So you’ve got two-step authentication set up to harden the security of your email account (you do, right?). But when was the last time you took a good look at the security of your inbox’s recovery email address? That may well be the weakest link in your email security chain, as evidenced by the following tale of a IT professional who saw two of his linked email accounts recently hijacked in a bid to steal his Twitter identity.
 Earlier this week, I heard from Chris Blake, a longtime KrebsOnSecurity reader from the United Kingdom. Blake reached out because I’d recently written about a character of interest in the breach at British phone and broadband provider TalkTalk: an individual using the Twitter handle “@Fearful“.
Earlier this week, I heard from Chris Blake, a longtime KrebsOnSecurity reader from the United Kingdom. Blake reached out because I’d recently written about a character of interest in the breach at British phone and broadband provider TalkTalk: an individual using the Twitter handle “@Fearful“.
Blake proceeded to explain how that same Fearful account had belonged to him for some time until May 2015, when an elaborate social engineering attack on his Internet service provider (ISP) allowed the current occupant of the account to swipe it out from under him.
On May 11, Blake received a text message on his mobile stating that his Microsoft Outlook account password had been changed. A minute later, he got another text from Microsoft saying his two-factor authentication (texted login codes to his phone) had been removed. After that, he could no longer log in to his Outlook account because someone had changed his password and removed his recovery email address (changing it to a free and disposable yopmail.com account).
Minutes after that, someone tweeted out the message from his account: “This twitter account is officially operated by Elliott G.” The tweet prior to that one mentions Blake by name and is a response to an inquiry to the Microsoft Store before the account was taken. The alias on Blake’s @Fearful account was changed to “Glubz”.
Blake said it took some time to figure out how the miscreant had hijacked his Twitter and Outlook accounts. Turns out, the recovery email address that he’d supplied for his Outlook account was to an email address at his local ISP, and the attacker executed the first step in the hijack by tricking a customer service employee at the ISP into redirecting his messages.
The attacker, apparently another person with a British accent, called Blake’s ISP pretending to be Blake and said he was locked out of his inbox. Could the ISP please change the domain name system (DNS) settings on his domain and associated mail account?
According to Blake, an investigation into the incident at the ISP shows that the customer service rep asked the caller to verify any other email addresses associated with Blake’s ISP account, and after some waiting the support employee actually read off a few of them. Seconds later, the attacker sent an email to the support person that spoofed one of those email addresses. After that, Blake’s ISP complied with the request, changing the DNS settings on his account to settings that the caller supplied for an account at Namecheaphosting.com.
OG IS A THING
With all of the access to other accounts that one’s inbox affords, the attacker in this case could have done some serious damage and cost Blake a lot of money. So why was he only interested in Blake’s Twitter account?
Short usernames are something of a prestige or status symbol for many youngsters, and some are willing to pay surprising amounts of money for them. Known as “OG” (short for “original” and also “original gangster”) in certain circles online, these can be usernames for virtually any service, from email accounts at Webmail providers to social media services like Instagram, Snapchat, Twitter and Youtube. People who traffic in OG accounts prize them because they can make the account holder appear to have been a savvy, early adopter of the service before it became popular and before all of the short usernames were taken.
“I didn’t realize this was even a thing until all this happened,” Blake said of the demand for OG accounts. “It wasn’t until the day after my email accounts were hacked that I realized it was really my Twitter account he was after.”
As it happens, the guy who is currently squatting on Blake’s @Fearful Twitter account — a young wanna-be hacker who uses the nickname “Glubz” — is very publicly in the business of selling hijacked OG accounts. In the screen shot below, we can see Glubz on the script kiddie-friendly online community Hackforums promoting his “OG Store,” in which he sells “Snapchats,” Email accounts and “Youtubes” for $10-$40 apiece, payable via Bitcoin or PayPal. The bottom of the message includes a link to Glubz’s personal site — elliottg[dot]net (also hosted at Namecheaphosting.com).
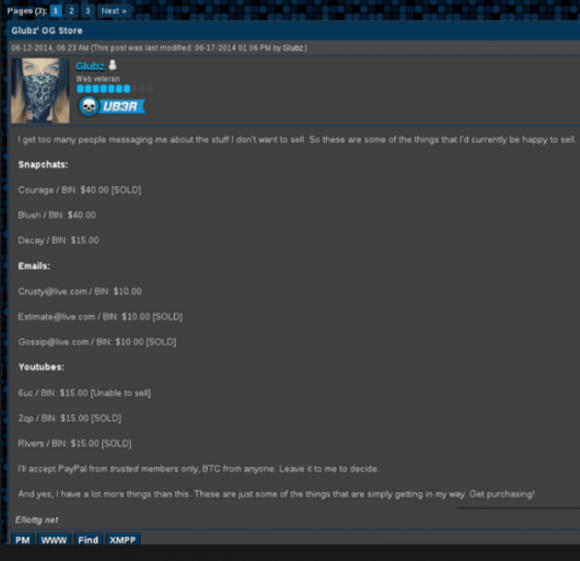
Glubz on Hackforums selling “OG,” hacked accounts with short usernames at popular social networking sites.
Here’s Glubz on another script-kiddie friendly forum (Forumkorner) responding to one of dozens of requests from other members to offer his best appraisal of the market price for various hijacked OG accounts.
WHO IS GLUBZ?
Blake said it took him all of about five minutes to find who and where his virtual mugger lived. Turned out that the kid wasn’t far from Blake — in a U.K. town just a few dozen kilometers away.
Searching Google for “Glubz” brings up an Instagram and Snapchat account by the same name. Most of the pics that were until recently on Glubz’s Instagram are stock photos, but a couple of them appear to be taken from a mobile phone. Happily, the same photos are archived here. One of them shows what looks like the front yard and street in front of Glubz’s home as seen through his window shades.
Glubz’s own personal OG Youtube account is, naturally, just “Ty,” (no doubt hijacked as well). In one of his tutorials on how to “hack” stuff, Glubz explains a trick he learned for determining the country in which any given Yahoo! email account was created. In his video, Glubz steps through the reset-password process for one of his accounts — glubzmain@yahoo.com — which shows that the last two digits of his mobile phone are “19.”
Glubz also had an entry at the now-defunct skidpaste.org, a site which sought to document the known aliases, addresses and other contact information on young script kids (hence “skid”) who fancy themselves much better hackers than they really are. That entry pegged Glubz as one 16-year-old Elliott Gunton of Norwich, U.K. Sure enough, the Skidpaste entry shows a mobile number for Gunton that ends in “19.” Pull the Google Street View listing for the Norwich address in Glubz’s Skidpaste entry, and one can see the street pictured in Glubz’s Instagram photo.
On Tuesday, London police said they had arrested a fourth individual in connection with the TalkTalk hack — a 16-year-old boy from Norwich. Reached via direct message on Twitter, Glubz (@Fearful) was evasive and would neither confirm nor deny being arrested. Meanwhile, Fearful’s Twitter “favorites” page is a mix of jail jeers and tweets from people wishing him well for getting out on bail.
Back to the beginning of this post: Take a minute to check out and think through the security of your inbox. If you’re not sure whether your provider offers two-step authentication, have a look at TwoFactorAuth.org.
But just as importantly, consider putting in place the same protections on the email account that you use as your recovery email address. If your recovery email address is an account given to you by your ISP, consider perhaps changing it to a service that offers two-step authentication and that may not be so easy to get on the phone. I am speaking from experience here, as someone who had his own inbox compromised because of a social engineering call to his own ISP.
Update 12:51 p.m. ET: As others have mentioned in the comments here, it’s not for nothing that a social engineering attack against Blake’s ISP recalls the recent alleged hack of CIA Director John Brennan’s inbox. In that incident, the attackers called Verizon to reset Brennan’s password. Wired.com breaks down how that attack succeeded.



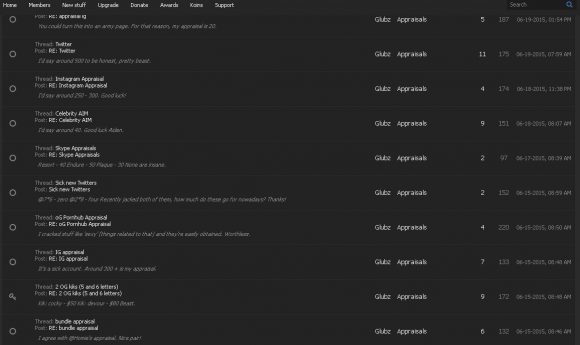

Seems like a lot of work to be selling a single ID for $15.
This was a good article, reminds me I should check out my own inbox security.
I don’t know if it isn’t worth it. Assuming a reasonably incompetent ISP support rep, you could probably do four an hour. And some of them are more than $15.
It’s no millionaire-maker, but if you’ve got a list of targets and a little time, you could make a few bucks pretty easily.
(It would be even faster if you have a REALLY incompetent support rep and/or one who doesn’t care. There’s one ISP in my town who, as long as they know it’s my business on the other end of the line, will just read you an email account’s password off their list, over the phone. So if you can pretend to be me, you’re in.)
My ISP (Plusnet) makes customers queue for at least 30 minutes before answering any phone calls. So I think that nobody is going to bother wasting all that time for little reward.
Poor service as a security measure!
That explains a lot of ISPs I guess.
I am an active member of this “OG” market and the Twitter name @fearful is worth a lot more than $15. While there’s a lot of garbage he was selling for $10-$15, those were just some worthless Snapchats and emails. But Twitter usernames go for a lot more than stuff like Snapchat usernames, because they have a higher demand. Not to mention the fact that “Fearful” is a good alias. That username is worth an upwards of $400. Yes, I know, it sounds crazy and unrealistic that someone would pay that much, but you’d be surprised. People will do anything for a big e-penis.
@Brian thanks for the timely reminder to protect seemingly unrelated systems.
Upon reflection, I have control of an interesting twitter handle (6-characters, simple, single word), and this reminded me to enable 2-factor authentication on the entire authorisation chain.
Well $15 would be the price for an email. A Twitter handle like that goes for about $100-150
Some twitters are worth over $500 and can be taken in less than 30minutes. Not exactly Chump change.
Very good advise.
twostepauth.org does not appear to resolve. Are you sure you don’t mean twofactorauth.org?
Second that!
Third that. Brian, update your link to https://twofactorauth.org/
Gah! No freaking idea how that happened. Fixed. Thanks.
I’d like to get some feedback on how my email is set up. What I did about 6 years ago was to combat spam, but it may also be protecting me from hacking as was described here.
What I did was delete my POP3 account for my main email address at my business domain. I then created a new POP3 account with an address that is unguessable and never published – that’s right, I never use my true email address. Then I turned my old email address into an email forward that goes to my real email address.
This was part of my anti-spam system that involves creating new email forwards when I have to register a site for something. I create a forward that clearly shows who I am giving the email address to and I forward that to my real address. If I should get spam at some point, I instantly know how a spammer got it. And the best part is that all I need to do is delete the forward and the spam stops.
I think this will protect me a little more than average since a social hack will seem strange if someone wants a password reset for an email forward. 🙂
Check the Properties/Internet headers of your rerouted Email. It may show your proper Email.
However thieves are lazy and unless they really want you that may never get looked at.
I do something similar. I have a ton of (formerly) free Google-registered domains. I set up an alias for every company I do business with in the Google Apps control panel and never give out my real email.
When I start getting spam (or worse) at one of the cutout email addresses, I just delete the alias and set up a new one.
ebay seems especially susceptible – in seven years, that address has been compromised three times.
Why aren’t you just using catch-all to receive at any address without needing to set it up first?
Catchalls are not as great as you think they are.
Enjoy the day that some spammer decides to dictionary attack you.
a@catchall.com
aa@catchall.com
aaa@catchall.com
b…..@catchall.com
c…..@catchall.com
etc etc etc
I used to do this, but mail forwarding generally breaks modern mail security protocols SPF & DKIM.
Also, it turns out that basically any vanity domain is probably more at risk than just Gmail/Outlook/Hotmail — it’s easier to hijack DNS for a vanity domain than for Google/Outlook/Yahoo (which isn’t to say it hasn’t happened for all of them).
I don’t have a good recommendation for how to handle this problem.
You could set up two Google accounts which point to each-other for protection, set up Google Voice on both and use those as the recovery systems. You’ll want to set up backup codes:
https://support.google.com/accounts/answer/1187538
I’d suggest you put them into a bank vault.
You probably should get a FIDO U2F key:
https://support.google.com/accounts/answer/6103523?hl=en
I think this mostly works.
Note:
If your Google Voice forwards to a normal cell service, you’re at risk if someone can con your carrier into replacing your SIM card.
If your Google Voice forwards to a normal land line, you’re at risk if someone can con your provider into adding forwarding to anything.
You can use Hangouts instead of Google Voice forwarding.
Sounds too much like the kids on the playground. It’s just a little too difficult my me to take any of this seriously.
I think the point of the article is at 10,000 feet while you’re standing on the ground.
@Mike… I think the point that is that if a kiddie can compromise your mailbox, then someone specifically trying to target you for more nefarious reasons can easily do it too.
It’s an old argument. Given that some mail boxes are easier than others to target and that email is such a big target in the first place, it really is time for people to wise up to the issues surrounding certain things. There are things to stay away from. If you want to use unsafe technology, your likely going to have trouble.
Your blog is very interesting and entertaining Brian. You speak with knowledge and truth. Thank god we have you!
Very good article. So if two-step authentication and secondary email addresses could be hacked what options are available? What secondary email address should one use?
Unfortunately, I believe you should only use a major mail providers with 2FA preferably w/ a U2F dongle instead of SMS as the second factor. You can have a pair of them as I note above:
http://krebsonsecurity.com/2015/11/talktalk-script-kids-the-quest-for-og/comment-page-1/#comment-394911
If you’re willing to increase/share risk across competing providers, you can do that, but remember doing that means that your weakest link is the union of the weakest links for your providers. Normally we think that adding diversity improves security, but here each additional distinct component increases risk, since it’s a new attack point that may be slightly weaker than the ones whose risk you’ve already accepted.
If you haven’t read about @mat, you should 🙁
Good article! Reminds me to review my Apple recovery list.
I would suggest that
a) there is no reason for using ISP-provided mail box except for junk accounts
b) email is probably the weakest recovery channel in 2-factor authentication. SMS, one-time pad or a recovery key are more secure options.
We talk about SMS as a valid 2FA, and it’s “better” than nothing, but it really isn’t secure.
An attacker willing and interested in attacking you can socially engineer the provider (typically cellular carrier) of your SMS service and redirect SMS service — either by adding SMS forwarding or claiming that the SIM was lost/stolen and asking for it to be replaced.
I always thought “OG” (particularly in the UK) referred to “old git” – which would be appropriate when considering that these valued short-named accounts tend to also be accounts that have been around for many years. Depending on the use, the value may lie in their age as much as in the shortness of the name.
[For American readers, “git” has existed in the UK as a term of abuse for centuries, roughly akin to “bastard”, and can be found in Shakespeare. The fact that it’s also a software versioning tool is mildly amusing.]
Well timed article, I just received a 2FA password-reset verification text out of the blue from Twitter a couple days ago. Quickly figured it was someone trying to take control of my ‘OG’ account.
You should take the same precaution with hosting. I had setup two separate accounts at a well known hosting site for two different customers.
Customer A decided to cancel the web hosting. He didn’t call me. But he called the hosting site probably found from his CC statement.
Somehow, he convinced the ISP to remove another customers website that I had setup.
I had used different email addresses. CC used was customers so no connection other than my name I guess.
If the deleted website was eCommerce or lead gen then it would have been really bad. Luckily, it was for non-profit. I had set them up for free.
Chose hosting sites that have two-factor. And be careful which email and phone # you use.
It’s amazing how effortless it is to get people to do something. All you have to do is ask. Sometimes, I even give you personal information when I don’t have my guard up.
Paresh
The social engineering attack against the ISP resembles to the hack of CIA Director John Brennan’s AOL mailbox. The attackers in that case called Verizon to reset Brennan’s password, which they ultimately did.
Source: http://www.wired.com/2015/10/hacker-who-broke-into-cia-director-john-brennan-email-tells-how-he-did-it/
Re: “So you’ve got two-step authentication set up to harden the security of your email account (you do, right?).”
When it comes to any Internet-related service that you critically depend on, my personal recommendation would be to make sure that you have as much direct control as is reasonably-possible. It’s not terribly expensive or difficult to host your own mail on a VPS & manage your own domain through a reseller like Tucows – and for context, I say that while working for a company with a grand total of 2 full-time staff, including myself.
Compared to that approach, I see two-factor authentication as, at best, a band-aid solution to the fundamental issues that come along with depending on SaAS controlled by a third-party. Granted, I am obviously biased from doing IT/server admin on a daily basis & there is admittedly a learning curve – and it’s definitely a good idea to bring in someone qualified to do the initial setup. But with a decent “managed” VPS (where the provider handles things like OS updates for you), once the setup is done it’s no more difficult to manage EMail than with a cheap VHosting account – or services like Google Apps for Domains/Office 365, for that matter.
As a result, in order for someone to irretrievably compromise any of my critical EMail accounts, simply compromising the account itself wouldn’t even come close. I could still get back in, because I have access to manage the accounts. If the hosting account itself were compromised, I could still get back in because I have root access to the server. If the server’s root account was compromised, then I could still get back in because I have access to manage the VM. If the VM management console were compromised, I could still disable/redirect DNS for the server, because the DNS is hosted separately & controlled through the domain registrant account. If the domain registrant account were compromised, then I could still get back in because I’m also the reseller for the domain.
The only way to do it effectively (short of compromising the actual domain registrar) would be to compromise everything from the domain reseller account down to the individual EMail account – so 7 different accounts/logins that would have to be compromised, and in a fairly short period of time. And that could increased to 8 fairly easily, by using a separate provider for DNS hosting: someone like EasyDNS. Granted, the trade-off is that there are a lot more separate moving pieces – but it is also an application of the “don’t keep all of your eggs in one basket” principle.
The other benefit of that approach is that the providers I’m using are all primarily targeted at business customers, rather than consumers – so they should be substantially more careful/less-susceptible to social engineering attacks.
How does the info in this article apply (if it does) to someone who uses an email client on her/his own computer?
All your mail client does is pass your authentication credentials on the the mail server of whatever email service you’re using. This article concerns the process of securing and resetting your password and recovery email address, which has everything to do with using email, whether you use a client or you read/send mail via the Web.
Regarding that account at namecheaphosting.com, that’s probably not hosted at Namecheap. They provide a domain-forwarding service which has been abused by spammers for a long time: http://tacit.livejournal.com/608386.html
It has been my experience that Namecheap is in bed with the bad guys. They refuse to do anything about spammers abusing that domain-forwarding service.
Thanks for that, Joe. Interesting stuff that probably deserves a follow-up.
I notice Glubz on his Twitter says on Oct 30: ‘interview should be up on vice motherboard soon :)’
Joining the dots, is this then ‘ Crackas With Attitude’?
Great little hacker, useless on opsec.
WTF why did not Alarms did not go off when some one at phone company looked the DCI’s fucking phone number.
Some parents this Elliott Gunton @fearful must have. Arrested at age 16 for intrusion and theft of corporate data on millions of people and a few days later he is still tweeting away. I am I the only who thinks that maybe his computers should have been sized and locked up by mommy and daddy, if not the police. Kinda starting to understand where/how this punk went wrong.
Don’t worry, he has what’s coming to him, very soon.
Let’s see what happens when he goes after bigger fish to fry, when he’s 18 still living in his parent’s basement.
Typically, an 18 year old wouldn’t be able to sustain themselves. Even a lot of 20 year olds can’t. It’s not like the majority is just granted with a well paying job and enough cash to live on their own at that age. You really give me the impression that you yourself are 16, or at least young, and that you haven’t gotten the chance to experience the beauty of a mortgage as well as other necessary expenses. Forgive me if I’m wrong, but I hate the “hurr durr, u lib in ur mom’s basement” insult when it comes from another basement dwelling turd.
So this is apparently chained to the lack of opportunity and belief in the future. Wise. Life has changed a *lot* in my last 50 years – and not for the better. Less than 10% of kids are born into families with the actual means to give them a future, or even any idea of what life should, would, or could be about. Even several of our recent presidents are widely considered liars. What would we expect from a smart kid interested in the Net?
What’s the holdup with Twitter not giving the handle back to the rightful owner? Surely they have enough evidence now?
Thanks for the article. Long time follower. Appreciate the details and info you give out. Now i have to take the info and better my accounts 🙂 Keep up the awesome work.
So, um, now Hillary looks brilliant for taking personal control and running her own server, yes?
At least we know that minimum wage customer service morons at her ISP weren’t in a position to give away the whole shebang.
geeeeezzz
Technical security measures at quite a lot of places are still seriously lacking, but in most places, the idiot humans are still the weakest link.
I’m reminded of the @mat hack as well: http://www.wired.com/2012/08/apple-amazon-mat-honan-hacking/
Actually it’s probably more like the hacking of CloudFlare CEO’s email account (same group as the Honan hack).
http://krebsonsecurity.com/2012/06/attackers-target-weak-spots-in-2-factor-authentication/
Ah, yeah. Well, that’s why.
In computer software (security), we’re used to chained vulnerabilities/privilege escalation. Unfortunately, people don’t really consider it when reviewing their security.
@Brian: btw, does Twitter give any extra security for “verified” accounts?
https://support.twitter.com/groups/31-twitter-basics/topics/111-features/articles/119135-about-verified-accounts
Certainly, I’d encourage anyone with enough followers/potential prestige to get their account verified (yours is).
It /sounds/ like, in /theory/ verified accounts have an extra phone number associated that Twitter is supposed to use to contact the account holder for security stuff. — I have no idea if it works. Twitter’s verified stuff talks about how you can lose your verified sticker and doesn’t hint at them confirming your changes before you do things that would make it likely for your account to lose that status…
While @Brian writes about attacks on major people/entities, it’s worth noting that chained attacks (unfortunately) work on just about everyone.
The NYTimes arranged w/ HackerOne to document how attacks can apply to a normal person. — a CNBC (i.e. no paywall) article about it:
http://www.cnbc.com/2015/10/15/hackers-prove-they-can-pwn-the-lives-of-those-not-hyperconnected.html
Here’s the article about the garage door hack (used by HackerOne):
http://www.wired.com/2015/06/hacked-kids-toy-opens-garage-doors-seconds/
I’m not sure if home security systems have improved, at least a year ago, many of them were apparently just as dumb as (if not dumber than) garage door systems:
http://www.wired.com/2014/07/hacking-home-alarms/
— I generally encourage people to leave themselves logged into their home computers (yes, use 2FA, and yes please use a password manager), because we are willing to trust physical security. But technically, this isn’t good advice. The thing is, if someone can physically access your computer, they can hardware hack your computer — whether they plant a camera in your computer room, install an evil USB pass-through dongle for your keyboard, add a card to your PC Bus which runs code during the boot sequence, manually write files onto the hard disk drive in its boot sequence, or hack your router to later introduce malware to a file you download. — Some of these things can be protected against (secure boot could protect against some placement of files on your hard drive, but probably wouldn’t protect against a card on your Bus; USB isn’t a secured system, so an evil USB device can be a silent MITM), but again, if an attacker is willing to break into your house, they could be willing to work past whatever defenses you have…
Upon reading this article, I decided to review security on my email accounts.
On my hotmail account, in order to access any sensitive areas, it requires verification with a security code that is sent to the recovery email account that I have listed there. But one of the options is “I don’t have any of these” and then it allows me to enter a different email address or phone number instead that will be used for verification. How is that secure? Couldn’t a hacker follow this procedure and put his own info in here?
Thanks
Interesting last comment about v**izon. The last time I checked they had everything, including my secret wep2 password, on a web-facing server. I guess they just don’t care who hacks them.
I did try this a while ago, so my memory is a bit sketchy, but I don’t think control of the secondary email address is sufficient when you have 2FA on your Google account.
I started the password recovery process on my google account a few years ago, purely to see what an attacker could do. I got an email at my secondary and primary address. I clicked on the link in the email that went to the secondary address, and then google asked me to use the second factor to verify (ie. one of google authenticator, SMS, backup code). There was an option to say “I didn’t enable 2FA” or something similar. If I selected that, it pretty much told me to contact google customer support, and if possible have access to a computer that has logged in to the google account before, and some other information I can’t remember.
I didn’t follow any further, but I suspect if I did, then emails would once again be sent to my primary and probably secondary addresses. I as the legitimate owner could contact google and intervene, and if I did that from my normal computer, it would make the attacker’s case look very flimsy.
This sounds like poor security from Microsoft, or any other company that has 2FA but will reset accounts with only a single factor (in this case control of the secondary email). Beware any 2FA provider that doesn’t make you write down backup codes or supply a phone number, they will probably have many weaknesses in their password recovery procedure.
Often email and other account 2nd factor security only adds delay.
After the death of an older family relative I was faced with a $100+ monthly cable bill to just to keep a phone number and email account active — in fact $100+ just to keep email account! (An issue worthy of its own article: Pitfalls of email accounts provided through cable company!). I discovered several accounts after service termination that were tied to his old email. I couldn’t do a password reset because his old email address was now “frozen” but I was able to reset some of them through a “lost password; lost email” authorization but with a 30 day delay. Similarly when I tried to change the security email associated with some online accounts where I did have the password but after the old email account was closed, I was able to do so but only with a 30 day hold. The good news was that a mechanism existed to allow me to make the (legitimate!) changes. The bad news was that I was allowed to make the changes.
And of course we all remember the Facebook and Twitter account takeovers that happened when Yahoo released inactive email accounts for new registration.