With tax filing season in the United States well underway, scammers who specialize in tax refund fraud have a new trick up their sleeves: Spoofing emails from a target organization’s CEO, asking human resources and accounting departments for employee W-2 information.
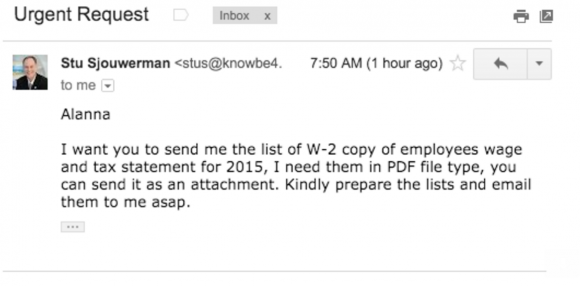
 Stu Sjouwerman, chief executive at security awareness training company KnowBe4, told KrebsOnSecurity that earlier this week his firm’s controller received an email designed to look like it was sent by Sjouwerman requesting a copy of all employee W-2 forms for this year (full disclosure: KnowBe4 is an advertiser on this site). The email read:
Stu Sjouwerman, chief executive at security awareness training company KnowBe4, told KrebsOnSecurity that earlier this week his firm’s controller received an email designed to look like it was sent by Sjouwerman requesting a copy of all employee W-2 forms for this year (full disclosure: KnowBe4 is an advertiser on this site). The email read:
“Alanna,
I want you to send me the list of W-2 copy of employees wage and tax statement for 2015, I need them in PDF file type, you can send it as an attachment. Kindly prepare the lists and email them to me asap.
Stu”x
Turns out, KnowBe4 just hired a new chief financial officer. The controller answered that she didn’t have access to that information, but that the new CFO could help. Sjourwerman said an analysis of the email headers showed the phishers used someone’s GoDaddy email server and the return address was not associated with the company.
“Our CFO had just stepped through all of our awareness training and smelled something phishy,” Sjourwerman said. “The two of them walked up to me and asked if I had requested a PDF with all W-2’s. Obviously, I hadn’t, and congratulated them on a good catch. But imagine if we would have sent off those W-2’s! It would have opened up our employees to identity theft because the W-2’s have their full name, address, wages and Social Security number.”
Fraudsters who perpetrate tax refund fraud prize W-2 information because it contains virtually all of the data one would need to fraudulently file someone’s taxes and request a large refund in their name. Indeed, scam artists involved in refund fraud stole W-2 information on more than 330,000 people last year directly from the Web site of the Internal Revenue Service (IRS). Scammers last year also massively phished online payroll management account credentials used by corporate HR professionals.
According to recent stats from the Federal Trade Commission, tax refund fraud was responsible for a nearly 50 percent increase in consumer identity theft complaints last year. The best way to avoid becoming a victim of tax refund fraud is to file your taxes before the fraudsters can. See Don’t Be A Victim of Tax Refund Fraud in ’16 for more tips on avoiding this ID theft headache.




We constantly get people trying to spoof an email from our CEO and send it to our CFO asking for a wire transfer. Unknown to them his email is different than what they are trying to spoof. It has gone down quite a bit since we set up SPF and DKIM on our domain. They now result to misspellings of our email domain.
And you can add DMARC.org to your domain for added protection.
I second what Franck is saying. SPF and DKIM alone will not protect you from these phishing attacks. DMARC at p=reject or quarantine will.
“You can send it as an attachment.” Red flag right there.
I think “kindly”, unless this is vernacular the spoofed person readily uses, is red flag also. Watch out: once these scammers start to correct their grammar and punctuation they will be much harder to catch.
When the Germans found out that Merkel’s iphone was hacked, didn’t they purchase a car-load of old typewriters? I sense an opportunity for traditional accounting as well…
The Soviets bugged American typewriters and that was over 30 years ago. I’m pretty sure it’s much easier with today’s COTS tech and even more effective if you do a custom job.
I think the phishers just spent too much time playing Bioshock. “Would you kindly…”
Kindly is a pretty common alternative for “please” in parts of the U.S. So depending which flavor of American English you speak, it may or may not be considered an error in informal conversation.
“the phishers used someone’s GoDaddy email server and the return address was not associated with the company”
So, I suppose we can assume that the domain in the email is not knowbe4.com, but rather something like knowbe4.mobi ? The text in the image is truncated, so we can’t see.
The screenshot has the CEO’s real address as the sender (From), but the email probably has a different Reply-To address.
I’m sorry for commenting on a different article, but it looks like comments are closed on that article.
I’m referring to: Dec 15, 2015: Don’t be a victim of tax refund fraud in ’16.
Brian: I think you should update that article. You suggest in that article that people file a 14039 and also get an IP PIN. As Reg Swiles notes in his comment on Jan 12, 2016 not everyone can get an IP PIN.
Looks like all I can do is file a 14039. I got caught up in both of the OPM data breaches.
Yes, you can apply for one, but the IRS is for some reason picky about to whom they issue those PINs. Point is, you won’t know unless you apply.
As Reg Swiles noted in his 1-12-2106 comment:
Apparently not everyone can get a PIN. This is from the IRS website linked in the article:
Determine your eligibility…
You must get an IP PIN to file your current or prior year returns in 2015 if:
You received a CP01A Notice with your new IP PIN and you lost it, or
You had an IP PIN in a prior tax year and you didn’t receive a new one this year, or
Your e-filed return rejected because your IP PIN was missing or incorrect
You may choose to get an IP PIN if:
You received an IRS letter inviting you to ‘opt-in’ to get an IP PIN, or
You filed your federal tax return last year with an address in Florida, Georgia or the
District of Columbia
That seems very clear to me. I’m not eligible.
There are 2 ways to fill out the 14039 form, you may already know this. 1) if you have experienced ID Theft issues which MAY affect your taxes, and 2) you have ID Theft issues and they HAVE affected your taxes. Then, with the police report that addresses the IRS tax indications, Notarized FTC Affidavit, and any other applicable documentation, etc., you most likely will receive the IP PIN. They do investigation on their side to support your application.
Thank you, Sarah. I understand.
Interesting that this example comes from a company that specializes in security awareness training.
I get the value and timeliness of targeting tax information, but has anyone heard of other examples of ceo-fraud/business email compromise that targeted W2 or tax info?
Is there also a company that specializes in HIPAA compliance hit by spearphishing targeting preceding year FSA transactions?
Is there a company specializing in PCI compliance that can write a note about being spearphished for employee credit card details?
Maybe my spidey senses are too finely tuned?
I am in manufacturing and my company was recently targeted in this very same scam. Not only did they ask for the W2’s, but they continued to follow up and get more assertive when they did not get a reply to their original request.
I had an employee of a client receive two similar messages, marked as spam both times: Dec.2015 and Feb.2016. Both originated from a US connection, then received from a GoDaddy server in Singapore – both times. Here’s the kicker: the reply-to address was ceopresdent@yahoo.com – both times! Hello! I forwarded both to Yahoo’s abuse department, but never heard back.
Good luck. I’ve had a couple of determined attacks going on for a couple years now from @yahoo.com and @gmail.com addresses. Every time a message comes in I report them to their host. Some of the messages are full of racist rhetoric, sometimes they’re polite, sometimes they’re official, but every time they include an attachment that contains a payload they’re trying to entice people to click on. The amazing thing is that everyone’s to: and cc: addresses are visible so I know they’re being received by state and local governments, educational institutions, even police departments. Yet Yahoo & Google do nothing. Years of reports. No action. After a couple dozen racist hate speech messages, which are clearly a violation of both company’s stated TOS, I’m pretty damn sure they’re both asleep at the switch.
Bottom line is know the people that you deal with inside and outside of your business. trust no one!
Because, on teh interwebs:
All men are men, all women are men, all children are FBI agents, and all email requests for sensitive employee information any time of the year come from criminals.
You’re not obligated to send anyone anything they ask for until they prove themselves worthy, even if it’s from the CEO, CIO, CTO, and / or any other 3 letter 3 piece suit that asks for something like this to be sent over a network connection. if they’re asking for something like this, then they really don’t know anything about todays internet connected world and need to be called on the carpet for that. that’s a total lack of a secure mindset.
And if someone should be fired or laid off because of refusing to do so, then that’s not a company that you should be working for in the first place, or you can just litigate that fact to them and bring their total lack of securing employee as well as and more than likely their entire customer base as well as their Share Holders. that should open their eyes to the gravity of the current trend over the past few years we’ve been having these issues with this type of criminal internet / intercontinental activity.
Then again, maybe they need to be out of business!
“Of course, that’s just my opinion, I could be wrong.”
I received the following phishing attempt about two weeks ago. It was specifically targeted at employees of the university where I work. The details were convincing and I’m sure that some clicked the link, which attempted to mimic a real link for our campus domain.
[University name and other identifiers redacted in square brackets]:
—–Original Message—–
From: [unknown sender] [mailto:xxxxx@xxxxx.gov.cl] [A Chile government domain]
Sent: Wednesday, February 10, 2016 5:42 AM
To: info@uoXX.gov [The common 2-letter abbreviation of our state’s name]
Subject: Your electronic W-2 is ready
Dear: Account Owner,
Our records indicate that you are enrolled in the University Of [STATE] electronic W-2 Program. As a result, you do not receive a paper W-2 by mail but instead receive e-mail notification that your online W-2 (i.e. “electronic W-2”) is prepared and ready for viewing.
Your W-2 is ready for viewing under Employee Self Service. Click here to login: hXXp://srsperfect.com/[STATE]secure-[STATE]-edu/welcome-cgi.html
If you have trouble logging in to Employee Self Service at the link above, please contact your Payroll Department for support.
If you would like to un-enroll in the electronic W-2 Program, please log on to Employee Self Service at the link above and go to the W-2 Delivery Choice webpage and follow the instructions.
________________________
This email was scanned by Bitdefender
The timing on this post is superb…my CEO was just impersonated in a message to the head of HR with this exact same scam. The reply-to is an aol address. Good stuff as always, Brian.
An HR Manager at my company received this exact same email. I am a member of InfraGard (FBI) and have sent them the source details. Good to know I’m not the only one taking notice.
SPF and DMARC can really help this issue as well as implementing a “Body From Spoof Rule”
CEO’s don’t look at W-2 forms, a reasonable Department Head would double check the request because its strange and likely misunderstood. If a CEO has a problem with an individual its one copy, they aren’t Accounting Clerks. I don’t know any CEO’s looking at W-2’s.
thank you for the useful stuff you share with us really everytime i visit your website i enjoy reading
thank you again
Does this security company have a link to headers and email? It sounds fishy, that they just got fished after their new employee just went through training.
Maybe it is the pessist in me, but it feels more like a good story to sell training as tax season hits.
Stu no doubt thanks everyone for the kind publicity
Great timing as I just went through this exact scenario. Sounds like this may be a campaign against Google for Business with a GoDaddy compromised email account. Any merit in those details?
That said, we all know that phishing has and will continue to happen as attackers develop ever more advanced approaches and our increasingly diverse and complex environments (data, sharing, cloud etc) mean there are even more ways to trick non-technical staff. I am surprised to not see any references to basic security policy regarding personal data (or HBI data) handling and requisite technical controls such as email content filters or endpoint DLP. It is next to impossible to prevent the influx of phishing approaches, but policies and technical options to protect the actual data are commonplace. That said, I recognize that we do not all have the means in our programs to implement critical controls (political, financial or resource-wise) but it is technically feasible in many common scenarios and worth mentioning IMO. (e.g. Content filtering for SSN is free in Gmail for Business …)
I always worry who, exactly, and how often, is minding the farm (godaddy, various linux repos and kernel bits, sourceforge, etc.) that we rely upon nowadays.
Funny, I thought you were going to talk about this company:
http://www.bizjournals.com/seattle/blog/techflash/2016/02/exclusive-rightside-employee-tax-information.html
They didn’t catch the “sophisticated attack” in time. Maybe the same perpetrators as the MO is exactly the same.
Does anyone know if popular email servers (exchange etc.) and/or gmail can ‘ban’ reply-to ?
That would be some kind of simple-but-effective defence, and, from my experience, corporate users don’t really use reply-to.
It’s probably not a good idea to prevent *senders* from using Reply-To headers. Many mailing-list packages require the use of Reply-To so that replies go to the original poster and not to the entire list if that is desired.
However, I think it should be possible to filter *incoming* messages based on all their headers, such that messages meeting certain criteria including the use of Reply-To get flagged or dropped on the floor based on policy.
SnapChat just disclosed today that they fell victim to this attack
http://techcrunch.com/2016/02/29/snapchat-employee-data-leaks-out-following-phishing-attack/
I am surprised that a company that trains others in security allows spoofed emails from outside the perimeter. My company only allows emails with our SMTP address from whitelisted IPs. This was due to, as we’re reading here, a barrage of phishing attacks using our CEO and CFOs email addresses. We use (and require) a company LOGO in our email signature as part of security recognition (though our mobile message system doesn’t support that standard 🙁 ).
The message here is train, train, train your end users. You can implement all the technology you want but the weakest link is between the chair and the keyboard.
Looks like the same thing occurred with Main Line Health:
http://6abc.com/news/main-line-health-employees-info-compromised-in-email-scam-/1228291/
everything in an email is text, including the header where the reply to and received from fields are, and can be edited and should be considered a lie. only the last ip address can be trusted. google and yahoo can’t do anything about that.
We just got these. End user responded. Then realized after she sent a message saying she is out of town. We played along.
X-Sender: muva@premierautobrokers.com
Reply-To: “xxx”
From: CEO’ name
Sent: Thursday, March 03, 2016 11:50 AM
To: XXX
Subject: Hello!!!!!!!
Are you at your desk?
Thanks.
Subject: Hello!!!!!!!
I want you to send me the list of W-2 copy of employees wage and tax statement for 2015, I need them in PDF file type, you can send it as an attachment. Kindly prepare the lists and email them to me. asap.
Thanks.
This attempt was thwarted by an atmosphere of skepticism which is imperative and only comes out of ongoing training and awareness. EVERY organization should elevate the importance of this kind of discussion.
Was this incident reported to the FBI even though the breach was avoided?