Banks in Europe are warning about the emergence of a rare, virtually invisible form of ATM skimmer involving a so-called “wiretapping” device that is inserted through a tiny hole cut in the cash machine’s front. The hole is covered up by a fake decal, and the thieves then use custom-made equipment to attach the device to ATM’s internal card reader.
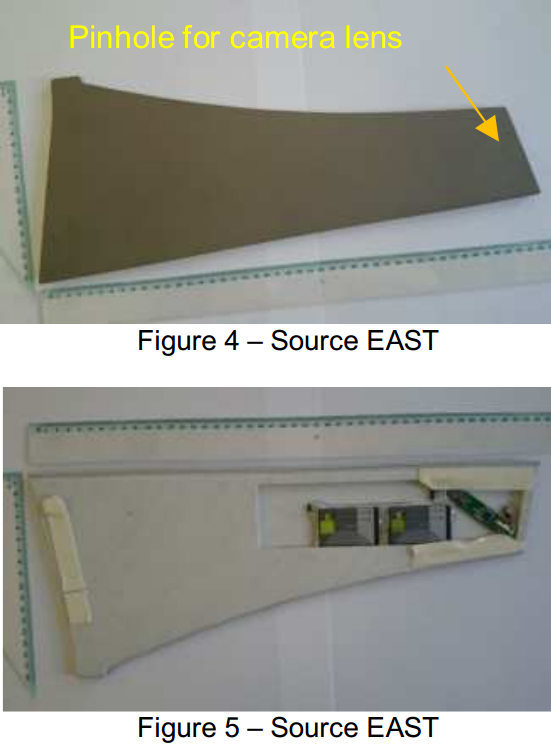
According to the European ATM Security Team (EAST), a nonprofit that represents banks in 29 countries, financial institutions in two countries recently reported ATM attacks in which the card data was compromised internally by “wire-tapping” or “eavesdropping” on the customer transaction. The image below shows some criminal equipment used to perpetrate these eavesdropping attacks.
“The criminals cut a hole in the fascia around the card reader where the decal is situated,” EAST described in a recent, non-public report. “A device is then inserted and connected internally onto the card reader, and the hole covered with a fake decal”
[pictured, bottom right].
Pictured above are what appear to be wires that are fed into the machine with some custom-made rods. It looks like the data is collected by removing the decal, fishing out the wire attached to the ATM’s card reader, and connecting it to a handheld data storage device.
I sought clarification from EAST about how the device works. Most skimmers are card slot overlay devices that work by using a built-in component which reads the account data off of the magnetic stripe when the customer inserts the card. But Lachlan Gunn, EAST’s executive director, suggested that this device intercepts the card data from the legitimate card reader on the inside of the ATM. He described the wiretapping device this way:
“It’s where a tap is attached to the pre-read head or read head of the card reader,” Lachlan said. “The card data is then read through the tap. We still classify it as skimming, but technically the magnetic stripe [on the customer/victim’s card] is not directly skimmed as the data is intercepted.”
The last report in my ATM skimming series showcased some major innovations in so-called “insert skimmers,” card-skimming devices made to fix snugly and invisibly inside the throat of the card acceptance slot. EAST’s new report includes another, slightly more advanced, insert skimmer that’s being called an “insert transmitter skimmer.”
Like the one pictured below, an insert transmitter skimmer is made up of two steel plates and an internal battery that lasts approximately one to two weeks. “They do not store data, but transmit it directly to a receiving device — probably placed less than 1 meter from the ATM.
Both of these card skimming technologies rely on hidden cameras to steal customer PIN codes. In a typical skimming attack involving devices that lay directly on top of the card acceptance slot, the hidden camera is a pinhole spy cam that is embedded inside the card slot overlay and angled toward the PIN pad. Just as often, the camera is hidden in a false panel affixed directly above the PIN pan with the pinhole pointed downward.
According to east, the use of false sidebar panels is becoming more prevalent (see image below for an example). It is not unusual for hidden cameras to be obscured inside of phony brochure racks as well.
As this and other insert skimmer attacks show, it’s getting tougher to spot ATM skimming devices. It’s best to focus instead on protecting your own physical security while at the cash machine. If you visit an ATM that looks strange, tampered with, or out of place, try to find another ATM. Use only machines in public, well-lit areas, and avoid ATMs in secluded spots.
Last, but certainly not least, cover the PIN pad with your hand when entering your PIN: That way, if even if the thieves somehow skim your card, there is less chance that they will be able to snag your PIN as well. You’d be amazed at how many people fail to take this basic precaution. Yes, there is still a chance that thieves could use a PIN-pad overlay device to capture your PIN, but in my experience these are far less common than hidden cameras (and quite a bit more costly for thieves who aren’t making their own skimmers).






Where are these ATMS physically located that someone can spend time physically tinkering with it and no one noticing?
It probably happens late at night, and the ‘perps’ probably park a large vehicle in front of the ATM to help hide their actions. If several people are involved, it would probably just look like 2-3 people standing around an ATM having a smoke or whatever.
And what about the atm security camera? Even if the thieves wore masks the camera would still show tampering and suspicious activity so one would think the atm should be inspected after such an event. Is it possible the tampering is ocurring at the place of manufacture?
ATM video? Probably only viewed once a problem is discovered. Let’s say that an ATM gets re-filled once a week, and the thieves hit the same day as the refill – that’s 7 days of video to review.
Now, possibly the logs on the machine might narrow the timeframe, but if they are relying on the video, they might have to check as many as, what, 168 hours of video, assuming that one week interval? I’m not suggesting it isn’t done, just pointing out that it takes quite a lot of time, and gives the thief plenty of time to disappear – assuming they didn’t use some patsy to do the actual work…
yeah……….There is not much help monitoring ATM cameras before the fact. Typically they have to try and figure out if the ATM threw a fault when this stuff was added to the ATM, and then, maybe, match it up to a date and time they can review – IF the camera data is still available. Even if you get some footage of these crooks, it may not be the best quality and show enough recognizable features to make a positive ID.
ID’ing these crooks is not as easy as it seems.
Last ultimate antiskimming defence. The activedge by Diebold. First card reader acepting cards by long edge. It defeats every current skimer.
The reality is often there literally is no recording going on in many ATM machines. Some of course are maintained by companies with security managers who do record 24/7, but some companies that own them, or even some banks themselves have no recording at all occurring. There are even some models of ATMs found in shopping malls and convenience stores that have no recording capability at all.
Thanks for the reporting, Brian. You’re blog is eye-opening to say the least. Now when I go to an ATM, I take a moment and tug, push, pull, and jiggle the pinpad and the guides around the card reader. When I pump gas, I look for signs of tampering, and run my card as credit, so I don’t have to enter my PIN. I keep up on my password discipline and pay attention to my financial transactions. Its sad that this is the level of paranoia that is required to keep yourself safe in this day and age…
Eric: paranoia is “unreasoning” fear.
You, me, and a few millions of other people have good reason to be fearful. Sadly we are outnumbered by many more millions of humans emulating some ostrich behavior.
Jonathan @nc3mobi
It occurs to me that these criminals HAVE to have access to a ‘practice ATM’. They aren’t figuring this out on the fly – and the tools that they bring with them are specific to this one task.
There’s probably a ‘skimmer shop’ operating out of a warehouse somewhere where they have a number of ATMs that they can practice on, and get good at doing this quickly and efficiently.
LE should be looking for someone with a pattern of obtaining ATMs that doesn’t work for a bank.
Agreed on practice units.
I would recommend that the networks look for devices that are either off line or online but not showing transactions as the posdible give away that they were out of service for experiments.
I would also look for the kinds of businesses that might have this possibility like convenience stores or liquor stores.
Eric,
Banks are hardly the only people who buy ATM machines. Anyone can buy an ATM and put it in their place of business or enter into business agreements to place ATMs in small businesses, events, etc.
Arthroscopic surgery for ATMs to implant a monitoring chip-mounted device…both devious and clever.
It’s worth noting that users should protect against leaving a thermal signature on the keypad as well: https://www.youtube.com/watch?v=8Vc-69M-UWk
That’s hilarious. That attack is not practical nor does it scale. FUD.
For criminals interested in bulk theft of PIN numbers, yes it isn’t practical.
But for things like door entry systems, it could be a practical way to deduce the entry code.
First, the skimmer wouldn’t know the sequence, thus, limiting the risks, especially with a 5-digit code where your card will be blocked after 3 failed attempts.
Second, the guy in the video hits accidentally the key “8” but it still shows as cold-blue in the thermal imagery.
Third, the couch is made up of leather and requires a good amount of sitting to transfer the heat while using the pin pad is a quick hit & release action, lowering the risk of having heat transferred to the pad. The heat should dissipate quite fast after the action.
I’m not saying it’s impractical, but that wouldn’t be very effective as the thief needs to be at the same place as the victim, which would quickly show up as a pattern after the police studies the footages of the recordings. (“Who’s this guy coming after each victim…?”)
Maybe we should wear padded gloves… 😛
Off topic, but — I am thoroughly enjoying SPAM NATION. I’m about 2/3rds through. I have given two copies as gifts. Thanks for the Zeus hardware browser, which I’ll try this weekend.
I read with interest your (perfectly reasonable) discussion of editorial conflicts and your separation from The Washington Post. If you wrote about that before, I missed it. And to think, in your WaPo blog and your great chats you used to teach people like me how to create limited user accounts in Windows XP. Best regards.
So long as you have a reason for being where you are; such as a cleaning service – nobody will notice you or look at you, love Spam Nation, Thanks Brian
Any information on a specific make/model of machine targeted?
Very clever way of skimming ATM data. You would think that the ATM machines would have some type of anti-tamper devices that would shut down the machine if it detected this type of “wire tapping”
I agree. ATM seem like way behind these days, technologically speaking. No anti-tampering devices?
I’d wager some number cruncher computed the cost of anti tamper for 100% of the machines vs compromise for a much smaller percent of machines.
A simple (also cheap) anti-tamper system is already in bank vaults. The exposed metal external shell has a wire connected to it. Just inside, installed with insulated stand offs, is another metal shell. When the shaft of the drill is in contact with both you get a completed circuit which should activate a silent alarm. Unless you have a non-conducting drill strong enough to cut through the metal shells this is effective and efficient.
There is another design with a glass sheet that breaks when drilled, but many ATMs are exposed to the weather and glass might break just from temperature variations and vibration.
Jonathan @nc3mobi
Nice choice of name Ross…
I wonder how expensive it would be to make this scam obsolete.
One idea I just had is proximity sensor (every phone has one) + atm activity monitor, if someone is withing 3 feet of the atm and no action is taken for more than 60 seconds (i.e. no card was inserted), an alert goes to the bank/store manager and they can quickly view video of the suspected time.
(if a backup repeatedly inserts a card while someone works on the tampering, it should set off an alert as well. .)
Another alternative, is a steel housing for the entire card reading apparatus (with the exact card with for the slot height). before any data leaves the housing it is already encrypted.
I assume this already exists in some form. .
The simplest approach is to move all ATMs into buildings w/ live human monitors.
That won’t happen. It doesn’t scale.
I wonder if people remember when car alarms were first introduced. And kids had fun throwing frisbees at them.
The problem with most approaches to securing these things is roughly the same as the reason that Reagan’s Star Wars effort was doomed to failure: it’s too easy to exhaust the defenders (who are defending too many targets — you can just shoot lots and lots of drones/false alarms). It’s also how we got the story of “The Boy Who Cried Wolf”.
To borrow from War Games, the lesson that Joshua learned: “A strange game. The only winning move is not to play.”
What would that look like here?
We switch to Chip/NFC where you never actually present any useful data to the other terminal. Making the terminals dumber (and more transparent) — basically a dumb pipe between the Card and the bank with the card/bank doing the encryption at their ends.
We could even go w/ the US chip (or NFC) approach where most transactions don’t involve a PIN.
—
The other thing that will help is a system where more people are able to pay eachother w/o actually using cash. In the US, there was a short surge in this w/ Square. But Square’s main business model is based on magstripe, which we’re all hoping will die yesterday.
Some countries (Canada, Finland) have banking networks that allow people to send money to each-other. But personally, I’ve found most of them have a rather high service charge (Interac e-Transfer is $1.50/transaction). PayPal also allows it, but I think at this point the adoption rate for PayPal may have stalled.
Ah, yes, let’s remove the physical connection and move to a wireless one for security. I mean, it’s not as though anyone within range could just record every last bit of data sent over that wireless connection then brute force the encryption on the recorded conversation.
Please tell me you’re joking…
Removing the PIN to “increase” security?
you do realize this is why carding “works”, right? all they need is a copy of your card, and without a PIN your money is gone and some guy has a few expensive handbags to sell on eBay.
If EMV is fully implemented in Europe, the card data would only be useful in the US or are they successfully circumventing EMV and using the card data in Europe?
If the ATMs were EMV then the data can’t be used anywhere other than internet transactions not requiring CVC2/CVV2 authentication.
Soon this Wiretapping technique will “arrive” in my country (In Asia). LOL… 🙂
Another practice I take into personal action is to try and use a single ATM as often as possible. This reduces your chances of exposure and in the event something does happen you can more easily narrow it down to the when/where. It can be slightly less convenient, but IMO it’s worth it for the few times I’ve needed cash and didn’t have it handy (maybe once in the past year…?).
Correct! I’d also add to limit the use of our debit card. Instead of using it for every purchase or to withdraw a small amount of cash, withdraw a bigger amount to cover your cash expenses for a few weeks, thus limiting your visit to the ATM.
I know, this isn’t a practical solution for those living paycheck to paycheck…
Now the theft of ATM starts to look suspeious. One stolen from a gas station overnight. I wonder if the folks needed an type of atm available here? Just a thought.
ok so they skim an EMV transaction and get PIN. Then what? Not much they can do with that data. They could do some card not present fraud as long as the merchant doesn’t require CVC2/CVV2. Why even bother steal the PIN, it’s not like they would be able to use it.
Or are we saying they are able to use the stolen data to create fake chip transactions with valid ARQC?
ATMs use PINs for magstripe transactions to authorize cash withdrawals, or account transfers.
If you capture the magstripe and PIN, you can make another card with the same magstripe data and then go to another ATM, use the captured PIN and withdraw all available funds from the account.
There’s no need to make purchases and resell products at a markdown in order to “cash out”, you can skip ahead and literally “cash out”.
I understood that this was happening in Europe, aren’t all ATMs chip enabled now?
Just because most (or even all) ATMs may be chip enabled doesn’t mean that all cards are chip enabled. Oddly, cards are mobile — people take them when they travel.
In theory there are some replay attacks for EMV, but I’d assume this is just a fancier attack on the magstripe data.
These guys still aren’t doing what the kid in Terminator 2 managed. I always wanted his little ‘withdrawal machine’.
I never liked to be the bearing of bad news, but what Brian states in his article is currently happening where I am located at. I have recently investigated where 4 ATMs have been forced opened. After opening the ATM’s they cover the camera or sometimes don’t bother. They have disconnected the power cords from the card reader and the other wires. I still have not figured out what they are really trying to do. The suspects have done this to the same manufacture. I believe that are trying to hook up directly to the card reader and they are looking for a power supply.
Is there no alarm when an atm is forced open?!
I might prefer that a 50,000-volt discharge would be triggered (if not properly disabled), rather than an alarm that won’t bring a security response in nearly enough time….
Hummm if this is done at like 0300-0400 in the AM when no one else is around, even if there was an alarm, it probably wouldnt matter. The crooks would rip it out immediately.
Some ATM’s are quite old, and the thinking back then simply didnt involve these brash physical attacks.
All ATM’s should have a photo electric eye randomly located inside, and upon light of any type, simply kick the ATM off line. It would protect the customers that use the ATM, and alert staff that the ATM is down.
Or simply do what I do for the Holiday Season. Go inside the bank, draw out a wad of cash and put it in a safe place. Pay for all purchases with cash, and avoid the dreaded breach letters that may come this year.
I’ve found a few devices that look like this on 7 different gas pumps around my region. It appears that the devices they are using for the gas pumps have the normal connections to allow the gas pump to continue to work, but the transaction is being rerouted through a bluetooth device. This way they are able to use the gas pumps own PIN pad and Card Reader without having to attach a skimmer or camera. It is really unprecedented and because of this they are able to leave these skimmers on for extended amounts of time. The longest we could determine that a device was on a gas pump was for almost 9 months. I’m hoping this is not going to be a new trend in the USA, but we’ve been seeing them for about 9 months. Seeing the images you’ve posted remind exactly of what those skimmer look like.
The Vi – Salus is not in the run ofpublicity like the other health products that excites the people and ready togo, but that die away in few weeks because they are physically very difficult tokeep up.
Food being part of the physiologic needs of people should be taken with some sort of discipline.
What is fascinating is that their shakes actually works
and delivers some wonderful results.
re physical security/theft practice – pretty sure that the ATM security standards require ‘accounting’ for ATM’s – owners of ATM’s are required to control them, both when in use and when in storage/offline etc, precisely to reduce this type of opportunity for thieves to practice.
Sounds like they could learn from the auto-theft industry, where criminals would hire new luxury cars to allow them time to practice new theft techniques.
In terms of solutions, pressure needs to be applied to the ATM vendors to build more secure units – they will only do this if they ‘need’ to – market forces should be applied. As any one bank will typically have multiple ATM’s in their estate, it’s relatively hard for them to drive improved standards.
Question: anyone know who is responsible for ATM ‘secure design’ – is there an industry group? do they have acknowledged standards? are these open (or are they relying on that old, and proven-unreliable approach, of ‘security by obscurity’)
Is there a good chance there is a company who supplies modded ATM’s to shady stores? The stores could easily claim ignorance and simply say the person they bought the ATM was the most affordable. I can see small business owners doing this. I’ve often thought a good bit of the skimmer found were installed by employees and/or owners of the location where the skimmers are found. It just seems like a smoother ans safer shady biz model than trying to distract people from you messing with an ATM no matter the time of day.
I seriously think there are some shady business owners to blame.
Also I agree with the practice machines. Hell they probably have chop shops for ATM’s too. Reselling ATM “modded” to the buyers delight. Seller/Buyer splits the profit, etc…
People put too much trust in a business just because it’s a legit business. I know of a Gas Station local that had/has skimmers and I would not put it past the owners to be behind them.
There should be a timer for “activity” directly within two feet of the ATM, specifically if there’s no ATM usage. It should sense depth and movement. If it senses an above average time of use that time should be marked for review. An above average time should be calculated and adjusted via algorithm based on month day (thursday, friday, sat, 1st, 3rd, etc.) and year (season, IE christmas/thanksgiving time possible longer). After branch hours and stand alone ATMs should be targeted more fully.
It seems that at least part of the problem could be helped if the card reader device was shielded with very hardened steel or other very hard metal. As the parts are fairly small this shouldn’t add too much to the cost.
I remember a case many years back, where a batch of POS arrived fresh from the factory in China to the UK, with a GSM module already built in. The GSM Module activated itself when ONLY gold or platinum cards were inserted and sent off the bulk dump via SMS to a cellphone number in Lahore Pakistan.
Here is what happened in Asia last summer:
http://www.financetwitter.com/2014/09/here-is-how-malaysian-atms-were-hacked-of-rm3-million-by-latin-americans.html
IMO the “latin americans” were carpatian gophers 😉