AshleyMadison.com, a site that helps married people cheat and whose slogan is “Life is Short, have an Affair,” recently put up a half million (Canadian) dollar bounty for information leading to the arrest and prosecution of the Impact Team — the name chosen by the hacker(s) who recently leaked data on more than 30 million Ashley Madison users. Here is the first of likely several posts examining individuals who appear to be closely connected to this attack.
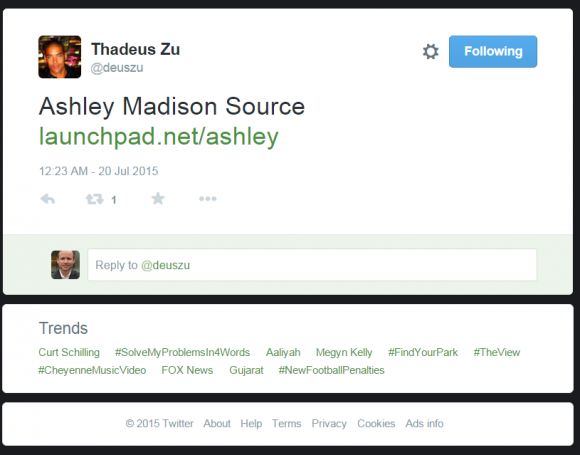 It was just past midnight on July 20, a few hours after I’d published an exclusive story about hackers breaking into AshleyMadison.com. I was getting ready to turn in for the evening when I spotted a re-tweet from a Twitter user named Thadeus Zu (@deuszu) who’d just posted a link to the same cache of data that had been confidentially shared with me by the Impact Team via the contact form on my site just hours earlier: It was a link to the proprietary source code for Ashley Madison’s service.
It was just past midnight on July 20, a few hours after I’d published an exclusive story about hackers breaking into AshleyMadison.com. I was getting ready to turn in for the evening when I spotted a re-tweet from a Twitter user named Thadeus Zu (@deuszu) who’d just posted a link to the same cache of data that had been confidentially shared with me by the Impact Team via the contact form on my site just hours earlier: It was a link to the proprietary source code for Ashley Madison’s service.
Initially, that tweet startled me because I couldn’t find any other sites online that were actually linking to that source code cache. I began looking through his past tweets and noticed some interesting messages, but soon enough other news events took precedence and I forgot about the tweet.
I revisited Zu’s tweet stream again this week after watching a press conference held by the Toronto Police (where Avid Life Media, the parent company of Ashley Madison, is based). The Toronto cops mostly recapped the timeline of known events in the hack, but they did add one new wrinkle: They said Avid Life employees first learned about the breach on July 12 (seven days before my initial story) when they came into work, turned on their computers and saw a threatening message from the Impact Team accompanied by the anthem “Thunderstruck” by Australian rock band AC/DC playing in the background.
After writing up a piece on the bounty offer, I went back and downloaded all five years’ worth of tweets from Thadeus Zu, a massively prolific Twitter user who typically tweets hundreds if not thousands of messages per month. Zu’s early years on Twitter are a catalog of simple hacks — commandeering unsecured routers, wireless cameras and printers — as well as many, many Web site defacements.
On the defacement front, Zu focused heavily on government Web sites in Asia, Europe and the United States, and in several cases even taunted his targets. On Aug. 4, 2012, he tweeted to KPN-CERT, a computer security incident response team in the Netherlands, to alert the group that he’d hacked their site. “Next time, it will be Thunderstruck. #ACDC” Zu wrote.
The day before, he’d compromised the Web site for the Australian Parliament, taunting lawmakers there with the tweet: “Parliament of Australia bit.ly/NPQdsP Oi! Oi! Oi!….T.N.T. Dynamite! Listen to ACDC here.”
I began to get very curious about whether there were any signs on or before July 19, 2015 that Zu was tweeting about ACDC in relation to the Ashley Madison hack. Sure enough: At 9:40 a.m., July 19, 2015 — nearly 12 hours before I would first be contacted by the Impact Team — we can see Zu is feverishly tweeting to several people about setting up “replication servers” to “get the show started.” Can you spot what’s interesting in the tabs on his browser in the screenshot he tweeted that morning?
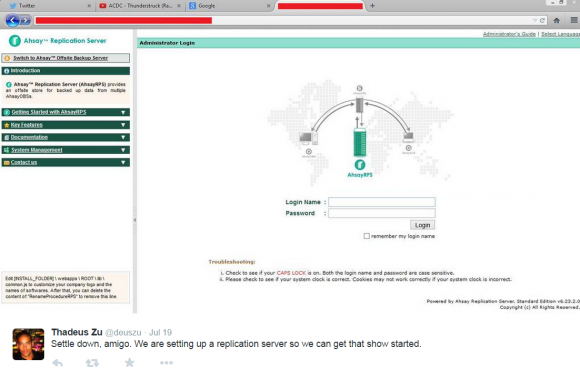
Twitter user ThadeusZu tweets about setting up replication servers. Did you spot the Youtube video he’s playing when he took this screenshot?
Ten points if you noticed the Youtube.com tab showing that he’s listening to AC/DC’s “Thunderstruck.”
A week ago, the news media pounced on the Ashley Madison story once again, roughly 24 hours after the hackers made good on their threat to release the Ashley Madison user database. I went back and examined Zu’s tweet stream around that time and found he beat Wired.com, ArsTechnica.com and every other news media outlet by more than 24 hours with the Aug. 17 tweet, “Times up,” which linked to the Impact Team’s now infamous post listing the sites where anyone could download the stolen Ashley Madison user database.
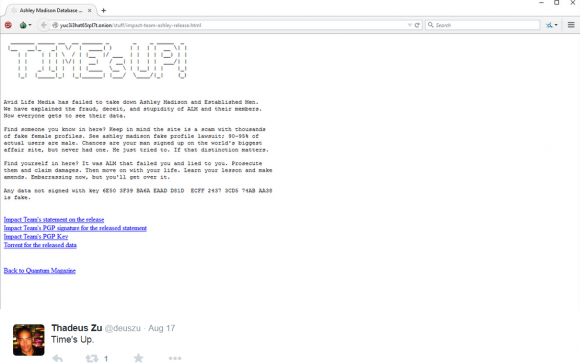
ThadeusZu tweeted about the downloadable Ashley Madison data more than 24 hours before news outlets picked up on the cache.
WHO IS THADEUS ZU?
As with the social networking profiles of others who’ve been tied to high-profile cybercrimes, Zu’s online utterings appear to be filled with kernels of truth surrounded by complete malarkey– thus making it challenging to separate fact from fiction. Hence, all of this could be just one big joke by Zu and his buddies. In any case, here are a few key observations about the who, what and where of Thadeus Zu based on information he’s provided (again, take that for what it’s worth).
Zu’s Facebook profile wants visitors to think he lives in Hawaii; indeed, the time zone set on several of his social media accounts is the same as Hawaii. There are a few third-party Facebook accounts of people demonstrably living in Hawaii who tag him in their personal photos of events on Hawaii (see this cached photo, for example), but for the most part Zu’s Facebook account consists of pictures taken from stock image collections and do not appear to be personal photos of any kind.
A few tweets from Zu — if truthful and not simply premeditated misdirection — indicate that he lived in Canada for at least a year, although it’s unclear when this visit occurred.
 Zu’s various Twitter and Facebook pictures all feature hulking, athletic, and apparently black male models (e.g. he’s appropriated two profile photos of male model Rob Evans). But Zu’s real-life identity remains murky at best. The lone exception I found was an image that appears to be a genuine group photo taken of a Facebook user tagged as Thadeus Zu, along with an unnamed man posing in front of a tattoo store with popular Australian (and very inked) model/nightclub DJ Ruby Rose.
Zu’s various Twitter and Facebook pictures all feature hulking, athletic, and apparently black male models (e.g. he’s appropriated two profile photos of male model Rob Evans). But Zu’s real-life identity remains murky at best. The lone exception I found was an image that appears to be a genuine group photo taken of a Facebook user tagged as Thadeus Zu, along with an unnamed man posing in front of a tattoo store with popular Australian (and very inked) model/nightclub DJ Ruby Rose.
That photo is no longer listed in Rose’s Facebook profile, but a cached version of it is available here. Rose’s tour schedule indicates that she was in New York City when that photo was taken, or at least posted, on Feb. 6, 2014. Zu is tagged in another Ruby Rose Facebook post five days later on Valentine’s Day. Update, 2:56 p.m.: As several readers have pointed out, the two people beside Rose in that cached photo appear to be Franz Dremah and Kick Gurry, co-stars in the movie Edge of Tomorrow).
Other clues in his tweet stream and social media accounts put Zu in Australia. Zu has a Twitter account under the Twitter nick @ThadeusZu, which has a whopping 11 tweets, but seems rather to have been used as a news feed. In that account Zu is following some 35 Twitter accounts, and the majority of them are various Australian news organizations. That account also is following several Australian lawmakers that govern states in south Australia.
Then again, Twitter auto-suggests popular accounts for new users to follow, and usually does so in part based on the Internet address of the user. As such, @ThadeusZu may have only been using an Australian Web proxy or a Tor node in Australia when he set up that account (several of his self-published screen shots indicate that he regularly uses Tor to obfuscate his Internet address).
Even so, many of Zu’s tweets going back several years place him in Australia as well, although this may also be intentional misdirection. He continuously references his “Oz girl,” (“Oz” is another word for Australia) uses the greeting “cheers” quite a bit, and even talks about people visiting him in Oz.
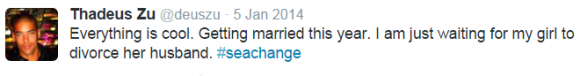
Interestingly, for someone apparently so caught up in exposing hypocrisy and so close to the Ashley Madison hack, Zu appears to have himself courted a married woman — at least according to his own tweets. On January 5, 2014, Zu tweeted:
“Everything is cool. Getting married this year. I am just waiting for my girl to divorce her husband. #seachange
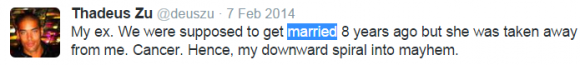
A month later, on Feb. 7, 2014, Zu offered this tidbit of info:
“My ex. We were supposed to get married 8 years ago but she was taken away from me. Cancer. Hence, my downward spiral into mayhem.”
To say that Zu tweets to others is a bit of a misstatement. I have never seen anyone tweet the way Zu does; He sends hundreds of tweets each day, and while most of them appear to be directed at nobody, it does seem that they are in response to (if not in “reply” to) tweets that others have sent him or made about his work. Consequently, his tweet stream appears to the casual observer to be nothing more than an endless soliloquy.
But there may something else going on here. It is possible that Zu’s approach to tweeting — that is, responding to or addressing other Twitter users without invoking the intended recipient’s Twitter handle — is something of a security precaution. After all, he had to know and even expect that security researchers would try to reconstruct his conversations after the fact. But this is far more difficult to do when the Twitter user in question never actually participates in threaded conversations. People who engage in this way of tweeting also do not readily reveal the Twitter identities of the people with whom they chat most.
Thadeus Zu — whoever and wherever he is in real life — may not have been directly involved in the Ashley Madison hack; he claims in several tweets that he was not part of the hack, but then in countless tweets he uses the royal “We” when discussing the actions and motivations of the Impact Team. I attempted to engage Zu in private conversations without success; he has yet to respond to my invitations.
It is possible that Zu is instead a white hat security researcher or confidential informant who has infiltrated the Impact Team and is merely riding on their coattails or acting as their mouthpiece. But one thing is clear: If Zu wasn’t involved in the hack, he almost certainly knows who was.
KrebsOnSecurity is grateful to several researchers, including Nick Weaver, for their assistance and time spent indexing, mining and making sense of tweets and social media accounts mentioned in this post. Others who helped have asked to remain anonymous. Weaver has published some additional thoughts on this post over at Medium.




Ashley’s Brother’s link still remains on this site, under the story “Leaked AM emails suggest execs hacked competitors.”
I’m curious as to why no one has bothered to check certain servers for trace information.
For example, MIT’s PGP server:
https://pgp.mit.edu/pks/lookup?search=impact+team&op=index
And surely a request for info (IP address, etc.) could be submitted to MIT as well as any other key servers out there.
The key has a couple of signers, one of which states “That was a big error. I hope they catch you,” and links to an article. The others being listed as Kodak, adela, Daniel Janes and, three removed sigs (possibly the four using the Twitter account?).
Cheers and feel free to share the reward cash lol. No, seriously 😉
Hey, he’s close to the source. He wants credit, but he’s not the man.
Hey, if she was the one that ordered for it to be done, she’s the man. What hacker dude would just after AM unless they were getting paid to or ordered to do?
Anyone can sign a key, right?
Does anyone know how to bring down the website allaboutashley.cr? who can I complain to?
You do realize that you’ve just created the Streisand effect, right?
I was reading this article and am trying to make sense of it – when you read this, it makes it sound as if the “paid delete” data reveals less in the leaked information than the regular data. Does anyone else interpret this the same way? The chart seems to imply it.
http://www.businessinsider.com/ashley-madison-full-delete-class-action-lawsuit-2015-8?r=UK&IR=T
Digg this. I found the name and address of the guy running the allaboutashley.cr site. It’s a Costa Rican website. So can’t be DMCd but he is in America. You can find the info easy enough if you search.
Does that mean we can’t force them to bring down website? I doubt that contacting the website will make them change their minds?
As much as Im hoping this story will just go away, Im afraid it will not. As more and more search engines pop up online, in particular those which allow a search by name or address, this story will only continue to spread. Facebook users will start posting links to search sites. Sh&% is about to hit the fan.
We all need to actively work at reporting twitter, facebook, etc users and get these links or sites taken down.
Sure, another major event in the news will temporarily distract the public, but unfortunately this story has staying power.
Will someone please remind me to breathe and that one day (maybe) this story will just go away.
Agree – Twitter/FB need to be reminded to delete these posts with links to stolen information.
http://www.businessinsider.com/ashley-madison-full-delete-class-action-lawsuit-2015-8?r=UK&IR=T
Breathe, please.
the founders hacked other databases to populate theres.
the data has been around the wringer on the internet for two weeks.
phishing sites where people load names to “check” are returning false possitives and “inserting” the checked names in order to get more desperate victims to pay something.
cc fraud and email fraud make up a percentage (5-25%) of the data.
anyone with brains will not trust this data, especially the longer it is “out there”. no custody chain for anything that is legal.
and the victims had the nerve to do what?
flirt online? online voyerism? this is a dating site.
you did nothing illegal! you flirted online? big deal.
the pitchfork crowd will just have to get over it.
the peeps who did this are evil. you are not.
Did Biderman lie when he said he knew who the culprit was?
“We’re on the doorstep of [confirming] who we believe is the culprit, and unfortunately that may have triggered this mass publication,” Biderman said. “I’ve got their profile right in front of me, all their work credentials. It was definitely a person here that was not an employee but certainly had touched our technical services.”
Do you think that the FBI can help with these offshore websites? Isn’t doxcing illegal?
You can also start looking here–found it on a BBS..
https://twitter.com/amlolzz..according to the source there this person and the thadeuz zu person are linked to the inner circle of the impact team group
https://voat.co/v/news/comments/454705
Dear Sirs,
> the hacker(s) displayed threatening messages on the computers of Ashley Madison employees, accompanied by AC/DC song Thunderstruck…
Curiously, the AC/DC song “Thunderstruck” was also prominently featured in a cyber-weapon malware, which was employed by Israel, USA and Australia against the iranian nuclear programme three some years ago.
For more info see the following article or contact F-Secure’s virus lab:
http://www.bloomberg.com/news/articles/2012-07-25/iranian-nuclear-plants-hit-by-virus-playing-ac-dc-website-says
Best Regards: Tamas Feher from Hungary.
deuszu (Dahl) posted the greek translation for Oedipus The King probably because they know they were outed. It was probably an inside job one of them did (ninja) or had someone do as an outside contractor. Judging from all the posts about child abuse they obviously would have an issue with AM. They’d be looking like the stereotypical man hating angry lesbians especially when there were so few women on there to begin with.
Plus Dahl and Rose were just hanging out with Taylor Swift so maybe they are doing it as a girl power thing. Or maybe it was Swift that orchestrated everything and they just met up to touch base! Hahaha
I meant to say they knew they were outed by their own doing
They were using Jared Fogle’s tactics of using their business trips (tour) to diguise their moves but went down like both the Silk Road founders by their own fault. Pretty shady tactics to be using especially on some pretty pretentious and hypocritical principles.
You don’t taunt a community that might’ve been on your side to begin with and expect not to get caught especially with a bounty out there. Keep quiet and move on. The intention was clear that they wanted to exploit this for their own gain too and drag it on.
If this had been a hack of a hospital database, and all data was dumped, resulting in suicides, and possible future executions of gay people in countries where it’s forbidden to be gay.
Then all people would have been asking for the death penalty for the murderous hackers.
But since it was a website dealing in a legal business that some people deem not up to their own moral standards, the murderous hackers don’t get talked about much, but all talk about the people who signed up to AM.
It’s great to see that people like Krebs are hunting the muckers, I hope they get caught and locked up for ever in a jail without any windows.
Because for me what ever the AM users might have done morally wrong, doesn’t compare to the murderers who dumped the database.
You should be very careful before making such accusations. What if you are wrong ? What would be the consequences ?
The problem is not being right. It’s that you probably won’t accept responsability for anything bad that could happen if you are wrong.
This is not proper process. There’s a reason why it’s called “due process” by the legal system.
It appears that the (Impact Team Hack Group) has interests in this material as well
FinFisher 2014 Leaked Material – The Uncensored Hidden Wiki https://ev3h5yxkjz4hin75.onion.cab/wiki/index.php/FinFisher_2014_
as in the finfisher dump are some very interesting clues…found in similiarities possibly…
———————————————————
on this site are various links…
http://8ch.net/ashley/
——————————————————-
the hack group has interest in the hack team activities and some other links…
——————————————————-
Brian, you’re mentioned again, with an actual link to your site. Kudos.
http://www.cbc.ca/m/touch/business/story/1.3206987
As others have stated, it’s more than one person operating the deuszu twitter. They might not even know each other personally, but if there are clues pointing at the US, Aus, CA, etc. They seem to operate on almost a 24 hour cycle. I also see that at least one of the members had nothing to do with it “I didn’t do it”. And other(s) that did, or at least have knowledge of who did. Krebs has said as much himself.
The conversation on twitter is probably a small portion of a larger conversation taking place via another channel, maybe IRC, email, facebook or ??
A lot of guilt though – I see that they closed the deuszu facebook immediately after this came out and also a tantrum on twitter and a lot of “come and get me”.
Both the AM hackers AND deuszu seem to think that the solution to problems is to sue in court. Funny that they have outed millions of guys but also hide behind technology instead of being public. if their cause is so just, then why not be public? Because they are scardycats, that’s why.
I have no idea if ruby rose or dahl are involved, but one of them might know one of the deuszu people. I do think at least one of the deuszu members is female – a lot of reference to “girly” and “oz girl” etc. But the rest are guys “amigo” “bro” “hombre” “redneck” “chief” etc.
Brian,
Great piece of detective work. Makes sense to me and I hope that these hackers get caught. They did expose a company that was selling a lie but in the process are destroying innocent people’s lives.
1. I have been constantly searching Google and other sites for AM hack list search engines and have yet to find one that allows you to search by the individual’s name, street address or zip code. Most of the searches are based on the email used on the AM account. Therefore, unless you have actually downloaded the hacked files, is there a way to find an individual’s name and street address on an account?
2. I see some have some lists on Pastebin that post emails and street addresses. Some are removed quickly and some remain. Can these people be charged for distributing stolen property? Maybe the government needs to make an example out of a few of these individuals.
3. AM is using DMCA to suppress the info. Suing AM and putting them out of business is going to prevent their ability to do this. Even if a class action lawsuit is successful, how much is each participant going to be awarded? So what is the lesser of two evils? Not sue and allow them to stay in business so they can continue to suppress? Or litigate them out of business and let the information come to the surface and be readily available?
Love to know his home address.
I presume that any question regarding veracity of the Gospels is not of particular concern to the enigmatic Zu, given that “Thadeus Zu” can be roughly equated to “The Divine Zu”.
(He is, after all, His own frame of reference wrt such texts).
cloud, DRM, IoT looks pseudo in front of these hackers.
release his info and everyone send an email to above address to get this crap off
Here’s an idea of Brian and others to consider.
The link on the tab in the image that shows “Thunderstruck” is a Youtube page. Since from the Twitter account we have a date and a time of the screen capture Youtube could easily perform a statistical analysis of views on that video and see if there was a person who was continuously streaming that video in that time frame. I bet the list of IPs is going to be very small.
It might just show a Tor exit node but maybe not.
After much digging we can share the following:
1) we have identified the owner of the AshleyBrother.
2) we have his name.
3) we have his address.
4) we have his email.
5) we believe we have his phone but still verifying.
6) we have a Google map of his address.
7) we have varied screen captures of his website.
8) we have the sites WhoIs information.
9) we have the business contact information for the server and domain provider.
10) we have identified the media contacts in his area.
11) while we will not share this data on this, or any blog, should the site remain active we will share all this data with the media to shine a spotlight on the misery peddlers that are profiting off the data theft. We are sure those impacted would appreciate knowing who and where the owner of AshleyBrother is. The story will start as local and quickly become national shining a spotlight on one individual.
This was posted back in thread. It should be repeated. Good work Sanji.
After much digging we can share the following:
1) we have identified the owner of the AshleyBrother.
2) we have his name.
3) we have his address.
4) we have his email.
5) we believe we have his phone but still verifying.
6) we have a Google map of his address.
7) we have varied screen captures of his website.
8) we have the sites WhoIs information.
9) we have the business contact information for the server and domain provider.
10) we have identified the media contacts in his area.
11) while we will not share this data on this, or any blog, should the site remain active we will share all this data with the media to shine a spotlight on the misery peddlers that are profiting off the data theft. We are sure those impacted would appreciate knowing who and where the owner of AshleyBrother is. The story will start as local and quickly become national shining a spotlight on one individual.
Guys I am sorry to share this but the websites are popping up by the minute. Google am hacks and now there are advertisements for new websites. There is no plugging this hole. Good luck y’all.
No they are not “popping up by the minute”. Talking about refer to sites like Trustify and the like which harvest email addresses and require substantial fees.
To report abuse of a .xyz domain, please contact the .xyz Abuse Team at xyz_abuse@gen.xyz
or 2800 Olympic Blvd Ste 100 Santa Monica, CA 90404
Tell them that their site contains stolen personal info on private individuals and needs to be taken down ASAP
https://am.kyber.fi/ is still providing the possibility to check if specific information was included in the leak (email address or credit card details). Please note that this web site does not host any actual information itself.
https://sintonen.fi/ashley-madison/ will continue to provide a forward to the current location of the website (in case it somehow would need to relocate).
Thanks for the peoples whose hacked this useless website keep up hackers try another!!!
i am a victim of the hacked data as I received an email last Wednesday from the impact team stating I had 96 hours to pay two Bitcoins or my data would be sent to my home address. They email contained a sample of recent credit card purchases and showed the last 4 digits of my card#. The email even showed my last name and zip code. I am terrified they will send the letter as I made the decision to not give in to the extortion. I am afraid to contact the FBI because I don’t want this to go public. I don’t know what to do. For my sake and that of countless others, I hope these cowards are caught and punished to the fullest extent of every law they’ve broken.
Hi George – I am so sorry to hear you got the same thing! My friend also had 96 hours to pay up….same thing: send 2 BTCs or the letter with address/CC/ will be sent. He is very nervous…I have to ask, did they send the letter? I respect your privacy, just asking for a friend if anything has happened yet. Hope you are hanging in there, and hope this blows over soon.