Two young Israeli men alleged to be the co-owners of a popular online attack-for-hire service were reportedly arrested in Israel on Thursday. The pair were arrested around the same time that KrebsOnSecurity published a story naming them as the masterminds behind a service that can be hired to knock Web sites and Internet users offline with powerful blasts of junk data.

Alleged vDOS co-owner Yarden Bidani.
According to a story at Israeli news site TheMarker.com, Itay Huri and Yarden Bidani, both 18 years old, were arrested Thursday in connection with an investigation by the U.S. Federal Bureau of Investigation (FBI).
The pair were reportedly questioned and released Friday on the equivalent of about USD $10,000 bond each. Israeli authorities also seized their passports, placed them under house arrest for 10 days, and forbade them from using the Internet or telecommunications equipment of any kind for 30 days.
Huri and Bidani are suspected of running an attack service called vDOS. As I described in this week’s story, vDOS is a “booter” service that has earned in excess of $600,000 over the past two years helping customers coordinate more than 150,000 so-called distributed denial-of-service (DDoS) attacks designed to knock Web sites offline.
The two men’s identities were exposed because vDOS got massively hacked, spilling secrets about tens of thousands of paying customers and their targets. A copy of that database was obtained by KrebsOnSecurity.
For most of Friday, KrebsOnSecurity came under a heavy and sustained denial-of-service attack, which spiked at almost 140 Gbps. A single message was buried in each attack packet: “godiefaggot.” For a brief time the site was unavailable, but thankfully it is guarded by DDoS protection firm Prolexic/Akamai. The attacks against this site are ongoing.
Huri and Bidani were fairly open about their activities, or at least not terribly careful to cover their tracks. Yarden’s now abandoned Facebook page contains several messages from friends who refer to him by his hacker nickname “AppleJ4ck” and discuss DDoS activities. vDOS’s customer support system was configured to send a text message to Huri’s phone number in Israel — the same phone number that was listed in the Web site registration records for the domain v-email[dot]org, a domain the proprietors used to help manage the site.
At the end of August 2016, Huri and Bidani authored a technical paper (PDF) on DDoS attack methods which was published in the Israeli security e-zine Digital Whisper. In it, Huri signs his real name and says he is 18 years old and about to be drafted into the Israel Defense Forces. Bidani co-authored the paper under the alias “Raziel.b7@gmail.com,” an email address that I pointed out in my previous reporting was assigned to one of the administrators of vDOS.
Sometime on Friday, vDOS went offline. It is currently unreachable. Before it went offline, vDOS was supported by at least four servers hosted in Bulgaria at a provider called Verdina.net (the Internet address of those servers was 82.118.233.144). But according to several automated Twitter feeds that track suspicious large-scale changes to the global Internet routing tables, sometime in the last 24 hours vDOS was apparently the victim of what’s known as a BGP hijack. (Update: For some unknown reason, some of the tweets referenced above from BGPstream were deleted; I’ve archived them in this PDF).
BGP hijacking involves one ISP fraudulently “announcing” to the rest of the world’s ISPs that it is in fact the rightful custodian of a range of Internet addresses that it doesn’t actually have the right to control. It is a hack most often associated with spamming activity. According to those Twitter feeds, vDOS’s Internet addresses were hijacked by a firm called BackConnect Security.
Reached by phone, Bryant Townsend, founder and CEO of BackConnect Security, confirmed that his company did in fact hijack Verdina/vDOS’s Internet address space. Townsend said the company took the extreme measure in an effort to get out from under a massive attack launched on the company’s network Thursday, and that the company received an email directly from vDOS claiming credit for the attack.
“For about six hours, we were seeing attacks of more than 200 Gbps hitting us,” Townsend explained. “What we were doing was for defensive purposes. We were simply trying to get them to stop and to gather as much information as possible about the botnet they were using and report that to the proper authorities.”
I noted earlier this week that I would be writing more about the victims of vDOS. That story will have to wait for a few more days, but Friday evening CloudFlare (another DDoS protection service that vDOS was actually hiding behind) agreed to host the rather large log file listing roughly four months of vDOS attack logs from April through July 2016.
For some reason the attack logs only go back four months, probably because they were wiped at one point. But vDOS has been in operation since Sept. 2012, so this is likely a very small subset of the attacks this DDoS-for-hire service has perpetrated.
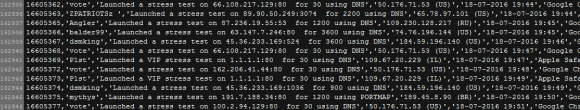
The file lists the vDOS username that ordered and paid for the attack; the target Internet address; the method of attack; the Internet address of the vDOS user at the time; the date and time the attack was executed; and the browser user agent string of the vDOS user.




Attack for hire? Unreal that the morals of humans have sank to this level. And ISP’s hijacking internet addresses? Who can you trust other than the IRS these days?
Back connect is not a ISP. It looks like a shady DDOS protection provider. When you give a Lulzsec member the right to make BGP announcements, what do you expect is going to happen???
The Lulz never stopped for this one.
Fun fact, Bryant used to work for Staminus but left the company just before the big hack/dump happened.
It gets more interesting!
$ host blackhatworld d0t com
blackhatworld d0t com has address 191.101.191.90
HMMM….
$ whois 191.101.191.90
{sn1p}
inetnum: 191.101.191/24
status: reallocated
owner: BackConnect Security LLC
ownerid: US-BSLL-LACNIC
responsible: Tucker Preston
Who’s side are they on, anyways?
It seems that security companies have a habit of eating from both hands. One only has to look at Cloudflare to see that’s true. Cloudflare knowingly offers protection to the very DDoS services that their other clients need protection from.
It’s the old ‘sword and shield’ mentality for many of them. Why not be the supplier for both? I get easily a half dozen people come by our live chat a week looking for ‘spoofing VPS’ and the likes it’s insane.
I have no doubt that all of the booters and requests are just logged and sent off to whatever 3 letter ORG might find them useful.
Francisco, why are you so gung-ho about this? In fact there was a massive IOT botnet hosted on your network for 3 months that you refused to do anything about. You’re just as bad as the others
Cloudflare is in an interesting dilemma though. Where do you stop being the police that decides who gets DDoS protection and who doesn’t?
Matthew Prince the CEO of Cloudflare gave a talk at black hat where he talks about that: https://youtu.be/SWFX-zEYwN0
Bryant not only left Staminus right before the hack, but was personally responsible for it.
Together Bryant Townsend and Marshal Webb (AKA m_nerva, famous for trying to snitch on lulzsec) conspired to hack Staminus and leak their database.
Proof: https://bgpstream.com/event/21051
Just a few days before the database leak, backconnect.net hijacked Staminus IP ranges.
Who can we trust when the control of the internet is handed over to a global trust? I’d love to see what Brian thinks about the future under a possible UN type direction. Who decides what is right and wrong, and will we see an increase in segmented internets that are broken into national intranets? Will we have a great wall of US internet that other countries will have to request access to sell goods and services?
Jade Helm 2: Electric Boogaloo.
Nice job! Wish cleaning up the internet was as easy as you make it seem. Thanks for your work.
Arrested my foot! They’ll be working on the next gen Stuxnet from Monday.
You’re an idiot, Martin. They’re not going to be programming anything at all, they’re both script kiddies and can not comprehend programming. It’s honestly the truth, these articles are making them look like something they’re not, I’ve interacted with AppleJ4ck and he knows nothing of nothing, others did his work for him.
vDos was made up from publicized attack scripts, and seeing as how it got hacked a re-branded, copy and pasted panel.
I don’t think the IDF care if they’re original, only if they’re effective.
Sorry raincoaster, but I’m failing to see where your rather irrelevant and moronic comment comes into context here?
It isn’t moronic at all, did you read the damn article? They’re 18, read for IDF service. Duh.
There are ways of expressing your opinion without coming off as rude, insulting and condescending.
That’s what I was thinking. They won’t do time. They will be recruited by Israel to do state sponsored hacking. Just like Sabu did for the FBI when he got caught.
Nice going Brian. I get fed that there are so many crooks on the internet. Everybody to the crook is a mark. Very cold and callous. Keep up the good work.
WAHOO !!!
Way to go Brian!
Keep up the GREAT work!
http://www.cardingmafia.ws
Details and visual replay of the Verdina BGP hijack event can be found on @bgpstream https://bgpstream.com/event/54711
Thanks Brian with providing me with more of an insight into workings of vDOS.
there goes my lifetime 1.2ks vdos subscription.
Thanks for the attack list, our services are there. Hopefully the customer list is released next, so I can see who the degenerate was. 😉
The customer list doesn’t show anything more than what the attack logs show, just what plan they had.
I purposefully did not publish customer email addresses because vDOS did not validate them, so anyone could have signed up as anyone else.
Brian. I got the report today. I have 50 atms that i work on for a few banks. Are they saying that so far all periscope skimmers are on motorized card readers? I went thru a rash of skimmers on NCR ATMs that were at main branchs of Banks. We did catch one of the perps when they came back to collect the skimmer and camera. Thanks for any additional info.
Maybe you meant to comment on another story?
Getting swamped by junk email on primary private email. All started when visited Obama Care web site looking to get a health care quote. Had to block sales calls for 2 weeks, one every 5 minutes. Now the email from everywhere just keeps getting worse. Junk mail is shutting down private email.
For those who don’t already know, BGP is Border Gateway Protocol (I was surprised to not see that explained in the article).
Thanks once again, Brian, for your excellent reporting.
So Backconnect hijacked a range containing vDos, and they also took down the entire /24 that it resided within? Did it show any regard for the other customers in that IP range?
Is Backconnect a criminal org or a real company?
What the FUCK?!?!?!
Exactly what I was going to say. No doubt that vDOS was acting unethical/illegal but what about these Backconnect guys? Something seems fishy.
Back connect uses primarily voxility, that says enough
To ebalorate, we had to have an upstream provider perform a nullroute on an voxility ip address that was being used as a command and control center for a botnet that could do 150gbit tcp. Voxility itself wasn’t responding to abuse emails.
Oh so that was you eh? Very handy for future reference!
Ironic, considering you used to use Voxility for many years :’)
A few days ago the vdos-s owner posted this on twitter: https://twitter.com/katelibby/status/772876933088571392
The IP address on the tweet appears to be 154.16.180.252, which belongs to Backconnect LLC. Based on the contents of this tweet this IP address appears to have been hosting a Linux/Mirai[1] botnet C&C. Given the timing it’s likely that this is related to the attacks by vDOS against backconnect.
Perhaps vDOS and Backconnect operated competing botnets, and this is all a fight between two criminal groups. Given the background of Backconnect employees, that seems overwhelmingly likely. (Look up their CTO Marshal Webb, a FBI informant that tried to take down lulzsec)
[1] http://blog.malwaremustdie.org/2016/08/mmd-0056-2016-linuxmirai-just.html
Found another Mirai botnet c&c on blazingfast, which is another voxility VAR
vDOS did not use a botnet to launch their attacks, but servers with spoofing enabled. That much is apparent even from Krebs’ article. Therefore it’s unlikely that there’s some kind of “competing” going on between two botnet herders.
Reading the MMD article, neither the IPs provided nor the pictures match up with what this AppleJ4ck/katelibby actor has posted on Twitter.
Most likely was some kind of hoax on AppleJ4ck/katelibby’s part to create a false sense of justification. The rest of the cards are on the table – Bryant Townsend from BackConnect said that vDOS admitted to attacking them with large, continuous attacks, so they retaliated to try to break the cycle of vicious attacks.
If Bryant Townsend is doing this to defend themselves… what is his excuse for all the other BGP hijacking coming out of his AS?
This wasn’t an isolated incident. It happens all the time from them. This is not acceptable behavior from a co-called DDoS protection company.
I wonder how Cloudflare would handled the issue if both Krebs and vDOS were both clients of theirs? Would they pick sides?
Have read multiple articles on DDOSers hiding behind Cloudflare.
Good work, Brian! Keep exposing the bad guys!
Regards,
1. Why wasn’t this service shut down before? It was an easy job for law enforcement. There was no need for hacked database to be published online. They were working for years, “hiding” behind CloudFlare. FBI was able to easily get their server’s IP, access to database, etc.
2. OK, you want to be a criminal. And you provide your service to other criminals. Why would you keep all that logs? And why don’t you at least use VPN and allow your customers to use TOR or VPN? 🙂
Well, it could be that they were waiting for the miscreants to turn 18 so they could have the book thrown at them.
When someone’s 16 or 17 the authorities have been known to just keep an eye on people so the day they turn 18 they can nail them to the wall with all their “adult” activity.
Penalties are much more severe for adults vs. juveniles.
Hey krebs,
I found a possible connection ‘applej4ck’ had to other sites. The day vdos went offline so did another booter ran by the same group he is in ‘Shenron’. It seems he operated this site as well. The stresser just returns 504 gateway timeout when sending an attack. Staff are no longer responding to tickets as well..
I believe applej4ck owns and operates this site?
As Krebs stated in his previous article about the profits vDOS made, “PoodleStresser, as well as a large number of other booter services, appears to rely exclusively on firepower generated by vDOS.”
You mention that when sending an attack, Shenron gives a 504 gateway timeout. This supports the conclusion that Shenron used vDOS’a attack API to launch attacks, since it is only timing out when launching an attack.
Though it is possible that Shenron is also run by the same people who ran vDOS, given this information there is also a possibility that it’s a separate individual, or group of individuals, who are just reselling vDOS.
Applej4ck is apart of lizard squad
Shenron is a lizard squad product.
They are no longer responding to tickets.
My conclusion is it was ran by applej4ck.
It’s important not to jump to conclusions. Remember that LizardSquad was made up of more than one person – in fact 3 – 5 people at the very least.
Just because LizardStresser uses vDOS’s API doesn’t mean that it’s run by the same person. Granted, the two operators could have known each other, but in my opinion considering that Brian Krebs says that many other booters use vDOS’s API, it’s far more likely that they’re ran by different people who incidentally knew each other.
If this is true, it’s absolutely ridiculous that these crooks are still at large. How many have not been arrested?
Clearly you dont see that lizard squad was just a law enforcement front that was perpetrated by krebs and the like.
You forgot to mention lizard people and chemtrails.
– Extradition to USA & trial –
Should happen for those 2 fools, but won’t due to “Politics” etc etc !
What idiots Allowed this to continue for 4 years, & why ?
A LOT of bad people on both sides !
L U L Z++
Thanks for the articles. Makes for some very informative reading
I don’t agree with this ‘series’ one bit, don’t you have better things to be doing with your time Brian? Comparing vDos to a Russian gang is ludicrous, if you mean a ‘gang’ as in the owners, administrators and support individuals (yes, this was how vDos was structured) of the site then I suggest you invest in a copy of the Oxford Dictionary and put it on the bookshelf beside your flamboyant, over dramatized “Spam Nation” (not going to lie though, it was a good read +1). I honestly do think you should start to verge away from the world of HackForums and find more interesting stories, products (I mean, you like to compare them to the likes of Russian gangs, so who knows what you’ll call them) that don’t involve 12 year olds and their Mommy’s credit card would be a start. AppleJ4ck did not know how to program, he had limited knowledge and constantly relied on his peers to do things for him – he had one thing though, which was money. I think your articles are giving the sense that AppleJ4ck was some type of hacking extraordinaire when in reality he was not, the botnets he used – were managed by someone else, vDos’ power – was not managed by AppleJ4ck but someone else.
Sorry you disagree that this was a big deal. I sense bitterness and sour grapes in your comment. Lots of people tend to get caught up in discussions about how sophisticated or not these kids are. Frankly, I don’t care, and sophistication wasn’t something I commented on in the story. They were doing a lot of damage to a lot people, and yes, they were supplementing some attacks with botnets. But they were enabling a lot of kids who wouldn’t begin to know how to launch these attacks.
Hi stackoverflowin,
An individual’s level of infamy is not measured by how they acquired the means to do damage – rather, it is measured by the level of damage they cause to society.
An analogous example would be a mass murderer purchasing a gun and killing 20 people. Do you try to detract from the level of damage caused by saying “Oh, this individual didn’t make the gun himself, this isn’t a big story”? No, of course not.
Perhaps Brian should start to investigate your ties to AppleJ4ck and Proxseas, and how you were fronting offerings for them on HackForums.
Jospeh, you fool.
A person’s level of infamy is relative in the eye of the beholder. A bomb could go off in Germany and kill 20 people. Everyone would cast off the event as simply “horror”. Yet, I’m sure there’s militants in their cave in Pakistan questioning the choice of colour on the bomber’s jacket and then emailing the terrorists responsible some good advice on how to smuggle C4. The same way that anyone who knows anything about malware development cringes when the name “HackForums” arises. You can denigrate anyone by suggesting they have ties to that rancid spool of spastics.
There is no honour among thieves, but there is certainly authority; be it intellectual or otherwise. The damage created by an individual, in regards to information-security, is not a measurement of his capacity to procure exploits but, rather, to wield them.
So, needless to say, I’m inclined to agree with “stack”. I’m sure Brian’s use of grandiose words (with even flattering connotations in some instances – I’m sure AppleJack would be fully erect if he heard you even mutter the notion that he’s at all skilled at anything computer-related) get him lots of views and praise from pseudo-intellects. You know the kind, the ones that append “researcher” or “enthusiast” onto an, already peculiar, job title.
Still though, it’s not a case of who’s the best at running illegal services; it’s who actually does it and then reaps up the whirlwind of ignorant blessings that follow every meagre mention of their idiotic alias.
– lucky12345 (Malware Enthusiast and Security researcher with no formal qualifications – but I have a Twitter so that must mean I’m skilled)
basically stack and robert are upset because nobody ever gives them credit for the nerdy work (
i compared the logs against some game servers if interested:
pastebin.com/s4x0Fgmy
also if anyone wants the log file in JSON format i’ve uploaded here:
https://mega.nz/#F!FgtCQSQS!FQbnDI4ZjvwHCCQtctQGcw
structure is like:
“ip”: {
“line”: [
(each person attacking this ip)
]
},
I found this a very interesting comparison
First of all, thanks for your coverage.
I wanted to say i’ve found the list much less valuable that i thought it would be, for the simple reason, as stated by other people here, that many of the users who launched attacks seem to be related to other booters (and some attacks were possibly launched with the VDoS API).
So all the “resellers” logs are somehow missing, and now many of them have closed.
(in the IP address field i wonder what’s logged in the case of the API calls, does anybody have the code and knows?)
Also it seems clear to me that we’re missing a bit of the story:
1) How did you get that “dump” on the day they were arrested? Was it some kind of massive plan by the FBI, with Cloudflare playing a role as informant and Backconnect for the technical “help”.
Were you “used” as journalist to comment the operation?
2) So Cloudflare finally either helped the FBI, or was forced to do it. Why did it take years to launch that operation, and why now?
Would be great to know what Cloudflare says..
At least now bad guys will think twice before using cloudflare.
One booter network down, that’s a good news for mankind. What about the dozens still up and running, including the government sponsored ones..?
1) As I stated in the article, the database came from a source back in July. As a journalist, I am generally not privy to the what the federal authorities may or may not be investigating, as they tend not to talk about that to reporters until it’s a done deal. As for the rest of your conclusions, I can only speculate that you are likewise very far off the mark.
Brian, are you ever asked by authorities to participate further in investigations? Do you ever find yourself testifying in court (when you’re not a direct victim)?
No and no.
Would you, if given the chance, for either of these?
Backconnect admitted they worked to take down the C&C used by vdos.
And how did they gather the intelligence? That’s in the article.
And that gentleman is how this scum POS has to be handled. Internet needs more BK’s.
No, we do not need more BackConnects. In fact we need the rest of the net to snub their network traffic for hijacking a BGP route.
This would have given cyber criminals the idea that if any scummy hackers under a company banner can do it, so can they. Expect copycat situations to start happening and on a regular basis now.
Badabing posted “Internet needs more BK’s.” I assume he meant “more Brian Krebs”—unless he has a hankering for a fast food burger, and there are none in his vicinity. He did not say (nor do I think he meant) “more BlackConnects”.
Well done Brian! Hard to believe all this was happening! I’m surprised it isn’t on the tv news. Thank you for the follow-up on the last article with this one. I will definitely keep reading your articles. Very well written sir!
GreyHat, I think you misread BK (Brian Krebs) as BC BackConnect). I think we can all agree one BC is plenty.
Brian, though, should open a school…
I’m surprised to see a notably higher level of vitriol & name-calling on this story than is usual on this forum. I wonder why.
Thanks again for the reporting, Brian. Glad to see some good happen, though I also question the means employed by BackConnect.
Thanks for publishing this. It’s refreshing to see scum like this get scraped off the internet, at least symbolically. It’s a shame that they’ll cone back online soon.
The most one can do is keep shedding light on these people, until a more concrete action can be taken.
I do wonder if we are watching history in the making.
To the best of my knowledge, this is the first instance in which a deliberate route hijack has been deployed as a defensive weapon against a cyberattack. It will certainly not be the last. The Rubicon has been crossed and there is no going back.
I’m not sure…
There was some discussion about using BGP to deal w/ DNSChanger, but I think they just let ISC run the servers in-situ instead. (Sometimes, instead of relying on BGP to redirect traffic, you can knock down the doors and take over the bad guy’s computers directly…)
There’s a Stack Exchange discussion from 2014 [1] that discusses BGP as a defense.
The Italian government arranged for Hacking Team to regain control of a botnet (or similar) in 2015 [2]. That isn’t quite the same thing.
[1] http://networkengineering.stackexchange.com/questions/10857/use-bgp-to-defend-against-a-ddos-attack-originating-from-remote-as
[2] https://www.bishopfox.com/blog/2015/08/an-overview-of-bgp-hijacking/
I’m not sure…
There was some discussion about using BGP to deal w/ DNSChanger, but I think they just let ISC run the servers in-situ instead. (Sometimes, instead of relying on BGP to redirect traffic, you can knock down the doors and take over the bad guy’s computers directly…)
There’s a Stack Exchange discussion from 2014 [1] that discusses BGP as a defense.
The Italian government arranged for Hacking Team to regain control of a botnet (or similar) in 2015 [2]. That isn’t quite the same thing.
[1] http://networkengineering.stackexchange.com/questions/10857/use-bgp-to-defend-against-a-ddos-attack-originating-from-remote-as
[2] https://www.bishopfox.com/blog/2015/08/an-overview-of-bgp-hijacking/
What kind of information were they storing about payments? Are they really that stupid?
Brian, thank you for the great article. Do you think the buyers will be punished? I truly hope they will be in some way..