In December 2013, just days after a data breach exposed 40 million customer debit and credit card accounts, Target Corp. hired security experts at Verizon to probe its networks for weaknesses. The results of that confidential investigation — until now never publicly revealed — confirm what pundits have long suspected: Once inside Target’s network, there was nothing to stop attackers from gaining direct and complete access to every single cash register in every Target store.
 According to an internal corporate report obtained by KrebsOnSecurity, Target commissioned the study “in anticipation of litigation” from banks that might join together to sue the retailer in a bid to recoup the costs of reissuing cards to their customers. Last week, a federal judge cleared those claims to go forward in a class action suit.
According to an internal corporate report obtained by KrebsOnSecurity, Target commissioned the study “in anticipation of litigation” from banks that might join together to sue the retailer in a bid to recoup the costs of reissuing cards to their customers. Last week, a federal judge cleared those claims to go forward in a class action suit.
The Verizon assessment, conducted between December 21, 2013 to March 1, 2014, notably found “no controls limiting their access to any system, including devices within stores such as point of sale (POS) registers and servers.”
The report noted that Verizon consultants were able to directly communicate with point-of-sale registers and servers from the core network. In one instance, they were able to communicate directly with cash registers in checkout lanes after compromising a deli meat scale located in a different store.
Verizon’s findings lend credence to the working theory about how hackers initially broke into Target. In February 2014, KrebsOnSecurity was the first to report that investigators had zeroed in on the source of the breach: Fazio Mechanical, a small heating and air conditioning firm in Pennsylvania that worked with Target and had suffered its own breach via malware delivered in an email. In that intrusion, the thieves managed to steal the virtual private network credentials that Fazio’s technicians used to remotely connect to Target’s network.
Verizon’s report offers a likely playbook for how the Target hackers used that initial foothold provided by Fazio’s hack to push malicious software down to all of the cash registers at more than 1,800 stores nationwide.
Target spokesperson Molly Snyder would neither confirm nor deny the authenticity of the documents referenced in this report, but she maintained that Target has made great strides and is now an industry leader on cybersecurity.
“We’ve brought in new leaders, built teams, and opened a state-of-the-art cyber fusion center,” Snyder said. “We are proud of where we stand as a company and will be absolutely committed to being a leader on cybersecurity going forward.”
Snyder said Target believes “that sharing accurate and actionable information – with consumers, policy makers, and even other companies and industries – will help make all of us safer and stronger,” she said in an emailed statement. “Sometimes that means providing information directly to consumers, other times that means sharing information about possible industry threats with other companies or through our participation in the Financial Services and Retail Information Sharing and Analysis Centers (ISACs), and sometimes that means working with law enforcement. What we don’t think it means is continuing to rehash a narrative that is nearly two years old.”
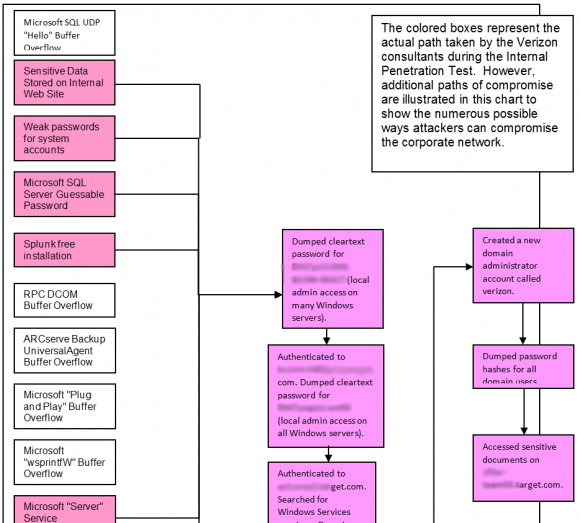
A high-level graphic showing the various routes that Verizon penetration testers were able to use to get all the way down to Target’s cash registers in 2013 and 2014.
THE ROLE OF DEFAULT AND WEAK PASSWORDS
The report notes that “while Target has a password policy, the Verizon security consultants discovered that it was not being followed. The Verizon consultants discovered a file containing valid network credentials being stored on several servers. The Verizon consultants also discovered systems and services utilizing either weak or default passwords. Utilizing these weak passwords the consultants were able to instantly gain access to the affected systems.”
Default passwords in key internal systems and servers also allowed the Verizon consultants to assume the role of a system administrator with complete freedom to move about Target’s sprawling internal network.
“The Verizon security consultants identified several systems that were using misconfigured services, such as several Microsoft SQL servers that had a weak administrator password, and Apache Tomcat servers using the default administrator password,” the report observes. “Through these weaknesses, the Verizon consultants were able to gain initial access to the corporate network and to eventually gain domain administrator access.”
Within one week, the security consultants reported that they were able to crack 472,308 of Target’s 547,470 passwords (86 percent) that allowed access to various internal networks, including; target.com, corp.target.com; email.target.com; stores.target.com; hq.target.com; labs.target.com; and olk.target.com.
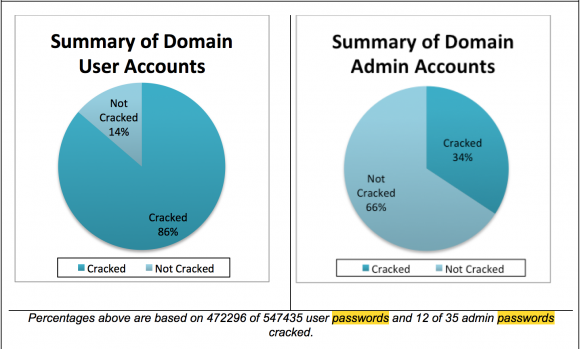
A summary of the user and administrator account passwords that Verizon experts were able to crack within one week of finding them on Target’s network.
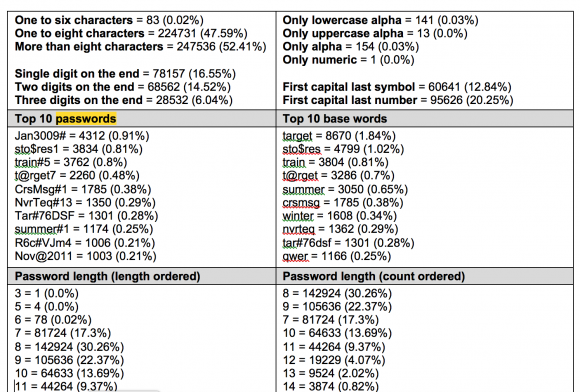
Below are some statistics that Verizon generated, including the “Top 10” rankings of passwords, lengths, base words, and character set complexities.
PATCHY PATCHING
According to the report, the penetration testers also identified many services and systems that were either outdated or missing critical security patches.
“For example, the Verizon consultants found systems missing critical Microsoft patches, or running outdated [web server] software such as Apache, IBM WebSphere, and PHP. These services were hosted on web servers, databases, and other critical infrastructure,” the report notes. “These services have many known vulnerabilities associated with them. In several of these instances where Verizon discovered these outdated services or unpatched systems, they were able to gain access to the affected systems without needing to know any authentication credentials.”
The report continues:
“Verizon and the Target Red Team exploited several vulnerabilities on the internal network, from an unauthenticated standpoint. The consultants were able to use this initial access to compromise additional systems. Information on these additional systems eventually led to Verizon gaining full access to the network — and all sensitive data stored at on network shares — through a domain administrator account.”
TURNING THE SHIP AROUND?
In the follow-up external penetration test conducted in February 2014, Verizon noted many proactive measures that Target was taking to protect its infrastructure. Among them were:
“Verizon found that Target had a comprehensive vulnerability scanning program in place, using Tenable Security Center,” the report notes. “However, the Verizon consultants discovered that remediation procedures did not address findings discovered by the vulnerability scanning program in a timely fashion, if at all.
Likewise, Target made major improvements to vulnerability remediation procedures, the testers found. Due to these changes, many of the most critical findings were fixed within a day or two of being disclosed.
Target also commissioned from Verizon an external penetration test, essentially to see how skilled attackers might fare trying to break into the company’s networks from the Internet. That test, conducted between Feb. 3, 2014 and Feb. 14, 2014, showed that Target was fairly robust at detecting and blocking external attacks.
“In this test, the Verizon consultants were unable to gain interactive access to any of the tested systems’ underlying operating systems,” the report’s executive summary notes. “Although Verizon did find vulnerabilities in some services, these weaknesses did not allow the Verizon security consultants to gain access to any of the systems.”
ANALYSIS
Target has never talked publicly about lessons learned from the breach, no doubt because the company fears whatever it says will be used against it in class-action lawsuits. However, the company has invested hundreds of millions of dollars in additional security personnel and in building out a “cyber fusion center” to better respond to daily threats that confront its various stores and networks.
At the Defcon security conference in Las Vegas this year I met the team leader of Target’s “red team,” a group of security professionals who get paid to constantly test the security of the company’s network and employees. From what I heard in off-the-record conversations, Target has a good story to tell in how it’s handling security threats these days. Unfortunately, the company has declined my request for the access needed to let me tell that story.
While Target hasn’t directly shared its lessons learned from the breach, the penetration test reports from Verizon include some useful — if somewhat obvious — findings that should be instructive for all retailers and larger companies.
For starters, segment your network, and limit the number of people who have access to more sensitive areas of the network. “Target should limit the access to portions of the network containing business critical systems to only the employees who directly manage those systems,” the report reads. “Where possible, Verizon recommends restricting employee network access based on job function.”
Also, establish a system for finding and fixing vulnerabilities on a regular basis, and follow-up to verify the gaps have been closed.
“Verizon recommends continuing to improve the vulnerability remediation program,” the internal penetration test report notes. “Target can significantly increase the security posture of the environment by leveraging the vulnerability scanning program that is currently in place. Vulnerability findings should be communicated to remediation teams and/or device owners using a risk-based approach. Remediation of vulnerabilities should be tracked over time to ensure that issues are being resolved in a timely fashion. Additionally, vulnerabilities should be retested after remediation to ensure that the solutions are complete. A comprehensive vulnerability management program will help the organization to better understand its security posture, while minimizing risk where possible.”
Finally, attack your own network regularly to find holes in your security posture — preferably before the bad guys find and exploit the same flaws.
“Verizon recommends performing routine vulnerability assessments of both internal and external systems, applications, and infrastructure,” the report concludes. “Routine assessments will help to identify vulnerabilities, missing patches, and configuration issues, thereby reducing the amount of time weaknesses exist in the environment.”





Is that cyber fusion center just for security? The state of the art center looks like a waste of money. Image the additional workforce, regular training etc. That’s a massive burden to suddenly carry. Why can this be outsourced to repeatable security companies in the US?
no. You have to test from the inside as well. Also an outside contractor isn’t going to care as much about your network as you should. They can be an aide but not the solution.
Completely agree: outsorcing is something which fits almost zero with Security, if you want a well done job and not a ..TESCO product.
A company the size of Target would do well to have an internal Red Team. Networks are often breached for almost a year before discovery, as the bad guys map out networks and gather information. A Red Team with inside knowledge will find things that an external team may miss, as each network has its own idiosyncrasies.
I disagree about an internal Red team. If I were on the team and knew the results were unsatisfactory but reporting it could cost me my job……..
@Elizabeth, this is why you need a well respected, independent internal audit and IT security division that is going to be applauded, not punished, for finding vulnerabilities and issues.
These do actually exist in some organizations.
That’s not how it works. Reporting issues is good for your job. The red team isn’t in charge of guarding issues, that’s a completely different teams responsibility so there’s no conflict of interest.
Oh Elisabeth! You stuck the finger in the wound !!! Yes, unfortunately very true. Nowadays message carriers are still killed (figuratively speaking). It is very true than when Security professionals put all outside the mouth, then usually they are fired. It’s a tough world to live in, as this is mostly happening when people on the top (CISO, CIO, etc.) have absolutely no clue of what they are doing, because they almost NEVER have a decent technical background. That is considered yuk yuk ! But then those with just MBAs are usually failing miserably in these positions.
That actually looks about the right size for a security force for one of the largest big box retailers in the nation. Not only should you have blue teamers constantly monitoring dashboards for the various security appliances, tools, and solutions, but you also have to have security engineers who work with other technology and business entities to create good processes, ensure security is baked into new solutions, policies are being enforced, and you definitely want an internal red team constantly probing and prodding the inside of the network, outside, as well as buildings and employees.
Security is done wrong when you’re that big, have 5 guys in an office and outsource all the things to other people. With that much at stake, you HAVE to take ownership of that knowledgebase.
Am I the only one that noticed there’s noone in the center, no computers visible (ok, could be running off VMs in a server farm with video over UTP, but still..), heck no monitors even on?
How hard would it be for Target to clear out an auditorium at Corporate, throw a couple desks together and monitors on them, and say “sure… we have a cyber fusion center… we’re TOTALLY secure now…”?
Looks to me like a picture taken before they opened up the center or staff it. No personal items on the desks or anything.
Great article, and not surprising what was discovered. And a precedent being set for action against the responsible party, per se, Target. A precedent that may be considered against possibly Anthem Blue Cross, even the OPM? The fallout of those breaches is enormously more damaging than the Target breach. We are having to deal with it personally on a daily basis, and the effort to placate us with an “after the fact” credit monitoring service isn’t worth a hill of beans.
Great article! Keep us informed!
Great article. Would love to see the same sort of report from the OMB breach, the IRS breaches, the DoE breaches, …
It is remarkable that Target seems to have failed to fulfill virtually every PCI DSS requirement, yet they (allegedly) passed their PCI DSS validation just a few months before the breach.
The flaws seem so obvious that it is inconcievable that the company performing the PCI DSS failed to find them…
Hey Erik,
Are you able to provide any documentation or external sourcing for that claim that target passed their PCI DSS Validation just a few months before the breach? I’m not doubting you, just would really like to see that analysis or any other supporting info. Thanks. Feel free to message me privately through the site’s contact form. http://krebsonsecurity.com/about/
Trustwave was their QSA so it is not surprising. They are the industry leading PCI rubberstamper.
I seem to recall claims as well that Target had recently demonstrated compliance prior to the breach. I also recall much ballyhoo about having a super secure operations center and a scanning tool that was mostly turned off due to too many alarms. Unfortunately I don’t have the sources (part may have been KoS) and hopeIm not mixing in some aspects from the flurry of other breaches that happened in the aftermath.
“Despite the fact that we invested hundreds of millions of dollars in data security, had a robust system in place, and had recently been certified as PCI-compliant, the unfortunate reality is that we experienced a data breach,” spokeswoman Snyder emailed last week.
http://www.darkreading.com/attacks-and-breaches/will-target-face-ftc-probe/d/d-id/1127824
http://www.darkreading.com/risk/compliance/target-pci-auditor-trustwave-sued-by-banks/d/d-id/1127936
“Target was [PCI] certified…in September 2013.
per Gregg Steinhafel Chairman President & CEO
http://www.technewsworld.com/story/80160.html
Jonathan @nc3.mobi
TARGETS PCI compliance date was publicly reported at the time. It was also reported that they spent 9 months out of the year, every year, to get their record of compliance.
Its common knowledge that the ROC is a point-in-time event that is out-of-date literally the moment its issued.
The only way most retailers can even hope to be issued a ROC is to have their QSA take much of their network out of scope. All this PCI nonsense does is raise awareness because only 25% of 10% networks are actually getting certified.
Well when TrustWave is your auditor, you don’t have to do much other than write the check. Not to mention, a PCI audit is a “point in time” audit, so you can be compliant today and non-compliance tomorrow.
It’s my understanding that PCI compliance doesn’t require network segmentation (or didn’t at the time).
Network segmentation is NOT a PCI-DSS requirement. However, without proper network segmentation, the scope of the audit extends past systems that store, process, and/or transmit cardholder data and can significantly increase the time, complexity and cost of compliance (not to mention the security risks).
Let be clear about network segmentation. According to the PCI DSS 1.2 and later either your entire network is in scope, or you segment your network to decrease scope. The guidance has been that “segmentation” = “segregation”. In other words to implement network segmentation, the PCI network has to be completely segregated, this includes authentication, which to be managed from the core network then requires 2FA. It also means that it has separate management systems, patching systems, et cetera. It in no way can co-exist with your core/non-PCI network.
Again, not required, but if you do network segmentation then it has to be 100%
The bit where you go into defining segmentation – that doesn’t exist in PCI (at least it didn’t when I was a QSA, or when this breach occurred). From my experience, there is no agreed upon definition for segmentation or where the line should be drawn. Almost ever QSA & ROC I’ve seen was happy with firewalls between the cardholder segment and the rest of the network, as long as those firewalls had *something* other than ANY-ANY rulesets.
The #1 most commonly misunderstood thing about PCI is that it is strictly defined. To do so would assume that the same configurations and rules work for everyone, so they made PCI somewhat vague and open to interpretation. This is generally a good thing, IF you can guarantee a good QSA. Unfortunately, a lot of QSAs have no technical background whatsoever, which results in ROCs being issued where they have no business being issued. It wouldn’t surprise me if that was the case here.
The bottom line is that PCI doesn’t work without qualified QSAs, and the demand for QSAs far outstrips availability, and that assumes qualified individuals would be willing to do QSA work long term. It is tough work to do long term.
The PCI certs we’ve done as a small online retailer are a complete joke. A self-assessment survey in which the answer to every question is ‘yes’, and a vulnerability scan during which we just turn off daemons that we know will trigger an exception for ten minutes and…miracle!…we’re compliant for another quarter.
Let me get this straight?
As a small retailer, are you being forced by your bank to have a conversation with an entity such as Trustwave who tells you that your answer can’t be “No”?
Prime example: My ex-husband owns a taxi business and has a single card-swipe device; and his bank requires him to have the annual “check-box” discussion with Trustwave.
It’s honestly disturbing. They are making money off of NOTHING.
“Let’s call some small merchants once a year who we’ve contracted with through their acquiring banks, ask a few questions & “Boom! Poof! Everyone is compliant!” It’s Magick!” 😉
If and when entities impacted by the necessity to maintain PCI Compliance encounter situations which seem unethical, these events should be reported to the applicable card brands and the PCI SSC. Things can’t change without people using their voices to share their experiences.
All those certifications merely ensure that they have the proper policies in place. I’m absolutely certain Target’s policies were impeccable– they just didn’t _follow_ them, because those constraints are annoying, and patching is extra work, and nobody wants to pay for it or do it unless forced.
That’s security in a nutshell right there.
Gorgeous NOC, but “cyber fusion teams” and all that jazz are BS. Target needed to patch. Plain and simple. Staying current is a ton of work, and they simply didn’t do it.
Well yeah, they definitely should have segmented their network too. That’s actually crazy!
Great reporting again. What amazes me about this and other attacks is how often the same mistakes are repeated over and over again with seemingly no one taking security issues seriously until it happens to them and hits Krebs on Security. Once this happens, as in this case, hundreds of millions of dollars are made available. In my last job, even thousands of dollars were hard to get, yet simple firewall rules blocked all but required access to branch POS machines and tools, such as Netflow, allowed suspicious network activity to be detected and analyzed, hopefully before the bad guys got in.
I can’t help feeling that all this was network security 101 clear back to 2001, when I took some of my classes in CCNA and MSCE. However, even A+ set the standard above what Target was practicing! Good grief!
What they are doing now is no different than what we started doing, way back in 2003, in our non profit organizational network security; so all this Target activity looks so amateur to me! We had to comply with HIPAA standards, and we also trained our staff to recognize best practices, and at least give them an introductory exposure to not only network security, but also interpersonal security to avoid any possible social engineering that may come into play. Other than the new tech, this all looks like the same old game to me. :\
I don’t care what the PR says about security. They are going to have a continued mess over there for quite some time. Sure the breach per se wasn’t directly their fault – this time. But if you have lax security skills built into a system and strip down a network – what’s left?
Its the people who have been trained to ignore those rules. The mindset is simply – Hey, target had a breach. A few higher ups lost their jobs. Most of the regular people are still employed. All is ok, the staff will still keep doing what their doing and truly not take any changes to heart.
The layout of that cyber room is an epic fail as well. Its too open, too many people can see what others are doing in respects to shoulder surfing. Different jobs need segregation, to some degree. There is a lot of wasted space in that photo. I am truly not impressed.
If I were them, they have a target on their back already. To stand their boldly and say, after a major security fail – we’re going to be a leader in cyber security – is a challenge to every hacker out there.
I see them having tons of phishing emails, social engineering attacks and other things heading their way. They are a retailer, not a cyber security penthouse.
They can say they brought in all this talent, but surely, its not for the long haul. As talent leaves, the new pristine network will get rusty and holes will appear once again. Call it a hunch, but I somehow see them in the future being the laughing stock of retail sometime in the future.
Hey at least it does not appear to be staffed 🙂
I have one question specific to obtaining credit card swipe data. If Target had modern point-to-point encrypted (P2PE) card readers would the bad guys been able to get the credit card data?
Yes. That was easy. The good guys have to block 100% of the attempts to get credit card numbers. The bad guys only have to be successful once.
If I had said “No,” you could have come up with 10 scenarios where I was wrong. If I answer your question “Yes,” there’s no way for you to refute it.
Next question.
Dumb PR flack is dumb.
“Snyder said Target believes “that sharing accurate and actionable information – with consumers, policy makers, and even other companies and industries – will help make all of us safer and stronger,” she said in an emailed statement. “Sometimes that means providing information directly to consumers, other times that means sharing information about possible industry threats with other companies or through our participation in the Financial Services and Retail Information Sharing and Analysis Centers (ISACs), and sometimes that means working with law enforcement. What we don’t think it means is continuing to rehash a narrative that is nearly two years old.””
If they believed in sharing knowledge for the public good, they would have placed the Verizon report on their website with a statement that it was there for the benefit of others to learn from their mistakes and that this hard lesson learned brought Target to world class levels of security. The report will be part of the legal discovery process anyway (unless they try to bury it under legally privileged status (if it’s in the public domain it may well become admissible.)
Instead, dumb PR flack starts up the smoke generators and begins hand waving.
Hey, claiming they are now going to be the best in security worked for Heartland. Why not Target?
Sharing doesn’t mean publishing. With the new R-SAC, they can share and learn from WalMart, Sears, BestBuy, Costco, etc. Sharing in public would be foolish.
Great article, as always.
I found the picture of the Cyber Fusion Center interesting. It appears to be a bunch of desks with monitors – but no computer, docking stations, keyboards, etc.
That pic is hilarious. Maybe they have the laser keyboards that display the keyboards ont he desk and they use hand signaling for mouse controls??? ha.
I work in a “fish bowl” work place like this and it is terrible to say the least. Companies need to find an in between solution. Don’t stick IT in a closet but also don’t put them in a fish bowl. Would you put your CFO in a fish bow???
CFO’s inhabit C-suites in ivory towers, IT folks far from it. Fishbowls are ok if all inhabitants have similar levels of authority and responsibility.
I think they’re using IKEA9000 PCs – you know, the fake plastic equipment that office equipment supply companies place on their showroom desks…?
(Firstly, I chuckled several times at some of the statements made about the room design… Way to go, guys = Thanks for starting my Monday with some humor!)
Based upon what is described above as the findings from the Verizon investigation, it is abundantly clear that Target was not compliant at the time of the breach.
Whether or not Trustwave presented findings that mgmt ignored is neither here nor there because the QSA should have identified that the required controls were not in place and therefore should not have issued a compliant ROC.
What’s depicted is not some scenario where segmentation was in place and functioning as intended. It sounds as though segmentation was non-existent to protect the CDE, in a secured method. While segmentation is not required for PCI, the entire environment comes into the scope of any PCI DSS assessment when it is not present.
Being compliant certainly doesn’t mean that an entity is bullet-proof. Although, the risk of breach is significantly reduced when all of the PCI DSS controls are implemented compliantly.
IMHO, there is absolutely NO WAY that a proper pentest (BTW = required for PCI) would not have detected all of the password issues discussed.
If the pentest findings were to indicate such issues, the entity would be required to perform remediation and retesting would be required to continue until remediation tasks were validated as completed. Incidentally, the QSA is required to review both the internal and external pentest results as part of the PCI DSS assessment prior to issuing a ROC.
It seems that we are back to – How the hell did they get a ROC?
If they got certified in 2013, then it would have been under the PCI 2.0 framework. No pen testing or vulnerability scanning required.
You’re right though. It seems laughable that a halfway competent QSA would have issued a compliant ROC, based on what was revealed here.
From PCI DSS v1.1: “Perform penetration testing at least once a year and after any significant infrastructure or application upgrade”
Pen testing and vul. scanning have been in PCI DSS from the beginning. v3 just adds the requirement to follow a standard methodology when doing it. The refinements and interpretation have helped but if you were meeting the actual “intent” of the requirement not just the wording you probably didn’t need to change much from the process…. of course discovering the vulnerabilities and getting someone to fix them are two different things.
…except that we don’t know how the room is actually used. I agree that day-to-day SOC and related work would be difficult in that room. There’s no indication (other than its cleanliness) that this is or isn’t anyone’s daily workspace.
But as a situation room, where you need ad hoc, cross-functional teams YET being able to have lots of people on the same page, it might work quite well. (There do seem to be separate rooms in the distant background.)
It looked like a marketing picture to me as well, though this could be a cold site or a new site which hasn’t been completed
Was thinking same thing. Stockphoto type thing going on. Picture was taken days before occupancy of actual workers. This was prob some kind of press photo. Also don’t want one of those “fail” photos where someone writes the wireless password on the whiteboard in the background type thing. So just remove everything you can.
Irrespective of functionality, I think the visitor cushions on top of the filing cabinets are a thoughtful tough that adds exactly the right bit of color to the room (also give a nice relaxed collegial vibe.)
Or they are using laptops. If you take a photo of our office after hours, they only be a few keyboards if any.
It was pretty empty as it was early in the (long) day of moving them into the space. Also, many of them do use laptops so only their monitors remain when they’re gone.
When the photographer and PR person arrived, several of the big monitors was running a cycle of info screens including network health reports, and the cell phone numbers of all the security team.
I suggested that maybe they didn’t want that info to be captured by somebody’s camera, even if they were a Target employee (and may not have been). They should not have had it up just because contractors were in there. One of the techs quickly threw together that PowerPoint slide to toss up on all the screens for the photo.
Thanks for the update! It seems that apathy in regard to their security risks were the petard by which Target was hoisted. I have seen it many times, scanners finding critical issues but management doesn’t give Security the resources to mitigate as they have other priorities.
That being said, Security cannot be left off the hook completely. Their defense in depth was pathetic. No network segregation, no password policy enforcement, no vulnerability management. A nice crunchy shell with a chewy center! Yum!
If anything valuable came of this breach, it was the wake up call that many companies heard loudly and clearly! Pay now or pay later!
Passing PCI compliance certification with all of its current 400 controls is NO guarantee of security and most of us already know that. PCI-DSS compliance framework is over 10 years old where it had originally 289 controls. That is where the fundamental weakness resides with any security framework being ISO, NIST, SAS or PCI, a metric in a point of time does not predict anything and does not assure your safe. If a organized crime syndicate, or state sponsored adversary wants to get in they will by continually probing for weaknesses both physical and technological means.
Exactly, and if OPM were following NIST would the hack have taken place or would there just be a zero-day vulnerability to blame.
Sure practice good security but never think you are safe due to check-box compliance.
Bad men need nothing more to compass their ends, than good men should look on and do nothing – John Stuart Mill
Also important to note, that if they got certified in 2013, that they probably rushed to get their PCI 2.0 certification in under the wire, which would have avoided some of the stricter requirements of PCI 3.0 (notably the vulnerability scanning and penetration testing requirements, which may have at least had some change of catching some of the issues).
I can’t help but think that this is going to be a huge black eye for Target’s QSA at least, and maybe for the industry in general.
Nothing I ever see with these breaches:
Was pen testing performed? Where is the record of that?
Was management notified of results? If so, who was and what were they briefed on? Did management formally and consciously make the decision to accept the risks they were informed of? Did Security staff notify management of risks? Did management for political or lack of understanding the risks decide not patch or fix them?
Too often and I almost bet in most of the major breaches, the above is never discussed in that management was notified and for whatever reason chose not implement the fixes, usually it based on convenience for higher management or so the business can continue to function without maintenance downtime.
There is an underlying issue as several pointed out. How did their PCI certification get issued with all the issues that were found? I bet because the Finance and/or IT department, CIO/CTO paid for the services to get the certification, saw a report of serious risk and issues, and decided to bury them so more money would not have to be spent to mitigate the risks and so their political survivability remained intact for the moment.
Exceptions to policy are far to often the “policy” these days. Especially when it comes to VIP/Executive elitists creating themselves exceptions and exceptions for anybody or anything that may shed light on their shortcomings as a leader. The IT Security and technical staffs then suffer the blame. Too bad we will never see the all the evidence leading up to the this or any major breach.
Agreed. If I never heard the word “exception” again for the rest of my life it would not be too soon!
There ARE no “exceptions”.
You are either COMPLIANT or you are NOT. It’s simple.
This concept is black & white, whereas the Standard itself has accurately been referred to many, many times as “the many shades of gray…” (that was long before the movie about shades of gray “stuff”…).
If you can’t change things for valid reasons but have plans in place to: let’s say, retire antiquated technology… Great! Document them and have hard timelines.
Meanwhile…
Guess what? To be truly compliant doesn’t mean a “project plan”. That’s why there is the option and necessity to implement a compensating control when the intent of the original requirement of sub-requirement is not met, which many assessors seem to be out-right afraid to use.
I’m guessing that they don’t want to document the not-in-place controls as a result of somehow raising “suspicion”.
The real deal is that it’s better to document things accurately and implement additional security controls as needed rather than write up some fiction in a ROC.
Take that for what it is…~!!
> There ARE no “exceptions”.
Sure there are. In PCI-speak they are called “Compensating controls” and they are used to avoid doing the hard work.
And the Elephant In The Room is:
Target had in-store pharmacies. If a deli scale could compromise the register network, does anybody think the patient and health records of the in-store pharmacies were miraculously untouched?
Has the OCR dug into HIPAA/HITECH violations because of this breach?
IIRC Target pharmacies are run by CVS and are independent entities. That said, I am sure there was the potential to breach medical data, but that isn’t what they were after, and there is no indications that any was compromised. Medical data doesn’t have a lot of value on the black market.
The partnership with CVS was just announced this summer, and the transition has not yet happened.
Oh yeah, it does. Medical fraud via identity theft is a major problem. Getting medical care on someone else’s dime via a forged identity card.
My point was that the OCR HIPAA fines are truly massive, not this chicken stuff that the FTC and others hand down.
As a reformed red teamer I’m shocked to see the plain text passwords from this pentest in this story. An organization as big as target will need some time to discover and change all the places those passwords exist. I speak from experience. I’ve penetrated organizations that were much more secure and would find remnants of a bad old default password multiple years in a row. I bet target isn’t too happy to see these published here.
Shocked? Really?
We’re now 20 some months after the breach. You don’t think that’s long enough to change passwords?
Brian, I must say that security common sense is like a deodorant, people who need it the most never use it..
Believe this report was released internally at Target over a year ago. If they didn’t mandate (and confirm) password changes when it first came out, that’d be another failure on Target’s part.
As a red teamer myself I am not the least surprised. Look at Sony, huge corporation and did the same thing. I have a lot of clients that use excel sheets. Its just insanity, no one cares.
A very nice picture of the new security center, including a lockable file cabinet in the foreground with what appears to be a key in the lock.
HA! Plus 1 to you Greg S! 😀
I wonder in they have any metrics in place to evaluate their problem identification and response times, how long problems go undetected, etc.
To an earlier comment, it’s not just the amount of money you throw at a problem, it whether it’s spent wisely (most “bang for the buck”).
Also, Target should take a look at Dr. Peter Sandman’s “Principles of Outrage Management”. Sharing truthful information with victims earlier helps offset the level of victim outrage.
Target brought in a lot of talent post breach , including top CIO Bob DeRhodes
( First Data , Home Depot , Delta airlines , Citi) and his team. Unfortunately , the talent left before completing their mission. Obviously the C-suites have historically neglected the security of their data and their networks. There continues to be a conflict of interest found between harvesting customer data and securing customer data. We have been preaching the limitations of silo’d data for over a decade now on the business side. On the security side , it is becoming increasingly apparent that silo’d data may be imperative to truly securing the interest of the customer. This is a monumental paradigm shift tantamount to turning around an aircraft carrier in a bathtub! Speaking to the PCI certification. Not all PCI providers are equal in scope and competence. Trustwave is the 1000 lb gorilla in the industry however , their effectiveness will still be limited by the customers commitment to security. In all honesty , true security is a fallacy as it stands today. Do your best , insure the rest.
Home Depot? Really? The firm that hired amateur criminals to do security? How about instead of hiring the CIO of the month, they have a highly tenured person with the internal pull to get the job done.
This data breach is a great case study demonstrating that (PCI) compliance does not automatically mean your digital assets are secure. It also shows how bad it can get when IT management routinely prioritizes the productivity of technicians far above the need for them to consistently practice basic security hygiene in their daily work. It’s entirely appropriate that Boards of Directors are requiring their management teams to do better than this.
And the security folks know this, it is when management doesn’t know it that there is a problem. We routinely face the issue of not being able to get funding if it isn’t a PCI related requirement, because management struggles to see the value.
That said, this hack could have been easily prevented with proper network segmentation with 2 factor authentication to reach the POS network, and application whitelisting on the POS devices. Short of implementing end to end encryption (which is very costly) this is the best way to secure your retail environment – it amazes me that so few do so.
I agree, to get funding we often need to get an auditor to tell management something is wrong or point it out to the Assessor so they can write it up and then you can get it funded.
> this hack could have been easily prevented with … with 2 factor authentication to reach the POS network,
Probably if they just had 2FA for all their suppliers they could have prevented the breach for a few $k.
I recall Verizon mentioned on their DBIR webcast that almost every breach they investigated started with a Citrix, OWA or some other external access that didn’t use two factor authentication compromising credentials. Once you can get into a network and start looking around then all the vulnerabilities and bad practice becomes an issue.
It’s hard to get signoff on 2FA for external access, management and pain in the ass usually shuts that down, but you don’t even need to worry about that if you segment right. Hack your way, or steal credentials to my network, know how much I care? 0. Because there are only 2 entry points to our POS network, both require 2FA, both only have RDP accessible, so there is no exploit vector – no 2FA token, no access to the POS side of the network. We can let vendors do as they please and it really doesnt matter. That’s not to say I don’t care about the security of my corporate network, but I can go home and sleep easy knowing that the security of my corporate network doesn’t really matter as far as a credit breach is concerned. And it’s only slightly more work to have to do all admin from those 2 entry points.
Did not see any comments of improving security relationships with third,parties……
Cyber Security is not only about external threats, It’s also about internal threats intentional and unintentional. I hope they implemented a robust Information Security Awareness Training Program. The users of a company can be a potential threat – likewise they can be a valued asset. Alert employees can spot the beginnings of an intrusion. For instance, if a password suddenly changed or unknown accounts suddenly appear.
Nice article. Great to see target turn things around from a security stand-point and to pro-actively monitor for security threats (and patch against them).Kudos to them.
So in other words… better password management, isolate your networks, and actually take heed to the vulnerability scanner. wow. and i bet most American businesses have even worse security management then target did… its basically a free for all, at least target detected a problem….lol
But we can’t be surprised, even in the linux community the so called security professionals don’t take defensive programs like tiger auditing seriously anymore, and its been deprecated for 8 years. ( like most defensive monitoring tools)
Pen testers can be helpful, but unless they are always coming up with 0 days i don’t see the usefulness if target actually did remediate the vulnerability issues found with their scanner. I think part of the problem is cyber security has nothing to do with defensive measures anymore and seems to only be about offensive penetration which is more exciting. There needs to be a balance especially since defense is needed more then ever now.
I always say, I don’t blame the more advanced systems that we have nowadays, compared to the 95-2005 decade, for the crisis we are in now. I don’t see systems of today as that much more complicated, but what I do blame is the mentality of the cyber communities nowadays who find offensive hacking more fun, who think they are entitled to break in simply because they can, and who just want to ensure jobs and preach against security measures they deem “trivial” or not part of a systems “threat model”. These things make me cringe and imo they are not the good guys. They are the problem. We will always have bugs till the end of time. What we really need to do is not have developers think of security as an afterthought, and we need to mirror the morals ane sense of right and wrong we have in the physical realm to the digital realm. We need education. We have really lost our sense of ethics, our sense of priorities, and that defensive balance needed for realistic long term security.
IMO, the target issue is a result of a failed cyber philosophy that needs to change, because we are becoming our own worst enemy.
+1
I find it laughable whenever I see any report involving Verizon’s “security teams” advising any company when their own company continues to store their FiOS customers router wifi passprases on their servers. Do their security teams audit/pentest their own in-house servers? Then why are they keeping my wifi passphrase (which should NEVER be anywhere other than within the router) stored on their account website? I did not give them permission to store my credentials from my router; Yes it’s mine, I bought it from them. I don’t care that ‘it’s their network’, this practice is unacceptable..I even contacted Stephen Northcutt of the SANS.org institute and even he was shocked.
http://jmikola.net/blog/fios-actiontec/
Shoot if you let Windows 10 configure your accounts for you, all your wifi passwords and those of your contacts gets stored together in the Redmond “cloud”. It is incredible that it seems the whole world sees this fornication as acceptable.
Maybe it is just a Facebook millennial mind set!? Wow! When I think back to “Peace – Love – Dove – and rock and roll” of the baby boomer generation, I guess this shouldn’t be surprising!
I guess Snowden didn’t have as much of an impact as I thought. So sad…..I don’t run Windows at home and refuse to intall 10 at work just for those reasons (and these)
http://arstechnica.com/information-technology/2015/08/even-when-told-not-to-windows-10-just-cant-stop-talking-to-microsoft/
They then proceeded to push these “updates” for 7 and 8 users; had to go around uninstalling four of them from all the pc’s in my building. Not fun.
Router (admin) passwords are a bit more serious than just getting on to wifi.
Well to be fair, unlike most companies, they generate a random password for each router device. There is no default passwords. And I don’t believe they store them.
But what is indeed hypocritical, is that they have a backdoor port into their routers, that they prevent the user from closing with their firmware. And that is probably the credentials you are referring to. The bigger problem is that almost every isp is doing that now. They also try to prevent the user from turning off UPNP and IGMP by hiding the pages in their firmware. So I agree their users are very vulnerable.
To get rid of their router is not easy if you want to use their special dvr protocol without also replacing the tv boxes.
It’s pretty much no brainer to segment the networks. And put as many layers as possible to the sensitive portion of the network.
I remember doing this in early days of net. And were far along now.
Why wouldn’t a major company follow standard security procedure as this?
Can’t trust anyone these days.
“It’s too hard!”
“It’s too expensive!”
“It’s on our priority list.”
“Good idea but not now.”
“I read that firewalls are obsolete.”
“What’s the value to the business?”
“Should we do that or something better?”
“You security people always want more firewalls.”
“The developers say it won’t work with their apps.”
“If it was a good idea we would have done it already.”
That was a great read, you have provided the best analysis of the target breach by far. Keep up the good work!
Maybe that room is for the 1000 IT personal Target said they will be hiring (back?). Turns out the 1000 they outsourced overseas a few months ago didn’t really work out so great. I would have considered working for Target before the breach, but after this they can forget it. They are going to have to fork over some dough for personnel now.
In my opinion the PCI framework is subject to too much interpretation and you can satisfy the requirements by implementation of quasi policies and procedures. I don’t blame them, but in most cases interpretation is the business side primary strategy for passing the audit and not the idea of trying to protect cardholder data.
Interpretation was most likely, at the time, a big reason Target passed their PCI audit.
“Paper” (policies and procedures) alone does not equate to compliance. While specific documentation is required as part of the Standard, the assessor is expected to collect evidence which validates that the required controls are in place, functioning as intended, and in a manner which is consistent with the documented policies and procedures. Testing must occur with evidence appropriately collected and stored to meet the retention requirements defined by the Council.
It should be noted that while some requirements are subject to interpretation, items such as changing default passwords and enforcing password policies are pretty straight-forward. Not too much to interpret/misinterpret there…!
Do we know for certain now that Target didn’t require 2 factor authentication for vendors who VPN ? In the link to the February article on Fazio Mechanical there’s some discussion that Target was probably requiring it only for VPN access to their segmented card data environment. But it’s all speculation.
Segmenting the CDE became mandatory under PCI (Req 11.3.4) as 6/30/2015.
David,
Respectfully, you are incorrect that segmentation is required. It is not and it has never been.
If you look closely at 11.3.4, you will notice that the first word is “IF”.
What changed specifically beginning with v3.0 of PCI DSS with respect to penetration testing is the further definition of the expectation of where the testing should be performed from and that the testing should confirm that segmentation controls are functioning properly IF in use.
Expert Troll –
PCI Security Standards Council
April 2012 – January 2013 (10 months)
Dyana – I see that now but I think the PCI Council could make it clearer by stating it as “Penetration testing is a best practice for testing the segmented CDE network until June 30, 2015, after which Requirement 11.3.4 becomes a requirement”.
Can a Level 3 entity with a segmented CDE perform their own internal pen test to meet 11.3.4? It doesn’t say anywhere in 11.3.4 about engaging an ASV to do this work.
it seems as though not enforcing a password policy – or the current accepted password schema that is obsolete (yea I think we need to rethink this) until technology catches up with authentication.
Currently google two step authentication by sending an auth code to a predesignated SMS number that requires an additional step to login, but in this day and age people are to hurried to care.
education of the end user and a willingness to not give away their precious information is the key here
The problem is rarely that the company is not enforcing a password policy. Ask any user.
The problem is that the system administrators can easily bypass any policy restrictions unless a third-party tool is used to keep them in check. Or they can write password policies that only affect their activities, such as service account creation.
It’s that old “Who is watching the watchers?” thing once again. If you’re not actively monitoring and reporting on small items performed by administrators and DBAs, such as what accounts are getting put into what groups, which accounts just had their password set to “never expire”, etc., you are going to have an epic fail.
The most certain path to an epic security fail it to put the IT security group under the CIO, which is what breached companies usually do.
CIO’s generally want it done fast and 80% is good enough because “We’ll fix it after it goes live.” and they never do. A good enterprise risk manager would never let that type of organization exist.