WikiLeaks on Tuesday dropped one of its most explosive word bombs ever: A secret trove of documents apparently stolen from the U.S. Central Intelligence Agency (CIA) detailing methods of hacking everything from smart phones and TVs to compromising Internet routers and computers. KrebsOnSecurity is still digesting much of this fascinating data cache, but here are some first impressions based on what I’ve seen so far.
First, to quickly recap what happened: In a post on its site, WikiLeaks said the release — dubbed “Vault 7” — was the largest-ever publication of confidential documents on the agency. WikiLeaks is promising a series of these document caches; this first one includes more than 8,700 files allegedly taken from a high-security network inside CIA’s Center for Cyber Intelligence in Langley, Va.
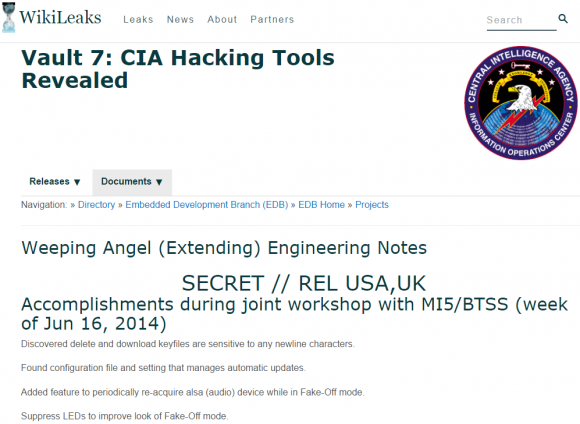
The home page for the CIA’s “Weeping Angel” project, which sought to exploit flaws that could turn certain 2013-model Samsung “smart” TVs into remote listening posts.
“Recently, the CIA lost control of the majority of its hacking arsenal including malware, viruses, trojans, weaponized ‘zero day’ exploits, malware remote control systems and associated documentation,” WikiLeaks wrote. “This extraordinary collection, which amounts to more than several hundred million lines of code, gives its possessor the entire hacking capacity of the CIA. The archive appears to have been circulated among former U.S. government hackers and contractors in an unauthorized manner, one of whom has provided WikiLeaks with portions of the archive.”
Wikileaks said it was calling attention to the CIA’s global covert hacking program, its malware arsenal and dozens of weaponized exploits against “a wide range of U.S. and European company products, includ[ing] Apple’s iPhone, Google’s Android and Microsoft’s Windows and even Samsung TVs, which are turned into covert microphones.”
The documents for the most part don’t appear to include the computer code needed to exploit previously unknown flaws in these products, although WikiLeaks says those exploits may show up in a future dump. This collection is probably best thought of as an internal corporate wiki used by multiple CIA researchers who methodically found and documented weaknesses in a variety of popular commercial and consumer electronics.
For example, the data dump lists a number of exploit “modules” available to compromise various models of consumer routers made by companies like Linksys, Microtik and Zyxel, to name a few. CIA researchers also collated several pages worth of probing and testing weaknesses in business-class devices from Cisco, whose powerful routers carry a decent portion of the Internet’s traffic on any given day. Craig Dods, a researcher with Cisco’s rival Juniper, delves into greater detail on the Cisco bugs for anyone interested (Dods says he found no exploits for Juniper products in the cache, yet). Meanwhile, Cisco has published its own blog post on the matter.
WHILE MY SMART TV GENTLY WEEPS
Some of the exploits discussed in these leaked CIA documents appear to reference full-on, remote access vulnerabilities. However, a great many of the documents I’ve looked at seem to refer to attack concepts or half-finished exploits that may be limited by very specific requirements — such as physical access to the targeted device.
The “Weeping Angel” project’s page from 2014 is a prime example: It discusses ways to turn certain 2013-model Samsung “smart TVs” into remote listening devices; methods for disabling the LED lights that indicate the TV is on; and suggestions for fixing a problem with the exploit in which the WiFi interface on the TV is disabled when the exploit is run.
ToDo / Future Work:
Build a console cableTurn on or leave WiFi turned on in Fake-Off mode
Parse unencrypted audio collection
Clean-up the file format of saved audio. Add encryption??
According to the documentation, Weeping Angel worked as long as the target hadn’t upgraded the firmware on the Samsung TVs. It also said the firmware upgrade eliminated the “current installation method,” which apparently required the insertion of a booby-trapped USB device into the TV.
Don’t get me wrong: This is a serious leak of fairly sensitive information. And I sincerely hope Wikileaks decides to work with researchers and vendors to coordinate the patching of flaws leveraged by the as-yet unreleased exploit code archive that apparently accompanies this documentation from the CIA.
But in reading the media coverage of this leak, one might be led to believe that even if you are among the small minority of Americans who have chosen to migrate more of their communications to privacy-enhancing technologies like Signal or WhatsApp, it’s all futility because the CIA can break it anyway.
Perhaps a future cache of documents from this CIA division will change things on this front, but an admittedly cursory examination of these documents indicates that the CIA’s methods for weakening the privacy of these tools all seem to require attackers to first succeed in deeply subverting the security of the mobile device — either through a remote-access vulnerability in the underlying operating system or via physical access to the target’s phone.
As Bloomberg’s tech op-ed writer Leonid Bershidsky notes, the documentation released here shows that these attacks are “not about mass surveillance — something that should bother the vast majority of internet users — but about monitoring specific targets.”
By way of example, Bershidsky points to a tweet yesterday from Open Whisper Systems (the makers of the Signal private messaging app) which observes that, “The CIA/Wikileaks story today is about getting malware onto phones, none of the exploits are in Signal or break Signal Protocol encryption.”
The company went on to say that because more online services are now using end-to-end encryption to prevent prying eyes from reading communications that are intercepted in-transit, intelligence agencies are being pushed “from undetectable mass surveillance to expensive, high-risk, targeted attacks.”
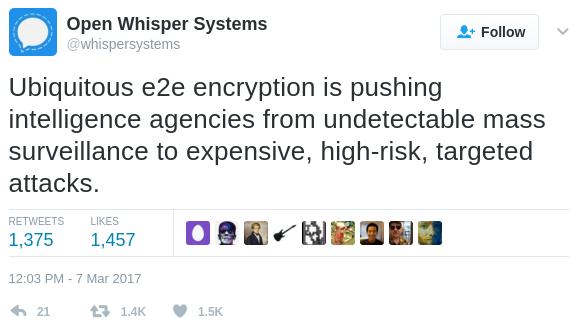
A tweet from Open Whisper Systems, the makers of the popular mobile privacy app Signal.
As limited as some of these exploits appear to be, the methodical approach of the countless CIA researchers who apparently collaborated to unearth these flaws is impressive and speaks to a key problem with most commercial hardware and software today: The vast majority of vendors would rather spend the time and money marketing their products than embark on the costly, frustrating, time-consuming and continuous process of stress-testing their own products and working with a range of researchers to find these types of vulnerabilities before the CIA or other nation-state-level hackers can.
Of course, not every company has a budget of hundreds of millions of dollars just to do basic security research. According to this NBC News report from October 2016, the CIA’s Center for Cyber Intelligence (the alleged source of the documents discussed in this story) has a staff of hundreds and a budget in the hundreds of millions: Documents leaked by NSA whistleblower Edward Snowden indicate the CIA requested $685.4 million for computer network operations in 2013, compared to $1 billion by the U.S. National Security Agency (NSA).
TURNABOUT IS FAIR PLAY?
NBC also reported that the CIA’s Center for Cyber Intelligence was tasked by the Obama administration last year to devise cyber attack strategies in response to Russia’s alleged involvement in the siphoning of emails from Democratic National Committee servers as well as from Hillary Clinton‘s campaign chief John Podesta. Those emails were ultimately published online by Wikileaks last summer.
NBC reported that the “wide-ranging ‘clandestine’ cyber operation designed to harass and ’embarrass’ the Kremlin leadership was being lead by the CIA’s Center for Cyber Intelligence.” Could this attack have been the Kremlin’s response to an action or actions by the CIA’s cyber center? Perhaps time (or future leaks) will tell.
Speaking of the NSA, the Wikileaks dump comes hot on the heels of a similar disclosure by The Shadow Brokers, a hacking group that said it stole malicious software from the Equation Group, a highly-skilled and advanced threat actor that has been closely tied to the NSA.
What’s interesting is this Wikileaks cache includes a longish discussion thread among CIA employees who openly discuss where the NSA erred in allowing experts to tie the NSA’s coders to malware produced by the Equation Group. As someone who spends a great deal of time unmasking cybercriminals who invariably leak their identity and/or location through poor operational security, I was utterly fascinated by this exchange.
BUG BOUNTIES VS BUG STOCKPILES
Many are using this latest deluge from WikiLeaks to reopen the debate over whether there is enough oversight of the CIA’s hacking activities. The New York Times called yesterday’s WikiLeaks disclosure “the latest coup for the antisecrecy organization and a serious blow to the CIA, which uses its hacking abilities to carry out espionage against foreign targets.”
The WikiLeaks scandal also revisits the question of whether the U.S. government should instead of hoarding and stockpiling vulnerabilities be more open and transparent about its findings — or at least work privately with software vendors to get the bugs fixed for the greater good. After all, these advocates argue, the United States is perhaps the most technologically-dependent country on Earth: Surely we have the most to lose when (not if) these exploits get leaked? Wouldn’t it be better and cheaper if everyone who produced software sought to crowdsource the hardening of their products?
On that front, my email inbox was positively peppered Tuesday with emails from organizations that run “bug bounty” programs on behalf of corporations. These programs seek to discourage the “full disclosure” approach — e.g., a researcher releasing exploit code for a previously unknown bug and giving the affected vendor exactly zero days to fix the problem before the public finds out how to exploit it (hence the term “zero-day” exploit).
Rather, the bug bounties encourage security researchers to work closely and discreetly with software vendors to fix security vulnerabilities — sometimes in exchange for monetary reward and sometimes just for public recognition.
Casey Ellis, chief executive officer and founder of bug bounty program Bugcrowd, suggested the CIA WikiLeaks disclosure will help criminal groups and other adversaries, while leaving security teams scrambling.
“In this mix there are the targeted vendors who, before today, were likely unaware of the specific vulnerabilities these exploits were targeting,” Ellis said. “Right now, the security teams are pulling apart the Wikileaks dump, performing technical analysis, assessing and prioritizing the risk to their products and the people who use them, and instructing the engineering teams towards creating patches. The net outcome over the long-term is actually a good thing for Internet security — the vulnerabilities that were exploited by these tools will be patched, and the risk to consumers reduced as a result — but for now we are entering yet another Shadow Brokers, Stuxnet, Flame, Duqu, etc., a period of actively exploitable 0-day bouncing around in the wild.”
Ellis said that — in an ironic way, one could say that Wikileaks, the CIA, and the original exploit authors “have combined to provide the same knowledge as the ‘good old days’ of full disclosure — but with far less control and a great many more side-effects than if the vendors were to take the initiative themselves.”
“This, in part, is why the full disclosure approach evolved into the coordinated disclosure and bug bounty models becoming commonplace today,” Ellis said in a written statement. “Stories like that of Wikileaks today are less and less surprising and to some extent are starting to be normalized. It’s only when the pain of doing nothing exceeds the pain of change that the majority of organizations will shift to an proactive vulnerability discovery strategy and the vulnerabilities exploited by these toolkits — and the risk those vulnerabilities create for the Internet — will become less and less common.”
Many observers — including a number of cybersecurity professional friends of mine — have become somewhat inured to these disclosures, and argue that this is exactly the sort of thing you might expect an agency like the CIA to be doing day in and day out. Omer Schneider, CEO at a startup called CyberX, seems to fall into this camp.
“The main issue here is not that the CIA has its own hacking tools or has a cache of zero-day exploits,” Schneider said. “Most nation-states have similar hacking tools, and they’re being used all the time. What’s surprising is that the general public is still shocked by stories like these. Regardless of the motives for publishing this, our concern is that Vault7 makes it even easier for a crop of new cyber-actors get in the game.”
This almost certainly won’t be the last time KrebsOnSecurity cites this week’s big CIA WikiLeaks trove. But for now I’m interested to hear what you, Dear Readers, found most intriguing about it? Sound off in the comments below.




In fact Donald Trump has problems…with hacking.
anyways big fish is Putin. Putin with all his cybermafia is good friend of D.Trump.
needless to say a lot data breaches been in places wich belong to Trump organisation.
Needless to say this wikileaks are just charade.
cia.fsb.sbu.mossad and all others playing the game just together.
anyways its just business nothing personal
Troll much Peroy?? Thats Exactly opposite of what the wikileak data shows??? Go back to the media matters holding Queue please.
It’s way too easy to sell to the alt-LEFt, the believe everything they publish.
whole point is you can expose…yes but then what??
Nothing the circus will go on.
wikkleaks guy if he going to expose some very dangerous facts
then they will take him down in 5min. Guaranteed 100%
So its not harmful information.
if someone will dare to bring out the names with facts and connections im sure that guy would be taken care by any world secret services. Dont forget every law enforcement and secret services working together side by side.
Its fact. this Snowden can do his kids play with this kindergarden non harmful information as longes there is no facts..names or connections.
Anyways people who got power and influence im sure they are so sure about their positions they dont care much. You can expose everything im sure they still just dont care.
The only question is; Who cares??? So what ??
“So what?”: Hacking tools/scripts developed by the CIA are now available with a trove of 0-day exploits to anyone interested. A number of the exploits are for networking infrastructure.
“Who cares?”: Anyone who enjoys the use of the internet should care, because it poses a very real threat to our connectivity. The massive ddos that took down large swaths of the internet did so using zombie bot-nets, this information stockpiled by the cia and then leaked can now be used by the orchestrators of that particular bot net to hold more of the internet hostage. Collateral damage in all this will be our freedom to move about the internet as nation states react to new and rapidly accelerated threats.
Sigh. Comments like yours are exactly why the world is going the way it is. Please, go back to sleep.
Great article Brian. Please do keep the analysis coming. My team is finally learning to read your information and take action AHEAD of my emails to them! Keep up the great work!@
What we are all watching is this great nation being destroyed little by little by some of their own citizens,
I, a patriot, never thought I’d see something like this in my lifetime. And there’s nothing we can do about. The cabal in power is set on to destroy everything, in the works of Steve Banner.
We allow these traitors to go into power, and now instead of taking control, Republican voters are afraid to admit they were wrong. So, we all sit here and wait while this country disintegrate.
Assange’s objective is to destroy us, he hates the US. And he’s a useful idiot bought and paid for by the Russians.
At least Assange doesn’t try to hide his hatred. Unlike the greedy judases in power who sold us in order to make a profit.
It’s a sad sad story. 🙁
WikiLeaks published its first document in 2006, so this goes beyond current events and the political party in power.
WikiLeaks would not exist without those providing the information to them.
Edward Snowden is a patriot, not you.
The genie was always out of the bottle. Your response is out of fear, as now you know what’s been going on. Know for sure that this is a collection of exploits that crims were not stopped from using so that the CIA could keep using them to. They turn a blind eye on crime so they can use the same tools. The CIA does the opposite of making people feel safe, once they know that they don’t do.
Assuming that the CIA does not have any more hacking tools that that we don’t know about the only people who very hacking tools to are criminals, countries like China, Russia, North Korea and and so on. Feel safer?
I agree. Every major nation state has something similar to the arsenal that the CIA possessed. This just slows down our ability to act on a level playing field with the rest of the world. I hate Assange, I hate Trump, I hate President Bannon. And most of all Russia. It may not end up being the work of Russia, but they’re probably rolling around like pigs in mud over this. My theory is that this is Russian doing. I know Wikileaks says it’s from disgruntled employee(s) but they have no credibility. The timing of the leak is just too suspicious, for me. there is no comparison to the NSA leaks. What Snowden did was wrong, but being outraged at his dumps is much more understandable. this is all targeted. You’re a fool if you don’t think other nation states hoard exploits and bugs for their spying benefits.
How can Apple state that most vulnerabilities are fixed in their latest iOS, but Cisco’s blog says they can’t really analyze how this affects them?
Having not looked through the documents in question, it could simply be a matter of detail explained in the dump. If there’s enough detail in the dump to point Apple to the area they need to look at then it’s just a matter of reviewing code for anything which would match the details in the dump.
In the case of Cisco it sounds like the detail wasn’t specific enough for them to narrow down which code they should be reviewing beyond a huge swathe of code in a huge array of products. Cisco has far, far, far, far more product lines than Apple, and without a whole lot of shared code between lines. On top they’re sometimes superficially similar, but underneath they’re often very different creatures.
If the leak was of docs associated with the team assigned to respond to Russian hacks, I’d guess Russia released this stuff on WL because we are taking some actions against Russia and they aren’t happy. Doubt the timing has anything to do with DJT’s stupid comments, more to do with Russia telling Trump to get his act together and stop the IC from doing whatever they’re doing.
Great writeup Brian! What I take from this is that there is a national security need for an agency or administration similar to US-CERT that is tasked with finding weaknesses in devices, firmware, software and infrastructure and that coordinates with manufacturers. Similar in idea to Underwriters Laboratories. As you note, “not every company has a budget of hundreds of millions of dollars just to do basic security research.”
Also appreciated the link to the discussion on NSA errors re signatures and tool reuse. Very eye opening, and as you say, it was a fascinating read!
Why doesn’t the CIA hack the Russian hacker Guccifer 2.0 , who hacked into the Democratic National Committee and John Podesta’s email ?
Guccifer 2.0 has a Twitter account and a Word Press account?
Guccifer 2.0 contacts all kinds of media outlets such as Motherboard, BBC and The Hill with Text messaging and Twitter Direct messaging. Why can’t the CIA hack into Guccifer 2.0’s Twitter account if they have such a threatening global covert hacking program ??
Unless Gu 2 is a complete idiot, which seems unlikely, there’s nothing of interest in his Twitter or WP files. They’re just ways to publish stuff from other places.
You might want to check the Smoking Gun dot com website. The Guccifer 2.0 twitter account has DM’s to and from Trump campaign Roger Stone, the campaign official who tweeted in advance that the Podesta leaks were coming. So yes, that account definitely has something worth looking into.
The Wikileaks stuff presumably came from the Russians, and unlike previous dumps this one was all organized and included helpful press releases. I would assume the Russians took out some stuff, and added some disinformation.
Is anyone looking at it from that angle?
There is so much misinformation going around, I heard from another reputable source from the security field that these documents suggest that the whole idea of these leaks resulting from Russian hacking is actually bogus and that its the agencies who have the ability to impersonate foreign state actors, Suggesting that this is all being done by US agencies tring to make it look like the russians.
Who do you believe?
That certainly seems to be the meme-du-jour for the Trumpkins: Russia is innocent, there’s no Russia connection. This was all a false flag operation by the CIA.
(And all the connections to Russia and lies about them? Pay no attention to the man behind the curtain!)
Being spread by the usual alt-right suspects @ Breitbart et al, and Russia. And of course as outraged as the Republican president usually gets over leaks, this one doesn’t seem to have bothered him. Almost as if he sees it as useful.
Maybe Congress should be focusing on repealing and replacing the Patriot Act. In addition to this latest document dump, if Trump’s accusations are true about wiretapping, as reported by the New York Times for weeks, then our government has been using these tools, that were given to them for fighting terrorism, for political means. Security is important, but government accountability is just as important.
Great idea about crowdsourcing security vulnerability notifications by the way!
If Trump’s accusations about being wiretapped are true, it means that a warrant was issued by the FISA court after probable cause was shown.
Your comment assumes the wiretap was legal and that the justification presented to the FISA court was truthful.
The head of the FBI suggested that the Department of Justice represent that no wiretap was ever requested.
No DoJ request means no FISA court approval.
That would make the wiretap extralegal.
…or there was never a wiretap.
Whoever is doing it, they are doing us a small favor – they are waving the warning flags the only question is are we going to pay attention to them?
What we know –
1. The biggest security problem remains the people involved who have access to the information and systems.
2. You can bet that for everything you know about what they can do there are two things you don’t know. No one compromises their best methods to gain only a fleeting advantage (remember the Enigma and Japanese Naval Code experiences).
3. Showing a little bit of your hand can gain you a lot of useful information on how the opposition reacts when under attack at very little cost and risk. That info is then used to inoculate your real weapon against detection and/or counter-measures.
#1 is so true. From the post “The archive appears to have been circulated among former U.S. government hackers and contractors in an unauthorized manner, one of whom has provided WikiLeaks with portions of the archive.”
So in the end, the real problem is that these weapons (trojans, ZDE, etc.) are unlike any weapon in history…they can be re-created at will from memory. If I try to steal an aircraft carrier or a nuclear bomb, someone is going to notice. If I walk out of my 9-5 at the CIA with the knowledge of a zero-day exploit (ZDE) I can drop by Best Buy, pick up a laptop, go to an internet cafe, code up the ZDE and send it to the power grid and shutdown a city. I don’t know of any such ZDE’s but SCADA exploits have certainly been explored by the three-letter organizations (e.g. STUXNET). The key point here is the old adage “Knowledge is power” in the Internet age, maybe it should be “Knowledge can easily be weaponized”.
NBC reports that the CIA and FBI knew late last year about the thefts and have been searching for the source of the leak. Why, once that happened, would they not have contacted vendors and service providers to notify them of the need to patch vulnerabilities???
reut.rs/2lZiNdI
It all boils down to your priorities. If your chief priority is spying on foreign and domestic netowrks, then you stockpile zero days, use malware aggressively regardless of what heppens next, etc. If your priority is homeland security, you disclose the holes, help domestic firms, train the public etc. The choice has been made a long time ago and, unfortunately, the masterminds of these policies weren’t code monkeys or gizmo geeks. They were people from the intelligence community who valued offence and, as shown in this and similar cases, pretty ignorant of the consequences of their actions. Now the genie has completely left the bottle and those who thought themselfs as un-hackable are paying the price.
Smart phones and smart tv’s are NOT safe to use. Those in high places and those with something to lose need to understand this. The single best line of defense on the iphone is the initial set of numbers used to login once the screen goes blank. After that, anything goes.
This is NOT anything new that just came about with Trump. We have been discussing all of this for many years now. It is actually at the heart of why this website exists in the first place. These devices ARE vulnerable. Routers have been compromised. ANY degree of ‘surprise’ when it comes to “wiretapping” of so completely ridiculous. If you use these devices, you HAVE BEEN WIRETAPPED. It does NOT matter who you are or where you are in the world. Discussions and concerns of NSA spying do have merit. It is no longer something that can laughed off as “conspiracy theory”. Technology HAS changed everything. People NEED to come to grips with this.
Assange is a threat just simply for the fact that he has dirt on so many people in places of power. His personal political views are completely irrelevant.
The whole thing regarding ‘Russian hacking’ is a red herring. It’s a some and mirrors deflection to keep the population confused enough to miss what is actually happening. I have no doubt the Russians have their under-the-table paid-for hacker groups. So does China. We all already know this. This is no surprise. We have discussed this at length on this website many times in the past. But that is a very different thing from this idea of “hacking the election”. I have seen absolutely NOTHING that makes me think Russia wanted Trump to win. If anything, Russia wanted Clinton to win. Clinton is the one that would have weakened the U.S. to the point of Russian attack (militarily). The Clintons are well known for their treason, subversion, and criminal activity. This goes back decades. Long before Trump had any idea of running for president.
Password Scattertothewind go look that up. The vault Clues and its 1% of the total. Things are getting interesting since they replaced Juli with a crap video program.
Alice Cooper said it best, “Welcome to my nightmare”
Or Pink Floyd’s “Welcome to the Machine”…
The CIA has a long reputation of sacrificing those that should be benefiting from it. From training foreign militants, funding murderous leaders, allowing hundreds of tons of cocaine to traffic into the US in exchange to deliver guns to contras on the return trips. This is no surprise.
If they worked to remove exploits and make people safer from these hacks, that would be one thing. but that is not they kind of people they are and hire. It is a scourge to humanity and perpetuates secret wars.
Like a crooked mechanic, that breaks something every time you bring your car in, so that you come back to get it fixed. The CIA keeps itself employed by creating the environment they need to thrive.
Indeed, the entire agency should be abolished.
Does an open democracy need an information gathering agency to protect its citizens? Sure. But the CIA has long ago strayed light-years from that mandate of simply gathering information.
Should planning assassinations of foreign political players, torture programs, working with criminal groups such as the Mafia, kidnapping, etc. be part of an American government agency’s peacetime raison d’etre?
The CIA should be phased out and its intelligence functions can be absorbed either by another existing agency or a newly established one.
There’s enough sociopathology in this world.
This whole thing is interesting. How many people are equating the CIA with what the NSA does. CIA is foreign surveillance and espionage.
That being said, the trove of information in this leak being public, now hurts some of our capabilities. It also leaves us way more vulnerable.
I really think there are 2 big questions that come out of this:
1) How can the CIA not just plug the leak, but prevent another even more damaging leak?
2) Will the vendors patch the exploits revealed?
Question 1 is important for the country and question 2 is important for the individual. I honestly doubt we will be seeing a trove of patches come out to protect the individual anytime soon. Companies will figure that the hoopla will die down before they have to spend the time, effort and money to patch things. This is the real danger, as it leaves way too much open for being exploited.
It is no surprise they are looking us but they should have no business doing something like that in EU. I have no problem them sniffing in US. Seems like this whole system is unregulated about this.
Brian — the website https://www.linkedin.com/pulse/cia-hacking-tools-review-cisco-primary-target-craig-dods now says:
“Due to unforeseen circumstances, the technical details of this article have been removed”
Hrm. That’s odd. Well, I still have it open in a browser tab. Here it is:
https://krebsonsecurity.com/wp-content/uploads/2017/03/CIA-Hacking-Tools-in-review_-Cisco-was-a-primary-target-_-Craig-Dods-_-Pulse-_-LinkedIn.pdf
The cat has long been out of the bag when it comes to hacking. My thoughts are if the U.S. doesn’t stay on the forefront of this, some other Nation, State, or rogue group will.
I wished we could all live in harmony, but that’s never going to happen. Someone will always try to steal your lunch money and you must be prepared.
Despite everything…, the U.S. is still the best game in town!
only question remainds here?
Why the police cia should survailence
regular citizens? And hack in their devices?
For what purposes? The citizens doing allready
what they should they work they pay taxes and etc.
why someone should spy on them ?
Can anyone explain it to me ?
Thanks for providing some clarity Brian. From reading media reports one could be lead to think that any phone can be hacked by anyone. What most media isn’t reporting is what’s required to actually exploit these vulnerabilities. It’s not as easy as someone in Langley pressing a button to hack your phone or TV. The same attack methods apply: dodgy websites, dodgy attachments, dodgy software, physical access.
I recall the maxim that “It is ok to hate us, as long as you still fear us”. If those well-funded entities offer up such “leaks” to the public, I suspect it is by their own design. NBC is now cited as a credible source???
Any box I can sit in front of for 30 minutes will be serving me coffee…..
It may have been completely coincidental, but yesterday Samsung pushed out a software update for my 2015 model Smart TV — I suspect they’ll be doing that for all of the post-2013 models in the aftermath of this story breaking as the company just can’t really take much more bad news this year if it wants to survive intact.
I just have to wonder about a few things here.
1. There are several thousand redaction in this dump. Like 10s of thousands. How does Wikileaks, an organization of no more than a handful of employees comb through this much data to make those redactions.
2. the timing of this dump is almost too good for President Bannon and his mouthpiece, Donald Trump.
This will no doubt slow down the investigative work of the IC into Russian actions with the election. I’m sure Trump is probably happy about this. That baffon has no understanding of security. But neither do most people, for that matter. they’re all suprised to learn that their smart TV can be hacked into. If they just read a newspaper over the last two years they’d know that hacking into TVs is old news.
This kind of dump just pisses me off. Nearly every other nation state has similar capabilities. this puts the US in a much tougher position to complete it’s espionage work. Wikileaks is just a mouthpiece for the Russkies. These are sad times we’re living in. Being upset at the Snowden leaks is much more understandable than being upset at these leaks. this is all targeted spying, not broad surveillance. But don’t have faith that the American people will know the difference.
A few items I would assume are true.
1. Known and revealed security holes will be fixed.
2. Any holes discovered by NSA and CIA are likely to also have been discovered by other well funded state actors such as China, Russia, and Israel.
3. This means most of the items revealed by Wiki Leaks are already known to potentially hostile external sources.
4. The publication of these holes will make the internet more secure in the medium time frame, will the very short term may be more dangerous until these holes are patched.
5. In the long term more holes will be discovered.
6. When more documents are leaked in the future the new holes will be patched.
7. The cycle will continue.
I have personally disconnect my smart TV for direct internet connection and use external devices for bringing streaming media to my TV. Anyone spying on my home would simply be bored to death, but I do this on principal.
Computer microphones can be disconnected when no needed and cameras can be taped over.
Smart Phones are the more likely source of “spying”. Controlling the microphone, camera, and GPS via malware is probably already in the WikiLeaksDump. Most of us use these 3 pieces for conveniences like Google Maps and Video calling. The trick is to come up with ways to allow the conveniences but stop the prying. Of course this is besides the personal financial data that passes through our phones.
Again in my case this is principal. My life would just be boring to the NSA or the equivalent from other countries and local police. However the principal of my personal business being none of any governments is very strong. The same for private companies.