My inbox has been flooded of late with pitches for new technologies aimed at making credit cards safer and more secure. Many of these solutions are exceedingly complex and overwrought — if well-intentioned — responses to a problem that we already know how to solve. Here’s a look at a few of the more elaborate approaches.
Some of these ideas may have benefited from additional research into where financial institutions actually experience most of their fraud losses. Hint: Lost-and-stolen fraud is minuscule compared to losses from other types of fraud, such as counterfeit cards and online fraud. Case in point: A new product called Safe Swipe. From their pitch:
“The basic premise of our solution, Safe Swipe…is a technology which ‘marries’ your smart mobile device, phone, tablet and or computer to your credit/debit card(s). We’ve developed a Geo-Locator software program which triangulates your location with the POS device and your mobile phone so that if your phone and credit card are not within a certain predetermined range of one another the purchase would be challenged. In addition, we incorporated an ON/OFF type switch where you can ‘Lock Down’ your credit/debit card from your mobile device making it useless should it ever be stolen.”
The truth is that you can “lock down” your credit card if it’s lost or stolen by calling your credit card company and reporting it as such. Along these lines, I received multiple pitches from the folks who dreamed up a product/service called “Siren Swipe.” Check it out:
“The SIREN SWIPE system immediately notifies local police (via the local 911 center) of a thief’s location (ie merchant address) once heswipes a card that has already been reported stolen,” the folks at this company said in an email pitch to KrebsOnSecurity. “SIREN SWIPE has the potential to drastically impact the credit card fraud landscape because although card credentials being stolen is a forgone conclusion, which cards thieves decide to actually use is not. For a thief browsing a site like Rescator, the knowledge that using certain banks’ cards could result in an immediate police response can make thieves avoid using these banks’ stolen cards over and over again. And in the best case scenario, a carder site admin could just decide not to sell subscribing banks’ cards in the interest of customer service.”
The sad truth is that, for the most part, cops generally have more important things to do than chase around the street urchins who end up using stolen credit and debit cards, and they’re not going to turn on the dome lights and siren over something like this. Also, the signals for fraud are all backwards here: The fraudsters know to use criminal card-checking services before buying and/or using stolen cards, so they don’t generally end up using a pile of cards that have already been cancelled.
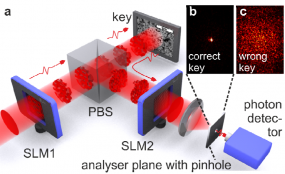
My favorite overwrought solution to making credit cards more secure comes from researchers in the Netherlands, who recently put out a paper announcing a card security idea they’re calling Quantum-Secure Authentication. According to its creators, this approach relies on “the unique quantum properties of light to create a secure question-and-answer exchange that cannot be spoofed or copied. From their literature:
“Traditional magnetic-stripe-only cards are relatively simple to use but simple to copy. Recently, banks have begun issuing so-called ‘smart cards’ that include a microprocessor chip to authenticate, identify & enhance security. But regardless of how complex the code or how many layers of security, the problem remains that an attacker who obtains the information stored inside the card can copy or emulate it. The new approach…avoids this risk entirely by using the peculiar quantum properties of photons that allow them to be in multiple locations at the same time to convey the authentication questions & answers. Though difficult to reconcile with our everyday experiences, this strange property of light can create a fraud-proof Q&A exchange, like those used to authorize credit card transactions.”
The main reason so many of these newfangled technologies are even being proposed is that the United States lags 20 years behind Europe and the rest of the world in adopting chip/smartcard technology in credit and debit cards. This is starting to change on both the card-issuing side (the banks) and the merchant side. Most of the biggest banks are already issuing chip cards, with smaller institutions following suit next year. In October 2015, merchants that haven’t yet installed card swipe terminals that accept chip cards will be liable for all of the fraud costs on any fraudulent transaction involving a chip card.
It’s unclear how much appetite there is for new technology to help banks fight card fraud, when so many financial institutions have yet to roll out chip cards. A payments fraud survey released this week by the Federal Reserve Bank of Minneapolis found that “high percentages of surveyed financial institutions report that fraud prevention costs exceed actual losses for many types of payments, especially wire, cash, and ACH payments. This trend is even more striking for non-financial respondents. In every payment category, a higher percentage of such firms responded that prevention costs exceed fraud losses.”
The Fed survey (PDF), which quizzed both banks and corporations, found that about half of the financial institutions that experienced payment fraud losses reported increases in those losses, while three quarters of the non-financial firms responded that loss rates had remained about the same over the prior year.
“In keeping with previous surveys, signature debit transactions are the payment type cited by the largest number of financial institutions as accounting for high levels of payments fraud losses (92% of financial service companies), while checks are cited by 75% of non-financial companies,” the Fed concluded. “While this finding could suggest that companies are overcompensating in prevention vis-à-vis likely losses, it is also possible that risk mitigation strategies and fraud prevention investments have indeed been effective.”





My plan is far more secure. Each credit card is issued with its own laser-equipped satellite. Whenever fraud is detected the satellite blasts the perpetrator with a razor-thin beam that etches the word “thief” on his forehead in 27 different languages. Using advanced optics, if the system sees that the person has already been branded then the next laser session fries him into bio-friendly ash that can be sprinkled on crops or high end lattes, imparting an extra zing. In addition, the reflected light from all the satellites will create so much ambient light that we’ll save trillions on street lamps and eliminate conspiracy theories about why the lamps go off when you walk past. This is fool proof.
+1 on this
Sirk – Your evil plan sounds excellent. It sounds like you may actually be Dr Evil. BTW, Number 1 corrects you that its “millions”, not “trillions”.
I think mozilla could help out in this. we could bump the number of languages from 27 to 80+ pretty easy.
We may need extended font support in the laser etching system. Who can help with that?
I feel like I should have thought of that.
I don’t want no laser fried street urchin on my latte. You’ll need to consult with Starbucks before implementing this plan.
@Bob in MA
Will update the spreadsheet to indicate you dislike zing. You’re now considered suspicious.
Sirk’s plan is not foolproof, but easily defeated by something every CC-stealing thug possesses — a hoodie.
@boris the spider
Um, I did say ADVANCED optics. As long as they don’t wear a tin foil hat the plan is safe.
I never knew I was a credit card stealing thug.
The things you find out after you’ve been wearing a hoodie for years.
LOL!!!
You sir, win the Internet today. Well, technically yesterday, but you get the idea
I love this.
Services like ” Safe Swipe” should be built into the bank card in the first place and people shouldn’t have to rely on a third party services to protect their credit cards from abuse if stolen
Hi Brian
This part does not make sense:
“In October 2015, merchants that haven’t yet installed card swipe terminals that accept chip cards will be liable for all of the fraud costs on any fraudulent transaction involving a chip card.”
Shouldn’t that read ‘magstripe cards’ at the end of the sentence?
I correct myself, the new chip cards probably still have a magstripe. So they will be liable for any fraudulent transaction where the magstripe was used instead of the chip?
It is my understanding that it is the person with the least security who will bear the brunt of the fraud. Thus, if a bank offers chip and pin, but the merchant only has the ability to do magstripe, the merchant would be considered the lesser security and thus bear the burden of the cost of the fraud.
It works like this:
Retailer doesnt accept Chip cards, retailer is liable for fraud.
Bank doesnt issue Chip cards, bank is liable for fraud.
Etc.
Chip / PIN cards will still contain a magstripe, which also means the addition of chip cards will mean little to fraud – /most/ retailers are going to setup terminals to default back to magstripe if the chip is broken, which means you can still easily clone cards; until magstripe is GONE from the market, the same fraud will exist (and fraud skyrockets for online purchases once chip cards are implemented.) Not to mention most banks will issue chip & signature, not chip & PIN, also negating the possible benefits.
I said this in an article on the Quantum Secure solution, but it applies to all of them: Not a single aspect of these proposals can address card-not-present transactions. They could be good in cases of either physically stolen cards, or cloned ones, but the best case scenario for any of those pitches is that it’ll drive fraudsters and other criminals towards online CNP fraud.
Don’t get me wrong; it’d be great to put a stop to clonings. But I’m yet to be convinced any of these pitches would be proof against such fraud. The first two in particular are laughable due to tons of presumptions of user activity and/or police response, and the last is giggle-worthy for thinking that, even if the tech turned out to be robust enough to survive everyday life – something not even attempted to be proven – that banks would shell out for it.
Interesting intellectual exercises, those. But far from failsafe or even reliable.
That may be true, but I do not believe that there is one single solution that will address all of the different use cases.
Eric- You are right in that there are a lot of reasonable solutions that address the problem of last century, card-present crime.
There has been a single solution that addresses all forms of commerce including physical presence (card present), electronic presence (using a computer), mobile presence (not using the internet), person-too-person and even non-presence (think of paying a paper invoice). The problem is that laser-etching-from-space gets more press. See http://www.NC3.mobi and start with 10 slides at the bottom.
Jonathan @nc3mobi
should be “person-to-person”
dangnabbbit @#!(&! damaged eyeballs!
Jonathan @nc3mobi
“…and the last is giggle-worthy for thinking that, even if the tech turned out to be robust enough to survive everyday life – something not even attempted to be proven…”
That is also my layman’s understanding of this – we aren’t at the point of even being able to transmit 1 bit reliably so wth they are selling I do not know.
Happy to be corrected of course 😉
“it’d be great to put a stop to clonings.”
Chip & PIN/Signature already does that, so no need to go to quantum technology. Despite 20 years of trying thieves have failed to succeede cloning these chip-based cards.
Closest they got was hacking into the payment machines and doing replay attacks using gaps in the issuing bank/payment provider servers checking the actual transactions.
Online theft is a completly different beast. Cards swiped and cloned – even today – are not useful for online theft as they lack the code on the back of the card. As such online theft involves hacking the online company so one gets access to both the number and that infamous code.
Some people claim there are mythical online companies that don’t require the code on the back. I’ve not seen these (both in US and outside) in over 10 years, but if they do exist they’ll quickly die out being swamped by all fraudulent cards going to them I expect.
So in essence, once moved to chip-based cards we are safe from cloning and as such hacks like Target/HomeDepot will become much less atractive, as – at least for now – any ram-scraped or swiped-stolen data there cannot be used to create a fake/cloned physical card. Experience in Europe showed this branch of theft completely disapearing to levels literally close to zero. The only exception being the point in case, that cards where still stolen there to clone and use in the USA and handfull of other countries that as that continued using non-PIN. Some EU banks have simply started to block non-EU debitcard usage (with option to unblock for users) to successfully eliminate that final branch.
So my point here being that, the real problem to be solved is the online theft. Any solution that tries to address physical card fraud, is addressing the wrong problem. That problem is mostly solved. The real issue is online fraude.
Possibly if your card has a chip, a chip-enabled terminal won’t allow the mag stripe to be used?
I ran into this at our local arena box office last week. The clerk tried to swipe my chipped American Express, but it threw some kind of error. She had to call a supervisor over to show her how to process using the chip.
This is a per retailer setting. Essentially you program the card reader for multiple scenarios, and most retailers will be forcing chip first (if available) but fail back to magstripe, although that /can/ be turned off.
@Mark
Correct. Chip terminals will prefer the chip. If there are (enough) errors it often allows fall back to the stripe.
Personally, I don’t let clerks touch my card (see is different but it stays in my hand). I swipe, tap, dip, whatever. I can’t recall being refused. A few have pushed back but caved when I suggested they get a manager and explain why I will be abandoning my purchase.
You do realize that you’re ony protecting yourself against possible actions of the individual that your dealing with at the time. You are still vulnerable to every attack on the rest of the process, from the terminal all of the way to the issuing bank.
In talking to my contacts, I think most institutions are planning to roll out the chip. Also, the Fed report I think misses the intangible cost of reputation risk and benefits of fraud avoided when it states ““high percentages of surveyed financial institutions report that fraud prevention costs exceed actual losses for many types of payments, especially wire, cash, and ACH payments.”
The fact that fraud costs less than fraud prevention means that the cost of fraud is not high enough.
The costs get pushed to customers, who have to deal with getting new credit cards, closely checking their credit card statements each month, checking the “free” credit monitoring that the compromised merchant or issuer provides, and dealing with problems with their credit rating.
If compromised companies had to pay the credit card holders $100 for each compromised account instead of providing useless credit monitoring, they would have more appropriate incentive to make sure the fraud or compromise didn’t occur in the first place.
No sneer, but I’m not sure how good the service for your creditcard company is, but if your company provides good service, I fail to see the hassle and risk?
I either call them or in online banking click “dispute transaction” or similar wording. No hassle, transaction blocked, card blocked and within a few days I have a new card. I also never had any issues convincing them a transaction was fraudulent. Often these are also pretty obvious in my experience.
So credit scores being affected seems – sorry – nonsense. Credit score is depending on you paying your bill on time. So unless your card company asks you to pay charges that you disputed, I don’t see that happening? And if they do, there are zillions of other banks to offer one cards.
Debitcards is a different issue though. Since that goes from your checking, lots of bad stuff can happen. So I’m not using these other than ATM and then only ATM’s inside banks. Not the outside ones.
But creditcards are from consumer point of view pretty safe and hassle free. At least in the US, where the law protects users. Outside the US laws allow banks in soem countries to be less friendly …
Overly complex is a polite way of describing some of these. At first blush, one of them even gets my snake oil senses all a quiver. Anyone investing in any of these or looking to actually implement them should probably do some due diligence and TCO analysis.
Folks should remember that even if someone has a better idea they need to get buy in and traction before it actually gets used. Selling to the consumer who has no liability would seem inefficient and misguided. Signing up processors and card brands is a long game.
Yay, more BS solutions when we HAVE the solutions to stop the majority of fraud. Between tokenization and E2E encryption, you can almost wipe out fraud that is based on breaches. THAT is what we should be pushing, and follow up with chip & PIN and force depreciation of magstripe.
I think you meant “force deprecation of magstripe”
If, and only if, you’re talking about card-present fraud.
I wonder if a myriad of different devices isn’t preferred to just one. With one system like a chip every fraudster will work to go after it, but with many different checks they don’t know which one they will be up against. The idea is to raise the cost of defeating security both in time and money.
Rather than treating mag stripe cards like VGer, by which I mean we build ever more elaborate infrastructure around them, regardless of cost, to facilitate their tragically hopeless mission, they should instead be retired. They are hopelessly insecure. Giving criminals 100’s of new pathways to exploit that fact doesn’t seem like the road to the future.
@sirk
This is exactly what EMV/chip will do Stripe will go away but the rollout is long.
I wonder, if some issuers could choose to issue chip only cards or if the operating regulations require stripe for compatibility? Mind you consumers will complain when they can’t make a purchase if they have a non-stripe card.
@dave
Chips can’t come fast enough but there will be a large percentage of card not present transactions for the foreseeable future. Web transactions don’t benefit from chips. Something new is going to be required.
Well, actually there are solutions, where the EMV chipcard is inserted into a reader which can be used to authenticate online purchases. Be it via USB connection, optical interface or Bluetooth.
The issue here becomes consumer convenience.
But with other hardware tokens (be it the phone or a USB key etc.) coming along, there are actually benefits here. Even if it is ony to authenticate a card and owner via it´s EMV chip for the first purchase on a new device or from a strange location which could then be used to whitelist that device in the risk scoring for future transactions.
le readers) but gas stations have an extra two years – until 2017.
Security through obscurity is no security at all.
“The enemy of security is complexity”.
Does it make sense to harden one system as best you can or have to harden 1000?
“the unique quantum properties of light to create a secure question-and-answer exchange that cannot be spoofed or copied”
lol. Even if this weren’t b.s., this invention is akin to the Laser Turntable, a gadget to play LPs using lasers introduced right before CDs hit the market.
Dumb question: are these “solutions” intended for the card holder or the card issuer?
The wording of the Siren Swipe pitch seems aimed at the card holder. It’s not very clear to me from the QSA verbiage exactly to which group they are trying to appeal, other than the use of the term “Quantum” tends toward the tech-hip card holder.
As a credit card holder, I don’t see any payback other than perhaps saving me the time I spend verifying transactions on my monthly statement were intiated by me or someone I allow to use my card.
I intentionally don’t have any debit cards associated with any account of mine.
Which product had QSA verbiage? And where?
Well, the product is named Quantum-Secured Authentication, which I abbreviated as QSA and the verbiage I referred to is the pitch sent to Mr Krebs.
@Eddie
I have to laugh. QSA is also the abbreviation used for PCI auditors. So I was naturally wondering if this had been reviewed at some level by one of these.
Well anyway, my point was that as a credit cardholder, neither of these “solutions” interest me – they solve a problem I don’t have.
Card issuers might possibly be interested but probably only if the cost of the solution is much less than the cost of the problem, which I doubt either of these two “solutions” appear to be.
I have used an AMEX card with a chip for the last 2.5 years and was still compromised, but online. When the compromise occurred, they overnight-ed me a new card with NO chip. I called them and they overnighted me another, this time with a chip. Presently, the only place I use the card that actually makes use of the chip feature is Walmart. Some other merchants have readers capable of reading chips and the slot to put them in, but the cashiers don’t even know what you are talking about when you ask why they don’t work. I tried a couple of readers at these stores but apparently the software has not been installed on the reader to support the chip. Walmart, at the cutting edge of American cyber security!
The outlandishness of these solutions speaks to the exasperation generated by trying to secure credit card transactions. No one wants to hamper consumer spending in any way, because that is what drives the economy. And there will always be competition to make it easier than the other solution.
I’ve said it before and I’ll say it again: Payment convenience will always outpace payment security. In fact, I declare that to be Collins’s Law.
I understand the costs increase for loss prevention, I am willing to pay a yearly fee for better security. People often say that there is no loss to the consumer in fraud because they aren’t liable. To me my account itself has value, if I can no longer use the same card number and I have to change billing and other information to me that is a loss. What if I’m traveling during the fraud and I can’t get a new card right this minute, in that case to me I’ve been harmed. Right now I just use one card for higher risk purchases and keep my good card safe as much as possible. I have a solution myself that would add a layer of tokenization on top of EMV and make the card number just what it should be, an account number and nothing more and not an authentication source. Data that is reused can never be very secure.
I’m waiting for a solution from Square (Up).
Their entire business model is based on giving pluggable mag-stripe readers away for free (and charging merchants a per-purchase fee, as the payment processor).
With the liability shift for mag-stripe processors, their business model should become unsustainable, which means they’ll need to do something.
They’ve shown that a market exists for their product, I’d expect them to try to create and deploy a Chip+PIN / Tap reader.
Since they’re willing to give away their current readers for free, if they reach sufficient volumes, perhaps they could give the readers to individuals too. And provide a way to use their product for general purchases over the Internet (possibly by reserving a span of Credit Card numbers and using one time CVV2 / Expiry dates tied to merchant+date+$$$).
The thing that makes it tricky is the need for the different interface. I suppose one could come up with an EMV chip reader that also plugged into the phone using the same earphone jack – I just don’t know how robust it would be.
I suppose one could also make use of a smartcard slot on a laptop. My laptop for work has such a slot – it was designed/intended for use with Windows login (or at least that’s what I interpret the purpose to be). But both EMV chipcards and smartcards are ISO 7816 compliant – I can insert my Visa card into my laptop and with a somewhat specialized application (which one can download off the net), one can read some amount of data from the card. It is a sort of tight squeeze – the smartcard slot wasn’t designed for something with raised numbering, but that being said, it would go.
Square has already announced and may even be shipping a chip-and-signature solution: http://www.wired.com/2014/11/squares-plan-exploit-big-switch-next-gen-credit-cards
My understanding is that PayPal already offers a chip-and-PIN reader overseas as part of its Square-like payment service.
Or people could using Bitcoin and avoid all this headache once and for all.
It already takes grandma 25 minutes to write a check, trying to explain bitcoin to her and getting her to use that will take even longer.
Old people are mostly too far gone for Bitcoin, I don’t have an interest in explaining it to people who don’t understand what email is. She can keep scribbling her checks. For everyone under 55, Bitcoin is not too difficult to understand and it is far far safer than credit cards.
Actually, I’m over 70, have no trouble understanding bitcoin at all, since I trade in the currencies market (real currencies, backed by a sovereign government with a central bank, not an artificial currency backed by nothing but imagineering hype to excite the true believers. ;^)
Apart from digital security, bitcoin suffers from a pronounced risk in using it, which is what this is all about, isn’t it? Preventing the risk of loss?
Surely you’ve noticed that the Russian Ruble has been dropping like a rock in value, in spite of the Russian central bank’s best effort to stem the tide by raising rates to 17%?
Bitcoin has no central bank, or even sovereign government, to back it in a crisis ;^)
In a crisis, like the tech stocks in the 2000 meltdown, all the smart money heads for the exits, while the believers hold all-the-way-down, losing just about everything.
Bitcoin suffers from the same risk. The Enron risk, the Refco risk, the MF Global risk, the Lehman Bros. risk, etc., etc. Hopefully you are old enough to remember some of these. ;^)
Clearly you do have trouble understanding Bitcoin if you think its value requires the support of institutional banks and governments.
because there has never been any security issues with bitcoin right?
Of course there have been, don’t be sarcastic. But it’s just a far more natively secure system. All security errors with Bitcoin have been implementation and wallet-level, not protocol-level.
How about this: When I swipe my card, my phone gets a text with a one-time PIN that I then enter on the pinpad. Not a sci-fi solution, lots of businesses do this today. It defeats the skimmer, it defeats the card shops, it defeats the POS malware collecting my stripe info.
As is, I’m worried EVERY time I use my bank card. That’s not right.
Yeah, I was thinking something of the same. Sort of an RSA authentication. It’s a pain for those of use without cell phones, but there are fewer and fewer of us for that to be a serious problem. It seems like this could be a very good solution, both for in person and on-line transactions.
Why go to all these lengths to secure an inherently insecure storage medium (magstripe) when the rest of the world is 20 years ahead and has more secure infrastructure solutions?
Why couldn’t we have a smart card with a little smarter chip that sends the account number as usual then is fed a nonce at the terminal. Have the card encrypt the nonce along with possibly the transaction amount using a private key that never leaves the card. Send that encrypted info to the bank server who would then use the corresponding public key to prove the card is genuine and is present.
You do realize you are describing an EMV transaction, basically?
Not a technical comment–more of a feel-good story, really–but in at least one small-town case, simple precautions by staff at several stores effectively prevented card fraud. And a bit of extra effort to help local police actually resulted in an arrest, that same day!
http://www.northkitsapherald.com/news/286126781.html
The problem with most, if not all of these solutions is that they are reactive. There needs to be a proactive solution to card number theft. One way to do this is to use temporary and random card number generator on plastic cards that do not display a card number at all. Think RSA key. That way, even if a thief steals the card number its no longer good. There are a number of hurdles to overcome in that solution, but it is totally doable.
Aside from that, people can stop using their credit / debit cards so much. Cash still works. Go figure.
“prevention costs exceed fraud losses.”
A few clarifications and rebuttals on the SIREN SWIPE concept, from its developer…
SIREN SWIPE is a service purchased by an issuing bank and it aims to “deflect” thieves from using their cards in favor of other banks’, be they original, counterfeited, cloned, etc. Since it is a deterrent, the card does not have to be canceled yet.
Sure, detectives care little about following up on credit card fraud days or weeks after the fact, given the manpower intensive investigation required and low probability of arrest. However, it’s very different with a realtime location report to a patrol officer, via a 911 center, which is how SIREN SWIPE works. The senior law enforcement officials who have advised on this with have been supportive of the idea and have confirmed that in the event of a crime in progress report, (particularly a felony forged instrument call) police have to respond. I’m sure police don’t really care about my burglar alarm going off either but they are required to respond to my house, knowing full well it’s around 95% likely to be a false alarm.
And there are certainly ways to get around SIREN SWIPE (e.g. micro deposits, etc). However, SIREN SWIPE exploits the time lag between when a thief validates the card is active and when he makes the fraudulent purchase. It attempts to capitalize on a thief’s doubt/fear of the card being cancelled, and thus activated for SIREN SWIPE, before he makes his purchase. That burglar likely knows how to get into my house and disable the alarm/power/phone line before the big alarm goes off. However, since I have an alarm sign in my front yard and my neighbor doesn’t, that burglar knows there is still more risk with my house so logically he could be expected to target my neighbor’s house instead. (50-60% of burglars will avoid a house known to have an alarm.) SIREN SWIPE is game theory more than anything else and that little bit of added risk with subscribing banks will make their stolen cards much less valuable and less frequently used.
Any further questions or comments are welcomed. Please feel free to email me at info@sirenswipe.com.
Personally, I have had a merchant holding a stolen (physically) credit card on the phone and called their local law enforcement on a different phone. Law enforcement said unless the card issuer (Visa) was going to press charges there was nothing that could be done.
Visa never, ever presses charges as it would offend a potential customer. Law enforcement simply isn’t interested, mostly because the merchants (who eat all the losses) have insurance. They might lose a deductible amount but never more than that. So if someone buys a $1000 TV with a bad card number the response is “So?” In the US there is zero interest in pursuing such transactions. The interest starts to mount up when they go after someone cloning cards and has 1000 blanks in a box. Until then, not so much.
@Ron B
I don’t think that is all that far off from what Smart Card EMV chips do at least logically they do a decent job of card present authenticity, except for the vulnerability with chip-n-pin where a person without the pin can send a code the means the pin was validated. The failings of EMV cards at present have more to do with card not present transactions in that I can still go online over the phone or to a non-EMV card reader and use your info. Any encryption on card present transactions doesn’t fix card-not-present though it could help reduce data theft at the POS.
While at the moment the cost of fraud is lower than the cost of fraud prevention, what happens when the first bank is hit in the manner that Sony has been hit? It would not be as easy, as banks have decent security in place (I think almost everyone has compared to Sony, given its long history of being hacked and clearly not fixing problems).
You cannot stop a well-organised, determined and knowledgeable hacker. The US showed us that with Stuxnet, and North Korea has now demonstrated it again with Sony; going so far as to seed torrents from Sony’s servers! Worse, Sheldon Adelson’s casinos have been thoroughly hacked – though it somehow largely stayed out of the news. One would expect a casino to have bank-strength security.
So when (not if) a state actor decides to take on a large bank, what happens? Worse – what if a country like North Korea, which I understand has been locked out of the international banking system, decided to focus not on a bank but on one of the up-stream financial institutions (IMF, World Bank, or one of many ‘banker’s banks’ – or a reserve bank)? This could cause a greater financial crisis than anything we have yet seen, and it is difficult to see how it could be prevented.
Claims that “fraud prevention is costing more than fraud” are not taking into account the fraud that those measures are preventing just by their existence, and are not taking into account the large, one-off hit that may be around the corner or a few decades away.
I would like to see Brian’s views on the impact of a Sony-level attack on a company or organisation that really matters.
“The truth is that you can “lock down” your credit card if it’s lost or stolen by calling your credit card company and reporting it as such.”
Well, Brian, I have the greatest respect for what you do, & for most of your solutions, but if I just got my credit card stolen, in my wallet, uh, & potentially my cell phone as well, I don’t necessarily have that magic number to call (which is on the back of my card ;^), unless, of course, I had the foresight to have it tatooed somewhere on my body (that I could easily see without my glasses, which were also stolen or broken, & without looking in the mirror ;^)
A couple of these remind me of a comedy sketch where someone took so long identifying themselves that they dropped dead and the last words they heard “your card has been authorised.”
The Netherlands paper is funny for other reasons too, chief among them being that the method relies on the relativistic nature of light more than its quantum properties.
Financial institutions already have significant fraud prevention mechanisms in place, so to state categorically that fraud prevention measures cost more than the actual amount of fraud is entirely specious, as an unknown, but probably massive amount of fraud is being prevented by the measures already in place.
What is not possible to know is how much additional fraud would be prevented by the implementation of further and more costly measures, and which of the existing measures currently in place, if any, could be permanently retired.
On Dec 11th, 2014 as Brian Krebs pointed out, the following sites failed to make the grade (albeit in the case of online.citibank.com where C could technically be considered as passing):
chaseonline.chase.com F
bankofamerica.com F
online.citibank.com C
suntrust.com F
login.fidelity.com F
personal.vanguard.com F
us.hsbc.com F
equifax.com F
Eight days later there is some improvement (think snail for a nanosecond or two); arguably a significant investment in fraud prevention which IMHO, could be ‘written off’ as increased operating expenses similar to (but not quite the same) as corporate losses due to fraud – which could save considerably on corporate taxes, no? Too simple and/or naive on my part I guess.
But who are we to doubt the conclusion(s) quoted in the article by Fed spinmeisters? Why it’s almost as reassuring as Alan ‘Green-speak’ was in the halcyon years prior to 9/11/01.
Nevertheless…
On Dec 11th, 2014:
chaseonline.chase.com F
bankofamerica.com F
online.citibank.com C
suntrust.com B > Stop the presses!
login.fidelity.com F
personal.vanguard.com B > Ta-da!
us.hsbc.com FBF (labile server config.)
equifax.com F
Awesome. Someday we’ll look back and reminisce about how we made it through all of this… or not.
I remember the stock market crash of 1973-1974 and the concomitant “US gasoline rationing system”. Motorists could only get gas according to the last number on their vehicular license plates (odd days and number vs. even and/or alphabetical). People would sometimes get into fights over who was jockeying or cheating as they occasionally had to merge into the long lines; it just couldn’t always be avoided. Sometimes stabbings were the end result. Most often, however, someone would simply run out of gas waiting in line but people would help each other push their vehicles to the pumps.
Despite all of that, back then it really did seem that we had much more time to enjoy life. Just sayin’.
Edit:
The date for the second list in my post should be Dec.19th, 2014.
Agreed, these banks deserve a slap for slow patching. But risk for this POODLE TLS bug is low in general, and SSL Labs ignores possible mitigations. E.g. equifax uses AES-GCM as prefered encryption. That one is not vulnerable to this attack, so e.g. using the latest version of IE, Firefox, etc makes you safe.
My point being, yes banks slack, but end-customers are not at direct risk.
Visa and MasterCard are determined to get their investment back on EMV before we move on to an actual secure solution. The card brands have single use code algorithms that they tried to rollout back at the turn of the Century. Single use transaction codes will solve the merchant security issue and transfer the security liability to the transaction processors and banks.
“prevention costs exceed fraud losses.” For the bank, this is obviously true, else the banks would have implemented better systems by now. For the individual affected, perhaps not so true.
“Fraud prevention greater than actual fraud losses” utterly abuses the notion of opportunity cost. The true cost of not having fraud prevention is not the fraud that occurs with the prevention spending. It’s the fraud that would have occurred without the spending on prevention.
I don’t what that number is, but you DEFINITELY don’t get that number by measuring the fraud taking place despite the spending.
The simplest solution (perhaps) for Consumers who don’t want their information jacked is to use old-fashioned cash for minor transactions particularly during peak shopping season.
What about check-writing , which is still possible and not much more challenging than using a plastic card? I know checks have forgery issues, but retailers still accept them.
What if hackers get e-check information? What data would they be capturing about consumers? Name, account and routing numbers definitely. What about retailers that scan or input your state-issued ID?
Consumers may not be liable but that doesn’t mean they want or need the hassle of identity theft. Until the retailers and card companies work this out, cash is the simple solution for us.
Kazoo – cash and checks are fine for physical presence transactions, but the growing avenues of commerce are electronic (via computer) and mobile (even without internet). Cash and checks are payment options squarely addressing the needs of the last century. We need solutions that address all our current needs. There is at least one that does.
Jonathan @nc3mobi
PS: My computers and phones don’t have slots that take cash or checks, but some computers have nifty retractable coffee cup holders!