Networking firm Ubiquiti Networks Inc. disclosed this week that cyber thieves recently stole $46.7 million using an increasingly common scam in which crooks spoof communications from executives at the victim firm in a bid to initiate unauthorized international wire transfers.
 Ubiquiti, a San Jose based maker of networking technology for service providers and enterprises, disclosed the attack in a quarterly financial report filed this week with the U.S. Securities and Exchange Commission (SEC). The company said it discovered the fraud on June 5, 2015, and that the incident involved employee impersonation and fraudulent requests from an outside entity targeting the company’s finance department.
Ubiquiti, a San Jose based maker of networking technology for service providers and enterprises, disclosed the attack in a quarterly financial report filed this week with the U.S. Securities and Exchange Commission (SEC). The company said it discovered the fraud on June 5, 2015, and that the incident involved employee impersonation and fraudulent requests from an outside entity targeting the company’s finance department.
“This fraud resulted in transfers of funds aggregating $46.7 million held by a Company subsidiary incorporated in Hong Kong to other overseas accounts held by third parties,” Ubiquiti wrote. “As soon as the Company became aware of this fraudulent activity it initiated contact with its Hong Kong subsidiary’s bank and promptly initiated legal proceedings in various foreign jurisdictions. As a result of these efforts, the Company has recovered $8.1 million of the amounts transferred.”
Known variously as “CEO fraud,” and the “business email compromise,” the swindle that hit Ubiquiti is a sophisticated and increasingly common one targeting businesses working with foreign suppliers and/or businesses that regularly perform wire transfer payments. In January 2015, the FBI warned that cyber thieves stole nearly $215 million from businesses in the previous 14 months through such scams, which start when crooks spoof or hijack the email accounts of business executives or employees.
In February, con artists made off with $17.2 million from one of Omaha, Nebraska’s oldest companies — The Scoular Co., an employee-owned commodities trader. According to Omaha.com, an executive with the 800-employee company wired the money in installments last summer to a bank in China after receiving emails ordering him to do so.
In March 2015, I posted the story Spoofing the Boss Turns Thieves a Tidy Profit, which recounted the nightmarish experience of an Ohio manufacturing firm that came within a whisker of losing $315,000 after an employee received an email she thought was from her boss asking her to wire the money to China to pay for some raw materials.
Ubiquiti didn’t disclose precisely how it was scammed, but CEO fraud usually begins with the thieves either phishing an executive and gaining access to that individual’s inbox, or emailing employees from a look-alike domain name that is one or two letters off from the target company’s true domain name. For example, if the target company’s domain was “example.com” the thieves might register “examp1e.com” (substituting the letter “L” for the numeral 1) or “example.co,” and send messages from that domain.
In these cases, the fraudsters will forge the sender’s email address displayed to the recipient, so that the email appears to be coming from example.com. In all cases, however, the “reply-to” address is the spoofed domain (e.g. examp1e.com), ensuring that any replies are sent to the fraudster.
In the case of the above-mentioned Ohio manufacturing firm that nearly lost $315,000, that company determined that the fraudsters had just hours before the attack registered the phony domain and associated email account with Vistaprint, which offers a free one-month trial for companies looking to quickly set up a Web site.
Ubiquiti said in addition to the $8.1 million it already recovered, some $6.8 million of the amounts transferred are currently subject to legal injunction and reasonably expected to be recovered. It added that an internal investigation completed last month uncovered no evidence that its systems were penetrated or that any corporate information, including our financial and account information, was accessed. Likewise, the investigation reported no evidence of employee criminal involvement in the fraud.
“The Company is continuing to pursue the recovery of the remaining $31.8 million and is cooperating with U.S. federal and numerous overseas law enforcement authorities who are actively pursuing a multi-agency criminal investigation,” the 10-K filing reads. “The Company may be limited in what information it can disclose due to the ongoing investigation. The Company currently believes this is an isolated event and does not believe its technology systems have been compromised or that Company data has been exposed.”
The FBI’s advisory on these scams urges businesses to adopt two-step or two-factor authentication for email, where available, and/or to establish other communication channels — such as telephone calls — to verify significant transactions. Businesses are also advised to exercise restraint when publishing information about employee activities on their Web sites or through social media, as attackers perpetrating these schemes often will try to discover information about when executives at the targeted organization will be traveling or otherwise out of the office.
Ubiquiti noted that as a result of its investigation, the company and its audit committee and advisors concluded that its internal control over financial reporting were ineffective due to one or more material weaknesses, though it didn’t disclose what measures it took to close those security gaps.
“The Company has implemented enhanced internal controls over financial reporting since June 5, 2015 and is in the process of implementing additional procedures and controls pursuant to recommendations from the investigation,” it said.
There are probably some scenarios in which legitimate emails between two parties carry different display and “reply-to” addresses. But if the message also involves a “reply-to” domain that has virtually no reputation (it was registered within hours or days of the message being sent), the chances that the email is fraudulent go up dramatically.
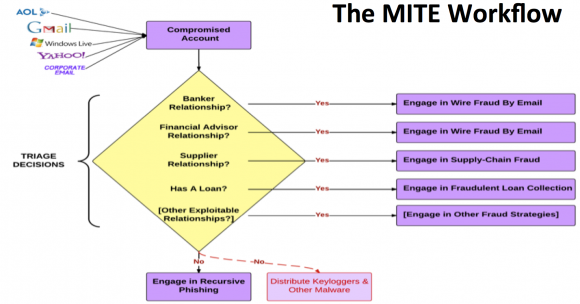
Business Email Compromise (BEC) or man-in-the-email (MITE) scams are adaptive and surprisingly complex.
Unlike traditional phishing scams, spoofed emails used in CEO fraud schemes are unlikely to set off spam traps, because these are targeted phishing scams that are not mass e-mailed. Also, the crooks behind them take the time to understand the target organization’s relationships, activities, interests and travel and/or purchasing plans.
They do this by scraping employee email addresses and other information from the target’s Web site to help make the missives more convincing. In the case where executives or employees have their inboxes compromised by the thieves, the crooks will scour the victim’s email correspondence for certain words that might reveal whether the company routinely deals with wire transfers — searching for messages with key words like “invoice,” “deposit” and “president.”
On the surface, business email compromise scams may seem unsophisticated relative to moneymaking schemes that involve complex malicious software, such as Dyre and ZeuS. But in many ways, the BEC attack is more versatile and adept at sidestepping basic security strategies used by banks and their customers to minimize risks associated with account takeovers. In traditional phishing scams, the attackers interact with the victim’s bank directly, but in the BEC scam the crooks trick the victim into doing that for them.
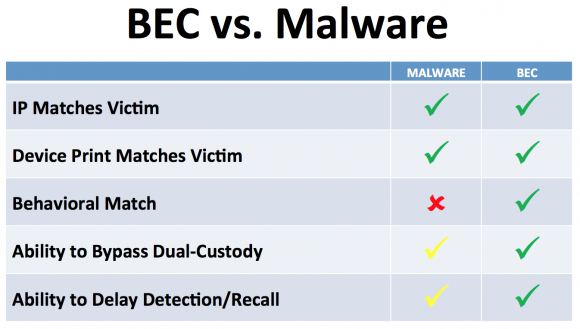
Business Email Compromise (BEC) scams are more versatile and adaptive than more traditional malware-based scams.
Hat tip to Brian Honan at CSO Online, who spotted this filing on Thursday. Update, 4:20 ET: Corrected the spelling in several instances of the networking company’s name.




Basically, employees have to drill into their head that email is not secure. Period! If you recieve email from your boss that you need to wire somebody $$, just tell him/her to at least phone you to verify who they are. In an idea world, they should initial this with the bank who can have 2nd factor identification.
Actually it should be you who calls them (at a known number) to verify the transactions.
Tidy minds are rarely tidy
To help mitigate this, email rules can be configured to block spelling variants of your company’s domain. If you have your SPF records configured correctly, you can also block any emails that come from outside your organization, from *@yourdomain.com, with hard or soft SPF fails.
DMARC.
we have been hit a number of times with these, but never have transfers occurred. In all cases for us, the reply to looked nothing like our domain, but that rarely matters. The source domain WAS our domain, and that made it easy to bypass any additional checking. Luckily we were able to locate the mailer program being used by multiple actors, and block some additional data in the message header.
But the real key is making sure accounting accepts NO direction for wires by email.
SPF doesn’t prevent From: address spoofing, you need DMARC for that.
DMARC on the other hand is pretty effective at that task
C-Level execs are often the targets of phishing attacks, and are many times the ones that don’t take security training seriously. We have started phishing simulations internally at my company, along with required security training courses. After the first round of training, our click rate for phishing dropped from 51% to 12% across the company. Not perfect, but I really feel phishing / network security training makes a big difference.
Only 12%? Which company do you work for, and what’s your PIN and SSN KTHX!
Brian, “our” should be “their” in paragraph 10. Since you are quoting their statement you might have copy/pasted and forgot to change that.
Keep up the good work (and when are you heading toward Winchester area? Would be cool to hang out sometime.)
– John
Unbelievable. The media reporting (including Brian) has been good on these types of scams lately- it’s shocking to see a company get taken for such a large amount (it’s about an entire month of revenue for Ubiquiti ). I would generally say an unfortunate breakdown of internal control systems, but given the size of loss and various layers of checks/balances, authorization limits that most companies have for large electronic payments- this looks like an extreme case of gross negligence or some type of internal collusion. They still have almost 1/2 B of cash though, I trust they will be more careful with the payments control environment.
Great reporting Brian, would enjoy understanding more details if they become available.
It never ceases to amaze me that this goes on and on in enterprise business! Don’t business execs EVER go to seminars about security at ALL! You’d think at least the banks would suggest this for their customers; especially since they are a target too!
I give up!! :/
Sure they go to seminars but, at the end of the day, they will almost always choose convenience over security.
Just like U.S. credit card processors choosing to stay with magnetic stripes while the rest of the world switched to smart chips.
Believe it or not, the FFIEC (US bank examiner) actually require an information security awareness program for consumer and commercial bank customers. Many banks have programs, but many customers just choose to ignore their guidance.
http://www.ffiec.gov/pdf/authentication_guidance.pdf
Hope this doesn’t ruin them. They make pretty good kit.
If a company uses GPG signatures on their email consistently and employees are taught to check that these are valid & associated to the right name, a lot of this risk vanishes.
Not really, it just makes things worse when a hacker compromises a computer with the GPG keys.
Two factor authentication is a must to protect against this scenario– and that means using an unrelated previously established means of communication to confirm authenticity of the request.
The other suggestions about screening for mismatched email or DMARC is probably worth doing, but again it will fail when someone’s computer or credentials are compromised.
Security here is accomplished by viewing each email as circumspect, not by making the recipient confident in its authenticity.
If an attacker has indeed compromised the sender’s PC, then using signed messages is no help.
But that’s not what happens in many of these attacks – including this one. The email is forged – it comes from some unrelated system. A much easier attack to pull off.
Note that encryption isn’t even the issue here. While it would certainly make an attacker’s job a bit harder if he can’t read messages, so can’t as easily imitate style and timing and such, the major protection is from the inability to put the analogue of the old-style recognizable signature – or even just initials – on the message.
Either GPG or S/MIME work for this role. Both Outlook and Apple Mail.app (on both Mac’s and iPhones) contain built-in S/MIME support; I don’t know off-hand about Android. GPG extensions are available for all the platforms, though they are a bit more of a pain to use on iOS. But some training and care is *definitely* needed: The usual mode for dealing with signed incoming mail, if the signature isn’t known to the implementation, is to accept the attached public key and signature. You have to check *who* signed the message, not just that it *was* signed. For applications like disbursements, it would be much better to have a fixed list of acceptable signatures. Which clients have such a configuration, I don’t know.
— Jerry
I had 2 clients hit with this scam in the past 2 months, they lost a total of $100,000.
I’ve seen one former SMB client in Kentucky become the target of a scheme similar to this except that it involved the impersonation of a former outside financial services provider, just last week.
Ko ko ko me
For the human stupidity, there’s no EMV solution…
This is exactly the kind of thing that is prevented by effective security awareness training. The bad guys have a back door into your network; your employees. You can spend a large amount of money putting all kinds of security software in place and you _should_, but it can be all wasted if you don’t also train your employees and keep them on their toes with security top of mind.
In my experience, training employees only works if they believe that management is committed to it. As soon as it gets out (believe me, it does) that so-and-so big shot does not adhere to the rules the employees become lackadaisical, too.
Much of this would be better done by filtering things out of the network (blacklisting if you will). It makes no sense to install extra software to all the computers in the office to prevent everyone from going to websites that create problems. Just block access to those sites. That extra software only serves to slow down the computers and bog down the network. Many companies disallow Facebook on company assets on company time. Facebook (and all it components) can be filtered out at the router level. Quite often, there are only five or six external (non-intranet) websites that really needs to be accessed anyway. Just filter out everything but those particular sites. Full (un-filtered) web access is rarely needed (on the business end of things).
With a real plan like this put into place….most email issues are relatively easy to mitigate. Although, way too many people still think that email is private. Email is NOT private. It NEVER was and NEVER will be. The closest that can be acheived is through running your own email server and even that is not private.
Thanks Brian, for bringing this up.
Marketwatch credited Krebs on Security (without a linkback to the story). WSJ headline says that $UBNT has had no CFO for awhile, but login required to see the rest of the story.
Brian,
I know you usually focus on cybercrime that affects the U.S., but have you seen this article?
http://www.ndtv.com/world-news/dixons-carphone-says-cyber-attack-may-have-exposed-customers-data-1205322
Keep up the good work
Another example of an old mail fraud scheme adapted for the digital world.
If you are in the security business you recognize it as a False Billing scheme with a few digital wrinkles. Virtually all the schemes from the former primary communication system of the past (mail) have transitioned to today’s primary communication email system.
Many companies appear to not take true security serious. You can usually determine this by examining a company org chart and see where, if at all, this responsibility is noted.
Sounds like some inside people got themselves a nice bonus. 46 million goes along way. And just blame it on hackers , say we will do better, do retrain.. And people forget about it when another inside job happens.
Almost happened to us. Not an inside job. Same team back in late 2014. They registered a close version of our domain (also using VistaPrint) and impersonated email from executive to accounting. We do have proper internal controls and we caught it immediately, but it definitely caused us to change a few things regardless of the fact that we caught it this time.
This was the exact motivation behind trusted operating systems and mail guards in the 90’s. Companies like Argus Systems and Nexor still sell them. Many businesses think that the ability to know who sent a message along with make forgeries difficult isn’t justifiable in cost. I just read a dollar amount that’s vastly more than secure messaging systems.
There’s a few others and I that could sell them a strategy to immunize them against this. They’ll probably never notice us. More likely, they had some security assessments from mainstream types with small fixes, some checklist items, and think they’re fine now. Until the next attack that exploits the inherent lack of trustworthiness in their infrastructure. A common problem that’s not going away for most in industry.
Businesses with email based processes like this could make impersonation much more difficult on the impersonators by buying FIPS 140-2 smart cards for their employees ($100/year) and requiring all email to be electronically signed. They could also require the same of their suppliers. This is a relatively cheap mitigation to this sort of risk and the only change in business processes is the requirement that the cards be plugged in to the user’s computers.
Wait – These companies are transfering millions of dollars using authorizations sent by e-mail? Seriously? They deserve to get hit.
And,”…held by a Company subsidiary incorporated in Hong Kong to other overseas accounts held by third parties…”. Tax evasion, maybe?
Agreed. As far as I’m aware, all companies that have hundreds of millions of cash assets in the bank have fairly sophisticated and comprehensive controls in place. The lack of CFO should not result in a lack of oversight.
The unfortunate thing with this loss is that the scammers who perpetrated this have now funded themselves for decades to continue to prey on other companies.
The company just reported the loss last week, does anyone know when it actually occurred and how long it took company to determine the fraud.
What’s the skill set needed to do something like this? Obviously technical part of the email spoof is required. But what about the mining for common phrases, that seems like it would take a good command of English (or whatever native tongue of the target). Would you need to know who send these types of requests – company names etc? Would you need to know part numbers for materials or otherwise have information about the purpose of the transfer?
I think companies need a sanity check (no pun intended) where large potential payments – which should be screened at an “O” level (what else is a CFO doing?)
Its simply no Attention to Detail. No one spot checks to see if the service was even done, or the contractors or service was even on the approved list or potential payroll /payment database or list. No one calls the number on the invoice to validate the amount and the validity of the other end.
Sure the CEO /CFO may chew your behind for questioning their order to pay if it is legit…. But the first time they catch a phony email for millions of dollars, they will quickly make the policy mandatory.
The rubber stamp of Approved…Approved…Approved Approved needs to go away. For the amount of money being handled in these cases – there has to be a better way. Heck, mail them a cashiers check with a 2-3 day delivery time. If something is bad, all it takes is a quick call to the bank to void payment. This might thwart some of the illicit activity.
A simple phishing email can do wonders, and until this scam is dead and buried, people need to figure out better way. =\
“O” level? You mean “C-class”? Not all “officers” are C-Class.
Who’s overall responsible ? CEO. Who responsible for finances? CFO. A Chief is a Chief regardless. Some have power, some are pawns.
i dont get it, how can one transfer more than seven/six figures dollars just by being ordered through an email! common sense dictates that a verbal check suffices i.e
a telephone call to verify the email order.
This is worrying when the geeks get out-geeked. Presumably, these geeks geek all day long, but not sufficiently to be thoroughly up on cyber-security.
Amazing, I’ve never heard of phishing getting so much from a single victim
I got a tip from an FBI Agent about a year ago, that has helped raise phishing awareness in my company.
On our Exchange server, I made a rule that adds [EXTERNAL] to the subject line of every email that originates outside of our Exchange environment.
My users are much more aware of phishing and it is pretty obvious when someone is trying to phish us.
Why has this not hit the mainstream news yet?
The mainstream news is ran by people that will only tell you what they think you need to hear. With them, it’s more about what they wont tell you. It’s part of what makes places like this a better source of news.
Submarine 0-day opportunity.
For tech companies having international development, some number will have the code generation located differently than code delivery… the foreign tech lead emails the code delivery department something to include (like a cert, seems unlikely that any reasonable org would accept a binary outside of a signed library, but then you’d think companies wouldn’t be scammed for 46M either… so maybe include a binary). Email would have some reasonable excuse about recent meetings gleaned from the purloined email stream, security, or blablabla.
Now the code stream being delivered with the product– or worse, an update– has a nice 0-day built in. For sale, or for botnet building, whatever way provides the best monetization.
Clearly the 46 Million loss on their 8-K filing did nothing to harm the company. They have been upgraded from hold to buy in the market. This goes to show, the aggregate lack of knowledge or understanding surrounding this event. It is not even known if there is more risk, but investors are encouraged to buy their stock.
http://www.dakotafinancialnews.com/ubiquiti-networks-upgraded-to-buy-at-zacks-ubnt/348686/
Shakes head sadly.