T-Mobile disclosed last week that some 15 million customers had their Social Security numbers and other personal data stolen thanks to a breach at Experian, the largest of the big American consumer credit bureaus. But this actually wasn’t the first time that a hacking incident at Experian exposed sensitive T-Mobile customer data, and that previous breach may hold important clues about what went wrong more recently.
On Dec. 30, 2013, T-Mobile said it notified a “relatively small” number of customers that unauthorized access to a file stored on servers owned by Experian had exposed Social Security numbers and driver’s license numbers. The mobile provider identified the breached vendor as Decisioning Solutions, an identity-proofing and authentication company that was acquired by Experian in April 2013. We’ll revisit this acquisition in a few moments.
Over the past week, KrebsOnSecurity has interviewed a half-dozen security experts who said they recently left Experian to find more rewarding and less frustrating work at other corporations. Nearly all described Experian as a company fixated on acquiring companies in the data broker and analytics technology space, even as it has stymied efforts to improve security and accountability at the Costa Mesa, Calif. based firm.
Jasun Tate worked for a year until April 2014 as a chief information security officer delegate and risk consultant at Experian’s government services and e-marketing business units. Tate said he and several of his colleagues left last year after repeatedly running into problems getting buy-in or follow-up support for major projects to beef up security around Experian’s growing stable of companies handling sensitive consumer and government data.
“What the board of directors at Experian wanted security-wise and the security capabilities on the ground were two completely different things,” Tate said. “Senior leadership there said they were pursuing a very aggressive growth-by-acquisition campaign. The acquisition team would have a very strict protocol on how they assess whether a business may be viable to buy, but the subsequent integration of the business into our core security architecture was just a black box of magic in terms of how it was to be implemented. And I’m not saying successful magic at all.”
Another recent former security employee at Experian who agreed to talk on condition of anonymity said it was clear that the company’s board was not well-informed about the true state of security within the company’s various business units.
“When I was there, the board was very big on security and wanting to invest in it and make sure we were doing what we needed to do in order to avoid situations just like this,” the source said. “In my opinion, there’s no way the board was told the whole story, because if they had been then things wouldn’t be where they are are now. We wouldn’t be talking about this. Some things had to have been hidden or spun in a way to look positive somehow.”
BLACK BOX MAGIC
Not long after it acquired the above-mentioned Decisioning Solutions in April 2013, Experian folded the company into its Decision Analytics platform — a unit which provides credit and noncredit data, customer analytics and fraud detection to lenders, cable and satellite companies, telecommunications firms, third-party debt collectors, utilities and to state and federal government entities.
Within hours of the latest T-Mobile breach news hitting the wires, KrebsOnSecurity was contacted by an anonymous source who sent this author a Web link that, when clicked, opened up a support ticket within that Decision Analytics platform in the United Kingdom — with absolutely no authentication needed. That support ticket I viewed appears to have been filed by someone in an office cube at Experian’s data center in Costa Rica who was requesting hardware support for a component of the company’s Global Technology Services division.
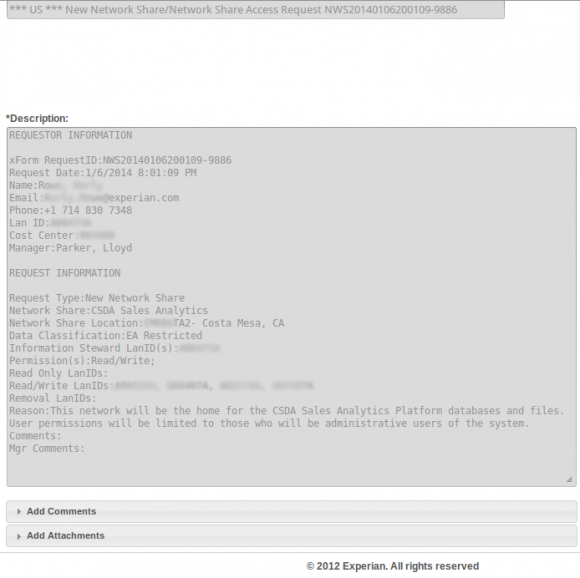
Countless internal support requests for access to Experian’s Decision Analytics credit information platform were exposed to the Internet without authentication until earlier this week.
That particular support ticket was relatively uninteresting, but according to my source anyone could view countless other support tickets filed via the support portal for Experian’s Decision Analytics platform.
The same source demonstrated how modifying just one or two numbers at the tail end of that link revealed requests for access to networked file shares from across a range of Experian’s business units. The requests included specific names of network shares, usernames, userIDs, and LanIDs, as well as email addresses, phone numbers of Experian personnel requesting and approving the changes.
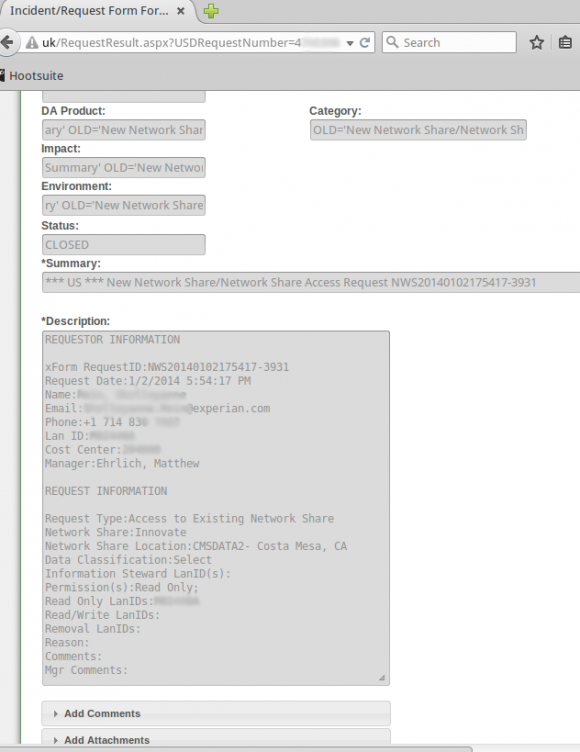
Countless internal support requests for access to Experian’s Decision Analytics credit information platform were exposed to the Internet without authentication until earlier this week.
The support site also apparently allowed anyone to file support tickets, potentially making it easy for clever attackers who’d studied the exposed support tickets to fabricate a request for access to Experian resources or accounts on the system.
In addition, experts I spoke with who examined the portal said the support site allowed anyone to upload arbitrary file attachments of virtually any file type. Those experts said such file upload capabilities are notoriously easy for attackers to use to inject malicious files into databases and other computing environments, and that having such capability out in the open without at least first requiring users to supply valid username and password credentials is asking for trouble.
KrebsOnSecurity sought comment from Experian to find out if it knew that its Decision Analytics support portal allowed anyone to view the tickets within. The company said in a statement that it had disabled the portal in response to what appeared to be unauthorized access to it and had notified law enforcement.
“We take any unauthorized access to our systems very seriously, and when we detected the unauthorized activities, we shut down the website and notified law enforcement,” the company said in a statement. “Our credit database and core infrastructure were not impacted – nor could they be accessed through this website. This site was a legacy version of a service to enable clients and internal users to create and log tickets for issues they may have and we had already deployed its replacement solution.”
ANOTHER ACQUISITION DISASTER
The two separate breaches of T-Mobile customer data that were caused by break-ins at Experian are dwarfed by the security disaster that ensued in the months following March 2012. That was the date Experian acquired Court Ventures, Inc., a company that aggregated, repackaged and sold public record data from more than 1,400 state and county sources.
“This acquisition strengthens Experian’s consumer data assets in North America and is a further step in Experian’s strategy to extend its global lead in credit information and analytics,” the company says on its Web site.
The only problem, experts say, was that Experian’s acquisition team neglected to do “due diligence” on Court Ventures’ existing customers to ensure that Experian was not inheriting legal or security problems that could haunt it down the road.
Unfortunately for Experian and countless Americans, hidden among Court Ventures’ customers was a human Trojan horse: A 22-year-old Vietnamese man named Hieu Minh Ngo was running an online service called Superget.info that catered to identity thieves, and he’d secretly gained access to Court Ventures and other data brokers by posing as a private investigator based in the United States.
Ngo’s business had attracted more than 1,000 paying customers, mainly identity thieves seeking to open new lines of credit in victims’ names, and/or to file phony tax refund requests in their names with the states and the Internal Revenue Service.
With the Experian acquisition of Court Ventures, Ngo’s customers had access to records on more than 200 million Americans, according to documents filed by U.S. prosecutors who successfully obtained a guilty plea and 13-year prison sentence for Ngo earlier this year.
Experian told Congress the oversight had not provably led to any harm for consumers. “There’s been no allegation that any harm has come, thankfully, in this scam,” said Tony Hadley, Experian’s senior vice president of government affairs and public policy, testifying in front of the Senate Commerce Committee in Dec. 2013. Meanwhile, investigators with the U.S. Secret Service and U.S. Justice Department have continued to arrest and prosecute many of Ngo’s customers for a variety of identity theft crimes, including new account fraud and tax refund fraud.
Experian also is now battling a class action lawsuit over Ngo’s identity theft service. In addition, several state attorneys general are reportedly investigating Experian over the Superget.info identity theft service that Ngo operated.
Now, in the days following revelations of a new breach at Experian involving the personal data on 15 million T-Mobile customers, lawmakers in the Senate are again demanding answers. The senators said the incident demonstrates the need for new legislation that addresses “both consumer notification and sets minimum security requirements for companies that collect and store such sensitive consumer data.”
In letters to T-Mobile CEO John Legere and Experian CEO Brian Cassin, the senators stated that the breach is “is extremely troubling to us given the sensitive nature of the compromised personal data, and its particular value to identity thieves,” especially with the exposure of social security numbers. The letter noted that according to the Department of Justice, 64 percent of the 17.6 million victims of identity theft in 2014 experienced a direct financial loss resulting from personal information fraud.
“This is particularly distressing based on your companies’ reported breach, because victims of personal information fraud lost an average of $7,761 compared to victims of bank or credit card fraud who lost an average of $780,” the lawmakers wrote. The remainder of their letter is here.
The credit bureau giant says consumers needn’t worry: The company is offering free credit monitoring for affected consumers through its ProtectMyID service, an highly profitable business unit of Experian (readers considering credit monitoring should read this article first).
GOOD LEADERS MATTER
Multiple former Experian security employees said that for years Experian seemed to be making great progress on establishing security as a core priority across the mammoth company. All interviewed directly attributed that progress to the leadership of then-chief information officer (CIO) John Finch, who helped hire and build up a staff of nearly 30 talented professionals to monitor Experian’s security “brain” — the “security operations center” or SOC for short. The SOC is designed to pull together real-time alerts about cyber attacks, as well as provide assessments about vulnerabilities across the organization’s far-flung computers and networks.
After Finch was lured away to take the CIO job at the Bank of England, many of the major in-progress projects designed to bake security into all aspects of Experian’s business ground to a halt, the former employees said on condition of anonymity. Core members of the Experian security team soon began seeking employment elsewhere. A year after Finch’s departure, morale suffered and the staff of the company’s SOC had dwindled from nearly 30 to about a dozen.
“I don’t have any ill will toward the company but what happened there was just a culmination of wrong decisions made outside of the security team’s control,” said one of Experian’s former security employees. “One of the challenges in security is being looked at as more than just an audit check box or the jerk that just wants to take the system down. But John saw security as an asset rather than a cost center, and a significant investment was made to grow security and mature the process. We got new tools, we got the architecture operating the way it should, and we began to get more collaboration from other teams which wasn’t there before.”
Finch could not be reached for comment. But the employee said after Finch’s departure, everything changed.
“We had a period of time there where security was viewed in a positive light, and things weren’t being swept under the rug for the sake of uptime.” the employee said. “He left and it kind of went the opposite direction. Once the leadership changed, the focus changed to controlling costs and not taking systems down for maintenance, and investments started disappearing from a lot of areas. We were in the middle of putting into operation certain tools to do next-generation detection of [cyber] threats, but we weren’t able to get many of them out into production. And that’s how Experian wound up where they are now.”
In a written statement provided to KrebsOnSecurity, Experian maintained that security remains a top priority for the company.
“Experian is committed to continuous investments in upgrading talent, processes, and technologies needed to protect our systems,” the statement reads. “Specifically, we made incremental investments of tens of millions of dollars in the last three years alone to strengthen our security positions. We employ over 200 highly skilled and experienced info sec professionals, and we supplement our own resources with leading third parties, as needed. As part of our continuous investment, we have increased the size of our security team over the last three years and upgraded our core competencies in information security.”





Time they quit pissing in the wind with statements and proved what state they’re in.
… Full spectrum audit from one of the big four.
Oh no, not one of the big four accounting firms as things could get worse. Experian might benefit and get a bigger tax haven. I know it’s all connected with computer code crime, efforts and money. Here’ a great documentary “The Tax Free Tour” that tells you exactly how big tax havens are primarily done by the big four.
http://ducknetweb.blogspot.com/2013/08/the-tax-free-tour-documentary-on-how.html
If it is all about security, then http://www.removemalwarevirus.com is the best place.
Well written indeed! Good mention again of the Superget.info identity theft case. Repackaging as you stated is happening out there with selling data. I harp on it constantly and said too that the Anthem folks should be aware who were breached as it’s the perfect storm and who knows how long they will wait and if they will repackage stolen data and make it look legit. One of the Anonymous guys told me there’s a ton of mathematicians and data wranglers on the dark side, not novices.
http://ducknetweb.blogspot.com/2015/02/anthem-data-breachcrooks-want-to-sell.html
My first thought about Experian’s, “customers shouldn’t worry” statement, that ProtectID would be provided free. What type of BS is that? The damage has been done. And the final statement that they have “committed to continuous investment” to improve their security, blah blah blah — I laugh. The evidence and reality speaks louder than their lip service. As for waiting, then repackaging and reselling personal data, they didn’t wait long here. I’d like to know a lot more about the Anthem breach, as many particulars as possible. And as a recipient of 3, yes 3, free credit monitoring ID theft prevention programs which have amounted to little value really, again, those programs are just a placebo, a token effort, to make you think they care. There, we offer you this, aren’t you happy we care? BUT! Brian, I love your articles, research, and connections! Keep it up!!!
It’s called PR: the biggest phoney profession out there next to lawyers.
That’s right. Back in 1991, Verizon New Jersey claimed it would make New
Jersey the first fully fiberized state with a plan called “Opportunity New
Jersey”. Customers paid Verizon about $15 billion dollars in excess phone
charges (and tax perks) to do this construction for over two decades, not to
mention additional rate increases along the way– and these increase have
been built into current rates for the last 2+ decades.
http://catless.ncl.ac.uk/Risks/27.80.html#subj6.1
Rates keep going up and service keeps going down. More complexity increases the number of failure points. You’ll be able to go to the poor house in an automobile and be short of breath and money getting there in your VW.
It KILLS me when a company gets hacked and then is like “We’re committed to securing blah blah blah crap” Its the same crap everytime. All these companies have people in leadership that don’t know what the hell they’re doing and are basically just stealing a paycheck every month.
Well written article and an interesting read.
I just don’t see anything here that I should alter my view of Experian as stated in a previous thread.
Is it possible that Finch wasn’t “lured away” as much as pushed out?
Pushed out? Perhaps not actively, but it wouldn’t surprise me if there had been a fall-out and alienation, regarding different mindsets between him and the execs.
It’s possible, but I doubt it. His new employer is bigger and more prestigious. That’s more of a standard ladder climbing thing.
Did John Finch leave to climb the ladder, or was he given a push? It’s not so black and white as that.
Undoubtedly he was using a lot of energy and social capital to advance and defend his security people and their initiatives. That’s what leaders do when they want to change organizational culture.
It was probably a tough job, especially if the company’s senior execs wanted to avoid talking about this kind of thing to the board of directors.
When a better and easier job came knocking, he was, no doubt, ready to say his genteel version of “take this job and shove it.”
So did Tony Hadley lie under oath, or was he inb4 the Secret Service et al began to find victims?
Was Brian the external accessant that caused the demise of now closed external portal? Regardless, if Experion already had a functional replacement up and running, it seems rather foolish that they didn’t sunset the old portal after the cut-over to the new one.
Thanks for another interesting read Brian.
Ps it would seem that Experian is interested in profit above all else as they moved their corporate domicile to Dublin although their ownership is in the UK and their biggest operational part is in the USA.
I contracted to Experian as a web developer for two years, at their North American HQ in Costa Mesa, and I can confirm, yes, pretty much the only thing they give a damn about is growth and revenue, otherwise they’d be more careful.
It’s ironic that the US Social Security Administration and the IRS use Experian to verify identity when creating an online account with either agency. So anyone who has access to Experian data can create a fake SSA or IRS online account.
It also makes setting a credit freeze on Experian problematic for anyone who needs to deal with SSA and IRS online.
So glad to see Congresscritters huffing and puffing about Experian allowing SSN and IRS data to be stolen.
When oh when will Congress get off its duff and update or eradicate the hopelessly insecure and outdated Social Security Number system? The Federal government needs to get its own house in order before it drags in others to account for their sins.
And what would it be replaced with? Your charge card number? Yeah, secure right. Remember congress made this number not to be used for anything except social security, and other smarter people said use it for everything. Because it was a secure number. Now every crook or computer user has it.
So, in theory does this mean that everyone in their system should be getting credit monitoring for free. Didn’t Ngo have access to all records. And they have info on, oh lets say… everyone. How is Experian deciding who gets”protected”? I think that in these cases the protection should be selected by the consumer. He/she should get to choose and the exposer pay that company.
No, while Ngo’s system had access to tens of millions of records, recall that he was still posing as a customer/buyer who had a “permissible use” to access that data. More to the point, he and his customers had to pay for each lookup, so, no, they didn’t look up all the records they had access to.
Although it was never alleged, I was always waiting for a 2nd shoe to drop there, namely that black hats had breached Ngo’s system and exfiltrated everything.
i love how experian always says 1. They didn’t access our credit files 2. No credit cards were exposed. If i have your dob and ssn, then accessing your precious credit file is child’s play because your challenge questions are a joke. The red herring that no credit cards were exposed is laughable. I would rather have my banks credit card # (it’s their money not mine) be exposed 100 times out of 100 as opposed to my dob and social etc. crazy that this company is allowed to be one of the Guardians of our information.
With the ticketing system, there was no need to directly access certain resources. Just anonymously file a ticket with all the information needed (and maybe even request credentials that would be validated, and thus you aren’t breaking into the system), and you can have others do all the work for you and get what you are requesting.
Ticketing systems are always one of the weakest links. In this case, it was really bad, but I do wonder how many times ticketing systems were leveraged to gain illicit access to some resource. “I have a ticket, so it must be valid. I need to get this done so I can keep up my metrics for ticket closure.”
Brian,
Another great article. I am a security professional who subscribes too and ***reads*** your article. A lot of things I only skim, but yours generally rate a closer inspection. Several really good lessons learned in here for companies, and the importance of leadership, bringing along the security professional team etc. Many will miss it in the race to cut costs this month but thanks for sharing. V
Most of the data at Experian is put in there without the persons knowledge. They make it very difficult to get your data removed from their systems. But even if you do get it removed, good luck getting something like a car loan.
That’s just the world we live in nowadays. If you get a pizza delivered, Domino’s will resell your name, number and current address at the drop of a hat.
Great article.
I must say, this is not unique. Thei higher ups typically in the security arena, are seen as a “drain”. They DONT bring in cash. They are an expense and the board and CEO usually sees them that way. (those that dont know better…a more technicaly educated CEO will understand the ramifications of this). From my experience, I have seen management down right lie or at best “pad the truth” to make things more palatable for the executives so they keep their bonuses etc. As spending massive money on security in most companies, is seen as a complete loss…it does nothing to improve the bottom line.
This is where problems start….CEOs and board are not truly in the “know” of the real issues….
A good security manager here, would lay it out and work with management explaining the huge liability and get legal on their side as well, making sure that the CEO and Board are not ignoring the elephant in the room.
AH! See that’s where, unfortunately, I think you are mistaken. In my many years of experience in cyber security management I was never allowed to be hooked in at the board level. I provided briefings and metrics continually to the CIO, COO, and CEO, but what got presented to the board was completely out of my control. I remember being told on more than one occasion how we could not use FUD with the board. Sadly, given all that’s happened over the past 5+ years it was and continues to be the truth. It’s only FUD when you don’t want to hear it. When it’s an inconvenient truth.
Yes, cyber security is an ‘expense’. But rather then frame it as an ‘expense’ I like to refer to it as an ‘insurance policy’. For example, do you have life insurance to cover you and your family? Is it enough? How do you know if it’s enough? That’s all that cyber security really is at the end of the day. Either you invest properly in it or you don’t. Pay the consequences accordingly.
In case you’re wondering, I don’t believe in all that “breach insurance” crap as a ‘compensating control’. What a load of audit garbage that is. I love reading articles about claims being denied by the insurance companies due to the claimant failing to do due diligence in securing their systems and data. It makes my day (in a sad way). For all those CEO’s, COO’s and CIO’s who chose not to invest in security, especially in today’s hostile world “Here’s yer sign!”
(Google that saying if you don’t understand).
Here’s a personal story that I hope makes my point. A few short years ago I was hired at a mid sized bank to help them shore up their cyber security (they didn’t really have any to speak of. Very sad…). They had just gotten slapped really, really hard by the feds for failing to do ‘due diligence’ on cyber security during their federal audit. Once the team and I finally finished building a real security program and an accompanying SOC, we had a very nice, consistent security program catching bad guys and defending the castle effectively and proactively.
The fed’s came back to re-audit the bank and BOOM, they gave us a glowing review on our cyber security program! Shortly thereafter the bank cut my position and several others in cyber security in order to ‘right size’ the organization. Sadly, you can’t get any dumber than that right there! All I can say is….
Here’s yer sign!
“Experian told Congress the oversight had not provably led to any harm for consumers.”
Provably? Do they think all thieves are stupid? The real damage could come years down the road, when they make use of the data they stole to commit their fraud.
And any smart thief would pick Experian’s pocket, not mug them, leaving little or no trace of data theft. I have to wonder how many breaches have taken place where the thieves left no trace that data was even stolen.
This comment to Congress was disingenuous at best.
Leadership is either naïve or deliberately ignoring the impact. In either case, the company needs new leadership from the top down.
Everyone at the C level should be replaced and a CSO put in place that has the power to say no to CEO and other officers (and board).
The security team should be in charge of all patching, change requests, and have the overriding authority to block any acquisition that does not pass muster after they have investigated the acquisition target.
I would allow that the security team be given the following battle plan:
1. Obtain any next gen security tools they can and get them implemented within the year (tuning and the like will require this kind of time frame)
2. Restaff the SoC with qualified personnel – staff it to cover 24/7/365
3. Establish a patching plan that includes at least a monthly downtime to allow for rebooting post patch
4. Hire an external pen and vuln testing company and perform monthly pen and vuln test. This may need to be weekly at first until all of the problems are addressed (I expect that their entire network is full of compromised systems, vulnerabilities and old systems (betting they have Windows XP on multiple machines))
5. Generate a weekly/monthly security report for the board and call out any C level or manager that does not comply with security steps
6. Create a comprehensive company policy around security and include stepped penalties for non-adherence. Non-adherence should include immediate termination penalties for some violations. Set a three strikes rule for non-critical policy violations – third strike is termination
This is by no means a comprehensive list, but is a good start.
At this point, no current management should be retained since they cannot be trusted to work to the basic rules set forth with PCI-DSS, PII, etc.
If I were in charge, I would have cleaned house after the first incident and I certainly would not have told Congress that no harm came to consumers.
I am wondering if there are some criminal charges that can be pursued for the CEO and other officers.
This friend speaks my words. Especially when it comes to ‘cleaning house’ after the first incident.
Which brings me to a question. Can the board of directors order a thorough house cleaning?
If I am on the board, I believe that I face personal financial exposure to this type of negligence and I would want to order a house cleaning and then bringing the SOC up to good capability and getting that external pen firm on board pronto.
Thank you!
Companies that are pursuing aggressive acquisition often do not plan ahead and apply resources to ensure a secure integration of IT systems. There is a rush to connect the new employees and systems; to “welcome” the acquired company. More mature acquirers use technologies such as virtual desktops, containers, VPN and secure portals to make sure the acquired company (often a startup with little security) is appropriately segmented from the corporate core network. However, that may create a less than optimal user experience. There is often pressure from the business to open up the firewalls and let the networks merge.
As a federal employee who has had my personal identifying information stolen three times this year; Anthem, OPM and Experian; I am exhausted! This week I got an email from OPM saying that my finger prints were stolen too. What idiot at OPM decided it was OK to string all personally identifiable information together. I am on an emotional roller coaster. I have developed what I would call a nervous disorder; I shred everything; I check my bank balance three times a day; I get annoyed when the server walks away with my credit card too long; I fire off letters to my Congressman or bank if something looks like there has been any accounting voodoo; I have become a nightmare! I think I might need medication. I have done credit freezes as you recommended. When I went to register on line for “my social security;” they said no can do because I had a credit freeze in place. How odd I thought, but now that I know that Social Security is in bed with Experian it makes sense. We are all in trouble! I have always thought the next act of terrorism will not be from the playbook we have grown accustomed to; but it will be the day every man and woman wakes up to find ALL of their money gone without a trace and then the Twilight Zone Episode where we kill each other off will begin. Time to stock up items for bartering. Grandma’s silver you turned your nose up to never looked so good. Krebs thank you for your incredible journalism; I have learned so much; I think your website should be required reading for everyone.
Have you looked any Facebook account that you may have? Are there clues about your mother’s maiden name (relatives on your friend list), the schools you have attended, places where you have lived, ….
@Rose, I can sympathize quite well. The same breaches, and the damage that follows. Regarding the SSA, if you can, go directly to an SSA office. We have our reports frozen at every bureau possible (more than just the big 4), and we were able to set up both SSA accounts while in the office, even though Experian was frozen. Then get 2 factor auth via a text for your cell. That will involve putting in the request from the now-active account, and then waiting for a letter from SSA, and then continuing with the directions given.
Should you have your ID actually used, NOW you will be busy. The professionals that are supposed to contact all the debtors, shut down the external fraudulent accounts, restore your credit, etc., well, sounds nice, but actually, the companies will only talk to the person whose ID it is. Then it relies upon YOU mailing in the copies of actual documents YOU need to produce, such as the proof of ID, police reports, notarized affidavits, and on and on. Be prepared to stock up on paper, ink, and lots of things to help you relax. You will need it.
I imagine that if one of the professionals is supposed to do this for you, then that’s another entity you trust will all your personal information, and more. I feel better handling it myself.
“Experian told Congress the oversight had not provably led to any harm for consumers.”
What an asinine statement……
I think what’s interesting here is the fact that T-Mobile is still aligned with Experian to run their credit reports after TWO breaches… This is concerning because there’s a reason why.
I mean, that’s a PR risk that could sink T-Mobile if consumers think that their information is not going to be protected, because people aren’t going to say that it’s Experian’s fault and not T-Mobile’s, we know how that works.
Once again I see demonstrated that the greatest talent in management is to hire highly skilled, knowledgeable individuals and then ignore their advice.
If you only knew how right you are.
Thanks for getting real, Jasun – down here with us and when talking with BK. You’re adding the reality back into an unreal situation.
No worries m8, those with a voice should speak up and those with the ability to enact change should do just that. Cyber Security (or lack there of) has become the Coup De Grace of the average citizens right to privacy. I dont proclaim to have all the answers but we do what we can when we can. Bitsdigits and ZainCommunications are all about just that. Raising awareness, Protecting Castles and developing solutions that are up to speed with the times we are in. Experian like other big ships have a monstrocity of a task, but at what cost?
I read this in a Security Newsletter over the weekend, and I found it amusing… T-Mobile is offering customers 2 years of free identity theft monitoring from… Experian!
SMH, haven’t even read the linked articles re: ProtectMyID service, but this already hits me in the face.
WRT ProtectMyID service, a “highly profitable business unit of Experian”, that’s akin to GE giving $50-150 coupons to consumers who need to go out and buy a new $500-800 dishwasher, because their original GE dishwasher could catch fire and burn down the house.
Those coupons should have been redeemable on dishwashers from competitors as well, lest GE be rewarded for their defect with an undeserved bump in sales of GE dishwashers.
Why should the company responsible for the defect, or breach, be enabled to profit from new business either directly or indirectly via the solution offered?
Most free credit monitoring leads to an enticement to be continued as a PAID service after the free interval expires. Rather than punish the perp, it rewards them with new opportunities for revenue.
Congress should require that any remediation of the risk or damage therefrom must in no way benefit the merchant guilty of a breach or manufacturing defect.
To me, it’s more like doctors who have left a patient in a horrendous, life-long condition through malpractice crowing about how they’ll provide part of the cost of a monthly massage.
Doing the math…
Experian boasts of “investments of tens of millions of dollars in the last three years” and still fails to protect the identities of at least 15 million consumers in just this latest breach.
Considering “according to the Department of Justice, 64 percent of the 17.6 million victims of identity theft in 2014 experienced a direct financial loss resulting from personal information fraud” and “victims of personal information fraud lost an average of $7,761”.
64% of 15 million is 9,600,000 and when you multiply that by 7,761, the potential cumulative cost to consumers is roughly $75 billion (spelled with a B). Perhaps Experian ought to be increase those “tens of millions of dollars” for lax security into the “hundreds of millions of dollars”, rather than wasting it on acquisitions which obviously serve to expose consumer data even more often.
Really?!?!?!
My family has a security freeze on our credit records with Experian and the other three consumer credit bureaus, but I’m wondering: might it be possible that Experian’s procedures are so compromised that a security freeze wouldn’t work? If so, what is the remedy?
Great article Brian but i would suggest you validate your sources….Tate was at Experian for about 3 months. And Mr Finch was actually fired from Experian.
After he outsourced all the development to India and moved Security Admin/Access Control offshore to Costa Rica to reduce costs. Think you must have some biased sources Brian.
Lovely team t-shirts you guys are wearing. Would look better without the nipple clamps, though. Just saying.
“Experian is committed to continuous investments in upgrading talent, processes, and technologies needed to protect our systems,” [nose grows] the statement reads. “Specifically, we made incremental investments of tens of millions of dollars in the last three years alone to strengthen our security positions. [nose 2ft long] We employ over 200 highly skilled and experienced info sec professionals, [nose 4ft long] and we supplement our own resources with leading third parties, as needed. [nose 8ft long] As part of our continuous investment, [nose 64ft long] we have increased the size of our security team [nose 128ft long] over the last three years [nose 256ft long] and upgraded our core competencies in information security.” [nose buffer overload]
[nose buffer overload]
should be:
[nose buffer overflow][arbitrary code execution][pwned][all records exfiltrated] [black TOR sales][another retirement penthouse courtesy of Experian]
It comes as no surprise that Experian scores an “F” on Qualys’ SSL Labs site (https://www.ssllabs.com/ssltest/analyze.html?d=www.experian.com) – for a vulnerability that was published almost a year ago (POODLE TLS).
This seems to be a pattern. Many of the companies that have been breached got an “F” from Qualys. Makes sense to me; if a scan that every internet user can run reveals failure it is likely that the situation on the back-end is even worse.
Of course companies tend to deny this. One of the largest ISPs/cable companies still maintains that Qualys is wrong about their score (F). Other companies have gone as far as mandating that Qualys no longer scans their sites.
Great security strategy!
The rating companies have been ducking regulation by the government for years. The idea was that if they kept their nose clean, the regulators would let them go on with business as usual. I think it is high time we slap some regulation on this industry, as they obviously don’t have the individual’s best interests at heart. I am one that usually doesn’t like expansion of big government, but this is definitely one area that is going to need attention; and victim’s rights need to be addressed and forced on the rating systems as well. Just because a crook took your good credit and trashed it, should not mean the victim should spend 10 years trying to run around cleaning it up by themselves. It is just getting ridiculous. Time to shut down the playground!
Private citizens and companies need protection against these clowns.
There should be legislation that enables an individual (at least) to require that all information held by an unworthy organisation is verifiably purged from their system (including all backups).
From the article it appears that these guys lucked out with somebody who took security seriously, but this was not a deliberate achievement of the organisation. They didn’t deserve him and they may have had no clue how important it was.
It’s time for me to once again rattle off some emails to members of Congress. All these dumb lawyers that think the verbiage alone can do a bit of regulation with data sellers are totally duped. We need to license and index all data sellers as step one. Pam over at the World Privacy Forum thought it was a great step to begin the process. Who are they? 3 years ago I started this informational campaign to get a law passed to do such and I still hound members of Congress about this.
http://www.youcaring.com/other/help-preserve-our-privacy-/258776
“Lobby group the Financial Services Roundtable (FSR) on Monday launched an
advertising campaign, stopcyberthreats.com, aimed at tackling an online
campaign by privacy activists who have dubbed Cisa `the Darth Vader bill’
and are worried by the sweeping legal immunity corporations will receive
under Cisa.”
“Credit check giant Experian said that the company would like to see the
legislation pass. “Experian supports legislation that would facilitate
greater sharing of cyberthreat information among appropriate private and
government entities,” said a company spokeswoman in a statement to the
Guardian. “Such sharing arrangements, under parameters set by law, could
improve our mutual efforts to better detect and respond to emerging cyber
threats.”
“The company also laid the duty to walk the knife’s edge between citizens’ information security and their personal safety at the feet of their elected
officials.”
Nothing has ever been successfully defended…there’s only attack, attack and more attack.
I think you need to double check your facts and sources regarding John Finch
All these “insiders” point to unhappy or biased former employees. Doesn’t change fact that Ngo sold millions of dobs and SSNs to identity thieves all around the world and was only stopped after secret service found out and told experian. Doesn’t change fact that they were fleeced of another 15m pieces of pii. This is a sloppy company that continues harm Americans thru their sheer incompetence and greed. Clearly they have a huge problem but sure…blame former employees.
No one is ignoring the actions of people like Ngo. The actions of Experian cant be ignored either. Ngo would have nothing to sell (or trade) without databases like those within Experian. Access to these databases have always been targets for blackhats and extortionists. As a civilization, we so proudly tout or technological advancement while simultaneously ignoring it’s dangers. An apathy has developed and grown around it’s shiny metal screens as we are all shown everything we want to see.
I am NOT to be treated like cattle. It makes no difference if it’s Ngo, Experian, Lulsec, The Church of Scientology, Apple, Microsoft, Sony, Chevrolet, Facebook, Coke, J.D. Power and Assoc., Comcast, AT&T, or even our so-called leaders of nations and captains of industry. Employees of these companies (and others) are NOT without some measure of responsibility to the human condition. Snowden felt this and acted as others have have.
We can simply accept having microphones and cameras watching our EVERY move or we can reject such blatant violations of human freedom. The ugliness that Experian represents is harmful to us all.