Credit and debit card payments giant Verifone [NYSE: PAY] is investigating a breach of its internal computer networks that appears to have impacted a number of companies running its point-of-sale solutions, according to sources. Verifone says the extent of the breach was limited to its corporate network and that its payment services network was not impacted.
San Jose, Calif.-based Verifone is the largest maker of credit card terminals used in the United States. It sells point-of-sale terminals and services to support the swiping and processing of credit and debit card payments at a variety of businesses, including retailers, taxis, and fuel stations.
On Jan. 23, 2017, Verifone sent an “urgent” email to all company staff and contractors, warning they had 24 hours to change all company passwords.
“We are currently investigating an IT control matter in the Verifone environment,” reads an email memo penned by Steve Horan, Verifone Inc.’s senior vice president and chief information officer. “As a precaution, we are taking immediate steps to improve our controls.”
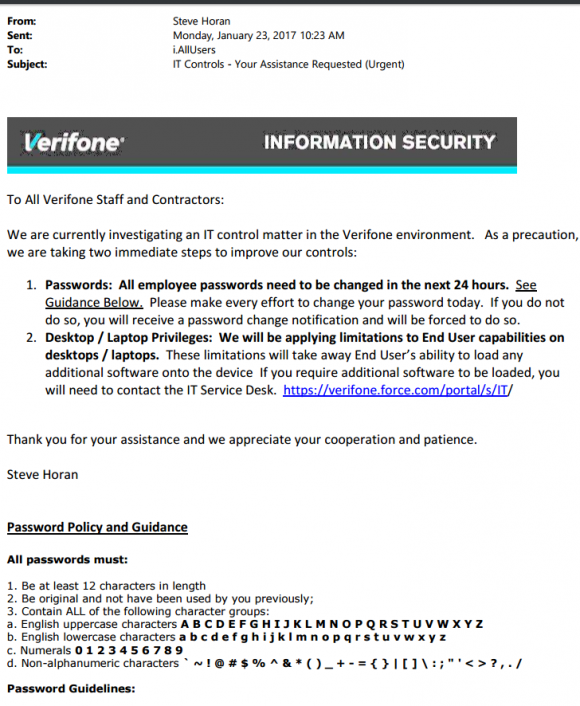
An internal memo sent Jan. 23, 2017 by Verifone’s chief information officer to all staff and contractors, telling them to change their passwords. The memo also states that Verifone employees would no longer be able to install software at will, apparently something everyone at the company could do prior to this notice.
The internal Verifone memo — a copy of which was obtained by KrebsOnSecurity and is pictured above — also informed employees they would no longer be allowed to install software of any kind on company computers and laptops.
Asked about the breach reports, a Verifone spokesman said the company saw evidence in January 2017 of an intrusion in a “limited portion” of its internal network, but that the breach never impacted its payment services network.
“In January 2017, Verifone’s information security team saw evidence of a limited cyber intrusion into our corporate network,” Verifone spokesman Andy Payment said. “Our payment services network was not impacted. We immediately began work to determine the type of information targeted and executed appropriate measures in response. We believe today that due to our immediate response, the potential for misuse of information is limited.”
Verifone’s Mr. Payment declined to answer additional questions about the breach, such as how Verifone learned about it and whether the company was initially notified by an outside party. But a source with knowledge of the matter told KrebsOnSecurity.com that the employee alert Verifone sent out on Jan, 23, 2017 was in response to a notification that Verifone received from the credit card companies Visa and Mastercard just days earlier in January.
A spokesperson for Visa declined to comment for this story. MasterCard officials did not respond to requests for comment.
According to my source, the intrusion impacted at least one corner of Verifone’s business: A customer support unit based in Clearwater, Fla. that provides comprehensive payment solutions specifically to gas and petrol stations throughout the United States — including, pay-at-the-pump credit card processing; physical cash registers inside the fuel station store; customer loyalty programs; and remote technical support.
The source said his employer shared with the card brands evidence that a Russian hacking group known for targeting payment providers and hospitality firms had compromised at least a portion of Verifone’s internal network.
The source says Visa and MasterCard were notified that the intruders appeared to have been inside of Verifone’s network since mid-2016. The source noted there is ample evidence the attackers used some of the same toolsets and infrastructure as the cybercrime gang that last year is thought to have hacked into Oracle’s MICROS division, a unit of Oracle that provides point-of-sale solutions to hundreds of thousands of retailers and hospitality firms.
Founded in Hawaii, U.S. in 1981, Verifone now operates in more than 150 countries worldwide and employ nearly 5,000 people globally.
Update, 1:17 p.m. ET: Verifone circled back post-publication with the following update to their statement: “According to the forensic information to-date, the cyber attempt was limited to controllers at approximately two dozen gas stations, and occurred over a short time frame. We believe that no other merchants were targeted and the integrity of our networks and merchants’ payment terminals remain secure and fully operational.”
Sources told KrebsOnSecurity that Verifone commissioned an investigation of the breach from Foregenix Ltd., a digital forensics firm based in the United Kingdom that lists Verifone as a “strategic partner.” Foregenix declined to comment for this story.
ANALYSIS
In the MICROS breach, the intruders used a crimeware-as-a-service network called Carbanak, also known as Anunak. In that incident, the attackers compromised Oracle’s ticketing portal that Oracle uses to help MICROS’s hospitality customers remotely troubleshoot problems with their point-of-sale systems. The attackers reportedly used that access to plant malware on the support server so they could siphon MICROS customer usernames and passwords when those customers logged in to the support site.
Oracle’s very few public statements about that incident made it clear that the attackers were after information that could get them inside the electronic tills run by the company’s customers — not Oracle’s cloud or other service offerings. The company acknowledged that it had “detected and addressed malicious code in certain legacy Micros systems,” and that it had asked all MICROS customers to reset their passwords.
Avivah Litan, a financial fraud and endpoint solutions analyst for Gartner Inc., said the attackers in the Verifone breach probably also were after anything that would allow them to access customer payment terminals.
“The worst thing is the attackers have information on the point-of-sale systems that lets them put backdoors on the devices that can record, store and transmit stolen customer card data,” Litan said. “It sounds like they were after point-of-sale software information, whether the POS designs, the source code, or signing keys. Also, the company says it believes it stopped the breach in time, and that usually means they don’t know if they did. The bottom line is it’s very serious when the Verifone system gets breached.”
Verifone’s Jan. 23 “urgent” alert to its staff and contractors suggested that — prior to the intrusion — all employees were free to install or remove software at will. Litan said such policies are not uncommon and they certainly make it simpler for businesses to get work done, but she cautioned that allowing every user to install software anytime makes it easier for a hacker to do the same across multiple systems after compromising just a single machine inside the network.
“It sounds like [Verifone] found some malware in their network that must have come from an employee desktop because now they’re locking that down,” Litan said. “But the next step for these attackers is lateral movement within the victim’s network. And it’s not just within Verifone’s network at that point, it potentially expands to any connected partner network or through trusted zones.”
Litan said many companies choose to “whitelist” applications that they know and trust, but to block all others. She said the solutions can dramatically bring down the success rate of attacks, but that users tend to resist and dislike being restricted on their work devices.
“Most companies don’t put in whitelists because it’s hard to manage. But that’s hardly an excuse for not doing it. Whitelisting is very effective, it’s just a pain in the neck for users. You have to have a process and policies in place to support whitelisting, but it’s certainly doable. Yes, it’s been beaten in targeted attacks before — where criminals get inside and steal the code-signing keys, but it’s still probably the strongest endpoint security organizations can put in place.”
Verifone would not respond to questions about the duration of the breach in its corporate networks. But if, as sources say, this breach lasted more than six months, that’s an awful long time for an extremely skilled adversary to wander around inside your network undetected. Whether the intruders were able to progress from one segment of Verifone’s network to another would depend much on how segmented Verifone’s network is, as well as the robustness of security surrounding its various corporate divisions and many company acquisitions over the years.
The thieves who hacked Target Corp. in 2013, for example, were able to communicate with virtually all company cash registers and other systems within the company’s network because Target’s internal network resembled a single canoe instead of a massive ship with digital bulkheads throughout the vessel to stop a tiny breach in the hull from sinking the entire ship. Check out this story from Sept. 2015, which looked at the results of a confidential security test Target commissioned just days after the breach (spoiler alert, the testers were able to talk to every Target cash register in all 2,000 stores after remotely commandeering a deli scale at a single Target store).
The card associations often require companies that handle credit cards to undergo a third-party security audit, but only if there is evidence that customer card data was compromised. That evidence usually comes in the form of banks reporting a pattern of fraud on customer cards that were all used at a particular merchant during the same time frame. However, those reports come slowly — if at all — and often trickle up to the card brands weeks or months after stolen cards end up for sale in bulk on the cybercrime underground.
Corporate network compromises or the theft of proprietary source code (e.g. the same code that goes on merchant payment devices) generally do not trigger a mandatory third-party investigation by a security firm approved by the card brands, Litan said, although she noted that breaches which can be shown to have a material financial impact on the company need to be disclosed to investors and securities regulators.
“There’s no rule anywhere that says you have to disclose if your software’s source code is stolen, but there should be,” Litan said. “Typically, when a company has a breach of their corporate network you think it might hurt the company, but in a case when the company’s software is stolen and that software is used to transmit credit card data then everyone else is hurt.”
LOW-HANGING FRUIT
Litan said if the attackers who broke into Verifone were indeed targeting payment systems in the filling station business, they were going after the lowest of the low-hanging fruit. The fuel station industry is chock-full of unattended, automated terminals that have special security dispensation from Visa and Mastercard: Fuel station owners have been given more time than almost any other industry to forestall costly security upgrades for new card terminals at gas pumps that are capable of reading more secure chip-enabled credit and debit cards.
The chip cards are an advancement mainly because they are far more difficult and costly for thieves to counterfeit or clone for use in face-to-face transactions — by far the most profitable form of credit card fraud (think gift cards and expensive gaming consoles that can easily be resold for cash).
After years of lagging behind the rest of the world — the United States is the last of the G20 nations to move to chip cards — most U.S. financial institutions are starting to issue chip-based cards to customers. However, many retailers and other card-accepting locations have been slow to accept chip based transactions even though they already have the hardware in place to accept chip cards (this piece attempts to explain the “why” behind that slowness).
In contrast, chip-card readers are still a rarity at fuel pumps in the United States, and Litan said they will continue to be for several years. In December 2016, the card associations announced they were giving fuel station owners until 2020 to migrate to chip-based readers.
Previously, fuel station owners that didn’t meet the October 2017 deadline to have chip-enabled readers at the pump would have been on the hook to absorb 100 percent of the costs of fraud associated with transactions in which the customer presented a chip-based card but was not asked or able to dip the chip. Now that they have another three years to get it done, thieves will continue to attack fuel station dispensers and other unattended terminals with skimmers and by attacking point-of-sale terminal hardware makers, integrators and resellers.
HOW WOULD YOUR EMPLOYER FARE?
My confidential source on this story said the closest public description of the email phishing schemes used by the Russian crime group behind both the MICROS and Verifone hacks comes in a report earlier this year from Trustwave, a security firm that often gets called in to investigate third-party data breaches. In that analysis, Trustwave describes an organized crime gang that routinely sets up phony companies and corresponding fake Web sites to make its targeted email phishing lures appear even more convincing.
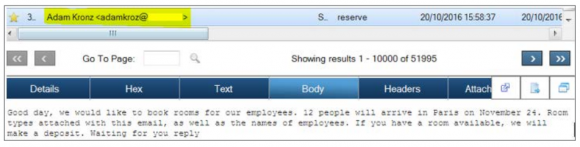
A phishing lure used in a malware campaign by the same group that allegedly broke into MICROS and Verifone. Source: Trustwave Grand Mars report.
The messages from this group usually include a Microsoft Office (Word or Excel) document that has been booby-trapped with malicious scripts known as “macros.” Microsoft disables macros by default in recent versions of Office, but poisoned document lures often come with entreaties that prompt recipients to override Microsoft’s warnings and enable them manually.
Trustwave’s report cites two examples of this social engineering; one in which an image file is used to obscure a warning sign (see below), and another in which the cleverly-crafted phishing email was accompanied by a phone call from the fraudsters to walk the recipient through the process of manually overriding the macro security warnings (and in effect to launch the malware on the local network).
According to Trustwave, this Russian hacking group prefers to target companies in the hospitality industry, and is thought to be connected to the breaches at a string of hotel chains, including the card breach at Hyatt that compromised customer credit and debit cards at some 250 hotels in roughly 50 countries throughout much of 2015.
In a common attack, the perpetrators would send a phishing email from a domain associated with a legitimate-looking but fake company that was inquiring about spending a great deal of money bringing many important guests to a specific property on a specific date. The emails are often sent to sales and event managers at these lodging facilities, with instructions for checking the attached (booby-trapped) document for specifics about guest and meeting room requirements.
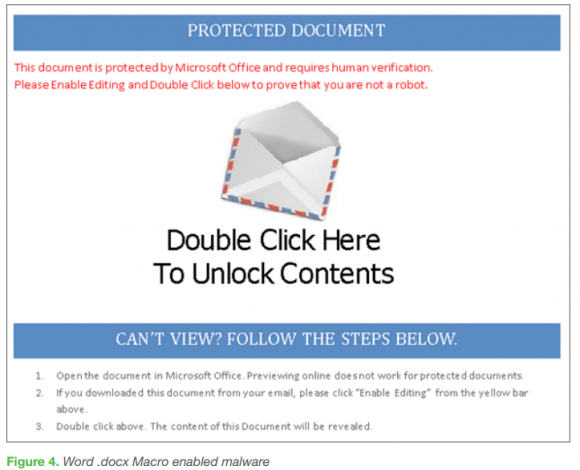
This phishing lure prompts users to enable macros and then launch the malware by disguising it as a message file. Source: Trustwave.





Kgb run the world!
How? – you create virus..you sell virus detectors.
you create criminals and terrorists you only you
take them off.
Everytime when is bigger arrests..then the law will be changed
rules will be Forced.
Yes guys its thats simple!!
What you can do about it? Nothing just ignore.
more panic more reactions …so its all provocations.
silmple
This. I have no idea what your point is, but I’m leaving it here anyway. I guess you’re saying everyone’s got their arses covered (including consumers) so this is a victimless type crime, is that it?
I believe he is saying that the KGB is ensuring it’s own existence by creating problems and then solving those problems.
(you create virus..you sell virus detectors.
you create criminals and terrorists you only you
take them off.)
Or something is ensuring its own existence by doing that, not sure what the KGB has to do with this exactly.
No! my point is whole thing is covered conspiracy theory.
maybe thats the way how world should work. I dont know.
to be honest to undestood about your article here..it takes better brain. i got not idea what is the Verizone. This article is for tech buffs…or crooks themselfes.
average joe cant read nothing here. Average joe will blame goverment and our leaders who-‘s main duty is just keep us safe.and force the like law -enfocememts do it.
why we shpuld care? For what the Fbi cia and homeland security get their wages?? To eat just mcdonalds??
World is abput average joe working and paying taxes and feeding his family. but whole this complicated information here not for avwrage Joe. And whole your blog is so complicated..to read even with good english! i dont think average joe have any time to learn about fraud or scams. its just with too complicated structure…im sure our life could be better of without all this high teck complicated terms and words.
life is simple..you work and you get salary. Thats it
Please take down or modify the picture of the email that went to all VeriFone Employees. No sense in helping out spammers and phishers by showing them what their internal mails look like.
Thanks!
I most certainly will not take it down. Maybe you haven’t read the whole story, but it’s likely the phishers in this case already know exactly what their internal emails look like.
The snap of the e-mail absolutely gives substance to the article. Definitely a story I’ll continue to follow.
Kudos for your reply Krebs, both for the substance and the style… “I most certainly will not” has a dignified fury to it that I haven’t enjoyed in years. I must work this into a work conversation soon.
…and there’s a strongly-implied “Up Yours!” rightly embedded in it as well.
+1 for Brian’s response!
Yes – knowing what the email looks like is paramount – and give one a pattern for what future phishing emails may appear.
Kudos to Brian!
Shut the hell up, Mark. Your request is asinine and I applaud Krebs for leaving it up.
great article !
Hi Brian, Another nice investigation! I’m curious if the Verifone laptops were used to run applications or were mobile dumb terminals to access a more secure company network running VDI.
If the laptops had admin privileges and were used to connect to the company network directly or over VPN, it would seem that Verifone got a pretty predictable outcome.
If Verifone was hoping that it was safe from compromised endpoints because they were just being used as fat clients…..wouldn’t that seem almost as naive, but point to different problems with the Verifone as well as different attack methods?
I am not a techie and just happen to read this article because we use Verfone and read a bunch of the comments. Can you explain why accessing your computer at work from home let’s say via a VPN is not a good idea? Also, allowing someone administrative rights to their PC…why is that a bad thing? Just curious….thanks!
Good question Donna. But your statement right there illustrates why security is needed. If you have to ask the question, you should not have Admin rights. It’s users like you who get fooled by phishing and malware and spam.
Do us a favor and stop using computers.
Why so rude???? Here I am reaching out to ask questions that I am curious about (but don’t have responsibility for) and I get that kind of reaction???? Just wanting to learn new things. Wow!
Donna, using a vpn from home is very convenient, but your PC is on the company’s network and if someone hacks your PC, they get the network.
Of course IT could limit the damage by less sophisticated attackers by keeping your accesss compartmentalized/segmented, but a company that lets its laptop users have admin rights probably isn’t so sharp at those other controls. Beyond vpn, there are virtual desktops you can access from a PC so your laptop only send keystrokes and mouse movements and only receives graphics to display on your monitor. These can be safer and more efficient in bandwidth, but depending on the setup might allow an attacker to just get your login info and then access the company virtual desktops from anywhere they want.
there are lots of ways you can learn more about how having admin rights on your pic is like
Sorry for the ID10t error.
Using your pc with admin rights is like running with scissors. For kicks maybe you could check out some of Brian’s old articles covering how to secure a pc if the Washington Post still has them online. The programs have changed but the principles have not. good luck
Thank you for the explanation…..it is appreciated!
Donna,
For example: a hacker sends a user an email that directs them to run an executable file, which will install a virus, and the user runs it. If the user does not have admin privileges, the virus cannot be installed.
If the user DOES have admin privs, and the virus gets installed on their home computer, then if they connect to their work desktop, the virus has a chance to infect the work computer, too.
Hope that helps,
Laura
Thanks for the explanation!!!!!
Another very thorough job Brian, thanks. Are you planning any comment on Wikileaks Vault7, especially the CIA’s choice to use rather than report 0Day vulnerabilities?
Possibly. If I have something to add to the story, as opposed to just re-reporting it. It has already received very wide coverage.
Thanks Krebs! your stuff is always content dense, and I appreciate it!
About the .docx file format for Microsoft Word – wouldn’t it need to be .docm or pre-2007 .doc to have macros? I opened a new Word document, entered some “hello world” Visual Basic for Applications code, and it did this when trying to save it:
“The following cannot be saved in a macro-free document:
– VBA Project
To save a file with these features… choose a macro-enabled file type…”
If that’s the case, email attachment filter rules could block .docm files just like .exe without affecting non-macro .docx files.
That’s exactly what we do. We send all dotm, dot, docm, xlsm, xltm, etc . to a central admin quarantine that we review several times a day to check for legitimate messages that we deliver but block the vast majority which are malicious. Some days we have literally hundreds of these that get by the spam filter but get stopped here. Some days, none, but it’s worth it to avoid the employee opening these malicious attachments.
Cardinal sin, local administrator on users machines! Bad! if they were silly enough to allow that i can’t imagine what their network looks like……
So essentially they allowed their users to be local admins on their machines. Inexcusable in today’s enterprise, especially for one in the payments or financial industry.
Is it even possible to pass PCI compliance when client machines can install whatever software they want?
PAY has had at minimum, 6 weeks to determine the scope of the breach. That they’re still being this dodgy with details indicates to me they have no idea what they’re looking at. Not at all surprising to me, but this certainly makes the case for much stronger reporting and disclosure laws.
Wait, the spokesperson’s name for Verifone is Mr. Payments? How epic is that. 🙂
Yes, it is. http://global.verifone.com/company/press-room/
I was hoping to hear back from Betty Declined in payroll, but alas she never rang. Their customer service rep Summer Sales also owes me a call.
Have you tried Chris Mammone in Investor Relations?
I am starting to wonder if Verifone hires based on name etymology or assonance.
As a customer and given what I know of how Verifone operates internally, it wouldn’t surprise me in the least.
Our HR manager is Helen Wait.
When we have a personnel issue, we’re told to go to Helen Wait.
Brian,
I thought at first that you were making some kind of corny joke about “Mr. Payment.” I had to go back and re-read the previous paragraph before I realized that was his real name!!!!!
Can’t make this stuff up!!
Thank you, Brian, for keeping us informed and demonstrating integrity in your reporting.
I really don’t see what further information can be identified about their standards by this image being shared?
It’s really basic stuff and sounds like they’re reinforcing the set process for additional software installations.
Unless Verifone denies its authenticity, it’s excellent primary source documentation that seems to verify at least 3 things: 1) security breach, 2) Verifone has a strong password policy 3) Verifone allowed most if not all laptop users to have local admin privileges (yikes).
Yes, it’s awkward that we see a user name, the alias for an internal distribution list and the internal branding from their IT team, but Verifone has lots of damage control and remediation to do – adding that to the list is trivial.
OMG, MR. Payment?
what a perfect name.
Nice article, thanks for the great read.
Mr. Payment ? Is that a real person ?
That’s really his name. I checked on LinkedIn.
Re: Low-Hanging Fruit
While in agreement that non-EMV pumps are ripe for attack, the lack of EMV capabilities in and of itself wouldn’t increase the risk of intrusion due to malware on a corporate users laptop. Older technology in those pumps may not have the most current security controls available, but there are plenty of other options available to a company like VeriFone to ensure proper segmentation and access. This section added context, just not necessarily to the specific threat being observed.
Brian,
At age 73 I am amazed at your knowledge, skill, contacts,.. and yes, balls, to go where most honest people fear to gather information to write these articles to educate us. And I don’t know how you put up with DOS attacks, swatting, etc.. Things like that scare the %&$# out of normal people like me.
Thanks for all you do.. Take care, Steve..
“Mr. Payment” … interesting.
Sincerely,
Professor Curious
Brian’s fine article refers to
> Verifone spokesman Andy Payment.
I suppose he has co-workers named Dave Decline and Charlie Chargeback.
Seriously, it’s good security discipline to avoid using role accounts — that is, instead of using “root” or “Administrator” to update systems, I should use my own named account, with elevated privs where needed.
It looks like this company uses pseudonyms for their PR spokespeople. I hope this practice doesn’t extend to their internal IT systems.
Typo in story? “…Oracle’s ticking portal…”
Why was it ticking?
That would be funny if it were. No, but I bet that typo was just tickling you crazy, eh? 🙂 It’s fixed, thanks. Ticketing was the word.
Well, Java goes ‘boom’ every month, so why not their portal software too?
Forgot to mention; your work would make one heck of a TV series. *smile*
Cheers!
There was talk of a movie…
https://krebsonsecurity.com/2014/03/sony-pictures-plans-movie-about-yours-truly/
On a related note, none of the gas stations which have EMV readers nearby me (in the US) have turned EMV support on.
The reason is that one of them tried.
EMV cards at gas pumps (at least as currently configured) need to be kept in the pump during use to authorize the final transaction amount. And people kept forgetting to remove the cards after they finished pumping gas.
So a gas station was left with a stack of hundreds of credit cards being left in their pumps.
Rather than have to deal with teaching everyone, they turned EMV support off until it becomes more common. Given the station’s location, they are not concerned about the fraud risk.
Very good point.
Folks forget to remove the nozzle from their tank before driving off. What are the odds they’ll remember to remove their card…
I’ve been using credit cards for 40 years and never left or lost one.
Since the appearance of chip readers, I’ve tried my best to leave my card behind. More than once I’ve had to turn around and grab it.
Only succeeded once, and it was in an old style mag strip reader at a card lock gas pump.
Fortunate for me, it was at a track where I was racing and another racer recognized the name and brought the card back to me.
I asked him if he filled his car with it first. He said no, though I would have been fine with it if he did.
Seems that could be managed to some degree as with cash: prepay a set amount, and require card removal before activating pumping. I suppose unused amounts could be credited back to the card/account, but doubt that can be done without a new card transaction?
A lot of gas stations where I am manage this by taking a preset authorised amount and just debiting the actual fuel spend when processing. No need for refunds/reversals – just ties up the original authorisation in the cardholder’s account for a while.
The problem is the preauthorization value.
You don’t know initially how big a tank is (perhaps 20 gallons?). At $4+/gallon, that’s ~$90..$100. You could easily have a gas customer whose card can’t handle a $100 preauth.
Hotels use preauth all the time.
It’s definitely possible to get this mostly right. IIRC PayPal had a gas station demo which handled this.
In the old days, pumps let you say “I want $5/gas / $10/gas / $20/gas / FULL”.
I’m not sure that’s still around, I think between price variability, and wanting customers to fill up, the feature is probably mostly gone.
If it was returned, then using preauth and then correcting to lower would be much more workable…
We have been using EMV cards, and EMV terminals here in Europe at least since 2003, no problem. We were probably early adopters. Where I live, more that 99% of all transaction are chip nowadays. It took some time to get the shops and cardholders to use the chip, even after the technical solution was in place. We have recently started to roll out EMV contactless cards and terminals but that is catching on really fast.
The flow in case of an automated fuel dispensers, AFD, is now:
The card is inserted in the ‘terminal’, and the PIN is verified. The PIN verification can be done securely by the card. A transaction is performed to the Cardholders bank with an estimated amount (from the pump). The response will contain an amount available, less than or equal the estimated amount. The fuel pump now allowed to supply fuel up to the amount available. The terminal will, once you hang up the hose send the actual transaction. It shall be sent within 20 minutes. Terminals not able to handle ‘amount available’ will get a declined answer if the estimated amount is larger than the amount available.
The problem with left over card can easily be handled by not starting the pump before the card has been removed from the reader.
A reason for non-active EMV readers could be that the Acquirer (the Merchants bank) and the Issuer (the Cardholders bank) are not able to handle the AFD flow yet.
Re: “EMV cards at gas pumps (at least as currently configured) need to be kept in the pump during use to authorize the final transaction amount. And people kept forgetting to remove the cards after they finished pumping gas.” This is false. EMV data is not required on the Pre-Auth Completion. Come to Canada and get some gas at an EMV pump, it is not rocket science. I can’t believe the amount of whining and misinformation floating around with the introduction of EMV at the point of sale. It’s no more difficult than signing a receipt and you don’t waste time with cashiers looking for a pen.
It took a breach for them to lock down software installs?
Lemme guess…. users were admin on the machines too?
Benny Hill I.T.
Was recently working with a company and their staff were amazed that our staff didn’t have Admin access on our machines: it caused them to do a software redesign before they could supply one of their products to us that was built assuming Admin privileges for install. This was from a global multi-industy leader with annual revenues in the range of $140bn and over 300,000 employees and they still let that stuff happen. Amazing.
This is a rampant problem in so many software packages, even those designed for highly regulated, supposedly security-focused sectors like health care and finance. The companies say the software requires admin rights (sometimes they are wrong and it works just fine without admin after install) or it requires less-than-secure settings like turning off Data Execution Protection or Address Space Layout Randomization.
These are not mom and pop or startups either. They have the resources to do it right, are expected to be doing it right, and still fall back on what’s easier.
Man, it is incredible how many software packages require admin access to run. I switched to Mac a decade ago and make it a point on all of my computers, Windows and Mac, that my user account is not an admin account.
I sometimes wonder how many problems could be avoided if network admins enforced this rule, and purchasing directors told vendors “We’re not buying your software if it requires admin access to install and run.”
Brian:
Thank you very much for this informative article! Keep up the good work!
Thanks Brian for your continued insightful reporting on these matters. Mr. Payment as their spokesperson is too rich. Larry Speakes was Reagan’s press secretary. These 2 guys we’re born into their careers.
I just had a cc declined in the last 24 hrs, was searching the web for info on data breaches, and found your blog. I called the cc company to ask why my card was declined and they said a merchant reported a breach. (They also declined to identify who the merchant was.) I think either someone else major has been breached, or this breach was larger than reported. The card worked fine yesterday evening and tonight was declined. The last three places I used the card was Wal-Mart, Sam’s Club, and Home Depot. My guess is that they all use Verifone.
The article does not imply that Verifone terminals themselves are suspect or at risk. The terminals themselves have very different security models than PCs and are independently validated by labs that try to attack the terminals.
Verifone’s services businesses are the issue here – their payment gateways and other similar services, not the physical card readers.
It’s also possible, though unlikely at this point, that Verifone’s software that is used by merchants – deployed in a non-hosted manner – could’ve been compromised and installed by merchants.
Merchants using point to point encryption with these software solutions will never be exposed to clear card data. The merchants you listed use a mix of Ingenico and Verifone and also use P2PE.
Andy Payment is his real name too.
Locally skimmed cards can be used very quickly, but a breached card may take weeks or months to be used. We’ve seen a recent uptick in fraud on cards from the Noodles & Co breach Krebs reported on back in May.
the biggest security breach at verifone is that they are using the same default password for all its POS since 20 years…..
If installed correctly the default passwords are to be changed by owner at time of install….not Verifones fault…either tech is at fault fornot training correctly or owner didnt listen when tech told them what to do. I have been a service tech for 27 years and have Installed Verifone and Gilbarco pos equipment. Its the owners that should take liabilty when they don’t follow explicit instructions to setup secure passwords.
Time to start paying with cash only, or refill debt cards. good grief
Guys just go to your local humen resorce center.
tell them you had enough…you want RFiED chip.
RFIED= no fraud no crime!
Little chip under ur skin can let you live free. Without fraud.
only Usa allowing fraud happend. Other countries dont. So how come ?
You will never get a Christian to do that – they would consider it the mark of the beast!
Glad to see the Verifone security team gets to get some additional controls implemented as a result of this limited breach.
No can not use cash !! Only criminals money lounders and drug dealers Use cash. Regular person use credit card.
be law abide citizen. Dont use cash only criminals use cash
For the past several years, the senior management of Verifone has intentionally reduced its IT staff to below minimum standards, while the company as a whole, as well as IT operations, has been expanding. A motto that has been circulating in the company for years is, “do more with less.” This mentality has directly caused their undoing, especially when it comes to the corporate IT department and security. Starting with CIO Steve Horan, and those above him, have refused to allocate sufficient funding for resources for years despite the recommendations of lower and middle management backed by factual data. These resources include both staff as well as updating their systems, software, and other IT solutions. This has left the corporate IT department in a perpetual state of barely being functional and constantly struggling to stay afloat on a daily basis. This breach is a direct result of senior management’s lack of focus, priority, and gross negligence towards its corporate IT department. Verifone, in damage control mode, has responded to this leak attempting to downplay the breach and its impact, giving the appearance that the breach is contained and under control, and that is just not true.
Sounds like a disgruntled employee…