In December 2013, just days after a data breach exposed 40 million customer debit and credit card accounts, Target Corp. hired security experts at Verizon to probe its networks for weaknesses. The results of that confidential investigation — until now never publicly revealed — confirm what pundits have long suspected: Once inside Target’s network, there was nothing to stop attackers from gaining direct and complete access to every single cash register in every Target store.
 According to an internal corporate report obtained by KrebsOnSecurity, Target commissioned the study “in anticipation of litigation” from banks that might join together to sue the retailer in a bid to recoup the costs of reissuing cards to their customers. Last week, a federal judge cleared those claims to go forward in a class action suit.
According to an internal corporate report obtained by KrebsOnSecurity, Target commissioned the study “in anticipation of litigation” from banks that might join together to sue the retailer in a bid to recoup the costs of reissuing cards to their customers. Last week, a federal judge cleared those claims to go forward in a class action suit.
The Verizon assessment, conducted between December 21, 2013 to March 1, 2014, notably found “no controls limiting their access to any system, including devices within stores such as point of sale (POS) registers and servers.”
The report noted that Verizon consultants were able to directly communicate with point-of-sale registers and servers from the core network. In one instance, they were able to communicate directly with cash registers in checkout lanes after compromising a deli meat scale located in a different store.
Verizon’s findings lend credence to the working theory about how hackers initially broke into Target. In February 2014, KrebsOnSecurity was the first to report that investigators had zeroed in on the source of the breach: Fazio Mechanical, a small heating and air conditioning firm in Pennsylvania that worked with Target and had suffered its own breach via malware delivered in an email. In that intrusion, the thieves managed to steal the virtual private network credentials that Fazio’s technicians used to remotely connect to Target’s network.
Verizon’s report offers a likely playbook for how the Target hackers used that initial foothold provided by Fazio’s hack to push malicious software down to all of the cash registers at more than 1,800 stores nationwide.
Target spokesperson Molly Snyder would neither confirm nor deny the authenticity of the documents referenced in this report, but she maintained that Target has made great strides and is now an industry leader on cybersecurity.
“We’ve brought in new leaders, built teams, and opened a state-of-the-art cyber fusion center,” Snyder said. “We are proud of where we stand as a company and will be absolutely committed to being a leader on cybersecurity going forward.”
Snyder said Target believes “that sharing accurate and actionable information – with consumers, policy makers, and even other companies and industries – will help make all of us safer and stronger,” she said in an emailed statement. “Sometimes that means providing information directly to consumers, other times that means sharing information about possible industry threats with other companies or through our participation in the Financial Services and Retail Information Sharing and Analysis Centers (ISACs), and sometimes that means working with law enforcement. What we don’t think it means is continuing to rehash a narrative that is nearly two years old.”
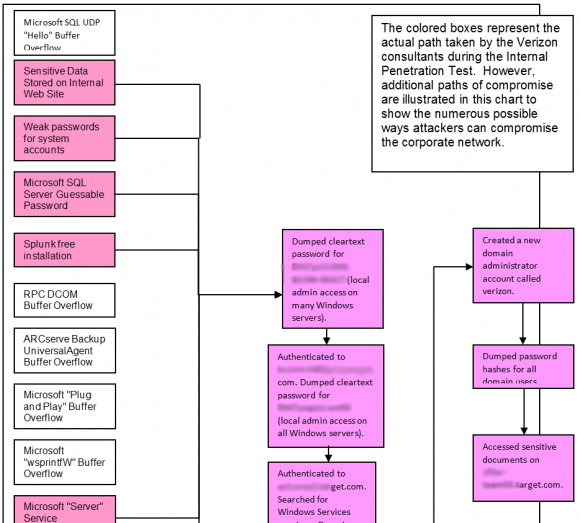
A high-level graphic showing the various routes that Verizon penetration testers were able to use to get all the way down to Target’s cash registers in 2013 and 2014.
THE ROLE OF DEFAULT AND WEAK PASSWORDS
The report notes that “while Target has a password policy, the Verizon security consultants discovered that it was not being followed. The Verizon consultants discovered a file containing valid network credentials being stored on several servers. The Verizon consultants also discovered systems and services utilizing either weak or default passwords. Utilizing these weak passwords the consultants were able to instantly gain access to the affected systems.”
Default passwords in key internal systems and servers also allowed the Verizon consultants to assume the role of a system administrator with complete freedom to move about Target’s sprawling internal network.
“The Verizon security consultants identified several systems that were using misconfigured services, such as several Microsoft SQL servers that had a weak administrator password, and Apache Tomcat servers using the default administrator password,” the report observes. “Through these weaknesses, the Verizon consultants were able to gain initial access to the corporate network and to eventually gain domain administrator access.”
Within one week, the security consultants reported that they were able to crack 472,308 of Target’s 547,470 passwords (86 percent) that allowed access to various internal networks, including; target.com, corp.target.com; email.target.com; stores.target.com; hq.target.com; labs.target.com; and olk.target.com.
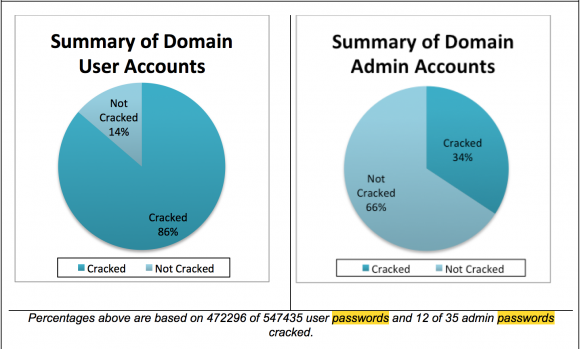
A summary of the user and administrator account passwords that Verizon experts were able to crack within one week of finding them on Target’s network.
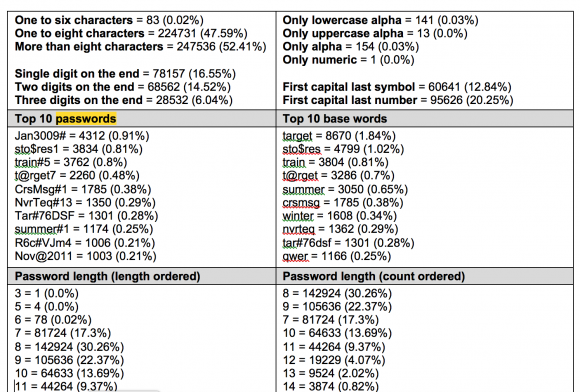
Below are some statistics that Verizon generated, including the “Top 10” rankings of passwords, lengths, base words, and character set complexities.
PATCHY PATCHING
According to the report, the penetration testers also identified many services and systems that were either outdated or missing critical security patches.
“For example, the Verizon consultants found systems missing critical Microsoft patches, or running outdated [web server] software such as Apache, IBM WebSphere, and PHP. These services were hosted on web servers, databases, and other critical infrastructure,” the report notes. “These services have many known vulnerabilities associated with them. In several of these instances where Verizon discovered these outdated services or unpatched systems, they were able to gain access to the affected systems without needing to know any authentication credentials.”
The report continues:
“Verizon and the Target Red Team exploited several vulnerabilities on the internal network, from an unauthenticated standpoint. The consultants were able to use this initial access to compromise additional systems. Information on these additional systems eventually led to Verizon gaining full access to the network — and all sensitive data stored at on network shares — through a domain administrator account.”
TURNING THE SHIP AROUND?
In the follow-up external penetration test conducted in February 2014, Verizon noted many proactive measures that Target was taking to protect its infrastructure. Among them were:
“Verizon found that Target had a comprehensive vulnerability scanning program in place, using Tenable Security Center,” the report notes. “However, the Verizon consultants discovered that remediation procedures did not address findings discovered by the vulnerability scanning program in a timely fashion, if at all.
Likewise, Target made major improvements to vulnerability remediation procedures, the testers found. Due to these changes, many of the most critical findings were fixed within a day or two of being disclosed.
Target also commissioned from Verizon an external penetration test, essentially to see how skilled attackers might fare trying to break into the company’s networks from the Internet. That test, conducted between Feb. 3, 2014 and Feb. 14, 2014, showed that Target was fairly robust at detecting and blocking external attacks.
“In this test, the Verizon consultants were unable to gain interactive access to any of the tested systems’ underlying operating systems,” the report’s executive summary notes. “Although Verizon did find vulnerabilities in some services, these weaknesses did not allow the Verizon security consultants to gain access to any of the systems.”
ANALYSIS
Target has never talked publicly about lessons learned from the breach, no doubt because the company fears whatever it says will be used against it in class-action lawsuits. However, the company has invested hundreds of millions of dollars in additional security personnel and in building out a “cyber fusion center” to better respond to daily threats that confront its various stores and networks.
At the Defcon security conference in Las Vegas this year I met the team leader of Target’s “red team,” a group of security professionals who get paid to constantly test the security of the company’s network and employees. From what I heard in off-the-record conversations, Target has a good story to tell in how it’s handling security threats these days. Unfortunately, the company has declined my request for the access needed to let me tell that story.
While Target hasn’t directly shared its lessons learned from the breach, the penetration test reports from Verizon include some useful — if somewhat obvious — findings that should be instructive for all retailers and larger companies.
For starters, segment your network, and limit the number of people who have access to more sensitive areas of the network. “Target should limit the access to portions of the network containing business critical systems to only the employees who directly manage those systems,” the report reads. “Where possible, Verizon recommends restricting employee network access based on job function.”
Also, establish a system for finding and fixing vulnerabilities on a regular basis, and follow-up to verify the gaps have been closed.
“Verizon recommends continuing to improve the vulnerability remediation program,” the internal penetration test report notes. “Target can significantly increase the security posture of the environment by leveraging the vulnerability scanning program that is currently in place. Vulnerability findings should be communicated to remediation teams and/or device owners using a risk-based approach. Remediation of vulnerabilities should be tracked over time to ensure that issues are being resolved in a timely fashion. Additionally, vulnerabilities should be retested after remediation to ensure that the solutions are complete. A comprehensive vulnerability management program will help the organization to better understand its security posture, while minimizing risk where possible.”
Finally, attack your own network regularly to find holes in your security posture — preferably before the bad guys find and exploit the same flaws.
“Verizon recommends performing routine vulnerability assessments of both internal and external systems, applications, and infrastructure,” the report concludes. “Routine assessments will help to identify vulnerabilities, missing patches, and configuration issues, thereby reducing the amount of time weaknesses exist in the environment.”





As a former CIO for a 400+ store retail chain, the internal penetration test is critical. There were two sets of penetration tests – blind and then with complete internal network documentation. It was performed on both the PCI and non-PCI networks. We actually made it a contest to see who would win ie our internal systems notifying us of potential intrusion against actual compromise. It is mind boggling that Target’s internal pen tests did not discover the issues that Brian reported on unless there was an element of corporate politics involved or their pen testers weren’t competent.
One other important component is the corporate acceptance of PCI and how it must not be just an “IT” issue. The PCI “12 Step” program requires commitment throughout the organization which is critical but it goes further than that. PCI compliance should be a part an overall security program. Implementation of PCI without it is just asking for trouble.
Every breach is due to a corporate failure with some portion of the PCI-DSS document.
I’d be astonished if they had a full-scope internal pen test by a competent group. I’ve lived through several and (so far) only one company kicked our butt through the goal posts. The remainder were just a joke: “Our scanners didn’t find any vulnerabilities so we could not attempt any exploits.”
Even when we complained that the testers were worse than useless, senior management was happy with the final report that showed we were impregnable so our complaints went nowhere. That alone is the clue that they were incompetent. But a good report = compliance and justification for not doing anything else and that’s all that matters..
Care to disclose the vendor that did such a good job?
You are missing one major point! Detecting and reporting the discovered vulnerabilities is one part, the other one is taking appropriate action.
Many times, taking the risk is considered less expensive by senior management, than fixing and changing the attitude and at the end of the day, the IT security guy can point as long as he likes, the accountant is making the final decision.
IT has a tendency to blame users for security failures. The Fazio employee who was phished has been widely reported as an example of a non-IT insider that failed at security. However, most insiders who fail to do their job at Target were IT insiders and IT security insiders. Nonmalicious insiders outside of IT have a lot of things to do besides security. IT and security personnel have no excuse.
There were many steps in the kill chain that allowed the attackers to succeed, culminating in Target security employees failing to heed warnings just before and after the exfiltration of stolen information. IT could have broken that chain at several steps had it been doing what it should have been doing. Phishing attacks are bound to succeed much of the time. That is a fact. IT people, deal with it.
Also, stop using terms like “shadow IT” to refer to what users are doing. A better term is “shadowy IT” to refer to what IT and IT security is doing too often.