of cards released for sale on the fraud shop since March 2014, when curators of the crime store advertised the sale of some 282,000 cards stolen from nationwide beauty store chain Sally Beauty.
The items for sale are not cards, per se, but instead data copied from the magnetic stripe on the backs of credit cards. Armed with this information, thieves can re-encode the data onto new plastic and then use the counterfeit cards to buy high-priced items at big box stores, goods that can be quickly resold for cash (think iPads and gift cards, for example).
The most common way that thieves steal this type of card data is by hacking into cash registers at retail locations and planting malicious software that surreptitiously records mag stripe data when cards are swiped through the machines. The breaches at Target, Neiman Marcus, Michaels and Sally Beauty all were powered by malware that thieves planted on point-of-sale systems.
Unlike with the Target and Sally Beauty batches, however, the advertisement on Rescator’s shop for cards sold under the Ronald Reagan batch does not list the total number of cards that are for sale currently. Instead, it appears to list just the first 100 pages of results, at approximately 50 cards per page. The cards range in price from $18 to $140 per card. Many factors can influence the price of an individual card, such as whether the card is a Visa or American Express card; similarly, Platinum and Business cards tend to fetch far higher prices than Classic and Standard cards.
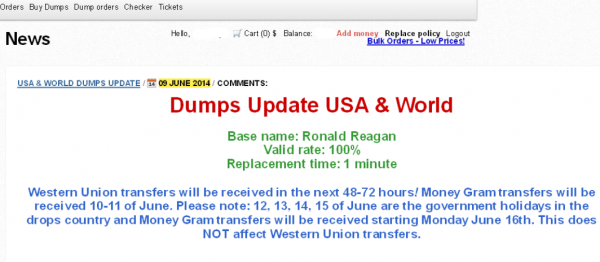
A new ad that debuted on June 9 for a fresh batch of cards apparently stolen from PF Chang’s China Bistro locations.
The ad for the Ronald Reagan batch of cards also includes guidance for potential customers who wish to fund their accounts via Western Union or MoneyGram wire transfers, advice that strongly suggests those involved in this apparent heist are once again from Russia and Eastern Europe:
“Western Union transfers will be received in the next 48-72 hours! Money Gram transfers will be received 10-11 of June. Please note: 12, 13, 14, 15 of June are the government holidays in the drops country and Money Gram transfers will be received starting Monday June 16th. This does NOT affect Western Union transfers.”
June 12 is “Russia Day,” a national holiday in Russia since 1992 that celebrates the declaration of state sovereignty of the Russian Soviet Federative Socialist Republic on June 12, 1990. “Drops” refers to individuals hired to receive money transfers on behalf of the card shop to help fund new and existing accounts. The shop also accepts payment via Bitcoin (for hopefully obvious reasons, customers cannot pay for the goods using credit cards).
It seems likely that P.F. Chang’s only learned of this breach very recently. The cards sold under the Ronald Reagan base are advertised at “100 percent valid,” meaning that fraudsters can expect all of the cards they purchase to have not yet been canceled by the issuing banks. For a deeper dive on how valid rates are a fairly reliable indicator of the recency of a breach, see my analysis of the valid rates on cards stolen in the Target, Sally Beauty and Harbor Freight break-ins.
Rescator, a miscreant closely tied to the Target breach, advertises the new batch of cards on his crime forum.
For more information on Rescator, the miscreant apparently responsible for selling (if not also stealing) the cards from this apparent breach, and in the Sally Beauty and Target breaches, see this story.
Update, June 13, 10:27 a.m. ET: P.F. Chang’s just confirmed that it had a breach, and that it has temporarily moved to taking carbon copies of customer credit cards at all locations. See this story for more information.




Any word on whether their subsidiary Pei Wei Asian Diner was also involved?
Guess for awhile I’ll have to get P.F. Chang from the freezer section at the supermarket — except at Target….
No, I didn’t talk to any banks who saw charges on the cards at Pei Wei.
When would PFChangs have first found out about this? Not until they were on rescator June 9 or would they have had a clue a week earlier?
…or (…oh the horror) use cash.
In general, avoid these American concept restaurant chains such as Pei Wei and PF Changs. I’ve never had issues with my card data at the real Chinese restaurants 🙂 The real Chinese restaurants won’t spend a penny on any POS system other than phone line terminals so by their very nature are less susceptible to hackers. And they don’t pay taxes so you don’t even need to worry about the restaurant staff swiping card data too make a buck either, they’re already loaded, don’t let the grungy dress and bed head fool you, these are rich folks. The CC trick most authentic Chinese restaurants play is that they have different relatives ‘visit’ during the summer and they work at the restaurant, they get a credit card in their own name and purchase $8,000 worth of merchandise before returning to Mainland China, without any intentions of ever paying a penny towards their credit card bill. Beautiful. And Banks keep on issuing cards to these visitors with temporary jobs and temporary housing. Blows my mind.
Why the name ” Ronald Reagan” ? Once again as I stated in previous articles , it’s time that banks and retail stores in the United States start moving to chip and pin systems.
Chip and PIN is not all that you think it is. I know everyone thinks its a miracle technology but its not. How are you going to buy stuff online with Chip and PIN? Exactly, you will provide the number without the “Chip” portion. Don’t forget the information still gets decrypted and can be RAM scraped. So the Target situation would not have been solved. Thieves will just buy their stuff online and have it muled, its really not that hard to see. The defense is to keep the attackers out in the first place. But honestly consumers are never held responsible for the purchases anyway so what does it matter for John Q. Public? Chip and PIN costs will be passed on to consumers further raising prices. Stop the attacks before they get in, don’t blame lack of Chip and PIN.
Chip&Pin is great for swiped. The problem is it does nothing for web transactions, so it will just push the fraud to the internet.
First off, preventing the intrusion is only part of the solution. The true solution is what is done after the intrusion.
Meaning Intrusion detection systems must be in place. And intrusion systems that cut the data stream after an intrusion are the next logical step.
Every system will at some point be hacked it is what is done to control the data after the hack that is where security folks earn their money.
In Europe we have a technology called 3D-Secure (branded Verified by Visa and MasterCard SecureCode by the two big card issuers); it’s required to make an online payment go through — all retailers in the UK, for instance, must show the 3D-Secure screen before they can take a payment.
It uses a password that is much longer than a PIN and consists of letters, numbers and symbols, and will only ask for a few characters each time a transaction is processed. So it’s also pretty robust against keylogging and what not.
So I feel America should just adopt Chip & PIN and 3D-Secure and be done with worrying about it.
3DSecure is garbage by comparison because key loggers easily defeat it and pinpads are OOB.
in comparison with what? I actually just told you how keyloggers do *not* defeat it. They ask for a random selection of characters each time so a keylogger would have to catch every permutation and match them together. That’s a lot of work.
Source for this information? I believe the user configures a PIN the first time they use it. There may be some issuers that do something smarter, but so far I’ve only seen/heard of static PINs. Since you’re entering it on your computer, not a pinpad, it’s not out of band. That’s pretty defeatable.
It’s crap by comparison to chip&pin. I’m not saying anything controversial here.
How about OTPs then? Some form of two factor authorisation online, you enter your details for the payment, then you’re moved to a OTP password page, generate this on your mobile device or even a physical handheld machine using Secure Key or something?
Wouldn’t a better approach be to use single use account numbers tied to a real number instead? There a few advantages I can see there – one would be that the account number would be inextricably linked with a single transaction, making it easily traceable to any breach source, the transaction would be a single exploit window, and could be tied to issuer triggers to immediately suspend suspect accounts. The root number would never be used, and this would be flagged if attempted (and in addition would not be honored). Another advantage to this approach in a larger context would be that consumers would be able to easily shift their underlying accounts to new issuers. Anyone who has ever tried to move their banking relationships from one bank to another will see the value in that approach.
That could be pretty toxic to conversions. What if I want to buy something in my underwear at 5AM. My phone isn’t charged and that’s exactly what I want to do. Find my phone.
You’re missing an important point in that swiped cards don’t capture the CVC2/CVV2 stamped on the outside of the card. The magnetic track only captures CVC1/CVV1 which could be used for cloning. So in these cases where the card was skimmed, the card cannot be used to make any Web transactions. This leads to card cloning as the only other method available. And while I would agree that chip and PIN is not yet a completely viable solution (from the security and consumer accountability/ liability shift perspective), it does make it much harder to clone the card.
To be fair, the massive thefts in past year have been from compromised POS systems, not online web sites.
Of the suggestions I’ve read over last few months the end to end encryption makes the most sense, where scanned data is handled by embedded software in the card scanner. The Chip and PIN thing always suggested would not be needed with end to end encryption, would it?
Using mules is much more expensive. Anything that drives the profit margin of the crime down reduces the crime.
Chip and PIN has reduced fraud in every country that utilises it. The tendency for people in these comments to disparage it absurd.
Actually that’s not true about consumers not paying for it; taken to the nth degree, the CC companies or banks just write it off as losses and the tax payer pays for it.
You’re correct Rick G. And further, even though you have a PIN and Chip card and the retailer has a PIN and Chip reader, you can still just swipe the card and use the good ol’ signature. So it’s not a fix until it’s required by card issuing banks and all retailers, and we do away with the silly signature.
It depends in the country. Eg: Australia is moving to solely chip-and-PIN. Also cards can only be inserted into a bank-provided terminal, so security is largely the bank’s problem. It’s not attractive for even huge retailers to avoid the bank terminals as then liability for hacks will fall upon the retailer. I’d suggest that liability falling to the card issuer even when it was not their system compromised is one reason for poor card security in the USA.
Time for death penalties. The only way to curb this and other crimes. Save a ton of money as well.
Except that capital punishment is actually more expensive …
Ya gotta catch ’em before ya can kill ’em. Navy SEALS?
Great post! Your first statement contravenes the principles of most religions and morality systems and your second and third statements are provably incorrect.
If these pos systems are being infected by malware how will chip and pin help? If you must enter a pin into a compromised pos system what makes you think that this won’t make it even easier for these guys to get your card and now your pin for atm withdraws?
Chip-and-PIN won’t stop these breaches, but it should make them far less lucrative for the bad guys, potentially removing a lot of the incentive for them to hack these companies because the stolen card numbers will only be good for online fraud.
There are enough places on this planet where you still can use magstripe cards.
So it will take some time until they are good for online shopping only.
Cheers
H9
Once the liability shift occurs, the stores where one might buy the sorts of things that are popular with the crooks will rapidly switch over to EMV readers.
If the stores fail to upgrade, the stores will get stuck with the cost of the stolen merchandise.
The liability shift does not happen in the US, which is part of the reason why vendors are not moving to chip&pin. I forgot the name of the law, but it’s one of those things where the US is much more protective of the consumer than Europe. You can bet that has something to do with it.
Just adding that I believe that the _Banks_ will eat it based on current legislation if they want wide adoption. There is no free lunch (or money). The reason you have the liability shift is that Europe assumes chip and pin is infallible and the consumer eats it. I’m not sure that’s a good thing, and the US believes as much.
The reasoning is simple:
1. You can’t blame the consumer based on US legislation.
2. So the bank or the merchant will have to eat it. The banks don’t want to eat it.
3. It slows down conversions and checkout lines, so if it doesn’t protect the store or cut down that much on fraud, the store won’t have the incentive.
So the banks _could_ incentivize it by giving out the machines free, but that might involve work on the POS. That might not even be enough to justify the investment because it slows down lines and is generally expensive to adopt into aging POSes.
So it never happens. In order to make it roll out the banks will need to shift liability to themselves. They don’t want that. So it never happens. You can see this exact situation in VBV.
Not quite rite SJ, the liability shift is scheduled for October of 2015, although I’d bet that that date gets postponed again.
The EMV liability shift is most certainly coming to the US in October 2015. Each card brand has made this crystal clear:
http://www.mastercardadvisors.com/_assets/pdf/emv_us_aquirers.pdf
https://usa.visa.com/download/merchants/bulletin-us-participation-liability-shift-080911.pdf
http://about.americanexpress.com/news/pr/2012/emv_roadmap.aspx
Etc.
Merchants will ultimately pick up the tab for fraud.
With regard to POS malware, Visa issued numerous bulletins to merchants advising of the risk, and the recommendation for merchants to consider P2PE (essentially encryption from tamper evident, hardened reading hardware to host processing systems), tokenization to replace card data with a functional but valueless surrogate equivalent, and EMV in readiness for the future.
http://usa.visa.com/download/merchants/Bulletin__Memory_Parser_Update_082013.pdf
http://usa.visa.com/merchants/protect-your-business/cisp/data-security-alerts.jsp
Etc.
Interested readers can learn more here about how P2Pe and tokenization can mitigate malware risks like that reported at PF Changs, contrasted with EMV.
http://www.voltage.com/blog/crypto/why-emv-wont-be-enough-to-prevent-criminals-attacking-retail-systems-and-what-to-do-about-it/
Regards,
Mark Bower
Incentives can and do exist for merchants to verify authorized card use in exchange for reduced liability. The system I have in mind is 3D Secure, which is why we enter our zip codes into gas pumps these days in the US. It’s a system developed and adopted by the card processors and if not observed can leave the risk to the merchant instead of the issuing bank. It’s also used on many ecommerce shops and can be used to verify card holder information beyond zip codes.
It’s not enough. And the infrastructure is barely there. As it is, VBV is a bribe. The liability shifts to the bank in most cases. Even when VBV isn’t applicable. The system is designed to punish the banks, which is (duh) why they don’t push it.
3dSecure has nothing to do with AVS.
We already do, and have for years. What’s your point?
WRONG!! Merchants do not get stuck with the costs of stolen merchandise, as long as you get a swipe and sig/PIN. The Banks eat the costs.
I just checked out this very point just the other day. The Chip and Pin credit cards in the United States are used by the wealthy (like the American Express top tier cards ) as a added security feature or people who travel over to Europe.
I seen a person last week use a chip and pin card at the local China-Mart. The cashier told me she sees a lot of people from Canada using these type of cards.
I can’t get a chip and pin card from Citibank, despite travel to Europe and Africa. I’m told the best available is chip and signature.
I have a chip+PIN from Citibank (credit, not debit card). That’s good.
What is NOT good is that the card will NOT work in Europe. At least, that’s what Citi told me when I asked them. In Europe it still works like a swipe card.
Sigh.
That’s because we Canucks have had them for years.
+1
Is it even good for online fraud without CVV? Everyone except Amazon (oddly, but it may have something to do with the fact that they store CCs) requires CVV. There’s no way you’re getting _that_ card code from a magstrip or a a chipped card, so it’s even less useful, no?
VBV and Securecode exist as the counterpart to this chip and pin stuff, but the liability shift doesn’t happen so the banks don’t push it. They eat it early and often from my understanding. It would be great if you went into that topic. There are many that think it’s some big mystery that we don’t have chip and pin without a crisis … or even with a crisis. I think the reason is basic economics. There is not a value proposition for the banks if they can’t blame the consumer like in Europe.
I think that Amazon requires CVV the first time you use a card. But you’re right that it doesn’t for subsequent uses to the same address.
I don’t think they ever require it. Ever.
Actually, they do require it when signing up a new card, and will periodically prompt you to re-enter it when placing orders. I’ve had to enter mine twice, per card, over the past year or so. I don’t know what the metric is that prompts them to ask you, perhaps it’s as simple as an address/phone change (I’ve moved in the past year), or maybe a combination of factors.
Amazon has asked me a few times in the last year to verify my card details and I haven’t moved recently. It must be some sort of automatic security “feature”
I don’t ever recall being asked. I’ve been asked to re-enter the card # itself. That’s it. Might vary by region, but see http://www.amazon.com/forum/video%20games?cdForum=Fx1T1DM93QU4XL1&cdThread=Tx2X6381BGO1A22
Well I can recall being asked to specifically input the 3 digit code on a couple occasions. I remember them very clearly because in both cases I didn’t have my wallet on me at the time (one time I left it at home and was at work, the other time I was just in another part of the house on a weekend).
Maybe that’s the trigger – detect if the customer has physical access to their card and prompt them to enter details if they don’t. Brilliant system to implement, though the logistics is tricky.
Hi Brian,
How would the thieves be able to use the stolen cards online without CVV2 ? Are still online places accepting transactions without CVV2 or were clerks at Target manually entering CVV2 after each card swipe as a counterproductive measure against fraud ?
Why don’t companies whitelist their POS systems?
It’s so easy that is should be criminal not to do it.
Remember that the POS never sees cleartext PIN, only enciphered PIN. PIN is handled by PIN Entry Devices (PED) which are far less susceptible to maleware as they generally run proprietary firmware with software integrity protections that most POS don’t have. Even the enciphered PIN could be taken out of the picture if EMV is implemented with offline PIN verification.
EMV could also help reduce online fraud if chip cards where used with personal PEDs that generated one-time pass codes. This is being used today in some Scandinavian online banking implementations.
Yeah, the standalone terminals where you swipe and enter card information are fairly secure. The problem is that they communicate with the register, which is usually the source of the breach, so you can assume any unencrypted data passed to the register is going to be breached.
There’s also the little problem of thieves wholesale replacing standalone & mobile terminals (card swipe devices that staff carry from table to table) with compromised units that aren’t encrypting data, that keep a copy of swipes and PINs on the terminal, but otherwise communicate fine with the register and POS system in use at the location (they pass along the sales, they just keep a copy of everything, that thieves access later).
Validated P2PE (such as Bluefin) is the only viable way to secure retail transactions and take the liability off the retailers. If P2PE had been in place, it would have eliminated all the thefts mentioned in this article. EMV/chip-pin would not have eliminated the thefts but EMV would make it harder for thieves to use stolen card numbers after the theft, driving down their value a making thefts less profitable.
time to bypass the 1950’s technology and use 21st century cryptocurrencies. the era of bitcoin is here for the masses!
Tell that to the people who had their money in Mt. Gox or any of the other sites that had their wallets emptied.
the people who lost their bitcoins to mt gox gave up their private keys. if you keep your bitcoins in your secure personal wallet then things are great. if you let mt gox or anyone else hold your bitcoins then shame on you. bitcoins are like cash keep them in your wallet and your good, if you give your cash to a bank or third party then your account can be frozen. bitcoin is the future but you have to treat it like you treat your cash or gold coins.
Sounds great, except Windows systems are about as secure as swiss cheese. There’s numerous pieces of malware out there that will happily drain your bitcoin wallet by simply waiting for you to unlock it while the malware is watching.
If I have cash in my wallet and I get robbed, I’m out the cash. Same holds true for bitcoin, except that with bitcoin you’re vulnerable every time you open your wallet, even for innocuous purposes. And there’s no recourse when you lose your bitcoins, they’re just gone.
Remember, they don’t call it buttcoin for nothing.
Bitcoin is not a currency, because currencies tend to only fluctuate a little. Something that drops in value by 50% in one day is a speculative investment.
Hundreds of thousands of retailers are already using P2PE, taking live track and PAN data out of vulnerable POS systems. Innovations like NIST Format-Preserving Encryption enables it to be used in legacy POS and payment systems, reducing the need for process and system change which is often the inhibitor with traditional approaches. Its a shame PF Chang hadn’t taken that step, especially as its relatively easy to deploy and manage and the payoff in risk reduction is huge, even in hospitality scenarios or quick service restaurants with custom card store and forward data flows. If they had, the attack would have yielded nothing.
Regards,
Mark Bower
VP Products,
Voltage Security.
Disclaimer: I work for a company who provides data-security for payments for acquirers, merchants and payment hardware vendors.
@ Mark Bower,
Afraid I did not understand one word of your post ha ha ha BUT, be aware, it was most assuring to know that there are people like you and your company out there really taking on these criminals. It is my firm belief that life imprisonment world-wide is the only way we have a
chance of stopping the very serious damage to confidence in the monetary system being caused.
If that CC is unencrypted in memory at any time it is trivial to get.
If you put in a physical device for the swipe, the miscreants will just add hardware to the device.
Many retailers “claim” to have full P2PE on their Point of Sale systems, especially when it’s PCI audit time! The true test is how they handle manual entry or a bad card swipe. If P2PE is enabled via a PIN Pad, but a cashier can manually enter a credit card number on the actual register, they don’t truly have a P2PE environment. I’ll feel better when I see manual entry options on more PIN Pads, including asking for CCV and expiry.
@BrianKrebs – Have you seen the new on-table credit card processors (Ziosk tablets) at Chili’s? They are essentially leaving customers alone with their pin pads, which are transmitting all credit card data wirelessly – oy!
It greatly reduces the scope even if you do some key-ins. Wireless shouldn’t make a difference. Why does it? You’d hope there’s already SSL in place. What’s more worrisome is if there’s some way to exploit that hardware.
I read here and there on malware injected into POS.
The thing that it is hard for me to understand is how did the attacker inject the malware?
Those POS are typically on wireless network in the store, which is secured by WPA or stronger.
Seems to me too suspicious.
They often get direct physical access to the units or obtain credentials surreptitiously from employees or contractors; also my understanding is that most POS systems are on wired network connections, not Wi-Fi.
Right you are James. I tend to think that systems security is like onions. Onions have layers. Security has layers. (Shrek fans will get it!)
The cyber crooks peal off each layer and the first layer is most often through the impersonation of user credentials. Two-factor authentication solutions are currently the most effective way to harden this first layer.
I imagine that most security professionals would agree. So why is that there is so little adoption of 2FA? Is it cost? Convenience? Operational challenges?
There are many options available for 2FA and I would be ecstatic to see a world where businesses (and consumers) begin to take authentication security seriously and kill off the username and password.
Regardless of which 2FA solution an organization chooses, I would applaud there efforts to shore up the first line of defense. Ideally they would use my company’s solution, but that’s for another discussion elsewhere.
Best regards,
Joe McDonald
Product Marketing Manager
WWPass Corporation
Add another retailer to the list of breached companies. It seems like continuous monitoring seems to be the only method to help prevent these breaches/compromises. The Rippleshot team is also at the NRF Loss Prevention Expo and look forward to seeing you speak tomorrow.
There is much more to it, but that is a start. It starts with the weakest link – actually two – people and software. people need to pay attention and follow the rules to the Nth degree. Just because some one “sounds nice and sincere” is NOT a viable (more like fire-able) option.
And software. A simple inventory of software that not being updated / used on systems and builds should be removed. People with specific needs can be addressed, and they should be responsible to patch that software, though its ultimately up to the IT department to patch if for them.
I don’t understand why links are allowed in emails unless they originate from a trusted / white listed entity. Then half of the attempts would immediately fail.
People are too lax when it comes to security violations. They know that the device is not theirs and may take a bit of a chance to see what that web site is all about. They also know if something should happen to the device, that more than likely (hopefully) the IT department will catch it and reinstall it as soon as possible, so they can try again.
Infractions (as well as good deeds) need to be documented and presented to the individuals during their performance reviews. If what they are doing is against comany policy and it leaks, or they brag about it, the company needs to act on it, or simply flush it since its not enforced.
Some of these “hacks” aren’t hacks at all – most are very simple social engineering blunders that should never happen. Once a company gets breached, its the same ole’ party line, the “we care” then appears and they shore up against expected losses over the next few quarters and hope the loyal people return. Due Care, Due Diligence and the Prudent Man Rule are supposed to be there 24/7/365, not simply tossed back on a track when a company has issues.
IA Eng wrote: “I don’t understand why links are allowed in emails unless they originate from a trusted / white listed entity. Then half of the attempts would immediately fail.”
This is a really good point. Most companies are hacked because employees click on phished emails. Eliminating links, maybe by converting emails to text and masking all URLs, solves the problem. And I’d estimate that far more than half of hacks result from phishing, probably over 90%. Of course, that means that the corporate system must block access to Yahoo, Hotmail/Outlook, Google, Juno, and other email providers.
The second part of this, however, is BYOD. If a company allows employees to use personal devices inside the company firewall, with those devices then becoming infected from phishing, the malware can transfer to corporate systems. BYOD is a short-sighted policy.
How is that viable? The second those links were audited based on a whitelist basis, you’d have corporations abusing the whitelists to achieve an advantage. You’ve just accomplished more damage with that than the offending fraud in the first place. A BLACKlist @ gmail, hotmail, etc. is a great idea though.
I admit that my response was a little ambiguous, but I did write, “Eliminating links, maybe by converting emails to text and masking all URLs, solves the problem.” I interpreted IA Eng’s whitelist comment in a more restrictive manner than you did. I would include only senders which are absolutely necessary for the business, with that list being rather short. Paypal, eBay, Facebook, Amazon, and all banks would not be on the whitelist.
And companies would need to be honest about their security situation. For example, Target should have audited its HVAC vendor, and when it turned out to not take security seriously, delete it from the whitelist.
“Due Care, Due Diligence and the Prudent Man Rule are supposed to be there 24/7/365”
With respect to hackers, the most effective rule would be the one involving Slender Man.
Time to consider tokenization.
Not sure tokenization will do anything here. Something has to be transmitted at least once.
NY Times article on this breach, online yesterday, prominently mentions Brian right in the second sentence:
“The possible theft was first reported by Brian Krebs, a security blogger …”
See :http://bits.blogs.nytimes.com/2014/06/10/p-f-changs-investigating-possible-data-breach/?ref=technology
Glad I haven’t eaten at a PF Changs for a while! Sorry for all those whose information has been comprised.
What sucks is I have never eaten at PF Changs. I decided to try two weeks ago and now this.
You could always pay cash.
Read what Brian wrote in the second paragraph of his report on this breach:
“Several banks contacted by KrebsOnSecurity said they acquired from this new batch multiple cards that were previously issued to customers, and found that all had been used at P.F. Chang’s locations between the beginning of March 2014 and May 19, 2014.”
Two weeks ago it was May 28, nine days past what was apparently the last date for this breach.
May 19th may or may not be the cut-off date. It could just be the last date that is currently showing up in the data breach. As new dumps are released, there could be newer dates.
While what you said is true, May 19th may be the date that PFC removed the miscreants access to their POS systems. Since PFC isn’t commenting there’s no way to know which interpretation is correct, so I’ll gladly admit I was wrong if the dates are based on information in the dump.
Personally, f I was a thief, I wouldn’t give out dates of when the card data was stolen. That’s too much information, law enforcement would simply use it to determine when and how the breach occurred, more clues to point back to me.
Now that you have written about this batch I’m assuming the price will drop since the banks and the client now have to disclose the problem to the public and the cards will start to be invalidated.
Nice job Brian, get us the information and reduce the criminals income all with one article.
Cheers.
Why are the banks still using old technology? Even Chip and Pin is weak compared to what COULD be done. Why not use something along the lines of x.509 certificates in smart cards? The merchant (online or offline) sends a request to the card with all the parameters and gets a digitial signature. The request is then forwarded to the bank.
This won’t work for phone orders or online orders without smart card readers (but USB smart card readers could be provided by the banks for about the cost of issuing a card after a breach).
There could be some type of pin required, but the terminal for entering it will always be a weak spot. Perhaps smart phone based payments systems are indeed our future.
Because it works for swiped transactions, it’s not reinventing the wheel, and will work in Europe.
There could always be backwards compatiblity with chip and pin and a mag strip for the older equipment.
Merchants using the latest technology would never have access to the credit card number of any sort (the protocol should perhaps expose the last 4 digits to allow merchants and consumers to see which card they used), therefore zero risk of compromise or exposure to compromized data (as the data compromised from older devices wouldn’t work on certificate based terminals).
This is a good idea if you can avoid transmitting the card number in the clear entirely because it stops mass harvesting from swiped ==> online. I’m not sure how chip and pin works because I’m a dumb American who at best had a chip and sig card =)
Read prior columns on these retail breaches such as Target. The numbers are being swiped from memory on Windows POS’es. Using a Windows PC for a POS is just lazy and stupid and incompetent.
Why would anyone use a general purpose computer designed to accept software updates and run multiple processes for a POS?
At a minimum should be locked down Linux PC if not an embedded software device. How often does POS software get updated? Should be reflashed to install POS software update, not particpate in over the wire updates. But these retailers getting hit run Windows shops. They have no idea what they’re doing.
That’s painting with a pretty broad brush don’t you think?
There are *millions* of deployed (in the field) Windows POS machines. If you search the PCI PA-DSS approved payment application list over 90% of approved payment applications require/run on some variant of Windows, whether embedded, POSReady, etc.
It’s impossible in many business segments to find an approved payment application running on anything other than Windows.
Love all the armchair pundits in these comments making broad statements with no root in reality.
Anybody know which point of sale system they are using? Last I knew it was Aloha.
Yes, definitely Aloha in both PF and Pei Wei.
What an incredible stupidity!!! How can a web site like this promote best underground shops for dumps ? Did people really get so retarded ? You promote so much these sites then you complain there are so many carders around. Its your fault fools
Daniel…your meds are in the bathroom, please go and take them now.
Brian is there any further insight into what states are impacted or was every PF Chang restaurant impacted.
As someone who was a victim of the target breach, I would hate to have to go through this yet again so soon….
Sigh…
I totally hear you, was hit by Target.
Have been battling myself to switch over to cash…its very hard…but until we actually have a mostly secure funds transfer environment – it makes little sense to use CC’s for most spending (or your just playing the roulette table again).
Changing behavior to match that reality is the hard part.
Brian you are like the cop from youtube who posted a video how to counterfeit credit cards. What do you expect people to do after they watch such videos ? a lot of criminals get advices and tips from you. You did more harm than those cyber crooks ever did
Really? I’m creating cybercriminals now, am I? There are 101 places you can find with a simple Internet search that will sell you these cards. My pointing out the location of one them is not a big roadmap. If anything, it’s a detour sign.
As an e-commerce system outside of the US we already treat any order involving a US issued card as high risk requiring manual investigation before allowing any order, and it’s getting close to just rejecting any order on a US issued card.
I know from speaking to plenty others in the business that we are not the only ones doing this. It’s just too much risk given the repeated breaches. The ‘trust’ of US cards is non-existent, and until there is a massive change in the way it is handled in the US it will never recover. It’s almost come to the point where it’s safer to accept an order with a delivery address in Nigeria made from an IP address in Indonesia using a card issued in Pakistan than it is to accept US cards.
OK, chip-and-pin won’t stop these attacks, but they will make the data gathered much harder to use, making it less worth the effort of getting in the first place. If the data can’t be used online (no cvv) and can’t be used in store (because they’ve finally moved out of the stone age and stopped using mag stripe) then it becomes less interesting to get.
Hacking will still happen, but chip-and-pin will make it harder. Sticking with mag stripe for everything is just like leaving your house unlocked all the time – the attitude of because someone could break in anyway, why bother locking it…
American cards are functioning just fine with heuristic modules such as Kount and Subuno. It’s the Europeans that might have it wrong, actually. I understand trying to secure swiped cards, but all that does is push the fraud to online. So stop indenting the card numbers. Don’t transmit the card number AT ALL through any computer and there’s no way to harvest it for online use.
Securing online transactions is … well … different.
VBV is of questionable benefit because of keyloggers, and the liability shift is no longer appropriate to anyone else than the bank. Pin pads for home use are futile. That will cost more than it saves in fraud write-offs because it’s stupid and nobody has one at their disposal. It turns money non-liquid because you need a pin pad.
Thank you, once again for all your efforts to combat miscreant activity. From a person who works in the financial industry it is really appreciated how you do education as well as inform us how schemes work so we can develop anit-fraud tactics. If you receive any updates on Pei-Wei please update, thank you again!
You know what’s absent from any of this technology?
A way to verify by central system a credit card with some sort of liability shift away from the merchant for transactions exceeding $X. I get that issuers don’t want to perform that service en masse, but it’s an absolute crime that responsible merchants _want_ to verify big transactions for $12,000 and can’t. For transactions like that, it’s viable to pick up the phone. Heck, charge the merchant a fee. They’d gladly pay. Banks just don’t care because they rarely eat it. That’s not good for merchants or the economy.
“Hello I’d like to verify that this $12,000 transaction is real.”
You can call them, but they disclaim liability in every way possible even if you get someone to “verify” it.
Any information on when this breach occurred, how long and what dates?
Read what Brian wrote in the second paragraph of his report on this breach:
“Several banks contacted by KrebsOnSecurity said they acquired from this new batch multiple cards that were previously issued to customers, and found that all had been used at P.F. Chang’s locations between the beginning of March 2014 and May 19, 2014.”
All this hacking is making me very nervous. I am going on an extended road-trip vacation and had planned to use my laptop to keep in touch and pay my bills. To do that, I’ll have to transmit user IDs and passwords using Internet connections on the road, such as at Starbucks or the local library. Is there any way to maximize security?
Use a VPN. There are free ones , but there are also paid ones like Golden Frog (just buy the minimal package) which I have used.
Maximize your anti-virus by adding Malwarebytes Pro which adds an additional real-time shield. It is probably the best scanner in the business. As soon as you install it (before your trip), run a system scan.
If you use Adobe Reader, go to Edit -> Preferences -> Security (Enhanced) and check Protected View -> Files From Potentially Unsafe Locations (or if you are paranoid, All Files).
Use Firefox with the NoScript add-on for surfing.
Instead Adobe Reader use Foxit..
Re Malwarebytes Anti-Malware Pro:
I keep getting “SDKD Database Load Defaults code 2001”
PC Cobbler, any ideas what is going on there?
I’ve never seen that error. Are you using the latest (2.0.2.1012 is current) version? If not, uninstall it, delete the C:/Program Files (x86)/Malwarebytes Anti-Malware folder, and install the latest from malwarebytes.org. If it were me, I would uninstall, delete, and reinstall.
You can always go to https://forums.malwarebytes.org/ and post questions. People there are good at answering the odd question.
SumatraPDF is another alternative PDF reader.
If this had happened before the Internet people would be outraged, now its business as usual and losses are added to the prices people pay. If consumers knew how much each was paying separate like they do with taxes they wouldn’t be happy.
I’m surprised by all the “but it doesn’t help with online fraud” and “it will just push the fraud online” comments. Whenever I use my credit card online, I always use a one-time number with a limit of just the purchase amount. I’m not worried about my online purchases much, since the credit card number I use is worthless as soon as the transaction goes through.
I don’t know how the European chip cards work, but I assume that they generate a new code for every use and that only the credit card company can verify the validity of the code. So having a chip card basically extends the one-time use of the card number from the online world to the physical world.
Why wouldn’t that solve a whole lot of this credit card theft?
People who _want_ to be bothered with one-time-use CCs like that will do so, but in general, this would be horrible for conversion rates. Should I really have to log into my CC company’s backend and go through a 2 minute process to buy a $20 product?
Probably not. Writing off 1/1000th of $20 is much better than abandoned carts out the wazoo.
That 120 seconds might be billions in revenue. They’d rather write it off and pass it on. To an extent, they’re right. It’s horrible to throw extra steps in front of purchases most of the time.
Not sure about anyone else but I ate at Pei Wei and then had a fraudulent charge to my account this past weekend. Had no clue why, this may have shined some light.
Why is this dated June 14? Are you writing from the future? Is there still time to stop this from happening?
Dale — the big number is the day.
I could not figure this out at a glance either. The 14 is the year and the day is 10. If the blog is not an out-of-the-box Workpress template, then perhaps writing 2014 instead of 14 would avoid some of the confusion.
Ditto. But I figured it out in the time an Atari 2600 can figure out Pi to 100 decimal places. IOW it took way too long.
Solutions for this type of thing are not complicated. We don’t need to reinvent credit/debit cards, we just need to follow basic security tenets.
1). Point of Sale processing systems should only have internet access to/from the card processor to approve/decline transactions. Firewall everything else incoming/outgoing.
2). Point of Sale networks should never be connected to other networks, only devices relevant to these sales should be connected to the network.
3). Retention of credit card data should be 0 days. There is no reason to keep credit card data… ever, for any reason.
4). Over the wire encryption for the entire Point of Sale network should be enforced.
Basically when you have these types of breaches it is generally due to unencrypted/unsalted card retention in a poorly or completely unsecured database attached to a production network. There is no excuse for this and companies should be strictly audited before being allowed to accept credit cards.
Thank you for making this point. The retailer has an obligation to meet these much of this criteria through PCI, though physical separation is not required (but it should be). It is a lot of work for the retailer and unfortunately not enough good PCI audits are being performed.
The issue in many, many cases is that the back office wants to be able to easily access the POS servers and databases (through client applications) to configure the terminals and perform reporting. In a case like this, a manager of a restaurant with a PC will want to be able to add items to the menu. That means the POS system will almost always be on the same network. Application publication software and correctly configured firewalls can help the application exist for a user virtually while it is still on a different network.
I would imagine that investigators should easily be able to pinpoint the actual restaurant where the cards were used, and then identify the waitstaff who had access to them. Why is that so difficult in today’s world?
Someone mind telling me how the heck you can buy stuff without the PIN?
I understand the whole concept of using an MSR206, using an embosser etc… except how you can swipe a card when you buy something and not need to enter a PIN?! Do they not ask for a PIN in America?
What is then even more confusing is I’ve seen dumps from countries like Spain and UK which aside from needing the PIN (which isn’t provided when you buy the dump) they also need a chip in the card to function… my guess is you have to use them abroad in USA where they don’t have chip readers in the till POS machine, but surely banks would just block them or call up the customer?
Thanks in advance to anyone that replies.
I know for a fact that some ATMs in the UK still primarily read magnetic strip data as opposed to EMV ICCs.
However, a skimmer can be applied to anything where the magnetic strip passes horizontally, so one assumes that the european dumps are from skimmers on ATMs. As I said, though, skimmers can also be applied to some Chip and PIN machines. Also, some unscrupulous retail workers have been known to use handheld skimmers to extract data.
@Luke2
You misunderstood me, my question was how could they use a PIN protected card in USA without it getting blocked and without knowing the PIN? I know whether or not it has a chip makes no difference as the POS machines don’t even check chips.
From what Eric said I understand USA cards don’t ask for a PIN when you’re in a store, but as European cards do (at least in Spain and UK they do) so how could they use them? As easy as just swipping? :-/
@Ajay
Cards in the US are of two types, debit/credit or straight credit. They can be run as credit cards, usually with nothing more than a signature required.
So if a carder has a physical card they can just swipe and sign when in a large store like best buy. The signature won’t match the card holder but by the time the card company figures it out the card’s already in the trash and the carders on to the next one. Thats why quantity is more important than quality for carders. You may have a 10,000$ limit on a card but it’s likely only good for a day and large charges will warrant a call to the cardholder.
@Eric
Thanks.
How do you “run” them as a credit card so that you don’t have to sign? Some cards you need a PIN for though, because I’ve spoken to an American which always uses a PIN in the shops, or are they wrong?
Sorry to ask so much, in UK we just use PIN.
If it is a credit card, then it doesn’t come with a PIN. (It may come with one for cash advances in ATMs, but sometimes not even that.) There is no such thing as swipe & PIN. Only a very few POS terminals are able to take chip cards, so for everywhere else, you have to swipe and (usually) sign either paper or a screen.
If they do take a chip, and the card has a chip, then it will require the chip be read. Only then would one possibly need a PIN.
I don’t have a debit card, but they are different and always come with a PIN as they are also used as an ATM card.
Thanks Dora.
Final question though as I’m still unsure of 1 thing. Some of the cards on rescator.so are from countries like UK where you need a PIN (4 numbers) to do a transaction in a shop or ATM.
I understand you can use a UK card in USA without the chip and it will work as the machines don’t check the chip there, however do they not ask for a PIN too?
If they don’t ask for the PIN and just expect you to sign for the transaction I feel sorry for the UK and other banks that fraud is still so easy… 🙁
I hope you realize that Chip & PIN hasn’t prevented this kind of organized fraud. US cards are more prevalent online because there’s simply more of them to be had. Americans are credit crazy, everything is a damn credit card here.
@SeymourB
So you’re saying if I went to USA with my UK card, I can just swipe it and won’t be asked for a PIN? :-O
If that is true no wonder dumps from countries like UK and Spain are being sold on rescator.so, easier to abuse them in USA.
@Ajay,
From my experience you will be lucky if they accept your UK Mastercard now. The trend lately seems that US traders are becoming more and more insular in their outlook.
Even with the backing of PayPal 90+% do not want to
accept it – even with expensive desktops and the like protected with Fed-X or DHL High Security
@BaliRob
But would they ask for the PIN?
If what you say is correct I’m confused as to why dumps are sold on rescator for those countries.
They most obviously work though, otherwise they wouldn’t have been copied in the first place since the customer would’ve have swiped them…
Confused!
Dear Ajay,
This is the absurdity of cards and PINs.
PayPal registration when it first came out was intended as an assurance for the trader that the purchaser and his/her card and address had been vetted and that registered traders using PayPal would show out to the purchaser as a reliable source. PIN numbers and card details are never used in open form – only PayPal have your security details.
PayPal is now becoming a more restricted service which saddens me because I had 100% feeling of security with them.
At the time of the purchase the customer is given a choice of what type of card to use. Prior to swiping the card you choose credit or debit. If the customer chooses debit, then they swipe and have to enter a PIN. If the customer chooses credit, then they swipe and have to sign. If your friend is always entering a PIN, then they’re always using their debit card as a debit card.
There is no difference in terms of liability for how the customer uses their card. With debit cards there’s usually a $50/transaction liability for fraudulent use of the customer’s card, which is usually (though not always) waived. Credit cards usually carry a $0/transaction liability. However if you run a debit card as a credit card, you don’t actually get any additional protection, it’s still $50/transaction. The liability is tied to the card, not the payment method used.
Beyond this there are pure debit cards, which only work at stations equipped for debit cards. This includes most, but not all, retail locations (restaurants without mobile payment terminals can’t run debit cards, since they swipe cards at a staff terminal).
It’s kind of a hidden choice. A lot of the time I struggle and you have to hit “cancel” or something.
Many PIN pads are heavy-handed about making users use PINs when the card it credit OR debit, I presume, because the interchange rate is lower. Costco only accepts Amex & debit card with PIN at gas stations for that reason I think. They negotiated a special rate with Amex and Debit+pin is a much lower rate.
Why would anyone use it as a debit card except where absolutely required? There’s no advantage to you.