AshleyMadison.com, a site that helps married people cheat and whose slogan is “Life is Short, have an Affair,” recently put up a half million (Canadian) dollar bounty for information leading to the arrest and prosecution of the Impact Team — the name chosen by the hacker(s) who recently leaked data on more than 30 million Ashley Madison users. Here is the first of likely several posts examining individuals who appear to be closely connected to this attack.
 It was just past midnight on July 20, a few hours after I’d published an exclusive story about hackers breaking into AshleyMadison.com. I was getting ready to turn in for the evening when I spotted a re-tweet from a Twitter user named Thadeus Zu (@deuszu) who’d just posted a link to the same cache of data that had been confidentially shared with me by the Impact Team via the contact form on my site just hours earlier: It was a link to the proprietary source code for Ashley Madison’s service.
It was just past midnight on July 20, a few hours after I’d published an exclusive story about hackers breaking into AshleyMadison.com. I was getting ready to turn in for the evening when I spotted a re-tweet from a Twitter user named Thadeus Zu (@deuszu) who’d just posted a link to the same cache of data that had been confidentially shared with me by the Impact Team via the contact form on my site just hours earlier: It was a link to the proprietary source code for Ashley Madison’s service.
Initially, that tweet startled me because I couldn’t find any other sites online that were actually linking to that source code cache. I began looking through his past tweets and noticed some interesting messages, but soon enough other news events took precedence and I forgot about the tweet.
I revisited Zu’s tweet stream again this week after watching a press conference held by the Toronto Police (where Avid Life Media, the parent company of Ashley Madison, is based). The Toronto cops mostly recapped the timeline of known events in the hack, but they did add one new wrinkle: They said Avid Life employees first learned about the breach on July 12 (seven days before my initial story) when they came into work, turned on their computers and saw a threatening message from the Impact Team accompanied by the anthem “Thunderstruck” by Australian rock band AC/DC playing in the background.
After writing up a piece on the bounty offer, I went back and downloaded all five years’ worth of tweets from Thadeus Zu, a massively prolific Twitter user who typically tweets hundreds if not thousands of messages per month. Zu’s early years on Twitter are a catalog of simple hacks — commandeering unsecured routers, wireless cameras and printers — as well as many, many Web site defacements.
On the defacement front, Zu focused heavily on government Web sites in Asia, Europe and the United States, and in several cases even taunted his targets. On Aug. 4, 2012, he tweeted to KPN-CERT, a computer security incident response team in the Netherlands, to alert the group that he’d hacked their site. “Next time, it will be Thunderstruck. #ACDC” Zu wrote.
The day before, he’d compromised the Web site for the Australian Parliament, taunting lawmakers there with the tweet: “Parliament of Australia bit.ly/NPQdsP Oi! Oi! Oi!….T.N.T. Dynamite! Listen to ACDC here.”
I began to get very curious about whether there were any signs on or before July 19, 2015 that Zu was tweeting about ACDC in relation to the Ashley Madison hack. Sure enough: At 9:40 a.m., July 19, 2015 — nearly 12 hours before I would first be contacted by the Impact Team — we can see Zu is feverishly tweeting to several people about setting up “replication servers” to “get the show started.” Can you spot what’s interesting in the tabs on his browser in the screenshot he tweeted that morning?
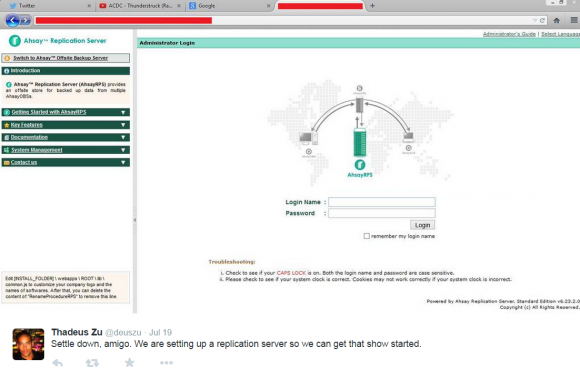
Twitter user ThadeusZu tweets about setting up replication servers. Did you spot the Youtube video he’s playing when he took this screenshot?
Ten points if you noticed the Youtube.com tab showing that he’s listening to AC/DC’s “Thunderstruck.”
A week ago, the news media pounced on the Ashley Madison story once again, roughly 24 hours after the hackers made good on their threat to release the Ashley Madison user database. I went back and examined Zu’s tweet stream around that time and found he beat Wired.com, ArsTechnica.com and every other news media outlet by more than 24 hours with the Aug. 17 tweet, “Times up,” which linked to the Impact Team’s now infamous post listing the sites where anyone could download the stolen Ashley Madison user database.
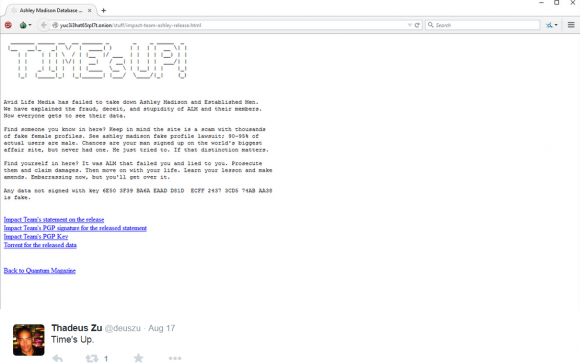
ThadeusZu tweeted about the downloadable Ashley Madison data more than 24 hours before news outlets picked up on the cache.
WHO IS THADEUS ZU?
As with the social networking profiles of others who’ve been tied to high-profile cybercrimes, Zu’s online utterings appear to be filled with kernels of truth surrounded by complete malarkey– thus making it challenging to separate fact from fiction. Hence, all of this could be just one big joke by Zu and his buddies. In any case, here are a few key observations about the who, what and where of Thadeus Zu based on information he’s provided (again, take that for what it’s worth).
Zu’s Facebook profile wants visitors to think he lives in Hawaii; indeed, the time zone set on several of his social media accounts is the same as Hawaii. There are a few third-party Facebook accounts of people demonstrably living in Hawaii who tag him in their personal photos of events on Hawaii (see this cached photo, for example), but for the most part Zu’s Facebook account consists of pictures taken from stock image collections and do not appear to be personal photos of any kind.
A few tweets from Zu — if truthful and not simply premeditated misdirection — indicate that he lived in Canada for at least a year, although it’s unclear when this visit occurred.
 Zu’s various Twitter and Facebook pictures all feature hulking, athletic, and apparently black male models (e.g. he’s appropriated two profile photos of male model Rob Evans). But Zu’s real-life identity remains murky at best. The lone exception I found was an image that appears to be a genuine group photo taken of a Facebook user tagged as Thadeus Zu, along with an unnamed man posing in front of a tattoo store with popular Australian (and very inked) model/nightclub DJ Ruby Rose.
Zu’s various Twitter and Facebook pictures all feature hulking, athletic, and apparently black male models (e.g. he’s appropriated two profile photos of male model Rob Evans). But Zu’s real-life identity remains murky at best. The lone exception I found was an image that appears to be a genuine group photo taken of a Facebook user tagged as Thadeus Zu, along with an unnamed man posing in front of a tattoo store with popular Australian (and very inked) model/nightclub DJ Ruby Rose.
That photo is no longer listed in Rose’s Facebook profile, but a cached version of it is available here. Rose’s tour schedule indicates that she was in New York City when that photo was taken, or at least posted, on Feb. 6, 2014. Zu is tagged in another Ruby Rose Facebook post five days later on Valentine’s Day. Update, 2:56 p.m.: As several readers have pointed out, the two people beside Rose in that cached photo appear to be Franz Dremah and Kick Gurry, co-stars in the movie Edge of Tomorrow).
Other clues in his tweet stream and social media accounts put Zu in Australia. Zu has a Twitter account under the Twitter nick @ThadeusZu, which has a whopping 11 tweets, but seems rather to have been used as a news feed. In that account Zu is following some 35 Twitter accounts, and the majority of them are various Australian news organizations. That account also is following several Australian lawmakers that govern states in south Australia.
Then again, Twitter auto-suggests popular accounts for new users to follow, and usually does so in part based on the Internet address of the user. As such, @ThadeusZu may have only been using an Australian Web proxy or a Tor node in Australia when he set up that account (several of his self-published screen shots indicate that he regularly uses Tor to obfuscate his Internet address).
Even so, many of Zu’s tweets going back several years place him in Australia as well, although this may also be intentional misdirection. He continuously references his “Oz girl,” (“Oz” is another word for Australia) uses the greeting “cheers” quite a bit, and even talks about people visiting him in Oz.
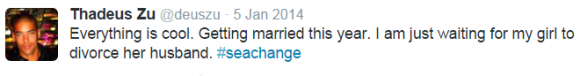
Interestingly, for someone apparently so caught up in exposing hypocrisy and so close to the Ashley Madison hack, Zu appears to have himself courted a married woman — at least according to his own tweets. On January 5, 2014, Zu tweeted:
“Everything is cool. Getting married this year. I am just waiting for my girl to divorce her husband. #seachange
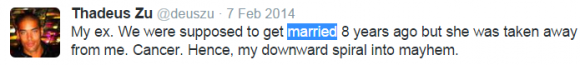
A month later, on Feb. 7, 2014, Zu offered this tidbit of info:
“My ex. We were supposed to get married 8 years ago but she was taken away from me. Cancer. Hence, my downward spiral into mayhem.”
To say that Zu tweets to others is a bit of a misstatement. I have never seen anyone tweet the way Zu does; He sends hundreds of tweets each day, and while most of them appear to be directed at nobody, it does seem that they are in response to (if not in “reply” to) tweets that others have sent him or made about his work. Consequently, his tweet stream appears to the casual observer to be nothing more than an endless soliloquy.
But there may something else going on here. It is possible that Zu’s approach to tweeting — that is, responding to or addressing other Twitter users without invoking the intended recipient’s Twitter handle — is something of a security precaution. After all, he had to know and even expect that security researchers would try to reconstruct his conversations after the fact. But this is far more difficult to do when the Twitter user in question never actually participates in threaded conversations. People who engage in this way of tweeting also do not readily reveal the Twitter identities of the people with whom they chat most.
Thadeus Zu — whoever and wherever he is in real life — may not have been directly involved in the Ashley Madison hack; he claims in several tweets that he was not part of the hack, but then in countless tweets he uses the royal “We” when discussing the actions and motivations of the Impact Team. I attempted to engage Zu in private conversations without success; he has yet to respond to my invitations.
It is possible that Zu is instead a white hat security researcher or confidential informant who has infiltrated the Impact Team and is merely riding on their coattails or acting as their mouthpiece. But one thing is clear: If Zu wasn’t involved in the hack, he almost certainly knows who was.
KrebsOnSecurity is grateful to several researchers, including Nick Weaver, for their assistance and time spent indexing, mining and making sense of tweets and social media accounts mentioned in this post. Others who helped have asked to remain anonymous. Weaver has published some additional thoughts on this post over at Medium.




could be wrong but isn’t the expression “pissed off” more of an Australian or British usage than American? From the Impact Team’s statement….
“And it was easy. For a company whose main promise is secrecy, it’s like you didn’t even try, like you thought you had never pissed anyone off”
Nope, “Pissed off” is pretty universal for the English language, doesn’t really matter what side of the pond you’re on.
Actually, ‘pissed off’ is more American or Canadian than anything else, but this is the interwebs. Attribution is hard.
To get pissed in most other English-speaking countries means to get drunk. Not to get angry.
Cheerios!
Oi! Oi! Oi! (see the Aus Parliament hack above) is a very Australian thing to say, however. Particularly in that context
and probably not something that many Non-Australians would be familiar with.
I thought he might be Aussie after reading that part, even before I got to the last bit of the article.
If this were the 90s or early 2000s I’d absolutely agree, but the internet, and the subcultures that tend to attract certain people, provide multiple clues and cues as to how to misrepresent oneself. Which is to say, you can’t trust idioms, especially when idioms become memes (or just common in certain groups of people).
Linguistically speaking, that Twitter is unlikely to belong to whomever wrote those release texts, but I say that not because they’re so dissimilar. For a broader picture, you may want to zoom out and look at the entirety of a few years of said individuals tweets (or even a subsection of them). One might also want to look at the franticness and compare it to the way the releaser talks.
This is someone who greatly admires the person who did it… But it’s not someone who did it. Brian Krebs, as usual, is shooting wild bullets at people looking for patterns and hoping some will hit the Target.
All of this is JMHO, and doesn’t mean much, because most attribution is total crap anyway.
But no attribution lacking ACTUAL data should ever be published. May as well go around saying ‘Is Brian Krebs sniffing POS transactions?’ — after all, he seems to have the dibs on the deets before most people on who got breached.
I mean, clearly this kid is mucking around with routers and stuff, but he looks more Lizardly than organised.
Case in point, how long would it take someone to google ‘She’ll be apples’ or ‘arvo’ (which I don’t think I saw once, somewhat unusual for someone trying to point at a local pub in Sydney)? Or whatever. The Acca/Dacca stuff is pretty blatantly trying to be Aussie too. But I don’t find it intriguingly blatant. To me it just looks like Brian Krebs got trolled hard.
Oi Oi Oi is also in the lyrics to TNT, the song mentioned in the tweet.
No idea. Don’t really know much AC/DC. I just figured they were copying that stuff from the Stuxnet/Natanz stuff — nothing I’ve seen in the twitter archive seems to suggest any actual creativity — everything actually is quite derivative from the last 20 years or so of pop culture, right down to the Dark Angel plotlines and secret government conspiracy theories. Shallow rabbit hole. Surprised people are finding it so interesting. No offense intended at whomever is actually tweeting the stuff. It sounds like he needs some friends and a good ear/shoulder.
http://www.msn.com/en-us/news/itinsider/security-expert-claims-to-have-found-ashley-madison-hacker/ar-BBm9Zxc?li=AA54ur
This article is claiming you’ve found culprit for sure, with no links back to your website or article. Shameless.
Yes, classy. Unfortunately, happens all the time.
I mentioned this before McAfee thanks to your website:
“John McAfee says a potential insider – a Female – stole the database……
http://www.ibtimes.co.uk/john-mcafee-ashley-madison-database-stolen-by-lone-female-who-worked-avid-life-media-1516833”
What about if this was the case…
In the part that reads “Zu is tagged in another Ruby Rose Facebook post five days later on Valentine’s Day. ”
Who would be with Rose on Valentines day? According to a google search, Ruby Rose is dating or engaged to “Phoebe Dahl” who is a woman. Could Thadeus Zu be a woman?” Could the person in the photo tagged as Thadeus Zu be Phoebe Dahl on Valentines day with Ruby Rose? Both are linked to Australia. Now time to do some Due Diligence on Phoebe Dahl.
Some Interesting coincidences. (not suggesting that these people are involved in the hack. Relating events only in relation to identity of Zu):
1) Thaddeus tweets getting married this year (2014) Ruby Rose and Phoebe announced their marriage in March 2014 – wikipedia
2) Tweet from last night:
————————————————-
@deuszu says this in the middle of each episode
Hussy, redneck, bro and hombre are a lovable crew. Tune in next week!
@deuszu Brian Krebs chases them around and his henchman gets “Zu’s Fu.” Then Zu crew drinks champagne as the private jet flies to sunset
————————————————–
Check this article – private jet july 24, 2015 (Their first time – source Ruby Rose tweet)… 5 people in the picture. Is this Thaddeus, hussy, redneck, bro, and hombre? an interesting coincidence, nothing more.
http://www.dailymail.co.uk/tvshowbiz/article-3172841/Ruby-Rose-boards-private-jet-fiancee-Phoebe-Dahl-finding-gunman-loose-backyard.html
Why would a random gunman shoot Ruby and Phoebe’s backyard? The date is July 23rd, 3 days after hack announcement. No motive for gunman’s attack, anyone ever find out?
Fly to Vegas the day after? Not my first choice of things to do after a traumatic event… too celebratory.
http://www.youredm.com/2015/07/23/random-gunman-found-in-ruby-roses-backyard/
Look who’s in the private jet. This crew could pull interesting things off. Shahidi CEO of Shots, also “king of twitter”. Thaddeus Zu likes to post on twitter alot.
This is all conjecture and coincidence.
The only other thing that could throw this theory off is the fact they may have hacked these celeb facebooks and tagged that profile. Otherwise these females need to be looked at…this seems like something a bitter man hating female would release. I think there files were stolen directly from the servers, there is no hack here. This person had physical access to the servers to download all of this source code. IMO of course.
Another coincidence, Interview August 15, 2015 – 3 days before the release. Both women sound very nice and support great causes.
“I know our lives will change a little bit but we’re both very modest and humble so I don’t think it’ll affect us too much,” she told our sister publication in the UK, HELLO! Fashion Monthly. “If anything, we’ll be able to use the spotlight to shed light on greater world issues. I know Ruby will use it to touch on LGBT issues and hopefully I’ll be able to promote my causes, which are sex trafficking, girls’ education and women’s empowerment.”
http://us.hellomagazine.com/celebrities/1201508137109/ruby-rose-fiancee-phoebe-dahl-on-wedding-interview/
The photo in Hmmmm’s post is 99% Ruby. The tatoos are the same as is the body type.
http://www.dailymail.co.uk/tvshowbiz/article-3184052/Orange-New-Black-star-Ruby-Rose-says-apology-Australian-Prime-Minister-Tony-Abbott-taken-context.html
Actually — you may have something very interesting here — or these are crazy hacks … This is definitely a picture of Ruby Rose on @DarkLeary’s (@DeusZu’s girlfriend ?) twitter feed:
https://twitter.com/DarkLeary/status/442610467945447425
someone has to look into this more deeply
thats how stupid people are. you go through all this to cover your tracks then you blab on social media with a stupid moniker showing off your hacks. how stupid. not a hacker at all IMO, a data thief maybe, but the impact team is operating like an old school AOL warez group… it seems with their text macros and style.
This Thaddeus guy has a specific way of writing. He leaves spaces before and after he quotes something. Specifically, things like ‘ leetness ‘ ‘ leet ‘ ‘ inspect element ‘ etc. It’s a fingerprint that very few use. If there could be a search done on Twitter to find instances of that kind of typing, it may lead to a real life account.
Again .. HOW did @deuszu get the entire Noel Biederman email file ?? No one without inside connections to the hack could have it since it’s NOT public…. the one in the partial torrent does not go back this far…..
https://twitter.com/deuszu/status/635485221027053569
The partial torrent does too go back that far. That’s where it starts.
Conspiracy theory: It’s a Stratfor-level rope-a-dope? Twitterer wouldn’t even have to know it to fall for it.
We haven’t really heard what, if any part, of Lizard Squad shook out from that stuff that Mr. Krebs was investigating around Christmastime, assuming law enforcement caught some of those guys when they took down that forum last month (as reported here in mid-July), or when the one Lizard dude got a ridiculously light sentence in Europe earlier this year (no idea when that was; I mostly read Mr. Krebs for his reporting on client-side patches…).
So does this mean you get the money, Brian?
3 questions for Brian:
1) Is it fair to say that you have been in touch with the CEO and ex-CFO of AM from the initial threat to release?
2) Are you now or have you ever been retained by AM to search out the hackers of AM.
3) Have you previously considered or will you consider the possibility that an AM insider(the ex-CFO who hacked nerve.com) was involved in this hacking of AM. My apologires if I am treading on old turf here…I haven’t followed that closely.
1) no
2) no
3) Insider? I believe that was mentioned by the CEO as a strong possibility in the first story about this. but the former CTO? Seems unlikely.
BK what do you make of all this? You stand this zany theory up my man and you will become immortal…
From an earlier commenter…
Some Interesting coincidences. (not suggesting that these people are involved in the hack. Relating events only in relation to identity of Zu):
1) Thaddeus tweets getting married this year (2014) Ruby Rose and Phoebe announced their marriage in March 2014 – wikipedia
2) Tweet from last night:
————————————————-
@deuszu says this in the middle of each episode
Hussy, redneck, bro and hombre are a lovable crew. Tune in next week!
@deuszu Brian Krebs chases them around and his henchman gets “Zu’s Fu.” Then Zu crew drinks champagne as the private jet flies to sunset
————————————————–
Check this article – private jet july 24, 2015 (Their first time – source Ruby Rose tweet)… 5 people in the picture. Is this Thaddeus, hussy, redneck, bro, and hombre? an interesting coincidence, nothing more.
http://www.dailymail.co.uk/tvshowbiz/article-3172841/Ruby-Rose-boards-private-jet-fiancee-Phoebe-Dahl-finding-gunman-loose-backyard.html
Why would a random gunman shoot Ruby and Phoebe’s backyard? The date is July 23rd, 3 days after hack announcement. No motive for gunman’s attack, anyone ever find out?
Fly to Vegas the day after? Not my first choice of things to do after a traumatic event… too celebratory.
http://www.youredm.com/2015/07/23/random-gunman-found-in-ruby-roses-backyard/
Look who’s in the private jet. This crew could pull interesting things off. Shahidi CEO of Shots, also “king of twitter”. Thaddeus Zu likes to post on twitter alot.
This is all conjecture and coincidence.
I think @deuszu owes Jeremy Buendia an apology for his ‘selfies’ … and this guy is calling other people frauds???:
https://twitter.com/deuszu/status/629362481522180096
https://instagram.com/p/oC72RlMi5m/
https://twitter.com/deuszu/status/624900631887638528
https://instagram.com/p/1RKRe7Mi4z/
Not sure if this came up already, but it strikes me this person is a kiwi rather than from oz. Certain slang and idiom in tweets (e.g. chur).
I know it has been suggested that it’s multiple people using the DeusZu account…I have noticed many times that tweets begin with the terms: Amigo, Hombre, & Ninja – is it possible that these are “code names” referencing who the account is speaking to? Or identifiers of who is tweeting from the account?
…just a thought.
Yep, I think that’s exactly what’s going on with the @deuszu account. they’re using it like an IRC channel.
In fact, a tweet from the @Deuszu account on July 14, 2015 seems to confirm this:
https://twitter.com/deuszu/status/621111757705089024
“There are five of us that run this account. Me [ the blackhat ], Kovacs [ the soldier ], Doc [ hacker/entrepreneur ], Chief [ ex spec op ]..”
I have found the second member of the five members of Team Impact. Full description and modus operandi.
Soon
In one of his Twitter accounts @ThadeusZu he deleted his description and general info. Here is what it said (can still be seen in source file):
Location: Cyber Realm
URL: https://www.nsa.gov
Description: Great Satire Creator and Instigator, Pursued by Authorities, On Most Wanted List, Extraordinary Hacker of Sandwiches, Cyber General
Created at: Tue Feb 10 23:45:31 +0000 2015
Time zone: Hong Kong
Also, he deleted accounts he followed (their account images are still in the ‘Inspect element’ image files :
– Toronto Raptors
– CBC News
– TTC (Toronto Transit Commission)
The only reason one would follow the TTC is if you used it. Suggests he was in Toronto in February 2015
You mentioned that one of the elements from the ‘Thadeus Zu’ tweets was that they began utilizing IP addresses from Canada.
Could this be when one of the ‘team’ went to Canada to work within AM? Could this have been how they infiltrated from the inside, then retreating back out at a safe distance, before they wreaked havoc for whatever the ’cause’ was?
I also saw some interesting data [from Annalee Newitz] that filtered through the female database and analyzed the data. It looks like there were only a very small percentage of live female members participating on the site.
If a member fell in love with another member, via cyber relationship and not IRL, and the expression of them leaving their husband for this new mate, and then it coming to light that they were a ‘robot’ or fake profile that just lead the man on to spend more money on the site, you could have a ‘jilted lover’ so to speak….and a motive to destroy.
But my thoughts, as a woman, are that the LGBT activist angle is the one that may very well play out. Whomever this was [collectively the team], they hate men. May have been scorned in their life once by a man [and my guess it was a married man to a young woman, who left her bitter and thus she has sworn off men and is now a lesbian who has an axe to grind with men who cheat.]
I think the Ruby Rose and Phoebe Dahl connection is interesting. [Roald Dahl is actually one of my most favorite writers] Can you imagine the story he could weave out of this tangled web?
I doubt there’s a single female among em. What’s more, I doubt that that’s even close to a correct theory at all and the LBGT thing is bizarre.
If it was men that were being cheated out of money and being set up with people that don’t exist, and it is men that typically hack (and certainly it’s more often men that typically sport hack without specific targets), and it is women who have a difficult time being unemotional (sorry, calls em like I sees em; I’m not sexist, but I’ll admit to finding females more often than not frustratingly emotional), why would you assume this is a woman? Because whomever it is claims they did this (note, claims) for an ethical reason having to do with ‘cheating’? I’m not saying that whomever did this didn’t do it for that reason (they may well have, but that’s not the impression I get at all)… I’m saying that it’s actually quite sexist to assume that IF that was their reason, then it was automatically a woman.
Attribution is difficult — not only because whomever investigates this stuff probably has to figure out where the people are coming from and try to get whatever evidence they can, but because they also have to link it to people in more than a circumstantial manner, and then beyond that they have to THEN try to prove a ‘why’? Why would you believe the ‘why’ out of all of the parts of this, the most? Why would you CARE about the why, to begin with?
People keep making this about emotions, but it’s just as likely to be a competitor hacking them (recall, from what I’ve heard they were hacking their competitors), someone with a personal grudge against one of the employees that had nothing to do with what was ‘for sale’ and everything to do with the people involved, or any of a number of other possibilities.
And frankly, in forensics, the why shouldn’t matter — at least not until you get to the trial stage — and when you get to THAT, it shouldn’t even matter much. The law is *supposed* to be reason divorced from prejudice, at least in theory. After the sentencing guidelines shake out, THEN some discretion might be called for to consider ‘whys’ but honestly, regardless of who was hurt, one should probably realize that (a) it almost certainly wasn’t about them, (b) all of their computing devices know as much or more than AM probably ever did and considering how many people are probably in some botnet or other at this point, you may well have already been ‘exposed’, and (c) you created this to be exposed, yourself.
If this were a third-party record-holder for someplace like Planned Parenthood or whatever I’d be considerably more indignant because the choice would have been removed from the equation. But do you not understand how data gets shared, in the first place? Or that, in all likelihood, all of these dating sites are probably hacked and traded away for less than what the reward is that’s on these peoples’ heads?
I understand the urge to be upset. I understand it feels like a violation. But have you read the ToS for the places you sign up for?
You’re relying on discretion, and breaches of discretion go back long long before the Mayflower.
Best wishes.
I agree, that this type of activity is not usually female-centric.
I was just weaving the silk-threads of the thoughts of ‘Thadeus Zu’ being a moniker of more than one person and the tie-in of past tweets and tags with Ruby Rose. [it could be all delusional with her being tagged and/or linked in past tweets, just as John Hinckley was obsessed with Jodie Foster] – but the thought plays well for a great novel.
Someone mentioned the locations of tweets, and the thought that they were on a seafaring vessel. I think that it may be airborne craft [and then the tags to Ruby Rose on a jet] and the use of a Satcom by some of the ‘team’
As a woman, my thoughts drift always to an emotional reason why someone would commit such a crime. [if indeed, the reason for the hack was to expose cheating spouses], or the revenge of a member who realizes they have been duped by AM for fraudulently allowing them to think they were paying for real exchanges between another member, when if fact, the data shows that most likely that was not the case.
Activists, if that is the underlying reason for the hack, would have an element of emotion.
This would perfectly fit Ruby Rose and Phoebe Dahl. They were living in Canada, plus Ruby goes on tour and some other member s could be in Australia and other places mentioned. Coincidentally the main person fits perfectly to Dahl’s real life, like getting married, talking about moving to Canada and it’s freedom, and saying that they more active and have other primary jobs. Plus Ruby Rose just happened to buy a new house in LA since her acting career is really taking off (so much so that no talent Ruby Rose can ride her popularity into dj’ing). Thadeus/Dahl also mentioned a big move and change. They kept talking about disappearing like it was a joke so it seems obvious now that they were “disappearing” into Hollywood life and be famous while hiding since nobody would suspect anything. It is the year of the woman and Rose and Dahl were just hanging out with girl power promoter Taylor Swift yesterday. They also knew that so few women were on there to begin with and they still released it. Why not try to take Tinder down instead where all the actual cheating is happening if they have no disregard for the innocent? It looks like AM was just a fantasy porn site for married men since most of them didn’t have an actual affair aside from the hookers that Thadeus didn’t know about until after. It seems pretty clear they’re be angry at men. Deuszu posts a lot about child abuse/molestation so that is usually done by men who would be cheating also if they are married. They could very well have been molested/abused/cheated on themselves too. There are subtleties and hints in the posts that show Thadeus is not a man and you can tell with deuszu that some of the nicknames are women. No all they have to do is find the link which they hinted that they can get rid of at any instant, which is probably a laptop or something. Something else will be discovered though since it obviously didn’t take long for the internetz to out them.
So the account was created in February of 2015, and some point after that a bunch of Canadian references were removed. Within that Twitter account, whoever it was talked about taking over accounts. So, February 2015 and yet there’s tweets going back years, and searching them is a bit funky (hence why Mr. Krebs has to put in date ranges to scrape). Could these have all been backdated via Twitter’s API? And the celeb links just have been paid for or flat-out hacked hacks/links (would explain the deletion far more reasonably than someone, say, going Full Streisand) — especially given this ‘guy’s penchant for stock art? I read someone said they followed him for about 6 months, but has anybody known anything about this guy PRIOR to early this year?
No conspiracy theories, just pondering possibilities. It takes true laziness to concoct characters out of TV shows and movies and do quotes from those movies. Someone trying to pull a ThadeuSoze? 😉
http://41.media.tumblr.com/5b7b6bc9ea3d42c2700683d5de9d95ed/tumblr_nis4q3B11V1rw1poro1_1280.png
This tour date pic and time zone shows that Thadeus (Dahl) was in Australia especially since she probably follows Rose around like a lap dog because of her insecurities about Rose cheating on her. Hey she’s bro and man so she probably would be thinking like the stereotypical male and give in to a hot woman.
Unfortunately, allaboutashley is still online
Did anybody find out anything more about allaboutashley?
Why is “allaboutashley ” still on line?
Did anyone find out more about “all aboutashley”?
Who is hosting this site?
It’s hosted in Costa Rica. I’m pretty sure it’ll be a while before it gets taken down.
I bet whoever diego and amigo is runs the site
From what I can gather allaboutashley.cr IP locates in Maidenhead, UK. Would like to see if any others see this.
allaboutashley.cr is hosted in Hampshire,UK, most likely, but could be on several servers. IP tracker found several locations, all in UK, but it is consistently there. http://www.redstation.com/ is named as the server provider. Also, http://www.creeperhost.net/.
For the all**********.cr site – does anyone have contacts or relationship with Sharesale – the affi;iate program. The ads they are running on that site, some are from there, and if this guy really wants to get paid, some info he used to sign up for ShareASale has to be real. The affiliate ID is right in the link of the ad, so not hard for a SaS employee to track down. at the very least – cut off his income opportunities from this.
If you have been following this account from the initial leak, you would know that they will often identify which one is ‘on’. Sometimes Black Hat as they call him. Sometimes others. Claiming to be in different time zones/locations. The gibberish is some form of communication amongst them to limit tracking I would think. But all in all it is a pretty ingenious way to attempt anonymity. Attempt being the operative word
To me it looks like someone who’s trying to make it look like this is what’s going on, when it’s not. There’s a whiff of wannabe LulzSec’ry with a tinge of desperation to it. It looks like he’s creating a story.
hmmm. Possibly. It just seems too random in response to be a tactic. IMO. Regardless, as brazen as this account has been, the right fuel could trigger a slip up
Thadeus Zu. T. Zu. Tzu.
Tha Deus. The God.
“God” Tzu. Sun Tzu.
Where there’s a tool?
Looks more like a strategy, not a tactic.
Hi Brian,
Glad that you agreed with me on the comments I made yesterday. Let me know if you need any other tips 😉
I still think it might be feds. I have not seen as much hatred for hackers and anonymity on the next before this hack. People are screaming for hacker blood.
Hi Brian,
Saw you recent post @deuszu … Glad you agree with my position I posted yesterday, let me know if you need any more tips 😉
I checked out that allaboutashley website. Checked nickname. Came back with accurate info. City, profile. But said, “Possible” CC transactions. Any idea what that means? Has anyone else tried and saw anything? I set up an account a few years back just to check it out but cant remember for the life of me if I paid or not. Apart from a CC transaction- I cant see myself being outed. But I cant recall. In fact in my right mind I don’t think I would ever do something so dumb. But who knows. Any feedback would be appreciated. (Hope that website isn’t collecting data- used burner email any way) BTW- I hope Brian is making the hackers feel the way they made 32 million people feel.
I don’t know how long that site will remain. However, it needs to come down. They serve no useful purpose other than to dissiminate stolen personal and private information.
Yeah. It’s like Hydra man. Cut one head off two more take its place. There’s no way to beat this back. I’m just wondering who the people are running these sites and what they do what the data of those who do searches.
“That account also is following several Australian lawmakers that govern states in south Australia.”
South Australia is a state, perhaps the term southern Australia would be better?
I found your @deuszu (The General) one of five members. I located ‘Doc’ at this point with other links sent to … edited for ATIP.
Michael
If he has admitted to previous hacking, why hasn’t he been arrested yet?
Why isn’t this guy in jail for admitted hacks?
Link, you should get a split of that reward money. You caught them as they were trying to “disappear” into Hollywood life with Ruby Rose’s career taking off.
To me, from looking at their tweets, it seems as if they each have their own signature to sign off each tweet. ‘Amigo’, ‘Folks’, and ‘Man’.
This could distinguish between each person.
The font differences are obvious…
HaHA narcissistic ‘ beta ‘ guys being scammed by AM
The most hilarious revelation about the Ashley Madison hack yet
https://tinyurl.com/py7qdx9
Hope U EnJoY ‘ Yur ‘ Fembots!
Man and bro are both Ruby Rose and the main person without a nickname is Phoebe Dahl. Oz girlie is Maia Mitchell. B hat could be John Shahidi and amigo and ninja could be Rudy Mancus. As mentioned before the main person was saying that these are not their main jobs so what a perfect way to “disappear” into Hollywood. What a perfect way to “hide” when no one would suspect it. Shahidi was a victim of bullying and the others could easily have motives, may have been victims of abuse/molestation, or have been cheated on so they can all be perfect suspects. If Ruby Rose has a new hair cut from bro’s comment about not wanting to jump fences it would be too much of a coincidence. Sad part is that they are going down for exposing an immoral business but it was still wrong to expose people’s private information especially on a site that had so few actual sites. It shows that it was probably just a fantasy porn site for married dude’s to jack off to. Isn’t every person that watched porn guilty of the same thing? At least they can cash in on their own starring roles in the movie they can make out of this. Now where’s my share of the reward money?
thank you the impact team for hacked shley madison
The various file data dumps provide some very vital clues..as to where would this type of data be located within the (Madison Database Storage Structure)how would this inner structure be compiled from a (Programmers Perspective) whose work would be compiling a (Database structure To accommadate vast storage of Information)..so according to my (Software expert sources) who deal with this type of (software Engineering) lets look at the file/data dumps and look in our simulation where would this type of information be stored..what is required to obtain such a vast amount of information…by simply (Hacking via The Front door?)…in easy to understand language…(PC-User via The Internet into a server based system) and obtain vast amounts of data information..simulation found that any presumed hacker–cracker group..with whatever reversed/custom built/software/tools at there disposal wouldnt get very far 1nce inside to access data..because of how the (Structure For storing Info Is Built Up)…in the simulation of a basic system…when you have (Admin access-To Such A Structure-You have complete access to the entire inner structure of everything that is stored in Parent/Sub Directories/Folders/Encryption the whole kaboodle A-To-Z-meaning that you have (Administrator access for the purpose of maintaining the entire inner workings of any given sites..software maintenance structure)..further consultation revealed that these hackers fundamental mistakes indicate that they had (Backdoor-Admin Access)..meaning that an inside source gave them the access login details to access the entire site inner software/data storage structure…it makes no diffirence how poorly designed a website is..in how it is built…there are always certain criteria that are in place..
——————————————————-
the dump data files provide the clues as to where they are located…any hacker..cracker..IT Expert who reads here and says it isnt so..the ashley data dump files provide the hidden clues..that are overlooked…because the only way you can access this amount of data is via the (Back-door-Admin Access) there isnt any other method you can access it..via the (Front Door)..thats the opinion of some (Software Engineering Sources)
——————————————————-
Regarding the twitter user Thadeuz endless tweets about whats going on..his opinions..lets take (Blackhat Reference)..could he be referring to a (Hacking forum/website/Hacking group?)..theres a hack forum/website/group…somewhere…korvacs..various names..what do you look for in his tweets..his possibly referring to hackers..crackers..within a hack..crack movement/group..his followers..some of there tweets are of a technical nature which indicates…theres a hack..crack group of individuals on twitter…social media etc..involved?…maybe?
——————————————————-
pronounciation of words in tweets..how the various tweets on this twitter account reveal some clues..that there are other persons posting on the same account..that shouldnt be a problem..a backtrace from twitter will reveal who has access to that twitter account and where it is coming from..indications..you can look at…(Ireland-Uk/..how do people pronounce certain words in tweets..could he/she be a individual..playing mind games.?..maybe?..personally i dont think so…
——————————————————-
references made by this twitter user as reading the media/getting info from the media..there isnt any noticible reference…as to where he/she might be getting info..the only reference is the tweets..
——————————————————-
he has knowlege of extensive computer/IT knowlege his profile on klear.com..when you read what he likes..then you realise..that this person knows more than what he/she is saying publically…on klear.com formerly twirlwind..you get a clue as to who this person chats with..what do they have in common with each other…(Computers/IT Technology)..websites of interest..people of interest..the common denominator there is activists/movements/internet activities/Computers/IT Tech..etc…the twitter user in his tweets claims his innocent..yet on klear prof the vast interest in the common denominator being (Computers/IT Tech etc)…the link to the dump files..before its known publically..how would such a person know where to find the site..post the link..and the blog owner here gets his link…it poses the question?..did it come from the same twitter source..that answer according to some sources is (Could very well be?)
——————————————————-
the site owner here gets a link to the download site for the dump data files..why?..to understand the phycology of hackers..crackers..you need to know what drives them..mainly to exploit online security systems..its a challenge..you dont know who i am.who we are etc..in fact…there mere statements..activities..always lead back to them…
——————————————————-
when that reward of 500.000 usd which is public..thats not enough for a person to split when you up that kind of reward up to over a 1mil bucks..some1 is going to split..money talks..in addition knowing who is swinging the right bat in the hacking..cracking arena..will give the answers to the questions..some1 knows something..somewhere..its just whose swinging the bat to open the right doors…
——————————————————-
—