The online attack service launched late last year by the same criminals who knocked Sony and Microsoft’s gaming networks offline over the holidays is powered mostly by thousands of hacked home Internet routers, KrebsOnSecurity.com has discovered.
Just days after the attacks on Sony and Microsoft, a group of young hoodlums calling themselves the Lizard Squad took responsibility for the attack and announced the whole thing was merely an elaborate commercial for their new “booter” or “stresser” site — a service designed to help paying customers knock virtually any site or person offline for hours or days at a time. As it turns out, that service draws on Internet bandwidth from hacked home Internet routers around the globe that are protected by little more than factory-default usernames and passwords.

The Lizard Stresser’s add-on plans. Despite this site’s claims, it is *not* sponsored by this author.
In the first few days of 2015, KrebsOnSecurity was taken offline by a series of large and sustained denial-of-service attacks apparently orchestrated by the Lizard Squad. As I noted in a previous story, the booter service — lizardstresser[dot]su — is hosted at an Internet provider in Bosnia that is home to a large number of malicious and hostile sites.
That provider happens to be on the same “bulletproof” hosting network advertised by “sp3c1alist,” the administrator of the cybercrime forum Darkode. Until a few days ago, Darkode and LizardStresser shared the same Internet address. Interestingly, one of the core members of the Lizard Squad is an individual who goes by the nickname “Sp3c.”
On Jan. 4, KrebsOnSecurity discovered the location of the malware that powers the botnet. Hard-coded inside of that malware was the location of the LizardStresser botnet controller, which happens to be situated in the same small swath Internet address space occupied by the LizardStresser Web site (217.71.50.x)
The malicious code that converts vulnerable systems into stresser bots is a variation on a piece of rather crude malware first documented in November by Russian security firm Dr. Web, but the malware itself appears to date back to early 2014 (Google’s Chrome browser should auto-translate that page; for others, a Google-translated copy of the Dr. Web writeup is here).
As we can see in that writeup, in addition to turning the infected host into attack zombies, the malicious code uses the infected system to scan the Internet for additional devices that also allow access via factory default credentials, such as “admin/admin,” or “root/12345”. In this way, each infected host is constantly trying to spread the infection to new home routers and other devices accepting incoming connections (via telnet) with default credentials.
The botnet is not made entirely of home routers; some of the infected hosts appear to be commercial routers at universities and companies, and there are undoubtedly other devices involved. The preponderance of routers represented in the botnet probably has to do with the way that the botnet spreads and scans for new potential hosts. But there is no reason the malware couldn’t spread to a wide range of devices powered by the Linux operating system, including desktop servers and Internet-connected cameras.
KrebsOnSecurity had extensive help on this project from a team of security researchers who have been working closely with law enforcement officials investigating the LizardSquad. Those researchers, however, asked to remain anonymous in this story. The researchers who assisted on this project are working with law enforcement officials and ISPs to get the infected systems taken offline.
This is not the first time members of LizardSquad have built a botnet. Shortly after their attack on Sony and Microsoft, the group’s members came up with the brilliant idea to mess with the Tor network, an anonymity system that bounces users’ connections between multiple networks around the world, encrypting the communications at every step of the way. Their plan was to set up many hundreds of servers to act as Tor relays, and somehow use that access to undermine the integrity of the Tor network.
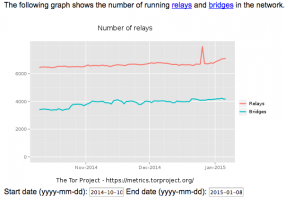
This graphic reflects a sharp uptick in Tor relays stood up at the end of 2014 in a failed bid by the Lizard Squad to mess with Tor.
According to sources close to the LizardSquad investigation, the group’s members used stolen credit cards to purchase thousands of instances of Google’s cloud computing service — virtual computing resources that can be rented by the day or longer. That scheme failed shortly after the bots were stood up, as Google quickly became aware of the activity and shut down the computing resources that were purchased with stolen cards.
A Google spokesperson said he was not able to discuss specific incidents, noting only that, “We’re aware of these reports, and have taken the appropriate actions.” Nevertheless, the incident was documented in several places, including this Pastebin post listing the Google bots that were used in the failed scheme, as well as a discussion thread on the Tor Project mailing list.
ROUTER SECURITY 101
Wireless and wired Internet routers are very popular consumer devices, but few users take the time to make sure these integral systems are locked down tightly. Don’t make that same mistake. Take a few minutes to review these tips for hardening your hardware.
 For starters, make sure you change the default credentials on the router. This is the username and password that were factory installed by the router maker. The administrative page of most commercial routers can be accessed by typing 192.168.1.1, or 192.168.0.1 into a Web browser address bar. If neither of those work, try looking up the documentation at the router maker’s site, or checking to see if the address is listed here. If you still can’t find it, open the command prompt (Start > Run/or Search for “cmd”) and then enter ipconfig. The address you need should be next to Default Gateway under your Local Area Connection.
For starters, make sure you change the default credentials on the router. This is the username and password that were factory installed by the router maker. The administrative page of most commercial routers can be accessed by typing 192.168.1.1, or 192.168.0.1 into a Web browser address bar. If neither of those work, try looking up the documentation at the router maker’s site, or checking to see if the address is listed here. If you still can’t find it, open the command prompt (Start > Run/or Search for “cmd”) and then enter ipconfig. The address you need should be next to Default Gateway under your Local Area Connection.
If you don’t know your router’s default username and password, you can look it up here. Leaving these as-is out-of-the-box is a very bad idea. Most modern routers will let you change both the default user name and password, so do both if you can. But it’s most important to pick a strong password.
When you’ve changed the default password, you’ll want to encrypt your connection if you’re using a wireless router (one that broadcasts your modem’s Internet connection so that it can be accessed via wireless devices, like tablets and smart phones). Onguardonline.gov has published some video how-tos on enabling wireless encryption on your router. WPA2 is the strongest encryption technology available in most modern routers, followed by WPA and WEP (the latter is fairly trivial to crack with open source tools, so don’t use it unless it’s your only option).
 But even users who have a strong router password and have protected their wireless Internet connection with a strong WPA2 passphrase may have the security of their routers undermined by security flaws built into these routers. At issue is a technology called “Wi-Fi Protected Setup” (WPS) that ships with many routers marketed to consumers and small businesses. According to the Wi-Fi Alliance, an industry group, WPS is “designed to ease the task of setting up and configuring security on wireless local area networks. WPS enables typical users who possess little understanding of traditional Wi-Fi configuration and security settings to automatically configure new wireless networks, add new devices and enable security.”
But even users who have a strong router password and have protected their wireless Internet connection with a strong WPA2 passphrase may have the security of their routers undermined by security flaws built into these routers. At issue is a technology called “Wi-Fi Protected Setup” (WPS) that ships with many routers marketed to consumers and small businesses. According to the Wi-Fi Alliance, an industry group, WPS is “designed to ease the task of setting up and configuring security on wireless local area networks. WPS enables typical users who possess little understanding of traditional Wi-Fi configuration and security settings to automatically configure new wireless networks, add new devices and enable security.”
But WPS also may expose routers to easy compromise. Read more about this vulnerability here. If your router is among those listed as vulnerable, see if you can disable WPS from the router’s administration page. If you’re not sure whether it can be, or if you’d like to see whether your router maker has shipped an update to fix the WPS problem on their hardware, check this spreadsheet. If your router maker doesn’t offer a firmware fix, consider installing an open source alternative, such as DD-WRT (my favorite) or Tomato.
 While you’re monkeying around with your router setting, consider changing the router’s default DNS servers to those maintained by OpenDNS. The company’s free service filters out malicious Web page requests at the domain name system (DNS) level. DNS is responsible for translating human-friendly Web site names like “example.com” into numeric, machine-readable Internet addresses. Anytime you send an e-mail or browse a Web site, your machine is sending a DNS look-up request to your Internet service provider to help route the traffic.
While you’re monkeying around with your router setting, consider changing the router’s default DNS servers to those maintained by OpenDNS. The company’s free service filters out malicious Web page requests at the domain name system (DNS) level. DNS is responsible for translating human-friendly Web site names like “example.com” into numeric, machine-readable Internet addresses. Anytime you send an e-mail or browse a Web site, your machine is sending a DNS look-up request to your Internet service provider to help route the traffic.
Most Internet users use their ISP’s DNS servers for this task, either explicitly because the information was entered when signing up for service, or by default because the user hasn’t specified any external DNS servers. By creating a free account at OpenDNS.com, changing the DNS settings on your machine, and registering your Internet address with OpenDNS, the company will block your computer from communicating with known malware and phishing sites. OpenDNS also offers a fairly effective adult content filtering service that can be used to block porn sites on an entire household’s network.
The above advice on router security was taken from a broader tutorial on how to stay safe online, called “Tools for a Safer PC.”




How about cell phone tips? Lots of credentials potentially stored there, even if you don’t do online banking…
Heard about your site in a cybercrime class I took online. I now have a tomato router to protect me from the FIOS router (which stores your WPA pwd on the net!!) Just hack the ISP and you win!
Honestly, on a lot of wifi routers, actually cracking the WPA password isn’t necessary to get in. Wireless Protected Setup is a lot easier to get through. Some have increased protections against this, but a lot don’t.
Tomato router to hack the ISP. I’m getting me one!
Thanks for the OpenDNS info, I’ll try them out. I never realized that it’s possible to change the DNS like this.
A few comments, as someone who’s been measuring home routers for a half-a-decade with Netalyzr. (ObAd: if you have an Android phone, try it out!)
To begin with, so much of the home routers, aka home gateways, aka home NATs, aka CPE (consumer presence equipment in ISP-speak) are abominably bad. Not only do you have common default passwords, but you have major vulnerabilities.
E.g. many use a vulnerable UPnP library that is exploitable externally. Others are vulnerable to a DNS rebinding attack, where even though the web interface is supposedly only accessible from within the home and is “protected” from malicious javascript because of how the browser operates, a bit of malicious javascript can still login and take over the home gateway.
With Netalyzr, we’ve seen cases of home gateways running dnsmasq (a good open-source program which handles DHCP and DNS forwarding) where the code is so old that its before the author even kept a changelog!
Thus my recommendation is one of two possibilities:
a) Use OpenWRT or similar, and keep the router up-to-date. Set a calendar appointment where every month you check to see if you need to update it.
b) Buy an Apple Airport Extreme. Once a month, check for updates (it unfortunately doesn’t auto-update).
Everything else is To Be Avoided. ISP provided stuff is particularly bad: if you have DSL or fiber you may be out of luck, but if you have cable, buy your own cable modem and your own gateway device (its cheaper in the long run too…)
The other is I CAN NOT recommend OpenDNS. They do have a blocklist service, but they do lots of other bad things to DNS, including very overly agressive wildcards, a blanket refusal to support DNSSEC (not validate, mind you, just support!), and in the past they have even used DNS to man-in-the-middle Google.
If your ISP doesn’t run a good DNS service, I’d recommend Google Public DNS (8.8.8.8 and 8.8.4.4) instead.
Great set of recommendations. I recently set up a Netgear WNDR4300 for a client and was pleased to see unique passwords assigned by the factory and a reasonably good WPS configuration.
Re: DNS rebinding – how can I test for this problem?
To test for the DNS rebinding vulnerability:
Type in “what is my IP” into Google.
Then copy and paste that address into your web browser both as http://{IP} and https://{ip}.
If you can connect to your router’s web interface, your router is vulnerable.
One small correction: “If you can connect directly to your router’s web interface without being required to enter a username and password combination (preferably different than the OEM defaults), your router is vulnerable.”
Is the router vulnerable even if I have changed the default password?
Nicholas–I would need to do this while not logged on to my network, correct? If I enter my IP while logged on I will get access. Please confirm.
You run this from WITHIN your network.
How the bug works is that this interface is supposed to only be accessable by the private IP (e.g. 192.168.1.1). Browsers these days include protections which prevent javascript from just going to these private IPs.
If its accessable from the public IP from within the private network, the browser protections fail, thus allowing malicious JavaScript to directly manipulate the NAT if it can guess the password.
Regarding your option Apple Airport ‘Extreme’: For functionality I would need only Airport ‘Express’. Do you still recommend (for the purpose of router security) Airport ‘Extreme’?
I like the extreme because it also has better WiFi antennas than the express.
The Extreme uses a multiple antenna MiMo setup that gets really good quality. A underappreciated but common problem on “why is my net slow” is simply a bad WiFi connection, and that comes down to the antennas.
If you live in a small apartment, you can get away with the express, but I personally think the premium for the extreme is worth it.
Great article Brian!
@Nicholas Weaver
about OpenDNS “and in the past they have even used DNS to man-in-the-middle Google.”
Any references?
Thanks
Thanks a lot for advice Nicholas, I will for sure try Netalyzer.
What is your opinion on RouterOS 6.x from Mikrotik ?
My router runs now RouterOS but it also supports OpenWrt. I have a somewhat better opinion on RouterOS but I see on OpenWrt forums many people flashed their Mikrotik hardware (which comes bundled with Level 3 or Level 4 RouterOS) to OpenWrt. I asked why there but never got an answer.
Once again Great work Sir. Appreciable (y)
Brian, interesting finding. I enjoy seeing generic “there’s a flaw” reports such as your earlier stories on hacked routers, evolve into “now this is the real-world impact.”
On the topic of router flaws, a new one came to light yesterday affecting a popular (and generally solid) line of wireless routers. A local network user (or a compromised PC) can execute any commands they wish on the router, without needing the admin password. Researcher jduck writes about the flaw as well as a few temporary solutions at https://github.com/jduck/asus-cmd
Nice ready, once again! 🙂
I think you forgot a link:
“If you don’t know your router’s default username and password, you can look it up here. ”
http://www.routerpasswords.com/
Just a bunch of immature Script kiddies wasting everyone else s time with this B.S.
Let’s pay to use lizardstresser[dot]su to DDoS Darkode. We could make the transaction via Tor and use a stolen credit card. Oh the irony.
From my testing (three years ago) OpenDNS didn’t block many malicious sites (so I stopped using it).
However, a Cisco M10 Valet seemed to do a very good job at blocking malicious sites with its seemingly hard-coded blocking by Safe Surfing feature which didn’t display as a feature in the administrative page (when I checked three years ago the feature was very vaguely mentioned on the manufacturer’s website).
Having trouble posting here – is that because of cyberattacks? I went on a popular Android forum and was immediately banned for asking about security… Hmmm…
At least one fios provider downloads your WPA2 password for web storage.
You should mention that at least one FIOS+router provided lifts your WPA2 password for net-accessible storage – one hack-job away from being public info.
patti, as CooloutAC mentions (I came across this), the Actiontec MI424WR GigE ‘Revsion E’ (for Verizon FIOS) is not WPS vulnerable prior to the listed firmware version, according to the spreadsheet (from the link in Brian’s article) . (The manufacturer or Verizon may provide further details).
The product brochure is here
http://teleproducts.verizon.com/fileshare/plm/brochure/ATGIGEBHR_brochure.pdf
So, to have FIOS, we have to use the provider’s routers. We can protect ourselves with an additional tomato router, but how do we keep our (manditory) provider’s router from being hacked?
As always: Inquire with the manufacturer (or ISP) for an upgraded hardware replacement or software update. Or, get another internet service provider, if that’s an option.
It depends on what model router you have. The newer revision actiontec routers have firmware coded in that tries to stop you from disabling UPNP and IGMP, which I would also highly recommend disabling for better security. You can still manually navigate to these hidden pages with these links.
http://192.168.1.1/index.cgi?active_page=900 =UPNP
http://192.168.1.1/index.cgi?active_page=6059 =IGMP
But there is nothing you can do to block the open backdoor unfortunately, unless you use another router (I love tomato), or use one of the real early actiontec revisions that actually let you block the port before the ISP’s changed the firmware in the newer revisions. You can still get the security updates for it manually.
As far as DNS servers I use to use GRC’s free shareware program to get the fastest ones for my area, but then decided that the ISP ones are actually the safest. I guess I am mistaken in thinking that?
If I were a disgruntled v*riz*n employee, I would just sell lists of the passwords they automatically lift from their provided routers.
Sorry for the post rate – it acts like posts are rejected… But this is an important recent concern of mine which hasn’t been addressed as far as I know: Our android devices have access to both our protected WPA2 networks and the open internet (with no router protection) – so aren’t we putting our WiFi at risk by attaching an android phone to it?
My opinion: The first device is the most vulnerable in that scenerio (the device itself—the android devices). Then, any devices further along the network they connect to my be threatened from the vulnerable device (if an android device is penatrated on the network).
Yet, with a vulnerable router the threat may come from the router end of the network.
Tomato router, not vulnerable. But if I attach my Note 4 to my WiFi, then my cell phone can be hacked and the tomato router is useless.
not sure what you mean your connected to your wpa2 network with no router?
But yes I’d imagine our phones connecting to our router means we are all screwed when they hack the phone, noone wants to say it I guess. Thats also why the security guys say Mac address filtering is useless.
I guess the safest people are those that live in the boondocks away from other people in wireless distance lol.
Sorry – I stopped using my ISP’s FIOS-interface/router because of its back door. Installed an inner tomato router for home LAN. Now I guess I need to install a second router (and LAN) to handle my android cell phone, because the cell phone makes *that* LAN internet-facing!!
Sorry – I meant that I stopped using the WIFI on my ISP’s FIOSbox router because of the back door (and who knows what else) they use. I have a second-layer tomato router for the home LAN. Now I guess I need another tomato router + LAN for my cell phone – a cell phone makes any LAN internet-facing if you connect to it, so I don’t want to do that to my main home LAN.
From what I can read on the OpenDns website DNS malware/malicious content filtering is not available in the free product, but as part of their Umbrella platform.
When I contacted them some months ago, wanting to buy this product for my own personal use it was not possible.
If these things are indeed unprotected and hacked, the government or someone should hack them again, clean them and change the password. Oh, and notify the major carriers that they might be getting a bunch of support calls but who cares, make it their problem rather than a national problem.
I’d argue the most important thing is to disable admin access from the internet…
Yes, but it it’s an ISP’s router, they have back doors so someone hacking the ISP gets your WPA2 pwd. Wouldn’t connecting your android cell phone to your WPA2 network make your pwd much less secure (i.e., via an android-related web hack)?
EDIT: asking this important credentials-security question on androidforums(dot)com got me immediately banned. Sysops won’t respond to queries. This seems mildly fishy?
Here’s another little secret, apparently. Android, ain’t secure. Same with apple, and windows setups, and I wouldn’t trust the blackberry produced after 2010. Remember those companies get part of their revenue from ads, on your system, those ads, and the companies are tracking you. They have access to the entire system. Even if you only use the WiFi, and have all Other tracking disabled, punch the map, and do a search, ads. Never heard of google voice? They listen, they can see, go to your camera settings, set the click to annoying loud, they take photos, just use the device as a phone? They track you even better, all the tracking is set on, you have to manually uninstall the functions that track, and you cannot update, that restores all the tracking,
Ya, lots of annoying capitalism – but what I’m really worried about is the massive cybercrime industry. When you hook your android phone up to your home LAN, doesn’t that convert it to be an “internet facing” LAN? This is extreme bad practice for a LAN.
Tyra banks had an episode about cell phone stalking victims years ago. Doing all those things you said, listening to these highschool girls, turning on the camera watching and photographing them, stealing all their friends numbers and pranking them as well. And we are talking about when people were still using flip hones…
Nowadays its so much easier, and android is the least secure out of them imo.
Also make sure that the router is not answering DNS queries on the outside interface! This is being exploited for Reflection attacks.
I think why comp sec professionals like this site is because you dig into some of our worst *real* adversaries, eg, card traders, organized crime, etc.
These little diversions are interesting in the sort of way one examines a particularly nasty little bug. I am not sure why there seems to be a continued stream of these nasty sorts of script kiddies, but there always have been and they have gotten decidedly worse over the years.
A key component of their progressing “badness” however is their unbelievable incompetence at hacking.
So, they are not very important for our daily corporate threat models.
As a security bug finder, I find their claims to competence to be especially deplorable, I suppose. It is not all “that hard” to learn how to become technically competent and find security issues, though thankfully our niche remains in rarity. Their technical boasting claims superior skills to us, however, yet in comparison their technical capacities are so low that their boasts make them especially noxious.
Worse, while I am one of the older hackers, not a person I know in this niche did not have prolific success in our teen, even tween years. Yet these guys could not find even a single web application bug even if they knew what a scanner was. Far less anything deeper or more severe.
Depicting them as they are, they are not unlike people who show too much body, yet their body is especially fat and hairy (or skinny and with strange scars).
In a way, these sorts do this almost to get the derision they so richly deserve because they love to try and “hack their enemies”, though their vengaence is ridiculously unwarranted.
Coupling their abhorrent technical capabilities – which do have a deep relief for us professionals attached to these observations – is their equally, if not more so, incompetent world views and models of moral rightness. Their political views put themselves as brave heroes of the most sublime knowledge, out to teach and correct even those who have spent more then ten minutes they have spent in trying to understand good and evil.
Like any ludicrous tyrant, one comes away seeing not only how they excel at being absolutely horrible in selfishness, conceit, even deep sadists: strong addicts of their own praise, the more undeserved it is, the deeper they love it… but one comes away simply astounded by the depth of arrogance in their claims to being right and morally superior to everyone else.
Still, as noxious as these human beings are, and bizarre as they are, unfortunately there are plenty of real, competent bad actors out there. Our niche is ever growing. Now there are plenty of actually skilled hackers working in governments (good and bad), and with very intelligence, organized, and motivated criminal organizations. As well as an ever growing pool of lone wolf baddies.
Put it into perspective — these guys are 10 years younger than the “Shut up I hack you” guy.
http://help.lockergnome.com/general/quot-shut-Hack-quot–ftopict37142.html
One other, unrelated note, on the actual subject matter:
Routers have been (largely unknown to the rest of the IT sec populace) a major attack vector now for many years. Governments were well into hacking these at least since the early two thousands. They surely have been ensuring they remain weak since even longer then that so they can continue to rely on them as key points of surveillance.
What anyone should be scared of in this way is considering that if someone who wants to hack your systems is of the major government level — your systems will surely get hacked. Reality is, however, that target pool is very most likely “not you”. With the possible exception of readers here as being VIP sec people of major corporations and gov agencies.
What they do – as Barnaby Jack showed so many years before his ATM haxoring fame – was that if you can take the router, you can compromise every system behind it.
Nowadays, while rarified, this knowledge is greatly expanded to include every manner of wireless router device. So, if an attacker wants to hack a corporation, they can do so remote from the installation or from a common phone application.
While more strict organizations perform some level of assessment and protection there remains almost no software system for good detection of these intrusions.
As usual, these script kiddies have hit at an area which is exceptional, but have done so with blindly comical incompetence.
A bit like a six year old that hits their teacher in the balls, I suppose, is what they are like. Particularly nasty, but particularly weak.
These governments think they are protecting people with these backdoors, but they are only making us less safe.
Does anyone know what kind of traffic this lizard stresser is generating or capable of generating? I am really interested to know, but I will stop short at actually playing them to dos one of my honeypots. I just need to know what the pattern (or a packet capture, even better) would look like..
If the router has SNMP enabled, sending a packet with a spoofed sender address can result in many kilobytes of response (amplified SNMP reflection attack).
An 80 odd byte “getBulkRequest” can result in up to 60KB of fragmented data being sent back.
So – the size of the attack depends on the number of compromised / known “bots” and the expected payload from each one.
They might be leveraging other techniques, but SNMP and IP spoofing is probably the most obvious to generate large amounts of DDoS traffic from consumer routers.
Did you just seriously recommend people to switch from their ISP DNS servers (presumably secure and on the same network), to a commerical provider which doesn’t even offer DNSSEC (presumably because it threatens their business model to falsify answers)?
Not nice. We just spent a lot of energy and time educating users to demand secure resolvers from their ISPs, and all the big providers around here has done so.
If there is any reason not to use your ISPs resolvers, which there can be, at least use Google’s. They are at least a business which relies on the open Internet to function. They will not mess with your replies.
“The administrative page of most commercial routers can be accessed by typing 192.168.1.1, or 192.168.0.1 into a Web browser address bar. If neither of those work, try looking up the documentation at the router maker’s site, or checking to see if the address is listed here.”
Or just look to see what your gateway is…
I quit routers years,but still wonder how secure the modem is?
Kinda related… maybe not known about, at least for noobs…
Gibson GRC.com still offers ShieldsUp – a free on-line port scanner that looks back at your computer to examine various (or all) ports to discover how invisible you are to the web.
[AT&T’s service ‘backdoor’ for my Uverse dls modem is on port 3479.]
Gibson and Leo ‘the computer guy’ offer audio and .pdf files of their weekly discussion – SecurityNow – on what’s new in the security news. The live video show is broadcast on Twit.tv on Tuesdays.
Windows 8 Firewall Control provides an interface to the M$ built-in Firewall and can really lock a computer down via group policies with no overhead. http://www.sphinx-soft.com/Vista/
CryptoPrevent is an all-purpose tool that prevents any malware that exploits the ‘Crypto-…’ vulnerabilities. Probably a bit overkill for all but the most paranoid.
And… finally, remember the 3-2-1 Backup Rule. 3 copies of any valuable data like pictures; 2 different medias (not three copies on your single harddrive, duh); and, 1 copy off-site (using something like Carbonite or LiveDrive or Google Drive (or just mail them to your ‘extra-storage’ gmail accounts)
The only problem with that is it only does the first 1056 ports. And if you want to do custom port range its only 64 at a time.
As you have mentioned in your case, and mine as well, most of these backdoors are in the high number range, usually between 3000-6000, and I wish shields up would let you scan a larger range. , if not all 65535.
Then again you can’t even close the backdoor on most of these routers anyways….
Good advice.
But, aren’t big outfits, like Google, being hit by international cybercrime on a weekly basis? What does that make google cloud other than a big target?
“OpenDNS also offers a fairly effective adult content filtering service that can be used to block porn sites on an entire household’s network.”
You say that like it’s a good thing! Presumably you heard that most Britons opted out of their government-offered ‘porn filter’. Basically, as soon as someone who is not me starts deciding which web sites I should not be looking at there’s a problem. I’ll bet that any filtering done by OpenDNS blocks a few things that the average person would not consider ‘adult content’ – in much the same way that the Australian government’s proposed filter blocked a dentist’s website, if not in more nefarious ways (blocking competitors, criticism etc.).
Please don’t advertise ‘content filtering’ services on a website that is supposed to be about security. Most of them undermine the user’s security and/or privacy to perform their designated function, and most of them manage to filter things that they shouldn’t while missing things that by their definitions should be filtered.
This is an interesting discussion thread. Do ISP’s typically offer free Botnet mitigation ? I have a house in UK and Germany and I cant seem to find such a capability. I saw the recent that 1/3 of all internet traffic is “bad bots” and I want to find some personal measures to mitigate this threat ?
Not having experience with multitudes of ISPs, my general thought is that mitigation is what the ISPs call “virus protection”, “free virus protection”, paid “security suite” or whatever other phrase is used.
I’ve seen major telecoms, et cetra, offering cloud-based services. I’ve never used these; but offer them as further reading:
http://www.verizon.com/support/residential/internet/highspeed/networking/setup/questionsthree/87766.htm
More enterprise oriented:
http://www.verizon.com/about/news/press-releases/verizon-business-extends-denial-service-defense-mitigation-services-europe
Sprint and AT&T offer managed security services too; but I don’t know if it’s available in Europe (I suppose it is).
Possible they are leveraging the external open port 32764 that was discovered earlier in 2014 that allowed ANYONE to reset the router to factory default and other mischief.
https://isc.sans.edu/diary/Scans+Increase+for+New+Linksys+Backdoor+%2832764TCP%29/17336
http://arstechnica.com/security/2014/01/backdoor-in-wireless-dsl-routers-lets-attacker-reset-router-get-admin/