Many news sites and blogs are reporting that the data stolen last month from 37 million users of AshleyMadison.com — a site that facilitates cheating and extramarital affairs — has finally been posted online for the world to see. In the past 48 hours, several huge dumps of data claiming to be the actual AshleyMadison database have turned up online. But there are precious few details in them that would allow one to verify these claims, and the company itself says it so far sees no indication that the files are legitimate.
Update, 11:52 p.m. ET: I’ve now spoken with three vouched sources who all have reported finding their information and last four digits of their credit card numbers in the leaked database. Also, it occurs to me that it’s been almost exactly 30 days since the original hack. Finally, all of the accounts created at Bugmenot.com for Ashleymadison.com prior to the original breach appear to be in the leaked data set as well. I’m sure there are millions of AshleyMadison users who wish it weren’t so, but there is every indication this dump is the real deal.
Original story:
A huge trove of data nearly 10 gigabytes in size was dumped onto the Deep Web and onto various Torrent file-sharing services over the past 48 hours. According to a story at Wired.com, included in the files are names, addresses and phone numbers apparently attached to AshleyMadison member profiles, along with credit card data and transaction information. Links to the files were preceded by a text file message titled “Time’s Up” (see screenshot below).
From taking in much of the media coverage of this leak so far — for example, from the aforementioned Wired piece or from the story at security blogger Graham Cluley’s site — readers would most likely conclude that this latest collection of leaked data is legitimate. But after an interview this evening with Raja Bhatia — AshleyMadison’s original founding chief technology officer — I came away with a different perspective.
Bhatia said he is working with an international team of roughly a dozen investigators who are toiling seven days a week, 24-hours a day just to keep up with all of the fake data dumps claiming to be the stolen AshleyMadison database that was referenced by the original hackers on July 19. Bhatia said his team sees no signs that this latest dump is legitimate.
“On a daily basis, we’re seeing 30 to 80 different claimed dumps come online, and most of these dumps are entirely fake and being used by other organizations to capture the attention that’s been built up through this release,” Bhatia said. “In total we’ve looked at over 100GB of data that’s been put out there. For example, I just now got a text message from our analysis team in Israel saying that the last dump they saw was 15 gigabytes. We’re still going through that, but for the most part it looks illegitimate and many of the files aren’t even readable.”
The former AshleyMadison CTO, who’s been consulting for the company ever since news of the hack broke last month, said many of the fake data dumps the company has examined to date include some or all of the files from the original July 19 release. But the rest of the information, he said, is always a mix of data taken from other hacked sources — not AshleyMadison.com.
“The overwhelming amount of data released in the last three weeks is fake data,” he said. “But we’re taking every release seriously and looking at each piece of data and trying to analyze the source and the veracity of the data.”
Bhatia said the format of the fake leaks has been changing constantly over the last few weeks.
“Originally, it was being posted through Imgur.com and Pastebin.com, and now we’re seeing files going out over torrents, the Dark Web, and TOR-based URLs,” he said.
To help locate new troves of data claiming to be the files stolen from AshleyMadison, the company’s forensics team has been using a tool that Netflix released last year called Scumblr, which scours high-profile sites for specific terms and data.
“For the most part, we can quickly verify that it’s not our data or it’s fake data, but we are taking each release seriously,” Bhatia said. “Scumbler helps accelerate the time it takes for us to detect new pieces of data that are being released. For the most part, we’re finding the majority of it is fake. There are some things that have data from the original release, but other than that, what we’re seeing is other generic files that have been introduced, fake SQL files.”
Bhatia said this most recent leak is especially amusing because it included actual credit card data, even though AshleyMadison.com has never stored credit card information.
“There’s definitely not credit card information, because we don’t store that,” Bhatia said. “We use transaction IDs, just like every other PCI compliant merchant processor. If there is full credit card data in a dump, it’s not from us, because we don’t even have that. When someone completes a payment, what happens is from our payment processor, we get a transaction ID back. That’s the only piece of information linking to a customer or consumer of ours. If someone is releasing credit card data, that’s not from us. We don’t have that in our databases or our own systems.”
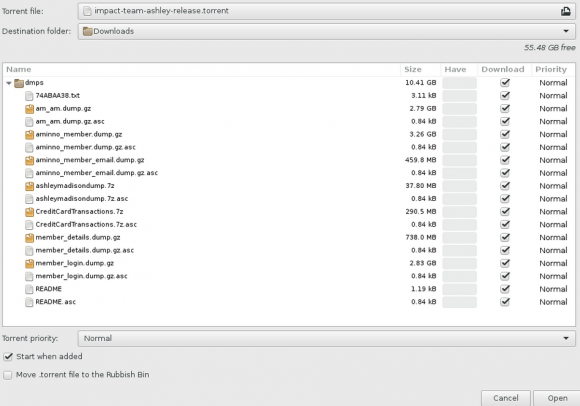
A screen shot of the archive released recently that many believe is the leaked AshleyMadison database.
I should be clear that I have no idea whether this dump is in fact real; I’m only reporting what I have been able to observe so far. I have certainly seen many people I know on Twitter saying they’ve downloaded the files and found data from friends who’d acknowledged being members of the site.
Nearly every day since I first reported the exclusive story of the Ashley Madison hack on July 19, I’ve received desperate and sad emails from readers who were or are AshleyMadison users and who wanted to know if the data would ever be leaked, or if I could somehow locate their information in any documents leaked so far. Unfortunately, aside from what I’ve reported here and in my original story last month, I don’t have any special knowledge or insight into this attack.
My first report on this breach quoted AshleyMadison CEO Noel Biderman saying the company suspected the culprit was likely someone who at one time had legitimate access to the company’s internal networks. I’d already come to the same conclusion by that time, and I still believe that’s the case. So I asked Bhatia if the company and/or law enforcement in Canada or the United States had apprehended anyone in relation to this hack.
Bhatia declined to answer, instead referring me to the written statement posted on its site today, which noted that investigation is still ongoing and that the company is simultaneously cooperating fully with law enforcement investigations, including by the Royal Canadian Mounted Police, the Ontario Provincial Police, the Toronto Police Services and the U.S. Federal Bureau of Investigation.
“This event is not an act of hacktivism, it is an act of criminality. It is an illegal action against the individual members of AshleyMadison.com, as well as any freethinking people who choose to engage in fully lawful online activities,” the statement reads. “We know that there are people out there who know one or more of these individuals, and we invite them to come forward. While we are confident that the authorities will identify and prosecute each of them to the fullest extent of the law, we also know there are individuals out there who can help to make this happen faster.”
Readers should understand that if this dump does turn out to be legit, that just finding someone’s name, email address and other data in the archives doesn’t mean that person was a real user. As the above-mentioned Graham Cluley points out, AshleyMadison never bothered to verify the email addresses given to it by its users.
“So, I could have created an account at Ashley Madison with the address of barack.obama@whitehouse.gov, but it wouldn’t have meant that Obama was a user of the site,” Cluley wrote. “Journalists and commentators would be wise to remember that the credentials stored by Ashley Madison must be considered suspect because of their shonky practices, even before you start considering whether any leaked databases are falsified or not.”




This just goes to show you, that one should never expect privacy online and should treat it as if you were in a crowded mall. Its the public domain, and uses software and hardware created and programmed by man / woman. As such can be broken in the same manner. It is time to stop holding companies responsible for data breaches and start holding people accountable for their own unethical action’s. Only this will start to get into the heads of the youth that privacy is in the hands of the holder. It is also worth noting that this is getting far more attention then the OPM breach, and that was far more serious then a data leak from a cheating website.
If you use the internet, then expect that your privacy may soon be violated, and only you are are responsible for your privacy unless specifically dictated by the posting of Privacy Act 1974 Compliance.
Found an email checker https://ashleymadisonleakeddata.com/
Checked my own email address and it’s a hit – supposedly I’m in the database. Problem is that I’ve never used AM. So…it’s a BS checker.
Maybe it is time to change your password or email services, as it appears possible your email was compromised and used. I checked all my email’s and they came up as not found. And I am 100% Confident and will take an oath that I have never heard of this site, and was only made aware of it after an episode of Law and Order SVU where they used a site similar to this in a rape assault case.
Perhaps we should ask barack.obama@whitehouse.gov if he’s ever signed up for the site, as his e-mail is listed as valid.
Why do you think they take separate planes? Seems to make that question all the more worthwhile now that you bring it up.
AM is owned by a company that owns other hookup sites. From what I’ve read, those sites were compromised too. Might you be a member of one of those?
That’s a really unfortunate development (but not at all surprising). It’s unfortunate because that site is indexing the data by email address, and as I said in the story, AshMad for the most part didn’t validate email addresses, so the existence of an email address in the database is nowhere near proof that the person who uses that email address was ever actually on AshMad. Now, if the search engines being stood up for this also indicate whether there is payment data attached to the account, that may be harder for people to explain.
No, actually it seems to be as favorable as a site like this could be, since it reports whether an email was validated/confirmed. I tried as a guess joe@yahoo.com, and it was positive, but it explicitly noted that it was an unconfirmed email address. Then I tried a couple of my emails and they were negative, which was a relief, since I have gotten spam from AM on one of them.
I registered 3 months ago with an unique email address, created for AM and never used anywhere else. It is in the database. And this email address cannot be guessed and hardly generated.
Looks legit to me.
I actually went on there years ago(wasn’t married at the time). I thought it was crap and got off the site. Interestingly enough- I put in an email in the checker website that I didn’t use and it registered. Seems suspect to me.
Can someone please tell me where I can find this..
What worries me is the opportunists that will create the search engines for these fake user DBs. Spreading malware, this would be such an opportunity to create multiple fake services.
Also, even if it had REAL data, we should remember that though being scumbags, some people might end up dead as a result. Divorce is the least of my concern for those caught, but suicide, murdering your spouse, being outed as gay. All of these might be lead to death. The likely scenarios of these are so serious that media has a special role. They absolutely have to be careful or they will be nothing but a tool to spread malware and help criminals. I am surprised Wired was so fast to publish their story, being reputable source. I would be worried about this due to all of these reasons.
BUt mostly because criminals will learn how to do better media baiting.
No pity here. Everyone ends up dead. This has happened, no ideas, comments, wishing or hacking will make it go away. If you want to make people feel better or deal with it, go for it. But it’s here and done.
I checked, my email address fake@fake.com was in there, but I don’t recall signing up. lol
What if you made purchase through iTunes?
pak pak !?
I have downloaded the torrent, do you guys know how to open the files ?
hey bro its in here http://www.kaplankomputing.com/blog/miscellaneous/ashley-madison-leaked-data-url-how-to-get-the-data/#comment-4
and please can you share the torrent plz
I’ll just wait till a searchable website comes up, has to be one soon right? Could be fun trolling ex’s new boyfriends. amirite?
Should AM members expect a lot of spam from Tinder and Match ?
You can search emails on https://ashleymadisonleakeddata.com
Theres ALOT of nervous women on that site right now !!
yeah,,, all six of them.
https://2.bp.blogspot.com/_D_Z-D2tzi14/S8TiTtIFjpI/AAAAAAAACxQ/HXLdiZZ0goU/s320/ALOT14.png
I found this article helpful in looking at the overall effect on the company – its minute. BUT look at the potential impact of each of the people involved. Their PII can be out there for decades….
http://www.csoonline.com/article/2932324/data-breach/breach-costs-chump-change-to-bottom-lines-of-big-players.html
Some thoughts:
1) AM doesn’t ever request address, phone number, real name, etc…..other than zip code.
2) AM purportedly doesn’t store credit card data……but who would use their credit card anyway? PayPal….
3) Who would use their daily email address and not a burner address?
4) Who wouldn’t have changed their password by now?
What’s really going on?
J
I’m most excited to see who’s dumb enough to use their work email. Because they exist.
I remembered signing up about 8 or so years ago. It’s been a while. Tried some old email addresses on ashleymadisonleakeddata.com and sure enough one of my alternate gmails was in the database. Browsed over to ashleymadison and tried an old password I used for everything back then and bam, I was in. I never signed up for anything so no credit card data, no real name, etc., but I can personally vouch that from a user database standpoint this leak look legit.
Enter names on this site to find out who was an AM member:
http://ashleymadisonleaked.com
The site takes a while to load search results, but results are found.
Ok so my fake email pops up in that list and it verified that I was a member. I paid with paypal never contacted anyone, just looked. Was constantly accused of stuff, so I just thought sod it! Thing is I didn’t do anything, but if my name gets out, my Mrs isn’t going to believe it. Thing is if like me you was daft enough to sign up you and I could end up lonely forever! it will be a permanent scar forever
Don’t worry, it seems that if you use a third party payement service such as Paypal, your payement information are not stored. It only happens if you paid directly with a Credit card on their site.
The only thing will be your email address and login name…as long as you didn’t use your “real” ones, you will be fine.
So my burner email pops up. Like a fool, I used a prepaid credit card with my home address (I know, I know, the hornies made me do it). But my question is whether the credit card data is synced with the profile data. If they have the credit card, can they connect that with my profile? I’m hoping the profile is disconnected but doubt that it is.
Why would you ever use real data on a burger profile, let alone a real credit card? Get a virtual credit card, citi bank credit cards offer them. and you should of never used your real address or name, the 4 digits in your street address and zipcode is all that needs to match for a credit card authorization to go through.
Is the credit card data synced with the profile? If they have my name because of the credit card, can they see my burner profile too?
Pro tip. credit card companies only check the first 4 digits of your address and the zipcode.. so say your address REALLY is JACK SMITH 1234 meow st. tampa,florida 33605
If you signed up or signed up anywhere and use a credit card with this information
ANAL PIRATE
1234 take it dr.
WTFville,fl 33605
The credit card company would accept the charge because the 1234 and 33605 matched.
Hi Everyone.
I downloaded the bit torrent to search for my husband – however he’s not there thank god. But now I’m very worried that I can get in trouble for downloading the bit torrent. I only looked and then immediately deleted from my computer. Please help. This is all very upsetting.
wouldn’t worry about it, unless it had credit card #’s or social’s.
Martha, I wouldn’t worry about a thing. I jumped on downloading the torrent within half an hour of its release last night and there were close to 20k people downloading it. I just grabbed the magnetlink for the file from piratebay and check it out again and there were almost 40k combined seeders and people grabbing the file. It hasn’t even been 24 hours yet and I’d guess that easily over 100k people have downloaded this, if not more. The only one that is going to get in trouble for this is the person or people that released it (if at all). Relax. You’ll be fine.
Trying getting divorced before sleeping around. Marriage is sacred. Being a whore isn’t.
Thanks for the link to check for emails in the leak. Now I know what my dad was up to.
If you searched for your dad’s email address, you clearly already assumed he was up to no good.
Just another perspective on this situation. I wont say I’m the majority, but I visited this site as a married man after hearing a radio talk show discuss it in detail. It was when the site first came out and I was curious after hearing an hour long discussion about it. I used my normal email address that is actually my name @ gmail.I didn’t fill out a profile, upload a photo, or put in what I was looking for. I wasn’t concerned about my wife finding out because i wasn’t doing anything wrong. I’m the guy that watches a movie then researches everything about that movie. Shooting locations, trivia, etc. I’m always crazy curious. Anyway, I own a business and now my name pops up and I’m sure people will judge. Just figured I’d throw in my two cents.. I’ll tell my wife about it when I see her. She wont care because we trust each other. But anyone who finds my name wont mention it to me and get an explanation so they’ll jump to their own conclusions which unfortunately aren’t usually educated ones.
Exactly. Context matters just as much if not more.
I hope you’re right about your wife. I think most spouses would not be so understanding. That you visited such a site at all demonstrates your interest in the subject matter. The first visit out of curiosity is just the gateway for actually using that site on a subsequent visit.
You say that you weren’t doing anything wrong. That’s what my friend said too when he got caught in a sting involving underage girls. He honestly believes that just because he never had the opportunity to have sex with the girl, means he is somehow innocent.
Interest in the subject matter does not mean intent on doing it. Some people like background information or are curious as to “why” someone would do something. If BK had an account on ALM, would you assume he was interested in an affair? Or would you understand that as an investigative reporter and avid security guru, he was investigating the site?
You know, that’s exactly the reasoning that my friend (the one caught up in that sting) used when the police put him under arrest.
The excuse is so common as to be cliche. You would not believe the number of people who justify their sexual choices with the old “investigative journalist” or “avid security guru” rationalization. When one probes further, it usually turns out that the overwhelming majority of these folks haven’t written an investigative piece in their entire life, nor understand much more about security than the average Joe.
My friend has been in denial for so long that it’s now past the point of rationalization. He has told himself the “investigative reporter” story for so long that he actually has come to believe it. Everyone who knows him just rolls their eyes.
Curious people interested in background information have abundant means to satisfy their curiosity for why people do what they do. By comparison, the AM site would be a poor resource and probably not very satisfying if understanding motives is truly all one seeks.
Why not just admit that visiting the AM site is a delicious naughty diversion. I don’t mind (although your wife might). In fact, I would actually respect someone more who just owned their sh-t.
In the same boat, my wife laughed when I told her.
Soon American Divorce Attorneys will be so rich they can build a real Death Star!
Is Bhatia currently an employee (not a contractor) of Ashely Madison when he makes these statements?
I find the reference to using a transaction ID for credit card data to ring hollow. When was this system change implemented? 29 days ago so you can honestly say we don’t have CC numbers in our database? Since the company is claimed to not be deleting account data when they say that they are, why is anything they say now to be trusted? Great stuff Brian, keep it up.
For a trustworthy source to determine if your email address is in the data, you can use Troy Hunt’s “Have I Been Pwned” at https://haveibeenpwned.com. I know at least some of the data has been loaded there, because I got a hit on one address from my organization being included in the AM dump.
Because of the sensitivity of this particular breach, haveibeenpwned requires that you be registered with the site using the email address or email domain you’re wanting to look up. So if you were signed up on AM using an email account you no longer own, you won’t be able to check on it. Nor will people be able to check for other peoples’ email addresses willy-nilly. More info about that here:
http://www.troyhunt.com/2015/07/heres-how-im-going-to-handle-ashley.html
The dump is a fake. Even if it were real most people are not going to use their real name or email address in their profile.
Am I wrong in thinking that any site that is making the aggregate data available for search essentially making itself complicit in the hack?
Well, I think the email checker at https://ashleymadisonleakeddata.com/
is very valid. I was a member on Ashley Madison and at one time or another had 4 different usernames and/or emails and I checked all of the emails I used and they all came up as a valid ashley accounts. I also checked emails that I know I didn’t use and they came up as safe. I also checked some user emails that I was corresponding with and they came up in the leak. So from a regular user, I think this is very legitimate.
I’m guessing you weren’t dumb enough to use your real name and email address. Just like most people on that site. So, I guess how valuable is any of the information to anyone if everyone on the site is using fake names and phony email addresses?
Would creating a large number of fake data dumps be a way to cause confusion over what data was actually leaked?
This sort of technique has be used to bury research that was deemed unfavorable for years. It wouldn’t be a surprise to find out that AM has brought in a professional damage control team and that they are seeding the fake dumps.
Even if Bhatia is not an employee does he own any stock or options? This would be typically be part of a CTOs compensation.
That’s what I was thinking too. If Bhatia has cash in the game, I would not believe a word he said about the leak, and what information they do or don’t retain. It’s in his best interests to emphasize the security measures taken by the company, whether they are true or not, and to paint the leak issue as one big fake. Even if it does turn out to be fake, I want to hear it from someone other than Bhatia.
I think this is legit. There are admin login credentials and internal documents.
https://www.trustedsec.com/august-2015/ashley-madison-database-dumped/
“This is much more problematic as its not just a database dump, this is a full scale compromise of the entire company’s infrastructure including Windows domain and more.”