When your credit card gets stolen because a merchant you did business with got hacked, it’s often quite easy for investigators to figure out which company was victimized. The process of divining the provenance of stolen healthcare records, however, is far trickier because these records typically are processed or handled by a gauntlet of third party firms, most of which have no direct relationship with the patient or customer ultimately harmed by the breach.
I was reminded of this last month, after receiving a tip from a source at a cyber intelligence firm based in California who asked to remain anonymous. My source had discovered a seller on the darknet marketplace AlphaBay who was posting stolen healthcare data into a subsection of the market called “Random DB ripoffs,” (“DB,” of course, is short for “database”).
Eventually, this same fraudster leaked a large text file titled, “Tenet Health Hilton Medical Center,” which contained the name, address, Social Security number and other sensitive information on dozens of physicians across the country.
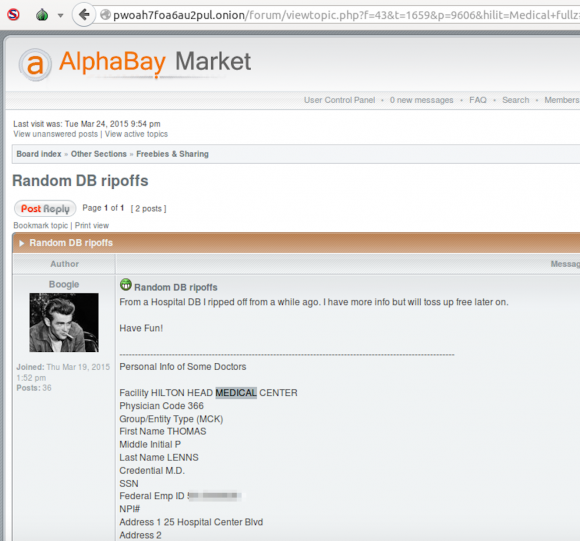 Contacted by KrebsOnSecurity, Tenet Health officials said the data was not stolen from its databases, but rather from a company called InCompass Healthcare. Turns out, InCompass disclosed a breach in August 2014, which reportedly occurred after a subcontractor of one of the company’s service providers failed to secure a computer server containing account information. The affected company was 24 ON Physicians, an affiliate of InCompass Healthcare.
Contacted by KrebsOnSecurity, Tenet Health officials said the data was not stolen from its databases, but rather from a company called InCompass Healthcare. Turns out, InCompass disclosed a breach in August 2014, which reportedly occurred after a subcontractor of one of the company’s service providers failed to secure a computer server containing account information. The affected company was 24 ON Physicians, an affiliate of InCompass Healthcare.
“The breach affected approximately 10,000 patients treated at 29 facilities throughout the U.S. and approximately 40 employed physicians,” wrote Rebecca Kirkham, a spokeswoman for InCompass.
“As a result, a limited amount of personal information may have been exposed to the Internet between December 1, 2013 and April 17, 2014, Kirkham wrote in an emailed statement. Information that may have been exposed included patient names, invoice numbers, procedure codes, dates of service, charge amounts, balance due, policy numbers, and billing-related status comments. Patient social security number, home address, telephone number and date of birth were not in the files that were subject to possible exposure. Additionally, no patient medical records or bank account information were put at risk. The physician information that may have been exposed included physician name, facility, provider number and social security number.”
Kirkham said up until being contacted by this reporter, InCompass “had received no indication that personal information has been acquired or used maliciously.”
So who was the subcontractor that leaked the data? According to PHIprivacy.net (and now confirmed by InCompass), the subcontractor responsible was PST Services, a McKesson subsidiary providing medical billing services, which left more than 10,000 patients’ information exposed via Google search for over four months.
As this incident shows, a breach at one service provider or healthcare billing company can have a broad impact across the healthcare system, but can be quite challenging to piece together.
Still, not all breaches involving health information are difficult to backtrack to the source. In September 2014, I discovered a fraudster on the now-defunct Evolution Market dark web community who was selling life insurance records for less than $7 apiece. That breach was fairly easily tied back to Torchmark Corp., an insurance holding company based in Texas; the name of the company’s subsidiary was plastered all over stolen records listing applicants’ medical histories.
HEALTH RECORDS GET AROUND
Health records are huge targets for fraudsters because they typically contain all of the information thieves would need to conduct mischief in the victim’s name — from fraudulently opening new lines of credit to filing phony tax refund requests with the Internal Revenue Service. Last year, a great many physicians in multiple states came forward to say they’d been apparently targeted by tax refund fraudsters, but could not figure out the source of the leaked data. Chances are, the scammers stole it from hacked medical providers like PST Services and others.
In March 2015, HealthCare IT News published a list of healthcare providers that experienced data breaches since 2009, using information from the Department of Health and Human Services. That data includes HIPAA breaches reported by 1,149 covered entities and business associates, and covers some 41 million Americans. Curiously, the database does not mention some 80 million Social Security numbers and other data jeopardized in the Anthem breach that went public in February 2015 (nor 11 million records lost in the Premera breach that came to light in mid-March 2015).
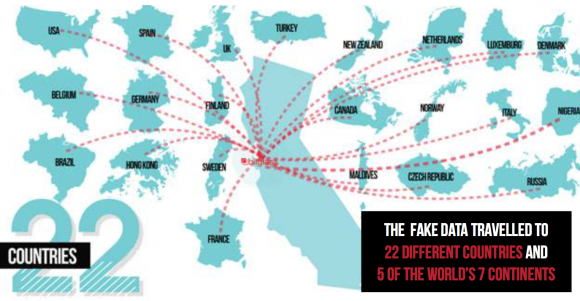
Sensitive stolen data posted to cybercrime forums can rapidly spread to miscreants and ne’er-do-wells around the globe. In an experiment conducted earlier this month, security firm Bitglass synthesized 1,568 fake names, Social Security numbers, credit card numbers, addresses and phone numbers that were saved in an Excel spreadsheet. The spreadsheet was then transmitted through the company’s proxy, which automatically watermarked the file. The researchers set it up so that each time the file was opened, the persistent watermark (which Bitglass says survives copy, paste and other file manipulations), “called home” to record view information such as IP address, geographic location and device type.
The company posted the spreadsheet of manufactured identities anonymously to cyber-crime marketplaces on the Dark Web. The result was that in less than two weeks, the file had traveled to 22 countries on five continents, was accessed more than 1,100 times. “Additionally, time, location, and IP address analysis uncovered a high rate of activity amongst two groups of similar viewers, indicating the possibility of two cyber crime syndicates, one operating within Nigeria and the other in Russia,” the report concluded.




Good post and as hackers keep progressing, it gets harder to find them and this is the point I made about the Anthem Breach. I had a hacker after reading my post about “repackaging” data tell me on Twitter that there’s dark Unicorns that exist out there and know how to work data just like the pros, which should not be a surprise to anyone, really, but when they come out and tell you such I think we should pay attention and not be bliss.
What if that “Tenet” list was out there and didn’t say “Tenet”? That’s the scary part as the bad guys don’t “have” to list a source and then it gets harder to find of course and our data goes up for bid on the dark web and can even be repackaged to be something else and show up on legitimate web sites selling data but it’s really stolen data without any inkling of where it came from. Repackaging is a big deal for concern. The folks at the World Privacy Center and myself talk about that quite a bit. The hackers could sit on it for quite a while before they go into the selling business and if they can disguise the data as not being stolen, they can make more money with it looking legit. I gave an example of a site that puts information up for bid and sale and there’s not much in the way of boundaries at all as such sites just take a little commission when the sale is made. There’s already some healthcare stuff up there and more, but so far it doesn’t appear to be anything stolen from what I see and I could be wrong as well.
http://ducknetweb.blogspot.com/2015/02/anthem-data-breachcrooks-want-to-sell.html
Can you explain what you mean by non-stolen information that is listed for bid or sale? Are you saying that the originator of the data (for example a healthcare organization) is putting up the data from their own systems for sale/bid? This is in reference to:
“There’s already some healthcare stuff up there and more, but so far it doesn’t appear to be anything stolen from what I see and I could be wrong as well.”
It’s reference to data being sold as valid sourced when actually it has been stolen and repackaged as marketing data.
Not sure why since the marketing data is much more detailed, accurate and given freely each time a smart phone farts off another ad.
There are folks who legitimately sell personal data, Uber, Facebook, Google, and a list of ‘ethical’ and a bunch of not so ethical companies.
It’s scary.
There are a whole laundry list of questions related to data sharing. http://wp.me/p5PMQN-hv
From the “If it sounds too good to be true, then it probably is” department:
“The researchers set it up so that each time the file was opened, the persistent watermark (which Bitglass says survives copy, paste and other file manipulations), “called home” to record view information such as IP address, geographic location and device type.”
Seems like magic. More likely just marketing hype.
Doubtful that said “watermark” would survive certain simple “file manipulations” such as a conversion to comma- or tab-separated values. Or a run through Excel with macros disabled. Or a good firewall that blocks unauthorized outbound traffic.
So only the careless are captured; the pros survive to hack another day.
Esther D wrote:
“From the “If it sounds too good to be true, then it probably is” department:
…
So only the careless are captured; the pros survive to hack another day.”
While your point that pros may have circumvented the web bug is valid, doesn’t the underlying result of the planted data reaching 22 countries deserve more than a snide and inaccurate remark about being ‘too good to be true’?
Snide, perhaps. Since you’re not being at all snide, perhaps you could expand somewhat on the “Inaccurate” part?
Survives “some” copy and paste.
If I take a standard web bug — the kind we’ve been complaining about since Yahoo introduced theirs — and pop that in every cell, the web bug will travel with the spreadsheet.
If I copy and paste the cells on a desktop operating system to an app that supports the spreadsheet’s clipboard format, the webbug links will survive. If there isn’t a proxy blocking outbound traffic, if an app level firewall isn’t used to cut the app off from the external network, sure — it’ll survive copy and paste.
If I copy and paste into an app that wants TSV or CSV, and requests that format then the webbug will be removed. If I save to TSV or CSV, the webbug will be removed.
So what you’re relying on here is the recipient of the spreadsheet opening it in a standard app (Open Office, Excel, etc.) and then copying and pasting from that app to another without actually looking at the content of the files.
But sure, that’ll survive copy and paste for the most part.
Forensic watermarking that stays with the content irrespective of how it is transmitted is relatively straightforward and there are even some good off the shelf products, such as NexGuard, that will enable this.
Finding and stripping the watermark can be very hard, depending on the product used to encode it.
No magic involved at all, and certainly no marketing hype.
Agreed. Forensic watermarks DO work. But IF AND ONLY IF you can actually CATCH the perp in POSSESSION of the watermarked file. Then you can use the watermark to PROVE that it’s YOUR file, and that the perp could have only gotten the file from YOUR server, etc. But if you CANNOT locate the perp using independent means, then a forensic watermark is useless, because it does NOT give you a breadcrumb trail that would help you FIND the perp.
But that’s NOT what’s being discussed in the article, is it? The claim of this company is that they have a technology that can PHONE HOME so that you do NOT have to catch the perp in the act. And further, that said technology is difficult to defeat by ordinary means. As I and others have pointed out, said claim is likely to be false, or at least highly exaggerated.
So I stand by my original statement. If this technology really works as claimed, then it must be some kind of “magic”. And if it does NOT work as described, which seems quite likely, then the claims about it must be “marketing hype”, pure and simple.
You’d think criminals would be the most suspicious….
Easy to isolate via VM or firewall control.
Easy to cleanse via CSV export.
But we have to worry about both smart and dumb criminals.
Good and scary article, thanks. Just for information, I think that there is a problem with the map of spain.
Spain pwns France!
Well spotted.
Thank you. Glad to know I wasn’t going crazy. I was just about to go looking at a map.
Maybe redact your last AlphaBay login time and Dr Lenns’ PII?
ssntracking and recordssn have my address listed with someone else’s ssn. There was also another website but I don’t see it any more.
It is time for people to stop pretending that having names and addresses and phone numbers showing up in search results is a good thing. It was a nice experiment while it lasted, but the past year has proven that it cannot be done successfully.
Wow, this was a real good article
the fundamental problem lies in the use of symmetric identification data, such as name, address, date of birth, soc.sec.nr, mother’s maiden name … &c
these data are quickly stolen and placed for sale on the “darknet” and elsewhere — as Mr. Krebs has pointed out
the solution is to get away from using the symmetric identification data
to do this we all need to learn to use public key encryption — in which you can verify your identity in public and at the same time retain control of your credentials
contrary to myth being spread by the public media public key encryption is not difficult. it can be distributed as packaged technology making it no more difficult to use than any ordinary password.
it must be noticed that a secure o/s is required for *any* hope of security where a secure o/s is one which will not allow itself to be compromised by the activity of an application program — whether by error or by intent.
Amen, Mike. Well said.
That is only part of it. Ultimately most companies find it cheaper by offloading security for things to smaller companies/contractors. In their mind, they are saving money and its not their problem if other people’s info is stolen and used.
Until “we the people” make it more painful for doing it cheap or not doing it at all, nothing will change. Its about avoiding costs and making a bonus check bigger.
For example here is the Sony Guys telling CIO magazine 2006, “It’s a valid business decision to accept the risk” said Jason Spaltro of Sony.
See what happened, it took a while but when they got hammered it was an acceptable risk and cost avoidance win.
This guy got a promotion for thinking like this, until “we the people” stack on the penalties, nothing will change in security land.
It is a valid business decision to accept risk. Security is all about accepting some risks. Perhaps Sony made the wrong decision. Did it cost them more to pay reperations, etc, than it would have to secure their systems? I have no idea.
The real problem comes when that decision isn’t made at all and the risk is implicitly taken on without any one knowing about it.
Companies don’t understand privacy and security rights because they are made up of people that don’t understand privacy and security rights. I posted two articles on my blog last week that detail how my rights have been invaded or not invaded (because I intervened) and what I did about it.
Write letters to CEOs, boards of directors, and send copies to regulators! Explain what you want, why you want it, and the consequences–good or bad–that will follow. Vote with your money! Tell other people what happened.
In other words, ‘shared secret’ is an oxymoron.
It’s not exactly a new idea, but still worth implementing.
http://www.amazon.com/Translucent-Databases-Peter-Wayner/dp/0967584418
I totally agree Mike, but until we impose some penalties on creditors that issue credit to the ‘wrong’ person, based on bad / stolen data there’s no incentive for them to ensure they get it right.
You are right on both counts.
Now how do we make this happen?
A secure O/S. Sigh. That’s the hard part. Slowly we are getting there with Intel’s trusted boot (TXT/TPM) and possibly leveraging off of microprocessor support for virtualization (like VMware) where we can protect trusted code in a memory page from being tampered with and with hardware support for cryptography (like Intel’s AES-NI). But we still have a long way to go.
HIPAA requires notification of a breach when personal health information (PHI) is disclosed.
Anthem insists that no PHI was accessed; hence no HIPAA reported breach and not on your list of HIPAA breaches from DHHS.
Premara may claim the same.
Both Anthem and Premera reported their respective breaches to HHS, as required by HIPAA and HITECH.
The Anthem incident was submitted to HHS on March 13, 2015.
The Premera incident was submitted to HHS on March 17, 2015.
(I believe others have weighed in as well.)
Reported to HHS as required under HITECH (and data security re Meaningful Use), yes.
A health insurance account identifier isn’t (necessarily, anyway) protected health information under HIPAA.
Reported to HHS as a breach doesn’t necessarily mean reported as a HIPAA breach, which carries some other (additional) penalties, potentially quite hefty.
Strictly speaking, Hong Kong isn’t a country. It’s part of China. Likewise I’m sure that Ireland are ecstatic at being part of the UK. Geography and clip art are obviously not strong points.
What I don’t understand is how Anthem can say that it wasn’t a HIPAA breach because no PHI was exposed when they clearly stated which items had been disclosed. They considered those items PII, but those items are protected identifiers under HIPAA also (straight from anthemfacts.com=names, dates of birth, Social Security numbers, health care ID numbers, home addresses).
The elephant in the room that nobody in business or healthcare seems to want to touch is that everyone is convinced there are all these benefits to society by digitizing and making all sorts of patient info available online and having all these plans for complex technological interactions with data, yet the industry as a whole is completely unprepared to protect our data. They are and for the foreseeable future, they will be, completely unprepared, industry wide. The commonly held vision of the future is not at all likely to be delivered with security and accountability. Companies who get breached whether right or wrong will continue to play the victim and pretend outcomes were not foreseeable.
It’s NOT just the future. The PAST wasn’t “delivered with security and accountability”, either, as those of us who worked with paper medical records know only too well. The difference is that computerization has made everything faster, easier and more efficient for EVERYONE… including (unfortunately) those who do NOT have our best interests at heart.
I’ve gotten notified about so many data breaches over the years affecting my own information, and I’m sure there were many more that went undetected. At what point has the available data been milked so thoroughly that it’s no longer worth paying for? And why does anyone extending credit treat possession of that data as a way to confirm someone’s identity?
France v Spain: The image appears to be France, the name is shown is Spain. Is the image wrong and it is really Spain? Or, is the name wrong and it is really France? A good reminder that there are no editors on the mis-information superhighway.
Jonathan
Since both France and Spain appear on the list, it hardly matters.
Tell that to the Spanish, who are probably wondering why they are all now speaking French. 🙂
BK – please remove or obscure the name of Dr. Lenns from the above. A name is personally identifiable information (PII) and appears in contradiction of your own privacy policy.
Personally identifiable information
We do not share personally identifiable information with third parties, with one limited exception: we may disclose personally identifiable information about you if we have a good faith belief that doing so is required by law, such as pursuant to a subpoena or other judicial or administrative order.
http://krebsonsecurity.com/wp-content/uploads/2010/04/kospp.pdf
Jonathan,
It isn’t PII as it is publically available information that has been released as such by the center. The center advertises the MD’s that work for it on their website. So Brian has done it right, as pretty much always.
People need to refuse to provide SSNs to healthcare providers. And prohibit your HR department from sharing it unless required by law.
Ted,
Is this sarcasm?
Don’t give your “Social Security” number to your healthcare provider.
How do you think the SSN came into being in the first place? This is what it was designed for.
But if it is sarcasm, it’s brilliant.
Eh? The SSN was originally intended ONLY for use by the SOCIAL SECURITY Administration, IRS, and a bit later, MEDICARE. It says so right on the older cards: “not for identification”.
Problem started in the 50’s and 60’s when there was a need for some universal identifier, but nothing else was available. Government let first the banks and later just about everyone get away with using the SSN for ID. With the benefit of 20-20 hindsight, that probably wasn’t such a good idea.
And you DO have the right to refuse to give your health care provider(s) your SSN. But it’s moot, because they will probably just get it from your insurance carrier or another medical provider. So it’s quite likely that your SSN will be in ALL of your medical records at ALL of your providers and insurance carriers (not to mention a whole bunch of third-party billing processors), whether you gave it to them or not, ready and waiting for some ne’er-do-well to come along and grab it.
In Canada, the Social Insurance Number, by law, cannot be required by federally-incorporated companies – like banks. I believe most provincially-incorporated companies also follow suit.
My office does not collect social security numbers on our patients. I also refuse to put my social security number on the forms at my doctor’s office and they do not have a problem with that. All your doctor needs is your name, birthdate and insurance policy group and ID numbers to be able to bill. It may be different if you have Medicare or Medicaid.
Very good news, it is noteworthy that forums are offering crime 90 million personal register.
United states I have no doubt that he or they have something to do with such crimes .
http://crdclub.so/showthread.php?t=24917
Docs still earn too much, why not rip them off?
Sweeping regulations are in order, but they won’t happen. Sucks that non-security people constantly find themselves in charge of massive amounts of sensitive information. Then, when something goes awry, the big-name companies can blame the third-party. This way, no one really has to take responsibility for anything.
Who regulates the regulators?
No matter how careful you are in protecting yourself against hackers, they are going to get you one day if they haven’t already.
I received a notice from Premara about the breach of their data. They offered 2 years of ID protection for free. My attempt to sign up online failed. My attempt to sign up by phone failed. Finally, I was told a security code would be mailed so I could access my Experian credit file. I never received the code. Contacted them again by phone and a supervisor overrode the system somehow (giving her access to my credit report) so I could access it. At least for now, my credit report looks fine. I check my bank accounts and credit card accounts regularly now.
I expect to learn at some point that my identity has been stolen. I’m not at all confident in anything.
No one should be confident about anything, seems almost everyone, including me, is having problems with ids and credit.
The system is falling apart. In the past year, we have seen the beginning of the end of the internet.
This should be a lesson to health industries. Never let your clients record stay vulnerable to hacks. So many people are now doing fraudulent activities in order to access benefits that are meant for others who are most in need. Hope this will be a wake-up call and spur the health sector to do something about their network security.
This scenario is exactly why, back in the heyday of promotion of EHRs about 7-10 years ago, I sent a registered letter to a contractor of my employer’s health care insurance carrier demandingt that they remove all EHRs about me and my family from all their servers immediately or I was going to file both a HIPAA violation report with the federal government about the contractor and an ethics violation report with my employer about the HR employee who ramrodded the activity, placing our records on an internet-exposed server without first seeking my permission
The original response was it would take 6 weeks to remove them but when I informed them I was ready to file complaints, they were all removed in less than 24 hours.
Now, do I believe all of my and my family’s EHRs are safely removed from where they could be easily stolen? Of course not. I know my employer’s insurance carrier still maintains our EHRs on Internet-exposed servers. In fact we were recently informed that >possibly< some of my dependents' information may have been stolen.
Don't I think some miscreant could break in to the physical records of my insurance and health care insurance providers and steal it anyway? Oh, sure I do. But I'm more confident of the security of our physical records from overseas hackers than I would have been if they were digitized and splattered all over various unknown internet-exposed servers. It's not like a Russian is going to fly to my hometown or hire a hometown local to steal my records.
Oh, they told me, trying to mollify me and convince me it was safe, we use SSL to protect your records, they said. They're completely safe they said.
The real issue with stolen healthcare data, as well as stolen SSNs, are that you can’t change that information to protect yourself going forward. You’re stuck with your information being breached and in public. The government will not change your SSN, nor will you be able to change most of your PII. Once its out, its out, and the most you can do is try to detect and react faster than damage can occur.
I believe that if you can show identity theft & criminal use of your SSN, the US govt will issue you, grudgingly, a new SSN.
It’s actually a great and helpful piece of info. I’m satisfied that you simply
shared this helpful information with us. Please stay us up to date like this.
Thank you for sharing.