New research suggests that an elaborate cybercrime ring is responsible for stealing between $3 million and $5 million worth of revenue from online publishers and video advertising networks each day. Experts say the scam relies on a vast network of cloaked Internet addresses, rented data centers, phony Web sites and fake users made to look like real people watching short ad segments online.
Online advertising fraud is a $7 billion a year problem, according to AdWeek. Much of this fraud comes from hacked computers and servers that are infected with malicious software which forces the computers to participate in ad fraud. Malware-based ad fraud networks are cheap to acquire and to run, but they’re also notoriously unstable and unreliable because they are constantly being discovered and cleaned up by anti-malware companies.
Now researchers say they’ve uncovered a new class of ad robot or “bot” fraud that was designed from the ground up to keep its nose clean — running not on infected hosts but instead distributed across a vast, rented network of dedicated Web servers and computers.
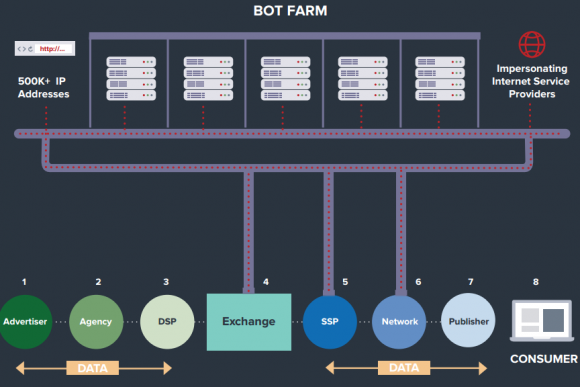
The Methbot ad fraud infrastructure. Image: White Ops.
According to White Ops, a digital advertising security company based in New York City, those rented computers are connected to a network of more than 570,000 Internet addresses apparently leased or hijacked from various sources.
White Ops dubbed the video ad fraud network “Methbot,” and says the individuals at the helm of this network are spending upwards of $200,000 a month just maintaining a fully automated fraud network that imitates real Web site publishers showing real viewers video-based advertisements.
Ryan Castellucci, principal security researcher at White Ops, said Methbot’s coders built many of the fraud network’s tools from scratch — including the Web browser that each rented computer in the network uses to mimic Web sites displaying video ads. Spoofing actual news Web sites and other popular video-rich destinations, Methbot requests video ads from ad networks, and serves the ads to a vast array of bots that “watch” the videos.
To make each Web browsing session appear more like one generated by a human, Methbot simulates cursor clicks and mouse movements, and even forges social network login information so that it appears the user who viewed the ad was logged in to a social network at the time.
“They’ve written their own browser from scratch in Javascript, and this allows them to arbitrarily control the information that gets fed back to the ad networks and to companies like us who try to detect this stuff,” Castellucci said. “This has allowed Methbot to scale to beyond anything the industry has seen before, putting it in a new class of ad fraud.”
Interestingly, the registration records for virtually all of those Internet addresses have been forged so they appear to be controlled by some of the world’s largest Internet service providers (ISPs).
For instance, one of the many Internet addresses White Ops says was used by Methbot — 196.62.126*117 — is registered in October 2015 to AT&T Services Inc., but the contact address is “adw0rd.yandex.ru@gmail.com” (the letter “o” is a zero). Adw0rd is no doubt a play on Google Adwords, an online advertising service where advertisers pay to display brief advertising copy to Web users.
Another address tied to Methbot — 196.62.3*117 — is registered to the same adw0rd.yandex.ru@gmail.com account but also to “Comcast Cable Communications, Inc.” Records for another Methbot IP — 161.8.252.* — says the address is owned by “Verizon Trademark Services LLC.”
Whoever dreamed up Methbot clearly spent a great deal of time and money building the fraud machine. For example, White Ops says the address space alone used by this ad fraud operation has a current market value of approximately $4 million. A full list of the 570,000+ Internet addresses used by Methbot is published in the White Ops report page.
“Methbot operators invested significant time, research, development, and resources to build infrastructure designed to remove these limitations and provide them with unlimited scale,” White Ops said in its report. “They created dedicated data centers to support proxy networks in order to hide the single origin source of their operation. This is the first time we’ve seen data centers impersonating residential internet connections. This makes the scale of this operation virtually unlimited, with none of the typical durability issues of maintaining a constant base of infected user machines.”
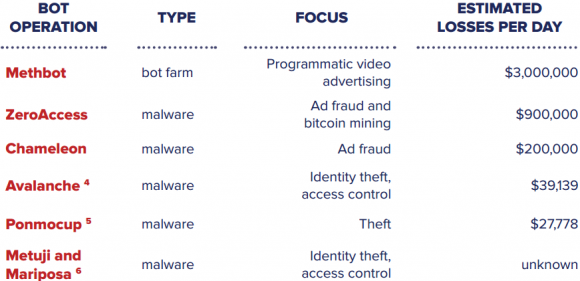
Methbot is thought to have helped steal quite a bit more ad revenue than malware-based ad bots that came before it. Source: White Ops.
White Ops said it estimated the earning potential of Methbot by looking at the number of phony video ad impressions it could serve up and the average cost to advertisers for displaying those ads. Assuming an average CPM (cost per mille, or per thousand number of impressions) of $13, the company estimates Methbot has the ability to serve between more than 300 million impressions each day, with a daily revenue ranging from $2.6 million to $5.2 million.
WHO RUNS METHBOT?
White Ops’s report doesn’t delve much into the possible actors behind this ad fraud network, but there are a couple of tantalizing clues in their findings. White Ops found that the Methbot network originally used a program called Zombie to test the ad code in a simulated Web browser environment, but that later the Methbot team built their own Javascript-based browser. The report also notes that Methbot employs a program called “Cheerio” to parse the HTML rendered by the video ads.
Both Zombie and Cheerio show up in this October 2015 discussion thread on the Russian-language tech forum pyha[dot]ru. That thread was started by a developer using the nickname “adw0rd,” the same nickname listed in the phony ISP internet address ranges used by Methbot. A glance at adw0rd’s profile on pyha[dot]ru shows the user is from St. Petersburg, Russia and that his email is adw0rd@pyha.ru.
The “contact” page for adw0rd[dot]com (again, with a zero) includes that same email address, and says the account belongs to a software developer named Mikhail Andreev. That page at adw0rd.com says Andreev also has the account “adw0rd” on Facebook, Google, Twitter, LinkedIn, Github and Vkontakte (a Russian version of Facebook). A look back at programming projects dating to 2008 for adw0rd can be found via archive.org. Andreev did not respond to requests for comment.
The “abuse” contact email address listed on many of the Internet address ranges that White Ops tied to Methbot was “stepanenko.aa@mmk.ru,” someone who appears to have at least at one time acted as a broker of Internet addresses. That same “stepanenko” email address also appears on the official contacts page for an Alexey A. Stepanenko, senior manager of support group IT management systems within the telecommunications infrastructure at Magnitogorst Iron & Steel Works, the third largest steel company in Russia.
Update, Dec. 23, 1:54 p.m. ET: Fixed a typo in the number of ad impressions White Ops said Methbot was able to produce daily.




Great work, Brian!
Regards
RWS
Do you haz 3 cent pirate toy? Me wood pay dollar top, 4 cent for 3 cent toy.
https://github.com/adw0rd also has Pyha listed under his ‘Organizations’ on Github. Def prob the dude or at least has a major part in it.
Best and most detailed report so far. The NYTimes one put it in lamen terms, Krebs’s is more geared to the security geek with details of the operation.
Don’t get it… Aren’t these guys just sending money to ad network operators like Google and Facebook?
They made it seem like so, but their websites got money as publishers on ad networks. Anyone can add their websites to serve ads from ad networks and get paid.
I’m still confused. At these IP addresses, software pretends to be “eyeballs.” I’m sure that can be done. It is the collecting money part I don’t follow since I don’t host advertising and thus never received payments.
Looking at a few of the IP addresses, I’ve blocked the hosting companies from my server due to hacking attempts. Granted lame attempts such as trying to log into WordPress, which I don’t use. Rather than just let the attempt 404, I log them, research the IP, and if from a hosting company, VPS, etc., I block the entire service since they are not “eyeballs.”
Joe, you raise an interesting point. Since Google and Facebook are making millions of dollars a day off of these fake viewings, do they have any reason to want to stop Methbot?
The only reason that ad networks have to stop something like Methbot is when it gets bad enough or open enough to erode advertiser trust in their services. Everyone in the ad tech industry benefits from fraud: ad agencies, third-party networks (AppNexus, Google AdWords), first parties running ads on their own sites (Facebook, search engine ads), and all the data and tracking technology providers. The big players just have to keep fraud a little lower than their competitors. Online advertising is basically mandatory for large businesses now, so they have to pick among the options available.
Source: worked in ad tech for years, including at a startup that never made money because we couldn’t get anyone to pay us to reduce fraud.
They’re not advertising, they’re hosting advertising. For example, Krebs doesn’t pay his chosen partners to serve you ads, his chosen partners pay Krebs to serve you ads. Similarly ad networks pay the malware hosts money to serve up ads to its malware clients which are faking being real people to the ad networks.
Because they’re faking hosts and clients they’re getting the website cut of the ad revenue. The real losers are the companies paying for advertising. Google, etc. are laughing all the way to the bank since they’re getting paid either way.
But what if your on BOTH sides? You supply ads and/or google AdSense. You advertise certain ads, and your bots do the clicking for you, adding revenue into your pocket. It raises the amount of revenue coming in. With all these IP’s is real easy to have one group of Ip’s to advertise, one group to click and view these advertisements and have others on standby.
If they own any of the businesses they are clicking on, I am sure their google ranking will go up as well. A secondary income can be seo rankings, referrals and more.
Crazy.
But that would be counterintuitive.
These guys use ad networks to spread exploits. It costs money to place ads into ad networks. They only do that when there’s a net gain for them because otherwise it’s a loss for them.
They’re clicking on someone else’s ad, an ad someone else paid the ad network to display, so that they, as a fake website, can share revenue with the ad network from their fake clients visiting their fake website.
Now if they were really clever they would create their own ad network and insert this model into it, thereby taking a larger chunk of the advertising budget. But that requires a long term investment since the ad network can’t be entirely fake or it would quickly implode. People won’t advertise with a network if it offers zero demonstrable gains. Most of the people would need to be real for there to be a gain. They would need to squelch their greed long enough to not sink the boat.
I think our friend Mikhail has just been caught red handed. Or maybe they made it seem like it was him, that is if he is a real person.
Being caught red-handed doesn’t mean much in Russia, it all depends on who you are working for…
Right. Even being religious doesn’t mean much in Russia: this Mikhail adw0rd Andreev says in his VKontakte profile he believes in God.
His site (http://adw0rd.com/portfolio/) says he has been working on an “X-project” since 2015
The revenue numbers don’t add up. Two million bogo-ads a day divided by 1000 per millie is 2000 millies per day. Multiply that by $13 dollars per mille gives a revenue of $26,000 per day… hardly worth getting ones’ 400 pound hacker ass out out of bed for considering the alleged expenses.
Let’s start with this sentence: “Assuming an average CPM (cost per mille, or per thousand number of impressions) of $13, the company estimates Methbot has the ability to serve between two million and three million impressions each day, with a daily revenue ranging from $2.6 million to $5.2 million.”
A $13 CPM impressions is the cost to the advertiser, right? Let’s say that Methbot gets 50% of that. So we have 2,000 M to 3,000 M (thousand) impressions per day at $6.50 per M results in revenue to Methbot of $13,000 to $19,500.
Brian, please enlighten us as to where the $3,000,000 to $5,000,000 per day came from.
I’m struggling with the math and maybe I’m interpreting it wrong too.
Could it be that Methbot causes 3million lost per day, and that the 3 million is broken up into chunks that go to ad agencies, third-party networks (AppNexus, Google AdWords), first parties running ads on their own sites (Facebook, search engine ads), and all the data and tracking technology providers. Methbot may only be making $13 per millie, but the advertisers are paying far more than that.
26k per day does add up, and could quickly recoup the costs associated with this venture, there may also be other revenue sources for Methbot utilizing the same infrastructure.
right? they must mean per year
I agree with your math, but where did the figure 2 million ads/day? With all that server power, they could be doing lots more.
Fascinating sh#t to read !
I haz a cat that could be traded for 3 cent pirate toy.
This is like running a fake newspaper publishing company that collects money from advertisers in exchange for printing the advertiser’s ads. The publishing company fakes the printing of the newspapers, but charges the advertiser for the “millions” of impressions (millions of fake readers). This is one reason that newspapers are audited for circulation figures.
In this case, not only are the circulation figures faked, but so is the publishing and distribution of the media.
Most businesses receive solicitations from several fake yellow pages companies. I’m guessing that they only print enough books are to send one to each of the stupid companies that paid for a ad.
I suspect we have been hit by this from PPC fraud that we have seen over the past several months. The source IPs do seem to come from providers like Comcast, so we can’t really block many small IP ranges under residential ISPs. What I thought was going on was that fraudsters had starting using residential proxies that are either hacked or intentional(paid to host a proxy). Now it appears that they are using spoofed IPs.
Of the two IPs listed in the article, I checked both and we were already blocking the first one but not the second. I look forward to downloading a 570k IP list and seeing what we are not currently blocking. But actually, I suspect we are already blocking 70%-80% based on the two provided examples.
If you don’t do business on an international level, why would you want those visitors to access your site? You should block any country that is a known source of problems and even others that are more “friendly”, as they can also be used to launch attacks. Then you can also start blocking hosting providers since traffic from them is generally unwanted proxy visitors.
Your list of options is limited. Why ignore simple defense methods that in my experience are very effective?
The problem is they spoof the country too. Like you we also have seen this kind of thing. An ad that was getting 2-3 clicks a day suddenly jumps to the top with 50 clicks and some site visits. Traffic looks normal, but when you start running down the IP’s in the logs you see people from all over the world are suddenly interested.
You see this a lot with what we call “slap games”. They are basically apps that are toys for infants. Bright colors that the child just touches to make something happen. Problem is the programmers pop an ad up from time to time. Parents just see the kid somehow got to some website and thinks nothing of bringing the app back up. Starting the process starts again.
Country spoofing is not a problem for us. We don’t block by reported country code – it’s not reliable enough. I have been doing manual lookup of IP WHOIS records for a long time and use those in deciding what to block. IP WHOIS records can contain errors, but the past several years I have only found a couple incorrectly assigned to non-US countries that were actually being used inside the US.
Just blocking one address range like 80.0.0.0/4 can cure a host(pun intended) of problems. But our block list has about 800 entries which may grow as I check the Whiteops list they have so kindly provided.
Right, but that is you. The ad network is the one getting spoofed.
This is not a case of PPC fraud, instead they targeted online “premium” video by spoofing the domains and creating fake players. They deliberately targeted sites/buyers that have very high CPMs ($13+ on average). In other words, their target was Branding advertising that doesn’t have clear KPIs like CPA and calculating ROI is hard.
You may be correct about Methbot not targeting PPC, but there are two others on the list that seem to be doing that. And I don’t know if we can say for sure Methbot is not also including some PPC fraud as well.
I can tell you with 100% certainty that if “I” had a large scale system that could effectively do fraud and appear as actual users, that I would be doing at least SOME PPC fraud. Why? Well, $13 for 1000 impressions is ok, but when you look at some keyword commanding upwards of $100-$300 (for placement bids) then you realize that just one session can easily earn enough to dwarf the more (machine)labor & time intensive impression fraud.
And if you can simulate user activity that means you can also use that system to take an action needed to simulate a conversion. Once you can do conversion fraud the only way to tell something is amiss is with the customer’s backend systems that indicate while CPConversion may be ok, the actual CPA is excessive.
It’s very, very difficult to prevent initial PPC & conversion fraud. But it’s not all that difficult to track it and then take some steps to reduce future fraud via different methods.
Interestingly, I added Magnitogorst Iron & Steel Works to a blacklist in August 2016 due to the significant amount of port probing originating from the network (161.8.0.0/16).
I wonder if the company knows that its IT department is running a secondary “business” on its network.
We have been blocking them for some time now, but we are using 161.8.0.0/15.
Whenever we look up some problem source and see it’s part of RIPE, APNIC, AFRINIC, JPNIC, LACNIC, etc. we block the widest range possible (like AFRINIC 154.0.0.0/8 or 154.0.0.0 to 154.255.255.255).
Are we really the only ones doing this? Or are people just not talking about it for fear of being “isolationist”?
I also do the same thing.
Block them from every port other than 25. Even if they can’t see your website, your contact information generally shows up in a Google search. This is assuming some eyeballs at the Russian steel mill actually want to view your website.
BTW, ip2location.com has a nice lookup. I then go to the Hurricane Electric BGP tool to get the IP space.
I did the same thing.
The question I have is what ad network has been writing $90M-$150M checks to these guys each month? And how did they miss that? Seems that getting enough accounts set up to hide your scam would in itself be something they notice.
I’m afraid I’m still not sure I understand what is going on. Does the following sound correct?
Methbot creates a bot network of sorts to act as fake sites. They have some ad-provider allow them to host ads on these sites.
Then they have another set of fake ‘viewers’ who hit the sites. This looks like a spike in internet traffic and ad views.
I’m not that familiar with ad metrics, but this then looks like, to the ad provider, that these sites are really busy, and many people are seeing the ads, so they pay the fake sites accordingly. When in reality, no one is actually seeing these ads save for the fake viewers. Thus, the ad-providers are shelling out large chunks of money due to this.
Would that be a fair summary, or have I continued to misunderstand?
That’s more or less how it works. The other shoe is that the ad network is charging advertisers a premium based on their metrics showing their ads are playing (fraudulently) to many viewers. So it actually benefits the ad network too, until the advertisers start refusing to pay the premium because they don’t trust the metrics.
OK, Brian. At this point, can we just take an ax to the transatlantic Internet cables linking Russia (and it’s former satellite countries) to the rest of the world?
IP addresses are spoofable. Another locale in the news that was all about our president-elect was India. False flag on Russia? Only the servers know…
Again this comes down to ethics and that idol Mammon. Because to the way the internet is structured, the ultimate arbitrators are hosting providers. Their servers know where things go, because without a real IP address (download Wireshark and check it our yourself) a packet can’t go from Alice to Bob. TOR may be the exception but look who that was developed by. I get over 80 spam emails per day of the form Easy Local Casual-Hookups . If you believe the Brooklyn bridge is for sale then you may believe that the ISPs and hosting providers can’t stop it. But they could, however they have no inccentive, legal or financial to do do so. Remember that discourse from Lenin: “… 100 per cent (profit) will make it ready to trample on all human laws; and 300 per cent and there is not a crime at which it will scruple, nor a risk it will not run, even to the chance of its owner being hanged.’ “
Forum spam and romance scams using proxy servers are a massive problem too, would be nice if ISPs could segregate hosting IPs from consumer browser IPs for example by using *.net domains with reverse dns for end users and *.com domains for cloud hosting or else there will be no way to tell the difference fairly soon.
Very nice job!
I am doing an academic study. The information and the approach contained herein will help me a lot.
Yet more proof that the ‘dark side’ of the internet is as much a business as the legal side. The level of sophistication and investment required to make these scams work is no different to that employed by legitimate companies, usually without all of the admin overheads required by regulation and legislation.
Typo of some sorts?
$13 CPM is $0.13 per view. Either it’s $26,000 per day and $780k per month, or it was 200~300 million views for $2.6m~5.2m per day…
Seems $26k per day and $780k per month is more plausible.
Oops, $13 CPM is $0.013 per view.
from the report “By mid-October, the White Ops MediaGuard Prevention Service was detecting three to five billion bid requests
per day from Methbot spread across multiple ad platforms”
3.000.000.000 to 5.000.000.000 impressions a day. His LinkedIn profile says he’s been working as Lead Developer on “High-Load platform for distribution of CPL traffic”.
This is people from Russia. They have a terrible economy but the people over there are extremely tech savvy and they don’t have any way to be gainfully employed so they resort to cyber crime.
For 3-5 million bucks I think it be worth spending the time to learn to do that.
A day… $3 – $5M a day. What wouldn’t you do for that kind of cash?
This cybercrime ring accounted for 20% online advertising fraud??
This is all good IMHO. The digital advertising industry is terribly flawed from the get go, and if nothing else will get them to fix it perhaps this will. Having worked a bit in digital advertising, they can’t figure out when to start and when to stop pushing ads to users because they don’t know when and why the viewer is browsing. For example, each time I buy something online I get no ads for the item until after I purchase it, then I get ads for about a month. All of those wasted ads are paid by the firm (e.g., Amazon, Lowes, Macy’s, etc.) peddling the product, but no one knows I bought the item before the first ad was pushed. So the middle man (Google, etc.) gets paid because they convinced the merchants that their advertising works. In actuality, it works perhaps less than 1% of the time. Meanwhile, the rest of us are who is paying for the wasted advertising.
That’s just poor campaign execution by the trader at the media agency/trade desk. What should happen is once you purchase the advertised product you are added to the exclusion list & would not be served any more ads, unless you clear your cookies, or they’re trying to get you to buy another sku in their inventory.
What is crime here exacly???
Did someone got killled??
Then allthis nonsense words…like
Bot,internet. Cyber.connection..hosting
Bla bla…..can anyome explain simple and plain
English!!!!!!
They’re stealing peoples money.
I see that Mikhail Andreev found your article, Brian.
It looks like Mikhail Andreev found your article, Brian!
Kevin above described it best.
“Kevin
December 20, 2016 at 5:41 pm
I’m afraid I’m still not sure I understand what is going on. Does the following sound correct?
Methbot creates a bot network of sorts to act as fake sites. They have some ad-provider allow them to host ads on these sites.
Then they have another set of fake ‘viewers’ who hit the sites. This looks like a spike in internet traffic and ad views.
I’m not that familiar with ad metrics, but this then looks like, to the ad provider, that these sites are really busy, and many people are seeing the ads, so they pay the fake sites accordingly. When in reality, no one is actually seeing these ads save for the fake viewers. Thus, the ad-providers are shelling out large chunks of money due to this.
Would that be a fair summary, or have I continued to misunderstand?”
I’m just a regular user who does not see a big difference between legitimate ads and this reported fraud. As a consumer I know I pay for the ads, and it seems everybody gets their cut. Service providers, search engines, ad networks. Everybody except us regular dummies. If I turn off all ad and tracking blockers in my browser I see lot of ads for services and products not available in my country. And I see a lot of ads for products I have bought online within the past few months. In short, it’s all fraud to me.
I do like to turn ad blocking off for interesting sites, such as this blog. I have subscribed to marketing emails from ~20 companies. I go through their messages couple of times per week – note that *I* get to choose when and if I open each item. And finally, I donate a few dollars to individuals, small businesses and open source projects that have Paypal links. As an example, there was an online converter that I used almost daily. So I sent a small sum for the guy who wrote it. He was so grateful he sent me an invitation to his wedding!
If my company buys $25,000 for a month of ads, and these guys scam $24,999 of the money into their pockets, that is a huge difference from a Dodge banner ad being shown to a user.
“Regular dummies” do get their cut, since that is how the sites they visit keep their lights on. I could argue that hiding ads is committing fraud against the owner of a website.
Don’t get me wrong, I make the damn things for a living and hate 99% of them. But like it or not, this is how a lot of sites survive.
“I could argue that hiding ads is committing fraud against the owner of a website”
Jesus, what’s your opinion of people that change the TV channel when ads come on. Burn ’em at the stake?
What’s your position on not reading billboards? Castration or just flaying?
“I could argue that hiding ads is committing fraud against the owner of a website.”
Please do. I’m interested to hear it.
The way I see it, the average user ends up paying for companies to advertise to them.
Mobile phones and tablets with cellular plans have data limits on their monthly plans. Ads, especially non-text ads with multimedia content, consume bandwidth. Loading this typically-unwanted content goes against the limits set for users each month. There are also many ISP’s that set data caps on their subscriber base to their home connections. Overages on these caps have real-world financial impact, especially if a portion of this data was consumed by advertising content.
Alternatively, ads take processor cycles to run. Processor cycles generate heat and consume electricity. This contributes to Heating/Cooling costs and electric bills. For laptops and other mobile devices, these processor cycles reduce battery life leading to real life inconvenience and financial impact.
So how is blocking this inconvenience fraud?
So every website owner the world over should absorb all the costs just because you don’t like ads? Believe it or not, websites are not free and neither are servers, rents, employees, insurance etc etc.
I’m of the opinion that if ad networks can’t take the necessary effort to weed out malware disguised as ads, I’m under no obligation to display those ads. The websites are mostly innocent victims, the people to blame are the ad networks who fail to live up to the job they’re tasked with.
Just look at Forbes. They implemented a huge anti-adblocker push recently. As soon as they did that malware was inserted into their advertising. Frankly I think Forbes, having taken such an active role in making visitors disable ad blocking, should be financially liable for losses incurred by visitors due to their failure to adequately screen for malware.
I don’t give a crap about ads. Show ads, don’t show ads, I don’t care. Serve me malware instead of ads? Then I care. I care enough to remove all advertising from every site I visit by any and all means at my disposal. Until they take adequate measures to clean up their act I have no moral or legal requirement to cooperate.
When I was still using ABP I had Krebs whitelisted since he takes adequate measures to screen his ads. I did the same for other responsible sites I visited. Frankly I need to go back and recreate my whitelists now that I’ve stopped using ABP…
The majority of adsense adverts are blocked these days, which is the most minimally intrusive and least offensive adverts out there – so your argument doesn’t add up.
That’s about the best way to put it.
Websites cost money. If I have a site with ads, you know the ads are how I pay the bills. So I am showing ads to keep from putting up a paywall. I am giving you content in exchange for the ads being shown to you. When you block the ads, I don’t get paid for showing the content and still have to pay for my site.
This isn’t like a billboard at all. If a billboard paid for the road you were driving on then it would be closer analogy.
And yeah, people have quit watching ads on TV. The first DVR’s didn’t show commercials at all. They had to just fast forward through them because it was killing the medium. It helped create a market for cheaper shows aka reality tv. It is also why so many ads have big blocks of text, so they can be read on fast forward.
Arguing that because you loaded the ad you should be compensated is not even realistic. You don’t charge UPS for bringing a package to your house, you don’t make the grocery store pay you for gas.
Like I said, I make ads for a living and I try to make them as obnoxious as I need to, with making them annoying. Sometimes I fail. I wrote the “We want to cya in a Kia” tag that is now used everywhere(seriously, sorry for that). I don’t believe in weaponized marketing. But I know I am in the minority. We have to be realistic and know that if we want good content, people have to be paid for it in some way. As advertisers, we want people that make malware ads to get caught. We want them to fail because we all get tarred with the same brush because of them.
Bug, I am trying hard to see your point. I am a normal everyday user. I don’t like the malware being served and I think the website and advertising community has to take on that responsibility.
From the advertising standpoint, what I object to is the way that advertisers present their material. Using your analogy of the roadside billboard, the billboards in this case jump out in front of the cars and continually move to block the road. The billboards grab hold of the car and drag it down. One small wrong move and you are redirected to see this obnoxious ad.
I block ads on websites when those sites present obnoxious website or I stop visiting them. If the website is responsible and respectful, I whitelist the site.
I am having trouble seeing where this is a security issue or even a crime. These people are merely exploiting flaws in the advertising ecosystem. These antics don’t make me or my data unsafe. These antics only jeopardize this revenue form. So do the fake stories and other sensationalized headlines. From my humble viewpoint, this is an online advertiser environmental issue and not my problem.
I think a couple people may have missed a point in all this. Brian kind of assumes people get how ads work automatically.
These guys aren’t creating fake ads to generate money. They are taking legitimate ads, and faking traffic to them to generate money.
This kind of thing has been done before, but never on this scale or with this much effort.
I don’t understand how a VPS IP can appear to be a residential IP?
I understand you can buy an IP from a VPS but then wouldn’t it appear in WHOIS records as part of the VPS’ allocation? How does one “register” an IP address?
Those Russians, lol
Makes money everywhere, everywhere, everywhere…
These hackers got out of the soviet block style houses they going to Moscow
Does America want some more?
Oh here’s two options:
You can move to the US and work as senior software developer. You’ll make 150 to 180 thousand a year to start off with.
Or …
Stay in Russia and make 200 thousand USD a day from Cyber Crime to start with. Soon you’ll work your way up to make 2/3 million USD a day with a group of Cyber criminals.
Choice is yours.
Pete,
When you become a Russian cyber villain, don’t leave Russia, or you might be extradited to a country with laws.
PS
Don’t post pictures of your expensive cars and vacations on VK, Facebook, or instagram.
Those russians are clever.
How they spend all this money they make?
Where i can send my cv to get job ?
1 miljon per day not bad at all.
Dear Brian, thanks for the insight into this business. One thing to add. Actually, I think you stepped back to early. Let me tell you what I mean. First, I did not like the website of Michael Andreev. This seemed to easy for me. If you’re earning a billion dollar per day, you have to hide yourself. If not, other interested parties, who wants to get a share of the pie, find you quickly and will convince you to cooperate. So I did a quick Google images search on his twitter account image, and voila. That image is used by various other twitter accounts to. You will find the result here: goo.gl/vZy9Pm Brian, please do not stop to investigate this and go deeper to find someone who’s real.
Looks like I know who is in charge.