As a greater number of banks in the United States shift to issuing more secure credit and debit cards with embedded chip technology, fraudsters are going to direct more of their attacks against online merchants. No surprise, then, that thieves increasingly are turning to an emerging set of software tools to help them evade fraud detection schemes employed by many e-commerce companies.
Every browser has a relatively unique “fingerprint” that is shared with Web sites. That signature is derived from dozens of qualities, including the computer’s operating system type, various plugins installed, the browser’s language setting and its time zone. Banks can leverage fingerprinting to flag transactions that occur from a browser the bank has never seen associated with a customer’s account.
Payment service providers and online stores often use browser fingerprinting to block transactions from browsers that have previously been associated with unauthorized sales (or a high volume of sales for the same or similar product in a short period of time).
In January, several media outlets wrote about a crimeware tool called FraudFox, which is marketed as a way to help crooks sidestep browser fingerprinting. However, FraudFox is merely the latest competitor to emerge in a fairly established marketplace of tools aimed at helping thieves cash out stolen cards at online merchants.
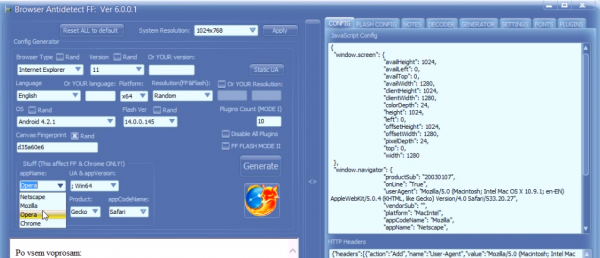
Another fraudster-friendly tool that’s been around the underground hacker forums even longer is called Antidetect. Currently in version 6.0.0.1, Antidetect allows users to very quickly and easily change components of the their system to avoid browser fingerprinting, including the browser type (Safari, IE, Chrome, etc.), version, language, user agent, Adobe Flash version, number and type of other plugins, as well as operating system settings such as OS and processor type, time zone and screen resolution.
The seller of this product shared the video below of someone using Antidetect along with a stolen credit card to buy three different downloadable software titles from gaming giant Origin.com. That video has been edited for brevity and to remove sensitive information; my version also includes captions to describe what’s going on throughout the video.
In it, the fraudster uses Antidetect to generate a fresh, unique browser configuration, and then uses a bundled tool that makes it simple to proxy communications through one of a hundreds of compromised systems around the world. He picks a proxy in Ontario, Canada, and then changes the time zone on his virtual machine to match Ontario’s.
Then our demonstrator goes to a carding shop and buys a credit card stolen from a woman who lives in Ontario. After he checks to ensure the card is still valid, he heads over the origin.com and uses the card to buy more than $200 in downloadable games that can be easily resold for cash. When the transactions are complete, he uses Antidetect to create a new browser configuration, and restarts the entire process — (which takes about 5 minutes from browser generation and proxy configuration to selecting a new card and purchasing software with it). Click the icon in the bottom right corner of the video player for the full-screen version.
I think it’s safe to say we can expect to see more complex anti-fingerprinting tools come on the cybercriminal market as fewer banks in the United States issue chipless cards. There is also no question that card-not-present fraud will spike as more banks in the US issue chipped cards; this same increase in card-not-present fraud has occurred in virtually every country that made the chip card transition, including Australia, Canada, France and the United Kingdom. The only question is: Are online merchants ready for the coming e-commerce fraud wave?
Hat tip to Alex Holden of Hold Security for bringing this video and innovation to my attention.
Update: The graphics linked to in the paragraph above on chip card transitions in other countries are from Doug King’s January 2012 white paper “Chip-and-PIN: Success and Challenge in Reducing Fraud” (PDF).




email me krebs, perhaps I can give you some more details about FFox as I own the software currently.
It would be cool if someone would make the same tool but open source to avoid NSA tracking
hi mister
I m searching fraudfox link or ( hugochavez , ex evolution seller ) email adress or informations to find a link to order ffox . Please reply to my email if you have more informations.thanks a lot
sorry for my english
regards
How soon until e-commerce sites start requiring history checks like credit report sites and the IRS, where you have to answer a series of questions about your history?
How soon until the digital criminal underground adapts to that?
Interesting video
I don’t whether they are ready, but it seems not to hard for the credit card company to check out card not present purchases where they have never bought there before and tie it to the phone number and address listed for the card.
But if they can make the merchant eat it the banks will do nothing even though they are the ones with the valid information.
Mike,
Usually the criminals have the cardholder’s name, number, and address for CNP transactions. Most banks do check those things, but in the end not much they can do when the criminal has all the valid info.
Mike you are wrong, banks still have to pay for the chargeback. A bank would rather just flat out decline any fraudulent transaction no matter who is liable for the loss. In either case they have costs. What is more likely is that with all the fraud they may be focusing in the issues that cost them more IE ( counterfiet) then items they can chargeback. End goal however is to stop all fraud.
Very interesting article!
At some point the banks are going to have to realize that CC’s need to be rotated like passwords. On a regular and aggressive schedule.
The banks are slowly moving to one time codes. EMV already does it with the iCVV, but soon the card number’ll be more commonly in the mix.. Is how Apple Pay works from what I understand, as it plugs into new system under development by card companies.
Wouldn’t be surprised if eventually we end up with cards like the old Paypal 2FA cards with the epaper display, where you press a button and fresh numbers pop up.
We just have to keep telling customers that the basics are important – check your statements and avoid using a debit card! I truely appreciate that the banks that I use in having the capacity to text me daily my balance information, so I know quickly if there is any weird activity happening.
One of my banks sends me a text message the moment my card is used. I usually get it even before I put my wallet back.
Another bank sends me daily updates, but I feel that isn’t nearly as beneficial as instantaneous messages.
Strangely, the bank that sends immediate updates is also the one that took almost two months before they applied the POODLE-TLS fix on the banking web site. The other banks applied the patch within days.
Re: “One of my banks sends me a text message the moment my card is used.”
My credit union provided that service when I went to Europe last summer for the VISA card they issue. My US-based iPhone chirped a message with the merchant, date-time and amount within seconds of every purchase I made in Germany, Austria and the Czech Republic and I could verify that the purchases were mine.
They claim, however, that the service is “not available” in the US. Does anyone have a clue why not (the customer service rep at the CU didn’t know)?
Thanks,
Any bank (or CU) could offer this service, but few do. Sending an SMS-message as soon as the transaction takes place is relatively basic.
However, it does require an investment (development) and maintenance. Simply a matter of cost vs. benefit.
Here in Sweden most online transactions have the banks in the loop to verify. Mechanism varies, but it boils down to various forms of second factor.
please keep in mind that “avoid debit” is not true in Europe.
and hope Americas (I mean continent) and US will follow Europe in some 3D tech adaptation as they do with chip.
Then you come on a company, that only uses a credit card, or debit cards for its business dealings. What are you supposed to do then? They will not accept cash, have no billing agency, have no local payment center, but it is a viable company. How would you pay them? Work exchange is no longer legal, and slavery isn’t a viable option, unless you have the name of a good slave.
You have to remember not all good companies accept all forms of cash, credit or payment. But bad companies have all options of payment accepted, because the sell the products they sell were bought for less then fair value. So let’s not judge.
My only problems, not just the bad guy uses no tracking software. And yes its built into the modern browser to be turned on by the user. So the bad guys found a stronger “bleach” to white out the tracks? Or it runs multiple times re-bleaching each touch or blocks the cookies better? Hmm, a two way firewall? Black ice?
Thank you for the article.
I feel my normal processes is not just paranoia now 🙂
For 10+ years now, any charge on my card out of my normal spending habits requires me to place a call to my CC company and authorize it. I have long felt this was worth while for the small burden.
With the predicted spike in online fraud rapidly approaching, why are so many online businesses waiting to implement two-factor authentication? Without the requisite device for the two-factor login, online fraud would seem much harder to accomplish. Some online companies offer two-factor for business customers, but not ordinary customers. To my dismay I’ve recently discovered that many bank and medical facilities not only do not offer two-factor authentication, but also their employees do not even know what it is.
They are wiating for congress to pass regulation. But it really needs to go further then that. As many posters describe. some banks send notification for suspicious activity or for certain amounts. Some don’t even bother.
You are so correct. You can set up a minimal amount to report at banks where this service is offered. This can usually be as low as $1 if you want to see people checking your credit line. This also means that EVERY transaction against your account will be reported, most often within minutes. If you don’t ask if this service is available, the bank might not tell you about it. Ask for it. You will have to modify your account(s) to do this and decide what is reported to you. It is worth the trouble, most especially if you are somehow time limited in reporting fraudulent transactions. It helps prove due diligence on your end. It is disappointing that some banks still do not offer this reporting service.
@Mahn: Gald this works for you.
When I transfered my personal domain to a non-US company, my cc flagged it as fraud and called (got my wife who was caught off guard). After calling them back and much convincing, they let it go through. I could see their point. Small charge (12.50 USD, over seas, etc.)
I recently renewed the domain and remembering the hassle, I called the number on the back of my card, provided company name, country, dollar amount, proved my identity and they thanked me for the heads up. Place the order and it was still f*’ing rejected. Wife gets called again. Why did I even bother? Vendor should have been listed as a previous authorized charge!
I had this same experience renewing, from the US, a domain name via Gandi.net (based in France) and Capital One (no foreign currency transaction fees). Capital One called a day after the transaction with an automated message that the charge had been declined. I called back, confirmed the transaction, and they said they couldn’t process it due to delay. After I asked how I could avoid the problem next time, they said even if I called in ahead of time to authorize the transaction, it would still be declined.
Automated fraud detection and alerting are pieces of the puzzle, but the system seems broken both for allowing fraud and for blocking legitimate transactions, especially when crossing national borders.
Chip card readers on computers and mobile devices so that online transactions can still be “card present”? Then we’re back to the problem of cloned cards (harder for chips than mag stripes but not impossible).
I’ve got to admit that my first thought was, “Where can I get this Antidetect.” Not for any illicit purpose, but I’d like something that makes me harder to identify on the interwebs.
And on the flip side of that, I’m not looking forward to bank & merchants digging ever deeper in to my PIID as they try to counter this trend. (Because of course there’s no chance of that uniquely identifying PIID being monetized, either as advertising by the “good guys” or identity theft by the “bad guys.”
My thought exactly. What a wonderful privacy tool this would be.
A lot of this browser detection is done through JavaScript. So the simplest and most effective solution would be to disable JavaScript. However, this will break the functionality of many sites that use JavaScript. Ideally there would be something that could block trackers but not useful scripts. Luckily, there are browser plugins that can do this.
The best is Ghostery, whose sole purpose is to block trackers. Adblock Plus is pretty good too, but its main focus is on blocking visible ads and not trackers per se. For example, it doesn’t block the Google Analytics domain by default. There’s also NoScript, which is a more thorough script blocker that gives you a lot of control over which websites are allowed to run scripts and plugins. It also makes the browser much more secure, preventing XSS and
drive-by downloads. However it can be very annoying to configure and requires knowledge about what different domains do (e.g. scripts from facebook.com are used for all sorts of things, but scripts from facebook.net are used exclusively for tracking).
Also there are other things you need to do to prevent browser fingerprinting. One is a user agent changer. A user agent is text that the browser sends to websites that contains various information about itself, such as the browser’s name and version along with the operating system’s name and version. You want something that can change this to a common user agent, such as Chrome on Windows 7, or better yet, a search engine spider user agent like Googlebot’s.
Also, disable cookies or delete them regularly. This includes Flash cookies.
I do all of the above except the user agent changer.
My concern is the user agent changer sending something that causes my browser to be unable to render the site properly.
Also, I wonder if user agent changers change enough each time so that trackers decide that it is different enough to indicate a different user.
trackers are done through cookies, so no, has nothing to do with the UA. You get an ID, and the tracking is attached to it.
That’s not always true: https://www.eff.org/deeplinks/2010/01/tracking-by-user-agent I expect this tracking to become more common as more people disable or regularly delete cookies.
A lot of this browser detection is done through JavaScript. So the simplest and most effective solution would be to disable JavaScript. However, this will break the functionality of many sites that use JavaScript. Ideally there would be something that could block trackers but not useful scripts. Luckily, there are browser plugins that can do this.
The best is Ghostery, whose sole purpose is to block trackers. Adblock Plus is pretty good too, but its main focus is on blocking visible ads and not trackers per se. For example, it doesn’t block the Google Analytics domain by default. There’s also NoScript, which is a more thorough script blocker that gives you a lot of control over which websites are allowed to run scripts and plugins. It also makes the browser much more secure, preventing XSS and
drive-by downloads. However it can be very annoying to configure and requires knowledge about what different domains do (e.g. scripts from facebook [dot] com are used for all sorts of things, but scripts from facebook [dot] net are used exclusively for tracking).
Also there are other things you need to do to prevent browser fingerprinting. One is a user agent changer. A user agent is text that the browser sends to websites that contains various information about itself, such as the browser’s name and version along with the operating system’s name and version. You want something that can change this to a common user agent, such as Chrome on Windows 7, or better yet, a search engine spider user agent like Googlebot’s.
Also, disable cookies or delete them regularly. This includes Flash cookies.
This is where the Host file comes in. It’s very easy block certain scripts/sites without blocking others. A growing number of sites will use a single site (usually for advertising) for analysis, stats, and tracking. Filter out THAT site and you can prevent alot of bad things.
This is great advice, only problem is that page you need to use functions on.
I agree scriptsafe and noscript drive me nuts. When i want to see a picture on a page, or video, or use a function on a webpage. I have to guess out of 30 domains which one to allow if I don’t know already. And then its so much for blocking my fingerprint.
I mean I guess to truly stop companies from doing this we would all have to do what the criminals and spies do and impersonate other people till it becomes unreliable and meaningless for them.
I use NoScript, Ghostery, and Sandboxie.
NoScript and Ghostery handles the meat of browsing. I do not mind their ‘difficult’ interaction, all though it hardly annoying.
Secondly, when I close my sandboxed browser, it deletes the contents every time.
If I just have to see that video on LiveStream/Break.com, I’ll shut down the browser which is set to clear out the sandbox, then fire it back up and temporarily allow Ghostery and NoScript. Easy.
After enjoying 12 seconds of insignificance, I’ll exit the browser, and sandboxie automagically deletes all content where I can start from square one.
Also, FYI, NoScript can remember what you allow, letting you surf your regularly scheduled websites with out discomfort. No more fear of Malvertising.
It’s very easy, and in my experience, ridiculously safe.
I know, and here I’ve been complaining about verizon putting id’s to track peoples phones over their wireless network.
And here is an article about browser fingerprints lol.
https://panopticlick.eff.org/ is worth a visit…
not hard to come by. on your average forum with leaked/cracked products. In fact it had been the mod of one community in which I partake, who cracked it.
search will do it.
Anybody else burst out laughing when they saw “cardrockcafe”?
nothing to see here folks, move alone.
you should’ve expected this!
Jon Marcus:
“I’ve got to admit that my first thought was, “Where can I get this Antidetect.” Not for any illicit purpose, but I’d like something that makes me harder to identify on the interwebs.”
Ditto! I would like to control who can track me.
For internet use I use a card that never leaves the house (and is locked away – I know the number etc.)
For cardholder present use I use a different card.
One card company noticed this “pattern” and where on to it v fast when a clone of my “internet” card was used in a cash machine.
Is it not good journalistic practice to note that you are on the advisory board of Hold Security?
I suppose it is, although as I’ve noted previously, I get nothing in return for my advice or participation on said board, which has frankly been next to nil.
All of the above suggestions for those that want to be less visible seem to be good, but for anyone who is wanting to see who is tracking them or to stop hackers and identity thieves, I would like to suggest checking out Disconnect Online Privacy Monitor.
Everything mentioned above is available plus a UI that is unbelievable in visually presenting who is tracking you. When our CIO came across this and started passing it on, it was amazing to see all of the features available. It basically is a VPN that secures the connection from prying eyes and more.
Firefox users can check out Request Policy, which uses a whitelist approach. NOTHING goes anywhere until you say it can. You will likely be amazed at how many websites call out to a huge assortment of ad/tracking sites, not to mention Facebook and Google, in the mere act of loading the HTML. No javascript required.
People annoyed with NoScript should avoid it, the setup is a major hassle.
How do I get to the “Request Policy” setting page/menu in Firefox? Tnx
There is a Firefox add-on called RequestPolicy, that might be what he was talking about. However, read the reviews first. The most recent review is titled :
“Annoying would be an understatement”
I have no experience with this add-on.
Certainly you know better than that … you get your name associated with them, and they get their name associated with you.
Without disclosure, it’s easy to start mutual admiration societies to boost your image; it happens in academia all the time.
How difficult can it be for the card issuers to generate one-time card numbers for inline purchases? Inconvenience shouldn’t be a big factor as the consumer is already online. Have a secure widget which pops out a new number for each purchase and the crooks have no way to submit a charge against my account.
There must be a knick in this idea, though, or I suspect it would have been done.
I recall seeing one-time card numbers several years back. Where did they go?
Citibank still has this feature, with some cards. Unfortunately it does require Flash.
The thing is, the purchaser really needs to care to make it a worthwhile feature: same with daily balance e-mails, etc. It would be very easy to say, “I don’t care; I’ll wait for my end-of-month statement and just dispute any charges which are fraudulent.” because the direct individual incentive is not there. You dispute, don’t need to pay the charge, and move on.
But I don’t like cities, past policies, who else? The list just got smaller, cities bought out the competition. They have spread it out overseas and as a business option, but I still won’ t use cities as an business.
As one of the people responsible for the WOW64 annotation in Gecko, I’m kinda* surprised that a fraudster would at it to Chrome for Android, since it should not exist there.
https://msdn.microsoft.com/en-us/library/ms537503%28v=vs.85%29.aspx
WOW64 – A 32-bit version of Internet Explorer is running on a 64-bit processor.
(Gecko uses the same indicator, for when 32-bit Gecko runs on a 64-bit processor w/ a 64-bit version of Windows.)
Note that Android is Linux, so it should look like this:
Mozilla/5.0 (Linux; Android 4.0.4; Galaxy Nexus Build/IMM76B) AppleWebKit/535.19 (KHTML, like Gecko) Chrome/18.0.1025.133 Mobile Safari/535.19
*ok, I’m not very surprised, it just shows that the Fraudster doesn’t understand and the site doesn’t care.
With the chips on all new cards, why don’t we see merchant accepting transaction from a computer equipped with a smart card reader? USB readers can be bought for less than $15 and will really improve the security of online transactions as the buyer will need to physically insert the card in his computer reader.
Even better would be to have companies with chip-readers actually enable them.
Home Depot was hacked rather badly a while ago. Many of their stores have readers that are chip-ready. But HD has NOT enabled them !! If you insert your chip-card, it tells you to swipe the card (of just ignores it).
You might think that HD would be just a little sensitive to this – but no. Their corporate head is still firmly planed in the nether regions.
Now I’m with HD here.
Banks are not close to be ready for chip-and-pin or chip-and-signature. They haven’t even ***started*** replacing all existing cards. Let alone that their backends are ready.
So enabling chip right now as a retailer guaranteed to make you the test-object for all those banks and experience all the first hand bugs. In this case I think HD is right to wait for the banks to signal they are ready.
A different story is of course a big fastfoot chain in our area just installing brand new computer terminals where you can order fom the screen … but having no chip-and-pin/signature capability. They’ll basicly have to eat all the fraude or replace/upgrade all of them later thsi year.
A few months ago I received an unsolicited replacement credit card from my credit union with the embedded chip. So maybe the cards aren’t out there in volume yet, but they are out there.
In a world where many smartphones now have fingerprint scanners for security purposes, should we perhaps adopt a different metaphor to avoid confusing browser digital fingerprints with the more literal actual digital fingerprints? digital footprint? electronic lipstick mark? cyber semen residue?
Your really Scraping the barrel with this story Brian . This tool is so old .. And who is your demonstrator is he a cop ? His is committing a crime ( by buying stolen credit cards number ) Should we report him to the police ?
Alas, it only took 43 comments to get my first fraudster? I’m slipping for sure.
True,
But it is still one of the best reasons to keep reading your stuff, at least for me.
Maybe THEY are slipping?
Keep poking anyway.
That’s the more interesting and noteworthy part of this whole thing.
In spite of all the updates and all the upgrades….
In spite of all the attention given to all the new stuff that gets churned out on a regular and timed basis….
There are problems that just never get fixed. We will get told so very clearly how this update or that update will fix this problem or that problem. We are expected to follow like sheep with our “auto update” mechanism turned on. We are expected to believe that the next iteration of os is safer than the last. But there are issues that just never really get takin care of.
I’m not seeing things get better (as far as safety or security); I’m seeing things dramatically getting worse. AV software isn’t worth using just simply because it will not catch what it needs to but what it will do is slow down the machine. This is a big part of why people are going with Ipads and handing all to Apple to deal with. The problem with that is that Apple isn’t all that safe either.
There are certain realities to this technology that people refuse to accept it seems. Things like the fact that email is NOT private. Nor is any of your text messages over your phone. You can do things with your computer to hide your tracks but there is no way to remove what goes onto a webserver for a site that you visit while surfing the net. This means that if your IP gets recorded to that server when you go there, There is NOTHING you can do to delete that information. This post of mine getting put to this website will likely stay on this webserver in perpetuity. Nothing I could ever do will change that after I click submit.
These look old, broken, and not very good in the first place. Tor Browser does a better job for free, and if you’re a fraudster needing a proxy in a specific location, surely it’s not hard to get one.
Right, because no ecommerce merchant would ever block a Tor node.
Frankly, I’d be surprised if anyone who cared about stopping fraud *wouldn’t* block Tor nodes from shopping. Not saying people using Tor are all bad, etc., just saying there has be an awful lot of fraud coming to merchants via Tor.
Oh, there’s a ton of it. You’d be amazed how many DON’T block Tor. Also, Brian, I meant something more along the lines of chaining Tor Browser + another proxy.
I talk to a few small-time fraud kiddies, and they love Tor and cheap SOCKS4/5 proxies (vip72, proxybonanza, etc.) The browser fingerprint obfuscation is provided by Tor Browser and the location-specific IPs are provided by the proxies.
Are you hot ?
I surmise that these new tools are STING operations by law enforcement. It isn’t beyond them to plant them online and if they aren’t doing this they should.
I can’t say it enough. Use CASH as much as possible to reduce the card theft.
Thank you for posting the video, I learned from it as folks who try to prevent fraud are not very good at the other side for sure, I tell people that about me all the time.
I’ll add usual two cents here on how the data selling epidemic in the US just pushes the hacking to no limit. I also told all that “repackaging” our data is a big deal too so the smarter hackers can resell stolen data to look like new legit data as well, Anthem victims, think about that one as they have 80 million files and can make a lot of money and sit on the data for a while too. Maybe the credit card as we know it will die one day. Also take a look at what the news media is now beginning, to charge you 20 cents to read “some” articles and how do you pay, with a credit card.
We get a two-fer here as the credit card companies get all that data to sell so companies can score you and conjure up all types of behavioral analytics about you and sell that too.
http://ducknetweb.blogspot.com/2015/03/major-us-newspapers-sign-up-and-invest.html
So what about that question you asked “ Are online merchants ready for the coming e-commerce fraud wave?”…
In addition I explained too how this could be an article written by a bot and how the jounobots can actually participate in “rigging” markets too, it all ties together as the credit card transaction is how the papers want to get their money, but the credit cards get more with data added in to sell and how long before someone hacks the papers next?
Why is anyone using browser fingerprinting for that? It seems a very unreliable way to detect fraud in any case (countermeasures have existed since forever), and I think everyone should use whatever measures necessary to avoid fingerprinting anyway, since the one thing that fingerprinting is really useful for is spying on users.
There’s for example the Chameleon browser extension which is a very good fingerprint obfuscator. Unfortunately it’s unusable with Gmail and other Google’s free services, otherwise I would keep it always on.
I read about this back in January I think it was first talked about. A lot of details were unclear then.
http://www.csoonline.com/article/2871248/fraud-prevention/this-tool-may-make-it-easier-for-thieves-to-empty-bank-accounts.html
Eventually the good will overtake the evil in technology. But its probably going to take some time to do so !
Omg Starfall
Hi
I WANT THIS TOOL TO AVOID NSA TRACKING
WTF