Analysis of open source information on the cybercriminal infrastructure likely used to siphon 80 million Social Security numbers and other sensitive data from health insurance giant Anthem suggests the attackers may have first gained a foothold in April 2014, nine months before the company says it discovered the intrusion.
The Wall Street Journal reported last week that security experts involved in the ongoing forensics investigation into the breach say the servers and attack tools used in the attack on Anthem bear the hallmark of a state-sponsored Chinese cyber espionage group known by a number of names, including “Deep Panda,” “Axiom,” Group 72,” and the “Shell_Crew,” to name but a few.
Deep Panda is the name given to this group by security firm CrowdStrike. In November 2014, Crowdstrike published a snapshot of a graphic showing the malware and malicious Internet servers used in what security experts at PriceWaterhouseCoopers dubbed the ScanBox Framework, a suite of tools that have been used to launch a number of cyber espionage attacks.
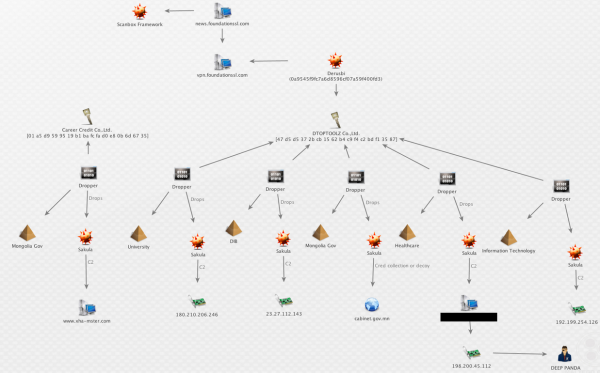
A Maltego transform published by CrowdStrike. The graphic is intended to illustrate some tools and Internet servers thought to be closely tied to a Chinese cyber espionage group that CrowdStrike calls “Deep Panda.”
Crowdstrike’s snapshot (produced with the visualization tool Maltego) lists many of the tools the company has come to associate with activity linked to Deep Panda, including a password stealing Trojan horse program called Derusbi, and an Internet address — 198[dot]200[dot]45[dot]112.
CrowdStrike’s image curiously redacts the resource tied to that Internet address (note the black box in the image above), but a variety of open source records indicate that this particular address was until very recently the home for a very interesting domain: we11point.com. The third and fourth characters in that domain name are the numeral one, but it appears that whoever registered the domain was attempting to make it look like “Wellpoint,” the former name of Anthem before the company changed its corporate name in late 2014.
We11point[dot]com was registered on April 21, 2014 to a bulk domain registration service in China. Eight minutes later, someone changed the site’s registration records to remove any trace of a connection to China.
Intrigued by the fake Wellpoint domains, Rich Barger, chief information officer for Arlington, Va. security firm ThreatConnect Inc., dug deeper into so-called “passive DNS” records — historic records of the mapping between numeric Internet addresses and domain names. That digging revealed a host of other subdomains tied to the suspicious we11point[dot]com site. In the process, Barger discovered that these subdomains — including myhr.we11point[dot]com, and hrsolutions.we11point[dot]com – mimicked components of Wellpoint’s actual network as it existed in April 2014.
“We were able to verify that the evil we11point infrastructure is constructed to masquerade as legitimate Wellpoint infrastructure,” Barger said.
Another fishy subdomain that Barger discovered was extcitrix.we11point[dot]com. The “citrix” portion of that domain likely refers to Citrix, a software tool that many large corporations commonly use to allow employees remote access to internal networks over a virtual private network (VPN).
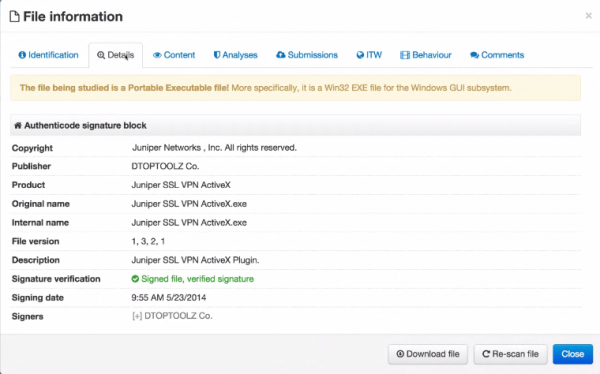
Interestingly, that extcitrix.we11point[dot]com domain, first put online on April 22, 2014, was referenced in a malware scan from a malicious file that someone uploaded to malware scanning service Virustotal.com. According to the writeup on that malware, it appears to be a backdoor program masquerading as Citrix VPN software. The malware is digitally signed with a certificate issued to an organization called DTOPTOOLZ Co. According to CrowdStrike and other security firms, that digital signature is the calling card of the Deep Panda Chinese espionage group.
CONNECTIONS TO OTHER VICTIMS?
As noted in a story in HealthITSecurity.com, Anthem has been sharing information about the attack with the Health Information Trust Alliance (HITRUST) and the National Health Information Sharing and Analysis Center (NH-ISAC), industry groups whose mission is to disseminate information about cyber threats to the healthcare industry.
A news alert published by HITRUST last week notes that Anthem has been sharing so-called “indicators of compromise” (IOCs) — Internet addresses, malware signatures and other information associated with the breach. “It was quickly determined that the IOCs were not found by other organizations across the industry and this attack was targeted a specific organization,” HITRUST wrote in its alert. “Upon further investigation and analysis it is believed to be a targeted advanced persistent threat (APT) actor. With that information, HITRUST determined it was not necessary to issue a broad industry alert.”

An alert released by the Health Information Trust Alliance (HITRUST) about the APT attack on Anthem.
But a variety of data points suggest that the same infrastructure used to attack Anthem may have been leveraged against a Reston, Va.-based information technology firm that primarily serves the Department of Defense.
A writeup on a piece of malware that Symantec calls “Mivast” was produced on Feb. 6, 2015. It describes a backdoor Trojan that Symantec says may call out to one of a half-dozen domains, including the aforementioned extcitrix.we11point[dot]com domain and another — sharepoint-vaeit.com. Other domains on the same server include ssl-vaeit.com, and wiki-vaeit.com. Once again, it appears that we have a malware sample calling home to a domain designed to mimic the internal network of an organization — most likely VAE Inc. (whose legitimate domain is vaeit.com).
Barger and his team at ThreatConnect discovered that the sharepoint-vaeit.com domain also was tied to a malware sample made to look like it was VPN software made by networking giant Juniper. That malware was created in May 2014, and was also signed with the DTOPTOOLZ Co. digital certificate that CrowdStrike has tied to Deep Panda.
In response to an inquiry from KrebsOnSecurity, VAE said it detected a targeted phishing attack in May 2014 that used malware which phoned home to those domains, but the company said it was not aware of any successful compromise of its users.
In any case, the Symantec writeup on Mivast also says the malware tries to contact the Internet address 192[dot]199[dot]254[dot]126, which resolved to just one Web domain: topsec2014[dot]com. That domain was registered on May 6, 2014 to a bulk domain reseller who immediately changed the registration records and assigned the domain to the email address topsec_2014@163.com. That address appears to be the personal email of one Song Yubo, a professor with the Information Security Research Center at the Southeast University in Nanjing, Jiangsu, China.
Yubo and his university were named in a March 2012 report, “Occupying the Information High Ground: Chinese Capabilities for Computer Network Operations and Cyber Espionage,” (PDF) produced by U.S. defense contractor Northrop Grumman Corp. for the U.S.-China Economic and Security Review Commission. According to the report, Yubo’s center is one of a handful of civilian universities in China that receive funding from the Chinese government to conduct sensitive research and development with information security and information warfare applications.
ANALYSIS
Of course, it could well be that this is all a strange coincidence, and/or that the basic information on Deep Panda is flawed. But that seems unlikely given the number of connections and patterns emerging in just this small data set.
It’s remarkable that the security industry so seldom learns from past mistakes. For example, one of the more confounding and long-running problems in the field of malware detection and prevention is the proliferation of varying names for the same threat. We’re seeing this once again with the nicknames assigned to various cyberespionage groups (see the second paragraph of this story for examples).
It’s also incredible that so many companies could see the outlines of a threat against such a huge target, and that it took until just this past week for the target to become aware of it. For its part, ThreatConnect tweeted about its findings back in November 2014, and shared the information out to its user base.
CrowdStrike declined to confirm whether the resource blanked out in the above pictured graphic from November 2014 was in fact we11point[dot]com.
“What I can tell you is that this domain is a Deep Panda domain, and that we always try to alert victims whenever we discover them,” said Dmitri Alperovitch, co-founder of CrowdStrike.
Also, it’s myopic for an industry information sharing and analysis center (ISAC) to decide not to share indicators of compromise with other industry ISACs, let alone its own members. This should not be a siloed effort. Somehow, we need to figure out a better — more timely way — to share threat intelligence and information across industries.
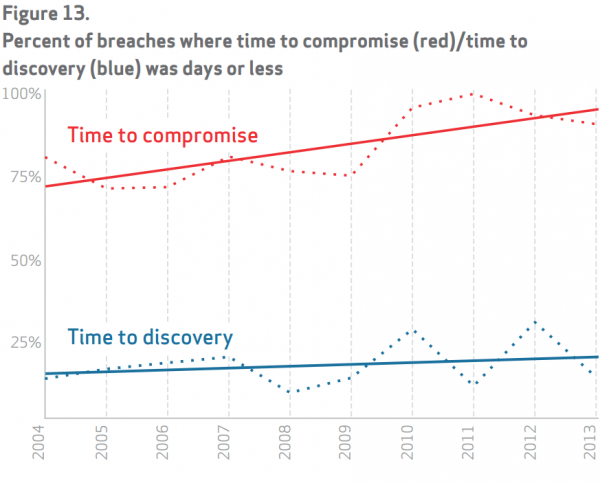
Perhaps the answer is crowdsourcing threat intelligence, or maybe it’s something we haven’t thought of yet. But one thing is clear: there is a yawning gap between the time it takes for an adversary to compromise a target and the length of time that typically passes before the victim figures out they’ve been had.
The most staggering and telling statistic included in Verizon’s 2014 Data Breach Investigations Report (well worth a read) is the graphic showing the difference between the “time to compromise” and the “time to discovery.” TL;DR: That gap is not improving, but instead is widening.
Then again, maybe this breach at Anthem isn’t as bad as it seems. After all, if the above data and pundits are to be believed, the attackers were likely looking for a needle in a haystack — searching for data on a few individuals that might give Chinese spies a way to better siphon military technology or infiltrate some U.S. defense program.
Perhaps, as Barger wryly observed, the Anthem breach was little more than the product of a class assignment — albeit an expensive and aggravating one for Anthem and its 80 million affected members. In May 2014, the aforementioned Southeast University Professor Song Yubo posted a “Talent Cup” tournament challenge to his information security students.
“Just as the OSS [Office of Strategic Services] and CIA used professors to recruit spies, it could be that this was all just a class project,” Barger mused.




Yes, a “class project”. And Pearl Harbor was a “field trip”.
I’ve often been puzzled by the fact that we have so many AV/Security companies and how they “pile on” the latest breach to secure some kind of recognition. Yet, as Brian posits, where was the protection/detection effort?
Very interesting read
Seriously Donald, That’s all the comment you have to offer? Please dont hold back sir.
Sincerely,
As you know, every new malware/virus starts its life as an unknown file, the Unknown file is the enemy. Here is how Comodo deals with executable files and their 3 states. A file can have 3 states, Good, Bad, Unknown.
1. A good file is the easiest to deal with…we know what to do, allow him in, let him execute…..its a good file…
2. A bad file is another easy one to deal with…its bad…kill it….quarantine it…..you see, as long as you know if a file is good or bad, life is easy…you know what to do…..
But the problem arises when you come across an
3. Unknown file : Unknown file is the enemy, so what do you do? Do you let it execute or do you not? What if you execute and it turns out to be a bad file…you are infected…can you take that risk infection? Of course you can’t! The days of playing lottery with your security is well passed!
Current legacy antivirus products do not understand nor do they classify a file into 3 states. They only know if a file is bad if they have a signature for it. So effectively they only know “part of one state” …so they can only identify bad files they recognize…the ones they don’t recognize, they don’t do anything with…
Comodo is the only company that can identify and treat each and every file to its 3 states, Good, Bad, Unknown…
Let me tell you why we can do that and how…
First of all, Good files….well as you know we are world’s largest Certification authority…we issue digital certificates and code signing certificates, We are Intel’s exclusive provider for code signing certificates. When you want to write software for intel CPUs you have to buy a code signing certificates from us. Everyone from Microsoft to HP, everyone that’s worth knowing, we know. We have a pretty good handle on all the good software out there.
Next…Bad files….Comodo has one of the largest Antivirus labs in the world, if not the largest….From China to Ukraine, From India to Turkey, From Romania to the USA, we have our antivirus labs in all these countries catching all the bad files.. So we have a very good handle on all the bad files as well…
Now comes the Unknown files…the enemy…..we put them in a containment in runtime. What that is, a container that the file runs in, so that if it turns out to be bad, it can`t cause damage. There is no user experience impact to the user. User continues to use the file as if there was no container, but actually the file is operating within a container. So this file could be either good or bad…if its bad, nothing will happen to your computer, cos this unknown file is operating within a container and whatever happens inside the container cannot affect your computer..so you are safe….yep…even if its malware running inside the container….
Additional Information:
-Our containment technology (automatic sandboxing) is a patented product and technology, no one can do what we can. Noone can identify an unknown file and put it into sandbox automatically, that would be infringing our Intellectual property.
-Our containment technology is very user friendly, lets say you are downloading an application from the internet, if its an unknown application, the user continues to use/operate it, but invisible to the user it goes and operates within the containment area. So the user is not denied the use of the application and user gets to use the application, but the application is running in the containment area (sandbox)..so everyone is happy…User is happy because they are using the application with no delay (it all done in runtime)…System admin happy because any unknown application will be running a safe containment area….
This message is unsigned and unattributed and strikes me as quasi-spam. It is not informative.
I don’t know but the Defense + HIPS in Comodo can be the only thing he is talking about. I’ve seen a lot of malware get around it – At the risk of sounding like another shill, I have seen one HIPS that always found every spy on my machine, including the legal ones placed there by the MPAA.
Lets just say it is from the same makers as one of the other best software firewalls out there called Online Armor. That said, I still don’t think either of them stands a tinkers ghost of a chance, unless placed into a blended defense; and there isn’t room for me to write all that down. The built in Microsoft white list in Parental Controls is one of those rivets in that armor/defense. Without cooperation and coordination among the majority of industry here in the US, we still don’t have a chance against these nation state bad actors.
I am always interested in hearing others defense-in-depth strategies as one can always improve themselves from the success of others… do you have your strategy written in a blog entry or other fashion that you can share? If not, you should consider doing that as many people might benefit. I am really interested to hear what you have accomplished, including how this strategy impacts the users and their experience.
You can use Windows AppLocker and/or Software Restriction Policy, EMET to lock down a system from beng exploiting by malware in Enterprise Editions and Server editions.
Posting SPAM like that will earn you the title of what is known in South Africa as a “doos”. Congratulations doos. Don’t you realise that spamming people doesn’t make them want your product any more than they did before you spammed them?
Like the mbam spammers lately?
As I was reading this I was updating my Linux distro on my 10 year old laptop. What’s that about EXE files again?
The question I have is how come that digital certificate issued to DTOPTOOLZ Co. was not revoked?
I would assume they issued it themselves.
When the boos gives you a link to some “new tool” in a work group meeting, you click on it….you do it.
A link that was sent to him as part of an email from his boss as part of an updated program that’s part of a company wide initiative. A link to a website that is “assumed” to be legit even though it’s from a very suspicious looked site address. A website that is (naturally) based in the cloud and is coded with all kinds of outside items (1px by 1px graphics) that is there for the spread of malware via a hacked/infected machine (a situation that no one seems to know anything about). It’s all trusted from every angle because it’s from the boss. It’s trusted because everyone seems to believe that cloud is the source of all things good, wonderful, and efficient. These things can’t be filtered out and won’t be because you can’t legally access the host file of Iphones and Ipads, if anyone even knows to anyway since the host file has such a stigma about it. Everyone expects Apple it filter it out and for MS to handle it in “the next update”.
In the end, it is very easy for something to be a very big problem and NOT get caught for years, while it slowly destroys the credit and bank accounts and files of the untold numbers of people and businesses.
While so many in the security community debate over “encryption”, the bad guys have already established a foothold on all the servers they need.
So much of this is that flashing 12:00 on the VCR because too many people are too afraid to do anything about it, too lazy to do anything about it, or are bound by their signature saying that they wont do anything about it because it’s company equipment and no one but IT is allowed to change anything.
“… So much of this is that flashing 12:00 on the VCR because too many people are too afraid to do anything about it, too lazy to do anything about it, or are bound by their signature saying that they wont do anything about it because it’s company equipment and no one but IT is allowed to change anything. …”
yup — rampant stupidity
At what point does the West say to China – enough is enough.
It’s not only the US being targeted by state sponsored agents – Canada too has been hit numerous times with China being fingered as the culprit – yet when push comes to shove Canada like the US and others seem to be unwilling to put their foot down.
Yes international politics is a tough game waded into only by measured moves – but at least a few words of caution are now needed.
^- – -<— – < – – – (He's been waiting for years). I'll keep waiting for the next infiltration/exfiltration.
I’ve been saying to myself, I’ll be glad to see a bigger breach (it’s all very likely to happen) and see if that changes anything about the openness of the internet. I’ll now wait for the next biggest breach. Yes, I’m being very cynical and living in todays reality.
What riles me is how can we expect our industry to go up against a whole nation state, without more coordination, either from industry itself or the federal government of the US?
I wouldn’t hold my breath waiting for Uncle Sam to make a move – US industry needs to band together with one common interest security group!
I think all institutions need to follow a simple rules;
1. White list a few servers that need to communication with the mothership. Blacklist all other means of communications through multiple hops.
2. set up the stereo-typical “rings of trust” for workstations. No direct passing of data from the outer rings to the next inner ring. No outside communication inbound or outbound from the inner rings.
3. set up kiosks for internet use that are slicked every night – use a DVD style load. All internet facing workstations are tightly controlled.
I have personally seen, witnessed and interviewed personnel on issues. A relatively high percentage of these people rather jeopardize a computer in the workplace, than the one at home. Sure there are a lot of “do-gooders” out there that do it right – but many a pen-tester will say; “It only takes one”.
Most of what I said about rings of trust – the highest cost of the whole issue boils down to redoing a wired network – and – humans adapting to a new set of rules. People who are professional web surfers at work will become bored, and can move onto another job to potentially increase the risk of infiltration.
Sure people may get a bit irritated that there are limitations of web activity. Kindly remind them that they have a job to do, and surfing the web all day is normally not one of them.
Commmon, it takes motivation, determination and some cash to keep a network secure. Simply sitting there looking around and banging a small drum will get you no where. Plant a seed in the security arena about GOOD, low cost or free tools that can be used to keep a network secure, will not only balance out the workload between people, but allow the security side of the house to see something that pertains to their job.
BYOD is the answer because if you forbid unnecessary web access on company machines, a lot of this crap goes away. No Facebook, no Gmail, no nothing. BUT, if you have the spare time in your schedule, you can bring your own device, which must never ever have any corporate data on it, and then use your own device on its own ISP connection to mess around in your downtime. It’s unrealistic to assume that people aren’t going to want to blow off some steam during the work day, but it IS dated thinking to assert that they should be allowed to do it on a work PC that has largely unfettered access to the company crown jewels.
They are the world’s “CHEAPEST” CA provider. What a load of crap!
Hi Brian and All:
Maybe I’ve missed it, but I haven’t seen anybody point out that Anthem also lost data for +200k people in 2010.
From spectrum.ieee.org: http://bit.ly/1I8quIi
It’s doubtful the 2010 and 2014 losses are related, but it’s a shame they didn’t learn a lesson. (Or, were they doing all the right things, and network security is impossible)?
I would like to see best-practice cryptography applied for PII in line-of-business systems, and only have the data in the clear at the last possible step. You don’t need to do the crypto in COBOL.
Very few business cases really need the SSN. Pick a substitute key and use it. Only use the SSN when absolutely necessary.
~DW
Check datalossdb.org for many more examples. Search for Wellpoint and you’ll find 2.8M records lost.
What I don’t hear is companies in Europe or Japan getting hacked. Is this information not making the news here in the US or are there better laws that strongly encourage companies to do a much better job with security?
Hadn’t you heard? U.S. Media doesn’t generally care about the rest of the world. 🙂
Google on:
Decade-long cybercrime ring
or
Loyaltybuild hack
or
Cyber-robbers hack European Central Bank
etc…etc…
Broadly speaking, entities all over the world are being compromised–nothing stops maliciousness from entering a country internet border. KrebsOnSecurity is mainly hitting on U.S.-based victim entities; but there are international victims in non-KrebsOnSecurity news–I suggest another source on international victims.
Anthem is part of the Blue Cross Blue Shield national program and therefore may handle claims from subscribers from other states when they travel/move and get ill/injured in an area covered by Anthem. Do you know whether the Anthem breach might affect subscribers of other BC/BS companies? Perhaps the 80 million figure includes that?
If you go out to the anthemfacts website it talks about who’s data was exposed. The 80 million number is based on how many records were potentially compromised which seems to be based on how many records where in the database.
Since BCBS affiliates work together to make sure their members have coverage nationwide, if you underwent medical care while in an area that is in the Anthem regional zone and had a plan through a different BCBS regional provider then your information might be in that 80 million records in Anthem’s database.
This happens because regional health care providers are usually only linked in with their regional BCBS provider, so the BCBS providers work behind to the scenes to make sure if you are out of your region that things get billed back to the correct regional BCBS agency.
This goes both ways, so if you are with Anthem on the west coast and go the east coast and end up going to the Dr while there it means your info is also in some east coast’s BCBS providers database.
Good information provided pivoting off the data
provided the domain “healthslie dot com” resides on IP
associated with we11point dot com. The domain looks
similar to another health industry domain . Could
thirdparty be associated with incident?
Was there third party involved in this breach?
Was there third party involved in this breach?
“healthslie dot com” hosted on same IP as we11point.
Domain looks similar to organization in health industry.
I read where there were other Blue Cross/Blue Shield affiliates included. There was a press release out today on the free ID services to become available to all affected.
Prilock seems to be the vendor of choice here and they’ll make a lotof money.
http://www.enhancedonlinenews.com/portal/site/eon/permalink/?ndmViewId=news_view&newsId=20150209005686&newsLang=en&permalinkExtra=Compromised-Anthem-Customers-Receive-Free-Prilock-Security
I could have tweeted with some of the Anonymous folks today as I wrote my impression as to what the reason was for the breach, to sell data. Who better to ask..
@anon99percenter What’s your opinion on this? Hackers ready to sell and make money from #Anthem breach? http://bit.ly/1zuCZI8
The Real Anonymous @anon99percenter 7h7 hours ago
@MedicalQuack I call them “digital criminals”…it is disturbing to say the least
Anyway too I just wanted to get an opinion here as Data Selling for profit is such a huge Epidemic for profit in the US so why wouldn’t the hackers want to get in the game, repackage the data and re-sell it back, looking like legal data for sale. It’s just like counterfeit drugs getting in the real system and circulating and I see this as a huge exposure. Another group chimed in with this below…so he’s telling us there’s some very talented math nerds on the other side and that talent has no problem repackaging data.
“All the hackers are in prison, those left are epic math nerds…..Some say a new hat is being created….”
Again along with the rest of the normal concerns, maybe not too many have thought of this end of the potential damage but it’s real and the potential for this data to be recirculated into the US is real too and let’s hope it’s not pilfered or flawed.
That’s another scary option but if they want to just make money, that probably would not happen as it takes time scramble up a data base. With 80 million files they could be doing all kinds of data selling in both the open and legal market and on the black market too. We need to index and license all data sellers in the US so we know who the sellers and buyers are so repackaged data as such that is stolen can be found easier by all means.
http://www.youcaring.com/other/help-preserve-our-privacy-/258776
Again with receiving that call about clinical trials from China I’m not too sure that there’s a possibility that someone could be digging around in the data they captured already. I don’t like the fact that someone in China has flawed data on file about me either and that comes with the territory too sometimes with selling data as they don’t care at times. I think kind of nerdy as I used to be a database person and developer. Here’s another bunch you may have never heard of too that sells a lot of data and skirts under the Fed laws as far as how they list themselves and they sell a lot of “secretly scored” data about all of us.
http://ducknetweb.blogspot.com/2012/08/e-scoring-credit-algorithms-invisible.html
Hi Brian, nice article. Hits close to home as I’m probably one of the ones who got their information stolen from this. I had a random question though, what tool did you use to see the WHOIS history for the we11point domain?
Scott,
I used Domaintools.com. Their historic WHOIS records are second to none. Their reverse WHOIS lookup also was indispensable here.
virustotal is commonly used to scan sites for malware. is this not one suggested to use? Citrix is also common tool for remote access. any recommedations?
Thank You Again Mr. Krebs,
Fascinating book, thanks for the autographed copy from Politics and Prose.
https://www2.fireeye.com/security-reimagined-part1.html
Fire Eye was recently brought to my attention. Is there anything like this for home computers ? If you have already written an article regarding this type of product, I’d be eager to read it well.
Best Regards and Keep Up The Great Work,
Glenn
This is the second time this organization has been had, and looks like it will not be the last. I do not know the time span between hacks, but some one lost the bubble – and hopefully – their jobs over these blunders. People need to be fired vice simply allowed to quit. Then there is some sort of record of the account on record.
Some may show a pattern, some may be victims (like end users), some staff are just over whelmed and some staff have a low level of caring – until the paycheck deposits.
There is obviously literally no one watching the perimeter what so ever. Its one hell of a boring job, and these companies need to pay some one – well – to sit there are recognize and potentially thwart these intrusions. Caveat: It takes understanding and motivation of network technologies to have a chance at catching the crooks in action.
What stinks about all of this is, there have been a crap load of breaches – many headlined by Brian, and still to this day, large corporations are simply dumb to the idea of doing something – anything to shore up against a breach.
SSN’s are needed for tax information. Why on earth these companies need that on internet facing web servers is beyond me.
I tend to agree that there need to be more overt firings. The more popular our industry gets, the more fakers and unqualified people there are taking helms. Look at a lot of the recent data breaches–even when a CSO or CIO gets let go, they are almost always allowed to “resign.” Why? There’s no need for euphemism here–the CEO’s job is to keep the business profitable, the CIO/CSOs job is to keep the data safe. If you can’t do that, unless the hack was shown to be amazingly expert or unusual, you SHOULD be fired. Because you are the one who sets the paranoia needle and security posture for the rest of the organization.
Phishes, trojan droppers, whatever. APT is nothing more than an excuse for executives to relax into a non-aggressive mindset about security. Blame the APT and it’s like oh, wizards targeted us, it wasn’t our fault. Meanwhile, how many companies are even running stuff like interdepartmental IDS/IPS? You can’t just fund defense in shallow perimeter security in 2015 and then act like its someone else’s fault when your data is getting exfiltrated.
Indeed, is also ironic that Anthem Inc., Sally Beauty Holdings, Target, Home Depot, Michael’s Stores and Staples – all of which have been hacked in a big way within the last several months have another thing in common. Their stock prices are, nonetheless, amazingly close to their multi-year highs.
I guess a rising tide lifts all boats regardless of whether the passengers aboard have had their personal information compromised or not.
look what I’ve found:
hxxp : / / www[d0t]dtoptoolz[d0t]co[d0t]kr / admin
DTop Toolz Co, Ltd, it’s the same company, according to crowdstrike. On the other hand, it’s registered to a South Korean ICANN registrar.
Hi,
Anyone has any idea, or speculation, on how in such cases is initial penetration can escalate to access to 80 Million records? Through gaining access to an Admin-level credential? Through planing a malware on the DB system itself? Any other way?
Cheers,
CJ
Once you get access to a workstation or server, even as non-admin, there are often multiple ways to escalate privileges. You just keep doing that until you reach your objective(s). Large organizations use a very consistent build process, and once you own one, you own them all. Lateral movement becomes almost trivial at that point.
…at the Irony.
Joseph R. Swedish
Total Compensation for 2013: $16,979,927
Stock Ownership for 2014: 142,114 shares
source: http://www.forbes.com/profile/joseph-swedish/
ANTM currently at $137.89
137.89 x 142,114 = $19,596,099
(California) Insurance Commissioner responds to 60 Minutes story about insurer denials of coverage for mental health treatment
“60 Minutes featured a story last night about Anthem Blue Cross’ denial of coverage for patients needing mental health treatment. “I am very pleased to see that 60 Minutes has brought national attention to our disputes with Anthem Blue Cross over their denial of coverage for mental health treatment,” said California Insurance Commissioner Dave Jones. ”
http://www.insurance.ca.gov/0400-news/0100-press-releases/2014/release135-14.cfm
Not to worry y’all cuz today, Tues. 2/10/15 ALL of the following companies stock prices are either @ or very, very, close to their multi-year highs. Go figure!
(ANTM) Anthem Inc, (SBH) Sally Beauty Holdings, (TGT) Target, (MAR) Marriot, (HD) Home Depot, (MIK) Michael’s Stores, (SPLS) Staples), (LHO) Lasalle Hotel Properties which includes White Lodging Services Corporation, Westin Hotels and Resorts, Hilton Hotels Corporation, Hyatt Hotels Corporation, et al..
And last but not least, (ADBE) Adobe. 😉
Brian, can you expand on the statement “… it’s myopic for an industry information sharing and analysis center (ISAC) to decide not to share indicators of compromise with other industry ISACs, let alone its own members”?
I’m not saying you’re wrong at all, *but* I have a former colleague who was at an Educational ISAC (REN-ISAC), and one of his laments one day was all the work he had to do to communicate out to various parties. Now, that’s not necessarily a contradiction of your statement – for one, it’s a different ISAC, and for two, you weren’t claiming total absence of communication nor was he claiming perfection… but it *does* seem to me that there’s strong effort at least in REN-ISAC to keep members and other associated parties in the loop with what they know.
If you see communications issues in any of the ISACs, I rather strongly think that’s worth it’s own column outside of the Anthem breach. Not to make more work for you, of course, but I think it’s an important and worthy subject.
I do not understand how it requires brilliant Chinese hackers to send a phishing email, and then somehow prevent a sys admin from noticing that he was logging in from other places and when he was asleep.
Anthem provides security training once a year, as part of compliance training. How is anyone at Anthem supposed to recognize even traditional attacks?
I can accept that this was a capable hacker, but frankly it seems more like an awesome fail than an awesome hack.
Here are tips to hold a lot of computer
“Class project” may well be correct.
But an important distinction in this class of data breach is the potential price tag of 80 million records under HIPAA/HiTECH .
Imagining different scenarios unfolding with different targets and your “yawning gap of discovery…”
A laymans perspective: As it seems there is not a quick fix to the current issues, nor does it seem we are confident that we can stay ahead of future hackers, why doesn’t the Federal Gov’t, say Homeland Security, take a page from China’s book and start recruiting from colleges, game programers and yes, even some of our homegrown hackers (if talented enough) could be turned from the darkside and create some sort of task force. Now, I can guess what some people would say, but it is my opinion that Edward Snowden was the exception, not the rule, besides, tell me a situation where you could guarantee that would never happen. There may be a group of Federal Gov’t employees working on this that I’m not awar of (very likely) but I would suggest that the talent that is needed is outside this group (if it exists). I understand that this would not satisfy the ones that want the quick fix, I too am one of the BCBS clients that was affected, however, if we don’t start now then it will be years from whenever we do start. I have a lot of respect for people like Brian, what he does is very important, kind of like a doctor, he determines what the virus is, how we contracted the virus and how to mitigate the virus. I would suggest that while we need people like Brian, we also need people that are completle focused on curing the virus and any variation that might follow. We need to be leading, not following!
Having said all that, the email we recieved from Anthem was, among other information, the hackers took our SSN and income data, the two most important pieces of information needed to devastate someone’s good credit. So my very direct question is, why in God’s name would an insurance carrier even need to know my income data and isn’t there a better way to ID people than the all important SSN?
In all likelihood my suggestions and comments will imply that I am not nearly as smart as most of the people on this site and I probably shouldn’t be here, but it felt good to vent. Thanks.
There’s a lot of noise on the patchmanagement.org mailing list about KB3001652 ( update for Microsoft Visual Studio 2010 Tools for Office Runtime), may contain a EULA and crash / lockup machines where this patch is pushed out in an automated fashion because the EULA must be accepted.
I think MS is being forced to push patches faster then they can test them, and are creating self-inflicted Danial-of-service-attacks on the their user communities.
I realize it’s a great challenge to develop and test patches and the bad guys are reversing them faster then they can be created, yet at the same time it seems like a lot of boxes are getting “bricked” by these updates lately to the point that people are waiting to patch the same way they wait for SP1 of any new OS. This will create a windows-of-opportunity for the blackhats.
Very interesting analysis. thank you!
Very informative article, enjoyed reading it, thank you!
If it was a class exercise the insurers are notifying their clients, offering credit protection services due to data loss. Seems to be real.
I would be interested to know if the DCMA brief server lock down was actually a data breach. The DCMA article sounds to me like business as usual.