New data gathered from the cybercrime underground suggests that the apparent credit and debit card breach at Home Depot involves nearly all of the company’s stores across the nation.
Evidence that a major U.S. retailer had been hacked and was leaking card data first surfaced Tuesday on the cybercrime store rescator[dot]cc, the shop that was principally responsible for selling cards stolen in the Target, Sally Beauty, P.F. Chang’s and Harbor Freight credit card breaches.
As with cards put up for sale in the wake of those breaches, Rescator’s shop lists each card according to the city, state and ZIP code of the store from which each card was stolen. See this story for examples of this dynamic in the case of Sally Beauty, and this piece that features the same analysis on the stolen card data from the Target breach.
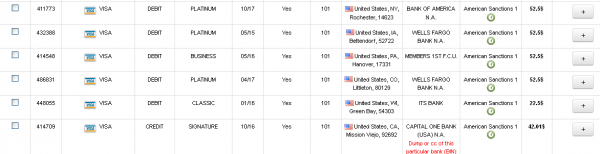
Stolen credit cards for sale on Rescator’s site index each card by the city, state and ZIP of the retail store from which each card was stolen.
The ZIP code data allows crooks who buy these cards to create counterfeit copies of the credit and debit cards, and use them to buy gift cards and high-priced merchandise from big box retail stores. This information is extremely valuable to the crooks who are purchasing the stolen cards, for one simple reason: Banks will often block in-store card transactions on purchases that occur outside of the legitimate cardholder’s geographic region (particularly in the wake of a major breach).
Thus, experienced crooks prefer to purchase cards that were stolen from stores near them, because they know that using the cards for fraudulent purchases in the same geographic area as the legitimate cardholder is less likely to trigger alerts about suspicious transactions — alerts that could render the stolen card data worthless for the thieves.
This morning, KrebsOnSecurity pulled down all of the unique ZIP codes in the card data currently for sale from the two batches of cards that at least four banks have now mapped back to previous transactions at Home Depot. KrebsOnSecurity also obtained a commercial marketing list showing the location and ZIP code of every Home Depot store across the country.
Here’s the kicker: A comparison of the ZIP code data between the unique ZIPs represented on Rescator’s site, and those of the Home Depot stores shows a staggering 99.4 percent overlap.
Home Depot has not yet said for certain whether it has in fact experienced a store-wide card breach; rather, the most that the company is saying so far is that it is investigating “unusual activity” and that it is working with law enforcement on an investigation. Here is the page that Home Depot has set up for further notices about this investigation.
I double checked the data with several sources, including with Nicholas Weaver, a researcher at the International Computer Science Institute (ICSI) and at the University California, Berkeley. Weaver said the data suggests a very strong correlation.
“A 99+ percent overlap in ZIP codes strongly suggests that this source is from Home Depot,” Weaver said.
Here is a list of all unique ZIP codes represented in more than 3,000 debit and credit cards currently for sale on Rescator’s site (Rescator limits the number of cards one can view to the first 33 pages of results, 50 cards per page). Here is a list of all unique Home Depot ZIP codes, in case anyone wants to double check my work.
In all, there were 1,822 ZIP codes represented in the card data for sale on Rescator’s site, and 1,939 unique ZIPs corresponding to Home Depot store locations (while Home Depot says it has ~2,200 stores, it is safe to assume that some ZIP codes have more than one Home Depot store). Between those two lists of ZIP codes, there are 10 ZIP codes in Rescator’s card data that do not correspond to actual Home Depot stores.
Finally, there were 127 ZIP codes for Home Depot stores that were not in the list of ZIPs represented in Rescator’s card data. However, it’s important to note that the data pulled from Rescator’s site is almost certainly a tiny fraction of the cards that his shop will put up for sale in the coming days and weeks.
What does all this mean? Well, assuming Home Depot does confirm a breach, it could give us one way to determine the likely size of this breach. The banks I spoke with in reporting this story say the data they’re looking at suggests that the breach probably started in late April or early May. To put that in perspective, the Target breach impacted just shy of 1,800 stores, lasted for approximately three weeks, and resulted in the theft of roughly 40 million debit and credit card numbers. If a breach at Home Depot is confirmed, and if this analysis is correct, this breach could be much, much bigger than Target.
How does this affect you, dear reader? It’s important for Americans to remember that you have zero fraud liability on your credit card. If the card is compromised in a data breach and fraud occurs, any fraudulent charges will be reversed. BUT, not all fraudulent charges may be detected by the bank that issued your card, so it’s important to monitor your account for any unauthorized transactions and report those bogus charges immediately.




Makes you want to start using cash again. Maybe I will, at least it seems the safer route nowdays.
Don’t use an ATM, those are dangerous too.
Yeah, to truly not have any reliance on cards, you have to write checks to cash, and not use ATM’s. I have a friend whose purse got stolen and the thieves were able to go to a branch and get all the money out of their account (she and her husband). They even were able to transfer the money out of their savings account at the bank.
I guess if you’re really extreme, you could not rely on banks at all and cash any checks made to you directly. But given that credit card fraud and bank fraud will be rectified in the US, it’s very likely the cash you lose or have stolen from you will be more than the costs of using checks and cards. There is no process for getting back stolen or lost cash.
” … the thieves were able to go to a branch and get all the money out of their account (she and her husband). They even were able to transfer the money out of their savings account at the bank.”
Had the account owners put into place a password for all at-the-bank (in person as well as telephone) transactions this would not have happened.
well, I am not sure I want to walk around with 3000 dollars in cash but more importantly pull out a wad of cash at the checkout line of HD, and then start counting out 2460.oo(my last HD purchase) in $20 dollar bills.
Paying it in hundreds would not be so bad but it would probably require a manager to triple check that I am not using fake bills. If I start counting out over a hundred and twenty bills, it will be a scene as well, so everyone know I am running around with a ton of cash.
What is the problem here though? Is it my bank – no. Is it Visa that mailed me the plastic card – no. Is it my record keeping/shredding bills/reused passwords/bad passwords – no. Is it homedepots bank – no. ….once again it is the middle ‘man’. The one part neither end of the transaction has control over. The fact that in order for me to pay HD and HD to get paid, they are forced to use a 3rd party solution. HD sucked at maintaining it or the solution had week security is beside the point. As the weak point simply does not exist if I pay HD in cash.
This is where I am seeing technology like bitcoin having true long-term value and potential. You remove the middle man, you pay the merchant directly without the need to keep someone else in the loop and keeping that loop secure.
I laugh when I see everyone so worried about this data breach. First of all I never use a debit card for purchases; I only use a credit card. You are 100% protected by Federal law against unauthorized charges. So what’s to worry about? If your card gets used by a fraudster, just call the credit card company and let them know about the unauthorized charges. They will remove them and send you a new card.
Sure, you are not directly responsible. But where do you think the banks recoup those costs from? To think that you are not paying for this at all is ignorant. All these costs are pushed down to the customer. I doubt that at the end of this year, despite the billions that will be lost due to these breaches you will see a single back have a loss on the books. Think about it.
@Brian: Could the fact that most Credit Cards in Canada are using Chip & Pin be the reason why this breach would be limited to US only Home Depot stores?
I don’t think there’s any question about that, Chriz.
It is more complicated than that. Chip and Pin does not require the encryption of the mag stripe card data. It can still be stolen and the card cloned for use in a non-Chip and pin transaction. Of course, that card couldn’t be used locally, which reduces its value on the market and the interest from the attackers.
Another factor in that depending on when a retailer implemented Chip and Pin, they may have had the opportunity to use P2PE (peer to peer encryption) to protect the card data in transit, and tokenization, to keep the card data out of the IT systems. This would prevent POS attacks from getting at the data.
So, if you’re an attacker, there is less incentive to bother with Canadian stores.
However, if you are a Canadian, it is still necessary to review all your charges to watch for fraud.
It would be great to allow the consumer to block all non-Chip and Pin/Signature transactions on their card, but it my limited reading, I haven’t seen anyone mention this. This would prevent online transactions, but one could have a different card for that. Banks will decide to block non-Chip transactions, so why not let users do that as well?
Mr. Hacker, while Chip & PIN still transmits the primary account number in the clear, the EMV standard uses a dynamic card valuation value (CVV) that is unique for that transaction. So duplicating an EMV card’s track data on a magnetic stripe would not work. Now in a card not present environment, the criminal would have the card number, name and expiration data, but if the merchant requested the CVV2 that would not be available.
So if my credit card had an EMV chip used with a PIN, this couldn’t be gotten on a POS hack?
If you performed an EMV transaction using Chip & PIN (Mastercard) or Chip & Signature (Visa) then the pan(Card #), expiration date, and additional service code data could be obtained but not the CVV # required to make a magstripe card that would function in Card Present Fraud. The dynamic CVV transmitted during an EMV transaction is for that transaction only. It is not the same as one transmitted via an EMV NFC transaction nor is it contained in the magstripe on an EMV card. It could be used for Card Not Present Fraud (ecommerce).
Just a point of clarification the dynamic CVV is not the CVV printed on the card either. The point I was trying to make is that some ecommerce vendors do not require this data so you only need a PAN and Expiration date. If you have the zip code too, as is the case in this breach , that also helps when performing ecommerce card not present fraud. That is quite possibly all you need. The hard part is how do you turn your fraudulent transactions into real money. That requires a great deal more effort than with Card Present fraud. Where you can immediately resell the goods.
@Shawn A Thank you. Much appreciate the explanation.
Which ecommerce retailers don’t require the CVV? That seems to defeat any CNP fraud where the data was obtained from skimming or POS data breach. Therefore, why would card companies allow CNP transactions without the CVV?
I use my card(s) online several times a month and cannot remember the last time someone asked for the CVV. Maybe it was Western Union.
I have always wondered why as a credit card industry they don’t switch to a more secure technolgy. Sure, costs etc, but after a while it seems like it’s more of an ethical & financial liability not too.
After so many breaches, you would think that the added costs could be justified. Maybe even offer it as an opt-in to consumers and start investing more into new infrastructure.
Perhaps the “industry leaders” lead here so that more secure credit cards are the norm. Thank you @BrianKrebs for always having insightful and thorough research to share with the world.
It’s relatively easy to upgrade the large retailers, but the costs to upgrade to new CC terminals is prohibitive for small retailers and restaurants. I can recall dining in restaurants that until recently were still using terminals and software that printed the full bankcard number on their receipts.
Of course independent retailers are a smaller prize for hackers. If they hack the local hardware store how many cards will they actually get for the amount of effort required? The national chains are literally where the money is, since they have central IT systems, networked throughout the country.
BTW, I’ve already upgraded to EMV compliant credit card terminals at my store.
The one time my CC number was stolen was because the entire number and expiry was printed on a receipt at a Denny’s restaurant. I remember looking down at the receipt as the cashier stuck it onto one of those receipt spike things, thinking “You could steal all these numbers if you wanted.”
A few days later, somebody bought $600 worth of jewelry from a TV shopping network that did not even bother to verify the address or zip code of the purchaser, even when that person gave an incomplete zip. Incredible.
Another good reason to avoid Denny’s. Did you learn your lesson?
“It’s relatively easy to upgrade the large retailers,”
Actually, it’s not.
There is the logistics of replacing a dozen or more terminals at thousands of stores, which can take months, if not more than a year.
And before they’re replaced, the software has to be tested against the dozens of applications with which it will interact to ensure that everything works as expected and nothing breaks.
And – assuming that there is some one or some group ensuring the security of the environment – it must be verified that this new configuration has no known vulnerabilities before it goes into production.
And this assumes that there are no other projects already in the pipeline which are taking time away from the staff. IT usually has several, conflicting priorities/projects that must be juggled during any given day.
And this assumes that everything goes as planned. If something fails in the testing process, it’s back to the drawing board and then yet another round of testing.
And then there are blackout periods. Most retailers are reluctant to make any changes during high volume periods like back-to-school or Christmas.
And if that’s not enough, retail is a low margin business, so there often isn’t much free cash to spare. When you have an extra dollar to spend, do you buy more advertising to keep people coming through the door, or new terminals that aren’t required?
> It’s relatively easy to upgrade the large retailers
Oh no it is NOT. Large retailers have a huge rewrite and certification process. I know people who worked on two large retail EMV conversions and both were multi-million dollar projects taking close to a year.
This is one of the few areas where some Mom & Pop stores may have it easier than the big boys for the first time ever! My friend’s dress shop’s conversion was the simplest possible. She has one POS register, off-the-shelf software, that has a cable to the pinpad. She swapped out her pinpad for an upgrade. Done in 1 minute.
Makes you wonder how the zip codes would correlate to Starbucks locations. There seems to be something missing from the story to connect this with Home Depot.
After looking at the list of Zip Codes published and matching the Zip of the Home Depot I have shopped at before, I can tell you with absolute certainty that there is NOT a Starbucks in that same ZIP. So your theory is bogus.
There’s at least three Starbucks in the 94901? Maybe–I got the question wrong?
Anyways, Home Depot has turned into a chit hole. Most of the items we have been conditioned to buy are cheaper elsewhere! I hope the disgruntled, internal
thiefs, slash —Employees burn down every Home Depot and use the zip codes
as reminders? Yes–I hate HD. I hate my picture taken on each isle! I hate the
rude Employees! Burn Baby burn!
&%#! I JUST changed my card in January thanks to the Target breach. Today I changed the card AGAIN. Thanks Home Depot. By the way HD, have you secured the breach yet? Thanks SO much for keeping us in the loop on that (directed at HD, not Brian, who seems to know a lot more than HD).
Dear Retailers of the World: Please secure your shiznit. We’re getting tired of this.
Izzy,
Replacing a card is really a very minor inconvenience since we started using a 2 card system. Get yourself two credit cards. Use one ONLY for your monthly re-occuring type bills that are automatically paid by CC. Make sure that this card NEVER leaves the house, is never used for online shopping, or for anything else for that matter. Then use the other card to carry with you for all your other purchases (including online). When that card gets compromised because you used it at Target, or HD, it’s no big deal to have it cancelled and a new one issued. There is no one to notify because that card is only used for ad hoc purchases. We’ve been doing this for over 10 years, and have never had the card kept at home compromised, but have had to replace the one we carry every day a few days, and it’s been a very easy transaction to do so.
Just a thought…
@Brian, Do you know if Home Depot, Target, UPS etc, utilize tokenization ?
Does this coincide with when Home Depot started upgrading their POS card terminals? I remember the stores in AZ all got new card readers early this summer. Possibility of an insider who was installing/supporting these new systems.
If summer is considered to starts in late April or early May in AZ, yes. If not, then No: “The banks I spoke with in reporting this story say the data they’re looking at suggests that the breach probably started in late April or early May.”
I doubt all Home Depot stores got upgraded card terminals at exactly the same time. The process likely took several months. Early June is merely when I noticed Phoenix, AZ stores being upgraded.
Five years ago, I was one of the contractors to install new timeclock systems in Phoenix area HDs, for employees to clock in-out. Each system only took a few hours to install, one per store. Those contracts were trickling in over a couple months. There’s probably about a dozen of the card terminals at each store. So unless HD had a real motive to move quickly, this upgrade would have been slower.
Great reporting as always Brian- very helpful. Thanks
@Brian, thanks for all the investigative work you do, really. I’m imagining a TV show for you on a major news network, “Krebs on Security” has a nice ring to it, lol;)
The custodians of the current pay by plastic infrastructure in the US are about to have their lunch eaten for them by Apple.
The disruption to this industry will be announced in Apple’s iPhone 6/ iWatch/ iRetail unveiling on Tuesday.
I failed to include that those that could have obsoleted the mag-strip/swipe/sign infrastructure by simply upgrading it to a chip+pin system have left themselves open to this disruption by 1. Hurting customer confidence in card-based POS transactions, and 2. Leaving this gap open to new entrants offering ground-up bolt-on holistic replacements (Apple) by not fixing this with a sense of urgency.
The first-mover opportunity to act and avoid disruption and decline almost always lies with the incumbent.
I just cross-checked your list of ZIP codes for the Reno, Nevada area, which is extremely easy in that there is only one Home Depot in all of those zips, and with the exclusion of store #3309 in Carson City (ZIP 89706), all of the stores in the Reno / Carson metro are listed. Here’s a quick reference:
Store # 3312 (Carson City “south”) – 89705
Store # 8560 (Reno / Damonte Ranch) – 89521
Store # 3313 (Spanish Springs) – 89436
The other stores crossed as well, ZIP 89801 is Elko, NV (and all of the zip codes above do have a Starbucks, in an answer to a previous question.)
When is this going to end? When are these companies going to get their act together and tighten security and get chips in cards like Europe has had for a while now? This is crazy, scary, etc. If our info and identity is stolen can we sue? Seriously, at this point I see all of this as GROSS NEGLIGENCE.
On the subject of security is there any way to take a commonly sold phone and add software to it to make it comparable to the ridiculously expensive Cryptophone 500 that was able to uncover the fake cell phone towers?
Anyone know whether they’re running the same POS as Target?
How is a site that is known to sell stolen cc data still up and running?
For the non-US folks amongst us, can you tell us how many unique zip codes there are across the US? I know you have ~1,900 HD related zip codes, but is this out of a total of 10,000 codes country wide or 2,200 or what?
It seems odd to me that there’s such a close correlation between the zip codes. I’m sure there must be people from different areas who shop in HD, so you would expect a broader spread – representative of the general population and not just representative of people who live near HD.
A simple Google search shows there are 41,742 ZIP codes in the U.S.
Use bitcoin already!
no
I remember years back, a batch of new POS were installed in England, which all had the sniffer built in directly from the factory ( if I remember correctly it was in China). The sniffer ONLY got active on certain card types ( gold-platinum whatever) and its GSM module sent the data to a location in Pakistan via SMS.
The only way to prevent CC fraud is to stop using plastic.
I’m always glad when Brian gets to report on these breaches, because he explains it so well to someone who knows little about the IT aspect.
How was the time of April or May identified?
Keep up the great reporting/investigating! 😉
I’ve noticed that the Home Depots around me all use the Ingenico iSC250, a fancy new payment terminal that lets you do things like pay with Paypal and get receipts emailed to you. I wonder if someone hacked it? Wouldn’t be surprised… I’ve not much seen the iSC250 used at other retailers.
Did you ever wonder why you can pay with PayPal? The CIO was the CTO of Ebay.
I agree with you, Weapons Master. Keep Jair safe while you’re at it please.
It is far more likely that the data was hacked from the cash register PC, network, or servers.
The case of the PINPAD hacked at the factory or on delivery and PINPAD racer aside, the actual PIN PADs are very secure in real life. The iSC250 has recent certifications for things like tamper resistance, PIN encryption, and code signing under a standard called PTS (there is a list online somewhere). Messing with terminals tends to disable them.
The transition to devices encrypting all the data is growing but goes slowly. There are lots of reasons for this; however, one is that many retailers actually want the card data for analytics.
This is worse news that it initially sounds. Since Home Depot is a business whose customers are typically other businesses, that means the cards collected have a very high likelihood of being business cards.
Per Clark Howard (http://www.clarkhoward.com/news/clarkhoward/business-entrepreneurs/why-entrepreneurs-should-avoid-business-credit-car/nFM2):
“And what happens when you lose a business card or it gets stolen? The liability of a small business can be unlimited under current law. Contrast that to the fact that an individual’s liability on a stolen or lost personal card is capped at a maximum of $50.”
Unlimited.
Why is it assumed/implied that this is the result of a POS hack? If cards from virtually every store have been released, it would seem to me more likely that a central database was hacked — more likely than POS malware being successfully distributed across >99.5% of their stores.
I understand some data (CVV, full track data, encrypted tracks) should never be stored by merchants or processors — but that doesn’t mean it couldn’t have happened.
Should you ask why jeff Mitchell the supposed Sr. Director of security at Home Depot and self proclaimed CISO, why was he fired from Lowe’s as the Sr. Director of Security. Also why did he outsource security to fishnet to a friend and how much did he make by doing this?
It’s not the first hack on his watch in three years, look deep into this. There were others not reported and hide from the public. Not long ago they had someone internally crediting credit cards, hacked into the system, Nothing done by security to fix it.
Jeff Mitchell pulled all business from vendors and gave to Cisco, that’s the first issue with security, then outsourcing jobs to Fishnet was the second. Same thing he did at Lowe’s and got fired from there for security problems.
The hiring of Symantec and Fishnet to investigate the breach indicates the Home Depot management still have no clue.
Some interesting discussion here concerning Home Depot IT security operation http://www.bradreese.com/blog/8-20-2013.htm
No wonder it’s taking so long to do the forensics!
Fishnet – Possibly not the best choice here.
I’m disturbed by the staggering number of card numbers that were stolen and available for sale from Home Depot. It indicates to me that they don’t have a clue in allowing this to happen.
At my bank whenever I make a bill payment from my account the next day I get an email confirming it. Why can’t card companies offer the same service for their credit cards when a card is used? Any legitimate transaction is still fresh in your mind and it would cut down on the value of stolen cards.
I wonder: Did this hack affect self checkout too or did the hackers get a common back end database?
Is there any detail on what end-point protections have been in place in Target, Home Depot, PF Changes etc.. Are they using traditional AV/HIPS systems, Application Whitelisting apps etc? It seems to me the P2PE/Tokenization would have completely prevented the breaches in all of these cases.
A big part of the problem is that people do not want to pay for more secure systems. That is from the consumer, to IT, to the members of the Board. It is all about the bottom line. They want cheap, easy, and secure. Guess what? Those three cannot happen at the same time. Pick two and the other one almost vanishes.
Pin and chip is a good advancement but it has not been pushed here until recently due to greed – and I am including the credit card companies in the greed comment. It was better on the bottom line to eat the fraud vs update all of the credit cards and payment systems. The new pin & chip cards cost more and require replacing the swipe terminals. Remember, it was cheap and easy because it had not been updated in…oh, a decade or so. Awesome for the bottom line, horrible for security.
While I cannot comment on HDs situation, if people think it is simply an IT Security issue then they are blindly ignorant. It is a mindset issue and IT Security cannot do a thing until the company, the Board, and its customers are ready and demanding it.
JB is 10000000 % correct. These companies dont EVER think theyll be hacked. So theyd rather not spend money on security and hope and pray it never happens. The real problem is that since they are so large and process so much $$$$$ that Visa , Mastercard, discover and AMEX dont penalize them. They just fine them and slap their wrist. If you owned a small business and had just a small percentage of fraud processed in 1 month theyll close your account. No one wants to buy a alarm until their stuff is stolen.
Why not shut down Rescator.cc?
Generally speaking, for now, as you see:
Law enforcement can be very slow on certain international internet crime. I haven’t heard of Russia cooperating on this matter. The U.S. Federal judicial system is perhaps grinding through it very slowly from a website shutdown standpoint (I suspect quite likely a case is being put together at the Federal level since it’s a case involving international crime). The U.S. Federal prosecutors I’ve only seen release details of a case once a case is presented to a court.
The registrar of the domain, Regtime Ltd–Russia, allows it for the registrant. The network host, Cloudflare Inc–U.S, allows it. http://whois.domaintools.com/rescator.cc
Concerns could be sent to the associates in that direction (Cloudflare Inc/U.S. court system).
How many cards in the dump that are non-US based?