In October 2014, KrebsOnSecurity examined a novel “replay” attack that sought to exploit implementation weaknesses at U.S. financial institutions that were in the process of transitioning to more secure chip-based credit and debit cards. Today’s post looks at one service offered in the cybercrime underground to help thieves perpetrate this type of fraud.
Several U.S. financial institutions last year reported receiving tens of thousands of dollars in fraudulent credit and debit card transactions coming from Brazil and hitting card accounts stolen in recent retail heists, principally cards compromised as part of the October 2014 breach at Home Depot. The affected banks were puzzled by the attacks because the fraudulent transactions were all submitted through Visa and MasterCard‘s networks as chip-enabled transactions, even though the banks that issued the cards in question hadn’t yet begun sending customers chip-enabled cards.
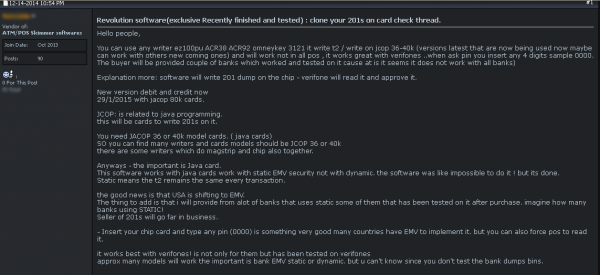
Seller in underground forum describes his “Revolution” software to conduct EMV card fraud against banks that haven’t implemented EMV fully.
Fraud experts said the most likely explanation for the activity was that crooks were pushing regular magnetic stripe transactions through the card network as chip card purchases using a technique known as a “replay” attack. According to one bank interviewed at the time, MasterCard officials explained that the thieves were likely in control of a payment terminal and had the ability to manipulate data fields for transactions put through that terminal. After capturing traffic from a real chip-based chip card transaction, the thieves could insert stolen card data into the transaction stream, while modifying the merchant and acquirer bank account data on-the-fly.
Recently, KrebsOnSecurity encountered a fraudster in a popular cybercrime forum selling a fairly sophisticated software-as-a-service package to do just that. The seller, a hacker who reportedly specializes in selling skimming products to help thieves steal card data from ATMs and point-of-sale devices, calls his product “Revolution” and offers to provide buyers with a list of U.S. financial institutions that have not fully or properly implemented systems for accepting and validating chip-card transactions.
First, a bit of background on chip-based cards is in order. Chip cards are synonymous with a standard called EMV (short for Europay, MasterCard and Visa), a global payment system that has already been adopted by every other G20 nation as a more secure alternative to cards that simply store account holder data on a card’s magnetic stripe. EMV cards contain a secure microchip that is designed to make the cards very difficult and expensive to counterfeit.
There are several checks that banks can use to validate the authenticity of chip card transactions. The chip stores encrypted data about the cardholder account, as well as a “cryptogram” that allows banks to tell whether a card or transaction has been modified in any way. The chip also includes an internal “counter” mechanism that gets incremented with each sequential transaction, so that a duplicate counter value or one that skips ahead may indicate data copying or other fraud to the bank that issued the card.
It appears that the Evolution software is designed to target banks that are in the process of architecting their payment networks to handle EMV transactions, but that nevertheless aren’t yet properly checking the EMV cryptogram and/or counter for these transactions. It also seems that some banks have inexplicably lowered their fraud controls on EMV transactions, even though they are not yet taking advantage of the added security protections offered by chip-based cards.
“The reason I think they bother to fake EMV transactions is that they know the EMV card issuing banks relax their fraud controls on them and don’t have it implemented properly and therefore they do not properly check the dynamic EMV data,” said Avivah Litan, a fraud analyst with Gartner Inc.
That’s precisely what the fraudster selling Evolution points out in his somewhat awkwardly-worded sales thread for his product, which he said relies on Java card software capable of writing to chip and mag-stripe based cards. Java Card refers to a software technology that allows Java-based applications (applets) to be run securely on smart cards and similar small memory footprint devices. Java Card is the tiniest of Java platforms targeted for embedded devices, and was originally developed for the purpose of securing sensitive information stored on smart cards.
“The good news is that USA is shifting to EMV,” he writes. “ This software works with Java cards work with static EMV security not with dynamic. Static means the [counter] remains the same every transaction. The thing to add is that I will provide from a lot of banks that uses static some of them that has been tested on it after purchase. Imagine how many banks using STATIC!“
This same fraudster appears to be the operator of an online store called “Last Carding,” which sells stolen credit cards and includes a number of tutorials on how to conduct card fraud. The crook running this site says he’s online twice a day, but that he takes Sundays off. Interestingly, the clock on his Web store says he operates on Central America time (-06:00 GMT).




> Java-based applications (applets) to be run securely
Even though it is a completely different security problem from Java in a browser, I had to laugh at the words ‘Java’ and ‘secure’ in the same sentence.
Good to see I wasn’t the only one who got a good little chuckle out of that.
I’m not sure you understand the difference between Java as a programming language, and Java implementation..
Indeed. Java is a highly safe and secure programming language everywhere *except* inside web browsers. It’s very hard to hack *into* programs written in Java. The problem is that Java is way too “over-powered” for a web-browser environment. A Java program is just like an .exe…it can mess with pretty much everything on your computer. For writing “real programs”, which you install on your computer intentionally and mean to have full access, it’s great. But this makes the ability to embed “applets” – essentially full Java programs (with all the rights and privileges thereof) – into a web page just as dumb as opening .exe attachments on strange emails.
This is why Brian always suggests “ditch Java if you don’t need it, but if you do, at least unplug it from your browser”. Unplugging Java from the browser removes the security hole (applets) while retaining the ability to install and run Java programs *outside* the browser – that is, for software you’d intentionally allow on your computer by running an .exe. In this capacity, Java is highly secure – that program you just installed will be much harder to hack than if it were written in an “unsafe” language like C or C++.
As an example, the OpenOffice.org office suite (a free competitor to Microsoft Office) is written largely in Java. This makes it resilient to most of the attacks that Office (written in a combination of C and C++) is vulnerable to. OpenOffice requires Java to be installed on your computer, but it does not require it to be enabled in your browser – because it’s not using the notorious “applets” feature.
In this light, Java is an excellent (indeed, ideal) choice for programming a chip-enabled credit card. It doesn’t guarantee that the implementation itself will be airtight (the developers still have to get all the crypto right, which is a challenge in itself), but it does do a lot to head off attacks *on the card firmware itself* – for instance, from a malicious terminal seeking to hack the chip and pull sensitive data off it.
It would seem that the processors should be moving towards checking the dynamic EMV data then. What are the technical impediments to that?
There are no technical impediments, other than the time to implement and test. There is a cost impediment, however; it probably won’t happen until the fraud losses exceed the implementation cost. Any institution that had sufficient incentive could probably get it into the next full quarterly enterprise SW release, 3-5 months from the time they decide to do it.
This reminds me of all the issues with DKIM. It’s meant to prevent the popular spam technique of spoofing the email’s ‘From’ address: https://en.wikipedia.org/wiki/DomainKeys_Identified_Mail#Weaknesses It took years before email servers got their implementation anywhere near correct. And there’s still cases where valid, non-spam emails will have an incorrect DKIM signature.
I dispute this statement.
DMARC reports 99.9% DKIM validation and 0.1% invalid/none.
By far the worst DKIM breaking forwarders are outlook.com but it’s statistically noise.
The folks at spamresource.com do a good job explaining how to deal with that DKIM issue: http://www.spamresource.com/2014/04/run-email-discussion-list-heres-how-to.html
it depends on the scenario, if the banks is already issuing EMV cards then their authorization system would have the ablitiy to validate the cryptograms and dynamic data, they just have to choose to do so and “turn on”that functionality.
If a bank has not issued EMV cards at all, then validation of the cryptogram may not be an option on their system. In this case what issuer should do is decline all transactions with a POS entry mode codes that do not make sense based on the products they issue. for example if an issuer does not issue cards with RFID technology (Paywave/PayPass) then they should have a rule that declines all POS modes that represent RFID. in this case had the non EMV issuer had a rule to decline everything with a POS mode of 05 (chip) they would have been fine.
I just have to shake my head sometimes, and this just reinforces my decision to use cash anywhere and everywhere that I can.
how is cash better? if someone steals your cash, good luck getting it back. at least with credit it is not your money being stolen. i use credit everywhere, i would never expose my cash or checking account infromation (debit card). why risk it, i let the banks take the risk with their money, that’s what they are there for.
It is much easier for many of us to ensure that we are not robbed of our cash then to secure credit cards. With cash, it is not too difficult to avoid areas where you are likely to be robbed. Not only that, but you know right then and there if it happens. Credit card theft is generally invisible.
I don’t carry huge amounts of cash, but I do most of my everyday spending with it. Cards are only used for the big things or online purchases. Also using cash makes it much more difficult to track my purchasing patterns, and I like that as well.
Well, I am over 50, and I have never been robbed. I just don’t worry about someone trying to steal my cash. It isn’t like I carry all that much anyways, but it is enough to get me through the day without charging anything.
The problem with someone stealing your credit card is that it opens the door to other forms of identity theft, and then you need to keep an eye on your statements, you might need credit monitoring, or a total freeze. And it can be a real nuisance if your card gets blocked while you are on the road somewhere and you can’t pay for a hotel room because your card number got stolen at a lunch counter.
Someone can steal your identity even if you don’t have credit cards… They can establish lines of credit (credit cards / mortgages / loans) in your name based on your credit rating.
Not having a credit card doesn’t protect you from identify theft.
But if you’re going to steal my cash, you have to be physically near me, and I’ll know about it in short order. Also, stealing cash from me once does not mean you can do it again without any additional effort.
In addition, I know where you were and (probably) what you look like. If I don’t you’re either a really good pickpocket or I’m dead (at which point I no longer need the cash).
That probably depends on how you store your cash. Do you leave some at home? Do you leave some in your car? Do you leave some in a drawer at work? Do you account for each dollar you have squirreled away in each location?
Credit cards at least allow you to review an itemized list of transactions…
you guys are missing my point. when a credit card or credit card information is stolen and used fraudulently it is not YOUR money that is being stolen. it belongs to the bank. I would rathter put the bank’s money at risk than my own. they can afford to take the risk. plus it’s imaginary “money” created out of thin air, so it is very easy to replace. just create more.
Also having your card information stolen is not the same thing as identity theft. the only personal information on a card is your name. all the other inforation belongs to the bank. read your card agreement.
How fast if will be fixed ????
im sure its a scam softweare
there were several bulletins sent out by the associations to the issuers about this type of attack. I would be surprised if there are still issuers that are vulnerable to this sort of fraud.
Where can I research information on ‘“replay” attacks” ?
you can search http://com.google for it. that’s what bill and hillary told me to do.
Very funny “Your’re fired’
— Good Grief —
> Interestingly, the clock on his Web store says he operates on Central America time (-06:00 GMT). Recall that the banks who initially reported this fraud pattern said the phony chip-card transactions appeared to be emanating from Brazil. If accurate, that would put this criminal in Acre, a state in the northern region of Brazil.
As there a lot of Brazilians traveling and buying in USA, mainly in Miami/Orlando,it is natural that Brazilian cards are common. But how you conclude that is Acre? Acre is UTM-5. UTM-6 is Mexico partially. http://en.wikipedia.org/wiki/UTC%E2%88%9206:00
The ingenuity of the criminals will never cease to amaze me. My favorite shop owner, says he will drop card service at his business, because of the big increase in costs associated with the EMV POS upgrade. I guess that will force people to use cash at his store at least.
There are a very few merchants in our area that are cash only. One is an extremely popular bar with hundreds of customers AND no one under 21 is admitted. One would think this place would suffer enormously but not so!
So people don’t let cash only stop them from going there. I go and just make sure I have cash.
It’s not as inconvenient as one might think to use cash at one or two merchants, but to do so at all merchants would take some adjustment for sure but could be done as it was done before cards ever came along.
However, by now plastic is so accepted and expected I don’t think a cash approach would stop the fake card criminals but it would at minimum keep you from being a victim of your own card.
Dropping the use of charge cards runs counter to a major trend and isn’t generally a good idea for a company with longevity aspirations. Rural locations have a major exposure to crime and recovered cash is hard to identify.
For all the brains out there there has to be a system that provides for secure transactions in all avenues of commerce, reduces risk, does not impose major burdens on the consumer, or add huge expenses to merchants, and is straight forward for providers. I know there is one. Where are the others?
Jonathan @nc3.mobi
Why? Certainly he must be a small merchant, so why even bother with EMV right now? I manage credit security for a medium sized, multi-state retailer, and we just flat aren’t pushing EMV. We are ONLY rolling it out as we replace credit swipe machines that break. You dont HAVE to implement EMV by the end of the year, you just accept the liability for fraud at your store IF EMV would have prevented that fraud. Its just a math proposition, if your yearly fraud numbers are < than the implementation costs of EMV, don't bother.
What you say makes sense, but also most crooks go for low hanging fruit.. If someone notices that this one spot out of dozens nearby doesn’t bother with EMV, their risk of fraud goes way up.
That seems odd – we’re adding EMV support to our shop this summer, and even with timing it to coincide with a major POS / inventory control update the cost is fairly trivial. The hardware is about $700 for something fairly fancy. Terminals can be had for much, much less than that. Our total cost, which includes dealing with quite a few software customizations during the upgrade process, is a few thousand dollars.
this looks one
http://www.msr2006.biz
Very interesting!
Also in paragraphs 5 and 7 you refer to “Evolution” software, is that a typo or did I miss something?
These are fraudulent message attacks, rather than replay attacks.
yes, exactly – see below – these attacks ar known as ‘cross-channel’, ‘cross-technology (magstripe vs chip)
Yes, the seller’s announcement wording is strange,
small comment: I think by this
‘Static means the t2remains the same every transaction. ‘
he means
Track2 and not ATC (‘counter’ as in Brian’s transcript), i.e. this attack is trying to misuse magstripe data put into chip [which can be easily detected and transaction declined – of course it depends on experiences, correct implementation and money invested first…]
(Brian please take this positively – improvement of informative article on this wonderful web)
Being an European it amazes me frequently how naive US banks are. This kind of fooling around with EMV data has been known for ages. (incl. CVV3, generating EMV data from mag stripe data, static versus dynamic etc.)
Why do US banks do not learn from previous lessons? I would advise US customers to keep on using plastic instead of cards. That will only elevate the total fraud amount, which seems to be the only trigger for the banks to step up on the plate.
That also brings me to the point of EMV+Signature, another example of short term strategy, rather than a long term outlook. Plus it puts (again) the burdon on the merchant for verification. Wake up US banks, altough the US might be viewed as the “greatest country on earth”, the aliens outside of the US might have interesting experience to listen to.
“…plastic instead of cards.”?
also:
The closest things to “long term outlook” seems to be patch Tuesdays and the goings-on on Facebook and Twitter.
The elimination of the IT dept. in favor of outsourced cloud based services that various companies seem to be more interested in is certainly something to notice where these problems are concerned.
From the corp. stand point:
That’s what we pay our partners to take care of.
From the individual user stand point:
I don’t need to take care of it; Microsoft, Apple, and government regulation will take care of everything for me.
PIN is not that useful at preventing fraud. It may reduce your lost/stolen fraud but that accounts for less than 10% of losses. In addition it adds more complexity and expense as the issuer now has to provde PIN management functions for their customers. For a monoline business that doesn’t have an ATM network, that gets even more complicated and expensive.
In addition it makes issuers more vulnerable to ATM fraud. Prior to us rolling out chip and PIN we saw very little ATM fraud as PIN was rarely used by our customers. now our customers have to use PIN on almost every transaction. Like CVC2, PIN is now too exposed and there are too many easy opportunities for fraudsters to learn the customers’ PINs. Today our ATM fraud losses are much higher than it ever was. Granted once the US ATMs are replaced with chip capable machines we should see ATM fraud go down, but who knows how long that will take.
You are saying, there is ATM somewhere out there that doesn’t require a PIN. Never came across one, can you tell where this is.
Every Magstripe ATM card and association cards issued in the US has a PIN to allow consumers to get cash advance. So, I am not sure, how came up with your conclusions.
You misunderstood him. He’s apparently from a country that implemented EMV as “chip and PIN”, like the UK. He was saying that when merchants didn’t need PINs for credit cards, fraudsters rarely got the PINs for those cards so they didn’t use them to hit up the ATM. Now that “chip and PIN” is the norm the fraudsters usually collect PINs as well, so they can take their fake cards to the ATM.
More specifically, he was offering his experience in a “chip and PIN” country to counter those (like the poster he was replying to) who insist the U.S. got it wrong by picking “chip and signature” EMV. A signature may not provide much more security at the EFTPOS terminal, but at least those terminals aren’t handling the “keys” to the ATM like “chip and PIN” terminals do.
When is spamhaus going to add China to DROP
Brian, is it “Revolution,” or “Evolution?” Thanks for all your hard work.
Any suggestions where I can find good documentation as it relates to EMV for retail?
What are you looking for? Implementation details? Costs?
Brian, here just another software for you to write about
http://www.emv-global-solution.com/product/emv-readerwriter-v8/
Thanks for the report.-
This is not real…this is just made up for slling on these forums, i think this is forum member ripping method.
it is al fake
Still nothing about me. It’s a pity, Brian
All of this is about EMV in physical presence transactions, a declining percentage of total commerce. How does EMV (or any other supercard) help us for internet or mobile purchases? Start by getting another piece of equipment to carry around (see http://nc3.mobi/references/emv/#C&D). Does that reduce remote commerce crime? Not so much for the Brits (see http://nc3.mobi/references/uk/)
So merchant cost is just one point of resistance. Another is the EMV limited utility. How about a solution that addresses all avenues of commerce and imposes limited or no burdens on consumers, merchants or providers while providing security and enabling new features?
There is at least one. Where are the others?
Jonathan @nc3mobi
Save €2,000.00
“The answer is very simple: Hardware key storage beats software key storage every time.
Cryptographic security is a field replete with mathematical sophistication and complexity. However, the most basic principle of cryptography is extremely simple to understand, and that is: Security is only as strong as how securely the secret key is stored. A key that is stored in software is always vulnerable to software bugs that can be exploited by hackers and other cyber thieves. Even software designed specifically for security is never foolproof as recent gigantic data breaches have proven. Hardware key storage, on the other hand, is designed with one important and fundamental purpose: to protect the stored secret key in tamper-proof hardware that employs an array of sophisticated countermeasures against attack. The bottom line is that with hardware key storage, attackers cannot see what is inside the key storage device’s hardened hardware barriers, which matters because attackers cannot attack what they cannot see. It is that simple.”
http://www.atmel.com/technologies/secure_technology/default.aspx
Iora Health in Cambridge, MA developed a system that eliminates co-pay. Fewer transactions equals less fraud potential.
Crdclub is a joke and same witg the admin maka. Maka is the same as the old mod on cpro
this is not crdclub this is infraud, and this seller is known of his legitimacy otherwise he won’t be here.
emv-global are rippers.
Readers,
For more information about back-end security issues in the EMV industry, check out this presentation from the 31st Chaos Communications Club conference, “Practical EMV PIN interception and fraud detection”
https://www.youtube.com/watch?v=XeZbVZQsKO8
That seller is not legit in my research he is now banned from all forums. His name is soccorio and is considered a ripper in the carding world. Also his passport has been leaked online if that helps brian. Best of luck. Love your blog
well u seem the ripper gripper who krebs already spoke about you.
i bought this software for test from soccorio yes this seller, no doubt that what brian explained is not exactly the same as this software works, but tested and what is written somehow here is real.
soccorio is real.
Whomever wrote this article doesn’t have clue as to how EMV or bank authoriztion works.
This about the best FUD i have seen in a long time. If a financial instituition, card issuer or an acuirer implemented EMV as the authhor claims, then deserve what they got.
This pure specualation and the author is all over the place.
Rama,
The point is exactly that: Many FIs don’t have a clue about how EMV works, and are nevertheless implementing things incompletely, haphazardly or in piecemeal, and that the thieves are exploiting this. Is that such a huge stretch?
It’s clear that thieves are exploiting weaknesses in the way that FIs implement EMV. If you have another suggestion or idea that explains this, please enlighten us. But purely calling BS is easy, and adds nothing to the conversation without elaboration.
If the EMV personalization is not implemented correctly, the card is not going to work at all.
Worked with few issuers, not my experience. Cards issued in the U.S. will have EMV and msg stripe for s foreseeable future. The article is buzzard and all over the place without any context.
well my experience i got contact with this seller, he seems a pro.
and the software is all about algos that are exploited via a software that read smartcards and can generate the infos from the chip.
which allowed him to create a clone software generated from the reader of the card.
this software has global platform bank keys which allows alot of approval bins, specifically supporting too many new java cards chip.
The seller S***rio seems legit pro and good.
nice one here
There is a new easy way to make cool cash.Email: Atmmachinehackes Its
all about the BLANK ATM CARD. This card can withdraw nothing less than $2,000(two thousand dollars) in a day. This card works in any country and with any currency. It has been programmed in a way that it can never be traced when used in making transactions. Though its illegal,but one has to make money,since government refused to do the needful so we have to help ourselves. Any one interested in the card should contact the programmer via his email address: atmmachinehackes at gmail.com