How much would a cybercriminal, nation state or organized crime group pay for blueprints on how to exploit a serious, currently undocumented, unpatched vulnerability in all versions of Microsoft Windows? That price probably depends on the power of the exploit and what the market will bear at the time, but here’s a look at one convincing recent exploit sales thread from the cybercrime underworld where the current asking price for a Windows-wide bug that allegedly defeats all of Microsoft’s current security defenses is USD $90,000.
So-called “zero-day” vulnerabilities are flaws in software and hardware that even the makers of the product in question do not know about. Zero-days can be used by attackers to remotely and completely compromise a target — such as with a zero-day vulnerability in a browser plugin component like Adobe Flash or Oracle’s Java. These flaws are coveted, prized, and in some cases stockpiled by cybercriminals and nation states alike because they enable very stealthy and targeted attacks.
The $90,000 Windows bug that went on sale at the semi-exclusive Russian language cybercrime forum exploit[dot]in earlier this month is in a slightly less serious class of software vulnerability called a “local privilege escalation” (LPE) bug. This type of flaw is always going to be used in tandem with another vulnerability to successfully deliver and run the attacker’s malicious code.
LPE bugs can help amplify the impact of other exploits. One core tenet of security is limiting the rights or privileges of certain programs so that they run with the rights of a normal user — and not under the all-powerful administrator or “system” user accounts that can delete, modify or read any file on the computer. That way, if a security hole is found in one of these programs, that hole can’t be exploited to worm into files and folders that belong only to the administrator of the system.
This is where a privilege escalation bug can come in handy. An attacker may already have a reliable exploit that works remotely — but the trouble is his exploit only succeeds if the current user is running Windows as an administrator. No problem: Chain that remote exploit with a local privilege escalation bug that can bump up the target’s account privileges to that of an admin, and your remote exploit can work its magic without hindrance.
The seller of this supposed zero-day — someone using the nickname “BuggiCorp” — claims his exploit works on every version of Windows from Windows 2000 on up to Microsoft’s flagship Windows 10 operating system. To support his claims, the seller includes two videos of the exploit in action on what appears to be a system that was patched all the way up through this month’s (May 2016) batch of patches from Microsoft (it’s probably no accident that the video was created on May 10, the same day as Patch Tuesday this month).
A second video (above) appears to show the exploit working even though the test machine in the video is running Microsoft’s Enhanced Mitigation Experience Toolkit (EMET), a free software framework designed to help block or blunt exploits against known and unknown Windows vulnerabilities and flaws in third-party applications that run on top of Windows.
Jeff Jones, a cybersecurity strategist with Microsoft, said the company was aware of the exploit sales thread, but stressed that the claims were still unverified. Asked whether Microsoft would ever consider paying for information about the zero-day vulnerability, Jones pointed to the company’s bug bounty program that rewards security researchers for reporting vulnerabilities. According to Microsoft, the program to date has paid out more than $500,000 in bounties.
Microsoft heavily restricts the types of vulnerabilities that qualify for bounty rewards, but a bug like the one on sale for $90,000 would in fact qualify for a substantial bounty reward. Last summer, Microsoft raised its reward for information about a vulnerability that can fully bypass EMET from $50,000 to $100,000. Incidentally, Microsoft said any researcher with a vulnerability or who has questions can reach out to the Microsoft Security Response Center to learn more about the program and process.
ANALYSIS
It’s interesting that this exploit’s seller could potentially make more money by peddling his find to Microsoft than to the cybercriminal community. Of course, the videos and the whole thing could be a sham, but that’s probably unlikely in this case. For one thing, a scammer seeking to scam other thieves would not insist on using the cybercrime forum’s escrow service to consummate the transaction, as this vendor has.
As I noted in my book Spam Nation, cybercrime forums run on reputation-based systems similar to eBay’s “feedback” mechanism — in the form of reputation points granted or revoked by established members. Rookie and established members alike are all encouraged to use the forum’s “escrow” system to ensure transactions are completed honorably among thieves.
The escrow service can act as a sort of proxy for reputation. The forum administrators hold the buyer’s money in escrow until the seller can demonstrate he has held up his end of the bargain, be it delivering the promised goods, services or crypto-currency. The forum admins keep a small percentage of the overall transaction amount (usually in Bitcoins) for acting as the broker and insurer of the transaction.
Thus, if a member states up front that he’ll only work through a crime forum’s escrow service, that member’s cybercriminal pitches are far more likely to be taken seriously by others on the forum.
Security researchers at Trustwave first pointed my attention to the exploit[dot]in zero-day sales thread last week. Ziv Mador, vice president of security research at Trustwave, said he believes the exploit is legitimate.
“It seems the seller has put in the effort to present himself/herself as a trustworthy seller with a valid offering,” he said. Mador noted Trustwave can’t be 100% certain of the details without the vulnerability in their possession, but that the videos and translation provide further evidence. The company has published more detail on the sales thread and the claimed capabilities of the exploit.
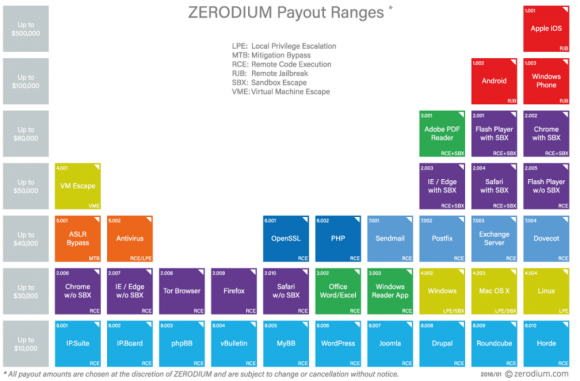
Is $90,000 the right price for this vulnerability? Depends on whom you ask. For starters, not everyone values the same types of exploits similarly. For example, the vulnerability prices listed by exploit broker Zerodium indicate that the company places a far lesser value on exploits in the Windows operating system and far more on vulnerabilities in mobile systems and Web browser components. Zerodium says the price it might be willing to pay for a similar Windows exploit is about $30,000, whereas a critical bug in Apple’s iOS mobile operating system could fetch up to $100,000.
Vlad Tsyrklevich, a researcher who’s published quite a bit about the shadowy market for zero-day exploits, says price comparisons for different exploits should be taken with a grain of salt. In his analysis, Tsyrklevich points to a product catalog from exploit vendor Netragard, which in 2014 priced a non-exclusive Windows LPE vulnerability at $90,000.
“Exploit developers have an incentive to state high prices and brokers offer to sell both low-quality and high-quality exploits,” Tsyrklevich wrote. “If a buyer negotiates poorly or chooses a shoddy exploit, the vendor still benefits. Moreover, it’s difficult to compare the reliability and projected longevity of vulnerabilities or exploits offered by different developers. Many of the exploits offered by exploit brokers are not sold.”
BuggiCorp, the seller of the Windows LPE zero-day flaw, was asked by several forum members whether his zero-day was related to a vulnerability that Microsoft patched on April 12, 2016. BuggiCorp responds that his is different. But as documented by security vendor FireEye, that flaw was a similar LPE vulnerability that FireEye said was featured in a series of spear phishing attacks aimed at gaining access to point-of-sale systems at targeted retail, restaurant and hospitality industries. FireEye called the downloader used in those attacks “Punchbuggy,” but it did not specify why it chose that name.
If nothing else, this zero-day thread is an unusual sight on such an open cybercrime forum, Trustwave’s Mador said.
“Finding a zero day listed in between these fairly common offerings is definitely an anomaly,” he said. “It goes to show that zero days are coming out of the shadows and are fast becoming a commodity for the masses, a worrying trend indeed.”



![The sales thread on exploit[dot]in.](https://krebsonsecurity.com/wp-content/uploads/2016/05/buggicorp-580x255.png)

0.0 How does linux figure into this sort of thing?
Linux defaults to non-admin, non-root access. Every attempt to install an application or change any system settjng requires an admin log in.
Oh LPE exploits still happen under Linux.
The same sort of thing can happen on Linux.
The Google search I used: selling local privilege exploit Linux
Someone created a nice video showing how to use a local privilege exploit on Linux:
https://vimeo.com/147391580
It should feel similar to this article’s video (the main difference is that the article’s video has a Russian narrator and the Vimeo link has a narrator writing in English and who didn’t bother to disable some Windows dialog).
Note: the value of a Zero Day exploit is that the vendor (in this case probably the Linux kernel team —although i haven’t verified that it wasn’t a third party module; in the case Brian is reporting, the vendor is of course Microsoft) doesn’t know about it and thus hasn’t had an opportunity to fix it. Once the vendor finds out about an exploit, they’re likely to fix it. So the exploit in this video should be fixed by now (as long as you’re running software that’s newer).
MySpace breached, all accounts stolen. http://www.businesswire.com/news/home/20160531005770/en/Time-Confirms-Breach-Myspace
It’s looking like a principal technical growth career would be intrusion detection. I constantly wonder/worry about how many low\-profile, undetected intrusions there are – LanDesk had been infiltrated for 2 years before they figured it out.
To be honest with you the IDS systems are so blind these days. What works well in my environments are the FireEye NX appliances. I am sure people will disagree but I have yet to see intrusions that were not detected in combination with a good endpoint signature-less solution such as Cylance. FireEye throws in IDS/IPS free now. The other issue is companies continue to not patch and they also don’t run IPS in blocking mode. No one’s fault but their own.
@Robert, did you mean cylance caught all attempts of intrusions even after the intrusions evaded IDS/IPS?
Yep sure did and then the FireEye appliances block the callbacks for systems that do get infected. Tested many scenarios in our labs before choose those 2 systems.
Thanks Robert, appreciate your quick response!
@Robert, reason I ask is we are in the market to replace our old very popular AV (signature based) after it failed to detect a few malware/ransomware. I’ve heard good things about cylance, just wanted to get some more info before we invite the account manager (so I can avoid any sales pitch and get to the tech/cost details)
Thanks for informing me about that! Looking forward to read more from you!
You said that they could potentially make more money selling the exploit to MS than offering it online. But wouldn’t they sell it to multiple bad guys, thus multiplying their take?
Depends. Often things are sold “exclusively”, e.g. if you have stolen 100 credit card stripes, you’d sell them exclusively to one customer. If two customers bought the same bundle and one used some of the cards and got them voided, then when the other buyer tried to use them, they’d be upset.
The same can apply for exploits. Whomever uses a zero-day will typically eventually trigger an IDS or something and the bug will be analyzed / reported to the vendor for analysis, and then be patched.
That isn’t to say that a researcher must sell only one copy of a thing. But the theory is you can get more value by making it a “scarce” resource and only selling to a single willing customer.
Also, keep in mind that each transaction you make (a sale in this case) increases your risks and obligations. Fewer transactions are thus better.
I’m not saying that a given person will follow this logic, but it does exist (as with credit cards) and it isn’t unreasonable for them to apply it here too.
And also “tax free”
While I believe I understand the chart from Zerodium, I can’t say I understand their color system, or why/how they are organizing by column. Their site doesn’t offer any key/legend, either.
Anyone care to speculate?
Easy enough to tell if you look at the items. For instance Purple is browser, Red is phone, Yellow is OS, etc.
The column organization is arbitrary, but basically lets them give an easy at a glance way to tell what’s worth the most, which is the top row, the phone stuff.
Also, it looks similar to a periodic table, which is probably not a coincidence.
Indeed.
The article linked to the page w/ the image: https://www.zerodium.com/program.html
you can see boxes which essentially describe the colors.
What puzzled me was the high value for Windows Phone — which to my knowledge has very little userbase.
One notable thing:
http://web.archive.org/web/20150731004316/http://zerodium.com/program.html
Used to specifically list “BlackBerry OS 10” (not the correct way to write the product, but whatever). It now just lists “BlackBerry” (which could be the Android product series, but then I’m not sure why it’s worth listing at all).
My guess: Either MS is contributing, or the US gov has targets that use windows phones they want to be able to get into (or at least cover that possibility)
IE has a different color than Firefox and Chrome (for one that doesn’t fit the browser as same color). And I was talking about the columns, not the rows—those I get. Once I think I have the colors figured out, I hit a strange issue. But mostly, as a former research guy, used to making charts and graphs, I can’t figure out why they didn’t include a key/legend. That’s just SOP.
Good article, and I appreciate the simplified description of some exploit methodolgies. Are you aware of some sort of a “hacking for idiots” guide to hacking that describes TTPs in sufficient detail for the reader to gain a functional understanding of these methodologies (and ultimate goals) without getting into a level of technical depth required to actually hack or perform pen testing? I have been unable to find something like this, and if it doesn’t exist, I see a money maker for you authoring a book that provides a managerial level view of this sort.
I’m sure there’s information security for dummies or similar books that would cover protecting against hacking and would describe basics.
Krebs provided a good read on the TTPs leveraged in the Target breach, and the SANS case study below provided more detail. I find this level of detail to be quite instructive at a non technical level. I have not seen any sort of more comprehensive book of this sort out there anywhere.
https://www.google.com/url?sa=t&source=web&rct=j&url=https://www.sans.org/reading-room/whitepapers/casestudies/case-study-critical-controls-prevented-target-breach-35412&ved=0ahUKEwjdhK2ewIXNAhXG4yYKHQwgDUYQFggfMAA&usg=AFQjCNEdgA671ny42apvq3a4tE57uZFVbA&sig2=er_ljsyHCHaCxfRIeGHyhg
My link to the SANS article is bad but it can be googled for reference.
No problem…..
Just update the system and set it up with 2fa (for servers).
“One core tenet of security is limiting the rights or privileges of certain programs so that they run with the rights of a normal user — and not under the all-powerful administrator or “system” user accounts that can delete, modify or read any file on the computer. ”
Do you have any more articles about this or know where I can read up on it?
Thanks
https://en.wikipedia.org/wiki/Privilege_separation isn’t a terrible place to start…
90 grand one time, or the potential for Millions if used in an evil way…..Hummmmmm
That is why the creators for most of the exploits and zero days never come forward and want to win a bouty. By working with the potential good side, the people on the other side probably wont share any information with that person. They re probably seen as not trusted and can compromise some projects.
It could all be smoke and mirrors, sure, but the fact that it can be available is quite real. If you think about the millions of lines of code, and the small amount of error that is required to open up an “opportunity” for some one to find a lucrative bug, its not all that hard. I am sure microsoft on occasion using some sort of fuzzing to see what bugs still remain. I bet most seem buried and if the “experts” at microsoft cannot fathom the bug, them let it go until later. Yes, there are smarter people out there in the world than microsoft employees.
Time will tell if another “emergency patch” will come flying off the shelves in the next few weeks, months, or never.
*FEDERAL RESERVE COMPUTERS HACKED: REUTERS SAYS, CITING DOCS
This is being all over the news. Interesting thing that I could not find a source of information and being bi-lingual I have no problem finding an information in Russian.
Perhaps this is true, perhaps not… I would not believe something that only exists virtually.
I also can tell, that it seems to be a joke. Think of a criminal, who would publicly advertise selling drugs. What would you think of him?
Otherwise it is an entertaining article. Thank you !
Criminals never sleep long time ago tgey used zeus why 0 day is bettter?? And where they get idea? This article is so dificult to undestood so many dificult words im not tech geek not undestood.anyways i have question,if this guys are so smart and good skillls, why they dont put skills and knowledge on good use???why they using talent for bad purposes? Something must be wrong this guys can work at bank easily!!! Or software company owners why they do bad?
Could of guessed it was Russian