Fraud experts in Mexico have discovered an unusual ATM skimming device that can be inserted into the mouth of the cash machine’s card acceptance slot and used to read data directly off of chip-enabled credit or debit cards.
The device pictured below is a type of skimmer known as a “shimmer,” so named because it acts a shim that sits between the chip on the card and the chip reader in the ATM — recording the data on the chip as it is read by the ATM.
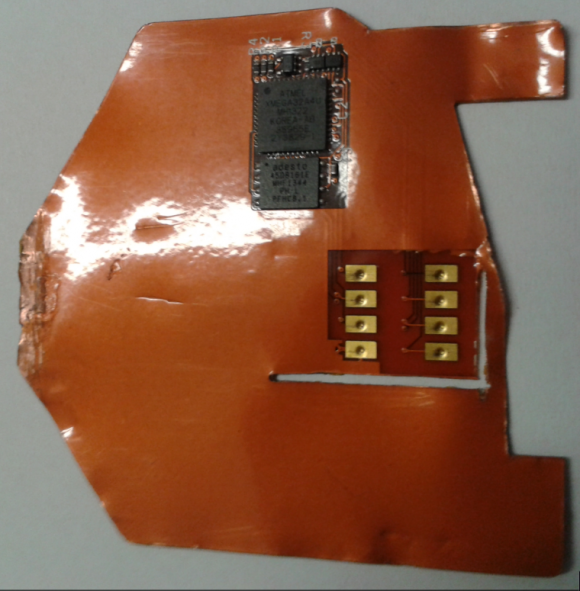
This card ‘shimming’ device is made to read chip-enabled cards and can be inserted directly into the ATM’s card acceptance slot.
The chip reading component includes the eight gold rectangular leads seen on the right side of this device; the electronics that power the data storage on the shimmer can be seen in black at the top of the image.
According to information from Damage Control S.A., a security and investigations company based in Mexico, this device was found inside a Diebold Opteva 520 with Dip reader (the kind of card reader that requires you to briefly insert your card and then quickly remove it). The device is inserted from the outside of the ATM and no access is required to the ATM internals. Damage Control, which disseminated the information via a service called CrimeDex, didn’t say whether this shimmer was accompanied by a component to steal card PINs, such as a hidden camera or PIN pad overlay.
Here’s a look at what this thing looks like while it’s sitting inside a compromised ATM’s reader (notice how the chip-reading components shown in the first image are obscured in this one by the ATM’s chip reader):
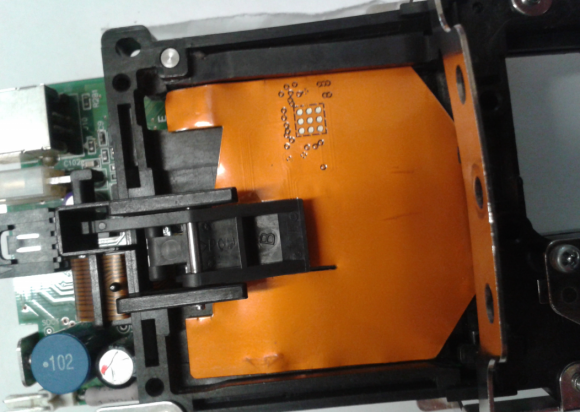
The shimming device, as seen inside of an ATM. Notice how the chip-reading components shown in the first image are obscured in this one by the ATM’s chip reader.
Cards equipped with a computer chip are more secure than cards which rely solely on magnetic stripes to store account data. Although the data that is typically stored on a card’s magnetic stripe is replicated inside the chip on chip-enabled cards, the chip contains an additional security components not found on a magnetic stripe.
One of those is a component known as an integrated circuit card verification value or “iCVV” for short. The iCVV differs from the card verification value (CVV) stored on the physical magnetic stripe, and protects against the copying of magnetic-stripe data from the chip and using that data to create counterfeit magnetic stripe cards.
Banks can run a simple check to see if any card inserted into an ATM is a counterfeit magnetic stripe card that is encoded with data stolen from a chip card. But there may be some instances in which banks are doing this checking incorrectly or not at all during some periods, and experts say the thieves have figured out which ATMs will accept magnetic stripe cards that are cloned from chip cards.
“This suggests to me that the thieves plan to target an issuer where they know the CVV is not going to be checked,” said Charlie Harrow, solutions manager for global security at NCR, an ATM manufacturer.
For more on ATM skimmers and other fraud devices, check out my series All About Skimmers.
Update, Aug. 12, 3:29: Added language to clarify that Mexican security firm Damage Control reported the skimming attack via Crimedex, which is a service of video intelligence firm 3VR.





I think people are getting the wrong impression of how secure these chip enabled cards are. So far in the USA very few if any locations use them so there has not been a focus by attackers on exploiting them. They are not as hard to clone as people think and once attackers do focus on them I think there will be utter surprise. We will see soon, my clients that are banks sure think they are the magic bullet which is scary.
I agree. Chip and pin is just another small hurdle being put in place, not a real solution. The problem is that instead of implementing a real best of breed security layer, the USA is implementing an incremental step.
The public will be surprised how little chip enabled cards do to prevent fraud. Cue the tech experts a year from now explaining over and over again why money continues to be stolen out of accounts.
“…the USA is implementing an incremental step.”
Yes, chip and signature. I don’t believe many institutions here have sent out chip and pin cards yet. Still dragging their feet.
What exactly does “Signature” give me for protections? They are not really doing signature matching at all. And if they are claiming that they are then why am I rarely asked for a signature anymore and where is my sample control signature that I would have to use in order to enroll?
It’s the chip that helps I think. It is one step better than what most Americans have now.
Last summer we took our new chip and sig card on vacation to Scandinavia. Over there they all have chip and pin and we had some trouble at small grocery stores whose machines didn’t work with our card.
People here now can get chip and sig from their bank by asking. Perhaps smaller banks and credit unions are not quite ready.
Actually, my credit union is touting chip & sig cards, and plans to start rolling them out this fall.
Wells Fargo is issuing chip and PIN credit cards. I’ve used mine all over Europe and it works great but of the few times I’ve used it in the US, I’ve never once been asked for a PIN.
I wish my credit union was going Chip and Pin instead of Chip and Ignore Signature. I’ve had my new credit card card for months, but don’t use it that much and have never had the chance to use it in Chip and Signature mode.
Very much agree. Chips don’t really do much to help in real security.
Mastercard/Visa/Amex love them because now it gives them yet another reason to save their money by making vendors pick up the cost of fraud if they don’t support them. Beyond that, there’s not much use for them.
You can’t rely on sequential chip numbers because not every transaction will be done with a chip.
You can’t use them on-line because you don’t have the support for on-line transactions or from the computers making the transaction.
And it’s not really more secure in the POS either. The attack vector used against Target was reading in-memory data IIRC, and chips won’t solve that.
It’s amazing that the cost of fraud when moving to Chip/Pin moved from merchants to everyone who owns that type of card issued by that bank.
No one talks about it. No one. As the shimmers take off I’ll suffer higher rates because some guy in Mexico,Ukraine,Russia, etc decided to beat the better mouse trap.
Merchants are spending billions in the chip/pin move. What are some of the better solutions?
I can’t say what the “best” is but I can tell you what works EXTREMELY well. And that is two factor dynamic authentication. For instance, I swipe my card at the store, immediately on my phone I get a “do you approve” prompt and I click yes. That will stop 99% of fraud out there. This can even be a delayed prompt so if I don’t have my phone I can approve within X hours or so. If people don’t want to add this protection then they pay a higher interest rate which goes to cover any fraud that happens. Just my opinion and what I see that works. Actually all systems I would use 2FA, from Remote Desktop to Last Pass I use Duo.
I think few merchants se going to be supportive of a system that gives the consumer any option to delay approval.
If I were a merchant, absent an immediate authorization from the network, my customer will leave empty handed.
There is ALWAYS a delay in payment to the merchant. It doesn’t immediately get deposited into their bank account so that’s not a concern at all. The only concern would be a delay in the checkout process which as I mentioned you could approve the purchase in X hours etc.. And by the way this is ALREADY available, this is nothing new.
I think Robert is referring to the delay in approval, if the consumer holds up the approval process merchants will likely not go for it. I wouldn’t want the customer to walk with merch that hasn’t been approved for payment.
Absolutely. If the merchant doesn´t get payment approval, why should he let the cardholder out of the door with the goods?
Also, with the small timeframes that auth systems are required to respond before an auth request times out, no cardholder would be quick enough to dig out his phone and answer some two-factor challenge.
Not entirely true. I get transaction alert texts from my credit union and they often arrive before I walk away from the checkout. Those few seconds we’d spend acknowledging a transaction is still less time than waiting for someone to write a check!
when the authorization request is made the decision to approve or decline the auth needs to be completed in a matter of seconds…less than 3 i believe. This text solution doesn’t prevent fraud on the initial transaction, what it does is it can limit the fraud to just that transaction. when you say “decline” chances are the issuer has already approved the auth anyway and the fraudster has left with the merchandise. all this is doing is telling the issuer to block the account and not allow any additional transactions to go through. the issuer will still have to reimburse you for that first fraudulent transaction though.
I agree with Johnny Long. Our dependence on static or multi-use authentication methods has got to stop. Asking merchants to spend billions to modify a broken system seems like a pretty bad idea considering by the time they complete the integration they will most likely be no better off. The bad guys are already way ahead on figuring out techniques to compromise chip and pin technology. What we need is a leap, not small incremental steps. IMHO any strategy or solution based on static or multi-use credentials is doomed to fail.
There is nothing better then cash. And everyone has heard of counter fitting. Damn spellcheck. Next is a check. Even that has been compromised. So what makes everyone think a bankcard, credit agency card or a debit card is not going to be compromised? And don’t just blame the big three for trying to find a way to use the information they were taught in graduate schools, or in show off games. They have long cold winters and need diversions.
Security needs to remember the customer. They don’t want fifty cards in their purse or wallet. That’s why the big three companies. One card for everyone. But shifting the blame for security of the card to the merchant, from the card issuer? Bad idea. Card security is a issurer problem.
Yes of course, but banks ALWAYS seek to shift what they formally call RISK (an insurance term that means ANY money payouts and less capture of floats) onto someone else. It’s THE strategy, and their mathematicians and actuaries have proved that it is the most profitable way to shift costs, increase margins, including the profit from avoiding the cost of real security. They will never give that strategy up, never.
For you see, they understand the same as you do, that cash is king, and to the extent that they have it, you do not, and that’s the entire point. Next if the principle that borrowing (again, cash to them and not to you) accelerates and increases your spending and their earning. If you paid cash for everything, you would pay 40% less and do far less actual transacting as well. In spending and in the transaction process, the function of elapsed time is to increase spending as time decreases. If you slow down the transactions, you will change your mind and pay some significant amount less in consequence, they know that too.
I don’t disagree with you, but how will this work when you travel abroad and don’t have mobile access?
This is hopelessly naive when we live in a world where Android doesn’t offer rolling updates and iOS locks the phone down. Also, in a world where people live in countries where their banks don’t want to honour transactions, anyway (and of all people, if you’re the Johnny Long I believe you are, shouldn’t you know this?). And in a world where malware exists and phones can be bypassed and so on. MAYBE something 2-factor that involves issuing everybody a SecurID type fob with no need to connect to a centralised server and nothing at all that that device can do OTHER than offer up a randomly generated code. Anything else and, sorry to break it to you, it can be and will be bypassed — and quickly — and in the meanwhile it’ll make some things even more targeted than they already are.
People keep thinking there are simple solutions. The truth is (a) there aren’t and (b) if there were, the whole ‘security industry business model’ would collapse. I’m fairly sure there’s a lot invested in just making things always *just* good enough to make it for a few weeks or months until the next bug comes along (or gets introduced). Rolling dev cycles and rolling response cycles make (corporations) bank.
The simple solution does exist, it is the original: cash and travelers checques, period.
There are 2 technologies, both exist and are fairly easy to implement, which will mitigate 99% of card-present fraud, and a 3rd to deal with card not present:
1) End2End Encryption: This is encryption from the card reading device itself, all the way to the bank. The merchant NEVER sees the card number during the transaction, the only time they would see it, is if the bank sends the card number back with the authorization. This would mitigate Target style breaches.
2) Tokenization: When the bank replies with the authorization or denial, they reply with a token number that looks like a CC #. This number is stored by the merchant for any post transaction needs, or can be used for scheduled billing. The average retailer would implement it where the token can only be used by that merchant and with that bank, and only for refunds or chargebacks. The token could not be used to authorize additional transactions, and it is worthless at another retailer, or with another bank. In the scheduled billing implementation the token is still only valid at that retailer and at the retailers bank, but can also be used for future authorizations. (This is how most online companies like AT&T let you store your card number for future use or automatic payments.)
That covers everything except for skimming card numbers, which is going to continue for quite some time. The easiest way to bypass chip cards is to gain the card data and then write it to the magstripe of a chip card and break the chip. When a card reader encounters a broken chip, it is up to the retailer what to do next: deny the transaction, or allow the transaction via magstripe – most retailers go with the latter, because they don’t want to lose ANY sales. This bypasses the protection of the transaction counter that gets incremented with each use, and in many cases will bypass the protection to prevent cloning of cards.
The only way to truly prevent skimming fraud is to use an authenticated transaction like mentioned, or something like ApplePay where you have to authenticate to your device before it will even enable the card data to be sent over NFC. (Also, tokenization is how ApplePay and others store your card number, they don’t store the actual card, which helps protect your card number to a degree.)
3) To deal with card not present transactions, at least those that are online based, the answer is a modified tokenization scheme. Amex used to provide this, where you have a one-time card number, aka a disposable CC#, and card numbers that can be setup to be used x number of times, or to be used indefinitely, but can be turned off at any time. There are numerous ways to implement this, disposable 1 time numbers are the easiest. Disposable #’s that are valid until you terminate them pose some other issues if the token card # is stolen, but these can also be tied to a specific retailer so that if you used a disposable CC# for say your monthly subscription to a website, the disposable # would only be valid at that website, tied to the merchant ID. There are aftermarket solutions for customers for this (Blur offers them), but most customers dont care enough to use them, because the customer isn’t liable for fraud.
Tokenization is fairly easy to accomplish and doesn’t require a lot, the POS never knows the token card number isn’t the actual card number. It just requires the retailer’s bank to support it, and some minor POS updates. The retailer I work for has implemented it, and did so years ago, and it works great.
E2EE is a bit harder to implement, as you have to do special configurations to each card reading device in every store so that the devices and the retailer’s bank have a secure connection, but it can be done without huge pains, and doesn’t require huge changes to the POS application, but does require some. The biggest roadblock in E2EE is cost. Most, if not all, acquiring banks charge a per transaction cost to retailers for E2EE, as do the 3rd party solutions on the market. To implement a point to point encryption solution where the card reader talks to a server that is the last hop before going to the bank can be done, but you basically have to build it yourself, and it gets very expensive to try an do in-house, not to mention, it gives attackers a single place to go after. I can speak from experience, it is EXTREMELY hard to get the business to sign off on E2EE when it costs 3-7 cents a transaction. That seems like nothing, but for us, a smaller regional retailer with 400 stores, it comes out to about $3.2M per year, every year, on top of the initial labor and implementation costs. Like all security, it is very hard to get the business to agree to something that takes away from the bottom line, especially to the tune of millions each and every year.
Disposables are probably the hardest to implement, because each issuing bank, that is, the bank that issues the CC to the customer, has to have a system in place to allocate, manage, and authorize these disposable card numbers. Banks are notoriously behind on technology, and the cost to completely change all their backend systems can be outrageous.
At the end of the day, the solutions exist, but the current liability model prevents them from being implemented, because no one wants to bear the costs, when at the end of the day, all fraud costs are passed back to the consumer in ways that most consumers don’t even realize, so there is no motivation on the banks or retailers part to spend the money to secure payments. Heck, even the new chip / signature solution hasn’t changed the liability model enough. For us, we simply looked at the costs of implementing EMV / Chip’n’Sig and then looked at our yearly fraud numbers (that would be prevented by EMV) and decided it was MUCH cheaper to eat the fraud and not retrofit stores for EMV, only implementing EMV for new stores.
End-to-end encryption is actually being rolled out in a lot of places. I know this because I’ve had to do a bunch of work to integrate with the various EMV kernels in preparation for it.
Retailers are jumping on it because it reduces their costs astronomically by removing the entire IT infrastructure of the retailer from the PCI scope. It doesn’t matter what happens to any of their systems, it’s prohibitively hard to decrypt the sensitive data without the HSM that the acquirer has.
That said, for smaller retailers there’s always the option of network segregation: Have the POS on one network which tells a back office server to initiate a chip transaction on a terminal which is on a separate network, all encrypted using TLSv1.2. Again, we have clients who use this model.
Logical argument. But, I do a lot of traveling where the argument over the cost to the customer and if you are lucky, even the phone sucks. Badly. Where you are talking bytes per second. Where the most modern OS is xp. Where the card is usually run with a hand press. Or copied to the credit slip by hand. How does encryption help the sale of services or products? Or should some of the other factors of identification be needed. Add an iris scanner? A biometric print? If I remember, correctly, the best security, is the least obvious, the shorter the sequence the more secure the sequence. You can have a million number sequence , encrypted, but their has to be, a three number sequence at the start of each group, with the credit card company identifier. To get it to the right credit company, and they operate outside of the bank. So now instead of one file reader, at the store, one at the bank, and at the credit company, all tuned, to say yes no, ?
There is nothing here to detect fraud. Or stop it. Just authorize it.
There is nothing to deter the crook, just the customer, and the punish the sales associate. Hey don’t even do the most obvious with a good camera, always the worst cameras possible under the worst conditions.
I don’t disagree there can be challenges, and there is no one size fits all solution. But if the retailer is forced to do hand imprints due to technical limitations, we are A) talking about a different type of fraud, and B) there isn’t a technology solution to that problem. Imprint fraud will always exist, so long as it is still a valid method for taking CC’s – just as there will always be a threat when you use a CC to pay for dinner and the waiter takes your card away to process the transaction. In the latter example, you could alleviate this issue with no raised and no printed number on the card, no magstripe, and chip only, but now that customer cant use their card at places that don’t support chip transactions, or when traveling to places that do imprints (or places when the internet connection goes out and they have to fall back to imprints.)
The fact remains, that there are no perfect solutions, and so long as the older, more insecure methods (imprint, magstripe) are still in use by retailers, the CC companies will continue to make cards that support the less secure methods. And until the liability model shifts and retailers and consumers visibly have to eat fraud charges, there isn’t going to be enough motivation or uproar to phase out the older methods more quickly.
Remember when traveling meant going to the bank to get travelers cheques? Essentially you could do the same for old CC tech. Drop imprints and magstripe, and retrain consumers to carry cash or travelers cheques just in case, but that would never ever happen, because that means giving customers the option of not using their CC, and there is too much money involved to allow that.
A lot of people here don’t seem to be aware of the primary advantage of how the chip cards work. The chip isn’t just an electronic transmitter of data like the magnetic stripe. The chip has a secret number (the private key) embedded in it that never leaves the card and is made to be extremely resistant to being read, even by someone who has possession of the card and can probe it under a microscope, let alone just from the external contacts by a skimmer. When the card does a transaction, it doesn’t send this code number to the credit card company, instead it does a special calculation with the secret number and sends the result to the credit card company. The calculation result is based on the time and retailer and item and so is different for every transaction and so it does a criminal no good to capture the traffic or data stored by the retailer. The mathematical calculation and result are such that the credit card company can verify that any transaction calculation result could only have been computed by that one chip in that one unique card. You can look up public key cryptography and cryptographic digital signatures to learn more.
There have been some flaws in chip card security, but generally it is said that they have proven to be quite secure in the countries where they have been deployed.
Oh god, this again. “It doesn’t do enough so we won’t do anything”.
As long as chip & pin is introduced sensibly, face-to-face fraud will drop. Yes, it will probably move to card-not-present fraud but that can then be mitigated with 3D Secure.
yes, exactly, +1
This is why we need chip cards that actually establish an encrypted tunnel all the way from the chip to the bank, using PKI, along with ATMs and POS terminals that simply support such tunnels, and receive separate (also encrypted) confirmation from the bank of a transaction.
The flow would look something like this:
ATM or POS terminal prompts for card.
ATM or POS terminal reads issuer address from card (not a secret) and gets from user account selection info, e.g. checking vs. savings.
ATM or POS terminal establishes TLS connection to that address and sends transaction details: amount, checking vs. savings, etc.
Issuer attempts to establish tunnel to card’s chip, and verifies integrity of tunnel. (Similar to secure VPN)
Issuer verifies or rejects card.
ATM or POS terminal notifies user if card rejected, prompts for PIN otherwise.
PIN goes to issuer over encrypted channel from terminal.
Bank either performs the transaction or not, and notifies terminal of which.
Terminal notifies user.
This still isn’t 100% secure because the PIN is disclosed to the terminal. To fix that would require a card with a numeric keypad.
A malicious terminal could also prompt the user to OK a withdrawal of $M and then tell the bank the transaction is for $N, where $N > $M. This can’t be fixed unless the “bank card” becomes a fairly complex trusted device issued to the consumer, which actually presents the user interface for each transaction, and which the issuer designs so as to always display to the user and tell to the bank the same transaction amount. This leaves the user needing to trust only the issuer and merchant/ATM provider. Third party tampering with the terminal wouldn’t be able to do anything but cause declined transactions (denial of service), barring attackers that have cracked strong crypto.
@Johnny Long
So, what do you suggest ? Do nothing until we find the perfect, uncrackable system ? Magnetic stripe is fundamentally broken, the chip is a technology which can be (incrementally) improved. I used to work for a GSM operator. until 2001-2002 it was pretty easy to clone a GSM SIM. After that, better chips were made which were locking themselves when detecting attempts to brute-force them to get their data. If the hackers figure out a way to clone the Credit card chips, it will surely work only on some cards, not all as it happened with magnetic stripe. And those can be replaced with stronger chips without the need to replace all infrastructure.
Even in this incident related by Brian, the attack only works because there are still instances accepting cards with info cloned on the magnetic stripe. The sooner this obsolete technology will disappear the safer we’ll be.
Of course they are secure….. if you implement them properly. They all have there own inbuilt key and crypto engine, and produce a unique cryptogram for every transaction. If the issuer doesn’t bother to configure the chip correctly and doesn’t bother to open the cryptogram and test contents, then you can clone them. If the issuer is going to be a cheapskate, not bother learning what the technology does and then implement proper transaction authorisation…. then the technical hurdle is higher than magstripe cloning, but cloning as a packaged fraud solution for the grunts on the street is possible. I suspect it sill take your issuers to be whacked by cloning before they open the manual and work out that CHIP transaction authorisation can be a lot strong than magstripe transaction authorisation.
CHIP and PIN was rolled out nationwide in the UK in 2004; within weeks my daughters CHIP’n’PIN card had been cloned. Only because she could proove she was using the ‘real’ Card in Cambridge within 30 minutes of the ‘cloned’ card being used 100 miles away in Oxford was she able to prove there was £1500 of fraud on her card ….
I still don’t use Contactless Payments in case I can’t prove it was me …
Brian- excellent info.
One would think everyone would check for CVV but apparently thieves found an interesting vulnerability allowing them to target specifically. Great photos show the thieves went to some length to build the skimmer slim to fit in the tight space with highly integrated SMT components. I wonder how many shimmers installation ‘fails’ there have been as it looks tricky to insert.
Thanks for great reporting !!!
It never ceases to amaze me the lengths to which these “miscreants” will go to make a little money. Why can’t they use their obvious talents in worthwhile, nay-even legal, endeavors? Oh well.
Unfortunately, it pays better and the risks are relatively low. If a person is “ethically and morally challenged”, it isn’t a big leap to cross that line. Fortunately, there are some “good guys” left who are willing to try and stop them.
Little money? LOL. I personally know of people who made millions in a single month from skimming cards and capturing pins. They do it because it’s easy money and most of them despise banking organizations, so it’s a win/win for them.
To the people who wonder why ‘miscreants’ (their quotes, not mine) get up to such things and not to better things: You need to adjust your thinking and start from a different place, entirely: The security industry ecosystem. There’s no economic benefit in actually fixing the problems, just like there’s no economic benefit in actually creating secure systems or making AV that actually works without a subscription model.
At the end of the day, if you really want to fix something, you close down the very rivers and valleys of revenue that come with only partial fixes. Which means the entire ‘security industry’ would collapse. Suffice to say the security industry has no desire to collapse — and suffice to say at some point if you do make a system/network sufficiently secure, you’ll certainly not be making jobs available for people who go around skimming your bankcards.
While I’m sure we agree that ‘carding’ and ‘skimming’ are unethical, and that it’d be lovely if people did things that are better for themselves and society, minus the ethical and moral potholes, it might be a good idea to consider what, exactly, kinds of jobs those might be — especially given the various skill levels (and often lack thereof) possessed by various types of ‘miscreants’ (and perhaps their dubious ethics). We no longer live in a world where technical knowledge is enough, in and of itself, to provide a pathway to success. So we need to start thinking about what might be, and bear in mind that we may not necessarily want all the ‘tech’ that would come our way if we willy-nilly encourage people to keep pushing the envelope. I’m sure someone thought they were really doing something good for humanity, for instance, when they developed in-car wifi.
You’re one of those guys that can only see nails because all you have is a hammer.
Not at all. I’m just one of those people that think things like toasters have no business being connected to the internet (not to mention airplanes, cars, buses, climate control, elevators, refrigerators, etc).
Lest ye forget, those who make the best active defense people and those who make the best active offense people rarely think the same way, have the same skillsets, or have similar mindsets.
It’s easy to break things. It’s harder to explain why something can be broken, and it’s even harder to fix it (especially when you don’t work for the company that makes a product).
If anything, I’m someone who sees an entire garage full of tools and understands that you don’t use the edge of a hammer to pull out a screw.
I wonder how long before NFC-based systems like Apple Pay will also be leveraged for authentication at ATM’s; such a set-up would seem ideal for eliminating both the risk of skimming and PIN capture. Obviously such a solution is not ideal for every customer but for a growing segment of the population it would seem to eliminate the risk of useful data being stolen.
A long, long, long time by my guess.
Banks are slow, and hate change. While most of the larger banks and credit card companies are on board with ApplePay and others, the majority of the smaller guys are not. My bank, which is a regional 3 state brand has not implemented, and don’t plan to soon. They want everyone else to work out the bugs, and the cost of implementation to come down. The likelihood of a customer choosing a new bank due to lack of support is so low that it’s not worth it to them.
Not to mention, the costs would be astronomical to try and replace all those ATM’s. ATM’s are NOT cheap, especially when we are talking about the bank owned machines in their lobby or drive-thru. Then you have all those independent ATM’s owned by 3rd parties that place them in gas stations and such. The companies that place those likely aren’t going to want to spend the money to upgrade the security when the risk is low for them, nor are those independents that aren’t using a 3rd party to have an ATM in their business.
I think we would need to see a cost effective way to retrofit existing ATMs to support NFC withdrawals, however, I fear that any retrofitting of ATM’s opens a potentially huge hole to the types that create ATM skimmers and other ways to defraud. Unless you could retrofit them with all the components strictly inside the ATM and nothing externally, I see it as too risky. And that doesn’t even include dealing with the software updates that would be required to the ATM, and considering the vast majority of ATM’s run WindowsXP or other outdated OS, it would seem to indicated that there is no motivation to strengthen the security of ATM’s.
Of all the stories I read and see on ATM theft and fraud, the vast majority of skimming style fraud seems to be in countries that have security issues as a whole, not places like the US, Canada, Europe, etc. Its going to be even harder to get those places to spend the money. 99% of the theft I hear about here in the US with ATM’s involves the physical theft of the devices themselves, which NFC authorizations wouldn’t solve.
I think it would be great to get NFC to ATM’s, I just don’t see it soon. At least not until a huge chunk of the population has adopted NFC for payments, and we are probably a generation or 2 away from that.
If these malsubjects would put all that ingenuity to good use… oh mine! Google would be out of business! Scary!
What’s I think is a little oversight in the article is that in Mexico the cards were issued as Half – EMV, this is, they use Chip plus signature, not chip plus PIN.
This means, if you have Chip’s information, I think is plausible to get chip’s information and use it for a fraudulent transaction using a fake signature.
I have witnessed well documented credit card fraud cases being rejected by a major bank in Mexico since they supposedly were done using chip transactions. In this case of course the responsibility, according to the bank, is transferred to the cardholder.
Chip & Signature doesn’t make it “half EMV”. EMV cards have a list of cardholder verification methods (CVMs) that are in priority order. They can use any of the following:
Online enciphered PIN
Offline enciphered PIN & signature
Offline plaintext PIN & signature
Offline enciphered PIN
Offline plaintext PIN
Signature
No verification
EMV is not about making everything perfectly secure. It’s about allowing retailers (or rather acquirers) to make fine-grained decisions about how much risk to allow.
So there are pins, signatures, magnetic stripes and now chips. These layers of security are still somewhat easily bypassed. Would adding in retina and fingerprint scanning simply be too much PII to jeopardize, given that those too, will probably be cracked at some point in their security lifecycle?
It’s tough to change fingerprints or retina patterns if the info gets stolen, as in the USA’s Office of Personnel Management breach.
Interesting article about a Toronto company Nymi. They testing biometrically-authenticated wearable payments with MasterCard, TD.
http://www.itbusiness.ca/news/nymi-testing-biometrically-authenticated-wearable-payments-with-mastercard-td/58661
I am one of the testers. it is terrible and inconvenient and will never gain popular acceptance. the idea is kind of cool but not practical at all.
Dynamic two factor authentication with your phone fixes all of this but the credit card companies don’t want to bother with this. Give people that use the 2FA a lower interest rate or other benefits and use the money from the people who don’t want to use it to pay for any residual fraud costs.
Also, who wants to go around with their phone tracking everything they do INCLUDING every financial transaction they make (in and out of roaming)? If I didn’t know you were being serious, I’d think you were trolling. What an awful idea. 🙂
Johnny: Dynamite solution.
Brian
Good article. Do Mexico use Chip & PIN?
I am constantly amazed at the level of skepticism (NIH?) from the US side of the pond on EMV C&P.
All the stats in the UK point to a huge reduction in counterfeit card fraud and roughly a third reduction in card fraud overall since 2004.
One of the biggest issues is the requirement for backward-compatibility with non Chip & PIN territories. We really need to get the stripe off the cards (and the PAN too, while we’re at it, but that’s another story).
No, EMV Chip & PIN is not perfect. But when I read the comments on your blog it always sounds like “Well until they improve the airbags and seatbelts, I’m just not using them!”
I wouldn’t mind so much, but (apparently) two thirds of UK-issued card fraud stems from the US. I know we like Disneyland but that’s a heck of a lot of Mickey!
M
All of you saying we should move to 2FA with phones miss the point of banking, which is that it is (possibly by law, i’m looking at you, EU) required to be accessible to everyone fairly and evenly, and not everyone has a mobile phone, or wishes to carry a code generator fob with them at all times.
Ease of use for ALL customers has to be a consideration. Once you solve that for a good security system, let alone one with 2FA, come post about it, until then, stop moaning.
(also relevant, while 2FA raises the barrier to entry of breaking card security quite high, it’s not as foolproof as you might think)
Really people. This isn’t a hack of the EMV chip security which remains extremely high. It’s a interim, cost reduction of hacker tools. It’s easier to hide than a mag stripe reader and fits in places that use EMV chip readers but designed to strip the unsecured info on the magnetic stripe which is useful to create clone mag stripe cards though of somewhat limited utility in that they can only be used on systems that don’t verify the iCVV.
None of this is useful once the laggard USA converts to EMV chip readers which will be quite soon after the risk shifts to the merchant in Oct.
The vast majority of CC fraud with EMV chipped cards is done by cloning the mag strip and that opportunity is rather short lived.
The remaining vulnerability will be online, CNP, purchases. There are ways to mitigate that and it will be interesting to see how that evolves.
Finally – someone who (i) read the article completely; and (ii) understands EMV.
The USA currently has 47% of global card fraud yet only 24% of global card volume. EMV will absolutely close that gap (although Chip and PIN would have closed it further).
EMV will not eliminate card fraud. It will make fraudulent CARD PRESENT transactions much more difficult for the bad guys. All of the talk about End-To-End encryption will not be at all helpful for CARD NOT PRESENT transactions (eg. that series of tubes we call the internet). Tokenization and 2FA would definitely help online fraud issues.
Please remember one other important thing – more than anything else, EMV is meant to shift the liability from the Card Associations to the Merchant.
For all the technobabble spouted here, EMV is a very good solution for the EXISTING technology. It’s practical. And it works – the UK has seen a 70% DROP in card fraud since introducing Chip AND PIN in 2003. Fraudsters migrate to the weakest link. And right now, the USA is that rusty, old and tired magnetic-stripe link.
Interested to know if this wasn’t just a skimmer but a man-in-the middle attack between the ATM reader chip reader and the chip. With the current EMV protocol this isn’t authenticated or encrypted and there are viable MITM attacks if you can make the shim thin enough and fast enough. Is this the first in the wild (rather than the lab)?
PS: No you can’t clone an EMV card – it signs the transaction with a private key as Dan says. Yes EMV would have stopped the ‘Target’ type attack because the data intercepted would be valueless except in ECom and MOTO (which is a much tougher cash-out than cloning mag stripe).
JD
Your comments about ATMs could be more informed. Having just gone through an upgrade of several NCR ATMs I can tell you that WindowsXP is no longer an issue. The chip card readers on those ATMs are not supported by the embedded XP O/S. I can’t imagine Diebold or Hyosung are any different.
And, having seen what it takes to install mandatory headphone jacks in all ATMs a few years ago for ADA compliance, then installing a NFC reader on an existing ATM will be no big deal. Hyosung already makes a model with both an NFC and a fingerprint scanner built in.
All of these comments and not one joke about “Chip & Skim?”
Anyway, Chip & Pin was a typical exercise in closing the barn door after the horse has escaped. Yay tokenization: Apple Pay, Google Pay, etc.
Reading all the comments made things a lot more confusing for me.
Can we summarise the situations/implementations under which EMV is beneficial and under what conditions it fails(ie, the data gets leaked through POS etc)
Interestingly many comments on how chips are not helping. Looks like many have zero understanding why chips are not secure here. It’s because some issuers does not check even CVV! Chip and magstripe has different CVVs.
And second reason – come technologically challenged countries in payments – for example Cambodia and USA – because of them we have zero security and magstripe still.
Some things don´t quite make sense.
First, if it was a dip reader, I doubt it was an EMV enabled ATM, since EMV requires the card to be present during the transaction while the in-and-out dip readers just read the magstripe.
Second, while you could get some data from an EMV chip, you wouldn´t get enough to make a magstripe clone (iCVV/CVV3 in the EMV chip is different from the magstripe CVV). Any issuer not checking the CVV-mismatch should seriously ask himself if they know what they are doing.
My local Target finally has their chip readers up. Swiped my card as usual but the reader insisted I put it in the chip reader slot. Chip transaction seems to take a long time to compared to swiping, I don’t imagine the stores will be happy with that.
I haven’t seen one person mention what, to me, is an easy and obvious solution. User control. The retailers and CC companies track and store so much information about you and the transaction – so much so that they say they can tell if a woman is pregnant before she knows by what she is buying (see the Target and Church goers suing them for sending baby coupons to their daughter). There is no reason they cannot implement a simple system were I, the user, can go in and limit my card to $x/day $x/transaction or put a geo fence on where my card can be used (they know where you are, what you are buying, how much etc so there is no reason to not be able to put any type of limit on a transaction). Most people do not travel outside of their city/town on a daily basis. The user can relax the requirements when they do. If you are a consistent traveler (aka business person) then you may have to fall into a higher risk category (aka higher costs/interest on your card). Think Discover card ‘freeze’ feature – easy on, easy off. Yes you need a smartphone/app but it is the users choice at that point if they want that feature. If I have a $100/transaction limit and I know I’m going to spend $101 I should be able to easily ‘unfreeze’ my restriction for the transaction then ‘freeze’ it/turn back on my restrictions. Put the control into the users hands.
“But there may be some instances in which banks are doing this checking incorrectly or not at all during some periods”
Also some EMV cards have the same CVV on the chip and on the magnetic stripe (i.e. they don’t use iCVV). In these cases the criminal can create an exact copy of the magnetic stripe based only on the chip data.
I have never heard of this, and it goes against all the EMV best practices guides that the associations share with the issuers.
Not only best practices, firm requirements.
Whether it’s a “best practice” or “firm requirement”, the issuers have a lot of influence over the card schemes and sometimes blatantly break the rules while publicly claiming to comply with them.
I tested the cards of myself and colleagues with a magstripe reader and chip reader and found that many UK banks still did not implement iCVV despite despite the bank spokesperson saying that they do. See http://sec.cs.ucl.ac.uk/users/smurdoch/papers/ieeesp09tamper.pdf
Just because it’s a requirement, I wouldn’t believe something unless it’s been verified by an independent third party.
I don’t know about Visa but MasterCard recommends that iCVC is not used to authenticate an EMV transaction when ARQC is available. some partial grade terminals still exist where ARQC is not used (funny enough, mostly in Mexico and Latin America). that’s really the only time iCVC comes in handy
They help quite a bit, but are only a new hurdle. They are especially good for retailers, then implement encrypted devices with tokenization – they no longer see or store CC info on their networks. This does solve the Target Attack – if tokenization is implemented. So if brick and mortar retailers implement correctly, it’s a good step.
The problem is that the banks went to chip n signature, not chip n pin, because they were not ready by the Oct 2015 deadline. Also, it doesn’t solve eCommerce, PC or mobile payment yet. Again, good step, but there will be many hacks still.
BTW – the biggest risk, if you don’t shield your chip enabled CC, I can read it remotely and swipe at least one transaction. Funny that the banks are not recommending shields with the cards (or issuing them with a shield pocket).
Kerbs wrote about this skimmer thing, but in EU we all have chips and pin, and this is old about 10 years or so. Even if somebody stole your money, in day or so you will get full refund with big apology from your bank. So it’s not a big deal.
New thing is RFID cards, that you can pay without entering pin. This is limited to around 15€ per transaction but still, 15€ without pin too much.
so this shimmer reads the track data from the chip which includes the iCVV/iCVC. The fraudsters then take this data and create a magstripe card?
This should never work if the issuer is validating CVV/CVC on their card present magstripe transactions as the iCVV/iCVC that was stolen will never match the true magstripe CVV/CVC.
You’re right. Hence the penultimate paragraph in the story:
“Banks can run a simple check to see if any card inserted into an ATM is a counterfeit magnetic stripe card that is encoded with data stolen from a chip card. But there may be some instances in which banks are doing this checking incorrectly or not at all during some periods, and experts say the thieves have figured out which ATMs will accept magnetic stripe cards that are cloned from chip cards.”
well that’s just silly. Simple fix.
Once again it shows that EMV is not broken, it’s just that it is not being implemented correctly.
Always love hearing people in US still using a signature to “prove” identity….It makes me imagine someone riding to work on a horse and cart making a phone call on an iphone.
USA is one of the only few “1st class ” countries in the world that still dont have C&P/EMV yet… They will be implementing it this Oct 2015. The stats are.. USA makes up for 24% of world purchases on CC & accounts for 50% fraud.
Catch up you guys lol
Michael: Heaven forbid. NEVER!! Doing anything but placing and shifting as much cost and risk as possible on the naive end retail consumer, regardless of the type of business, would be un-American!
Please don’t say ‘PIN numbers’, Brian. I expect the best of you.
I include Brian Krebs web site in my book:
When Bank Systems Fail Debit cards, credit cards, ATMs, mobile and online banking: your rights and what to do when things go wrong (2nd edn, PP Publishing, 2014) http://www.stephenmason.eu/?page_id=40
This will go into the next edition.
Regarding ‘trust’ and ATMs see my article with Timothy Reiniger:
‘“Trust” Between Machines? Establishing Identity Between Humans and Software Code, or whether You Know it is a Dog, and if so, which Dog?’, Computer and Telecommunications Law Review, 2015, Volume 21, Issue 5, 135 – 148: http://www.stephenmason.eu/?page_id=218
ATM fraud has increased in Europe. so nobody should be complacent.
This looks like it’s using an Atmel ATXMEGA32A4U and a flash chip, no evidence of a battery suggests pulling power from the chip reader in the ATM. So you could track the Atmel chip by pulling it’s serial number. As for detection, setting up the ATM’s with a current sense and cuttof(aka a PTC or diode fuse) would stop operation of the shimmer. Might be worth the ATM companies checking out, it’s a 10 cent part.
Most commenters seem to neglect the fact that ‘Chip’ and ‘PIN’ are independent security mechanisms and address different problems.
Chip addresses the Counterfeit problem. It provides the assurance to the bank that the card being used is not copied card, but the original card issued by the bank. How it does this is, by creating a one time value for each transaction that can be validated by the bank. There are different levels and many options for a bank to choose from while implementation. The specifics of the implementation determines how many more checks the bank will place on top of the basic EMV security and how the card will perform in different environments/different types of terminals. Chip&PIN and Chip&Sig cards are identical from this perspective.
PIN addresses the lost/stolen card usage problem. It provides the assurance to the bank that the card is being used by the cardholder, or someone who knows the secret information. PIN, in general, is indeed independent from Chip. What comes with the chip is the ability to validate PIN for transactions where the terminal is not connected through a communication line. So, there’s the possibility of checking PIN on more transactions.
So in summary Chip&Sig cards provide protection against copied card usage only, and Chip&PIN cards address both issues at the same time.
Rules and recommendations followed in US today for card configurations are a result of EMV implementation experience from other parts of the world for years, so doesn’t allow for some configuration mistakes which existed 10 years ago. Also, as the article suggests banks should be processing other basic checks to make sure only eligible transactions make it through. CVC check, ARQC check, applying limits on certain types of transactions etc.
On the other side, EMV will not address all Fraud issues, since it’s strictly limited to the transactions where physical chip is used. Magnetic stripe transactions, e-commerce transactions etc. will not be EMV. There are emerging payment technologies, such as tokenization, biometrics etc. that address other types.
As some suggested, EMV migration is a step in the right direction, it’s not the final destination.