I received a number of media requests and emails from readers over the weekend to comment on a front-page New York Times story about an organized gang of cybercriminals pulling off “one of the largest bank heists ever.” Turns out, I reported on this gang’s activities in December 2014, although my story ran minus many of the superlatives in the Times piece.
The Times’ story, “Bank Hackers Steal Millions Via Malware,” looks at the activities of an Eastern European cybercrime group that Russian security firm Kaspersky Lab calls the “Carbanak” gang. According to Kaspersky, this group deployed malware via phishing scams to get inside of computers at more than 100 banks and steal upwards of USD $300 million — possibly as high as USD $1 billion.
Such jaw-dropping numbers were missing from a story I wrote in December 2014 about this same outfit, Gang Hacked ATMs From Inside Banks. That piece was based on similar research published (PDF) jointly by Dutch security firm Fox-IT and by Group-IB, a Russian computer forensics company. Fox-IT and Group-IB called the crime group “Anunak,” and described how the crooks sent malware laced Microsoft Office attachments in spear phishing attacks to compromise specific users inside targeted banks.
“Most cybercrime targets consumers and businesses, stealing account information such as passwords and other data that lets thieves cash out hijacked bank accounts, as well as credit and debit cards,” my December 2014 story observed. “But this gang specializes in hacking into banks directly, and then working out ingenious ways to funnel cash directly from the financial institution itself.”
I also noted that a source told me this group of hackers is thought to be the same criminal gang responsible for several credit and debit card breaches at major retailers across the United States, including women’s clothier Bebe Stores Inc., western wear store Sheplers, and office supply store Staples Inc.
Andy Chandler, Fox-IT’s general manager and senior vice president, said the group profiled in its December report and in the Kaspersky study are the same.
“Anunak or Carbanak are the same,” Chandler said. “We continue to track this organization but there are no major revelations since December. So far in 2015, the financial industry have been kept busy by other more creative criminal groups,” such as those responsible for spreading the Dyre and Dridex banking malware, he said.
ANALYSIS
Certainly, learning that this group stole possibly close to USD $1 billion advances the story, even if the Kaspersky report is a couple of months late, or generous to the attackers by a few hundred million bucks. The Kaspersky report also references (but doesn’t name) victim banks in the United States, although the New York Times story notes that the majority of the targeted financial institutions were in Russia. The Group-IB/Fox-IT report did not mention US banks as victims.
Two readers at different financial institutions asked whether The Times was accurate in stating that employees at victim banks had their computers infected merely after opening booby-trapped emails. “The cybercriminals sent their victims infected emails — a news clip or message that appeared to come from a colleague — as bait,” The Times’ story reads. “When the bank employees clicked on the email, they inadvertently downloaded malicious code.”
As the Kaspersky report (and my earlier reporting) notes, the attackers leveraged vulnerabilities in Microsoft Office products for which Microsoft had already produced patches many months prior — targeting organizations that had fallen behind on patching. Victims had to open booby trapped attachments within spear phishing emails.
“Despite increased awareness of cybercrime within the financial services sector, it appears that spear phishing attacks and old exploits (for which patches have been disseminated) remain effective against larger companies,” Kaspersky’s report concludes. “Attackers always use this minimal effort approach in order to bypass a victim’s defenses.”
Minimal effort. That’s an interesting choice of words to describe the activities of crime groups like this one. The Kaspersky report is titled “The Great Bank Robbery,” but the work of this gang could probably be more accurately described as “Death by 1,000 cuts.”
Why should crime groups like this one expend more than minimal effort? After all, there are thousands of financial institutions here in the United States alone, and it’s a fair bet that on any given day a decent number of those banks are months behind on installing security updates. They’re mostly running IT infrastructure entirely based on Microsoft Windows, and probably letting employees browse the Web with older versions of Internet Explorer from the same computers used to initiate wire transfers (I witnessed this firsthand just last week at the local branch of a major U.S. bank). It’s worth noting that most of the crime gang’s infrastructure appears to be Linux-based.
This isn’t intended as a dig at Microsoft, but to illustrate a point: Most organizations — even many financial institutions — aren’t set up to defeat skilled attackers; their network security is built around ease-of-use, compliance, and/or defeating auditors and regulators. Organizations architected around security (particularly banks) are expecting these sorts of attacks, assuming that attackers are going to get in, and focusing their non-compliance efforts on breach response. This “security maturity” graphic nicely illustrates the gap between these two types of organizations.
As I wrote in my December story, the attacks from the Anunak/Carbanak gang showcase once again how important it is for organizations to refocus more resources away from preventing intrusions toward detecting intrusions as quickly as possible and stopping the bleeding. According to the Fox-IT/Group-IB report, the average time from the moment this group breaks into bank internal networks and the successful theft of cash is a whopping 42 days.
Kaspersky’s report notes a similar time range: “There is evidence indicating that in most cases the network was compromised for between two to four months, and that many hundreds of computers within a single victim organization may have been infected.” Both the Kaspersky and Group-IB/Fox-IT reports contain pages and pages of threat indicators, including digital signatures and network infrastructure used by this group.
So those are some takeaways for financial institutions, but what about banking customers? Sadly, these developments should serve as yet another wake-up call for small to mid-sized businesses based in the U.S. and banking online. While consumers in the United States are shielded by law against unauthorized online banking transactions, businesses have no such protection.
Russian hacking gangs like this one have stolen hundreds of millions of dollars from small- to mid-sized businesses in the U.S. and Europe over the past five years (for dozens of examples, see my series, Target: Small Businesses). In the vast majority of those cyberheists, the malware that thieves used to empty business accounts was on the victim organization’s computers — not the bank’s.
Now, add to that risk the threat of the business’s bank getting compromised from within and the inability of the institution to detect the breach for months on end.
“Advanced control and fraud detection systems have been used for years by the financial services industry,” the Kaspersky report observed. “However, these focus on fraudulent transactions within customer accounts. The Carbanak attackers bypassed these protections, by for example, using the industry-wide funds transfer (the SWIFT network), updating balances of account holders and using disbursement mechanisms (the ATM network). In neither of these cases did the attackers exploit a vulnerability within the service. Instead, they studied the victim´s internal procedures and pinpointed who they should impersonate locally in order to process fraudulent transactions through the aforementioned services. It is clear that the attackers were very familiar with financial services software and networks.”
Do you run your own business and bank online but are unwilling to place all of your trust in your bank’s security? Consider adopting some of the advice I laid out in Online Banking Best Practices for Businesses and Banking on a Live CD.
Update, 3:45 p.m. ET: A copy of the Kaspersky report on the Carbanak gang is here (PDF). Also, Fox-IT has released a Q&A on the differences and commonalities between their December report and Kaspersky’s this week.




Once again, the intrusion/criminals are not so “highly-sophisticated” are they? To quote Pogo “We have met the enemy, and we are the enemy!
We (businesses and consumers) need to look after our own procedures and not depend so much upon “highly-sophisticated” defenses that are being foisted upon us.
Regards,
I Know your not talking about the infested game website full of cheaters that still uses java? haha jk.
I always find it sad when people just blame users. and are quick to say oh thats just a ddos attack, oh thats just a phishing attack, oh they didn’t have much security on that server it wasn’t a real sophisticated hack. As if its some competition to prove your smarter. As if its never the criminals fault. As if any of that matters to the million victims, as if you could even pull the same thing off but in your dreams.
I hate to break it to ya, but hypothetical theories aren’t worth a dam thing. And no matter how smart you think you are, and if you don’t use your computer like a scared little boy not allowed to talk to strangers , your most likely virused just like the rest of us.
I hate to break it to ya…..
If more people would lock their stuff up instead of just operating on the naive basis that all these companies out there are as pure as the wind drivin’ snow that they can be so trusted with ‘everything’ that is you, the world would see ALOT LESS thievery. People are leaving the proverbial door wide open. Companies are made up of people too and they are just as bad (if not worse) than the average user.
Too much trust put in Facebook
Too much trust put in Apple
Too much trust put in Microsoft
Too much trust put in Sony
Waaaay too much trust put in the so called leaders in Washington
Too many people think an update is going to cure all their ills.
Too many people think that answer to all the worlds computing needs is going to be found in the cloud.
lol….very few people seem to actually WANT to learn how and why these machines do what they do. It’s actually seen as a bad thing….as something that someone else is responsible for. Well, YOU are responsible for the computer YOU bought…..NOT Apple, Microsoft, or your antivirus software vendor.
And so what do you suggest people do to lockdown their facebook, apple and microsoft? lol Don’t forget linux buddy, security by obscurity is a fools game. Is it their fault for not finding the info on how to secure their pc online? Should they learn how to fix their own cars now too? Is it even reasonable to expect them to?
Here is a decent windows 7 tutorial http://hardenwindows7forsecurity.com/Harden%20Windows%207%20Home%20Premium%2064bit%20-%20Standalone.html
Still not 100% and still not something everybody should be expected to do, and something you can’t do if your not a standalone machine.
And What is it we should be telling our leaders in Washington, what is it you suggest?
What I suggest is a bit of understanding with regard to the reality behind the way these things actually work. I see absolutely NOTHING wrong with expecting someone to understand that their car will need it’s oil changed on a regular basis (no matter who does it). You talk about “a fools game”….only a fool would use these things and never bother to consider what these things are. What is not reasonable is the extreme amount of ignorance/apathy being put to these things.
People will cry about the rich getting richer and how corp. America is so evil yet they will jump at the chance to buy the newest iphone or android. Apple is making a killin off people with their iphone/ipad addictions.
You can’t lock down Facebook; it’s not yours. My suggestion….DON’T USE IT.
As for Washington: if more people would stop looking to Washington for all the answers and for the meaning to life, they might actually develop their own solutions to life’s little issues. Washington is in it for themselves (for it’s own aggrandizement)…..NOT for your petty needs.
Learn something about your own computer so you can take care of it yourself and quit paying money (that would be better spent elsewhere) to build up someone else’s bank accounts. This is not unreasonable. It is infact, the more intelligent way to do things in life.
oh, if more people actually understood to remove Java from their computer, if more people would understand to keep cookies cleaned out and to filter out certain sites to never get those cookies again, if more people would just quit crying and be more responsible in this world…..
FLOPPY DISKS NEEDED HERE! Know an individual in the military who mentioned our weapons systems (ie Nuclear) cannot be hacked because of the old floppy disk still being used (ohh can I say this on live internet?)….. intentionally used because it is fail safe and hack proof. I have no idea HOW it works or is set up, just that floppy disks are on board. We need to go back to the old drawing board. Sometimes, “old school,” is just plan BETTER…
Remember K-I-S-S? It does work for many things..
One of the first rapidly spreading viruses was a floppy disk boot sector virus.
That would be these guys :
http://arstechnica.com/information-technology/2014/04/60-minutes-shocked-to-find-8-inch-floppies-drive-nuclear-deterrent/
60 Minutes shocked to find 8-inch floppies drive nuclear deterrent
Air Force says archaic systems aid cyber security of Minuteman missiles.
by Sean Gallagher – Apr 28, 2014 12:38pm CDT
18 years ago I had a friend that coded in assembely, for fun he had written some code that changed the head settings of the floppy drive itself rendering it usless. His skills were incredable. If he could do that and more, no doubt others can.
Anyone have a link to the times article?
It’s in the first sentence of this piece.
You also may want to add a reference to Fox-It’s update to their reporting:
https://www.fox-it.com/en/press-releases/anunak-aka-carbanak-update/
It contains some clarifications from their side on the differences reported by them (and you) and now Kaspersky. No golden answers, but addresses some questions.
Excellent reporting. There are voices now suggesting the same as you recommend, that is, concentrate on the intrusions in progress rather than focusing on keeping contacts out.
See: Lee, Y. (2015, Feb 10). Letting hackers in to prevent cyberattacks. Wireless Design and Development.
http://www.wirelessdesignmag.com/news/2015/02/letting-hackers-prevent-cyberattacks
Since I began reading your blog last year, because I do on-line banking I have increased my own security on my Mac: password manager that generates unique, difficult passwords; better security on my router; always install software updates, etc.. It seems to me that even if I do all the right things (even if I reverted to writing and mailing checks), my bank accounts could be hacked through the bank’s computers. What, if anything, can I do to protect my accounts? Are there questions I should be asking the bank’s IT department?
Thank you for the important work you do.
Linda, you can ask your bank anything you like about security, but it’s unlikely you will get a straight answer to your question, either because (and most likely) the person you ask doesn’t know and/or they feel like talking about security is a no-no.
Cannot agree with you more Brian…No online banking for me, online paying, online anything relating to a credit card if I can help it, or my $$$.. my bank loves it when I go in every week for a statement.. and they never say no, or charge for it either.. (better not). They can afford the paper printout, whether they like it or not.
Such a productive use of your time. I’ve worked in ITSEC for several banks and in my experience the IB platforms get treated high priority. When heartbleed hit the institution I worked at had every IB system patched (including non prod) within 24 hours with minimal downtime.
If a bank user gets hacked and you lose money from your account, it’s insured. So who cares?
I care – damn! If a bank gets hacked, somebody has to cover the cost. Is it going to be the bank or the end-users by paying higher taxes for processing and higher interest rates? I’d lean on version 2. So, a bank that doesn’t treat its security properly is not my bank. I have had many of my accounts cancelled here and there.
Fraud losses are a drop in the bucket compared to credit losses. even in this example 100 banks $300 million that works out to $3 million per bank. that’s peanuts. if anything is driving up your interest rates or fees it certainly isn’t fraud expenses. it’s your neighbours who are over extended and can’t pay their bills defaulting on their loans that. There are also operating costs like maintaining a payment processing system, and all the other systems required to run a bank that drive up costs, not fraud.
You can check their website at https://www.ssllabs.com/ssltest/ Check it on the log in page which is probably 3rd party. Other then that nothing you can really do.
Interesting, the bank got a big fat ‘B’. I’d prefer an A. I’m thinking about printing out the report and giving to my bank lady to pass it on.
Thanks.
Below, “C” is getting potentially very bad. I wouldn’t be concerned with “B”. I’ve seen “C” in which a user can potentially raise their own computer security level by running an updated browser with a higher encryption installed.
“B” from my comparisons has been about average for the sites I’ve checked, very few were above “B”.
I think if you call them linda and send them the report they will make the changes. An A+ might not be nescessary but I see no reason why they can’t be an A.
I took your advice and printed out some of the comments from here and the SSL report and presented them to my bank representative. She said that she hadn’t even heard of the big bank heist but by the time I got to the bank she had read NYT article. Will it change anything? Don’t know, but I will be doing an SSL report periodically and taking it to the bank for further discussion. Someone in this post mentioned a bank with A+ SSL, what bank is that? She asked me and I didn’t know. Thanks for all the ideas and links, it’s been an interesting couple of days.
“B” rating is the best I’ve seen at a financial institution since checking after one vulnerablity October through December pushed many to “F” and many fixed that problem (still the same “F” out there at some). I checked eight financial insitutions. I haven’t checked them all again recently.
I’ve only seen one “A” and that was with a non-financial email provider.
The best advice I can give on this is to shop around. I picked a credit union association that responds to customer’s needs mainly because every customer owns a piece of the business. I just happened to know the head of security at this organization, and would once and a while comment on issues I noticed about their layout. I don’t think that was even necessary as he was already on it; and they have steadily been increasing web and other security for several years now. They have genuine multi-factor logon security enforced now, and have had pro-active monitoring of personal and business accounts that flag suspicious behavior much the way some credit card companies have practiced for several years now..
If you find a bank or other institution that answers your questions about things such as this, then that is probably the place to go. Our local CU actually insures business accounts as well. That is something you won’t get in an ordinary FDIC insured standard national bank.
If you actually know someone who is a bank officer, simply ask them if he or she is aware of Brian’s blog — if they respond “yes”, then it’s quite likely the IT staff has regular readers who alert the officers internally and who will be a lot more cognizant of and proactive about the sort of dangers Brian exposes on behalf of their banking institution. If they answer “no” or “who?”, then explain who Brian is, what benefits are provided by signing up for the free KOS newsletter, provide them with the URL, and request (maybe demand) that they have their IT folks sign up immediately.
Brian’s right, you’re unlikely to get useful answers from the bank.
I think you can try to get them to do things like:
[Bank]
1. Use 2FA for your logins — https://twofactorauth.org/ see “Banking” — if your bank isn’t on this list, this is the first thing you should get them to change.
2. Ask if they use 2FA for internal management of your accounts. (This is of course vulnerable to attacks on DBAs, as discussed in other articles by Brian, but see #5)
3. Ask them about controls you can add to your account(s). Perhaps requiring two people to sign off on any changes to your accounts autopay.
4. Ask them if you can receive notifications for all changes to your accounts (including changes to the notification settings!) — note that you could potentially drown under auditing logs, you’ll need to set up a process to review such logs/reports (two people should probably review them).
5. If you’re big enough, you might ask if there’s a person who can be assigned to your account to review transactions weekly. Ideally such a person will learn your transaction behavior and recognize when things don’t match.
[Web quality]
6. you could ask them to get “A” grades on ssl testing sites, here’s an example of a semi-major bank not getting that:
https://www.ssllabs.com/ssltest/analyze.html?d=rbc.com&latest
— banks should serve all external content via https — the “No secure protocols supported” for “rbc.com” is a fail in my book.
https://www.ssllabs.com/ssltest/analyze.html?d=wellsfargo.com
— these guys don’t support the latest version of TLS (but at least they offer https for their domain…)
7. banks should redirect all connections to https
8. banks should use HSTS for all servers — http://en.wikipedia.org/wiki/HTTP_Strict_Transport_Security — doing this means they tell your browser “the next time your user enters http://www.rbc.com, connect to https://www.rbc.com, don’t bother visiting http://www.rbc.com”
9. Banks shouldn’t be using RC4, their certificates should be updated to have a stronger signature, they should support forward secrecy.
[Mobile]
11. If you are considering using a banking app for a mobile device (I wouldn’t, but hey, it’s your money), you could ask if they have an independent auditor assigned to it, and whose report you could read. — Mobile applications have a really bad track record when it comes to security, they often disable certain certificate validation checking (which is a huge risk).
Sounds like a full-time job. no thanks.
Most organizations that have “support” lines deal with things using something roughly like “buckets”.
If one person makes a comment about a certain thing, it goes into a bucket. Each person who makes a similar comment has their comment added to that bucket.
If 100 people make similar comments about that same thing, it’ll probably “overflow” the bucket, at which point someone (typically a manager) will ask “why are we getting so many complaints about this thing? can we do something to alleviate it?”
Phone support, and in person support is expensive, so there’s an incentive to reduce the amount of time spent on common problems.
If everyone acts like an ostrich and sticks their respective heads in the sand, then nothing will be done. OTOH, if everyone complains, something might be done, because all those complaints cost money (or at least slow down service for others, which result in more complaints about slow service), and addressing them will save money when the complaints stop arriving.
The one solution is to do away with the use of email and come up with a better solution or fix the existing protocols to make them a lot more secure.
I have to disagree somewhat with the recommendation of focusing more on the intrusion in process than perimeter defense. Both are absolutely critical and both should be key parts of an organizations security strategy. You cant favor one over the other.
I support the assertion that banks need to be able to respond much quicker. The “bad” guys will always find new ways to attack and not detecting and responding rapidly leads to great damage. Of course having a solid plan and process to defend against such attacks is required and a fundamental part of doing business. But it has been my experience that banks/businesses can and will be hit. Mr. Krebs continually provides evidence of this activity as banks and other businesses move along blissfully unaware or unwilling to act.
This is a great follow-up on the earlier article.
Well the head of IAD for the NSA disagrees with you. I think alot it comes down to available resources and mitigating damages, and because viruses are just so overwhelming. In 2013 she said at least “1 million new viruses made every month, that don’t even stay in the wild long.” We are all probably living with hepatitis right now on our computers lol
From a consumer perspective, if you don’t use your computer like a scared little boy not allowed to talk to strangers. Meaning you browse random webpages, post on forums, watch porn, play online games, download music, go on facebook, im strangers. Then your most likely virused like the rest of us. I don’t care how smart you think you are, your already virused and just don’t know it. And if you think I shouldn’t be doing those things, then you’re more disenfranchising then the governments most of these so called hacktivists are against…(that never go after other hackers btw)
The reason why people prefer phones now, not only because its more portable and turns on faster, its because instead of formatting your hdd once a year after it gets bogged down, you just get a new sim card or new phone, free of charge when something doesn’t work. Instead of the laptop that becomes a virused paperweight for most people nowadays. The irony is when it finally hits home and people realize how much more intrusive and easily hacked their phones are in the future, oh wow society is going to start hanging more people.
Its to the point now I don’t even bother paying for any security suites anymore and wouldn’t recommend any. If these guys are directly hacking banks, what is symantec going to do for me if they target me except give me more headaches? I feel like one of those old computer guys I use to argue with when I was a kid lol. But i realize now they were always right. Its not because I think a competent user can stay virus free without an a/v suite. Its because I think no matter what a user does, if he actually uses his pc, not even if hes targeted, if he is just active on his pc, he will be virused no matter what eventually and probably won’t even know it. Thats the problem, we are all already compromised, its just not detected.
Just to clarify I would still recommend MSE or Avast> used with windows firewall. But my point is, if we are going to get virused anyway why waste money on it.
As a 10 year veteran of the ITSEC community and having worked for 2 major vendors all I can say about your comments is “complete bollocks”.
Agree completely with OBM… CooloutAC’s comments are hogswoggle. Been doing IT security for close to 20 years. Run an integrated defense on a small network of PC’s and Macs used by relatively unsophistocated users. NEVER had an active virus. Only a couple of warnings.
Yes, you CAN get pwned just by using your computer. But it’s NOT that likely. MUCH more likely IF you click on random links in emails and/or download crufty SW and games from doggy sites.
You guys sound like your still living in the early 90s lol.
First of all a business should only be allowed to use whitelisted sites. Which many businesses do now, like the hospital my mother works at. But I’m talking about home users.
I believe it was Brian who had an article about NBC.com, as one example, giving people viruses just by simply going to the url, without having to click anything. Would you blame that on users for going to that shady site? Its their own fault for going to nbc.com? Were they not blocking enough ads and scripts, that then end up making the page unuseable for the fucntion they want to use? lol Do you really think your 100% secure from direct attacks when you have to have doors open to make connections in the first place? really? Is it my fault when my computer gets infiltrated by some admin on a game server? Do you really think its not common for people to get targeted nowadays, when someone online who is not a hacker or nerd is the minority online now? Sometimes I wonder if hacktivists and IT professionals are more disenfranchising then the gov’t, with their complacency and blaming users, and its no wonder we are in the situation we’re in now.
Do you really think any a/v company is keeping up with more then a million viruses made every month that don’t even stay in the wild more then a month or two? Do you not believe these statistics from the NSA? Are they lying to us? And this was a 2013 estimate, every year it gets exponentially worse. Is your definition of “not getting a virus” because your a/v program doesn’t detect one? lol
If you want to disagree with the NSA , and with Brian, and with real security experts, fine , I guess you “IT” guys know better…..
One thing we can agree on, though, is there is no security, But rather then blame users like a typical criminal hacker, or like an IT guy who wants to save face at his job, I believe it should not be the responsibility of the user,, it should be the responsibility of the people making money off these services. Unfortunately many experts say there was nothing even Sony could of done to protect themselves. All i know its only going to get worse. And if your one those guys that never have any problems, You must not do much on your pc, and I don’t believe limiting ourselves is the answer.
Most companies I have worked for don’t allow employees to auto update their work laptops. Updates had to be done by the IT department once it had been determined the update wouldn’t mess up other programs. This rule leaves the laptop vulnerable to these attacks. Sadly, I worked for credit card processing companies!
Not just laptops but desktops too. Our enterprise is pretty good and reasonably swift about distributing updates for Microsoft products, but they don’t bother with pushing updates for Adobe products or Java. So I do my own, either when I get the Microsoft Black Tuesday notices or when I receive the e-mail about a post on KrebsOnSecurity. Same for browsers other than IE: A big chunk of users have Chrome, and a somewhat smaller number use Firefox (including the IT staff), but officially they are “not supported”. The weakest link…
Just yesterday I was at a local store for a major national retailer, and their online inventory checking and ordering system box was running XP and IE8. I guess they haven’t been bitten yet.
CC processing companies exist like sand on a beach. Basically anyone can do it. Bunch of lines of PHP and developing directly on prod isnt too uncommon from my experience. Go figure what those do about security…
The security maturity graphic is awesome. Thank you for being a calm rational voice among the press.
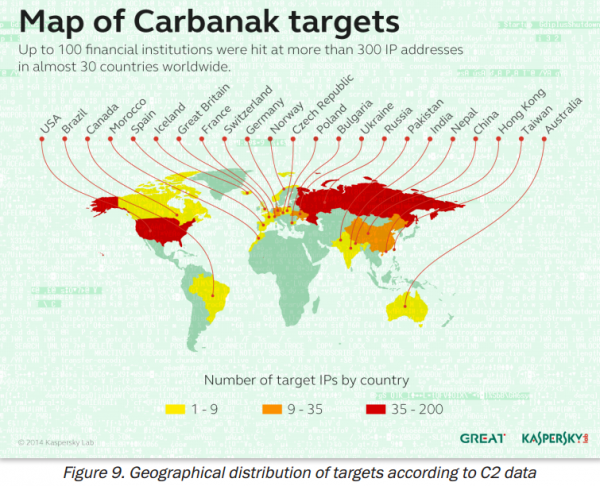
I wonder why some developed and wealthy countries are not on this map. Middle East, Singapore, Malaysia for example.
Also not on the map as targets are Israel and Japan.
Might be due to not knowing the languages well enough to find out who in the particular bank has the keys to the electronic vaults.
Good thought.
[This post is pure speculation]
Yes, security-by-obscurity-of-language is definitely a possibility.
Israel in general is pretty big on security (Trusteer was Israeli).
Notably, GDP for Israel is above Hong Kong which was targeted, and certainly the GDP for Japan being ~#3 in the world means it should be targeted assuming it’s simply a GDP shopping list.
It’s also possible that security-by-currency-isolation is relevant. Currency transactions between Brazil and USD may be fairly common, and India/China w/ USD. The European countries have common transactions to EUR (Norway isn’t on the EUR, but it would have lots of transactions to it). Australia should have lots of transactions to USD. The number of transactions by average entities starting w/ the NIS and going to USD (or other) would be lower, and it’s possible a spike there would be noticed. While I’m sure there are currency trades between the Yen and dollar, it’s again possible that a spike in such transactions would be noticed. I think the same rarity in transactions could apply to the Arab states.
Brian,
Thanks for the post and additional material presented. In light of the reported fraud by cyber criminals on banks as reported in this article, as well as other breaches to the likes of JP Morgan, it is painfully obvious that security holes exist in every environment, both big and small. As the head of IT for a Small Financial Institution, it feels like more like a matter of “when” not “if” a hack occurs.
It is time for technical security to take a second look at how information if shared. For all the breaches that make headlines, there are the security measures that are working. The working security measures beyond FW, AV, Layers, Spam Protection etc… I am looking for what is working beyond a commercialized set of security product all advertising the next best mouse trap! There is a need and a time for increased collaboration and information sharing.
There is a need and a time for increased collaboration and information sharing.
This is exactly what Obama posited in a recent speech on cyber security: http://www.whitehouse.gov/issues/foreign-policy/cybersecurity.
This is another decades-long lame attempt to contral “illegal” cybercrime, that isn’t being controlled as though it’s really “illegal”–illegal often isn’t illegal when it comes to cyber crime that is illegal in many countries, but not others.
The “illegal” actors will often still be allowed to traverse across the worldwide internet, as the “criminals” are later identified by even more as yet to be spotted threat indicators (shared-collaborated-indicators). Let’s keep on passing indicators around and watching the “illegal” activity continue.
Scan for how many times “criminal” is used in this one article (four times) and user posts (five times so far). How much closer do you think these known “criminals” with identified indicators are to being stopped from their “criminal” activity?
I suggest the indicators be used to track down the “criminals” internet access points and have it permanently taken away for being a major public nusiance, putting it very mildly? If not, I’ll see the next victim of “illegal” activity, as it’s allowed to occur (by the exact same group with known indicators).
To answer your question about what works – I believe a stronger focus on People and Process focused controls leveraging internationally accepted best practices and standards such as ISO 27001 / 27002, as opposed to focusing on the latest Technology Silver Bullet.
As you can see from the security breaches matrix published at the button of the link below, most of the high profile breaches we have seen since 2005 could have been prevented by implementing as little as 3 of these types of People and Process focused controls:
https://www.cloudeassurance.com/news/industry-news/
Yes, I had thought that I read this “story” somewhere else, but it’s “hot” news on the teevee
Two of many hings which need consideration in my opinion are:
1. How are these cyber criminals able to use these huge amounts of money? Are these large sums totals over the entire cyber crime industry? And judging from the dollar volume, it is quite a profitable industry. Only Scruge McDuck likes to play with and count his money.
There must be a pipe line from the victimized banks to the profiting distribution banks.
2. Most IT department policies in my work experience, would wait a considerable time before installing updates, especially Microsoft because of their penchant for breaking something. So often the time between detection of a problem and the installation of a patch is significant. With the instant communication network we have now, adetected security flaw is like the Christmas Tree at a drag race. A race between the criminals and the IT department. Guess who has the better dragster!
It’s not mention which are these eastern european countries. I am really curious to know. Is the source from one country or many?
Wat Dreary_, alias _Brown
Will_, an irregular Dog, who hath an underhand way of disposing of his
Goods. I’ll try him only for a Sessions or two longer upon his
Good-behaviour. _Harry Paddington_, a poor petty-larceny Rascal, without
the least Genius; that Fellow, though he were to live these six Months,
will never come to the Gallows with any Credit. Slippery _Sam_; he goes
off the next Sessions, for the Villain hath the Impudence to have Views
of following his Trade as a Tailor, which he calls an honest Employment.
_Mat of the Mint_; listed not above a Month ago, a promising sturdy
Fellow, and diligent in his way; somewhat too bold and hasty, and may
raise good Contributions on the Public, if he does not cut himself short
by Murder. _Tom Tipple_, a guzzling soaking Sot, who is always too drunk
to stand himself, or to make others stand. A Cart is absolutely
necessary for him. _Robin of Bagshot_, alias _Gorgon_, alias _Bluff
Bob_, alias _Carbuncle_, alias _Bob Booty_.
All suspects.
Cool Story,
Bro
In 2010 the average time to find a compromised computer on a network was 156 days (Trustwave global security report).
In 2013 the average time to find a compromised computer on a network was 229 days (Fireeye report).
Tell me again how focusing on finding “live” intrusions is the best way to secure the data on my network?
The ease, speed, variety and number of attacks have all progressed at a rate far beyond that of the ability to detect and mitigate those attacks once underway.
The tools and methods simply do not exist to make that a viable option right now, and they get comparatively worse every day.
With such incredible amounts being syphoned away on not just this example but the many, I have to wonder what on earth the thieves are doing with THAT much money. One can only buy so much before it’s absurd, unless what one is purchasing is big-scale weaponry. “Where is the money going?” is my question.
It’s a fair and reasonable question. One we are not likely to every get an answer to.
This isn’t just a handful of rogue hackers of anger management issues. The black hats in question are going to be part of a group; likely hired (under the table) by a government or a much larger and well known organization. The high dollar figures (as it is reaching) could easily be used to fund ISIS or development of Iranian nuclear ambitions. All at the expense of the entire planet. Money so easily had via the ineptitude, carelessness, laziness, and apathy of the masses where computers and the Internet are concerned.
hhhhmmm….let’s all be beggars to our own demise.
As I started to read this story, I was depressed thinking about the pain and troubles these hackers cause millions of ordinary citizens who are just trying to keep their heads above water. Then I saw Brian’s shining ray of good news.
“Most cybercrime targets consumers and businesses, stealing account information… that lets thieves cash out hijacked bank accounts, as well as credit and debit cards… But this gang specializes in hacking into banks directly, and then working out ingenious ways to funnel cash directly from the financial institution itself.”
FINALLY! The greedy cretins that are responsible for failed security are getting their OWN asses stolen. Now that USD $300M – $1T has been stolen from the banks themselves, they will have some incentive to secure their own coffers and in the process, ours.
Ironic, isn’t it? By succumbing to blind greed, the cyber thieves have probably killed the goose that lays the golden eggs.
The only shadow on this silver lining is that given our government’s recent proclivity to reimburse financial institutions for losses resulting from THEIR OWN criminal activities, and the current laws failing to protect businesses as they private consumers, I fear that the Feds will decide to bail out the banks. Financial institutions SHOULD be allowed to fail from their own mistakes. Isn’t that what conservative Republicans keep telling us? That we should sink or swim based on our own ideas and our own efforts? Let those lazy people starve if they don’t work hard enough to feed their families and reward the highest earning taxpayers with the lowest effective tax rates. That’s what they tell us and as lawmakers, that is how they write the tax laws. So if any banks can’t survive the losses caused by their own bad business practices, let them fail. That is true Capitalism. None of these “poor baby” bailouts. If the Feds must reimburse somebody, reimburse the CUSTOMERS who suffer, not the institutions that failed to implement safeguards.
They are going to put chips in the cards and eliminate encryption.
Be that as it may; it is certain one dissaffected Per|son cannot withstand the Mobocratical Power, which it Page 273is manifest has gained great Strength of late Years, and, I am persuaded, will continue to flourish more and more every Day. They have many wise Maxims by which they govern themselves; such as, “no wooden Shoes”, —”Liberty and Property and no Excise”—
no French Dancers
—”no Mounseers”—Let every Man toast his own Cheese, &c. such prudential Axioms, founded on the soberest Sense, must undoubtedly con|tribute to render their Administration both wise and prosperous. It does not appear that they have made any great Progress in the modern Art of War; on the contrary, there is Reason to suppose that they all hold it in Contempt; as it is certain that on many Occasions, when our mixed Form of Government has endeavoured to oppose them, by sending the Soldiery against them, they have always laughed at the Military Force, and re|pelled them from the Assault, without their daring to Fire. Their Military Discipline seems to be derived from the Romans; they know no Use of Cannon, Fire-Arms, &c. but proceed to Battle with Sticks, Bludgeons, setting up loud Shouts, somewhat like the War-hoop of the Indians, and hurling Stones, Brickbats, Bottles, Glasses, &c. with tremendous Force on the adverse Party. They are likewise totally Strangers to all Re|sinements of modern Luxury; Bread and Cheese, and Porter being their chief Sustenance; Gin being only used by them when they are low-spirited, or are going to be hanged. They do not paint their Bodies with Woad, like the ancient Britons, but generally with Kennel-Dirt, which lends them a formidable Air in Battle Thus enured to Danger, it will be no wonder if the Mobocracy at length becomes Masters of this King|dom, which, as I conceive it, must shortly be the Case, unless the Vices of People of Fashion should descend to them, and retard them in their Progress. Of this, I must own I am inclined to cherish some Hopes, as I am in|formed, that, in some Parts of the Town, they drink, and game and swear, and are full as wicked as the better Sort of People. Particularly in Hockly the Hole, I am told, that they have a Place called White’s Chocolate|house, that clean Lodgings for Travellers are dearer than ever, and that you cannot any where Shave for a Penny, the Depravity of the Times having raised the Prices of every Thing there, as well as at the St. James’s End of the Town.
TRUE INTELLIGENCE.
From my own Apartment,Aug. 10.
AFTER a Soliloquy, which I have this Morning held with myself, agreeably to the Advice of Lord Shaftsbury, the Upshot was, that I determined to in|form the courteous Reader, that the Plan of the Gray’s Inn Journal is now drawing towards a Conclusion, and in the Course of a few Papers more, Ranger must sub|side into an absolute Silence.
Silence is Golden. Thanks for the Upshot.
AV industry is dying because of Mac. Nobody in private sector needs Kaspersky, Symantec and the horde of their loving bloggers including “this author” and super secure NSA/CIA cyber agents. Poor dudes. Steven owns you even when he is dead. Now all they can is attempt to sell to corporate sector.
Not gonna work. Mac’s gonna come there as as well.
Here’s a shovel [===|> dig your head out of the sand. Both Linux and Mac have had major security issues last year. Or are you being sarcastic?
has Kasparsky published their report yet?
just noticed that kaspersky.com is down.. coincidence?
It’s sometimes called DDoS retaliation (or retribution by some, usually the ones who are involved and got outed)…
What you said! “Most organizations — even many financial institutions — aren’t set up to defeat skilled attackers; their network security is built around ease-of-use, compliance, and/or defeating auditors and regulators. Organizations architected around security (particularly banks) are expecting these sorts of attacks, assuming that attackers are going to get in, and focusing their non-compliance efforts on breach response.”
Thank you for telling it like it is!
According to the Times article, one of the banks used to create fraudulent dummy accounts was J.P. Morgan. Doesn’t the U.S. have banking regulations in place to prevent this type of fraudulent activity? And if so, how did these criminals bypass that mechanism? It seems that J.P. Morgan deserves a closer look from regulators in regard to this type of activity.
Don’t worry be happy!!!! its only cyber vandalism.
and don’t forget a few of my other words of wisdom:
ISIS is the JV team
You can keep your doctor
I ended the Iraq war
signed
B.O.
There’s always at least one nutter shows up, ^^^^^ no matter what the article’s about.
England and US government working to create more back doors and ban encryption. It’s going to get worse.
To me, the big story here is that a bank can be hit with a false $10 million transfer from one entity to another and never notice it. The other big story is that once noticed, it seems that $10 million has disappeared and is not recovered.
I’d like to know exactly how that happens in any modern bank with fiduciary responsibility to impose accounting and operational controls.
I used to work for Bank of America in their cash management software division. We sold cash management software to Fortune 1000 companies to manage their cash balances on a daily basis. Some of these companies have hundreds of millions of dollars scattered across a dozen banks. But I still don’t see how you LOSE $10 million in one shot.
I also remember Kevin Poulson’s Kingpin in which it was said the main hacker had NO trouble penetrating small and medium size banks and many of them. His problem, however, was that once inside, the banking software was so complicated he couldn’t figure out how to do direct transfers of the type reported here. This implies to me that there has been some insider help.
There was a book published, oh, I don’t know, thirty years ago, about a group of gold smugglers back in the ’60’s. At one point they were offered the codes and procedures to make wire transfers from a major bank (BofA IIRC) by an insider in exchange for a cut of the action. They were all set to hit several branches for hundreds of millions but got caught before they could pull it off. This current hack sounds very similar.
What’s with all these foolish comments: “How do they spend all that money?”
How do the one-percenters manage to spend all their money?
How does the Saudi royal family manage to spend all their money?
Answer: Expensive trips to far-away places (first-class airfare and $1000/day hotel suites). Expensive meals, catered parties. A couple of villas in warm places. Servants. Five or ten of the world’s most expensive cars. Designer clothes. Jewelery. Art and antiques. Not to forget gambling.
And if that doesn’t suffice to explain their motivations, then remember these old chestnuts: “Money is how we keep score and know who’s winning.” “The one who dies with the most money is the winner.”
Sheesh…
Esther its not a foolish question. I assume he means American hackers, living in America, because we have the IRS and you might have to explain any deposit over 5,000 dollars which might cause a red flag.
But any criminal enterprise has money laundering schemes as part of the business. BK has had articles about this. Sometimes they even trick people through emails to work at home, to unknowingly launder money for them.
http://krebsonsecurity.com/2014/08/white-label-money-laundering-services/
The problem here is so obvious: banks leverage insurance. If the Feds didn’t allow the written off losses, you would believe banking would stop its losses. Instead, the numbers show a banker loses less to cybertheft than annual contracting and IT (likely outsourced).
But vulnerability will always be via the least paid, least informed, least bothered.
Banks need to be accountable. But their interest shows how much. (puns!)
>It’s worth noting that most of the crime gang’s infrastructure appears to be Linux-based.
Whilst this is hardly surprising can you explain how this has been observed?
Most platforms generate data packets using specific software libraries, and most of those libraries have particular quirks which are observable.
At the TCP/IP layer:
Long form: http://nmap.org/book/osdetect.html
Short (old) form: http://nmap.org/nmap-fingerprinting-old.html
At the useragent layer, assuming that an attacker uses an actual Browser / Mail Client / Document Editor (winword v. latex/openoffice), there’s often a useragent field (for documents, this is a generator field as opposed to the wire useragent field of transactions).
http://en.wikipedia.org/wiki/User_agent
http://www.w3.org/Protocols/rfc2616/rfc2616-sec14.html#sec14.38
http://word.tips.net/T000601_Determining_Word_Versions_of_Documents.html
When you “compile” an executable, just as when you generate a web-request/word document, your compiler tends to both include intentional signatures, and implementation specific fingerprintable bits.
One example:
http://stackoverflow.com/questions/727813/is-there-a-way-to-know-which-compiler-generated-a-static-library
It’s probably that the investigators also connected to the origin (of the original attack packets), or the destination (of Command / Control servers) and did finger printing on them.
Thank you for taking the time to give such a detailed and well written reply.
But should we really trust Anything kapersky
Says when it comes to banking since they are a Russian company and most of the banking attacks directed at Americana come from Russia.it’s especially disturbing when this company tries to single out the NSA.
I agree.
Chase actually offers businesses the same protections consumers get in regards to liability.
With that said, I can tell you from firsthand experience it’s much harder to keep a balance of keeping operations running as expected and securing them then it looks from the outside.
I have spent almost 30 years in IT, and the last decade I’ve been on the operations and security side of the things. I think every security guy (and team), should be forced to spend a day (or a week) in operations; they would probably be super stressed out and running back to their scanners. It’s one thing to say, “things have to happen this way,” as a security guy (which I am), and another to actually implement it without crashing systems. Add to this the poor quality of patches being pushed out, and it’s understandable why some systems don’t get patched, (some can’t be patched without breaking them).
I think operations and security teams need to work together better to come to a point where things get more secure and it doesn’t cause an undue stress on production systems. I realize security needs to come first and at the same time we need to think about the effect on operations and how to minimize it.
In an environment which makes money by-the-hour productivity is many times chosen over security.
It’s easy to be on the sidelines, but it’s bloody in the trenches.