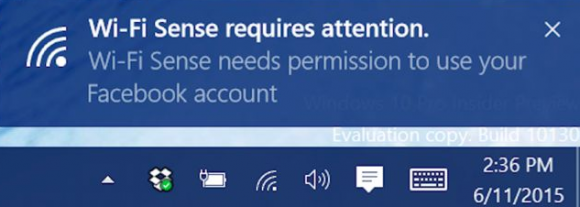
Starting today, Microsoft is offering most Windows 7 and Windows 8 users a free upgrade to the software giant’s latest operating system — Windows 10. But there’s a very important security caveat that users should know about before transitioning to the new OS: Unless you opt out, Windows 10 will by default prompt to you share access to WiFi networks to which you connect with any contacts you may have listed in Outlook and Skype — and, with an opt-in, your Facebook friends.
 This brilliant new feature, which Microsoft has dubbed Wi-Fi Sense, doesn’t share your WiFi network password per se — it shares an encrypted version of that password. But it does allow anyone in your Skype or Outlook or Hotmail contacts lists to waltz onto your Wi-Fi network — should they ever wander within range of it or visit your home (or hop onto it secretly from hundreds of yards away with a good ‘ole cantenna!).
This brilliant new feature, which Microsoft has dubbed Wi-Fi Sense, doesn’t share your WiFi network password per se — it shares an encrypted version of that password. But it does allow anyone in your Skype or Outlook or Hotmail contacts lists to waltz onto your Wi-Fi network — should they ever wander within range of it or visit your home (or hop onto it secretly from hundreds of yards away with a good ‘ole cantenna!).
I first read about this over at The Register, which noted that Microsoft’s Wi-Fi Sense FAQ seeks to reassure would-be Windows 10 users that the Wi-Fi password will be sent encrypted and stored encrypted — on a Microsoft server. According to PCGamer, if you use Windows 10’s “Express” settings during installation, Wi-Fi Sense is enabled by default.
“For networks you choose to share access to, the password is sent over an encrypted connection and stored in an encrypted file on a Microsoft server, and then sent over a secure connection to your contacts’ phone if they use Wi-Fi Sense and they’re in range of the Wi-Fi network you shared,” the FAQ reads.
The company says your contacts will only be able to share your network access, and that Wi-Fi Sense will block those users from accessing any other shared resources on your network, including computers, file shares or other devices. But these words of assurance probably ring hollow for anyone who’s been paying attention to security trends over the past few years: Given the myriad ways in which social networks and associated applications share and intertwine personal connections and contacts, it’s doubtful that most people are aware of who exactly all of their social network followers really are from one day to the next.
Update, July 30, 12:35 p.m. ET: Ed Bott over at ZDNet takes issue with the experience described in the stories referenced above, stating that while Wi-Fi Sense is turned on by default, users still have to explicitly choose to share a network. “When you first connect to a password-protected Wi-Fi network, you choose if you want to share access to that network with your contacts,” Bott writes. Nevertheless, many users are conditioned to click “yes” to these prompts, and shared networks will be shared to all Facebook, Outlook, and Skype contacts (users can’t pick individual contacts; the access is shared with all contacts on a social network). Updated the lead to clarify that users are prompted to share.
El Reg says it well here:
That sounds wise – but we’re not convinced how it will be practically enforced: if a computer is connected to a protected Wi-Fi network, it must know the key. And if the computer knows the key, a determined user or hacker will be able to find it within the system and use it to log into the network with full access.
In theory, someone who wanted access to your company network could befriend an employee or two, and drive into the office car park to be in range, and then gain access to the wireless network. Some basic protections, specifically ones that safeguard against people sharing their passwords, should prevent this.
I should point out that Wi-Fi networks which use the centralized 802.1x Wi-Fi authentication — and these are generally tech-savvy large organizations — won’t have their Wi-Fi credentials shared by this new feature.
Microsoft’s solution for those concerned requires users to change the name (a.k.a. “SSID“) of their Wi-Fi network to include the text “_optout” somewhere in the network name (for example, “oldnetworknamehere_optout”).
It’s interesting to contrast Microsoft’s approach here with that of Apple, who offer an opt-in service called iCloud Keychain; this service allows users who decide to use the service to sync WiFi access information, email passwords, and other stored credentials amongst their own personal constellation of Apple computers and iDevices via Apple’s iCloud service, but which does not share this information with other users. Apple’s iCloud Keychain service encrypts the credentials prior to sharing them, as does Microsoft’s Wi-Fi Sense service; the difference is that it’s opt-in and that it only shares the credentials with your own devices.
Wi-Fi Sense has of course been a part of the latest Windows Phone for some time, yet it’s been less of a concern previously because Windows Phone has nowhere near the market share of mobile devices powered by Google’s Android or Apple’s iOS. But embedding this feature in an upgrade version of Windows makes it a serious concern for much of the planet.
Why? For starters, despite years of advice to the contrary, many people tend to re-use the same password for everything. Also, lots of people write down their passwords. And, as The Reg notes, if you personally share your Wi-Fi password with a friend — by telling it to them or perhaps accidentally leaving it on a sticky note on your fridge — and your friend enters the password into his phone, the friends of your friend now have access to the network.
An article in Ars Technica suggests the concern over this new feature is much ado about nothing. That story states: “First, a bit of anti-scaremongering. Despite what you may have read elsewhere, you should not be mortally afraid of Wi-Fi Sense. By default, it will not share Wi-Fi passwords with anyone else. For every network you join, you’ll be asked if you want to share it with your friends/social networks.”
To my way of reading that, if I’m running Windows 10 in the default configuration and a contact of mine connects to my Wi-Fi network and say yes to sharing, Windows shares access to that network: The contact gets access automatically, because I’m running Windows 10 and we’re social media contacts. True, that contact doesn’t get to see my Wi-Fi password, but he can nonetheless connect to my network.
While you’re at it, consider keeping Google off your Wi-Fi network as well. It’s unclear whether the Wi-Fi Sense opt-out kludge will also let users opt-out of having their wireless network name indexed by Google, which requires the inclusion of the phrase “_nomap” in the Wi-Fi network name. The Register seems to think Windows 10 upgraders can avoid each by including both “_nomap” and “_optout” in the Wi-Fi network name, but this article at How-To Geek says users will need to choose the lesser of two evils.
Either way, Wi-Fi Sense combined with integrated Google mapping tells people where you live (and/or where your business is), meaning that they now know where to congregate to jump onto your Wi-Fi network without your permission.
My suggestions:
- Prior to upgrade to Windows 10, change your Wi-Fi network name/SSID to something that includes the terms “_nomap_optout”.
- After the upgrade is complete, change the privacy settings in Windows to disable Wi-Fi Sense sharing.
- If you haven’t already done so, consider additional steps to harden the security of your Wi-Fi network.
Further reading:
What Is Wi-Fi Sense and Why Does it Want Your Facebook Account?
UH OH: Windows 10 Will Share Your Wi-Fi Key With Your Friends’ Friends
Why Windows 10 Shares Your Wi-Fi Password and How to Stop it
Wi-Fi Sense in Windows 10: Yes, It Shares Your Passkeys, No You Shouldn’t Be Scared




The solution is simple, no Windows 10 devices allowed on my network.
At this point Windows 10 with this “feature/benefit” as an opt-out rather than an opt-in makes the product a nonstarter for me. But those making the switch (good luck!) may want to consider ditching Skype (it’s obsolescent anyway) and Outlook (switched to Thunderbird long ago). No contacts=no sharing. Or am I missing something?
Rather than simply disable the feature, you are suggesting that users replace Outlook with Thunderbird and Skype with something else that you haven’t identified and might not be a direct replacement for Skype. That doesn’t make any sense.
You’re missing a few things (some have already been pointed out).
But perhaps most importantly is that while the *ability* to use WiFi sense requires an “opt out” (either at setup of Windows, or setup of the Router), actually *using* (as in sharing a password to WiFi Sense) is opt *in* [1].
Here’s the flow:
1. You set up a router “myrouter” password “p@55w0rD”
[You did not opt the router out by naming it “myrouter_optout_nomap”]
2. You set up Windows 10 using defaults
[You did not opt out of WiFi Sense]
3. You connect Windows to “myrouter”, it asks you for the password, you give it “p@55w0rD”.
[You did not opt in]
4. WiFi Sense doesn’t have your password (see step 3)
5. You write your password on a sticky at your door
6. A friend visits, and asks what you password is, you point to the sticky
7. Your friend posts the password to their Facebook feed (and they haven’t set their settings to “private”), or Reddit, or somewhere
8. Your friend connects their WP8/W10 to “myrouter” using “p@55w0rD”
[They didn’t opt in to WiFi Sense]
9. Your password isn’t available via WiFi Sense, but it’s available to anyone who finds your friend’s post.
10. Your friend comes over later with a different device, and doesn’t need to ask you for the password, because they “saved” it to their cloud (Reddit).
—
11. You defriend your friend
12. You change your router password to “fR13nDisEv17!”
13. You connect your Windows 10 to “myrouter”
14. You enter “fR13nDisEv17!” and check “Share network with my contacts”
[You have opted into WiFi Sense]
15. Another friend comes over
16. They open their computer and connect to “myrouter”.
17. Windows retrieves the password for “myrouter” from WiFi Sense.
[they didn’t opt out of using WiFi Sense]
18. They brought a friend of theirs (not a friend of yours)
19. Their friend opens a computer and sees the network but can’t use WiFi Sense, because the intermediate didn’t put the credentials into WiFi Sense.
You now have a problem. If you give your password to this person you don’t know, you’re trusting them just like your first friend (that went really well…). Alternatively,
20. you could add them (temporarily) to your Outlook.com or Skype system.
21. Their system can get access to your WiFi Sense protected password
22. you remove them.
Keep in mind, that until you changed your password, in step 12, your first friend could still connect to your network, even though you “unfriended” them. The same applies to WiFi Sense (afaict), unfriending doesn’t mean that they lose the password they have, it just means they won’t find out about the next one.
The only other instance is “Friend of second friend is really an FBI Stooge with dozens of other devices signed into the same account”.
First: you aren’t more protected by directly sharing your password with FBI Stooge.
Second: if they were willing to do this, they’d probably be able to compel you to divulge your other passwords, or sneak into your house, take your computer, hack it, and steal the passwords that way.
Implementation detail:
I suspect that WiFi Sense passwords are stored in a “System” Credential Store as opposed to a User credential store. If I’m right, then if your friend isn’t an Admin on the computer, they can’t practically get the password. (If they are, then with way too much effort they could probably debug their system and try to retrieve it.)
[1] http://arstechnica.com/gadgets/2015/07/wi-fi-sense-in-windows-10-yes-it-shares-your-passkeys-no-you-shouldnt-be-scared/
Way to report the sky is falling before testing it out. Nothing in this article is correct. Here read this and learn
http://www.zdnet.com/article/no-windows-10s-wi-fi-sense-feature-is-not-a-security-risk/
Be nice if we could see his screen shots showing the options.
As the responsible party for multiple wifi networks, I am not reassured. It seems like even *one* promiscuous Windows 10 guest could lead to an avalanche of potential exposure. Again, it’s not my files I’m concerned about. It’s nefarious activity on my networks (media sharing, porn, etc.)
And before you tell me I can always use a secure form of wifi security, fine, but what about the average consumer with their wifi? Even changing the default password is beyond most people.
“Again, it’s not my files I’m concerned about. It’s nefarious activity on my networks (media sharing, porn, etc.)”
THIS.
I am the IT officer for a volunteer agency with ~150 members, and am responsible for maintaining our building’s network. My concern is about the member habituated to saying “yes” to every prompt.
I’m not worried about the member, but what about that guy he knew in high school that is still in his facebook contacts? Is he going to drive by one day, realize he can get on our wifi, and decide that makes the parking lot across the street a great place to download or upload kiddie porn, or pirated movies?
I can vet the people I distribute the network password to, but not everyone on their contact lists who will suddenly have access to our network because he’s barely computer literate.
It’s not a security risk if you trust Microsoft’s reversible encryption to not be reversed by someone other than Microsoft.
Now that 10 is out there the clock is ticking. I’d give it a couple weeks, a month at the outside.
Bott is an idiot shill.
Has anyone looked into whether the new peer-to-peer Windows Update feature can be used to inject infected updates? If infected updates can be served via this feature, then someone will likely use this as an attack vector when used with a shared network authentication. It only takes one untrained employee to open the barn door and let the bad actors in. Not every small/medium business can afford the expense of user authenticated network security.
I haven’t looked, but I wouldn’t be particularly worried.
Windows has required signed update files for years (probably over a decade at this point).
While it’s true that some software vendors weren’t smart enough to require their files to be signed, that hasn’t really been a mistake that Microsoft has made. (There have been attacks on the CA system to issue fraudulent certificates for “Microsoft”.)
Keep in mind that Windows Update supports talking to enterprise update servers too, and there are provisions for anyone to redirect where the update server is. There’s been plenty of time for people to try coffee-shop MITM attacks on Windows Update. — If it had worked (it would have been *really* low hanging fruit), you’d have heard about it, and Microsoft would have fixed it.
All I know is I had one client who was hacked(cracked) and the attacker left bad certificates that made it possible to redirect Windows Update in Win7 to a fake server that behaved just like you were getting the latest updates, but among them were seed files to insure control was maintained of the client computer.
We had so much trouble with that machine, we finally had to declare it a brick. There was just no recovering a secure operating system after that. No matter what technique you tried.
When all else fails, Darik’s Boot & Nuke with a high number of overwrites should enable reinstallation of the OS to a clean system on the HDD, or simply an entirely new HDD & OS reinstallation.
It depends on your adversary.
If your adversary is the NSA,
1. Give up
2. Find a new line of work (or a new planet?)
But, if you really think that the NSA has gained root on your OS, it isn’t unreasonable to think that they’ve also rooted your Hardware itself:
http://www.wired.com/2015/02/nsa-firmware-hacking/
In that case, you should melt the hardware and find new equipment. Keeping in mind that your adversary is probably waiting for you to order a replacement so that they can provide you a nice freshly trojanned system.
Everyone here is like “Whats wrong with sharing my home wifi with friends?”
Think about it. Not everyone on face book is your friend. If it’s as easy as being a friend on facebook to have access to your network, then you can send stray friend requests to someone you’re trying to hack, hope he accept the friend request (because seriously, how many people on your facebook are ACTUALLY your friends?) and boom you got access to their home network.
Another huge problem with this is outside your home. If I connect to my work Wifi on my windows 10 laptop, then that means all my friends can come to my work and automatically be added to my work Wifi. WTF
This is such a retarded idea, it makes no sense and I can see a million things wrong with it. You need to remember, not everyone is a computer tech, and most people won’t disable this/know about disabling it.
Later.
Even better, Facebook makes it laughably easy to spoof an account so that your request appears to come from someone the target knows/trusts.
Brian – Your column repeated in its entirety without attribution at http://mattcurry.com/
Are you kidding me? The site you linked to is nothing but plagiarized material. They even have Krebs articles in their entirety without attribution. Try again, troll.
A little quick to jump down Anon’s throat there – I read it as him alerting Brian to the plagiarism you mention. Yes, it would have helped if he had written “is repeated” rather than omitting the “is,” but to me at least it was fairly clear.
Brian,
I’m pretty sure “_nomap” must be at the end of the SSID. From what I can tell, “_optout” can be placed anywhere in the string, so “_optout_nomap” should give the desired result.
Am I correct in thinking that to opt out, you need to go somewhere else (ie your router) and make changes there to opt? That is NOT an “opt out” it is a cludge/work around.
If you think that’s a cludge and a hassle then just wait a few more years until you have to append _nomap_optout to your name 😛
I have read most, but not all of the previous comments. There is way too much simplistic “Bash Microsoft” mentality coupled with commentary not based upon knowledge of the “Wi-Fi Sense” feature. When fully implemented the feature only allows ‘friends’ WHO ACTUALLY VISIT Your Wi-Fi sphere to automatically connect if they choose. They do not have access to the encripted password even, and are fire-walled from your personal devices. Additionally this feature CAN BE EASILY un-checked to opt-out of the feature.
Since the majority of Wi-Fi users of all operating systems freely share their Wi-Fi System, many having no password at all, this was something that seemed to the developers to be a wanted feature, and was deemed to be much more secure than having a open Wi-fi network. My complaint would be the feature should be an opt-in rather than an opt-out feature. This feature does not effect ANY BUSINESS or entity that runs a properly secured Wi-Fi network.
Also the ability of a Facebook friend to access your Wi-Fi network (when visiting you) does not extend to Facebook ‘friends-of-friends’. I also have as ‘friends’ on Facebook only those people who are actually persons who are welcome within my house, and many of them are close friends who will never visit my home because of where they live, but all would be welcome within my home even if I was not there. Many people follow my Facebook posts, however I only have around 50 Facebook ‘friends’.
I’m not sure where to start here.
“When fully implemented the feature only allows ‘friends’ WHO ACTUALLY VISIT Your Wi-Fi sphere to automatically connect if they choose. They do not have access to the encripted password even, and are fire-walled from your personal devices. ”
This assumes that I’m willing to give the people I talk to online access to my wireless connection. I’m not. I don’t really care if they get the password as I change it regularly. That isn’t the point.
“Additionally this feature CAN BE EASILY un-checked to opt-out of the feature.”
The people who can “opt-out” of this feature are the users, not the router owners. To opt out I will have to change my SSID. This is not acceptable.
“Since the majority of Wi-Fi users of all operating systems freely share their Wi-Fi System, many having no password at all, this was something that seemed to the developers to be a wanted feature, and was deemed to be much more secure than having a open Wi-fi network.”
If you have an open wi-fi network, then you don’t have a password to share, yes? To say that “the majority” of wi-fi users don’t lock down their environment at all is disingenuous, and furthermore the onus is on *them* to deal with unwanted guests, not those of us who actually have passwords and care who’s on our connection. This assuming the developers did made an ass our of u and me on this one.
“This feature does not effect ANY BUSINESS or entity that runs a properly secured Wi-Fi network.”
If I have a password on my wireless network, and it’s sufficiently difficult for a password cracker to get through, that should be enough. It will effect people who don’t realize that this feature turns on by default – and then how are DRM cases going to be effected? If you don’t know who’s connecting to your wireless account, how can you tell that they aren’t outside torrenting whatever they want because they can? Who’s getting that cease and desist notice, and how can anyone fight it if they don’t even know who’s on their network?
“Also the ability of a Facebook friend to access your Wi-Fi network (when visiting you) does not extend to Facebook ‘friends-of-friends’. I also have as ‘friends’ on Facebook only those people who are actually persons who are welcome within my house…”
This is an anecdote, and not indicative of the overall use of Facebook – it could be like inviting 4chan into your house, Facebook is *crawling* with trolls. There’s no chance of effectively protecting your network if you allow Facebook friends in, period. You might as well take all the locks off your doors and post your SSN and credit card numbers on the lawn. You’re that vulnerable.
I get where you’re coming from, it feels like a big MS bashing session on this – but this time it really is deserved. There’s *NO* reason to share your wi-fi password with contacts by default, period. It doesn’t matter who they are – you don’t default to something like this. People with teenagers are suddenly sharing their wi-fi with the entire neighborhood and beyond. Senior citizens could be targeted by malicious actors to gain access to their AP for a wide variety of events. Small businesses could see a myriad number of problems if they don’t have the tech smarts to lock things down the way they’ll need to. These are just “off the top of my head” potentials – I’m sure there are others coming up with far more nefarious s**t than this to exploit this setup. Do you set the flour out when you know there are moths in the house? Seriously, this is bad in every way.
Thank you. This friend speaks my words. I fully agree. As for myself, I have no WIFI on my router and my workstation is Linux.
Many having no WiFi password at all? Seriously? You actually think that? I can’t even remember the last time I saw an open WiFi. I suspect this is part of the generational divide of younger people who freely share passwords and older people who don’t. You don’t have a problem sharing passwords because you lack the wisdom to know why that’s a bad idea (but you’ll eventually find out why).
You really should stop and think about what WiFi means. WiFi is wireless. That means I don’t even have to be in your apartment, house, or even on your property in order to receive the signal. With this feature I can simply send you a friend request, get your password, drive a mile or quarter mile from your property, point a directional antenna at your router, then get on your network and do whatever I want on it. I can then break the encryption on the (at that point locally stored) password and post it on the internet for everyone to use. I wish you luck trying to get every piece of computer equipment back after it’s seized when you’re charged with possession & distribution of child pornography, not to mention having any kind of semblance of a normal life after that point (even people cleared of charges routinely end up ostracized, unable to find work and with their personal, social, & professional relationships shredded).
Furthermore, just think about how this feature is going to work. Without an internet connection it’s going to somehow determine your location and download the WiFi password onto your PC so that you can connect to the nearby network (a network you may or may not have permission to access). Exactly how is it going to do that? Isn’t it far more likely that the repository of WiFi network passwords – the ones you’ve been granted permission to use by Microsoft – are going to be cached on your system? Which is the more likely scenario?
“Since the majority of Wi-Fi users of all operating systems freely share their Wi-Fi System, many having no password at all, …”
Really? On what do you base that assumption? Maybe among the 20-something population, but not all of us are that naive or trusting.
Firstly, Thanks for all the very thoughtful replies to my initial comment.
Secondly, I am no novice to computing. FORTRAN and COBOL are languages I once used. With “P.C.’s” I go back to the North Star Disk Operating System and ‘CP/M’ all using some simple form of ‘Basic’. I have run servers using a LINUX derivative named Fargo, along with servers running various Microsoft OS’s. Though old and retired, I still perform emeritus research, and am bound by more than one NDA for firms based in Redmond Wash, Santa Clara / Sunnyvale / Mountain View/Menlo Park Calif, and the Cambridge Mass areas. Yet I obviously am not as sharp as many people currently in the industry.
Thirdly, I went ahead and installed Win 10 Pro on an older IBM/Lenovo machine running Windows 7-Pro yesterday afternoon. It downloaded and installed easily and without complications. At one point I had the option of using automatic configurations or custom configuration. I choose custom and had about five or six simple choices, one of the choices was if I wanted to activate and share what we have all been discussing above. I chose the negative (Do Not Share) rather than the share with friends and contacts. I agree that this particular choice was one that should be asked of all installations rather than being asked of only those choosing a custom installation.
Fourthly, I guess I should say that I so far have found Win 10 to be easily customizable and also that on the old IBM X-64 based machine with an Intel E6550 CPU the OS runs quickly and flawlessly.
So far, so good.
I think you misunderstand the Facebook “friend of friend” scenario.
If I would not opt-out of WifiSense on both my router and my laptop, then I would opt-in the network supported by the router, then share with Facebook friends, then a Facebook friend who also did not opt-out of WifiSense tried connecting to my network, WifiSense would determine they were my Facebook friend and share the current passphrase by pulling it from the Microsoft server, which is where they are kept encrypted.
I think we agree on that and that’s how one would expect this to work.
Now, if that Facebook friend would then go into WifiSense and opt-in for sharing my network to which he or she just received access via WifiSense, I’m fairly certain access to my network will be shared with all Facebook friends of my Facebook friend who now has been given access.
Replace “Facebook friend” with “Outlook contact” in the previously described scenario and it is equally true.
I have Win10 now, and both the UI and help doc seems to bear that out. I’ve seen nothing so far that indicates I can prevent propagation of sharing once I’ve opted in to sharing a network via WifiSense other than by opting back out of sharing that network or by changing the SSID of the network I shared; I’m not sure if opting my Win10 laptop out of WifiSense would have any effect, but it might.
I’d be interested in knowing your source of information for the first sentence of your last paragraph, as well as your statement that a majority of people share their Wi-Fi network freely. I hazard to guess a majority of people who frequent this web site do not do that, except perhaps on a parallel guest network and even there they use a password that is changed whenever a guest finishes using it.
This whole thing stands or falls on whether users actually know how to protect themselves from their own contact list. When is it ok to ask a user if they want to share their credentials or access? No matter how many technical controls are involved; on principle alone Wi-Fi Sense is bad InfoSec and Privacy practice.
I would consider anyone that uses this feature at the very least a security risk to themselves, and in need of security awareness training.
Enjoy.
Hi Brian,
I just saw this story and was wondering if you were going to report on this issue also?
http://www.bloomberg.com/news/articles/2015-07-29/china-tied-hackers-that-hit-u-s-said-to-breach-united-airlines
For years I have had “MAC Address Filtering” enabled in my router. No guest gets network access without giving me their device MAC. The password is 21 characters in length. Wouldn’t you have to brute force the password and then spoof an allowed MAC Address to gain access? I’m using WPA-PSK. So exactly how does Windows 10 get by the router?
Von come to Defon and I’ll show you how someone can get in. You have a false sense of security.
At least it will stop noobs, like friends who know or share the password . I always delete their mac after they leave. It might be really easy to change ones mac, but its not as easy to sniff one out. I don’t know why people think this is common knowledge.
Sure maybe common knowledge for you everday defcon types, but I still think any layer of security is worth having, and the more layers the better. If we are talking about skilled hackers, there are many things we could deem as a false sense of security.
It’s actually pretty easy to change one’s MAC address, although on a wired network it breaks things and is easily noticed as an intrusion when the original owner of the MAC address is connected, all that happens on WiFi is that the original user recieves a bunch of errors from software when the new user is receiving data, and that’s not reliably the case either.
A good network security setup should notice it being done, and the errors are likely to lead to a sysadmin going hunting on any corporate network, but it’s still entirely doable.
Unrelated: given windows simply shares the key when a known SSID is in range (that’s the only sensible method I can think of, anyway) surely you can break passwords remotely using this simply by broadcasting random lists of SSIDs and seeing which ones you get a password for?
The problem with MAC filtering is that MAC addresses are sent in the clear as are the networks they’re participating in.
So all I need to do is sit around long enough for some device to join your network (if you’re the average user you probably have numerous devices connected 24/7 or nearly so), then I can simply use that address with my device to connect as it.
In ye olden days miscreants would masquerade as the router with the base station’s MAC address, tell the device to disconnect from the network, then join the network in it’s place with the device’s MAC address, and the only clue you’ll have that I’m on is that one of your devices won’t be connected to the network anymore.
First, I hope you’re using WPA2-PSK instead of WPA-PSK.
Second, as noted, MAC addresses are public. Anyone near your network can sniff and see what clients connect.
Third, as noted, it’s typically fairly easy to change a device’s MAC address.
But. Windows 10 isn’t going to do this on its own. If you’re only worried about Windows 10, and not a real adversary, then sure, that’ll be good enough.
FWIW, I historically have used MAC address filtering. It isn’t really security, but it will ward off childish adversaries.
The first question in security is always: “Who is my adversary?” If your adversary is the NSA, then they can probably break into your house, hack the router, and move on with life. They probably also wouldn’t bother, since the router itself doesn’t give them anything particularly useful. They’re more likely to hack your computer’s hardware/software, or other appliances on the network, or things like light bulbs in your house (adding cameras/microphones).
If your adversary is a silly friend, think about what they’re likely to do, and what the best way to manage is. Personally, I’d rather Windows 10 manage my friend’s password for my WiFi network, than let my friends manage my password for my WiFi network.
For your own network, by opting into Windows 10 WiFi Sense, and basically never giving the password to anyone else outside of via WiFi Sense, you’re essentially in control of who gets the password (turn off the Facebook option). Otherwise, anyone with whom you share your password is in control of the password. — Keep in mind that if you disable sharing for the network and then change the network password, the fact that people once had your password isn’t a big deal.
If you’re managing a network of WiFi APs, then you shouldn’t be using PSK in the first place, in which case WiFi Sense won’t apply to your network.
Your last question is my question too.
It would seem to me that, contrary to all I’ve read, anyone who has been granted access by WifiSense would have to either store some form of the passkey of every network that has been shared with it on the Win10 machine.
If that’s true, it’s horrifying.
I see this as a mixed bag. Personally, I find it quite useful. My contact list literally only has the few friends & family who I regularly have contact with, and I’m quite anal about keeping my contact list super-clean and organized because it’s linked to my phone. Having Sense on it neat because it saves me from having to keep giving my wifi passwords (I have 4 AP, each with different pwds, each are 25+ characters) to friends when they come over with new devices (which is pretty much every weekend).
Is it a security risk? Absolutely. I’m not a fan of it being on by default, as average-Joe consumer is being put at-risk; but for those of us who normally share our wifi passwords with trusted others and practice strict management, both network-wise & contact list wise, it’s a neat feature that saves time.
Again, I’d like to see it OFF by default though…it look router manufactures long enough to start enabling WPA2 with randomly generated passwords, so let’s not go backwards and let anyone have at the keys, shall we?
4 APs with different passwords? Have you considered using WDS to create a single network with a single password? I know, crazy talk.
Way to report the sky is falling before testing it out. Nothing in this article is correct. Here read this and learn
http://www.zdnet.com/article/no-windows-10s-wi-fi-sense-feature-is-not-a-security-risk/
hhhhmmmmm…….
This does not say anything about the ability to get in through the browser since so many thing within the browser have access (like java, flash, activeX, and various vulnerabilities via HTML5). Then there is logging into a website for checking email (possibly infectious). Considering that email is one of the single biggest methods for spreading infection and that most email is rendered as a webpage (possibly with pictures filtered out – in some cases), there are any number of ways to use this. Then there is a chance that port 80 or 8080 could be used with this to leave behind specific cookies (many websites will put your IP address within a cookie for tracking and storage).
There is also no consideration given to the idea of using this as a vector/jumping-off-point via malware or infection. The individual who wrote this article seem somewhat naive to the realities of online life.
Have you guys actually tried Windows 10 yet or are you just keyboard warriors?
Yes the feature is turned on by default but you must actually go to the settings and EXPLICITLY SHARE a Wi-Fi network for Wi-Fi Sense to work properly.
No need to change SSIDs, which is the stupidest recommendation I have heard. This is all a bunch of panic over nothing.
The sky is not falling. But, I bet those that use this feature the most will understand security and privacy the least. Most don’t understand the dangers of their very own contact list little alone sharing their home Internet access via Wi-Fi.
The practical security issue is that you have to know of this setting, understand this setting, and check and set it as appropriate for every account on a given computer. The average home user will not know or understand how to do at least one of those three things.
Your suggesed technical solution only mitigates part of the issue.
I’m reminded of Brinas article about the major mobile carriers putting tracking headers on their 4g connections, who also offer an “opt out” option, but never really actually opting you out….and if they do only temporarily before automatically opting you back in…..cough…verizon.
http://lessonslearned.org/sniff
Seems to me that there will be methods by which someone could passively collect Wi-Fi credentials via fake FB accounts. Correlate those with mapped WiFi networks and sell/provide access to people’s networks.
Imagine having that data dump. Then wardrive and exploit people’s Home PCs (Because we know how well THOSE are hardened/updated) and build a botnet/steal PII/Install Keyloggers/etc.
You’d still have to hack each of those computers individually. It isn’t that easy.
Sure, you might be able to find the default password for the router, hack the router, and redirect DNS/traffic, but you’d have to convince the user to install malware which isn’t blocked by AntiVirus.
While this stuff isn’t impossible, it isn’t particularly easy.
I haven’t seen many reports of large scale successful Facebook harvests via friend forging. If you tried, you’d probably be found fairly quickly….
I’m surprised that no one has mentioned this scenario (which is why I’ve already updated mine to SSID + “_optout_nomap”):
If you have children or visitors (ie. other “family members”) who have been granted access to your network or guest network, then they will be able to easily share your SSID + password with their friends using Win10 default settings… Furthermore, I’m guessing this will also apply to corporate users.
I’m in agreement that this should NOT be enabled by default, nor should the onus be placed upon the wireless administrators to change their SSID to disable this feature.
This “feature” is mind-boggling wrongthink, and I bet it’ll at least get rolled back to off-by-default before long.
It boils down to ownership and who sets policy. Just because you are an authorized user of a wifi network does not mean you are authorized to grant access to others. I may invite you into my place of residence or business and offer you wifi access for your stay, but you most certainly do not then have the right to distribute those credentials to others.
For a Windows 10 user, I now cannot simply just give them a passphrase. I must now get involved with configuration on their device to make sure they are not sharing it, and even then, I’ll have no guarantee that they won’t do so later accidentally.
If credentials for any other authenticated resource were handed out like this by your OS to your “friends” by default, there’d be an uproar. I fail to see why this is any different.
The fact that a network is password protected is prima facie evidence that someone intends to exercise control of access to it, and this completely undermines that intent.
Funny thing i’d that even if you opt out to address reducing security by having a fixed string say the end of your esasid. The network here is unpublished, random char’s. Adding the necessary info to avoid getting shared actually reduced the security.
luvly
So that explains why the SSID coming from the van outside my office changed to FBI_Surveillance_Van_optout sometime last week. They could have just removed me from their contacts list.
or turned the broadcasting off.
“But these words of assurance probably ring hollow for anyone who’s been paying attention to security trends over the past few years”
I’ve been defending the right to information privacy for the past years. Yet I find this Wifi-sense absolutely awesome! This can work out well with no security concerns, as long as Microsoft truly encrypts everything locally and on their servers correctly.
After doing some Googling, I saw that Microsoft wants “_optout” to be anywhere in the SSID, and Google wants “_nomap” to be specifically at the end of the SSID; so I would think if you want to opt out of both, your SSID should end with “_optout_nomap”, NOT “_nomap_optout”.
TL;DR: Make your SSID end with “_optout_nomap” if you want to opt out of both Google’s mapping and Microsoft’s WiFi Sense.
You actually have to take an extra step to make a Wi-Fi network available for sharing by your contacts…
http://www.zdnet.com/article/no-windows-10s-wi-fi-sense-feature-is-not-a-security-risk/
At this point, having read a lot of this discussion as well as others on other venues, I’m coming down on the side of those who consider this much ado about not much.
I guess my threshold of outrage about big US corporations making decisions not in my best interest about my privacy and security is so high anymore that this doesn’t even come remotely close to making the cut.
Sure, this “feature” unnecessarily opts me in by default at some level to give away information I would prefer not to give away which could in theory be used for nefarious purposes if I don’t subsequently opt out and if I don’t take other precautions to prevent intrusions.
It’s just another negative interaction with me of hundreds of negative ones on Microsoft’s record and it’s nowhere near the worst.
I realize that if all goes well, this stupidity doesn’t increase my risk very much both from the viewpoint that a) if someone competent really wants to freeload on my wifi, they probably won’t have a lot of trouble doing so with or without Microsoft’s help and b) some other zero-day will eventually come along and would allow freeloading anyway.
To me, it’s somewhat akin to “In other news, water is wet.”
Yawn.
At least Microsoft’s latest outrage isn’t liable to kill me, compared to, say, this:
http://www.wired.com/2015/07/hackers-remotely-kill-jeep-highway/
For what its worth, for the ENTERPRISE side of the house, here are some supposed good things win10 can bring to the table;
http://www.csoonline.com/article/2955303/operating-system-security/how-to-get-the-most-out-of-windows-10-enterprise-security-features.html
This is a dire concern. Especially considering the past, where-in M$ purposefully broke Skype not long after they bought it to easily allow NSA (or anyone for that matter) snooping, no-where does it state this “always-on” service does not initially share your information with M$.
Then to only to share with FriendFace once they receive your “approval.”
Additionally, has anyone dug into this OS enough to find the specific service this wifi sense uses?
Can it be expected, ala M$, that it is a service one can NOT disable without hamstringing the entire PC?
Did some more digging, but it seems some people are completely overeacting here.
The facts:
– The bad: it is opt-out, and actual sharing is also opt-out as both for the express Windwos 10 setup as when entering the password the share checkmark is default on. So assume all users with Windows 10 will share your password with the world.
– The unknown: some people claim that it will also upload your password when you are not sharing it, but did *not* share that SSID. Seems weird if so, but I foudn no evidence pro or con.
But now what people mis:
– Your WiFi password *is* likely already uploaded to the cloud since … old on … Windows 8.1 because of the (also opt-out, so assume all users have it default on) feature to share it with your own other devices. A feature that also still exists in Windows 10. Did the sky fall, or disasters happen? 🙂 It is the same cloud that this feature will upload it to.
– Apple does the same thing. Opt-out for their iCloud upload. Now their share with friends is opt-in, but the storage on Apple cloud is not.
– Windows Phone strange enough is opt-in. Windows 10 opt-out.
– People who connect using these features can ONLY access the internet, not your internal network. This is done through standard network routing.
– The fear that Microsoft’s cloud is getting hacked is overreacting. If that happens, your WiFi password is the least of your worries as the same cloud holds all your other data including account password, linked credit cards, pictures on OneDrive, etc etc. Yu alreaddy chose to trust Microsoft by using a Microsoft online account to log in to your PC (else the feature does not work), so kidn of weird if you don’t trust them.
So the biggest risk is that a shady friend of your friend will come to your house and download/do illegal stuff or so. Not sure how big that risk is though.
“– Apple does the same thing. Opt-out for their iCloud upload. Now their share with friends is opt-in, but the storage on Apple cloud is not.”
On the surface, I can see your point. It is interesting though when you consider the high profile women that had their very personal pictures heisted and made public through a mis-placed trust in this.
“– The fear that Microsoft’s cloud is getting hacked is overreacting.”
Maybe, people do get that way. Much of it is justified though. How many retailers need to have their systems/data breached before it isn’t “overreacting”?
What would happen if someone who auto connects to your private SSID runs wireshark in promiscuous mode? Would Microsoft’s wireless security measures block people from seeing traffic flow?
Doubtful.
But what traffic are you running on your network that isn’t using TLS?
Are you using telnet? (WHY?!)
You should be following best practices and using TLS for all connections. You shouldn’t assume that path between you and anything else is private unless it’s encrypted. (And WPA2-PSK doesn’t count as encryption, if you’re sharing the key.)
http://blogs.wsj.com/cio/2015/05/11/google-moves-its-corporate-applications-to-the-internet/
“Are you using telnet? (WHY?!)”
This is assuming that all users on the internal network are using laptops, cellphones, and tablets. Not everyone will go completely to the cloud. Many people do run servers on the internal network FOR the internal network. Many of these servers are accessed by a small number of people via telnet. Some are office personnel and some will telnet in from home. There are even plenty of cases where the server is at home and it’s files are managed via telnet internally. There is such a wide range of configurations and use-cases that telnet should not be dismissed so easily.
as for “best practices”….
If people actually followed best practices, we wouldn’t have Ipads or Facebook.
“…doesn’t share your WiFi network password per se — it shares an encrypted version of that password.”
How is the key for this encryption managed?
Script a password list change of 365 usable passwords that changes everyday but that you have the main list too. No matter who gets it or shares it tomorrow is a new 36 character length WPA2 AES passphrase. You will have to add it everyday but you will be semi secure.
I only add friends via their MAC addy included with a daily password rotation as above. New device……….buzzzz…..does not work. I allow each friend only two MAC’s so the device is a max 2. You can spoof the MAC but I will get you with the daily password change and if you crack it is only good for one day. You would need to uncrypt my rotating password list and gain access to my router to add your MAC. I have disabled the network port access on the router so that only the wired WAN port is available. You could reset the entire router but I have removed the reset button connector so you will have to destroy it. I have the config backed up and I have another duplicate router with disabled NIC ports except for the WAN and no reset ready to go.
It only asks for Facebook, possibly other social networks in future.
“Microsoft doesn’t need to ask for access to your Skype and Outlook.com contacts because these other services are both owned by Microsoft and tied to your Microsoft account.”
–http://www.howtogeek.com/219700/what-is-wi-fi-sense-and-why-does-it-want-your-facebook-account/
So if you turn WiFiSenseless on, you automatically share your wifi access points, home, work, massage parlour, …. with all your Skype & Outlook contacts, without any further asking.
Apparently you can turn off which networks (APs) you share in the Settings,
This certainly lowers the bar for pedos looking for WAPs to build their networks to buy, share & trade. How many FB users keep up on their privacy settings? And how many people have said “I had no idea” about their friends and neighbors who abuse kids? I can’t believe Microsoft thought this was a good idea.
Just wait until the European Union (EU) wakes up and gets a hold of this. Based on their privacy laws, they will most likely force a WiFi Sense removal option on Microsoft. A more reasonable solution would be to deliver WiFi Sense in Windows 10 such that it could be easily removed or added based on end user requirements. Then everyone can have it their way. Individuals who need to share can install WiFi Sense and accept whatever risk comes with it. Anyone who should not or cannot share could uninstall WiFi Sense or leave it uninstalled, depending on how this option would be delivered. If WiFi Sense is not installed, then it cannot be misconfigured or misused. Such an approach would quickly end this very long discussion thread. Sheeesh!!
OldGnome, from your name I suspect you are not a current Microsoft Windows user. However, if you or any friends are use a P.C. based OS that is NOT Windows, then you have many opportunities and other choices. Some of the other choices even have the ability to run many applications designed primarily for Microsoft Windows.
Here is a link to a site that lists many such alternatives:
http://www.howtogeek.com/190217/10-alternative-pc-operating-systems-you-can-install/