As KrebsOnSecurity observed over the weekend, the source code that powers the “Internet of Things” (IoT) botnet responsible for launching the historically large distributed denial-of-service (DDoS) attack against KrebsOnSecurity last month has been publicly released. Here’s a look at which devices are being targeted by this malware.
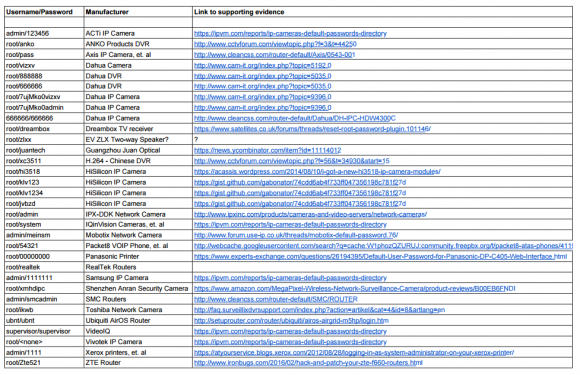
The malware, dubbed “Mirai,” spreads to vulnerable devices by continuously scanning the Internet for IoT systems protected by factory default usernames and passwords. Many readers have asked for more information about which devices and hardware makers were being targeted. As it happens, this is fairly easy to tell just from looking at the list of usernames and passwords included in the Mirai source code.
In all, there are 68 username and password pairs in the botnet source code. However, many of those are generic and used by dozens of products, including routers, security cameras, printers and digital video recorder (DVRs).
I examined the less generic credential pairs and tried to match each with a IoT device maker and device type. As we can see from the spreadsheet above (also available in CSV and PDFformats), most of the devices are network-based cameras, with a handful of Internet routers, DVRs and even printers sprinkled in.
I don’t claim to have special knowledge of each match, and welcome corrections if any of these are in error. Mainly, I turned to Google to determine which hardware makers used which credential pairs, but in some cases this wasn’t obvious or easy.
Which is part of the problem, says Will Dormann, senior vulnerability analyst at the CERT Coordination Center (CERT/CC).
“Even when users are interested in and looking for this information, the vendor doesn’t always make it easy,” Dormann said.
Dormann said instead of hard-coding credentials or setting default usernames and passwords that many users will never change, hardware makers should require users to pick a strong password when setting up the device.
Indeed, according to this post from video surveillance forum IPVM, several IoT device makers — including Hikvision, Samsung, and Panasonic — have begun to require unique passwords by default, with most forcing a mix of upper and lowercase letters, numbers, and special characters.
“As long as the password can’t be reversed — for example, an algorithm based off of a discoverable tidbit of information — that would be a reasonable level of security.” Dormann said.
Some readers have asked how these various IoT devices could be exposed if users have configured them to operate behind wired or wireless routers. After all, these readers note, most consumer routers assign each device inside the user’s home network so-called Network Address Translation (NAT) addresses that cannot be directly reached from the Internet.
But as several readers already commented in my previous story on the Mirai source code leak, many IoT devices will use a technology called Universal Plug and Play (UPnP) that will automatically open specific virtual portholes or “ports,” essentially poking a hole in the router’s shield for that device that allows it to be communicated with from the wider Internet. Anyone looking for an easy way to tell whether any of network ports may be open and listening for incoming external connections could do worse than to run Steve Gibson‘s “Shields Up” UPnP exposure test.
HELP! I NEVER CHANGED THE DEFAULT PASSWORD!
Regardless of whether your device is listed above, if you own a wired or wireless router, IP camera or other device that has a Web interface and you haven’t yet changed the factory default credentials, your system may already be part of an IoT botnet. Unfortunately, there is no simple way to tell one way or the other whether it has been compromised.
However, the solution to eliminating and preventing infections from this malware isn’t super difficult. Mirai is loaded into memory, which means it gets wiped once the infected device is disconnected from its power source.
But as I noted in Saturday’s story, there is so much constant scanning going on for vulnerable systems that IoT devices with default credentials can be re-infected within minutes of a reboot. Only changing the default password protects them from rapidly being reinfected on reboot.
My advice for those running devices with the default credentials? First off, make sure you know how to access the device’s administration panel. If you’re unsure how to reach the administration panel, a quick search online for the make and model of your device should reveal an address and default credential pair that can be typed or pasted into a Web browser.
If possible, reset the device to the factory-default settings. This should ensure that if any malware has been uploaded to the device that it will be wiped permanently. Most devices have a small, recessed button that needs to be pressed and held down for a several seconds while powered on to reset the thing back to the factory default settings.
When the device comes back online, quickly fire up a Web browser, navigate to the administration panel, enter the default credentials, and then change the default password to something stronger and more memorable. I hope it goes without saying that any passwords remotely resembling the default passwords noted in the image above are horrible passwords. Here’s some advice on picking better ones.
Unfortunately, many of these devices also require periodic software or “firmware” updates to fix previously unknown security vulnerabilities that the vendor discovers or that are reported to the hardware maker post-production. However, relatively few hardware makers do a good job of making this process simple and easy for users, let alone alerting customers to the availability of firmware updates.
“When it comes to software updates, automatic updates are good,” Dormann said. “Simple updates that notify the user and require intervention are okay. Updates that require the user to dig around to find and install manually are next to worthless. Devices that don’t have updates at all are completely worthless. And that can be applied to traditional computing as well. It’s just that with IoT, you likely have even-less-technical users at the helm.”
Only after fixing any problems related to default credentials should readers consider checking for firmware updates. Some hardware makers include the ability to check for updates through a Web-based administration panel (like the one used to change the device’s default password), while others may only allow firmware updates manually via downloads from the manufacturer’s site.
Firmware updates can be tricky to install, because if you fail follow the manufacturer’s instructions to the letter you may end up with little more than an oversized paperweight. So if you decide to go ahead with any firmware updates, please do so carefully and deliberately.
BUT WAIT, THERE’S MORE
Several readers have pointed out that while advising IoT users to change the password via the device’s Web interface is a nice security precaution, it may or may not address the fundamental threat. That’s because Mirai spreads via communications services called “telnet” and “SSH,” which are command-line, text-based interfaces that are typically accessed via a command prompt (e.g., in Microsoft Windows, a user could click Start, and in the search box type “cmd.exe” to launch a command prompt, and then type “telnet” <IP address> to reach a username and password prompt at the target host).
The trouble is, even if one changes the password on the device’s Web interface, the same default credentials may still allow remote users to log in to the device using telnet and/or SSH.
Brian Karas, a business analyst with IPVM — a subscription-based news, testing and training site for the video surveillance industry — said in his experience often times IP camera users can change whatever settings they want in the device’s Web interface, but that’s no guarantee the changes will affect how the device can be accessed via Telnet or SSH.
“The problem is there’s no hard and fast rule,” Karas said. “What often happens is Telnet and SSH are an operating system-level login, and the [Web interface] tends to be more of an application level login. Sometimes changing a password on one changes the password on the other, but more often the Web [interface] is completely different, and changing the password there may not change the underlying password” needed to access the device remotely via SSH and Telnet, he said.
Case in point: In February 2016 I published This is Why People Fear the Internet of Things, which examined a whole slew of IP cameras sold by Chinese Web camera giant Foscam that — by default — included a feature which would quietly phone home to a vast peer-to-peer (P2P) network run by the company. As I explained in that piece, while the Web interface for those P2P cameras included a setting allowing users to disable the P2P traffic, disabling that option didn’t actually do anything to stop the device from seeking out other Foscam P2P cameras online.
Interestingly, Karas said he’s been pressing Dahua — whose IoT devices are heavily represented in the above default password list — to tell him how many of their devices are vulnerable. Karas said Dahua told him that although the company’s newest models didn’t have this problem, the company was preparing to launch a trade-in program for customers with default-insecure devices.
“They didn’t give me a straight answer on this one, but that that tells me is they have a whole bunch of devices that may not be firmware updatable, which means they can’t make those devices more secure without swapping out the underlying hardware.”
Update, 8:30 p.m. ET: Added final section with the sobering caveat that all of this hassle in changing the default passwords and updating the firmware may not actually solve the problem for many (if not all) of the affected devices.




“… many of these devices also require periodic software or “firmware” updates to fix previously unknown security vulnerabilities that the vendor discovers or that are reported to the hardware maker post-production. However, relatively few hardware makers do a good job of making this process simple and easy for users, let alone alerting customers to the availability of firmware updates.”
The problem is even more basic: Many manufacturers don’t put out many firmware updates to begin with. And when they do, they’ll only write them during a product’s “lifecycle”, which for these IoT devices is less their actual service life and much more their time being sold as a “new” model. Too many perfectly functional and in use devices don’t get firmware updates because the manufacturer has decided to move from “Model I” to “II”, nevermind that Model I still needs security development. And that’s just plain wrong.
Kudos to any manufacturer out there who does develop security fixes for older but still in-use devices. And shame on those who don’t.
Sorry, had to get that rant off my chest.
Interesting to see the EV ZLX speaker on that list. It doesn’t have a network jack or wifi.
Dave,
As I said in the post, please don’t take these as gospel. If you look carefully, you will see a question mark next to that entry. If you know another device that matches that password, please let me know. Thanks.
yes, GRC does look old school, haven’t tried it, but
http://www.censys.io also lets you scan your own network for open ports.
In your home network:
Turn on ALL your gadgets that you think have connectivity (toaster?),
got to http://whatismyipaddress.com/
and enter it at https://www.censys.io/
Then see what is exposed to the internet. Then harden these devices – or simply unplug/disable connectivity if necessary
Hi,
Except that Mister/Miss end user (i may be one of them to some extend) have absolutely no idea of what you’re talking about and then just don’t care about it.
So burden shud be put on those in the know of if we (collectively) want some results.
My (little?) experience is that “users” just want “things” (iot or not) to just work … they shud not be concerned with all those “nerd” things re password and such.
By the way we “as a corp.” are unable to define “good” vs “bad” password … so what about our users ?
brgds Eric
Re,
Very sorry … shud have put Miss before Mister (french ? :-))
ShieldsUp! at grc.com is older but a much more comprehensive port scanning service. It will scan while you wait allowing you to see if your firewall changes have actually closed down your open ports.
Yesterday’s SANS exercise
https://isc.sans.edu/forums/diary/The+Short+Life+of+a+Vulnerable+DVR+Connected+to+the+Internet/21543/
Mentioned in the article but not dealt with is the main culprit: UPnP. Job 1 when setting up any home/soho router should be to ensure that UPnP is disabled.
Yes, but, as the article stated if the company puts in a back door and that remains unchangeable and inaccessible to users then it is all just a waste of time and effort. It comes down to trust – if because of business ethics and predatory actions toward profit exist then the reliability of companies to “do the right thing” just does not exist. How can you possibly tell if a company is trustworthy?
That would be a question to ask all those people that live their lives on social media through their smart phones who’s only news comes to them via Facebook and Yahoo.
Sheeple that are convinced Apple and Facebook can do no wrong. Living without a care in the world while playing on the Playstation network.
How close do you want to be before YOU are called a tin-foil-hat wearing conspiracy theorist?
Hi,
I may add to that that users (buyers) are just concerned about usability .. The fact that Krebsonsecurity or ovh may be ddosed by their choice does not even remotely concern them (imho).
Brgds Eric
What happen when one has a BSOD and a wired keyboard
is needed?
In addition to uPnP, there are many configurations of small routers in which the user has configured the DMZ option, allowing traffic directed to the router’s WAN address to be sent to a defined internal host. That ‘DMZ’ internal host will likely come under similar assault.
I once had an OpenVPN server connected in this fashion, and immediately saw a large number of login attempts via SSH using a variety of default usernames (root, admin, etc). I have since migrated off using the carrier router’s DMX option, and replaced it with one running OpenWRT, which I could more securely configure.
Smart printers are another area to worry about — ones that can reach out to the internet to receive email that they will print, order ink, etc.. They can also update firmware.. which is at the same time good (apply security patches) and disconcerting (download SOMETHING and install.. could this be abused?).
IF all of your devices are behind a firewall, your safety factor for this area would be…?
… Mildly improved. You’re closing the door for things that have a known entry point to get into. You’ve still go systems that are going to go out around that to the web for updates (which someone might hijack or hack that source), you could find them beaconing all sorts of things they shouldn’t. You might find WiFi secretly enabled with a hotspot or publishing your wifi password to your network. You might find that you shut off all external ports on your firewall that you could but that there was some off/unpublished entry or port knock that lets it in. It’s a best practice to protect them behind a firewall, certainly, but it’s not going to fix all of your problems. What happens when your SMART TV with 50 apps by default has one that connects to some weakly protected server for something. That server gets compromised adn instead of pulling down a feed of vidoes from some fun sounding entertainment site, it pulls down a video that exploits a flaw on your TV giving hackers a shell into it remotely over https 443 or something. Your firewall is there, it’s blocking all incoming connections but your TV made the connection so you’re sunk and they’re on your LAN. This isn’t all that far fetched these days.
What’s the state of the industry regarding outbound firewalls? If you could ensure that your TV can only make connections to Netflix, for example, that might help.
And if you have a networked printer, camera, or other locally-used device, block any outbound connections trying to leave the LAN regardless of purpose.
Etc …
It is possible to go through the settings of individual devices and not only force a specified IP over the LAN but also tell the device to use a specific DNS and then program in for the DNS server ip 127.0.0.1, 0.0.0.0, or even just leave it blank. This will result in a device that the LAN will see but has no connectivity with the net. At that point, if the DNS ever changes for that device (without you purpously doing it), that might be a good indication of something on the LAN being infected.
Just keep in mind that doing this will likely mean that the device will also not be able to do automatic updates or be accessable to web based apps that might be part of it’s function.
Using firewalls for filtering is not effective. For Netflix, the clients keep updating, and will fail to function unless you find all of the new metrics servers, or finally unlock all of the internet to that device.
If you want to unlock Clash of Clans on a VLAN (say, for the kids), then you need to create 2 different DNS objects that resolve to 221 different IP addresses in a non-static manner. Then, you’ll have several more service ports that need to be opened up just to connect to Apple’s Game Center, etc. That’s 30 minutes of research and trial-and-error just to get one game to work.
Now, let’s add Steam. Then FaceTime messaging. Then Microsoft updates. Adobe updates.
Each requires custom network object and service definitions, then apply an exception to your internal network(s).
This brings us back to that deer-in-the-headlights look from average consumers.
Then, they just turn off all security and enable UPnP. Usually, that’s the default configuration from consumer routers anyway.
With the exception of Verizon’s routers. They have the same generic configuration, but also come with a bonus backdoor that can’t be disabled. The techs can see into your LAN, even though they shouldn’t. Their first-level call handlers don’t know how to read an IP subnet, but have internal access to your network, from the public internet side of the circuit.
Imagine the cracking of that password algorithm!
“Now, let’s add Steam. Then FaceTime messaging. Then Microsoft updates. Adobe updates.”
Once all this is in place, there is no longer any point as the system becomes compromised anyway. How many articles do we really need to read about Flash, Java, ActiveX, rootkits, various other Adobe nonsense, and various MS updates that break the system?
NAT is not necessarily going to save you. This is addressed in the story. Just do a Ctrl-F for UPnP.
It’s not just UPNP. IPv6 is often routed openly by default on many routers, if it’s supported at all. All your IOT devices with a valid public IP and no firewall by default? Woo hoo!
Auto IPV6 tunnels are also another great vector.
Ok, with UPnP turned off, NAT would then be “good”?
Brewski, “…many IoT devices will use a technology called Universal Plug and Play (UPnP) that will automatically open specific virtual portholes or “ports,” essentially poking a hole in the router’s shield for that device that allows it to be communicated with from the wider Internet. ”
Note the “from the wider Internet”. I don’t have lots of experience with this, my viewpoint is, disabling UPnP at the NAT would block that protocol (UPnP) from passing through.
Just saw a blurb on the net – someone took an Internet-enabled refrigerator (with the big screen on the door) and brought up pornhub on it in the store.
IoT fail.
I wish he or she did the same with my fridge. Good quality porn is hard to come by especially when you just wait for the microwave to do its job.
What is the best way to contact you regarding an invitation to be interviewed guest for radio show in Los Angeles?
I like the follow ups like this. Good flow while maintaining interest, exposure and education without getting dry.
Hmmmm… windows 10 home edition does not recognize ‘telnet’ as a command…
dism /online /Enable-Feature /FeatureName:TelnetClient in the command prompt as an Administrator.
In addition to changing the default password on network devices I always change the user name just in case. This practice has served me well when clients would argue for weaker passwords as the user names (sometimes a made up name) will add some great protection. In most of these Linux based devices user names are case sensitive thus adding a capital letter or two greatly improves security.
Also I have seen the p2p deactivated by default on the latest foscam cameras.
I would also note that I have noticed the vendors tech support will offer to edit customers firewalls via remote control possibly adding to the problems.
Pretty interesting article, though the default password issue has been with us for a long time. From my university days till today dictionary based attacks have been the most successful. Even when told to pick hard passwords they can’t, or won’t. Even changing them back to iloveyou. Lol. The manufacturers of these things don’t help, rarely releasing firmware updates, or just not at all. Many don’t think it’s necessary because they are used to infrastructure and protocols at the corporations.
I do see some areas of opportunity being profitable hero. Secure public key, secret key encryption is getting more accessible (people use it all the time, they just aren’t aware), devices built around single board computer’s allow for more flexibility and change, open data projects, and creative crowd sourcing projects will help.
The madmen ‘running’ things gave away the root servers, a critical component of the Internet. We’ll take it back with a public and open block chain and pubic key infrastructure. Hackers wanna watch us sit on the couch or micowave hotdogs, we’ll force public/private encryption and certification on everyone. Maybe setup public ANN security for good measure. Lol.
Seems like these devices would be inherently more secure if they simply refused any connections from outside the local net 192.168.1.* only.
If a customer wants to open the IoT device up more then that is something that would actively have to be done.
Did I miss something with my too-easy-to-be-true statement?
Convenience. Brittany doesn’t wanna stress over how to configure her camera so that she can watch her dog, Princess Fifi prance around the house while she sits at Starbucks.
Plug it in, download an app, and open it while on the same wifi network. The software links everything up so that it knows where the camera is when out and about.
Granted, there are solutions for this – VPN, proxies, etc – but none of them convenient enough for the masses.
This is the issue in a nutshell. Consumers don’t care about security unless it inconveniences them. And then they disable it. When have you seen a home router/firewall that touted it’s security features front and center? At least a successful one? 😉 The features that sell home routers are performance, wireless coverage and price. And UPnP is a virtual necessity these days. Have you ever tried to configure an enterprise firewall at home? I have and I had to configure SNAT, DNAT and multiple ports just to get my XBox to communicate. And in-game chat never did work right so I went back to a consumer firewall and UPnP.
IoT devices are the same thing. Ease of use, TTV (time-to-value) and price are paramount. Are there better ways? Of course! Some IOT devices are configured using a local connection to an app on your phone. Authenticate with the device! Need access from another device? Let the first device generate a “reasonable” login and password to use on other devices. It’s not impossible to make things secure and easy to use, but it takes thought, a user-focused approach and (gasp) some actual user testing. But until there’s an actual ROI on a secure, easy-to-use interface vs. one that’s simply easy-to-use, only developers that have a genuine passion for building secure software will build them. And sadly, I haven’t seen many of them outside the security community.
-rod
For the last 15 years I have managed a web hosting facility and the enterprise networks of several companies. I have seen and works a number of cyber security problems, a couple times with an FBI agent in my office. We have worked hard to secure networks and systems. It has been a long and painful learning process.
.
My greatest fear with the Internet of Things is its potential for us to relive all the mistakes and problems of the past, but with an order of magnitude more systems. The things we do to harden operating systems are not being done on most IoT products I’ve seen.
.
Today in reading your column you have made my fear and concern a real problem. Take notice everyone. This has the potential to become a HUGE problem.
Just switched out My cable modem. I had to disconnect the wireless part of it to bridge to my router. In order to do that I had to log on to the admin section. And the default user ID was admin and password…. password.
What I don’t understand is why this problem wasn’t seen coming from a million miles away. Or was it? This exploit seems to me to be so painfully obvious in hindsight and considering my very limited knowledge of such things, it must be pretty darn obvious for ME to see it as obvious.
I *was* seen a million miles away. People have been warning of this eventuality for years. And various malware and miscreants have been exploiting these flaws for some time. I guess it just takes a big attack to grab everyone’s attention.
Some coverage of this issue:
DISTRIBUTED CENSORSHIP OR EXTORTION? THE IOT VS BRIAN KREBS
http://hackaday.com/2016/09/29/distributed-censorship-or-extortion-the-iot-vs-brian-krebs/
Hardware test – How to Become Part of an IoT Botnet
https://www.insinuator.net/2016/10/how-to-become-part-of-an-iot-botnet/
Now I know how Mr, Krebs is able to figure out all this stuff.. he actually lives in the future!
Note the future date on this post – Oct 16… or is someone getting in and making adjustments?
greg
October 5, 2016 at 5:22 pm
From a phone, that’s what I see; don’t know what’s seen from desktop.
The big number is the day.
Explained to user how to read date.
Explained we do not have (or publicly admit) to having time travel device.
Don’t get me started on the confusion caused by ambiguous date formats – 12/1/2016 is the first of December in the US, and the 12th of January in the UK. The IT ‘Profession’ deserves most of the criticism it gets, for not caring about standards. I quote from Dilbert: “Salesman: It conforms to all the standards” – “Dilbert: you mean, it does nothing useful, but it’s not your fault”
There’s a Red Tiger white paper that looks at printer security. It can be found here: http://bit.ly/1sq1kyG
Anyway, one of the things it talks about is having access controls on every device. I wonder if we’re ever going to get ahead of the hackers given how difficult this may be for many organizations.
–KB
two down and another 500 to 1000 to go 🙂
I’m waiting for the vulnerabilities of devices and software that use brokers to connect externally like most NAS or even teamviewer
Brian mentioned in this week’s Economist:
http://www.economist.com/news/science-and-technology/21708220-electronic-tsunami-crashes-down-solitary-journalist-internet-stings
I’m sure DDoS is not the only threat repurposed IoT poses to the Internet. I immediately thought how these bot networks can be used as proxy relays for C2, or active offensives. What other practical capabilities do you see that we can we expect from compromised Things?
Brian,
We met in Chicago at a Security Conference in November 2012. I shared my story about the Krebs Cycle and the guy who wrote the tune in University of Guadalajara Medical School who wrote the song to memorize the Krebs Cycle.
Anyway, thanks for a brilliant article and analysis (as usual).
If you thoroughly review the material and links at http://internetcensus2012.bitbucket.org/paper.html you will see the parallels between the Carna BotNet and Mirai.
On another note, I like and admire you, personally and professionally, and on some level it makes me sad when a guy who diligently reports cybersecurity news has to become part of the news yourself.
You are a courageous and bright Star on the Internet. Please never give up. We need you.
Thank you.
Your friend in Chicago,
William Favre Slater III
http://billslater.com/wfs_contact.txt
Xerox indicates that their printers are not vulnerable to Mirai malware because telnet and SSH are not enabled:
https://www.xerox.com/information-security/enus.html
From the Xerox article:
================================
What is Xerox doing about this?:
Xerox has studied the botnet source code and determined that it cannot successfully attack any Xerox device. The two services the botnet uses, telnet and SSH, to open a command line are not supported.
Impact:
Xerox devices may be targeted but cannot be successfully attacked. See below for recommendations on what you can do to prevent your Xerox device from being controlled by unauthorized individuals.
What should you do?:
– Don’t connect your Xerox device directly to the public Internet. Make sure it’s behind a firewall or router so that only you and your users have access to it. This keeps outsiders from accessing the machine and interrupting your business. Please check with your IT department if you’re unsure.
– Don’t leave the administrator’s password set to the default. Change it so that unauthorized individuals can’t easily guess it and take control.
– Choose a password that is at least 8 (eight) characters in length with a combination of letters, numbers and special characters.
Never share the administrator’s password with anyone who does not have a legitimate need to know.
================================
An office I deal with uses 8×8 phones. Most are older Aastra phones. Beware of trying to change the admin password without talking to support first. I spent 3 hours restoring 2 phones I changed. There is a specific way to do it. Their newer phones (less than 2 years old I’m guessing) automatically change the password after initial login/setup.
I’ve had several clients having all sorts of problems with device security. Users are participating in BYOD (bring your own device) to offices and they are contributing to more visible security threats for their business.
What I’m wondering if we, as IT professionals, have not been communicating the right way to engage our users towards understanding the immediate threats of cyber/phishing attacks. I was wondering if enterprise architecture is a solution to help businesses get the right messages to their users across departments. I am concerned that security issues are only getting worse and we need to better communicate to users how they can contribute in avoiding getting targeted. I just came back from a workshop earlier last month and am thinking about how to increase engagement with users—types of communication paths—to make them both more aware and more active in threat prevention.
One technique I’ve seen from an IoT manufacturer (that I’d like to see become mainstream) is to assign a unique default password for each device, which is printed on the bottom of the device next to the serial number. A factory reset would revert the device’s password to this unique value. Even if the default password is never changed, it would require physical access to the device to retrieve.
There are other security issues that the manufacturers need to be aware of and mitigate, but this one will take care of a large attack vector. The cost, of course, is a slightly more complicated assembly line process.
Yes, this is effective. Considering that devices have be assigned unique MACs anyway, the additional cost is matching the assigned password to the physical device. If Huawei can do this for their $40 LTE CPE router, I don’t see why others can’t.
Another way is to have the random password display on an/the LCD. My kid’s $30 ‘pocket Wifi’ does this.
We surely live in interesting times!
Now, how come all the 3-letter agencies fighting this (and also terror – at least officially) seem to have made no efforts what so ever to make the internet a safer place?