AshleyMadison.com, a site that helps married people cheat and whose slogan is “Life is Short, have an Affair,” recently put up a half million (Canadian) dollar bounty for information leading to the arrest and prosecution of the Impact Team — the name chosen by the hacker(s) who recently leaked data on more than 30 million Ashley Madison users. Here is the first of likely several posts examining individuals who appear to be closely connected to this attack.
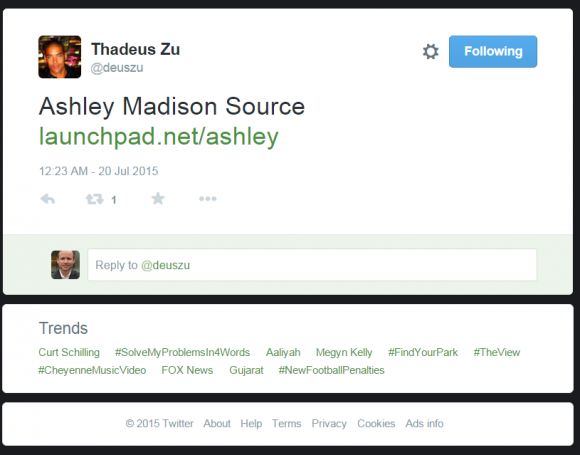 It was just past midnight on July 20, a few hours after I’d published an exclusive story about hackers breaking into AshleyMadison.com. I was getting ready to turn in for the evening when I spotted a re-tweet from a Twitter user named Thadeus Zu (@deuszu) who’d just posted a link to the same cache of data that had been confidentially shared with me by the Impact Team via the contact form on my site just hours earlier: It was a link to the proprietary source code for Ashley Madison’s service.
It was just past midnight on July 20, a few hours after I’d published an exclusive story about hackers breaking into AshleyMadison.com. I was getting ready to turn in for the evening when I spotted a re-tweet from a Twitter user named Thadeus Zu (@deuszu) who’d just posted a link to the same cache of data that had been confidentially shared with me by the Impact Team via the contact form on my site just hours earlier: It was a link to the proprietary source code for Ashley Madison’s service.
Initially, that tweet startled me because I couldn’t find any other sites online that were actually linking to that source code cache. I began looking through his past tweets and noticed some interesting messages, but soon enough other news events took precedence and I forgot about the tweet.
I revisited Zu’s tweet stream again this week after watching a press conference held by the Toronto Police (where Avid Life Media, the parent company of Ashley Madison, is based). The Toronto cops mostly recapped the timeline of known events in the hack, but they did add one new wrinkle: They said Avid Life employees first learned about the breach on July 12 (seven days before my initial story) when they came into work, turned on their computers and saw a threatening message from the Impact Team accompanied by the anthem “Thunderstruck” by Australian rock band AC/DC playing in the background.
After writing up a piece on the bounty offer, I went back and downloaded all five years’ worth of tweets from Thadeus Zu, a massively prolific Twitter user who typically tweets hundreds if not thousands of messages per month. Zu’s early years on Twitter are a catalog of simple hacks — commandeering unsecured routers, wireless cameras and printers — as well as many, many Web site defacements.
On the defacement front, Zu focused heavily on government Web sites in Asia, Europe and the United States, and in several cases even taunted his targets. On Aug. 4, 2012, he tweeted to KPN-CERT, a computer security incident response team in the Netherlands, to alert the group that he’d hacked their site. “Next time, it will be Thunderstruck. #ACDC” Zu wrote.
The day before, he’d compromised the Web site for the Australian Parliament, taunting lawmakers there with the tweet: “Parliament of Australia bit.ly/NPQdsP Oi! Oi! Oi!….T.N.T. Dynamite! Listen to ACDC here.”
I began to get very curious about whether there were any signs on or before July 19, 2015 that Zu was tweeting about ACDC in relation to the Ashley Madison hack. Sure enough: At 9:40 a.m., July 19, 2015 — nearly 12 hours before I would first be contacted by the Impact Team — we can see Zu is feverishly tweeting to several people about setting up “replication servers” to “get the show started.” Can you spot what’s interesting in the tabs on his browser in the screenshot he tweeted that morning?
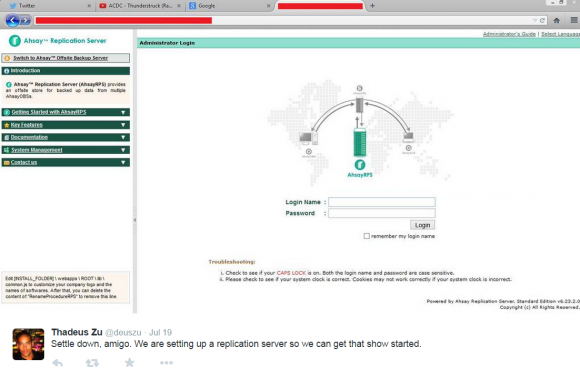
Twitter user ThadeusZu tweets about setting up replication servers. Did you spot the Youtube video he’s playing when he took this screenshot?
Ten points if you noticed the Youtube.com tab showing that he’s listening to AC/DC’s “Thunderstruck.”
A week ago, the news media pounced on the Ashley Madison story once again, roughly 24 hours after the hackers made good on their threat to release the Ashley Madison user database. I went back and examined Zu’s tweet stream around that time and found he beat Wired.com, ArsTechnica.com and every other news media outlet by more than 24 hours with the Aug. 17 tweet, “Times up,” which linked to the Impact Team’s now infamous post listing the sites where anyone could download the stolen Ashley Madison user database.
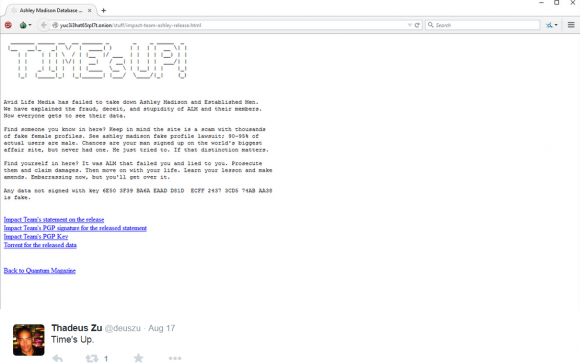
ThadeusZu tweeted about the downloadable Ashley Madison data more than 24 hours before news outlets picked up on the cache.
WHO IS THADEUS ZU?
As with the social networking profiles of others who’ve been tied to high-profile cybercrimes, Zu’s online utterings appear to be filled with kernels of truth surrounded by complete malarkey– thus making it challenging to separate fact from fiction. Hence, all of this could be just one big joke by Zu and his buddies. In any case, here are a few key observations about the who, what and where of Thadeus Zu based on information he’s provided (again, take that for what it’s worth).
Zu’s Facebook profile wants visitors to think he lives in Hawaii; indeed, the time zone set on several of his social media accounts is the same as Hawaii. There are a few third-party Facebook accounts of people demonstrably living in Hawaii who tag him in their personal photos of events on Hawaii (see this cached photo, for example), but for the most part Zu’s Facebook account consists of pictures taken from stock image collections and do not appear to be personal photos of any kind.
A few tweets from Zu — if truthful and not simply premeditated misdirection — indicate that he lived in Canada for at least a year, although it’s unclear when this visit occurred.
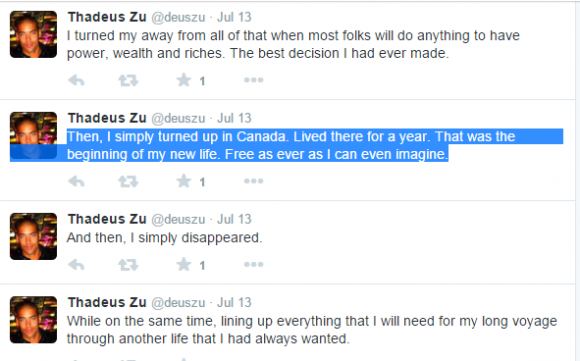 Zu’s various Twitter and Facebook pictures all feature hulking, athletic, and apparently black male models (e.g. he’s appropriated two profile photos of male model Rob Evans). But Zu’s real-life identity remains murky at best. The lone exception I found was an image that appears to be a genuine group photo taken of a Facebook user tagged as Thadeus Zu, along with an unnamed man posing in front of a tattoo store with popular Australian (and very inked) model/nightclub DJ Ruby Rose.
Zu’s various Twitter and Facebook pictures all feature hulking, athletic, and apparently black male models (e.g. he’s appropriated two profile photos of male model Rob Evans). But Zu’s real-life identity remains murky at best. The lone exception I found was an image that appears to be a genuine group photo taken of a Facebook user tagged as Thadeus Zu, along with an unnamed man posing in front of a tattoo store with popular Australian (and very inked) model/nightclub DJ Ruby Rose.
That photo is no longer listed in Rose’s Facebook profile, but a cached version of it is available here. Rose’s tour schedule indicates that she was in New York City when that photo was taken, or at least posted, on Feb. 6, 2014. Zu is tagged in another Ruby Rose Facebook post five days later on Valentine’s Day. Update, 2:56 p.m.: As several readers have pointed out, the two people beside Rose in that cached photo appear to be Franz Dremah and Kick Gurry, co-stars in the movie Edge of Tomorrow).
Other clues in his tweet stream and social media accounts put Zu in Australia. Zu has a Twitter account under the Twitter nick @ThadeusZu, which has a whopping 11 tweets, but seems rather to have been used as a news feed. In that account Zu is following some 35 Twitter accounts, and the majority of them are various Australian news organizations. That account also is following several Australian lawmakers that govern states in south Australia.
Then again, Twitter auto-suggests popular accounts for new users to follow, and usually does so in part based on the Internet address of the user. As such, @ThadeusZu may have only been using an Australian Web proxy or a Tor node in Australia when he set up that account (several of his self-published screen shots indicate that he regularly uses Tor to obfuscate his Internet address).
Even so, many of Zu’s tweets going back several years place him in Australia as well, although this may also be intentional misdirection. He continuously references his “Oz girl,” (“Oz” is another word for Australia) uses the greeting “cheers” quite a bit, and even talks about people visiting him in Oz.
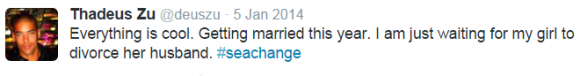
Interestingly, for someone apparently so caught up in exposing hypocrisy and so close to the Ashley Madison hack, Zu appears to have himself courted a married woman — at least according to his own tweets. On January 5, 2014, Zu tweeted:
“Everything is cool. Getting married this year. I am just waiting for my girl to divorce her husband. #seachange
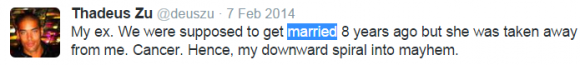
A month later, on Feb. 7, 2014, Zu offered this tidbit of info:
“My ex. We were supposed to get married 8 years ago but she was taken away from me. Cancer. Hence, my downward spiral into mayhem.”
To say that Zu tweets to others is a bit of a misstatement. I have never seen anyone tweet the way Zu does; He sends hundreds of tweets each day, and while most of them appear to be directed at nobody, it does seem that they are in response to (if not in “reply” to) tweets that others have sent him or made about his work. Consequently, his tweet stream appears to the casual observer to be nothing more than an endless soliloquy.
But there may something else going on here. It is possible that Zu’s approach to tweeting — that is, responding to or addressing other Twitter users without invoking the intended recipient’s Twitter handle — is something of a security precaution. After all, he had to know and even expect that security researchers would try to reconstruct his conversations after the fact. But this is far more difficult to do when the Twitter user in question never actually participates in threaded conversations. People who engage in this way of tweeting also do not readily reveal the Twitter identities of the people with whom they chat most.
Thadeus Zu — whoever and wherever he is in real life — may not have been directly involved in the Ashley Madison hack; he claims in several tweets that he was not part of the hack, but then in countless tweets he uses the royal “We” when discussing the actions and motivations of the Impact Team. I attempted to engage Zu in private conversations without success; he has yet to respond to my invitations.
It is possible that Zu is instead a white hat security researcher or confidential informant who has infiltrated the Impact Team and is merely riding on their coattails or acting as their mouthpiece. But one thing is clear: If Zu wasn’t involved in the hack, he almost certainly knows who was.
KrebsOnSecurity is grateful to several researchers, including Nick Weaver, for their assistance and time spent indexing, mining and making sense of tweets and social media accounts mentioned in this post. Others who helped have asked to remain anonymous. Weaver has published some additional thoughts on this post over at Medium.




Deuszu website — is anyone able to crack: http://chem-309.umd.edu/main/main.html?weblang=2
Thadeus Zu is a play on words.
Read it as “The Deus Zu”, or “The God Zu” and you unravel the clue one step further.
Did a very quick search using this as a reference and came up with this, one of a handful of potential expansions on this theme
http://nzetc.victoria.ac.nz/tm/scholarly/tei-Stout52-t9-body-d1-d6-d1.html
Sorry but this Thaddeus guy’s reaction screams guilty. Reading his posts he clearly knew a hell of a lot from the beginning and have to agree that if he’s not directly involved he knows who did it. It’s interesting to see how much he’s protesting his innocence one second then challenging people to come and find him the next. Well played Brian, well played.
Also check out Ruby Rose deleting anything to do with that name. FBI may be wanting to chat with her while she’s in the USA. If she knows them personally I reckon she’ll ditch them ASAP over her career.
While Thadeus is a real name (usually spelled as Thaddeus) since his twitter username is deuszu it might be that it means something like “The Deus”. Deus in latin means god so this guy describes himself as a god (that’s some ego!) As for Zu, it may also be an indication but I don’t know what.
There’s not a lot of new stuff here but well done Brian on pulling it all together in one place and adding a few new bits. It’s been clear from day one that Thadeus Zu wants people to think he knows a lot about this. The difficulty is finding out who he is – the work that Brian has done may lead one step closer and publishing may be another step but there are still a lot of steps to go. Then there’s the question of how involved he really is. It’s going to be interesting but don’t hold your breath.
Of course that’s right. There is nothing new. The information that Brian is analyzing was created in the past.
The deep analysis is new, though. At least I don’t recall anyone else doing the work that Brian and Nick did.
I noticed they appear to be using Ahsay Replication Server. I wonder if they purchased a license, or may have had some download activity and/or signed up for a trial.
The address line is blanked out but, from my limited understanding of the Ahsay solutions, they would either be on the cloud, or have their own infrastructure. If that’s the case, someone has to know something, and the database may have even been placed in one of those locations.
The guys was also actively hacking other sites https://www.google.com/search?q=deuszu%20was%20here&rct=j
Ashleymadison.sucks was registered in Cayman Islands dude claims he is Hungarian from Cayman Islands. Coincidence?
I found this guy also on YouTube. Check this out! James Ryan (a musician from Austriala!!!!) writes on YouTube “This song is dedicated to Wikileaks from @Deuszu” https://www.youtube.com/all_comments?v=pSJiBzwq8o8
One of the people behind that one account( there are 4 or 5 that operate it) is Polish and part German. I’m not sure what his connection with U of Maryland is, but ftp://ftp.umiacs.umd.edu/pub/cdunne/twitter/NodeXL-Collection-wikileaks_2012-10-24_11-00-00.xlsx
By reading his tweets that you have listed, I would suggest that he is an Australian. His idiom and word choice seem very Australian. There is probably some program that can analyse language to give a probability of country of origin.
Here is a screenshot of that YouTube video.
https://i.imgur.com/PgwvYll.png
From a basic interpretation of the information provided I’d be inclined to say that Thadeus Zu is not a person, but people. If you consider the spread of countries, stories, pictures of people, different activities, and such there is strong indication that there are multiple people posting.
This would also explain the number of indirect tweets, almost a comment board.
From a psychological perspective this also seems highly credible, there are seemingly incoherent and seemingly unlinked comments and statements made through the account, which can sometimes suggest that there is an individual who has internal conflicts, but is more likely to suggest that in fact there are a number of people with different opinions and voices all wanting to get their message out in an egotistical display.
This is the downfall of groups like this, they are happy to be viewed as a collective when it provides them with anonymity and stability, but in the end, they all want to be recognized as the true talent behind the organization.
This might be a description of Schizophrenia or multiple personality. How could someone even be able to tell the difference between this and multiple people using the same account?
As if any of this even matters much anyway……
That picture with the DJ Rosee is of two actors from the movie Edge of Tomorrow. The two actors names are Franz Drameh and Kick Curry so that is a false flag.
Have you considered that there is no “Thadeus Zu” and that it’s just a dummy account used by an intelligence agency? As someone else pointed out here “Thadeus” is quite clearly derived from “the deus” and as for Zu, check this out: “Zu was an ancient dragon or storm-bird found in many Mesopotamian myths.” Storm -> Thunder -> Thunderstruck…
Have been watching you guys going back and forth on twitter very funny stuff watching it unfold. I would say he is seriously worried at this point. Good work Brian very good work.
Looks like deuszu has now responded to the recent allegations i think.
https://twitter.com/deuszu/status/636825753795952641/photo/1
Krebs, can I play you in the movie? Please?
Very good work. I am sure AM staff has performed a detailed audit of their back up media. Dumps seem to indicate that the hacker(s) have a backup not just hacked data. I bet their are missing tapes or disk or other media. Hope they logged backups properly.
My cousin is a dba at Namecheap, the server provider for the site. I’m working on getting Ashley’s Brothers contact info. Will share if site remains up. I’m sure folks would be interested.
http://www.telegraph.co.uk/technology/internet-security/11827265/Is-this-the-Ashley-Madison-hacker.html
Considering the probable state of AM’s finances, and the lawsuits already filed, I think I would want to see that CAD 500K in an escrow account before I told them anything.
Looks Like Zu is having a tantrum. More misdirection, most likely. Not to be tinfoil-hatty about it, but I believe the term is “false-flag”?
Who the hell knows. What I find sad is the whole “clues point to Australian”. Of course they do. If he IS the hacker, sorry, if *I* were the hacker, it would probably take about 30 seconds of googling to get enough vernacular to point to a different geolocation.
If he IS the hacker, I’m going to say that there is very little that could be inferred from social media, unless he got ripped-high/drunk and did something mind bogglingly stupid.
Any evidence (if any) will be in meta data. This is at best gamesmanship, at worst a sympathizer keeping the heat off of the real target, intentionally or unintentionally.
I heard back from my cousin. After 8 PM there but he said he would poke around tonight and likely get it to me tomorrow his time/tonight our time. More to come.
Jesus, quoting ‘The Matrix’ just confirms you are a trench coat wearing, mom’s basement type of guy.
Perhaps take your noble, self-righteous crusade and aim at something a little less trivial and faintly ridiculous… you know, something like ISIS?
Thomas Anderson is Neo, and the founder of MySpace. B
Trying to figure out what Zu’s play is here. All of his tweets have had an element of the insane, the inane… but an underlying hint of intelligence or purpose. Now he keeps harping on “When the FBI come where is your evidence”, which is silly. Law Enforcement want leads. Then they’ll go after evidence.
So is he actually coming unhinged, or just playing at it. If I were a bertting person, my guess (but a very slight guess) is that he is not the hacker, but did not expect New York times/mass media articles, and is now worried about what heat this will bring down on previous hacks/website defacement.
But again, who knows?
I like your the way you think off-the-cuff, trousers.
Usually the weakest link is the person connected by a thread with a sense of dread and no planning abilities, afilliarities.
I feel bad for the kid. He’s trying to play with the idea of voices in his head, not realizing he’ll never be a Croesus cracker. MMORPGs are fun to play, but not so fun when the bedsprings are loaded and the proxies offloaded?
Levels.
It seems that many have come to the same conclusion as myself from the info Brian and others have discovered. I’m not a tech but do have investigative experience and its evident that Thad as a person or a group has carelessly provided many “tells” that have already narrowed a list of suspects (i.e.. Australian/NZ’s with tech aptitude to pull this off who have traveled to Toronto) down to its ultimate conclusion…a apprehension. Not sure this happens today, next week or next month but the more they blather and dump the more crumbs they leave behind and the shorter the trail gets. Good work Brian and all that are contributing on this thread.
Ted, please thank your cousin for all of us. Getting the identity and address of “Ashley’s Brother” will be put to good use.
It’s been pointed out that the launchpad link was also posted publicly to the “full disclosure” mailing list on 2015-08-19:
http://seclists.org/fulldisclosure/2015/Jul/100
This appears to weaken the argument linking @deuszu to the hackers substantially (lots of people listen to AC/DC).
Would brian krebs like to comment on this?
No it doesn’t. That report used the name of Brian Offenheimer,who was a vp at ALM, since departed. Assuming it’s fake, it proves nothing.
Everybody knows somebody. I think somebody who knows zu (Thomas Anderson/ITt0m?) will have slipped up and led LE to the hacker(s).
HA!
John McAfee says a potential insider – a Female – stole the database……
http://www.ibtimes.co.uk/john-mcafee-ashley-madison-database-stolen-by-lone-female-who-worked-avid-life-media-1516833