Millions of Web sites were shuttered Monday morning after Microsoft executed a legal sneak attack against a malware network thought to be responsible for more than 7.4 million infections of Windows PCs worldwide.
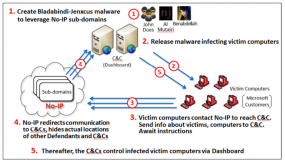
A diagram showing how crooks abused no-ip.com’s services to control malware networks. Source: Microsoft.
In its latest bid to harness the power of the U.S. legal system to combat malicious software and cybercrooks, Microsoft convinced a Nevada court to grant the software giant authority over nearly two dozen domains belonging to no-ip.com, a company that provides dynamic domain name services.
Dynamic DNS services are used to map domain names to numeric Internet address that may change frequently. Typically, the biggest users of dynamic DNS services are home Internet users who wish to have a domain name that will always point back to their home computer, no matter how many times their ISP changes the numeric Internet address assigned to that computer.
In this case, however, the attackers responsible for leveraging two malware families — remote-access Trojans known as “njrat” and “njw0rm” — were using no-ip.com’s services to guarantee that PCs they infected would always be able to reach the Internet servers.
Microsoft told the court that miscreants who were using these two malware strains were leveraging more than 18,400 hostnames that belonged to no-ip.com. On June 26, the court granted Microsoft the authority to temporarily seize control over 23 domains owned by no-ip.com — essentially all of the domains that power no-ip.com’s free dynamic DNS services.
Microsoft was supposed to filter out the traffic flowing to and from those 18,400+ hostnames, and allow the remaining, harmless traffic to flow through to its rightful destination. But according to no-ip.com marketing manager Natalie Goguen, that’s not at all what happened.
“They made comments that they’d only taken down bad hostnames and were supposedly redirecting all good traffic through to users, but it’s not happening, and they’re not able to handle our traffic volumes,” Goguen said. “Many legitimate users that use our services have been down all day.”
Goguen said while Microsoft claimed that there were more than 18,000 malicious hostnames involved, no-ip.com could only find a little more than 2,000 from that list that were still active as of Monday morning. Meanwhile, some four million hostnames remain offline, with customer support requests piling up.
“So, to go after 2,000 or so bad sites, [Microsoft] has taken down four million,” Goguen said.
Microsoft told the Nevada court that despite numerous reports released by Internet security firms over the past year about large volumes of malicious activity emanating from no-ip.com’s service, the company “consistently failed to take sufficient steps to correct, remedy, or prevent the abuse and to keep its domains free from malicious activity.”
But according to Goguen, the first time Microsoft brought its concerns to no-ip.com was at 7 a.m. on June 30, when the company’s CEO received a knock on the door of his family home and was served with a copy of the court order granting Microsoft authority over the 23 no-ip.com domains.
“We work with law enforcement all the time, and our abuse department responds to abuse requests within 24 hours,” Goguen said. “It’s pretty sad that Microsoft had to take such extreme measures to go about this.”
Goguen isn’t the only one who believes Microsoft swatted a fly with the equivalent of an atom bomb. Some of Microsoft’s previous legal sneak attacks targeted “bulletproof” hosting providers — those that promise to keep sketchy (and high-paying) customers online despite pressure from security firms and law enforcement. But according to Dmitri Alperovitch, co-founder of security firm CrowdStrike, treating no-ip.com like one of these shady providers is a mistake.
“They have always been very responsive to security researchers and law enforcement,” Alperovitch said of no-ip.com. “I do not consider them a bullet-proof or abuse-proof host.”
Meanwhile, Goguen said no-ip.com is considering its legal options for responding to the outage and to Microsoft’s allegations that the company somehow turns a blind eye to abuse complaints.
“We’re speaking with our lawyers about this, but right now we’re doing everything we can to fix this, and we need our users to understand that.”
In tandem with the action against no-ip.com, Microsoft also named and accused two men — software developers thought to reside in Kuwait and Algeria — of authoring and selling the njrat and njw0rm.
The complaint against no-ip, the accused malware authors, and the rest of Microsoft’s various legal filings in this case are available at this link.




It doesn’t take much reasoning to assume that MS is working with a government entity.
Someone is lying about the time MS contacted no-ip.com. on this article. Assuming MS could be held for perjury, you have to assume the no-ip.com CEO is lying. If not, then make a change in the way the courts work by having the courts make a simple phone call to verify facts. (I assume MS had a paper trail.) As far as making 4 million suffer, that’s a small number compared to having 1 Billion having spam and DOS attacks on the internet occur.
nice try, microsoft. we all know how you are and what you do. of course microsoft is lying. this is not about malware. if it were, they would just update their anti-malware tools and block the stuff. this is to take no-ip down so they can market their azure crap-platform to small companies.
this was a well executed plan, with the help of the usa courts/government. it was only way to take down no-ip even on areas outside the usa.
no-ip.com is still up and running.
Huh? When did Microsoft claim to have contacted no-ip before the court order was delivered?
The article says Microsoft claimed there were “numerous reports released by Internet security firms over the past year” but that’s not the same thing.
You don’t get the point: MS is here working *AS* a government entity. Does this US judge ever heard about separation of powers?
Did you really mean the one-time swat of a billion blowflies justifies the mental and financial harm of some million honest contemporaries?
Wake up!!
Separation of powers separates the executive, legislative and judicial branches of the government. MS is not a part of any branch.
This seems an awful lot like killing the patient to cure the disease. Also, I’m uncomfortable with the seeming ease of how a corporation influenced lawmakers decisions into letting the corporation take action. To me, that screams justified vigilantism, but hey, what do I know?
The magic number is 70.
Thats how many hours an unprotected pc without UAC or malwarebytes lasted before malware was able to worm its way in.
By unprotected l mean using a free AV.
So i wont be shedding any tears for the cybercriminals and malware authors or no-ip for allowing it to continue.
No tears cybercriminals and malware authors, yep.
As for No-IP, near as I can tell the vast majority of their customers haven’t committed a crime. So why are they being punished?
Should HotMail, GMail, Yahoo and a few other services be closed? Certainly miscreants misuse those providers.
Are your proposing ANY service provider that had a crook use their services should be shuttered? Would that include Microsoft?
Deliberately punishing the innocent along with the guilty is a poor logic and flawed humanity.
I’ve gotten spam from Hotmail before. Should they be closed down because of it?
Where is the greater good here?
Complaining about your email being down for one day is selfish. Sacrificing your e-mail for one day to stop the countless criminal activities this stopped is the “Greater Good.”
This has to be the silliest internet hissy fits I’ve seen in a long time.
Shutting down an entire company for a few abusers without regard for legitimate users is by definition selfish.
It’s not just email, and it wasn’t just one day. Besides, it was *completely unnecessary* – if they’d cooperated with no-ip instead of seizing the domains there would have been no outage and the attack on the malware network would almost certainly have been just as effective.
Thats your response? I get spam from hotmail,gmail,whatever mail all the time.it goes right into the junk mail ,which these companies have provided for me to filter btw,until i allow it.
That is the difference.I havent been infected with a virus for a good 11 years now.Gee how did that happen? By not using “free” or hacked software.
I gave many free internet services and operating systems a chance, but they always seem to fail one way or another with basic use.
Those wrongly affected by Microsoft’s actions should take Microsoft to small claims court for damages
Make them fight thousands of cases in thousands of courts and die a death of thousands of cuts.
Good luck every getting the money even with a winning judgment.
even if you could get the money all 4 million sites could win the maximum allowable in small claims and it would be nothing more then a blip on the books for M$ that would be simply be claimed as a loss next year and written off.
Total silly idiotic slacktivism waste of time.
Posted on the Facebook page for Microsoft’s Digital Crime Unit :
” … Due to a technical error … some customers whose devices were not infected by the malware experienced a temporary loss of service. As of 6 a.m. Pacific time today, all service was restored. We regret any inconvenience these customers experienced.”
Service restored … or perhaps not. Plenty of people responded saying their domains were still unable to resolve and sites were down.
From Computerworld :
“No-IP spokeswoman Natalie Goguen wrote via email that Microsoft made a technical change on Tuesday to forward legitimate traffic back to No-IP, but “it didn’t do anything.”
“Although they seem to be trying to take corrective measures, DNS is hard, and they don’t seem to be very good at it””.
And a postscript : Microsoft’s actions appear to have had an unexpected (and possibly beneficial) side-effect. According to Kasperky the No-IP operation was also being used for a number of state-sponsored or state-approved malware attacks. Possibly some governments will be less than pleased as a result.
Computerworld’s summary says :
“Although Microsoft was taking aim at two malware families called Bladabdindi and Jenxcus that employed No-IP, Rau wrote the seizure has had a larger impact on so-called APT (advanced persistent threat) campaigns, which are long-running infiltration operations often run by nation states.
Computers used in these campaigns “are now pointing to what appears to be a Microsoft sinkhole,” Rau wrote.
The malware includes Flame, which was found on computers in Iran and other Middle Eastern countries, and the Italian company Hacking Team’s Remote Control System, which is spying software intended for use by law enforcement.”
The Kaspersky analysis is at
https://www.securelist.com/en/blog/208214339/Microsoft_seizes_22_NO_IP_domains_disrupts_cybercriminal_and_nation_state_APT_malware_operations
you don’t see a problem. alrighty then, guess there isn’t a problem..argh.
you are kidding, right?
you seriously suggested that ms play a chase it’s tail game…ms provides ip address, wait one day while noip removes address and miscreant starts new one… then repeat cycle.
other than burning cpu cycles and resources, your proposed solution isn’t a solution at all. but that’s what you propose, that noip just let these miscreants keep creating new accounts.
even on googles places, google sends a paper letter to verify the address, would that be such a burden to you and grandma? or does she keep moving every few days?
noip doesn’t seem to have addressed the issue,and if you are telling me that is the best they could do,they are pretty pathetic.
again,your suggestion is wait until ms complains about specific ip addresses.. and that IS exactly like the bar that ends up getting raided. your attempts to argue that noip was wronged have only added weight to the position that ms did the right thing.
sorry, but i don’t buy your argument. i understand the human shields are upset, that restaurant had good food,and unbeatable prices. there is a reason for that.
there are many things noip could have did. it would be nice if they did some of them instead of the complaint response shell game. but the fact is they admit 2000 existed the day after the ‘raid’. so they know they have a problem, and didn’t handle it.
if you can present an actual solution, i would love to hear it, but so far your proposal is to allow the miscreants to simply sign up new addresses. got anything else? and if so, why didn’t noip already implement it?
misplaced comment. should be reply to johnston.
sorry about that.
You seem to think that no-ip was benefiting somehow from having the illegal users. How exactly do you think that worked?
The fact that there’s no way for them to magically tell which users are legit and which aren’t doesn’t justify shutting down the entire service. It *certainly* doesn’t justify shutting down the entire service without warning.
And the idea that it would have taken them a day per IP address is ridiculous. They could have given MS direct access to their infrastructure if necessary, so that MS could zap addresses as fast as they liked.
So … “there are many things noip could have did”, huh? How about you name three?
Also, you seem to be under the impression that permanently shutting no-ip down would be a huge victory against the criminals. It wouldn’t. The bad guys would just move to another technique for C&C, it isn’t as if they haven’t got lots of options. It’s only the legitimate users who would suffer.
Incidentally, describing no-ip’s customers as “human shields” is both offensive and inaccurate; it isn’t as if they’re being somehow subsidized by the bad guys, or are only being provided with service in order to distract attention. This isn’t Facebook; the end users are the customers, not the product.
we covered this already.
telephone, snail mail, signup delay. three things.
of course the human shields find it offensive, just like the legit patrons of a mob owned restaurant, they were there for legit purposes and the great meal at a cheap price is a ‘loss’ to them. why coúldn’t they raid the restaurant and keep the food coming? not the first time someone said that, won’t be the last.
your assumption that a bar owner has to have direct, or even indirect benefit is also off. it creates a blind side to any sis
tuation where you don’t truly understand motivation. in your model, you have to know the answer to motivation as the starting point for determining behavior. unfortunately,meven when folks try to accurately describe theirn own motivation they are oftem way offf, and sometimes completely wrong. i caution against discounting ‘scenarios’ simply because you don’t know the motivation. it’s a bad habit that some folks in infosec share, so you have company there, yet one could argue it’s a factor in allowing 9/11 to take place.
the internet security firms don’t count to you as noip being aware of the problem. that logic says they knew from the internet firms but because the internet firms didn’t have standing, it’s ok to ignore them. that again puts it into the seedy bar truning a blind eye situation. you are doing a wonderful jog digging noip into a deeper hole.
i understood that on one prior occasion ms alerted them, however, whether it was grandma, a bum,, ms, or the security firms, it’s clear they were alerted to the problem. the actions they took were clearly insufficient, as noip admits to 2000 of the ms initial list. given the churning of the ‘bad’ ddns, it’s surprising it’s that high. effectively designed malware should have had that come out to zero. thus one argue the differential of 18000 and 2000 is more a measure of the ‘quality’ of the malware than of remedial effectiveness.
my sense from your technical semantic arguments is that you feel comfortable with false precision. for you and others in the same boat i suggest that it’s better to be approximately correct than precisely wrong.
i regret i can’t continue this discussion past this point other than to say ‘sorry your favorite bar was raided’.
You seem determined to think of no-ip as criminals (“mob owned restaurant”) and I see absolutely no justification for that. I can only assume that you’ve already made up your mind that they must be bad guys (hey, bad things never happen to good people, right?) and simply aren’t willing to think rationally about it.
“your bar was raided” – you also seem determined to minimize the importance of the service. For many of the legitimate users, the loss of service was not trivial. It should be more like “sorry we trashed your cities telephone exchange, but hey, criminals were using it to phone each other!”
“telephone, snail mail, signup delay” – telephone and snail mail would be too expensive, and I don’t see how a signup delay would help. Basically what you’re saying is that only huge megacorps should be allowed on the internet and that if small businesses try to provide internet services they deserve what they get. Obviously, I disagree.
There is another very positive, if somewhat painfully gained, side effect: As this whole thing could only happen the way it happened with/between/concerning usa entities one effect certainly is that even more people avoid anything usa related.
It’s simple: If you are dealing with a us company or with any entity de facto under us jurisdiction (like us companies abroad) you will sooner or be f**d.
us companies don’t care about anything but us law, even in other countries. And us courts habitually ignore law so as to have the us entity win.
No-IP probably provides decent service. But they are us based and most of their domains are under us TLDs like .com. So, while I wish them (yet another m$ victim) good luck I also strongly advise against using their – or any us companies – services.
How could no-ip tell the legit customers from the criminals? They couldn’t or didn’t. But they should have.
Running a reputable internet resource takes time/money. If you don’t earn enough revenue to pay people to enforce your terms of service, you’re going to become a magnet for people who plan to ignore them.
If your legitimate website/email is hosted by a company that is undercutting the prices of other companies, you should ask yourself why. And you shouldn’t be surprised when you are inconvenienced because your host can’t manage its own business well enough to keep from becoming a dangerous nuisance to the rest of the internet. If you want 0% downtime, don’t use a host with unsustainably low prices, because they’re either running an FBI honeypot or they’re going to go down, too.
There’s simply no point in no-ip (and the dozens of other DDNS providers, free or otherwise) spending huge amounts of money in a futile effort to catch every bad guy that might try to make use of their services.
The best case scenario? The bad guys stop using DDNS. So what? They’ve got plenty of other options, perhaps it takes them a couple of weeks to retool. It just isn’t worth it.
As for the customers, it would be foolish assume that spending more money guarantees you a better or more “reputable” service. Most of the time, all it really guarantees is a bigger profit margin.
I agree with the pro Microsoft banter/comments above. The host company had been given numerous opportunities to curtail or change their portion of business practice which was making their facility so appealing to nefarious users, including a number of foreign government entities attempting to mask their presence in the US. Those who seem to believe that any firm providing services like No-IP are needed on the INTERNET are delirious.
I can sum up my thoughts by simply saying “Bravo Microsoft”
” Those who seem to believe that any firm providing services like No-IP are needed on the INTERNET are delirious.”
Tell that to home DSL subscribers, like me, who need the ability to SSH into their home networks. Tell that to people who want to run small web servers from their homes. Tell that to people who use dynamic DNS to find their stolen laptops.
Eaglewerks,
Your understanding of how the Internet –currently using IPv4– works is deficient, and before you say IPv6 that is realy no better in some respects and a lot worse in others.
As the Internet of Things (IoT) gets going and mobile devices trying to communicate with other mobile devices the Many-talk-to-Many issue will reappear over and over, and the only workable solution currently is for both devices to use DDNS or equivalent.
Pretending otherwise and sticking your head in the ground is only going to make your less than desirable features a static target for others to take aim at.
The fight with malware seems became brutal. I cannot imagine how many innocent people/web sites suffered this seizure.
I’m rather amazed at the number of people who think that either Microsoft or the court acted properly in this matter. What happened was blatantly wrong in so many ways.
Its bad enough that we have ex parte orders running rampant for law enforcement but now we are OK with vigilantes asking to be handed control of another companies assets?
Lots of paranoia & conspiracy theories running through the commentary to this article. I suppose that No-IP could have tried to rid themselves of cybercrims and MS wouldn’t have become involved.
And I suppose that a large portion of the 4 million “innocent victims” could have made an issue of the “abuse” themselves without help from the reactionaries writing here…;^)
Good work as always, Brian. Have a good day!
http://blogs.technet.com/b/microsoft_blog/archive/2014/06/30/microsoft-takes-on-global-cybercrime-epidemic-in-tenth-malware-disruption.aspx
The link above is an article from Microsoft stating that it was an accident that users went down for the time they did. Yes you can agree that giving them 100% control and seizing no-ip company domains was a mistake by lawmakers but honestly kudos to Microsoft for trying. Microsoft gets crap about their operating system being buggy and full of infections but now their trying to do something about it and everyone is STILL giving them crap.
Microsoft by its actions against no-ip.com in my opinion is guilty of malicious prosecution, or for false imprisonment (the hijacking of a legal entity and its 4 million users).
kidnapping each user by taking them somewhere they did not wish to go without their consent ,the users contracts were with no-ip.com not Microsoft.
It does not matter if Microsoft in its infinite wisdom and bloated ego believed they could pull it off transparently they failed. If Microsoft wanted to accomplish “filtering” of suspect users going through the no-ip.com site they should have approached no-ip.com with funds, equipment and expertise.
Funds because the problem is with, in my opinion, the design of Microsoft’s operating system,
Worked with processor manufacturers to design in an id “not reconfigurable” similar to the mack address of the lan adapters only encrypted to uniquely identify a machine, and allow /disallow access on a list managed similar to Virus keys.
How about a class action suite against Microsoft asking for 1,000 for each day their site was affected for each of the 4 million honest users of no-ip.com.
Microsoft will only respond to actions that cost them money.
I agree with C U Anon. Eagelworks, you have no idea what No-Ip is for. It’s NOT a criminal enterprise. It doesn’t even host content. It simply redirects it using a non-IP domain name.
That’s like saying go-daddy is pro-crime/malware.
ALL hosts host malware, even COMPLETELY LAW-ABIDING ones. You can’t have a perfect world. It’s impossible. No-ip isn’t popular because it allows abuse. Rather, because it’s free and allows some hf skid to run connections in a RAT to his home IP, even when he’s on the go. It can be legitimately used as well. I use it for lawful purposes. What? So I’m a criminal?
If you plan to support bringing down a DYNAMIC DNS SERVICE which is NOT CRIMINAL, then why not ban hosting providers, all of them too? OH WAIT, the government and MICROSOFT USE THEM.
ISPs use them, so does Law Enforcement, and so do the people who CATCH cybercriminals. You can’t fight every cause. Sometimes, you DO need to fight the symptom, because fighting the cause only means you’re fighting people who have nothing to do with it, causing collateral damage.
you sir, no offense, but have a completely inadequate and beg my pardon, moronic understanding.
MyWOT does the same, by its users saying every host is a spammer because someone HAPPENS to use their service. with FREE service you ARE going to get that. nothing is entirely perfect. you’re going to have people who abuse EVERYTHING, even LEGITIMATE things.
An Operating System like Windows is used to run the builder for SpyEye, which generates a malicious stub. WHY NOT BAN MICROSOFT? After all, they’re ENABLING malicious activity, are they not?
It’s a DANGEROUS way of thinking. Treat the people doing the wrong, NOT the tools they use to do it when those tools are NOT designed explicitly FOR that.
you have very little understanding in this, no offense. please just get more understanding, because the fact a service is USED FOR a purpose, doesn’t mean it’s DESIGNED FOR it, NOR does it mean that they don’t respond to abuse reports, because no-ip DOES.
It’s up to the community to REPORT it. If the community reports it, they investigate. Investigation also does NOT mean it gets taken down, because often these notices are FALSE/inaccurate.
it takes time to JUSTIFIABLY shut down a domain, just like it is even with U.S. LEGAL hosting businesses.
the question is how to detect them, not how to shut down the businesses running them. in the end, you’re ruining a LOT of LEGITIMATE organizations who DO use it LEGITIMATELY, who now are paralyzed.
“In its latest bid to harness the power of the U.S. legal system…”
You need to complain to Nevada court that allow all things to happen. Not to Microsoft. Not to No-IP.com neither.