vDOS — a “booter” service that has earned in excess of $600,000 over the past two years helping customers coordinate more than 150,000 so-called distributed denial-of-service (DDoS) attacks designed to knock Web sites offline — has been massively hacked, spilling secrets about tens of thousands of paying customers and their targets.
The vDOS database, obtained by KrebsOnSecurity.com at the end of July 2016, points to two young men in Israel as the principal owners and masterminds of the attack service, with support services coming from several young hackers in the United States.
To say that vDOS has been responsible for a majority of the DDoS attacks clogging up the Internet over the past few years would be an understatement. The various subscription packages to the service are sold based in part on how many seconds the denial-of-service attack will last. And in just four months between April and July 2016, vDOS was responsible for launching more than 277 million seconds of attack time, or approximately 8.81 years worth of attack traffic.
Let the enormity of that number sink in for a moment: That’s nearly nine of what I call “DDoS years” crammed into just four months. That kind of time compression is possible because vDOS handles hundreds — if not thousands — of concurrent attacks on any given day.
Although I can’t prove it yet, it seems likely that vDOS is responsible for several decades worth of DDoS years. That’s because the data leaked in the hack of vDOS suggest that the proprietors erased all digital records of attacks that customers launched between Sept. 2012 (when the service first came online) and the end of March 2016.
HOW vDOS GOT HACKED
The hack of vDOS came about after a source was investigating a vulnerability he discovered on a similar attack-for-hire service called PoodleStresser. The vulnerability allowed my source to download the configuration data for PoodleStresser’s attack servers, which pointed back to api.vdos-s[dot]com. PoodleStresser, as well as a large number of other booter services, appears to rely exclusively on firepower generated by vDOS.
From there, the source was able to exploit a more serious security hole in vDOS that allowed him to dump all of the service’s databases and configuration files, and to discover the true Internet address of four rented servers in Bulgaria (at Verdina.net) that are apparently being used to launch the attacks sold by vDOS. The DDoS-for-hire service is hidden behind DDoS protection firm Cloudflare, but its actual Internet address is 82.118.233.144.
vDOS had a reputation on cybercrime forums for prompt and helpful customer service, and the leaked vDOS databases offer a fascinating glimpse into the logistical challenges associated with running a criminal attack service online that supports tens of thousands of paying customers — a significant portion of whom are all trying to use the service simultaneously.
Multiple vDOS tech support tickets were filed by customers who complained that they were unable to order attacks on Web sites in Israel. Responses from the tech support staff show that the proprietors of vDOS are indeed living in Israel and in fact set the service up so that it was unable to attack any Web sites in that country — presumably so as to not attract unwanted attention to their service from Israeli authorities. Here are a few of those responses:
(‘4130′,’Hello `d0rk`,\r\nAll Israeli IP ranges have been blacklisted due to security reasons.\r\n\r\nBest regards,\r\nP1st.’,’03-01-2015 08:39),
(‘15462′,’Hello `g4ng`,\r\nMh, neither. I\’m actually from Israel, and decided to blacklist all of them. It\’s my home country, and don\’t want something to happen to them :)\r\n\r\nBest regards,\r\nDrop.’,’11-03-2015 15:35),
(‘15462′,’Hello `roibm123`,\r\nBecause I have an Israeli IP that is dynamic.. can\’t risk getting hit/updating the blacklist 24/7.\r\n\r\nBest regards,\r\nLandon.’,’06-04-
2015 23:04), (‘4202′,’Hello `zavi156`,\r\nThose IPs are in israel, and we have all of Israel on our blacklist. Sorry for any inconvinience.\r\n\r\nBest regards,\r\nJeremy.’,’20-05-
2015 10:14), (‘4202′,’Hello `zavi156`,\r\nBecause the owner is in Israel, and he doesn\’t want his entire region being hit offline.\r\n\r\nBest regards,\r\nJeremy.’,’20-05-
2015 11:12), (‘9057′,’There is a option to buy with Paypal? I will pay more than $2.5 worth.\r\nThis is not the first time I am buying booter from you.\r\nIf no, Could you please ask AplleJack? I know him from Israel.\r\nThanks.’,’21-05-
2015 12:51), (‘4120′,’Hello `takedown`,\r\nEvery single IP that\’s hosted in israel is blacklisted for safety reason. \r\n\r\nBest regards,\r\nAppleJ4ck.’,’02-
09-2015 08:57),
WHO RUNS vDOS?
As we can see from the above responses from vDOS’s tech support, the owners and operators of vDOS are young Israeli hackers who go by the names P1st a.k.a. P1st0, and AppleJ4ck. The two men market their service mainly on the site hackforums[dot]net, selling monthly subscriptions using multiple pricing tiers ranging from $20 to $200 per month. AppleJ4ck hides behind the same nickname on Hackforums, while P1st goes by the alias “M30w” on the forum.
vDOS appears to be the longest-running booter service advertised on Hackforums, and it is by far and away the most profitable such business. Records leaked from vDOS indicate that since July 2014, tens of thousands of paying customers spent a total of more than $618,000 at the service using Bitcoin and PayPal.
Incredibly, for brief periods the site even accepted credit cards in exchange for online attacks, although it’s unclear how much the site might have made in credit card payments because the information is not in the leaked databases.
The Web server hosting vDOS also houses several other sites, including huri[dot]biz, ustress[dot]io, and vstress[dot]net. Virtually all of the administrators at vDOS have an email account that ends in v-email[dot]org, a domain that also is registered to an Itay Huri with a phone number that traces back to Israel.
The proprietors of vDOS set their service up so that anytime a customer asked for technical assistance the site would blast a text message to six different mobile numbers tied to administrators of the service, using an SMS service called Nexmo.com. Two of those mobile numbers go to phones in Israel. One of them is the same number listed for Itay Huri in the Web site registration records for v-email[dot]org; the other belongs to an Israeli citizen named Yarden Bidani. Neither individual responded to requests for comment.
The leaked database and files indicate that vDOS uses Mailgun for email management, and the secret keys needed to manage that Mailgun service were among the files stolen by my source. The data shows that vDOS support emails go to itay@huri[dot]biz, itayhuri8@gmail.com and raziel.b7@gmail.com.
LAUNDERING THE PROCEEDS FROM DDOS ATTACKS
The $618,000 in earnings documented in the vDOS leaked logs is almost certainly a conservative income figure. That’s because the vDOS service actually dates back to Sept 2012, yet the payment records are not available for purchases prior to 2014. As a result, it’s likely that this service has made its proprietors more than $1 million.
vDOS does not currently accept PayPal payments. But for several years until recently it did, and records show the proprietors of the attack service worked assiduously to launder payments for the service through a round-robin chain of PayPal accounts.
They did this because at the time PayPal was working with a team of academic researchers to identify, seize and shutter PayPal accounts that were found to be accepting funds on behalf of booter services like vDOS. Anyone interested in reading more on their success in making life harder for these booter service owners should check out my August 2015 story, Stress-Testing the Booter Services, Financially.
People running dodgy online services that violate PayPal’s terms of service generally turn to several methods to mask the true location of their PayPal Instant Payment Notification systems. Here is an interesting analysis of how popular booter services are doing so using shell corporations, link shortening services and other tricks.
Turns out, AppleJ4ck and p1st routinely recruited other forum members on Hackforums to help them launder significant sums of PayPal payments for vDOS each week.
“The paypals that the money are sent from are not verified,” AppleJ4ck says in one recruitment thread. “Most of the payments will be 200$-300$ each and I’ll do around 2-3 payments per day.”
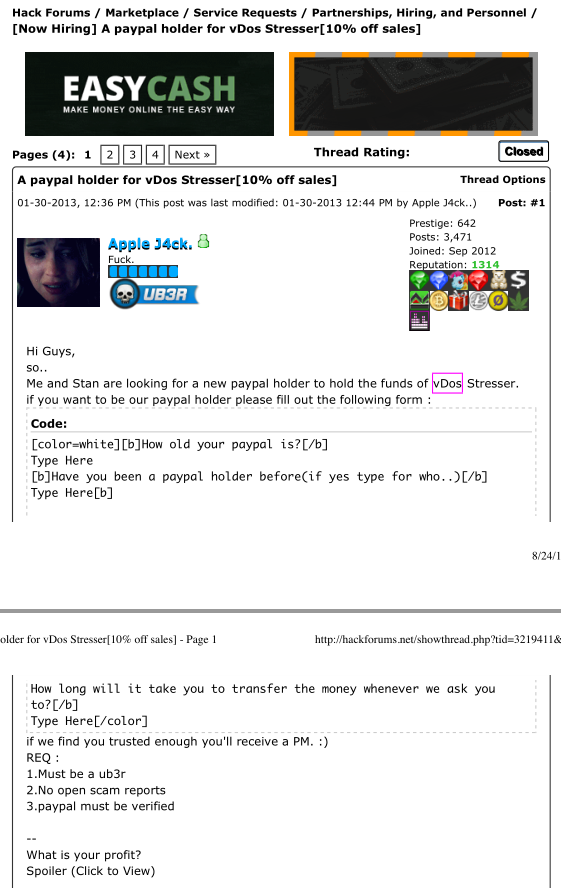
vDos co-owner AppleJ4ck recruiting Hackforums members to help launder PayPal payments for his booter service.
It is apparent from the leaked vDOS logs that in July 2016 the service’s owners implemented an additional security measure for Bitcoin payments, which they accept through Coinbase. The data shows that they now use an intermediary server (45.55.55.193) to handle Coinbase traffic. When a Bitcoin payment is received, Coinbase notifies this intermediary server, not the actual vDOS servers in Bulgaria.
A server situated in the middle and hosted at a U.S.-based address from Digital Ocean then updates the database in Bulgaria, perhaps because the vDOS proprietors believed payments from the USA would attract less interest from Coinbase than huge sums traversing through Bulgaria each day.
ANALYSIS
The extent to which the proprietors of vDOS went to launder profits from the service and to obfuscate their activities clearly indicate they knew that the majority of their users were using the service to knock others offline.
Defenders of booter and stresser services argue the services are legal because they can be used to help Web site owners stress-test their own sites and to build better defenses against such attacks. While it’s impossible to tell what percentage of vDOS users actually were using the service to stress-test their own sites, the leaked vDOS logs show that a huge percentage of the attack targets are online businesses.
In reality, the methods that vDOS uses to sustain its business are practically indistinguishable from those employed by organized cybercrime gangs, said Damon McCoy, an assistant professor of computer science at New York University.
“These guys are definitely taking a page out of the playbook of the Russian cybercriminals,” said McCoy, the researcher principally responsible for pushing vDOS and other booter services off of PayPal (see the aforementioned story Stress-Testing the Booter Services, Financially for more on this).
“A lot of the Russian botnet operators who routinely paid people to infect Windows computers with malware used to say they wouldn’t buy malware installs from Russia or CIS countries,” McCoy said. “The main reason was they didn’t want to make trouble in their local jurisdiction in the hopes that no one in their country would be a victim and have standing to bring a case against them.”
The service advertises attacks at up to 50 gigabits of data per second (Gbps). That’s roughly the equivalent of trying to cram two, high-definition Netflix movies down a target’s network pipe all at the same moment.
But Allison Nixon, director of security research at business risk intelligence firm Flashpoint, said her tests of vDOS’s service generated attacks that were quite a bit smaller than that — 14 Gbps and 6 Gbps. Nevertheless, she noted, even an attack that generates just 6 Gbps is well more than enough to cripple most sites which are not already protected by anti-DDoS services.
And herein lies the rub with services like vDOS: They put high-powered, point-and-click cyber weapons in the hands of people — mostly young men in their teens — who otherwise wouldn’t begin to know how to launch such attacks. Worse still, they force even the smallest of businesses to pay for DDoS protection services or else risk being taken offline by anyone with a grudge or agenda.
“The problem is that this kind of firepower is available to literally anyone willing to pay $30 a month,” Nixon said. “Basically what this means is that you must have DDoS protection to participate on the Internet. Otherwise, any angry young teenager is going to be able to take you offline in a heartbeat. It’s sad, but these attack services mean that DDoS protection has become the price of admission for running a Web site these days.”
Stay tuned for the next piece in this series on the hack of vDOS, which will examine some of the more interesting victims of this service.




wow. If only people used their skills for good…
Nice, any chance you could check few victim IP’s? Very interested as for who attacked them.
No, not at the moment. But I’m toying with the idea of publishing the entire attack list with timestamps, attack size, etc. If I do that, you’ll be able to look it up yourself.
I don’t see much wrong in publishing the victim IP list with timestamps.
I agree. But as I mentioned at the end of this already very long story, that’s fodder for another piece in this series 🙂
Many of the targets will be backend servers the owners of which attempted to prevent attacks via cloudflare/sucuri/other service here. While one or a few skiddies already found the real ip, there’s not much benefit of making it easier for the next attacker.
I’d say it’s worth stripping out domain info / similar before publishing
I’m waiting the next installments with bated breath, and so do some friends of mine who were befallen with lasting dDOS attacks. However, much of the traffic came from Amazon Web Services rather than Cloudflare.
Great idea. Please do !
That would be very interesting who they attacked.
Dont they have a skype resolver or something like that too that you can publish any logs?
You are looking for extra cost on your anti DDOS filters ?
This would be pretty cool to see.
Dejar Mr. Krebs
Excellent reporting.
Hope you go with the idea of publishing that who’s who, so attacked sites can really know what happened and attackers would also need some explanation to do.
You have a moral responsibility now that you have this information to let the rest of the world know too whereas your reputation would only increase.
It looks like Cyber crime, so whom or what starts the investigate/prosecute on behalf of the Web et al?
Not sure that there’s a connection, but
found some ties to deobfuscated.com/databases
(Whois classified) which contain hundred of hacked accounts files ,
some with sql injection command.
What happens to the funds confiscated by or the funds frozen by Paypal when an account is identified as belonging to a user who violates their terms of service?
They generally hold for 6 months then release them. I don’t think they can confiscate the funds without criminal proceedings.
I’m not certain these days. I know they would freeze the account until and unless the person who owned it provided some documentation about who they were in real life. As you can imagine, most times the people using these accounts for money laundering and for DDoS-for-hire services are unwilling to come forward, and end up writing it off as a loss.
But really, the person to ask about this is Damon McCoy, the academic quoted in this story. Hopefully, he can weigh in on this.
Tiny thing: “tends of thousands”
Hopefully this will spur the Israeli wheels of justice to focus on this group.
“The DDoS-for-hire service is hidden behind DDoS protection firm Cloudflare”
This is infuriatingly common, and it by itself has turned my opinion of Cloudflare to the negative. They just don’t care about hiding services like this because they get money from both ends.
I believe most of these types of sites are utilizing the Free plan. Matthew Prince had mentioned that when questioned on ISIS related sites. I would expect a similar situation for Booters. They don’t need the paid plan features, as their sites are purely marketing fronts. So unless these specific sites are reported, it’s very difficult to vet every free site for its content.
Cloudflare ignores DMCA reports. It does the absolute minimum (forwarding the report to the upstream provider, which might be the criminal themselves) even though they are providing the DNS services for the criminal websites (there are music/film/software piracy/childporn sites that have been up for years.) Cloudflare claims to be the good guy, but it feels exactly the same as reporting cheaters in MMORPG games, nobody wants to do anything because they earn money from the bad guys.
If there was ever an argument for changing how DMCA liability works, Cloudflare, aka crimeflare, would be at the top of the list.
Do you think there is any way to use the attack history on a police case against them? I know for sure that they attacked my services but since that are just some lines from some database it dosent seem to be valid proof at all?
Well, you can match your logs with theirs. If the time stamps and attack type and IP address line up, that’s a pretty good match. Whether or not that would be admissible in a court of law is another story.
Expert witness testimony from someone like you would probably be crucial, to build the case. Watch for these kinds of cases to end up in court more and more as time goes by with cyber-criminals continuing to exploit the “Wild West” atmosphere.
It’s probably more an evidence chain-of-custody issue than an expert attesting to what it is.
Looks like the v-mail[dot]org domain is protected by WhoisGuard now. Itay Huri also owns dealstation.us. The WHOIS information is not protected and references an address and phone in Israel. Maybe the same guy?
http://whois.domaintools.com/dealstation.us
Brian, how many times did you find your own site in the target DDoS URL columns?
I bet quite a few.
My site is listed in vDOS attack logs at least four times in just the past few months. Nice thing about that is I actually have detailed files from Prolexic/Akamai about each attack, so this should be fun.
Now that you’ve named these guys, it leaves questions open.
Can their actions be prosecuted in/by Israel? Or would Israel prosecute them only if they attacked IPA’s inside Israel? etc…
I guess we will see 🙂 But when you make that much money in BTC, there’s a tendency not to report it to authorities. At the very least I’d think the Israeli tax authorities would be interested.
According to their once used EV certificate, they were incorporated under the legal name “VS NETWORK SERVICES LTD” in the UK. The company is now dissolved.
Links:
https://crt.sh/?id=7475563
https://beta.companieshouse.gov.uk/company/09586775
Well, that’s how the FBI nailed Al Capone — income tax invasion. Whatever does the job, so why not?
Are they using malware zombies to launch the attacks? They must be. That would seem make the question of the “stressor” product, as a legitimate offer, moot and open them to prosecution. I am guessing that the source did not get his hands on zombie control servers? But they have to be linked to the commerce system by some kind of automation.
No. The servers in Bulgaria or wherever Verdina.net keeps them would coordinate the attacks, which mostly used reflective, amplification attacks like NTP, DNS, etc. These sorts of methods let you launch very large attacks with just a handful of powerful servers at the ready.
Those are crazy numbers if accurate. Be careful Brian. You’re getting deeper into their world with each piece. Very impressive journalism and just tremendous work you do. You’re the Woodward and Bernstein of the Internet Age. Get this man a Pulitzer. Honestly.
We would also very much like to see the databases that were recovered. I am thinking that a trail from victim to service purchaser would be possible. In some cases I think the person booking the DDOS would be doing so for someone else. And linking the activity back to the real party responsible would be priceless.
please and thank you?
Strange that a U.S. company like Cloudflare would not consider a relationship with a DDOS-for-hire business a conflict of interest. Seemingly, it could be perceived that Cloudflare could actually utilize such services to boost their own claims in stopping ‘record attacks’ against “clients”. IMHO, that just stinks.
Sorry to say, but this is the first thing that came to my mind also. Surely not behind all, but could be behind some.
Any chance of ‘Booter Nation’ coming out soon?
Oh man. Call Starkist.
https://www.youtube.com/watch?v=5U5UH1kQeUA
“The service advertises attacks at up to 50 gigabits of data per second (Gbps). That’s roughly the equivalent of trying to cram two, high-definition Netflix movies down a target’s network pipe all at the same moment.”
Brian,
The above statement is so wildly inaccurate and misleading, that I’m forced to call your attention to it.
It *might* have been slighly more accurate to say “…down a target’s network pipe every second” but even that modified statement would have served more to mislead and confuse than to clarify.
1080p Blu-Ray disks contain content which can range in size from about 20 gigaBYTES up to in excess of 40 gigaBYTES, for double-layer Blu-Rays. (Note: That’s BYTES not BITS.)
But even ignoring the difference between bits and bytes (x8), for most people your statement gives readers no useful point of reference which even vaguely relates to their own experience, e.g. in streaming high-def movies.
The Blu-Ray specification mandates that the maximum bitrate of the combined (compressed) audio and video on a Blu-Ray disk shall not exceed 54 megaBITS per second. In practice, the combined video+audio bitrate for most Blu-Ray content typically averages a bitrate which is only perhaps half of that maximum allowed rate. For convenience, we can say the average Blu-Ray bitrate is 25 megaBITS per second. Thus, if attackers could send down a stream of 50 gigabits/second this is actually to say that they could send down the equivalent of TWO THOUSAND simultaneous Blu-Ray video+audio streams to the victim.
But that’s just a figure based on actual Blu-Ray data coming off an actual local Blu-Ray disk. Streaming services such as Netflix actually apply further compression to their “high def” content so as to further reduce the bandwidth requirements, and dramatically so. The official Netflix recommendation for their high-def streaming service is that customers should have down-link bandwidth of at least 7 megabits per second. (In practice, I’ve had complete success using Netflix high-def streaming with only a 6 megabit/second downlink.)
The bottom line is that if you had wanted to relate the maximum DDoS attack strength possible with this service to something that most of your readers could actually relate to, and that they actually have direct experience with, then it would have been better to say that the maximum attack strength available from this dubious service was/is the equivalent of sending about SEVEN THOUSAND Netflix high-def streams to the victim, all simultaneously.
Expressing the maximum attack strength in this way should give readers a better appreciation of just how devastating such an attack could actually be, e.g. for a small or medium sized business.
Wow, thanks, Ron. I learned a lot there. I read the whole darn thing. Your desire for exactitude is a beautiful (if sometimes maddening) thing.
I’d wanted to call you to get your take because I knew you would know. But you’re a total vampire and don’t operate on any schedules useful for someone trying to not work all night. Alas, I am just going to have to figure out a creative way to wake you up earlier in the day. 🙂
Ah, yup. Here I am on lunch break. http://bit.ly/2cdWyw5
But seriously, none of you young’uns, born after about 1960 or so, will ever really know what it was like, back in the early daze of computing (e.g. 1970’s), when the only time the serious hackerz of that era could get machine time to do either serious work or play was in the middle of the night, after the day’s productions runs on the mainframe had finished. Back in the day, any and all folks who were actually serious about this bizness were *all* hard-core night owls. In my case the habit just never wore off.
Anyway, I just had to make sure your readers had a clear feel for just how bad this DDoS-for-hire service you found & exposed really is/was. (Is it still up after your report? I can’t imagine why it wouldn’t be, but I haven’t checked.) Given the 50 gigabit/sec figure you cited, that horrid service had/has the capacity to utterly annihilate a typical DSL line 7,000 times over. And a typical modest dedicated box in a data center with 1Gbps bandwidth would also easily be crushed into absolute invisibility.
As a practical matter, direct (non-spoofed) attacks can usually be dealt with by most competent providers, provided that the number of actual packet sources is not too awfully big. But sizable botnets can still cause great problems without even spoofing the packet source addresses.
The MUCH bigger problem is spoofed source IP reflection attacks.
Like any other self-inflicted human problem (e.g. global warming) this problem will only ever be solved when a sufficient number of people stand up and start demanding that the problem be solved. First however it has to be established which specific networks connected to the Internet are causing the problem, i.e. which networks allow their own end users to spoof their IP addresses. And for this part of the problem individual end users from all over the world can and should help with the data gathering. I strongly encourage everyone who wants to do their small part in this war to visit the following URL, download the client, and help the Internet community at large to at least figure out where the “bad” networks are. That is the first step on the road towards eliminating this (DDoS) problem once and for all.
https://www.caida.org/projects/spoofer/
Erm, 50gigabits is about 6.25GB, which sounds like about the size of two high-definition Netflix movies.
So while the analogy is a bit awkward, it doesn’t seem inaccurate to me: 50gbps is about the amount of bandwidth needed to send two high definition netflix movies in a single second, No?
The Capital and Lower Case B/b is where this gets confusing for people. Gotta multiply or divide by 8 to get on the same sizing and people forget.
I’m not a user of Netflix or any similar service so I may be mistaken, but here goes: Netflix provides streams, not downloads, so it’s not appropriate to make reference to a download from Netflix of files with a combined size of however many gigabytes. A Netflix customer, I imagine, would be more likely to comprehend the number of programs s/he would be trying to stream at once, and the running time of each of those programs is irrelevant.
There is no technical difference between streaming and downloading except that in streaming, the aim is not to save to permanent storage, and in fact several ecosystems actively try to prevent saving via DRM.
Yes, but you’re forgetting that when you’re using Gigabytes as a measure of total data and not data rate, then that’s equivalent to sending the entirety of 2 Netflix movies at ONCE (the whole movie not a stream) within a second to the receiver. It’s better to use Gigabits/s and compare that to Netfix’s streaming rate which is probably close to 7 Megabit/s. So like the user above said, that would be like sending 7,000 Netflix streams simultaneously to the recipient.
Hint: Brian didn’t say sending DVDs down the pipe, but Netflix. Netflix uses (currently) MPEG-4 (Part 10) for encoding. It doesn’t take too much effort to find out that their average bit rate per customer watching HD content is 4-5 megabits per second. Take an average movie at 90 minutes. 5 mb/sec * 3600 * 1.5 = 3.375 GB per second. 50 gb/sec equals 6.250 GB/sec. So, Bryan was close to what he quoted on Netflix.
Additionally, Netflix doesn’t start with BluRay for their encoding, because (simply) that would be cascading strong compression with strong compression, which generally results in unwatchable content and might be suitable for free porn. Netflix, for several years, starts with a master in the IMF (Intermediate Master Format) which is a low-level “mezzanine” compression format. Before that, Netflix would often start with an uncompressed media format, such as HD-SDI (1.5 gb/sec).
Note: I haven’t rounded any numbers, but I didn’t take the time or trouble to convert 1000 to 1024 for my calculation. (1 megabit is actually 1,048,576 bits.)
Oops! I forgot to add… “Nonetheless, I really liked this article, and as always, I greatly appreciate your investigation skills and your ability and willingness to get this kind of story out and in front of a wider audience.”
Honestly, I wouldn’t want to be running a small or medium business on the Internet these days, or even a big one, now that I think of it. (Hello Sony Pictures!) It’s just too damn dangerous. Good people are working hard to try to fix the spoofing/reflection problem, but it’s a hard problem, not technically, but more politically. Getting all network operators to Do The Right Thing (and implement BCP 38) is not materially different from the problem of hearding cats.
Right. Which is why the next story has to be about which hosting firms are enabling the booter market – by spinning off “resellers” that they control, just to distance themselves from any abuse complaints generated by the dodgy clientele they are courting.
What is to be gained by the individuals paying for a DOS attack? That is a lot of money being spent.
There is the old saying of “follow the money.” Just as important is the answer to the question “Why is they money being spent?”
“What is to be gained by the individuals paying for a DOS attack?”
Google for “DDoS” and “extortion” and start reading. This can be (and is), sadly, a lucrative and highly profitable enterprise on the modern Internet.
The Internet has become the cyber-equivalent of a lonely isolated stretch of Highway 101 in Mexico:
http://n.pr/2ce38D8
“Today, kidnappings and carjackings are so frequent, federal police officers escort drivers in armed convoys…”
The only difference between the deserted stretches of Mexico Highway 101 and the modern Internet is that when it comes to Internet DDoS attacks, there are any number of *companies* nowadays… NOT police, but commercial for-profit *companies*… who will be only too happy to sell you “protection” from the roving bands of bandidos. (The ethics of some of these companies… specifically the ones who are also and simultaneously providing protection to the DDoSers as well… is left as an exercise for the reader.)
…and don’t forget well-off kids (my definition of kid is “anyone without young kids themselves”) kicking game adversaries of the net.
How is it legal for you to post internal data from a leaked database online?
it’s not.
Troy hunt never did anything like that, how do you justify it?
Are you kidding me? Are you a friend of them?
It’s like releasing the death note of a serial killer. How is it a crime to let people know of criminals victims?
Troy Hunt deals with passwords. If he releases the leaks, he’ll get thousands of people who use their passwords on other websites hacked.
And he does release the safe parts of the data he has, on haveibeenpwned.
Krebs deals with… less sensitive info, usually.
Great job!
I own one of the biggest hosting companies in Israel and am very interested with some more details about the targets of the attacks.
If i find any of my IPs as target for attacks, I will file a law-suite against them, forcing them to court – seems like their nightmare.
Great job but i still think that all data should be published with an opt-out option for those who can prove the risk and ownership on the resource being published.
Noam, as I mentioned in the article, their service was configured so that it could not attack Israeli internet addresses.
I agree with those who said you should publish the list of targets+timestamps.
I’m sure they would all like to know they’ve been a target.
Also i’m sure Krebs would like to see these guys arrested, and if there are some big companies in the list or israeli sites (hosted outside of israel), then they will be surely in trouble.
Your wish is granted.
http://krebsonsecurity.com/2016/09/alleged-vdos-proprietors-arrested-in-israel/
Well, it is true that $20 anonymous attacks were denied in their system but be sure that $10 BTC attacks are welcome and the owners took personal care about those customers.
The guys are now arrested and soon they will be sent to the US, I am not sure that the $600k they made worth the 25 years in federal prison.
Noam, would love to speak with you a bit and see if we can potentially work together. -Nicole
Thank you Nicole, I prefer CloudFlare over Incapsula, for many many good reasons.
How come hackforum’s admin (Omni) isn’t getting arrested over allowing people to sell these kind of services on his site?
hoping you reply to this
You are naive! Police need proofs .criminals have money good lawels.. now days its very difficult to proof ..
As also people who will undestood how tge world works system they will be so exited about this rigged world system that they never fight against!
>> The proprietors of vDOS set their service up so that anytime a customer asked for technical assistance the site would blast a text message to six different mobile numbers tied to administrators of the service
Well, then it would serve them right if someone were to spam-bomb their support email.
I work for a ISP and I am pretty interested in seeing if any of the logs show any of my customers.
I also work for an ISP and we get several attacks per week.
Would be very interested to see if our IP ranges appear in the lists.
Sounds like the Israelis are running a protection racket. Either buy DDOS “protection” or something bad happens to your server!
Back in the day there was sexxygirls.com (or some such site) – they made the news because Canadians were getting $3k phone bills for using 900 nuber dial ups – thanks to malware they were getting. Hmmm – I wonder who hosts them? WE DO! Pack up the server and send to the RCMP and we’ll stay out the news, and we did. The point is that they paid the bill, on time, every month. Cloudflare takes money from anyone who pays on time.
take a look at this security article written by Mr. Huri on the subject of DOS ( use google translate..)
http://www.digitalwhisper.co.il/files/Zines/0x4B/DW75-4-AmplifiedDDoS
Yep. That actually was posted very recently. That is some serious hubris. Huri says he’s about to be drafted into the Israeli Defense Forces. His pal Yarden/AppleJ4ck is a couple of years older.
Do you know where specifically he’s getting drafted to?
That’d be interesting if he’s drafted into a technological position within the military.
Israeli Defense Force. Military service is mandatory in Israel.
The link returns 404. This is the link to the PDF magazine
http://www.digitalwhisper.co.il/files/Zines/0x4B/DW75-4-AmplifiedDDoS.pdf
It may not last long 🙂
Local media reports two of them have been arrested on Thursday as a result of a request by the FBI.
http://www.themarker.com/technation/1.3063772
People used that site to test their own sites, when you pay a lot of money for DDoS protection you’re going to check everything is working correctly.
I’d be surprised if the two were arrested, you can’t illegal obtain evidence in most countries and prosecute people with it.
I guess the bigger concern here is the threat to release people’s personal information that was obtained illegally. Reminds me of the Ashley Madison leak, what good can come of it.
Oh really?
“when you pay a lot of money for DDoS protection”
So you pay a lot of money for DDoS protection but can only afford a $20/m SST service from “hackforums”?
99% you would be even violating your hosting provider terms of service when you launch a DDoS attack to check your protection. At the very least you would need an approval from them, and the attack should be from legit source who give you their permission to do so, not from hijacked IP’s.
And jokes on you, they already got arrested.
About “releasing people’s personal information”, hundreds of big websites, if not thousands, get hacked yearly, and their databases get dumped and leaked.
If you aren’t doing anything illegal, you’ll have nothing to worry about.
If you are, on the other hand, I can understand why you would be worry.
Brian,
FBI huh? Well, they are the responsibly agency now. Shouldn’t the NSA have caught these folks a while back? I think there’s more to the story. Whoever started funding this business is or until now was being watched. I have to wonder how high up this goes.
I try to follow the money. I doubt we will ever really find out.
Seriously, its easy to track who did what. Even with a distributed botnet when you can collect all the traffic. Politics and money folks.
Brian, I hope your sources aren’t simply using you to bust this ring because the FBI hit a dead end. Please stay safe and be careful not to dig too deep.
https://bgpstream.com/event/11463
https://bgpstream.com/event/16276
https://bgpstream.com/event/21051
https://bgpstream.com/event/3177
https://bgpstream.com/event/32572
Not the first time bryant townsend has operated a bgp hijack. Saw someone posted this and it got deleted but take a look at all the suspected hijacks.